Abstract
The collection of information is one of the most crucial processes in many internet-enabled applications for multiple mix-zones over road networks. It is essential to use road networks for prolonged time duration in an energy efficient manner. However, network life time increases in response of reducing the stability period (i.e. time required before first node dies).The stability period reduces due to the high energy variance of nodes. In this paper, we present a protocol named as clustering based energy efficient and communication protocol (CEECP) for multiple mix-zones over road networks, which is proposed to reduce the loop holes of prevailing clustering protocols. Additionally, we present a novel CEECP for chain scenario to connect with the road side units for gaining benefits of V2V as well as, V2I communication for Cooperative Traffic Information Systems. The stability period is responsible to preserve coverage properties of the network. It analysis that as the stability period increases, the trustworthiness of the network increases. Hence, it is indispensable to articulate a clustering protocol that shall be energy efficient, low energy variant and of high stability. It has been proved that our scheme outperforms SEECP and VBN as well as, includes its variants with respect to stability period and energy variance.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
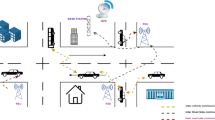
The multiple mix-zones over road networks are data gathering networks that comprise of highly populated equally distributed entities, which are responsible for the reliable monitoring from the far off distance [1]. Road network can be defined as the special type of networks which may provide different type of services to their users such as message alerts, driver forecast and infotainment. Additionally, there are two kinds of communications that can be achieved under this environment, which includes vehicle to vehicle (V2V) and vehicle to infrastructure (V2I) [2, 3]. It is evident from the existing literature that communication among the vehicle can only be achieved by using wireless communication; therefore, it requires designing of an efficient and secure communication in this environment among different components. Road network plays a very significant role in a number of applications of multiple domains related to ITS, like driver security, vehicular security, traffic congestion, weather forecast and brake warning [4]. Thus, there is an immense need of an inter-vehicular communication system which will be secure, robust and entitled to deliver safety related message within due time. Numerous efforts have been made to standardize the construction and deployment of road networks. There are many standardized organization like IEEE, which have been proposing a set of standards to describe the architecture of road network. This has been known as wireless access vehicular environment (WAVE) or IEEE 802.11p that defines layers to support WAVE communication. As a matter of fact, existing solutions in the market related with the secure communication over the road network suffer from various challenges including high traffic density and high mobility of nodes on the roads [5]. Therefore, it is indispensable to safeguard sensitive information which must not be apprehended by malevolent attackers in the network. Additionally, the system must be efficient enough to authenticate the driver’s identity and at the same time, must safeguard the confidentiality of passengers and drivers. The IEEE 1609.2 standard has described the phenomena of security services for vehicles to validate other entities in the premises by using certificates, which are managed by centralized certificate authority (CA). On the other hand, it is very difficult to deploy PKI in road networks and are articulated for those networks which are centrally controlled and have ubiquitous connectivity. Road networks may also suffer from relatively high velocity and constrained mobility pattern, due to which it changes its topology frequently [6]. Whereas, PKI deployment in road network articulate for centralized networks has a lot of problem with respect to scalability, because it is strenous for a vehicle to access CA due to high mobility of vehicles [7, 8]. Nevertheless, as the numbers of CAs are small, it may cause single point of failure; whereas, if we increase the number of CAs, it will definitely raise the network overhead. There are certain existing solutions [9, 10], which may consider RSU as CA. Also, it is imperative to note that the density of RSUs may be sufficient enough to cover the range of every vehicle over the road network [11].
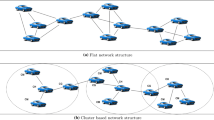
To mitigate the above shortcomings and limitations of road network, a new concept of vehicular cloud computing (VCC) has shown a remarkable development for next generation road networks. Vehicular cloud is a new concept that provides innovative solutions for the above shortcomings in road networks. It provides a distinct interface that enables an administrator to observe and react to the specific events. The major drawback of such networks lie in the constrained resource devices, which may be power and processing units. Moreover, the exceptional qualities and limitation of roads may lead to the several tasks, that may include clustering [12, 13], routing [14], node localization [15], system security [16], and time synchronization. Also, fast and secure data transmission [17], energy efficient solutions [18] and longer system lifetime [19] can be the main problems for road network. A user may directly communicate with RSU during communication over road network, and in response, RSU may communicate with reported server [20–22]. Despite, the existing hurdles to articulate an energy efficient communication mechanism with cost effective solution and self-connectivity, there is an immense need to focus on energy consumption and transmission range which may result in energy constrained systems [23]. Contemporary research has revealed that, clustering is an extensively used process in many applications that will excellently lower the energy ingesting of road network environment [24]. During the execution of clustering protocols, information collected by member vehicle is transferred to RSU via reported server (RS). Therefore, the energy utilization in the network using clustering protocol is probably less as compared to the energy transmitted directly [25, 26]. Nevertheless, in cluster based routing, RS gets overloaded due to improper cluster formation that may result in extraordinary energy drainage of RS and the resulting performance of road network gets an adverse impact. Analysing previous problems we can eventually deduce that RS selection and their load balancing are also the key issues for clustering road network [27].
Mix-zone is a special region in a road network which will enable user to change his identity in an anonymous method, so that an adversary may not establish a connection between the old and new pseudonym. The user anonymity in mix-zone can be ensured by monitoring the number of users entered, changing their identity and their exit from the mix zone in such a way that the linkage between their old and new pseudonym must not be revealed.
1.1 Contributions
Due to intrinsic disadvantages of prevailing approaches such as; lack of consideration for the market penetration rate of equipped vehicles, and less robust and unstable structure, we are motivated to propose a new cooperative traffic information system. Henceforth, in this paper our main objective is to introduce a hybrid approach for achieving traffic information of vehicles in optimized manner and estimate traffic density of roads. Our main contributions are as follows:
-
1.
We have given a novel clustering based energy efficient and communication protocol (CEECP) for chain scenario to connect with the road side units (RSUs) for gaining benefits of V2V as well as, V2I communication for CTIS, respectively.
-
2.
We have introduced a technique where a small group of members are discarded before converting into a cluster, so as to control the number of formed clusters in road segments.
-
3.
We also offer a unique technique for overviewing information related with traffic in lower penetration terms of equipped vehicles.
-
4.
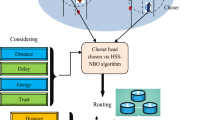
In order to attain enhanced cluster stability, we are allowed to select those vehicles as cluster heads (CHs) that may have a maximum trust value and strong connectivity among them. Our proposed technique acquires higher clustering efficiency by employing the vehicular cloud infrastructure.
-
5.
Various performance evaluation metrics are used to determine the overall outcome of the proposed scheme where the final results obtained are found to be satisfactory in different network scenarios.
2 Network Model and Assumptions
We assume a road network which consists of a number of vehicles that are spread uniformly over a field for constant monitoring of environment. As far as network model and the vehicles are concerned, we further make several assumptions.
-
1.
Once RSU and vehicle nodes are deployed, they are assumed to be stationary. Whereas, RSU is placed away from the road network environment.
-
2.
Sensor nodes are not equipped with GPS or other location detection devices thus, being oblivious of location.
-
3.
Reported sever gathers information and data which is periodically sent to vehicle nodes.
-
4.
We further assume that each vehicle node has a distinct identity (ID) and all nodes possess similar resources and capabilities.
-
5.
Nodes possess the ability to work in a low power sleeping mode or in an inactive mode.
-
6.
The amount of transmission power can be adjusted by RSU which controls power level and may be placed to the desired recipient according to their distance.
-
7.
The links are assumed to be symmetric. If the power of transferring node is known, a node can assess the distance to another node on the basis of the received power of signal.
2.1 Traffic Information Management Protocols
A self-organizing traffic information system (SOTIS) is proposed in [9]. It is capable of operating in a radius of 50–100 km approximately, of an individual user. When a vehicle gets information, it is determined that the information is correct and updated as compared with recent available information. This is achieved by comparing that information with a ‘knowledge base’, and subsequently, results of the analysis are further transferred. Moreover, another system called Traffic View is proposed which emphasizes on the data aggregation [10]. It focuses on collecting and transmitting information about a vehicle’s speed and position. Traffic reports are sent to the center through Internet via UMTS in vehicles which are equipped with the CoCar system. Subsequently, the information from other sources is also combined with these reports. Then, the processed traffic information is transferred from the center to all vehicles belonging to cell which originated the reports.
Furthermore, the concept of introducing network is proposed for streets and highways communication. This is known as road network [3]. A remedy is proposed to measure the density of road traffic at any given time in urban environments in [14]. Another prominent aspect for road traffic estimation is the learning capability. Hence, a model is proposed which is known as a classification and regression trees (CART) model which forecasts the short-term traffic volume at locations.
Another prominent aspect that is focused for traffic estimation is the learning capability. A model is proposed in [15] known as a classification and regression trees (CART) model which forecasts the short-term traffic volume at a locations. It can be achieved by the following paradigm: Introducing the concept of decision tree, one has to classify the historical traffic states by applying the linear regression models and then constructing the tree model by storing weights in the leaf nodes. Finally, future traffic information is predicted by allocating the current state vector to the most congenial historical pattern and regression model. Moreover, OLWSVR approach has been proposed by the researcher in [16] for the purpose of short-term prediction of free way traffic data. This approach has harmonic SVM for regression by using weighed learning method as it is an online weighted support-vector machine for regression.
2.2 Problem Formulation
Recent study has shown that traffic prediction aims to anticipate traffic conditions of the road points for the up coming events consisting of current and historic traffic conditions. It is comprehended that, traffic at near by road points may effect each other in terms of temporal domain and as well as, spatial domain. This has encouraged us to investigate traffic clustering (Sect. 4). Our analysis in section-4 concludes that clusters on a specific time occurrence on various days remain stable. Study has also shown that the influence of one of the road point on another road point inside the same cluster may get higher then the one in a dissimilar cluster. So, we have considered traffic forecast cluster by cluster. In this section, we have proposed our technique to anticipate the up coming traffic conditions of all road points that shall reside in the same cluster. Besides, it may be compared with the case when one neural network is fabricated from the input data. It shall resolute that which (clustering) panel can be helpful for traffic anticipation. Let us assume the current time. Obviously, the best option can be P*t0, which may be responsible for all traffic conditions of the road points at a particular time during past days. When P*t0 is employed, there occurs a clustering change in P*t0 and in response all historical data must get stored. Hence, the neural networks related to the different clusters may be lost and new ones may be fabricated from the previous data for the new clusters. This may be the wastage of time as well as storage resources.
Henceforth, we have decided to select the clustering approach acquired from the oldest historical traffic data. This may not considerably distress our estimation results, because real traffic data shows stable clustering property.
3 Energy Dissipation Radio Model
In this scenario, a modest energy mechanism is developed where signals are transmitted and amplified when the transmitter disperses energy to execute the radio electronics. The receiver disperses energy for reception. Although, for relatively short distances, the free space model is employed [2]. For the purpose of larger distances, multi path fading model is used. [4, 5].
We further formulate a model for road network related to those used in [6, 10] in order to achieve our proposed protocol. For this, we have based our model on following assumptions:
-
1.
RSU is stationary and positioned away from the road network-field where all the vehicle nodes are similar in nature, possessing reserved energy and initiate with constant energy.
-
2.
The vehicle nodes may change their transmitter power as they possess power control abilities.
-
3.
Each vehicle also possesses the ability to transmit directly to RSU or to any other node.
-
4.
Nodes have no mobility and are assigned with an identification (id) number.
-
5.
Vehicles have data to transmit to RS because they sense the range of transmission in atmosphere at a stable rate.
-
6.
The vehicles have variable communication range possessed by the multiple mix-zones where the data can be transmitted outside communication range of that cluster by RS.
-
7.
The radio model used in [7] is same for all the analysis and may be referred for more details. Equation (2) explains the total transmission cost for sending a k bit message to a distance d meter.
Transfer a k-bit data package over a separation d, the energy ingestion is:
The term ETx represents energy consumed per-bit throughout transmission. Eamp(d), amplification energy per-bit, is given by:
The parameters εfriss_amp and εtwo_ray_amp denote amplification features for free-space and two-ray model accordingly. So d0 can be computed as:
To obtain a k-bit data package the receiver expands:
4 Protocol
4.1 Clustering of Vehicles
The vehicles which are well equipped, formulate dynamic clusters whereas, the most satisfactory and suitable amongst them form RS [18]. RS acts as a source for controlling and propagating data within the clusters. The clusters which are dynamic move with vehicles travelling at high speed because they are mobile in nature. Consequently, dynamic cluster design results in comparatively steady topology even with high-speed vehicles as long as, the vehicles are moving at a similar velocity.
4.2 Cluster Formation Procedure
When a primary vehicle enters different section of the highway, it initially searches existing clusters. That is accomplished by communicating with an RSU if it is within its communication range or by propagating a cluster-join-request-message (MCJR). As explained in protocol, when a vehicle which is called Vinit, does not receive any response for staying time (Ts), it originates the process of cluster formation to detect cluster member by broadcasting Minit message. Moreover, vehicles establish proximity relationship by revealing their existing speed and position data in HELLO-messages (MHELLO) to other vehicles and Vinit which are in their range of communication. A primitive group is formulated comprising of vehicles which are travelling in similar directions and in the neighborhood of each other. Nevertheless, all nearby vehicles cannot be incorporated into a single cluster because of the varying speed levels of vehicles in certain areas. In addition, the development of small clusters with a little number of members is discouraged by setting a member threshold.
4.3 Cluster Maintenance Procedure
Apart from cluster formation protocol, a cluster maintenance protocol is also required to deal with topology variations which occur due to frequent fusion and non-fusion of clusters by vehicles. For this purpose, we use maintenance protocol which consists of three different situations as mentioned below in Fig. 1.
The vehicle called Vinit, originates process of cluster formation to detect cluster member by broadcasting Minit message after waiting for some time (Tw) when it does not receive any response. Moreover, vehicles establish proximity relationship by revealing their existing speed and position data in HELLO-messages (MHELLO) to other vehicles and Vinit which are in their range of communication. A primitive group is formulated comprising of vehicles which are travelling in similar direction and in the neighborhood of each other as illustrated in Fig. 3. Nevertheless, all nearby vehicles can not be incorporated into a single cluster because of the varying speed levels of vehicle in certain areas. Also, the development of small clusters with a little number of members is discouraged by setting a member threshold (MEMthr).
Additionally, Vinit measures the speed disparity of all its nearby vehicles with a threshold (_Sthr) for selecting cluster members bearing the similar speed level. The nearby vehicle is considered as a basic group member if speed disparity of relative neighbor of Vinit is comparatively lesser than the threshold. It helps in assuming that cluster members travel at a similar speed. Vinit propagates Mcluster message, if it finds the number of members to be more than MEMthr, so as to inform its ID to all cluster members. If it finds the number of members to be less than MEMthr, it discards the process of cluster formation and again waits for Tw as shown in Fig. 4. Thereafter, non-clustered members respond by accepting the M cluster and place their CH ID temporarily to the ID.
4.4 Cluster Joining
When a clustering gets a membership request message from RS which is non-clustered, it will agree to accept the vehicle. It incorporates its identity (ID) to the list of cluster members conditionally if its comparative pace lies within the cluster threshold (_Sthr).
4.5 Cluster Configuration Protocol
Cluster configuration protocol regulates and controls the state transitions of the finite-state machine (FSM). It comprises of seven state-transition conditions on each mobile vehicle for the protocol FSM (1) Initiate/Enter a highway: in this state, the medium only enters the street or highway. (2) Cluster joining: a pseudo-vehicle, which is not a part of any cluster, gets the authentic advertisement message from neighboring RS. The RS broadcasts the invite-to-join (ITJ) advertisement message every tj time unit. The pseudo- vehicle inspects the strength of signal denoted by Pr after it receives the ITJ message. If signal strength is found to be more than the predefined threshold that is denoted by Pth r, we consider the received ITJ message as authenticated. As a result, the vehicle shoots a request-to-join (RTJ) message which comprises of ID and network address of vehicle, to the advertising cluster head. The MZ incorporates the requesting vehicle into the cluster-member list and sends it an acknowledgment (ACK). The cluster size or the cluster radius is determined by threshold Pth r and is denoted by LC. (3) Electing the cluster head: a pseudo vehicle gets the ITJ advertisement messages within tj time units if it lies within the transmission range of RS. This is due to the fact that the vehicle replicates the ITJ advertisement message every tj time unit. If a pseudo fails to get a valid ITJ advertisement message within tj time units, it will choose itself as RS and issue new pseudonym. (4) Losing contact with the cluster head temporarily: there occurs a change in the state of vehicle from cluster member to pseudo cluster member in order to ensure timely delivery of safety messages. It happens when cluster-member vehicle fails to get the schedule assignment broadcast every time unit. In pseudo-cluster-member state, the vehicle receives/transmits safety messages by tuning Transceiver I to the ICC channel. Whereas, the disconnection may result from error in wireless channel and the pseudo-cluster-member vehicle attempts to continue the communications with the previous pseudonym by preserving Transceiver 2 functioning on CRC channel. (5) Failing completely to establish contact with the RS: it results when the pseudo-cluster-member vehicle fails to receive the schedule assignment consecutively for second time. The pseudo cluster- member transforms its state to pseudo when its contact is completely lost with the previous pseudonym. If it fails to receive any message from this vehicle consecutively for third time, it will remove this vehicle from the member list. (6) Locating the RS: the pseudo-cluster-member vehicle continues communications with the RS and transforms to state of cluster-member if it again gets scheduled assignment from RS. (7) Merged by other cluster: if the vehicle gets authenticated Invitation to Join (ITJ) advertisement message from the nearby RS, which comprises of more cluster member vehicles, it results in merger. If the gap between two vehicles is less than LC, there occurs a merger. LC is regarded as the nominal gap between two vehicles, which can reduce the impact of oscillatory gap between nodes. The vehicle transforms to the state of cluster member and connects with the adjoining RS, whereas, previous cluster-member vehicles either connect with nearby MZ or configure to another new cluster corresponding with the cluster configuration protocol (Fig. 2).
5 Experiments and Evaluation
5.1 Experiment Setup
Performance analysis of CEECP protocol has been measured according to average energy remaining in the network, stability period, energy variance among nodes and network lifetime. The overall performance of CEECP is equated with SEECP [4] and VBN [5] protocols. We have performed simulations using SUMO simulator [28] as shown in Fig. 3, and simulation parameters shown in Table 1. The simulation scenario is comprised of randomly distributed 10,000 vehicle nodes deployed in 14 km × 12 km area having 500 RSU at the road network [29, 30]. The protocol having various transmission range comparison is shown in Table 2.
In this study, we have focused our analysis on the effects of SEECP protocol in heterogeneous as well as homogeneous setups with RSU at the road network environment.
We have analyzed the traffic volume for v(Ξ(v)) which is computed as the weighted average of the actual clusters by means of the weight wi(t), ∀t∈Ψ as given below,
Moreover, θ (t) represenst the traffic volume (i.e. set of equipped vehicles) of cluster t.
5.2 Performance Evaluation
The vehicles are designated by the cluster-head to function as a dispatching point throughout communications between clusters. It may contain the cluster-head itself. Figure 4a shows the percentage of vehicle traffic selection and gives a reduced percentage of vehicles. Similarly, the CEECP outperforms the SEECP by decreasing the ratio of MPRs around 20%. This outcome gets justified by the transmission power consumption of the connectivity factor as shown in Fig. 4b.
Percentage of stability: This can be calculated by applying division operation between the number of current vehicles in each cluster and the previous number of vehicles in the same cluster. The distance element ensures that the clusters are shaped by vehicles having convergent distance to navigate before reaching the endpoint as shown in Fig. 4c.
Packet delivery ratio: For estimating the quality of service of a protocol, two metrics are considered; the end-to-end delay and the packet delivery ratio. The packet delivery ratio can be calculated by applying division operation between the total number of received packets and the total number of sent packets. Figure 4d shows that CEECP is able to increase this proportion. The main reason behind this fact is that CEECP is capable of increasing the connectivity, maintains the stability, and decreases the end-to-end delay as compared with other approaches. We have compared our method with existing methods based on packet loss during different trannsmissions ranges as shown in Fig. 5. Figure 5a exhibits Packet loss during 100 m transmission range, Fig. 5b exhibits Packet loss during 400 m transmission range, Fig. 5c exhibits Packet loss during 500 m transmission range, Fig. 5d exhibits Packet loss during 700 m transmission range. Moreover, experimental results have revealed that our method has less Packet loss during different transmission range as depicted in Fig. 5. Finally, we have compared packet delay of our method with existing methods as shown in Fig. 6. Experimental results have revealed that our method has outperformed the existing techniques. Figure 6a exhibits Packet delay during 100 m transmission range, Fig. 6b exhibits Packet delay during 400 m transmission range, Fig. 6c exhibits Packet delay during 500 m transmission range, Fig. 6d exhibits Packet delay during 700 m transmission range.
6 Conclusion
The major drawbacks observed in existing scenario for road networks are inefficient consumption of energy and operational network lifetime. A very important issue is to enhance the constancy period to conserve the coverage characteristics of the network. In this approach, we have given a threshold decision based clustering protocol which is appropriate for time critical applications. Moreover, we have also suggested CEECP protocol which can utilize lingering energy of nodes as a parameter for vehicle selection. The deterministic clustering selection helps in reducing the improper load balancing among the nodes and provides balanced energy consumption. The energy dissipation of vehicle is reduced by threshold based inter-cluster data transmission protocol. In addition, numerical calculations are performed for selection of clustering vehicles around RSU communication to minimize the energy consumption of distant CHs. Simulation results show that CEECP protocol outperforms SEECP and VBN protocols in terms of load balancing, energy efficiency, energy variance and stability period.
References
Bali, R. S., & Kumar, N. (2016). Secure clustering for efficient data dissemination in vehicular cyber–physical systems. Future Generation Computer Systems, 56, 476–492.
Memon, I. (2015). Authentication user’s privacy: An integrating location privacy protection algorithm for secure moving objects in location based services. Wireless Personal Communications, 82, 1585–1600.
Memon, I., Hussain, I., Akhtar, R., & Chen, G. (2015). Enhanced privacy and authentication: An efficient and secure anonymous communication for location based service using asymmetric cryptography scheme. Wireless Personal Communications, 84(2), 1487–1508. doi:10.1007/s11277-015-2699-1.
Tarhani, M., Kavian, Y. S., & Siavoshi, S. (2014). SEECH: Scalable energy efficient clustering hierarchy protocol in wireless sensor networks. IEEE Sensors Journal, 14(11), 3944–3954. doi:10.1109/JSEN.2014.2358567.
Cuomo, F., Rubin, I., Baiocchi, A., & Salvo, P. (2014). Enhanced VANET broadcast throughput capacity via a dynamic backbone architecture. Ad Hoc Networks, 21, 42–59.
Gustav, Y. H., Wang, Y., Kamenyi, D. M., Zhang, F., & Memon, I. (2013). Velocity similarity anonymization for continuous query location based services. In 2013 International conference on computational problem-solving (ICCP) (pp. 433–436). doi:10.1109/ICCPS.2013.6893578.
Gruteser, M., & Grunwald, D. (2003). Anonymous usage of location-based services through spatial and temporal cloaking. In MobiSys.
Bamba, B., Liu, L., Pesti, P., & Wang, T. (2008). Supporting anonymous location queries in mobile environments with privacy grid. In WWW.
Gedik, B., & Liu, L. (2005). Location privacy in mobile systems: A personalized anonymization model. In ICDCS.
Ghinita, G., Kalnis, P., & Skiadopoulos, S. (2007). PRIVE: Anonymous location-based queries in distributed mobile systems. In WWW.
Memon, I., & Arain, Q. A. (2016). Dynamic path privacy protection framework for continuous query service over road networks. World Wide Web,. doi:10.1007/s11280-016-0403-3.
Memon, M. H., Li, J.-P., Memon, I., & Arain, Q. A. (2016). GEO matching regions: Multiple regions of interests using content based image retrieval based on relative locations. Multimedia Tools and Applications,. doi:10.1007/s11042-016-3834-z.
Hassanabadi, B., Shea, C., Zhang, L., & Valaee, S. (2014). Clustering in vehicular ad hoc net-works using affinity propagation. Ad Hoc Networks, Part B, 13, 535–548.
Rajini Girinath, S. S. D. (2013). A novel hierarchical model for vehicular traffic regulation. Telecommunication Systems, 52, 2101–2114.
Memon, I. (2016). A secure and efficient communication scheme with authenticated key establishment protocol for road networks. Wireless Personal Communications, 85(3), 1167–1191. doi:10.1007/s11277-015-2833-0.
Memon, I., Chen, L., Majid, A., Lv, M., Hussain, I., & Chen, G. (2015). Travel recommendation using geo-tagged photos in social media for tourist. Wireless Personal Communications: An International Journal, 80(4), 1347–1362. doi:10.1007/s11277-014-2082-7.
Memon, I., Mohammed, M. R., Akhtar, R., Memon, H., Memon, M. H., & Shaikh, R. A. (2014). Design and implementation to authentication over a GSM system using certificate-less public key cryptography (CL-PKC).Wireless Personal Communications, 79(1), 661–686. doi:10.1007/s11277-014-1879-8.
Akhtar, R., Leng, S., Memon, I., Ali, M., & Zhang, L. (2015). Architecture of hybrid mobile social networks for efficient content delivery. Wireless Personal Communications, 80(1), 85–96. doi:10.1007/s11277-014-1996-4.
Kamenyi, D. M., Wang, Y., Zhang, F., Memon, I., & Gustav, Y. H. (2013). Authenticated privacy preserving for continuous query in location based services. Journal of Computational Information Systems, 9(24), 9857–9864.
Memon, I., Jamro, D. A., Mangi, A. F., Memon, M. H., & Basit, M. A. (2013). Source localization wireless sensor network using time difference of arrivals. International Journal of Scientific and Engineering Research, 4(7), 1046–1054.
Kamenyi, D., Wang, Y., Zhang, F., Memon, I., & Gustav, Y. (2013). Preserving users’ privacy for continuous query services in road networks. In 2013 the 6th IEEE international conference on information management, innovation management and industrial engineering (ICIII2013) Xi’an, China (pp. 352–355).
Gustav, Y. H., Wang, Y., Domenic, M. K., Zhang, F., & Memon, I. (2013). Direction and velocity similarity anonymization in continuous query location based services. In 4th international conference on computational problem-solving (ICCP 2013) (pp. 433–436). Jiuzhai, China. doi:10.1109/ICCPS.2013.6893578.
Cheng, R., Zhang, Y., Bertino, E., & Prabhakar, S. (2006). Preserving user location privacy in mobile data management infrastructures. In Proceeding of the 6th workshop on privacy enhancing technologies (PETs) (pp. 393–412).
Barkhuus, L., & Dey, A. (2003). Location-based services for mobile telephony: A study of users’ privacy concerns. In Proceeding of the 9th IFIP TC13 international conference on human–computer interaction (INTERACT).
Dahl, M., Delaune, S., & Steel, G. (2010). Formal analysis of privacy for vehicular mix-zones. In Proceeding of the 15th European conference on research in computer security (ESORICS) (pp. 55–70).
Wang, T., & Liu, L. (2009). Privacy-aware mobile services over road networks. Proceedings VLDB Endowment, 2(1), 1042–1053.
Dahl, M., Delaune, S., & Steel, G. (2010). Formal analysis of privacy for vehicular mix-zones. In Proceedings of the 15th European conference on research in computer security (ESORICS’10) (pp. 55–70).
Simulation of urban mobility (SUMO). http://sumo.sourceforge.net.
U.S. Census Bureau.TIGER, TIGER/Line and TIGER-related products. http://www.census.gov/geo/www/tiger/.
U.S. Geological Survey. http://www.usgs.gov.
Acknowledgements
This research has been funded by The National High Technology Research and Development Program of China (Nos. 2014AA123103, 2015AA124103) and National Natural Science Foundation of China (Nos. 61401040, 61372110).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Arain, Q.A., Uqaili, M.A., Deng, Z. et al. Clustering Based Energy Efficient and Communication Protocol for Multiple Mix-Zones Over Road Networks. Wireless Pers Commun 95, 411–428 (2017). https://doi.org/10.1007/s11277-016-3900-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-016-3900-x