Abstract
Vehicular networks (VANETs) are a subset of wireless ad hoc networks that enable communication between moving items and/or with the underlying road infrastructure. More comprehensive and individualized information may be exchanged thanks to wireless connectivity. Every problem relating to wireless communication and ongoing analysis among vehicles is handled by VANET. A new VANET routing model with a link breakdown handling scenario is presented in this study. The first step in the routing procedure is the selection of the best CH, for which the Hybrid Shuffled Shepherd NBO (HSS-NBO) algorithm is introduced and distance, time, energy, and trust are taken into account. Following the optimal CHS, the proposed link dynamic behavior (LDB) measure, link throughput (LT), distance, congestion, and routing are all taken into account. In order to prevent performance degradation, it is also necessary to estimate the connection breakage during routing. Effective management is required if the link breaks. This effort ensures better connection breakage handling by taking link reliability into account, calculating a new distance degree, and evaluating a new node's level of trust based on previous data transfer. In comparison to existing approaches like NBO, SSOA, HHO, LOA, and RHSO, the trust for vehicles counts 100 offers a higher trust of 89.21%.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The speedy raise in populace and development of vehicles creates a mess in urban areas with traffic jams and road accidents. Every year, nearly 1.25 million people around the world die due to road accidents. Meanwhile, anxiety, delays, and noise are the major causes of traffic jams [1,2,3]. These problems are solved by a smart and effective means of transport named VANET. VANET is a mobile network introduced for moving vehicles that acts as a bridge between the physical and digital worlds. The emergence of VANET [4,5,6] is to improve road safety and decrease road congestion. VANET not only obtains information on vehicle nodes and roads but could also provide route planning, road warning, and other services for drivers and passengers [7,8,9]. It can also assist to find parking areas, to pay for parking and tolls downloading music, video, and software updates, updating default vehicle navigation systems with real-time traffic situations, and so on. Generally, VANET [10,11,12] model has two components namely RSU and OBUs, where RBUs are installed on the roadside and OBUs are installed on vehicles with maps and GPS [13,14,15]; still, it has the challenges to limit its performance.
The challenges faced by VANET are intermittent connection, recurrent transforms in the topology of the network, and vehicle density’s uniformness [16, 17]. These challenges can be rectified by the usage of an effective routing protocol. RPs is classified into two categories. They have distributed routing and centralized routing. In distributed routing, the way of routing is selected previously instead nodes are elected dynamically from the relay nodes whereas centralized routing has a preselected routing path but it causes a problem packet transmission process due to the movement of the vehicle. The RPs in VANETs [18,19,20] can be broadly classified into four types: cluster-based RPs, topology-based RPs, location-based RPs, and broadcast-based RPs. The development of wireless technology helps VANETs in the creation of a larger spectrum to promote a higher volume of data transfers. The standards for wireless access are WAVE and DSRC. The WAVE is actually an updated version of DSRC, which was introduced for VANETs high-volume data transfer. Due to the great mobility of the nodes in the network region accessible, connection failures are highly prevalent [21,22,23]. After establishing the new parallel pathways prior to the packets saved in the buffer through the destination newly formed path, the node before the failure of packet buffers [24]. With VANET, comfort and protection are ensured in regard to petrol stations, weather, parking, traffic jams and emergency notifications [25,26,27]. The majority of the techniques listed rely on one-hop clustering, which only permits communication between one-hop neighbors. As a result, there are numerous clusters created and the coverage range is narrow, which lowers cluster stability. Furthermore, the bulk of these research projects merely took the location or speed of the vehicles into account while forming the clusters; the direction or equipment of the vehicles was not fully taken into account. When choosing the CH, these procedures also employed a variety of tactics, each with its own set of restrictions and disadvantages. Though, the performance of VANET routing is to be significantly enhanced to deal with the minimization of packet loss, link breakage, clustering problem, privacy preservation, etc.
Below points are the contributions:
-
Developed a VANET routing model with optimal CHS on considering the distance, delay, energy, and trust.
-
Performs routing on considering the distance, congestion, LDB measure with proposed evaluation, and LT.
-
Ensures better link breakage handling by considering link reliability, next hop selection with the calculation of new distance degree, and new trust evaluation of nodes based on its past data transmission.
Section 2 describes extant VANET routing works. Section 3 describes the system model on VANET. Section 4 describes optimal CHS and Sect. 5 briefs routing under proposed parameters. Sections 6 and 7 brief objectives and link breakage handling. Sections 8 and 9 explained the results and conclusions.
2 Literature review
2.1 Related works
In 2021, Chen et al. [28] proposed to solve data acquisition by using the protocol named TLBGR in VANETs. The protocol was separated into 2phases: next-hop selection and next-intersection selection. In 2021, Folsom et al. [29] designed a new NRHCS for VANETs. Concepts like cluster configuration, re-clustering, CHS, and adding and deleting clusters were carried out with factors such as vehicle displacement, and vehicle link counts. The vehicle with improved linkage support was considered as CH during cluster arrangement. In 2020, Manivannan et al. [30] presented a general idea of problems that arose in VANETs such as verification, privacy, and dissemination of secured messages. In 2019, RSU-assisted QTAR, a routing system for VANETs was presented by Jinqiao et al. Combining spatial routing's benefits with static road map data allowed QTAR to examine traffic data for individual road segments using the Q-learning algorithm. In 2020, Sun et al. [31] proposed an IVF model which formed a collection of vehicles at an intersection. In 2021, Mohammed et al. [32] introduced a 2HMO-HHO algorithm that forwarded data among destination and source vehicles. In 2021, Ammar et al. [33] solved the crisis of multi-criterion routing like reduction in e2e latency, minimization of network overhead, and increased e2e delivery ratio in VANETs. In 2020, in Cheng et al. [34] proposed a CP-oriented DC model for VANET. Based on vehicle features and nodes among vehicle nodes a connectivity prediction method was implemented based on connectivity amongst nodes. In 2023, Ali et al. [35] have suggested a brand-new clustering approach for VANET that is based on the Harris Hawks Optimization (HHO) algorithm. In 2019, Mohammed et al. [36] Using an imperialist competitive algorithm, a clustering-based routing protocol is developed in this paper, where nodes are grouped in accordance with movement information like vehicle velocity and node degree. In 2018, Bagher et al. [37] For VANETs with reliable applications, a clustering-based reliable routing technique was put forth in this study.
3 System model on VANET
The TA (server), a mobile onboard unit fitted with a vehicle, and an RSU are the three fundamental elements that make up the VANET system paradigm.
-
TA TA stands for the trustworthy management centre of the network. As RSUs and OBUs join the network, TA assists with registration and certification [38].
-
Road Side Unit RSUs are used to control and interact with vehicles that are within their communication range [38].
-
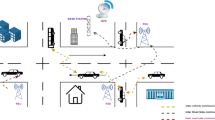
On-Board Unit On-board equipment periodically broadcast traffic-related status information. The selected network consists of the vehicles denoted as Vn, in which n implies vehicles moving to various sites and is specified as L1, L2, L3, L4, L5, L6, L7, L8 and L9. To go to the destinations, it is assumed that the cars would move at a constant pace. Any location designated as, AP1, AP2, AP3, and AP4 with a comparable coverage area is enclosed by an exact Access Point (AP). Congestion problems arise if the routes chosen are not the best ones. As a result, the best route should be chosen in order to avoid traffic and crashes and reduce congestion. Every AP has the capacity to be controlled by many vehicles.
Figure 1 illustrates the recommendedHSS-NBO oriented model for VANET routing.
4 Optimal cluster head selection
The optimal CHS is the initial phase for VANET routing that is done by considering.
-
a.
Trust
-
b.
Distance
-
c.
Energy
-
d.
Delay
-
Trust [39]: It is a joint measure, which guarantees mobility, reliability, privacy as well as security. It is split into indirect and direct trusts. It is modeled in Eq. (1), wherein, \(B\),\(A\) and \(C\) points to nodes, \(TS_{\left( {B - A} \right)}\) points to the final trust of \(B\) on \(A\) and \(W\) refers to the weight associated with trust.
$$ TS_{\left( {B - A} \right)} = W \times DT_{\left( {B - A} \right)} + \left( {1 - W} \right) \times IDT_{\left( {B - A} \right)} $$(1)$$ DT = \frac{E}{{D\left( {B,A} \right)}} $$(2)$$ IDT = \sum {DT\left( {B - C} \right) \times DT\left( {C - A} \right)} $$(3) -
Energy [40]: Here, the energy of each node is taken and its mean is computed to obtain the energy as shown in Eq. (4). The energy lies between 0.5 and 1.
$$ E = Mean\left( {V_E } \right) $$(4) -
Distance [41]: The distance amid each node to CH is assessed with Euclidean distance as revealed in Eq. (5).
$$ D_{iab} = \sqrt {{\left( {a_2 - a_1 } \right)^2 + \left( {b_2 - b_1 } \right)^2 }} $$(5)Here, \(\left( {a_1 ,b_1 \,} \right)\) points to coordinate of node and \(\left( {a_2 ,b_2 \,} \right)\) points to coordinate of CH. The overall distance is assessed by considering the mean of \(D_{iab}\) as in Eq. (6), here, \(i = 1,2...count\,\,of\,CH\).
$$ D = Mean\left( {D_{iab} } \right) $$(6) -
Delay [42]: It is defined as the ratio of distance and speed as exposed in Eq. (7).
$$ Dy = \frac{{\it Distance}\ \left( D \right)}{{Speed}} $$(7)
5 Routing under proposed parameters
The routing takes place on considering.
-
a.
Distance
-
b.
Congestion
-
c.
Proposed LDB measure
-
d.
LTI
-
Congestion \(\left( {Cn} \right)\) [35]: It is computed based upon the velocity of the vehicle as shown in Eq. (8–10). Higher the speed of the vehicle in the route; the less will be the congestion. Let U and Q refers to routes.
$$ P\left( {U / Q} \right) = \frac{{P\left( {U \cap Q} \right)}}{P\left( U \right)} $$(8)$$ P\left( {U \cap Q} \right) = \frac{{n\left( {U \cap Q} \right)}}{n\left( s \right)} $$(9)$$ n\left( {U \cap Q} \right) = n\left( U \right) + n\left( Q \right) - n\left( {U \cup Q} \right) $$(10)Here, \(P\left( {U / Q} \right)\) refers to congestion probability in route U or \(Q\).
\(n\left( U \right)\) refers to count of vehicles in \(U\).
\(n\left( Q \right)\) refers to count of vehicles in \(Q\).
\(n\left( {U \cap Q} \right)\) refers to count of same vehicle velocity in route \(U\) and \(Q\).
\(n\left( s \right)\) refers to entire count of vehicle in route \(U\).
\(n\left( {U \cup Q} \right)\) refers to jointvehicle velocity of route \(U\) and \(Q\).
If the probability of vehicle velocity is high, the congestion will be low and if the probability of vehicle velocity is low, the congestion will be high.
-
Proposed LDB measure The purpose to propose the Dynamic Behaviour model is to characterize the efficiency of the link connected with the subsequent hop forwarder of the candidate.
Therefore, the link’s dynamic behavior is defined as \(u = \left( {V_n ,\,V_i } \right)\) LDB [5], as in Eq. (11).
$$ LDB_u \left( {V_n ,\,V_i } \right) = ETZ_u \left( {V_n ,\,V_i } \right) - LTI_u \left( {V_n ,\,V_i } \right) $$(11)In Eq. (11), \(u\) implies link between \(V_n\) and \(V_i\), \(ETZ_u \left( {V_n ,\,V_i } \right)\) represents the link quality cost to select the link u among the candidate forwarding node \(V_i\) and present forwarding node \(V_n\), and \(LTI_u \left( {V_n ,\,V_i } \right)\) is used to estimate the obtainable bandwidth at Vi by means of physical intrusion models and throughput at the MAC layer.
$$ ETZ_u \left( {V_n ,\,V_i } \right) = \frac{1}{{d_{for} \times d_{rev} }} $$(12)In Eq. (12), \(d_{for}\) implies the delivery ratio of packets transmitted from \(V_n\) to \(V_i\), \(d_{rev}\) implies a delivery ratio of the packet transmitted from \(V_i\) to \(V_n\).
As per the proposed evaluation, LDB is modeled based upon \(X\) as shown in Eq. (13). In Eq. (14), \(\,\,LQI\) implies link quality indicator and \(X\) implies the influence of LQI.
$$ LDB_u \left( {V_n ,\,V_i } \right) = ETZ_u \left( {V_n ,\,V_i } \right) - LTI_u \left( {V_n ,\,V_i } \right) + X $$(13)$$ X = \left\{ \begin{gathered} 0,\,\,\,\,\,\,\,\,\,\,LQI \ge 0\,dBm \hfill \\ \left| {LQI} \right|,\,\, - 255dBm < LQI < 0dBm \hfill \\ 255,\,\,\,\,\,LQI \le - 255dBm \hfill \\ \end{gathered} \right. $$(14)$$ \,\,LQI = - 0.33^\ast d + 110 $$(15)The LTI for \(u\) among \(V_n\) and \(V_i\) is defined as in Eq. (16).
$$ LTI_u \left( {V_n ,\,V_i } \right) = IR_u \left( {V_n } \right) \times normaT_u \left( {V_n ,\,V_i } \right) $$(16)Equation (16), \(IR_u \left( {V_n } \right)\) is described by means of the physical interfering model and \(normaT_u \left( {V_n ,\,V_i } \right)\) implies normalized link throughput [43], which could approximate accessible interference and bandwidth at the transmitter. Equation (17), \(SINR\) implies signal to interference and noise ratio and \(SNR\) implies signal to noise ratio [5].
$$ IR_u \left( {V_n } \right) = \frac{{SINR_u \left( {V_n } \right)}}{{SNR_u \left( {V_n } \right)}} $$(17)If the interference is high on the receiver side, the link has poor quality.
-
LT measure [5]: The link throughput is measured at the receiving side which incurs no broadcast overhead except for the transmitter time-stamp, whilst the computing overhead is small. Presuming that \(V_n\) receives the packet \(K\) from \(V_i\), the throughput of \(u\) among \(V_i\) and \(V_n\) is modeled as in Eq. (18).
$$ LT_{u\left( K \right)} \left( {V_n ,\,V_i } \right) = \frac{size\left( K \right)}{{Delay_{u\left( K \right)} }} $$(18)
In Eq. (18), \(size\left( K \right)\) implies packet size received in bits, \(Delay_{u\left( K \right)}\) implies elapsed time among time-stamp at receiver and sender.
6 Objectives with HSS-NBO-based optimization
The objective considered here is the minimizing function as in Eq. (19). The energy, trust, LDB, and LTP should be high, while, the delay, congestion, and distance during transmission of data must be small. In Eq. (19), the summation of weighs \(\omega_1\)–\(\omega_7\) is 1, i.e. \(\sum {w_i } = 1\).
The optimal CH is elected in this work by means of a new HSS-NBO algorithm.
6.1 HSS-NBO algorithm
The conventional NBO [44] and SSOA [45] approaches are combined to form a new HSS-NBO algorithm. The combination of 2 standard optimizations will boost the optimal convergence rate. The arithmetical formula of the suggested HSS-NBO technique is described here.
In actuality, NBO is used to solve optimization problems since it is a population-oriented slope optimization technique.
6.1.1 Initial population
The entire issue recorded in the \(d\) dimension is depicted as a beetle as in Eq. (20).
Each beetle has a deciding variable. Some beetles, together with the population \(s\) and range \(p\) in Eq. (21), are determined arbitrarily l.
The term \(Pop\) implied the initial population of the beetle and \(nb_{x,y}\) implies \(y\) component connected to the beetle \(x\). Beetles create solutions as in Eq. (22).
On considering the objective, Eq. (23) shows the populace of beetles.
6.1.2 Aptness of each region to collect water
Every beetle gathers additional water and moisture if it selects a higher objective value. Equation (24) shows if a specific beetle area \(nb_x\) has the prospective to hold up a larger number of beetles.
\(Y_{\max }\) \(\to\) High capacity of beetle count,\(Y_x\)\(\to\) capability of beetles count at \(nb_x\),\(f\left( {nb_x } \right)\)\(\to\) beetle competence, \(f_{\min }\) and \(f_{\max }\)\(\to\) minimum and maximum beetle competencies. The emergence of beetles is shown in Eqs. (25) and (26). The whole beetles to look for water is \(Y\).
6.1.3 Moving toward damp areas
Let's consider beetle \(nb_x\), \(nb_y\) and \(Y_x\). We can compute the distance amid \(nb_x\), \(nb_y\) as exposed in Eq. (27), \(h\)\(\to\) order of normand \(\beta\)\(\to\) [initial humidity] Hum0.
The attractive count of a region to attract beetles is shown in Eq. (28), where, \(Hum\left( c \right)\)\(\to\) moisture quantity that \(nb_y\) felt from \(nb_x\).
The coefficient of humidity rise \(\kappa\) is revealed in Eq. (29).
Here, \(\kappa_0\)\(\to\)initial humidity increase coefficient, it and \(Maxit\)\(\to\)current and maximum iterations.
One beetle attracts other by the moisture sensing coefficient and current position. Equation (30) is employed to recognize this attraction mechanism.
In Eq. (30), old and new beetle location\(\to\)\(nb_y^{old}\) and \(nb_y^{new}\). The \(levy\) in Eq. (30) is given in Eq. (31), here, \(u\) and \(v\) \(\to\)particular random vector (0, 1) and \(\gamma\)\(\to\) 1.5 (constant).
6.1.3.1 Moving wet mass
Beetles utilize their sense of smell to locate areas that are more humid. Beetles employ their center of gravity and wet patches to mimic this behavior. The beetles look for the center of gravity, according to Eq. (32).
In Eq. (32), \(nb_x^{new}\)\(\to\)new position, \(nb^\ast\)\(\to\)position with higher moisture and \(\overline{nb}\)\(\to\) water gravity position, \(\overline{nb}\) is specified in Eq. (33).
As per HSS-NBO, Eq. (34) is modeled by mingling the concept of SSOA as shown in Eq. (38). The SSOA update is shown in Eq. (35), where, \(y_{i,j}^{newshep}\) implies new position of \(j^{th}\) shepherd in \(i^{th}\) herd, \(stepsize_{i,j}^{shep}\) implies step size of sheep and horse.
On adding Eqs. (34) and (35), (36) is formed.
Consider \(nb_x^{new}\) and \(\,y_{i,j}^{newshep}\) as \(y_i \left( {it + 1} \right)\). Let \(nb_x^{old}\) and \(y_{i,j}^{shep}\) be \(y_i \left( {it} \right)\).
Here, conventionally, the ra value is set as (0, 1). Instead of that, we use ms and Dyadic transformation maps [26].
6.1.4 Population hunting or removal
The beetles returned to the nest after gathering moisture from the air. Incorrect solutions were prone to hunting and removal and in subsequent repetition; a new random solution could be created in the issue space.
Also, the flowchart of the HSS-NBO is depicted in Fig. 2.
7 Link breakage handling
VANETs have a very dynamic environment and the mobility of nodes in VANETs results in a higher probability of link breakage. on its past data transmission.
-
Link reliability It is computed based upon RSSI [46] as shown in Eq. (40), which, RSSI refers to the received signal strength indicator.
$$ RSSI = - 36^\ast \log \left( D \right) - 55 $$(40) -
New distance degree Instead of Euclidean distance [41] computation, a new distance computation is modeled as shown in Eq. (41). In Eq. (41),\(O\) refers to order of norms where the limit between 0 and 1, \(n\) denotes the total count of path, \(M\) and \(L\) denotes the various paths and \(\beta\) = 0.6.
$$D = \frac{{\sum\limits_{{K = 1}}^{n} {\left( {\left| {M_{i} - L_{i} } \right|^{O} } \right)^{{1/O}} } }}{{\min \left[ {\left( {\sum\limits_{{K = 1}}^{n} {\left( {M_{i}^{2} } \right)^{{1/O}} } } \right),\,\left( {\sum\limits_{{K = 1}}^{n} {\left( {L_{i}^{2} } \right)^{{1/O}} } } \right)\,} \right] + \beta }}$$(41) -
New trust evaluation A new trust [39] computation is modeled for handling link breakage as shown in Eq. (42).
$$ T_{i,j} \left( t \right) = \left[ \begin{gathered} \frac{n}{{\sum_{i = 1,j = 1}^n {\left( {\frac{1}{{\left( {1 - \alpha } \right)T_{ij}^X \left( {t - \Delta t} \right)}}} \right)} }} \\ + \frac{n}{{\sum_{i = 1,j = 1}^n {\left( {\frac{1}{{\alpha .T_{ij}^X DT\left( t \right)}}} \right)} }} \hfill \\ + \frac{n}{{\sum_{i = 1,j = 1}^n {\left( {\frac{1}{{\left( {1 - \alpha } \right).T_{ij}^X IDT\left( t \right)}}} \right)} }} \hfill \\ \end{gathered} \right] $$(42)
In Eq. (42), \(T_{ij}^X\) refers to trust value, \(node\left( i \right)\) refers to 1 hop of neighbor, \(T_{ij}^X IDT\) and \(T_{ij}^X DT\) refers to indirect and direct observation, \(T_{ij}^X \left( {t - \Delta t} \right)\) refers to previous experience, \(\Delta t\) refers to trust update period, \(\alpha \left( {0 \le X \le 1} \right)\) refers to parameter used to weight these 2 contributions.
8 Results and discussion
8.1 Simulation setup
The HSS-NBO method for VANET routing was made in NS2. The assessment was made forHSS-NBO over NBO, SSOA, HHO, LOA, and RHSO. The investigation was done on energy, delay, and so on for varied counts of vehicles from 100, 150, 200, 250, and 300. In addition, statistical analysis was done on congestion, delay, distance, energy, and LTP constraints.
8.2 Convergence analysis
The cost graph based on the minimization function is shown in Fig. 3 for 100 rounds. The evaluation of HSS-NBO is performed over NBO, SSOA, HHO, LOA, and RHSO. The constructed VANET routing model employing HSS-NBO has a somewhat higher fitness value in Fig. 3. For all schemes, the cost is higher at early iterations of 0. The HSS-NBO model, however, has a lower cost over NBO, SSOA, HHO, LOA, and RHSO models at the 60th iteration. The cost that the HSS-NBO model achieves is substantially lower in the 100thiteration, at roughly 1.2. As a consequence, the adopted scheme has the lowest cost by HSS-NBO-assisted optimum CHS. Also, routing under the conditions of distance, congestion, LDB measure (suggested evaluation), and LT also produced the lowest cost for the adopted scheme.
8.3 Analysis of delay and energy
The study of delay and residual energy is conducted for HSS-NBO over NBO, SSOA, HHO, LOA, and RHSO. Figure 4. In order to guarantee the timely delivery of data packets, the delay must be minimal. For effective data transmission, there should be a significant level of residual energy following data delivery. In Fig. 4a, the delay obtained using HSS-NBO is less than that obtained using NBO, SSOA, HHO, LOA, and RHSO. Thus, the selected scheme has a high residual energy as a result of the HSS-NBO-assisted optimum CHS. Nevertheless, the implemented system got reduced delay when routing was carried out using the proposed LDB technique.
9 Conclusion
A new VANET routing model with link breakage handling was presented in this work. The first step involved choosing the best CH, for which the HSS-NBO algorithm was developed to choose the CH by taking into account distance, delay, energy, and trust. After choosing the best CHS, the routing was done while taking into account the LT, suggested LDB measure, congestion, and distance. To prevent performance degradation, it was necessary to estimate the link breakage during routing. If the link breaks, the situation should be handled well. This study ensured better link breakage handling by taking link dependability, next hop selection with the computation of a new distance degree, and new trust evaluation of nodes based on their historical data transmission into account. From analysis, the delay increased with increasing vehicles for all techniques, including HSS-NBO and NBO, SSOA, HHO, LOA, and RHSO. The further research could look into the relationship between cluster size and network performance. The proactive intra-cluster communications to build communication links and forward data packets rise as the number of nodes in the clusters increases. In other words, if the network is deployed densely and the clusters are crowded, the routing overhead increases. Network overhead has to be focused in the future.
Data availability
The data is available in https://github.com/ujjwalll/GACMIS.
References
Srivastava, A., Prakash, A., Tripathi, R.: Location based routing protocols in VANET: issues and existing solutions. Veh. Commun. 23, 10023 (2020)
Dafalla, M.E.M., Mokhtar, R.A., Saeed, R.A., Alhumyani, H., Abdel-Khalek, S., Khayyat, M.: An optimized link state routing protocol for real-time application over Vehicular Ad-hoc Network. Alex. Eng. J. 61(6), 4541–4556 (2022)
Alzamzami, O., Mahgoub, I.: Link utility aware geographic routing for urban VANETs using two-hop neighbor information. Ad Hoc Netw. (2020). https://doi.org/10.1016/j.adhoc.2020.102213
Sudheera, K.L.K., Ma, M., Chong, P.H.J.: Link stability based optimized routing framework for software defined vehicular networks. IEEE Trans. Veh. Technol. 68(3), 2934–2945 (2019). https://doi.org/10.1109/TVT.2019.2895274
Alzamzami, O., Mahgoub, I.: Geographic routing enhancement for urban VANETs using link dynamic behavior: a cross layer approach. Veh. Commun. 31, 100354 (2021)
Cárdenas, L.L., Mezher, A.M., Barbecho Bautista, P.A., Astudillo León, J.P., Igartua, M.A.: A Multimetric predictive ANN-based routing protocol for vehicular ad hoc networks. IEEE Access 9, 86037–86053 (2021). https://doi.org/10.1109/ACCESS.2021.3088474
Kandali, K., Bennis, L., Bennis, H.: A new hybrid routing protocol using a modified K-means clustering algorithm and continuous hopfield network for VANET. IEEE Access 9, 47169–47183 (2021). https://doi.org/10.1109/ACCESS.2021.3068074
Singh, P., Raw, R.S., Khan, S.A., Mohammed, M.A., Aly, A.A., Le, D.-N.: W-GeoR: weighted geographical routing for VANET’s health monitoring applications in urban traffic networks. IEEE Access 10, 38850–38869 (2022). https://doi.org/10.1109/ACCESS.2021.3092426
Din, S., Qureshi, K.N., Afsar, M.S., Rodrigues, J.J.P.C., Ahmad, A., Choi, G.S.: Beaconless traffic-aware geographical routing protocol for intelligent transportation system. IEEE Access 8, 187671–187686 (2020). https://doi.org/10.1109/ACCESS.2020.3030982
Al-Kharasani, N.M., Zukarnain, Z.A., Subramaniam, S.K., Hanapi, Z.M.: An adaptive relay selection scheme for enhancing network stability in VANETs. IEEE Access 8, 128757–128765 (2020). https://doi.org/10.1109/ACCESS.2020.2974105
Bello-Salau, H., Onumanyi, A.J., Abu-Mahfouz, A.M., Adejo, A.O., Mu’Azu, M.B.: New discrete cuckoo search optimization algorithms for effective route discovery in IoT-based vehicular ad-hoc networks. IEEE Access 8, 145469–145488 (2020). https://doi.org/10.1109/ACCESS.2020.3014736
Li, G., Li, X., Sun, Q., Boukhatem, L., Wu, J.: An effective MEC sustained charging data transmission algorithm in VANET-based smart grids. IEEE Access 8, 101946–101962 (2020). https://doi.org/10.1109/ACCESS.2020.2998018
Hiremath, S.C., Mallapur, J.D.: Fractional-social ski driver optimization-driven routing protocol for routing electric vehicle under server hosted VANET. Multimed Tools Appl 81, 17437–17456 (2022). https://doi.org/10.1007/s11042-022-12543-6
Sehrawat, P., Chawla, M.: Interpretation and investigations of topology based routing protocols applied in dynamic system of VANET. Wireless Pers. Commun. 128, 2259–2285 (2023). https://doi.org/10.1007/s11277-022-10042-3
Aravindhan, K., Dhas, C.S.G.: Destination-aware context-based routing protocol with hybrid soft computing cluster algorithm for VANET. Soft. Comput. 23, 2499–2507 (2019). https://doi.org/10.1007/s00500-018-03685-7
Al-Ahwal, A., Mahmoud, R.A.: Performance evaluation and discrimination of AODV and AOMDV VANET routing protocols based on RRSE technique. Wireless Pers. Commun. 128, 321–344 (2023). https://doi.org/10.1007/s11277-022-09957-8
Srivastava, A., Prakash, A., Tripathi, R.: QoS aware stochastic relaxation approach in multichannel CR-VANET: a junction-centric geographic routing protocol. J. Ambient Intell. Human Comput. (2022). https://doi.org/10.1007/s12652-022-04391-x
Raja, M.: PRAVN: perspective on road safety adopted routing protocol for hybrid VANET-WSN communication using balanced clustering and optimal neighborhood selection. Soft. Comput. 25, 4053–4072 (2021). https://doi.org/10.1007/s00500-020-05432-3
BrijilalRuban, C., Paramasivan, B.: Energy efficient enhanced OLSR routing protocol using particle swarm optimization with certificate revocation scheme for VANET. Wireless Pers. Commun. 121, 2589–2608 (2021). https://doi.org/10.1007/s11277-021-08838-w
Hussain, N., Maheshwary, P., Shukla, P.K., Singh, A.: Attack resilient and efficient protocol based on greedy perimeter coordinator routing—mobility awareness for preventing the attack in the VANET. Wirel. Pers. Commun. 126, 2841–2868 (2022). https://doi.org/10.1007/s11277-022-09669-z
Lakshmanaprabu, S.K., Shankar, K., Sheeba, R.S., Enas, A., Uthayakumar, J.: An effect of big data technology with ant colony optimization based routing in vehicular ad hoc networks: towards smart cities. J. Clean. Prod. (2019). https://doi.org/10.1016/j.jclepro.2019.01.115
Daas, M.S., Chikhi, S.: Optimizing geographic routing protocols for urban VANETs using stigmergy, social behavior and adaptive C-n-F mechanisms: an optimized CLWPR. Veh. Commun. 14, 97–108 (2018)
Dharani Kumari, N.V., Shylaja, B.S.: AMGRP: AHP-based multimetric geographical routing protocol for urban environment of VANETs. J. King Saud Univ. Comput. Inform. Sci. 31(1), 72–81 (2019)
Wu, J., Fang, M., Li, H., Li, X.: RSU-assisted traffic-aware routing based on reinforcement learning for urban vanets. IEEE Access 8, 5733–5748 (2020). https://doi.org/10.1109/ACCESS.2020.2963850
Elhoseny, M. and Shankar, K.: Energy efficient optimal routing for communication in VANETs via clustering model. Emerging technologies for connected internet of vehicles and intelligent transportation system networks: emerging technologies for connected and smart vehicles, pp. 1–14 (2020)
Hemanth, D.J.: Energy efficient clustering technique for VANET. Adv. Parallel Comput. Technol. Appl. 40, 105 (2021)
Laroiya, N., Lekhi, S.: Energy efficient routing protocols in vanets. Adv. Comput. Sci. Techno. 10(5), 1371–1390 (2017)
Chen, C., Li, H., Li, X., Zhang, J., Wei, H., Wang, H.: A geographic routing protocol based on trunk line in VANETs. Digit. Commun. Netw. 7(4), 479–491 (2021)
Folsoma, R.D., Aravindhan, K., Thirunadana Sikamani, K.: A novel routing and hybrid based clustering scheme in vehicular adhoc networks. Int. J. Intell. Netw. 2, 103–114 (2021)
Manivannan, D., Moni, S.S., Zeadally, S.: Secure authentication and privacy-preserving techniques in Vehicular Ad-hoc NETworks (VANETs). Veh. Commun. (2020). https://doi.org/10.1016/j.vehcom.2020.100247
Sun, G., Zhang, Y., Yu, H., Du, X., Guizani, M.: Intersection fog-based distributed routing for V2V communication in urban vehicular ad hoc networks. IEEE Trans. Intell. Transp. Syst. 21(6), 2409–2426 (2020). https://doi.org/10.1109/TITS.2019.2918255
Hossain, M.A., et al.: Multi-objective harris hawks optimization algorithm based 2-hop routing algorithm for CR-VANET. IEEE Access 9, 58230–58242 (2021). https://doi.org/10.1109/ACCESS.2021.3072922
Hawbani, A., et al.: A novel heuristic data routing for urban vehicular ad hoc networks. IEEE Internet Things J. 8(11), 8976–8989 (2021). https://doi.org/10.1109/JIOT.2021.3055504
Cheng, J., Yuan, G., Zhou, M., Gao, S., Huang, Z., Liu, C.: A connectivity-prediction-based dynamic clustering model for VANET in an urban scene. IEEE Internet Things J. 7(9), 8410–8418 (2020). https://doi.org/10.1109/JIOT.2020.2990935
Ali, A., et al.: Harris Hawks optimization-based clustering algorithm for vehicular ad-hoc networks. IEEE Trans. Intell. Transp. Syst. (2023). https://doi.org/10.1109/TITS.2023.3257484
Mohammadnezhad, M., Ghaffari, A.: Hybrid routing scheme using imperialist competitive algorithm and RBF neural networks for VANETs. Wirel. Netw. 25(5), 2831–2849 (2019)
Bagherlou, H., Ghaffari, A.: A routing protocol for vehicular ad hoc networks using simulated annealing algorithm and neural networks. J. Supercomput. 74, 2528–2552 (2018)
Priyadharshini, M., Ananth, C.: A secure hash message authentication code to avoid certificate revocation list checking in vehicular adhoc networks. Int. J. Appl. Eng. Res. 10, 1250–1254 (2015). https://doi.org/10.2139/ssrn.3024722
Rouissi, N., Gharsellaoui, H., Bouamama, S.: Improvement of watermarking-LEACH algorithm based on trust for wireless sensor networks. Proc. Comput. Sci. (2019). https://doi.org/10.1016/j.procs.2019.09.239
Alzamzami, O., Mahgoub, I.: Geographic routing enhancement for urban VANETs using link dynamic behaviour: a cross layer approach. Veh. Commun. (2021). https://doi.org/10.1016/j.vehcom.2021.100354
Chahardoli, M., Eraghi, N.O., Nazari, S.: Namib beetle optimization algorithm: a new meta-heuristic method for feature selection and dimension reduction. Concurr. Comput. Pract. Exp. (2022). https://doi.org/10.1002/cpe.6524
Kaveh, A., Zaerreza, A.: Shuffled shepherd optimization method: a new Meta-heuristic algorithm. Eng. Comput. 37(7), 2357–2389 (2020)
Ivanic, M. and Mezei, I.: Distance Estimation Based on RSSI Improvements of Orientation Aware Nodes. In: 2018 Zooming Innovation in Consumer Technologies Conference (ZINC) (2018)
https://www.cuemath.com/probability-a-intersection-b-formula/
Suryadi, M.T., Satria, Y., Melvina, V., Prawadika, L.N., Sholihat, I.M.: A new chaotic map development through the comparision of the MS Map and the Dyadic Transformation Map. J. Phys: Conf. Series (2020). https://doi.org/10.1088/1742-6596/1490/1/012024
Funding
This research did not receive any specific funding.
Author information
Authors and Affiliations
Contributions
RKM conceived the presented idea and designed the analysis. Also, he carried out the experiment and wrote the manuscript with support from SSJ. All authors discussed the results and contributed to the final manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Mahesh, R.K., Jawaligi, S.S. VANET cluster-based routing protocol with link breakage handling: introduction to hybrid optimization algorithm. SIViP 18, 7527–7536 (2024). https://doi.org/10.1007/s11760-024-03297-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11760-024-03297-9