Abstract
A hybrid of supervised (artificial neural network), unsupervised (clustering) machine learning, and soft computing (interval type 2 fuzzy logic system)-based load balancing algorithm, i.e., clustering-based multiple objective dynamic load balancing technique (CMODLB), is introduced to balance the cloud load in the present work. Initially, our previously introduced artificial neural network-based dynamic load balancing (ANN-LB) technique is implemented to cluster the virtual machines (VMs) into underloaded and overloaded VMs using Bayesian optimization-based enhanced K-means (BOEK-means) algorithm. In the second stage, the user tasks are scheduled for underloading VMs to improve load balance and resource utilization. Scheduling of tasks is supported by multi-objective-based technique of order preference by similarity to ideal solution with particle swarm optimization (TOPSIS-PSO) algorithm using different cloud criteria. To realize load balancing among PMs, the VM manager makes decisions for VM migration. VM migration decision is done based on the suitable conditions, if a PM is overloaded, and if another PM is minimum loaded. The former condition balances load, while the latter condition minimizes energy consumption in PMs. VM migration is achieved through interval type 2 fuzzy logic system (IT2FS) whose decisions are based on multiple significant parameters. Experimental results show that the CMODLB method takes 31.067% and 71.6% less completion time than TaPRA and BSO, respectively. It has maintained 65.54% and 68.26% less MakeSpan than MaxMin and R.R algorithms, respectively. The proposed method has achieved around 75% of resource utilization, which is highest compared to DHCI and CESCC. The use of novel and innovative hybridization of machine learning, multi-objective, and soft computing methods in the proposed algorithm offers optimum scheduling and migration processes to balance PMs and VMs.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
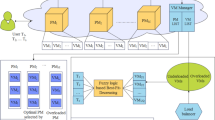
The ubiquitous nature of cloud computing has attracted tremendous users in recent years [1]. Cloud computing has the ability to handle an expanded volume of tasks by providing an adaptive online environment. The ability of the cloud is to support numerous users and tasks that provide many advantages. It introduces a new concern, known as load balancing [2]. The involvement of numerous users requires an efficient load balancing mechanism to maintain an unmanaged cloud environment system. Numerous load balancing methods are studied and examined in the previous work [3]. Here, the authors provided a clear view of the performances of different cloud load balancing techniques with their pros and cons. Figure 1a shows a balanced cloud environment in which user tasks are distributed to all virtual machines (VMs) in each physical machine (PM) to maintain load balancing. Similarly, Fig. 1b illustrates an unbalanced cloud in which user tasks are assigned to a particular PM to make it overloaded. The efficient utilization of resources makes a significant and balanced cloud.
Several researchers have shown interest in other clouds-related research such as task scheduling and VM scheduling process to achieve efficient load balancing, high utilization of resources, energy efficiency, improvement in quality of service (QoS), etc. [4]. In task scheduling, many optimization algorithms such as particle swarm optimization (PSO), fuzzy logic (FL), and genetic algorithm (GA) are used to achieve optimized solutions. Author [4] has analyzed various task and resource scheduling processes in different layers. Adaptive multi-objective task scheduling (AMTS) strategy was introduced for efficient resource utilization and energy efficiency [5]. The PSO algorithm is adapted for the task scheduling process. Temporal task scheduling algorithm (TTSA) deals with cost minimization problem in a hybrid cloud [6], where the solution for cost minimization problem is derived from hybrid simulated annealing PSO algorithm. VM-based task scheduling proves that load balancing and resource utilization can be improved jointly by a proper scheduling process [7]. To achieve this, greedy PSO (GPSO) algorithm in which particle initialization is better than traditional PSO is employed. In order to reduce the large consumption of energy and improve load balancing, resource pre-allocation and task scheduling were employed [8] in the process. Here, scheduling of tasks and allocation of resources are performed by the matching probabilistic and simulated annealing (SA) algorithms (CESCC).
MakeSpan is minimized by performing suitable load adjustment in a multi-data center cloud [9], in which a static load balancing strategy, namely the Multi-Rumen Anti-Grazing algorithm, is presented for load adjustment. Autonomous agent-based load balancing (A2LB) algorithm balances load among VMs in the cloud with the help of three agents as load, channel, and migration [10]. These three agents are incorporated in each data center (DC) to migrate VM from overloaded DC to underloaded DC. Another agent-based load balancing scheme is included with front-end agent (FA), server manager agent (SMA), and virtual machine agent (VMA) [11]. FA is responsible for routing VM requests, while VMA and SMA are responsible for load monitoring in VM and PM, respectively. Load balancing in a dynamic multi-service scenario in centralized hierarchical cloud-based multimedia system is considered as an integer linear programming problem [12]. The problem is solved by an efficient GA with an immigrant scheme. The load balancer is responsible for task migration, whereas load balancing is achieved using efficient task scheduling in DC [13]. Here, the tasks are scheduled by an improved weighted round robin (WRR) algorithm, which considers the current load on VM for scheduling. Dynamic Hadoop cluster on IaaS (DHCI) architecture has involved modules of VM migration, VM management, scheduling, and monitoring to achieve well-behaved load balancing for cloud system environment [14]. Parallel computing entropy is utilized for dynamic VM migration-based data locality scheme. Continuous VM migration is supported by named data networking (NDN) in order to balance load among DCs in the cloud [15]. In NDN, VMs and services are provided with a unique name to provide uninterrupted services during VM migration.
Though the above-discussed works improve load balancing, it is still a primary concern due to the increasing demand of cloud-based environment in every advanced computing field. Thus, it is necessary and demanding to design novel algorithms for load balancing in the cloud system environment. The major strength of the proposed method is that it includes the machine learning-based supervised and unsupervised technique to train the cloud systems to identify the loads on VMs and clusters them into underloaded and overloaded VMs. Once cluster formation is achieved, it would be easier for the cloud system to assign cloud tasks to underloaded VMs. Task assignments are performed using a mathematical multi-criteria-based TOPSIS-PSO method which will reduce the system complexity by introducing relative closeness for cloud performance metrics, execution time, transmission time, and CPU utilization to the PSO method. Further, a fuzzy-based technique is incorporated to identify the destination PM for the migration of overloaded VMs to achieve PM-level load balancing. The use of these soft computing based-techniques gives more realistic results than the previously existing work and enhances the proposed method strength. However, the proposed method does not focus on storage-intensive tasks and storage IOPS/transfer-based VM capacity which makes the work less advanced in a real-time-based cloud environment.
The significant contributions of this paper in cloud computing are summarized as follows:
-
Efficient CMODLB load balancing method is the hybridization of artificial neural network-based load balancing (ANN-LB), technique of order preference by similarity to ideal solution with particle swarm optimization (TOPSIS-PSO), and interval type 2 fuzzy logic system (IT2FLS) methods in order to balance load among VMs and PMs in the cloud environment. The objective of CMODLB is to improve multiple objectives such as MakeSpan, resource utilization, completion time, transmission time, energy consumption, and load fairness.
-
The proposed CMODLB is initiated by Stage 1 where the ANN-LB technique is applied using Bayesian optimization-based K-means (BOK-means) with ANN algorithm to create clusters of VMs into underloaded VMs and overloaded VMs. Runtime tasks are scheduled to underloaded VM to maintain the load balance.
-
In Stage 2, runtime tasks are scheduled by applying the TOPSIS-PSO algorithm, which supports three objectives for scheduling. The multiple objectives taken into account are execution time, transmission time, and CPU utilization.
-
In Stage 3, the VM manager monitors the load on PMs and migrates optimal VM from the overloaded PM. VM migration decision is also made if a PM has a minimum load in order to minimize energy consumption.
-
In the VM migration process, optimal destination PM is selected by decision making interval type 2 fuzzy logic system (IT2FL), which achieves efficiency in uncertainties. Fuzzy logic assures that the destination PM is underloaded based on significant parameters.
The rest of this paper is prepared as follows: Sect. 2 debates previous related literature on cloud environment-based load balancing. In Sect. 3, existing problems in the previous work are highlighted. Section 4 explains the proposed CMODLB load balancing algorithm working structure, while Sect. 5 examines the experimental evaluation of implemented work. Finally, Sect. 6 gives a glimpse of the contribution of the work and concludes with future scope.
2 Related work
The adaptive cost-based task scheduling (ACTS) method was introduced to minimize the completion time of a task to maximize its QoS [16]. Completion time on each VM has been taken as the cost of the data access path, and tasks were given a priority based on a deadline. The minimum cost path was allocated for a low-priority task, which had a minimum deadline. Here, VMs are selected based on completion time only, which has introduced unbalanced load and resource underutilization. Hence, this approach degrades the performance of the cloud when the selection of VMs is made only by completion time.
A two-level task scheduling technique was presented in a multimedia cloud [17]. In this mechanism, first-level scheduling was performed between users to DCs and second-level scheduling was performed among DCs to servers. Both scheduling levels followed the M/M/1 queuing system. However, M/M/1queue supports only a single server and also limits waiting space for tasks. This limitation makes it less efficient.
Li et al. attempted to reduce the heavy consumption of energy in the cloud by minimizing job completion time (JCT) [18]. For this purpose, task placement and resource allocation (TaPRA) and TaPRA-fast algorithm were developed. However, these algorithms are able to solve only a single-task placement problem and not suitable to handle multiple tasks.
Energy-aware dynamic task scheduling (EDTS) algorithm was involved with two algorithms, namely data flow graph critical path (DFGCP) and critical path assignment (CPA) [19]. Here, DFGCP was used to obtain a near-optimal solution, while the CPA algorithm was employed to find an optimal solution. This method fails to provide efficient resource utilization with lower energy consumption.
Load balancing was performed through VM scheduling in the cloud [20]. VM scheduling was carried out by combining two optimization algorithms, resulting in a new meta-heuristic algorithm named ant colony optimization with particle swarm (ACOPS). The workload for new requests was predicted based on historical information in ACOPS. A pre-rejection module was incorporated to minimize scheduling time. Maintaining historical information increases space complexity, and due to the pre-rejection module, user tasks do not experience better QoS.
Hybrid particle swarm optimization (HPSO) was applied for load balancing in centralized cloud-based multimedia storage [21]. In HPSO, each particle's weight was computed by multi-kernel support vector machine (MKL-SVM) and fuzzy simple additive weight (FSAW) methods. The involvement of three simultaneous and dynamic algorithms increases both load balancing time and computational complexity.
Honey bee behavior-inspired load balancing (HBB-LB) algorithm was presented to balance load across VMs and minimize the tasks' waiting time [22]. Load balancing was performed by the task transfer process in which tasks from overloaded VMs are migrated to underloaded VMs. Here, load balancing during initial task assignment is not considered and tasks are assigned to random VM, which increases MakeSpan and resource underutilization.
PSO algorithm and bacterial foraging optimization (BFO) algorithm were combined and introduced bacterial swarm optimization (BSO) to perform load balancing in DCs [24]. In a hybrid bacterial algorithm, the global solution over search space was determined by the PSO algorithm, and local search was performed by the BFO algorithm. This algorithm focused on only allocating optimal VM for incoming tasks; however, load on PMs was not considered.
Dragonfly optimization algorithm-based load balancing method was introduced to balance load among VMs [25]. Initially, each VM's load and capacity were calculated, and tasks were assigned to VMs randomly. If the load on VM was greater than the threshold, then optimal underloaded VM for each task was selected. This method increases MakeSpan for user tasks and suffers from high processing time.
Load balancing via optimal task deployment strategy was realized in [26]. Bayes theorem was introduced to find probabilities of physical host for optimal task deployment. Based on the probabilities, physical hosts were clustered to detect optimal PM for user task. In this way, the load across PMs was balanced. However, this method is not suitable to balance load across VMs.
VM migration was performed by using a distributed network of brokers [27]. Migration decision was made based on RAM and CPU state of VMs, and migration was performed by deriving policies by hypervisor. This method increases complexity and does not perform well in terms of resource utilization.
Firefly optimization–energy-aware virtual machine migration (FFO-EVMM) algorithm was presented to attain both load balancing and energy efficiency [28]. FFO-EVMM algorithm also utilizes the concept of artificial bee colony (ABC) algorithm for load monitoring on VMs. If a migration decision was made, then optimal VM for migration and optimal destination for migration were determined by FFO algorithm. This method increases migration time because time constraint is not considered in the migration process.
Energy-aware utility prediction model was introduced for VM consolidation in a cloud [29]. Here, VM consolidation model was applied periodically to optimize VM placement. VM migration was enabled if any resource of VM exceeds total capacity. Consideration of a single parameter for migration increases the number of VM migrations, which results in higher energy consumption.
Thus, the previous works seem to be insufficient to achieve efficient load balancing. The majority of the works focus on either task scheduling or load balancing in a cloud. However, introducing an effective task scheduling and load balancing (among VMs and PMs) method is a key concern in cloud computing. This work introduces an algorithm with the aim to increase load balancing performance by using effective clustering, task scheduling, and VM migration process.
3 Problem definition
An enhanced Min-Min algorithm, which involves two phases, was presented for load balancing in a cloud [30]. In the first phase, tasks were assigned to VMs based on execution time, and in the second phase, tasks were rescheduled to utilize unused resources. Since tasks are assigned to VMs, which provide minimum execution time. In the first phase, rescheduling of tasks increases execution time. Involvement of two scheduling processes increases overall MakeSpan, which degrades its performance.
In multi-objective tasks scheduling algorithm, tasks were given priority based on QoS, and VMs were sorted based on MIPS values [31]. Tasks and VMs were assigned as per the task and VM list. In this process, resource utilization is poor since VMs are sorted based on MIPS values. The VM list which is prepared initially is processed with all task set. After assigning a task to VM, the parameters of VM may change. This change is not considered in the presented method. Hence, the scheduling process is not much efficient.
Two-stage strategy for task scheduling includes Bayes classifier for classification of VMs in the first stage and scheduling algorithm in the second stage [32]. In this method, task queue, waiting queue, and ready queue were maintained, and tasks were put in a waiting queue until a suitable VM became idle. Maintenance of multiple queues and databases increases space complexity. This method allows waiting queue tasks to move into the ready queue only if the ready queue is free. Hence, waiting time for tasks in the waiting queue is increased significantly.
The self-adaptive learning PSO (SLPSO) algorithm was included with four update strategies to update the velocity of particles [33]. The best update strategy was detected in each iteration based on execution probability and used in the SLPSO algorithm. In SLPSO, frequent selection of update strategy leads to higher time consumption and higher complexity.
Load balancing mutation using PSO (LBMPSO) algorithm was introduced to schedule tasks and load balancing in which objective function was formulated based on expected execution time, transmission time, and round trip time [34]. All three times were computed for each task on each VM to find the optimal VM. If the number of VMs and tasks are large, then this method presents a large MakeSpan and high complexity. Hence, it motivates to introduce an effective idea to balance cloud loads without reducing execution time and resource utilization.
An efficient novel task scheduling algorithm called technique of order preference by similarity to ideal solution with particle swarm optimization (TOPSIS-PSO) algorithm has been introduced [35]. TOPSIS-PSO solves task scheduling issues using multiple objective-based technique i.e., TOPSIS. The TOPSIS algorithm generates fitness value for PSO technique using three multi-criteria, viz. execution time, transmission time, and cost. The algorithm has been found suitable for task scheduling approaches with less computational complexity but lacks load balancing issues. Hence, to get an efficient outcome, we performed a multi objective-based TOPSIS-PSO algorithm (using four objectives) for scheduling of the tasks in our dynamic load balancing approach.
A new hybrid task scheduling technique named PSO with gravitational emulation local search (PSO-GELS) has been introduced for grid computing [36]. The algorithm PSO-GELS perfectly examines its role with respect to MakeSpan. We compared it with our proposed CMODLB load balancing algorithm with respect to the obtained MakeSpan values for the same configurations set because of its dynamic nature. Previously, authors [36] have compared their work with various other existing algorithms such as SA, GA, GA-SA, GA-GELS (genetic algorithm–gravitational emulation local search), PSO, and PSO-SA.
Authors of [49] have introduced a crow–penguin optimizer which is the fusion of the crow search optimization algorithm (CSA) and the penguin search optimization algorithm (PeSOA) for the execution of multi-objective task scheduling strategy (CPO-MTS). The introduced CPO-MTS algorithm performed the execution of tasks in a minimal time by a converging problem to a global optimal solution rather than the local optima. Authors have compared their work with various other existing algorithms such as CPO, CSA, PSO, ABC, GA, ACO, and PeSOA. The introduced work is suitable for load balancing in a static cloud environment which makes the algorithm less effective.
A novel task scheduling technique named threshold-based multi-objective memetic optimized round robin scheduling (T-MMORRS) is presented to offer high-quality services and maintains bursty user demands [50]. Initially, some user requests are transferred to the server where the proposed algorithm performed a quick scan for workload conditions through a burst detector. Furthermore, if the obtained result by burst detector has a normal load, then T-MMORRS chooses threshold multi-objective memetic optimization (TMMO) else T-MMORRS will choose weighted multi-objective memetic optimized round robin scheduling (WMMORRS) for burstiness load. T-MMORRS technique is compared with the multi-objective genetic algorithm (MGA) and dynamic power-saving resource allocation (DPRA). T-MMORRS achieves higher efficiency and lower time consumption. However, the algorithm offers high complexity to the cloud system.
An efficient load balancing system using an adaptive dragonfly algorithm was proposed by the authors of [51]. Completion time, processing costs, and load parameters are used to develop the multi-objective function. Authors have compared their work with dragonfly optimization algorithm (DA) and firefly algorithm (FA) and claim that the proposed method has better performance than the respective algorithms. The limitation of this work was that the author has not focused on load fairness and resource utilization cloud parameters which makes the algorithm less efficient. For more detailed survey comparison of various existing load balancing algorithms have been discussed in Table 1.
4 Proposed work
4.1 System overview
The proposed work focuses on load balancing among PMs and VMs in a cloud environment through hybrid supervised (with target attribute, i.e., ANN) and unsupervised (without target attribute, i.e., BOK-means clustering) machine learning techniques for efficient load calculation and VM clustering process. The proposed cloud environment consists of M numbers of PMs as:\(P = \left\{ {PM_{1} ,PM_{2} , \ldots ,PM_{M} } \right\}\). In each PM, L numbers of VMs are included as: \(VM = \left\{ {VM_{1} ,VM_{2} , \ldots .,VM_{L} } \right\}.\) The cloud environment is involved with S number of users tasks represented as \(T = \left\{ {T_{1} ,T_{2} , \ldots ,T_{S} } \right\}\). To balance load among M PMs and L VMs, two entities, VM manager (\(VM_{Man}\)) and cloud balancer (CBal), are involved.
4.1.1 4.1.1 Contribution methods
The proposed cluster-based multi-objective dynamic load balancing (CMODLB) method is introduced for an efficient load balancing without the loss of resource utilization. Figure 2 depicts the overall functioning of CMODLB method. To achieve the goal, machine learning- and soft computing-based techniques have been used for each stage to learn the behavior of the cloud to develop the effectiveness and better performance of the cloud environment. The CMODLB method comprises the following three stages:
4.1.1.1 Stage I: Grouping of VMs using BOEK-means with ANN
In this stage, the load of cloud VMs under PMs is calculated using Bayesian optimization-based K-means with artificial neural network as shown in Fig. 3. The reason behind using ANN is to support multiple VMs simultaneously to get the current load with the objective to reduce the total clustering method. In our previous work [23], we investigated that the K-means clustering algorithm offers a major shortcoming in the initialization of the centroid which makes it more expensive to evaluate the functions. To overcome this problem, Bayesian optimization (BO) algorithm which builds a probabilistic model for the problem and finds posterior predictive distribution for that problem [37, 38] is introduced with the K-means algorithm.
4.1.1.2 Stage II: Task scheduling using TOPSIS-PSO method
For efficient task scheduling, the technique of order preference by similarity to ideal solution with particle swarm optimization (TOPSIS-PSO) algorithm [35] is performed with different cloud objectives. A VM is allocated to a task which minimizes execution time and transmission time and maximizes CPU utilization. Here, PSO algorithm is combined with a multi-objective-based TOPSIS algorithm in order to remove the PSO’s weak local search ability and to find optimal fitness function by considering three criteria. The relative closeness is formulated by the TOPSIS algorithm which is the objective function for PSO. All underutilized VMs are taken in PSO algorithm, and fitness value is calculated using multi-objective TOPSIS algorithm. The use of multi-objective TOPSIS method introduces the most efficient task scheduling outcome. PSO algorithm is set with tasks on underloaded VMs (\(T_{U} = \left\{ {T_{U1} ,T_{U2} , \ldots ,T_{UQ} } \right\}\)), and at each iteration, the fitness value for a particle is calculated. The fitness value gives particle local best (LBest) and global bbest (GBest) values, and both values are updated.
4.1.1.3 Stage III: VM migration using Iterative Type 2 Fuzzy Logic (IT2FL) method
For PM-level load balance, it is necessary to maintain destination PM with a balanced load even after VM migration. Available resources are also important in destination PM selection which provides better performance for user tasks. Therefore, a selection of optimal destination PM should be performed in an efficient manner. To realize this fact, interval type 2 fuzzy logic (IT2FL) is incorporated in VM migration process as shown in Fig. 4 that illustrates the flow diagram of IT2F logic for PM selection. Here, rule base follows rules to obtain fuzzy output. PM with high output is taken as PMdes (destination PM). Lotfi A. Zadehi introduced IT2FL set to extend the functional properties of Type1 and general fuzzy logic systems. IT2 FL gives the possibility to provide more parameters to describe membership functions (MF) and handles more uncertainty [40]. It is the first-order uncertainty fuzzy set model.
The overall process of the CMODLB method includes a grouping of underloaded and overloaded VMs using supervised ANN-LB technique, scheduling of tasks by TOPSIS-PSO multi-criteria-based technique, and VM migration using iterative type 2 fuzzy logic (IT2FL) method is depicted in Fig. 2 where as Table 2 explains description of used notations in the manuscript. Each significant stage has been discussed in detail in the following sections.
4.2 BOEK-means with ANN-based clustering (Stage I)
Knowledge of the currently available load on VMs will improve task scheduling, thus reducing the unbalanced DCs and decreasing resource underutilization. To achieve this, we have introduced \(VM_{Man}\) that will perform clustering of VMs based on their current available load in each PM; \(VM_{Man}\) maintains VM list with their load information and PM list with their information. VMs are clustered as per their current load given as follows:
-
Underloaded VMs: Set of VMs having load lower than the target value, and it is denoted as VMU.
-
Overloaded VMs: Set of VMs having load greater than the target value, and it is denoted as VMO.
Group formation of VMs is realized by BOK-means with ANN algorithm. In BOK-means with ANN algorithm, all VMs are fed into ANN to calculate their current load. The load on each VM is considered as weight values and denoted as \(W = \left\{ {W_{V1} ,W_{V2} , \ldots ,W_{VL} } \right\}.\) Based on the weight value of each VM, BOK-means algorithm forms clusters such as underloaded VMs with \(VM_{U} = \left\{ {VM_{U1} ,VM_{U2} ,..,VM_{UQ} } \right\}\) and overloaded VMs with \(VM_{O} = \left\{ {VM_{O1} ,VM_{O2} ,..,VM_{OR} } \right\}\). Weight value in terms of the load is calculated using Eq. (1) as follows:
where WL and LL denote the weight and load on Lth VM, while \(E_{j}\) s represents the execution time of Sth assigned tasks on VML. C(VL) provides the capacity of VML and computed as:
The capacity of each Lth VM (\(C\left( {V_{L} } \right)\)) is calculated by considering the number of processors (NP), the number of million instructions per second (MIPS), and bandwidth (BW) of Lth VM. Figure 3 illustrates BOK-means with ANN algorithm-based clustering process. The optimal centroid maximizes the performance of the K-means clustering algorithm. For a given function f(c) that represents optimization problem and c represents the attribute of user task belonging to the compact set of centroids (\(c \in C\)), the probability of clustering improvement is expressed as:
where\(\gamma \left( c \right)\) is obtained from
Here, \({\mu }_{c}\) is the predictive mean function and \(\sigma (c)\) is a predictive marginal function. Improvement in an optimal solution is obtained from Eq. (3). After the initialization of the optimal centroid, all VMs are initialized with their weight values. Then BOK-means method was performed to find optimal clusters.

Algorithm 1
depicts the complete process of clustering of VMs using the BOK-means method ANN algorithm. The obtained cluster includes g1 and g2 where
Here,\(g_{1}\) includes a cluster of underloaded VMs and \(g_{2}\) includes a cluster of overloaded VMs. In the cloud, each VM is able to execute different tasks having dissimilar execution times. This process of execution of different tasks in different VMs may dynamically vary the current load of VMs. Because of this dynamic execution nature, it may happen that a VM in \(g_{1}\) may achieve heavy load or a VM in \(g_{2}\) may lead to achieve less load. Such factor motivates to introduce a balancer that will maintain each cluster group without losing their uniqueness. The key role of the balancer is to make a decision on load balancing by assigning its each VM to a suitable cluster location. For example, if any VM in \(g_{1}\) has changed its current load, then it is the responsibility of the balancer to remove that VM from \(g_{1}\) and put it into a suitable cluster location in \(g_{2}\). Hence, each cluster maintains optimal VMs. To understand its concept more deeply, let us consider four VMs in the cloud system having VM_ID from 0 to 3. Each VM initially assigned some tasks to their specific IDs (0 to 3). Using ANN, the obtained VM loads are \(VML_{1} = 0.19\), \(VML_{2} = 0.19,\) and \(VML_{3} = 0.20\). Further, assume that using ANN the obtained values are clustered into the underloaded and overloaded clusters using the BOK-means method. To classify \(VM_{U}\) and \(VM_{O}\), a threshold is set from which \(g_{1} = \left\{ {VML_{2} {\text{ and}} VML_{4} } \right\}\) is obtained as an underloaded and \(g_{2} = \left\{ {VML_{1} {\text {and} } VML_{3} } \right\}\) is obtained as an overloaded cluster. The threshold is calculated using Eq. (6) and Eq. (7), respectively. Obtained VM loads are depicted in Table 3.
\({\text{if}}\;\left[ {g_{1} < g_{2} } \right]\;{\text{then}}\;g_{1} \;{\text{is}}\;{\text{Underloaded}}.\) \({\text{else}}\;g_{1} \;{\text{is}}\;{\text{overloaded}}.\) if \(\left[ {g_{1} = g_{2} } \right]\) then LBal will assign tasks to VM having minimum load among VMs of \(g_{1}\) and \(g_{2}\) both. The obtained underloaded VMs are further being used for task assignment execution using a multi-objective-based TOPSIS-PSO scheduling algorithm.
4.3 Multi-objective-based TOPSIS-PSO scheduling algorithm (Stage II)
The next step is task scheduling process in which each task is allocated to the optimum underloaded VM of cluster \(g_{1}\). The task scheduling process aims to balance the load between VMs and to make the best use of resource utilization. In this process, to preserve load among VMs, the set of VMU determined by BOK-means with ANN algorithm is taken and other VMs have been excluded. Incoming user tasks \(T = \left\{ {T_{1} ,T_{2} , \ldots ,T_{S} } \right\}\) are assigned to optimal underloaded VM in \(VM_{U} = \left\{ {VM_{U1} ,VM_{U2} , \ldots ,VM_{UQ} } \right\}\). Based on multiple parameters such as the execution time of task, the transmission time of the task, and CPU utilization, an optimal VM is selected.
The execution time (ET) of Sth task on Lth VM is given by
Execution time is computed by obtaining the ratio of the length of the Sth task \(length_{S}\) and MIPS of Lth VM. Optimal VM is nominated for Sth task that reduces ET.
The transmission time (TT) for a task TS on VM VL is computed as
The transmission time of the Sth task on a specific VM is obtained by taking the ratio of task size \(Size_{S}\) and bandwidth of VM \(BW_{L}\). Similarly, CPU utilization of VM is calculated by
The TOPSIS algorithm is initiated by assigning some weight values for every three criteria which are signified by \(\left[ {E_{T} ,T_{T} ,U_{CPU} } \right] = \left[ {H_{E} ,H_{trans} ,H_{U} } \right]\) and includes the following steps:
Step1 Construction of Decision Matrix (DM). The decision matrix is constructed using multiple alternatives and multiple criteria.
Here, TU1, TU2, TU3, TU4, and TU5 are called alternatives (tasks) and ET, TT, and UCPU are known as multiple criteria. ET1i, TT1i, and UCPU1i represent the execution time, transmission time, and CPU utilization of Ti on VMUQ, respectively. The obtained DM values for five tasks TU1, TU2, TU3, TU4, and TU5 on underloaded VMU (vmID = 0) with ET, TT, and UCPU are expressed in Table 4.
Step2 Construction of Standard DM. In this step, each criterion is compared with each column alternative to transform into non-dimensional attributes. In this standardization, each row of DM is divided by the root of the sum of the square of respective row as follows:
where each element in DMrepresents in ath alternative and cth criteria for \({DM}_{ac}\).
Step3 Construction of Weighted standard DM. To get weighted standard DM, each attribute weight value is multiplied by each element in standard DM. The weight values for execution time, transmission time, and CPU utilization criteria are evaluated as
where \(H_{E} , H_{trans} {\text{and }}H_{U}\) are the weight values for \(E_{T} , T_{T} {\text{and}} U_{CPU},\) respectively, and \(E_{TQ} , T_{TQ} {\text{and}} U_{CPUQ}\) on Qth VM. The weight values should be a positive integer.
Step4 Evaluation of ideal and negative solution. In this step, an extremely positive ideal solution that maximizes benefit criteria and a negative ideal solution that minimizes benefit criteria are determined. ET and TT are considered as performance criteria which are to be minimized, and UCPU is taken as benefit criteria which are to be maximized. Positive (A+) and negative (A−) ideal solutions are given by
where \({V}_{Ua}^{+}\) and \({V}_{Ua}^{-}\) represent the positive and negative solutions for ath alternative, respectively.
Step5 Determination of separation measures. In this step, each alternative is separated from \({A}^{+}\) and \({A}^{-}\) which is measured as
Equations (17) and (18) calculate the distance between each alternative positive and negative solution, respectively. Here, the number of criteria is 3.
Step6 Calculation of relative closeness. The value of relative closeness (RC) is achieved from the positive and negative separation measures \((f_{Q}^{ + }\) and \(f_{Q}^{ - }\)) of tasks on Qth VM with respect to positive ideal solution A+ and is defined as
The role of RC is to perform as a fitness value for the PSO algorithm. The ability of particle swarm reaction introduces solutions to optimization problems [36]. In PSO, a swarm comprises individual particles that fly on search space, and these particles handle solutions to the problems. By the experience of a particle and its neighboring particles, the position may be influenced by the best local position (LBest). However, if the neighborhood of a particle has the best position in the swarm, it would be the best global position (GBest). Once particle has been initialized, in each repetition particle is placed near to GBest and velocity using Eq. (20) and FV is calculated. The velocity of a particle is expressed as
where \({}_{Q}^{i + 1} Vel\) signifies existing velocity and \({}_{Q}^{i} Vel\) denotes the earlier velocity of \(Q\). \({}_{Q}^{i + 1} Par {\text{and}} {}_{Q}^{i} Par\) are the current and earlier position of \(Q\). Two learning factors \(L^{1} , L^{2}\) and the random numbers \(ran^{1} ,\) \(ran^{2}\) are involved in velocity computation with respect to the values depicted in Table 4. Each user task performs this process and is then scheduled to an optimal underloaded VM. The obtained relative closeness for each task T from TOPSIS is initialized to compute the fitness value for each particle. Initially, for each task, TOPSIS calculates a decision matrix for the given multiple alternatives (tasks) and three criteria (execution time, transmission time, and CPU utilization) using Eqs. (8), (9), and (10), respectively. The algorithm recalculates the standard decision matrix by a root of the sum of squares of respective rows using Eq. (11). Weighted standard DM is calculated using Eq. (12), Eq. (13), and Eq. (14) for \(E_{T} ,Trans_{T} ,{\text{ and}} U_{CPU}\), respectively. Next, positive and negative ideal solutions are performed to check maximum and minimum benefit from the criteria using Eq. (15) and Eq. (16). Separation of alternatives from \(f_{Q}^{ + }\) and \(f_{Q}^{ - }\) using Eq. (17) and Eq. (18) is performed. Relative closeness (fitness value) is obtained for each task with respect to each alternative as a particle using Eq. (19). The obtained FV value is further compared to the current local best particle value, which is calculated in the initial steps of PSO. If the current FV is larger than the current local best particle, then update the value of \({\text{LBest}}\) with the current FV value updated, else the value of \({\text{LBest}}\) will remain the same. Once the algorithm gets the value of all \({\text{LBest}}\), the largest \({\text{LBest}}\) is found by comparing them with each other. The largest \({\text{LBest}}\) will be considered as the global best particle \({\text{GBest}}\). Similarly, if the current \({\text{GBest}}\) is larger than the previous \({\text{GBest}}\), then the value of \({\text{GBest}}\) is updated with the current \({\text{GBest}}\) value; else, the value of \({\text{LBest}}\) will remain. The process is iteratively performed until the maximum number of iterations is reached. During each iteration, particle velocity and position are updated using Eq. (20) and Eq. (21). The final particle solution having the largest \({\text{GBest}}\) will be assigned to the most optimal underloaded VM \(V_{Uoptimal}\) for mapping.
By assigning each task to optimal VM, MakeSpan, completion time, and transmission time of tasks are reduced significantly. TOPSIS-PSO method assigns user tasks only to VMU. Therefore, TOPSIS-PSO-based task scheduling process with ANN-LB technique introduces load balancing and efficient tasks scheduling among VMS. Further, it reduces MakeSpan, completion time, and transmission time of tasks without reducing resource utilization. The overall procedure of the TOPSIS-PSO algorithm is shown in Algorithm 2. Finally, each task in the user task set is scheduled to optimal VM in the underloaded VM set, which can be expressed as
Tasks which are assigned to \(VM_{U2} {\text{and}}\user2{ }VM_{U4}\) are denoted in Table 5 where tasks \({\varvec{T}}_{0}\), \({\varvec{T}}_{3},\) and \({\varvec{T}}_{4}\) are mapped to \({\varvec{VM}}_{{{\varvec{U}}2}}\) and Tasks \({\varvec{T}}_{1}\) and \({\varvec{T}}_{2}\) are mapped to \({\varvec{VM}}_{{{\varvec{U}}4}}\). The given task assignment matrix table represents task mapping according to the increased number of tasks and VMs. The calculation is executed for both less and a considerable number of tasks, and related effects are observed for both cases. In this observation, a small number of VMs and runtime tasks are used.
The assignment of the best VM for user task results in better performance and better resource utilization. Therefore, MakeSpan, which is the overall completion time for all assigned tasks for a particular VM, is minimized significantly. Involvement of LBal efficiently monitors the load on grouped VMs and reassigns VM after task assignment to prevent VMs from overloading. Hence, balanced load among all VMs is maintained by efficient clustering and task scheduling processes. It is also necessary to balance load among PMs. PSO parameters are depicted in Table 6. Load balancing among PMs is realized by the VM migration process, which is elaborated in the next section.

4.4 VM migration based on fuzzy Logic (Stage III)
Both VM clustering and task scheduling are involved in load balancing across VMs, whereas VM migration is involved in load balancing among PMs. Load on each PM is monitored by the VM manager, which maintains PM information. PM load is calculated in terms of load on VMs that are presented in that PM as follows:
Equation (23) computes load on mth PM in terms of load L of all VMs (\(L_{i}\)) presented in that PM. VM migration also enables energy efficiency along with load balancing. VM manager takes VM migration decision in the following conditions:
-
1.
If a PM becomes overloaded (for load balancing)
-
2.
If a PM has less load (for energy efficiency).
When a PM attains one of the above conditions, optimal VM is migrated from that PM to optimal destination PM. Consider \(PM_{m}\) with \(\left\{ {VM_{1} ,VM_{2} ,..,VM_{i} , \ldots ,VM_{L} } \right\}\) and load on VMs as \(\left\{ {L_{1} ,L_{2} ,..,L_{i} , \ldots ,L_{L} } \right\}\). If \(PM_{m}\) is overloaded, then the optimal VM is selected and migrated from that PM to another PM. The optimal VM for migration is selected based on migration time, and it is computed for Lth VM as
Here, \(RAM\left( {VM_{L} } \right)\) represents RAM of \(VM_{L}\) and \(BW_{L}\) denotes the bandwidth of VML. Condition for a VM to be selected as an optimal VM for migration is formulated as
A VM that satisfies the above condition is selected for migration and denoted as \(V_{op}\). The next important step is to find an optimal destination PM for migration. Important mathematical definitions, terminology, and well-explained concepts that explain how IT2FL is set and the system is evaluated in the proposed research work are discussed in the following subsections. Detailed IT2FL set and system process are explained as follows (Fig. 4).
4.4.1 Interval type 2 fuzzy logic set (IT2FL)
Definition 1
A T2 FS is denoted as \(S^{\prime}\) and expressed by its T2 degree of membership function (DoMF) and \(\mu_{{S^{\prime}}} \left( {x,f} \right)\) is defined as follows:
where expression \(x \in X\),\(f \in D_{x}\) is the domain of \({\text{x}}\) in \(\subseteq\) \(\left[ {0,1} \right]\).The primary variable x of \(S^{\prime}\) can be denoted as \({\text{X}}\). The use of ʃʃ is to represent the union over, all correct values of x and f. If the universe of discourse (UoD) is discrete in nature, then it will be expressed as
In discrete UoD, ʃʃ is simply replaced with \(\sum \sum\)to represent the values of variables x and f. In this research, the continuous UoD approach is being focused on MF. The value of the fuzzy set \(S^{\prime}\) is expressed as:
where \(S^{\prime}\)is the fuzzy set defined over a UoD of primary variable x with T2 DoMF \(\mu _{{s^{\prime}}} \left( {x,f} \right)\).
Definition 2
If the value of \(\mu_{{S^{\prime}}} \left( {x,f} \right)\) = 1 in Eq. (24), then \(S^{\prime}\) is said to be IT2 FLS.
Definition 3
The vertical slice of \(\mu_{{S^{\prime}}} \left( {x,f} \right)\) is the representation of value \(x^{\prime}\) in \(x\) having 2d-plane with axes \(f\) and \(\mu_{{S^{\prime}}} \left( {x^{\prime},f} \right)\). Secondary MF is the vertical slice of \(\mu_{{S^{\prime}}} \left( {x,f} \right)\) [40], i.e.,
where\(\mu_{{S^{\prime}}} \left( {x^{\prime}} \right)\) is the secondary MF of \({\text{S}}^{\prime }\). Equation (30) is used when all secondary MF values of IT2 FLS are 1, otherwise \(f_{{x^{\prime}}} \left( f \right)\) will be replaced with value 1. The value of \(f_{{x^{\prime}}} \left( f \right)\) lies between \(0 \le f_{{x^{\prime}}} \left( f \right) \le 1\).
Definition 4
The representation of \(\mu_{{S^{\prime}}} \left( {x,f} \right)\) in IT2 FLS is achieved by footprint of uncertainty (FoU). The union of primary membership (\(D_{x}\)) is the FoU of \({\text{S}}^{\prime }\) as
where FoU for lower member function L(MF) \(L\mu_{{S^{\prime}}} \left( x \right)\) and upper member function U(MF) \(U\mu_{{S^{\prime}}} \left( x \right)\) are expressed as follows:
and
where \(infi\) and \(Sup\) are the infimum and supermum of the support of \(\mu_{{S^{\prime}}} \left( x \right)\).
Figure 5 shows the presentable image of IT2 FLS triangular MF for \({\text{S}}^{\prime }\) with its two bounded T1 FSs. \(L\mu_{{S^{\prime}}} \left( x \right)\) and \(U\mu_{{S^{\prime}}} \left( x \right)\) are the L(MF) and U(MF), respectively. The region between L(MF) and U(MF) is the footprint of uncertainty (FoU) [40] which is the primary membership that consists of bounded region for IT2 FLS. Any T1 FS within the FoU is the embedded T1 FS, and such sets are represented as L \((S^{^{\prime}} ){ }\) and U \(\left( {S^{\prime}} \right)\). Each input value in continuous UoD maintains DoMF that ranges the value between L(MF) and U(MF). In this work, triangular MF is used to characterize the fuzzy set. The expression of triangular MF is as follows:
A triangular MF \(\Delta \left( {a,b,c} \right)\) is the collection of optimistic boundary or lower limit \(\left( a \right)\), an expected value or middle value \(\left( b \right),\) and pessimistic boundary or upper limit \(\left( c \right)\).
4.4.2 Interval type 2 fuzzy logic system (IT2FLS)
IT2FLS is comprised of five stages, i.e., fuzzification, creation of knowledge base rule, fuzzy inference mechanism, type reduction, and defuzzification. The only difference between IT2 FLS and T1 FLS is that T1 FLS does not perform the type reduction stage. Type reduction is the central most part in IT2 FLS in which it transfers the fuzzy output set to T1 fuzzy set. The computational process includes input vectors \({ }x_{1} \in S_{1}^{^{\prime}} , \ldots .. ,x_{m} \in S_{m}^{^{\prime}}\) and single output \(y \in Y\). Knowledge base rules are characterized as \(Q\) fuzzy rules (FR) and expressed as [46]:
where \({\text{FR}}_{{\text{i}}}^{^{\prime}}\) is the ith fuzzy rule that consists of a set of universe of discourses (\(x_{1} ,x_{2} \ldots x_{m} {\text{and}} y\)) and linguistic variables (\(L_{i}^{1} ,L_{i}^{2} ..L_{i}^{m} {\text{and}} O^{i}\)). The part of FR (\(x_{1}\) is \(L_{i}^{1}\) and \(x_{2}\) is \(L_{i}^{2}\) and …..\(x_{m}\) is \(L_{i}^{m}\)) is said to be the antecedent or premise, whereas rule statement (\(y\) is \(O^{i}\)) is the consequence or conclusion. The execution process of an IT2 FLS and its mathematical terminology is discussed in the following steps:
Step1 Obtain the membership function of \(x_{m}\), on each \(S_{m}^{^{\prime}}\) using Eq. (26) which is represented as:
where \(L\mu_{{S_{m}^{^{\prime}} }} \left( {x_{m} } \right)\) and \(U\mu_{{S_{m}^{^{\prime}} }} \left( {x_{m} } \right)\) are the L(MF) and U(MF) functions of UoD \(x_{m}\) on fuzzy set \(S_{m}^{^{\prime}}\). The value of L(MF) always must be less than or equal to the value of U(MF).
Step2 Compute the firing interval of the mth rule, \(FoU_{Q} \left( { x} \right)\),
where\(f_{L}^{m} {\text{ and}} f_{U}^{m}\) are the upper bound and lower bound firing interval of mth fuzzy rule, respectively. Symbol \(\times\) denotes the product t-norm operation and expressed as:
Step3 Compute the type reduction step with the defined rule and firing interval \(FoU_{Q} \left( x \right)\) using the center of set (CoS) reducer method.
Perform Karnik–Mendel (KM) algorithm [47] to compute the left- and rightmost points \(y^{L} \left( x \right) {\text{and}} y^{R} \left( x \right),\) respectively. The KM algorithm is used to obtain the switch points for \(y^{L} \left( x \right){\text{ and}} y^{R} \left( x \right)\). The function of \(y^{L} \left( x \right)\) is to perform the firing interval switching from upper bound to lower bound. It is the minimum of \(Y_{CoS} \left( x \right)\) and can be computed as
The function of \(y^{R} \left( x \right)\) is to perform the switching firing interval from lower bound to upper bound, and it gets maximum of \(Y_{CoS} \left( x \right)\). It is computed as
where \(Ly^{L} \le y^{L} \left( x \right) \le Ly^{L + 1} \;Uy^{R} \le y^{R} \left( x \right) \le Uy^{R + 1}\).
Step4 Calculate the defuzzified output from [48],
The above equations will be used, in finding the best possible optimal destination PM. IT2 FLS has unique characteristics that provide better performance even in uncertain abound conditions and work well with missing components. The Java-based toolkit Juzzy [39] library files have been imported to input the IT2 FLS-based VM migration results in CloudSim. Configuration parameters for the fuzzy system are shown in Table 7. To understand the working approach of IT2 FLS in the proposed CMODLB method, a descriptive example is discussed. In our proposed method, we present a model for the possibility of selection of the optimal destination PM for VM migration, which depends on available memory (Avl_Mem), available CPU (Avl_CPU), and available load (Avl_Load) of destination PM. It is assumed that the selection of optimal destination PM takes input variable Avl_Mem, Avl_CPU, and Avl_Load having linguistic terms low and high and output variable Possibility with linguistic terms low, medium, and high. The input and output linguistic variables are defined by their fuzzy values. The Avl_Mem of mth PM is said to be low and high as defined in Eq. (44). Similarly, Avl_CPU and Avl_Load are defined in Eq. (45) and Eq. (46), respectively (Table 6).
The number of rules in the rule base is set by the product of the maximum number of linguistic terms in each input fuzzy set, i.e., \(2 \times 2 \times 2 = 8\). The corresponding eight fuzzy rules using Eq. (36) are elaborated in the following section. \(R^{1}\) is rule#1 which states: If available memory, available CPU, and available current load of jth PM are low, then there is a low possibility for this PM to be an optimal destination PM for VM migration. Similarly, other rules are defined in the same manner. It is shown that the highest possibility of being an optimal destination PM is achieved when the input set matches Rule#7.
The rules are stated as
Each input domain consists of two IT2 FS. Figure 6 a–c shows the UMF and LMF of input fuzzy set Avl_Mem, Avl_CPU, and Avl_Load using vertical slice representation by Eq. (26). Triangular MF has been used for the input crisp set given in Eq. (34). The obtained MF graphs represent universe of disclosure on the x-axis that ranges from 0 to 10, and the degree of MF on the y-axis which ranges between 0 and 1. Table 8 shows the FoU for upper and lower MF for each input and output linguistic variable. Representation of Type 2 set can be achieved through vertical slice, horizontal slice, wavy slice, zSliced, etc. However, in this experiment, vertical slice representation is performed due to its simplicity and ease. The FoU L(MF) and FoU U(MF) are the footprints of uncertainty for lower and upper membership functions for each input and output linguistic variable. Table 8 depicts FoU L(MF) and FoU U(MF) for low PM memory having triangular MF values \(\Delta \left( {x:1.0,3.0,3.0} \right)\) and \(\Delta \left( {x:0.0,1.0,5.0} \right),\) respectively. Similarly, other values are obtained. A fuzzy set is fed into the inference model which combines fuzzy set and rule base. Based on rules provided in the rule base, IT2 FLS provides single output for multiple inputs.
To understand its working nature, let the value of the input vector (\(x_{1} = Avl_{Mem} , x_{2} = Avl_{CPU} ,x_{3} = Avl\_Load\)) be (1.5, 3.8, 7.5). The input value of \(Avl_{Mem}\) is 1.5 which is low as given in Eq. (41), \(Avl_{CPU} {\text{is}} 3.8\) which represents low from Eq. (42) and \(Avl_{Load} {\text{is }}7.5\) which is high in range as per Eq. (43). The input value matches with rule number two (\(R^{2} :\) If Avl_Mem is Low and Avl_CPU is Low and Avl_Load is High THEN Possibility is Low). Using Eq. (36), the obtained lower and upper membership functions for \(Avl_{Mem}\),\(Avl_{CPU} {\text{and}} Avl_{Load}\) on each low and high linguistic variables are represented in Table 9. These bounds will be used in fuzzy inference rules for firing intervals IT2 FSs.
Figure 7 explains the comparable calculation for firing intervαal to a given input. When x = 1.5, the vertical line at 1.5 intersects FoU (for low Avl_Mem) in the interval \(\left[ {\mu Low_{L} \left( {Avl_{Mem} = 0.30} \right),\mu Low_{U} \left( {Avl_{Mem} = 0.52} \right)} \right]\). For x = 3.8, the vertical line at 3.8 intersects FoU (for low Avl_CPU) in the interval [\(\mu Low_{L} \left( {Avl_{CPU} = 0.28} \right),\mu Low_{U} \left( {Avl_{CPU} = 0.60} \right)],\) and for input x = 7.8, the vertical line at 7.8 intersects FoU (for low Avl_Load) in the interval \([\mu High_{L} \left( {Avl_{Load} = 0.31} \right), { }\mu High_{U} \left( {Avl_{Load} = 0.59} \right)\). From these inputs, two firing levels are then computed, i.e., firing interval lower membership (\(f_{L}^{m} )\) and upper membership (\(f_{U}^{m} )\) for each rule using Eq. (35) and Eq. (36), respectively. The lower firing intervals for rule#1 are obtained by multiplying each L(MF) of three inputs (\(Low Avl_{Mem} ,Low Avl_{CPU} and Low Avl_{Load}\)). Similarly, upper firing intervals for rule#1 are obtained by multiplying each U(MF) of three inputs (\(Low Avl_{Mem} ,Low Avl_{CPU} and Low Avl_{Load}\)) and hence \(f_{{\left( {1.5,3.8,7.8} \right)}}^{1} =\) \([f_{L}^{1} = 0.042,f_{U}^{1} = 0.187]\). The fired rule interval FoU for rule#2 is \(f_{{\left( {1.5,3.8,7.8} \right)}}^{2}\) = \(\left[ {f_{L}^{1} = 0.091,f_{U}^{2} = 0.091} \right]\). Similarly, each rule is performed in the same procedure to obtain rule FoU as given in Table 10. The centroid of the rules consequent is calculated using the iterative KM procedure [48]. For each fuzzy rule type 2 fuzzy set (FS) output, the centroid of the consequent is calculated for lower and upper interval \(y_{L}^{m} {\text{and }}y_{U}^{m}\). The total number of output FS for output possibility is 3, i.e., low, medium, and high. From Eq. (40), the obtained centroid of the low, medium, and high output FS is [0.5,3.45], [4.45,6.75], and [7.5,9.5], respectively. The centroid of each rule consequent for the output possibility is shown in Table 6. Type reduction is performed using KM algorithm, and we find left point (L) = 3 and right point (R) = 2. So, the value of \(y^{L} \left( x \right)\) is obtained to perform the firing interval switching from upper bound to lower bound, whereas the value of \(y^{U} \left( x \right)\) required to perform the switching firing interval from lower bound to upper bound using Eq. (41) and Eq. (42), respectively. It is needed to reorder \(y_{L}^{m} {\text{and }}y_{U}^{m}\) in an ascending manner where \(y_{L}^{1} \le y_{L}^{2} \le y_{L}^{3} \le y_{L}^{4} \le y_{L}^{5} \le y_{L}^{6} \le y_{L}^{7} \le y_{L}^{8}\) and \(y_{U}^{1} \le y_{U}^{2} \le y_{U}^{3} \le y_{U}^{4} \le y_{U}^{5} \le y_{U}^{6} \le y_{U}^{7} \le y_{U}^{8}\). Hence, reordered output possibility for lower bound is [0.5, 3.45, 3.45, 4.45, 4.45, 4.45, 6.75, 7.5] and for upper bound is [0.5, 0.5, 3.45, 6.75, 6.75, 6.75, 6.75, 9.50].
Defuzzification is needed to calculate the crisp output of possibility using Eq. (43). The possibility crisp output is the average summation of \(y^{L}\) and \(y^{R}\). The final crisp output \(y^{2}\) with respect to rule#2 is:
The obtained crisp output value suggests a cloud system that the PM with its input values for rule# maintains a low possibility for destination optimal PM for VM migration. It clearly shows that the output value 4.52 has a low possibility for VM migration. Figure 8 shows a graphical representation of triangular MF for output possibility using Eq. (31). The x-axis shows the possibility with respect to the input fuzzy set, and the y-axis shows the DoM between 0 and 1. The Low, Medium, and High linguistic variables for possibility are obtained by using Eq. (47). Low possibility is considered when the value of y is between 0 and 4.6. Similarly, Medium and High are obtained using Eq. (47). Table 11 depicts the lower and upper MF bounds for output possibility for its linguistic variables.
Similarly, to check the performance of IT2FLS with other rule bases similar mathematical steps have been performed for each set of rules by the obtained values of Mth PM properties. Table 12 shows the overall obtained rule# with their respective input values of three sets (memory, CPU, and load) and their respective output (possibility). It is explained that rule#1 has an output possibility of 1.3 which results in a low possibility for PMdes for VM migration from Eq. (47). Similarly, rule#2 and rule#4 have obtained low possibilities with values 4.52 and 4.23. Rule# 3, 5, 6, and 8 have achieved 4.98, 5.91, 6.84, and 7.0 crisp output values for medium possibility, respectively. The selection of PMdes for migration is to be made only when PM has high available memory, high available CPU, and low load. Finally, Rule#8 with its crisp output 8.99 has obtained high possibility to become optimal PMdes for VM migration.
The algorithm checks for \(VM_{U}\) in PM once PMdes is identified. If any PM has \(VM_{U},\) then that \(VM_{U}\) will be turned off after migration in order to save energy. Hence, this VM migration process results in load balancing among PMs along with energy efficiency. The complete working steps of VM migration-based IT2FLS algorithm are given in Algorithm 3.

4.5 Computational complexity
The proposed CMODLB algorithm is a hybridization of ANN-LB, TOPSIS-PSO, and VM migration using IT2FLS technique, which may get high computational complexity. The complexity of the complete algorithm is calculated for each working stage. The ANN-based backpropagation neural method takes \(O\left( {n^{4} } \right)\) complexity for feedforward and \(O\left( {n^{5} } \right)\) for backpropagation where ‘\(n\)’ is the number of inputs (VMs). VM load is calculated with the complexity of \(O\left( {n^{5} + n^{4} } \right)\) [41]. The computational complexity of BOK-means is of \(O\left( {N^{2} } \right)\), where \(N\) is the number of iterations [42] for Bayesian optimization. K-mean clustering algorithm takes the complexity of \(O\left( n \right)\) for computing distance between items. The reassigning cluster has the complexity of \(O\left( {km} \right)\). For centroid, it takes the complexity of \(O\left( {mn} \right)\); each of the above steps takes t iterations with \(O\left( {tkmn} \right)\) complexity, where ‘\(k\)’ is the number of clusters, ‘\(m\)’ is the objects, and ‘\(n\)’ is the dimensionality of the vector. In PSO-TOPSIS algorithm, PSO has the complexity of \(O\left( {ntlog\left( n \right)} \right)\) in which ‘\(n\)’ is the number of populations and t is the number of iterations. Besides this, the complexity of the TOPSIS algorithm is \(O\left( {n^{2} + n + 1} \right)\) for FV computation [35]. \(\left( {4p + 1} \right) M\) is the required design degree of freedom for IT2FL [43] where \(p\) is the number of antecedents corresponding to each \(M\) rule.
5 Experimental evaluation
This section explains the experimental evaluation of the proposed CMODLB load balancing method in a cloud system environment. This section also comprises subsections. In the simulation environment, the details about the proposed cloud environment are provided, while in the performance matrices, each significant matric is explained. Comparison of the CMODLB method with existing task scheduling and load balancing methods is shown in the comparative analysis section. Our proposed work is compared with other existing algorithms CESCC strategy [8], WRR method [13], DHCI [14], two-level mechanism [17], TaPRA method [18], HBB-LB [22], BSO algorithm [24], utilization model [29], TOPSIS-PSO [35], SA, GA, GA-SA, GA-GELS, PSO, PSO-SA and PSO-GELS [36] and FUGE [45] for its performance analysis.
Table13 explores the shortcomings that occurred in former scheduling and load balancing techniques. These shortcomings are taken as essential features for the experimental evaluation of the CMODLB proposed method.
5.1 Simulation setup
The proposed CMODLB in cloud environment uses JAVA (JDK 1.7) including Java runtime environment, Java class libraries, and Java tools. NetBeans 7.4 and eclipse are used for simulation. The essential classes for DCs, VMs, and computational resources are provided by the CloudSim tool [44], which supports modeling and replication of datacenters, virtualized server hosts, energy-aware computational resources, federated cloud, etc., of large-scale environment.
In Table 14, significant parameters considered in the simulation of CMODLB are depicted with their corresponding values. The values of parameters are categorized into physical machines, virtual machines, and tasks. Two to six numbers of PM having up to four processing units have been used with 4 GB RAM and 11 TB storage capacity with a maximum of 9600 MIPS. Around 10–50 numbers of VMs are used having a MIPS of up to 2400.
5.2 Performance metrics
This section discusses the significant performance metrics which are considered in the experimental evaluation. Definition of each metric is provided along with its importance. Significant metrics considered in this section are: completion time, transmission time, MakeSpan, number of VM migrations, resource utilization, and system load fairness.
5.2.1 Completion time
Completion time for a task that is assigned to a VM is a metric which is the summation of execution time (ET), transmission time (TT), and waiting time (WT) of Sth task on Lth VM and is expressed as follows:
If the load on a particular VM is more, then the tasks assigned to it suffer from high waiting time, leading to large completion time and overall high MakeSpan. Therefore, this metric should be as low as possible.
5.2.2 Transmission time
The purpose of these metrics is to calculate the transmission time, a task needs to reach a particular VM. Transmission time is the proportion of Sth task size by the bandwidth of Lth VM [35]. TT must be less to achieve better resource utilization and MakeSpan.
5.2.3 MakeSpan
MakeSpan is the total amount of time required by a VM to execute the assigned tasks [35]. It is also defined as the time difference between completion time of last job (Clast) and starting time of first job (Sfirst) and is expressed as,
This metric should be as low as possible. MakeSpan can be minimized by assigning optimal VM to user task, which can be achieved by task scheduling. Balanced VMs achieve minimum MakeSpan. It is also defined as the sum of completion time of tasks assigned on a particular VM and is given as
Here, R represents the number of tasks assigned to VM, whereas completion timep represents the completion time of pth task on that VM.
5.2.4 Number of VM migrations
Since VM migration consumes energy, CPU, bandwidth, and time, it is necessary to control the number of migrations performed in the system. This metric provides the number of migrations carried out in the system. VM migration takes place frequently if the system is unbalanced. Hence, this metric plays a vital role in the evaluation of load balancing.
5.2.5 Resource utilization
In a cloud infrastructure, resources are pooled to serve multiple consumers simultaneously. It is important to utilize these resources efficiently. An efficient task assignment process can achieve this by assigning each task to the optimal underloaded VM. Resource utilization can be calculated in terms of CPU utilization, memory utilization, and bandwidth utilization.
5.2.6 Load fairness
To analyze the performance of the proposed method having a large system load. The metric provides load fairness using its system load. The calculation of load fairness depends on the completion time of each task. It has been included that if a cloud system has a better completion time of tasks, then it has the potential to achieve higher load fairness. This analysis will predict the efficiency of system load with respect to the number of user tasks. System load fairness LF is given as [17],
where \(C{T}_{t}\) is the completion time of \(t\) tasks and \(N\) represents the total number of tasks.
5.3 Comparative analysis
In this section, the proposed CMODLB method has been compared with some of the state-of-the-art methods.
5.3.1 Analysis of completion time
This metric estimates the total execution time that comprises the waiting time of each task given in Eq. (48). The metric value should be low for an efficient cloud system. Figure 9 shows the comparative analysis among TaPRA method, BSO algorithm, and the proposed CMODLB method in terms of completion time. Here, completion time increases as the number of tasks increases. It is quite clear that BSO algorithm has maximum completion time as compared to TaPRA and CMODLB algorithm. This is for an imbalanced load on PMs in DCs. Hence, a large number of tasks cannot be accomplished in PM. In TaPRA method, completion time is slightly increased with the increase in the set of tasks. It completes 2000 tasks in approximately 42 s which the CMODLB does in 30 s. The average completion time of TaPRA method is 20.6 s, whereas the average completion time of the CMODLB method is 14.2 s. But BSO algorithm provides the average completion time of around 50 s which is higher than TaPRA method and the CMODLB method. Since TaPRA method allows a single-task assignment in each step, it takes more time than the CMODLB method. In TaPRA method, task assignment process is not able to consider execution time in order to minimize completion time. Clustering of VMs approach reduces the complexity of finding appropriate VM for the execution of tasks with respect to its current load. If the VM having less load executes the task, then the waiting time of tasks on that VM will be very less. This approach offers the lowest execution and transmission time. Due to the involvement of efficient load balancing and task assignment processes, the CMODLB method achieves 31.067% and 71.6% less completion time compared to TaPRA and BSO, respectively, as shown in Table 15. Therefore, load balancing-based CMODLB method reduces task completion time significantly.
5.3.2 Analysis of transmission time
The transmission time metric evaluates the actual transfer time of a task to reach the assigned VM. It includes the size of tasks and bandwidth of a VM as given in Eq. (49). For a well-organized cloud system environment, this metric must remain minimum. Figure 10 shows the comparative analysis among the PSO method, TOPSIS-PSO algorithm, and proposed CMODLB method in terms of transmission time. The experimental analysis is performed for 10 to 40 numbers of tasks having 10 numbers of VMs. Here, transmission time increases the number of tasks. It is noticeable that the PSO algorithm suffers from high transmission time compared to TOPSIS-PSO and the CMODLB method because the task scheduling process in PSO takes more time than TOSIS-PSO and CMODLB method. In PSO method, the transmission time slightly increases with the increase in the number of tasks. It gives nearly 0.711 s for 10 tasks, while TOPSIS-PSO takes 0.644 s and the CMODLB method achieves 0.60 s for the same. The average transmission time of PSO and TOPSIS-PSO method is 1.39 and 1.32 s, respectively, whereas the average transmission time of the CMODLB method is 1.30 s. The PSO and TOPSIS-PSO algorithms provide average transmission time around 0.09 and 0.02 s, respectively, which are higher than the CMODLB method. Due to efficient load balancing and task assignment processes, the CMODLB takes 6.65% and 2.12% less transmission time than PSO and TOPSIS-PSO, respectively, as shown in Table 16.
5.3.3 Analysis of MakeSpan
This metric gives the overall completion time of all the tasks in VMs. The metric results are low when the load balancing method is well formulated. The calculation for MakeSpan is performed using Eq. (50). The performance of the proposed work is analyzed through three sets of tests in terms of MakeSpan:
-
(1)
Test I: Experiment in Test I is performed for 15–60 numbers of tasks in 10 numbers of VMs to analyze the performance of the CMODLB with respect to static algorithms such as MaxMin and Round Robin.
-
(2)
Test II: 100–300 numbers of tasks are simulated for Test II. Results are compared with various dynamic algorithms such as FUGE [45], ACO, MACO, and TOPSIS-PSO [35] with the similar cloud setup configuration having 1000–20,000 task length, 50 numbers of VMs with 500–1000 VM bandwidth, 256–2048 VM memory (RAM), and 10 numbers of data centers with 2–6 numbers of PM.
-
(3)
Test III: To analyze the distributed nature of the proposed CMODLB algorithm, some grid computing-based algorithms [36] like SA, GA, GA-SA, GA-GELS, PSO, PSO-SA, and PSO-GELS are considered for performance evaluation. The experimental parameter values and simulation platform are kept similar for the proposed and existing algorithms for Test III.
5.3.3.1 Test I (MaxMin vs. R.R vs. CMODLB)
In the Test I experiment, the proposed CMODLB algorithm is compared with MaxMin and R.R algorithm for MakeSpan metric for 10 numbers of VMs and 15–60 numbers of tasks. Table 17 represents the obtained results for 15, 30, 45, and 60 tasks for MaxMin, R.R, and the CMODLB, respectively. Figure 11 shows that the proposed algorithm achieves 65.54% and 68.26% lesser MakeSpan than MaxMin and R.R, respectively. This analysis shows that the proposed CMODLB algorithm provides better performance in a cloud environment.
5.3.3.2 Test II: (TOPSIS-PSO vs. FUGE vs. ACO vs. MACO vs. CMODLB)
Experiment is performed to check the performance of the proposed CMODLB method with respect to MakeSpan for dynamic nature-based algorithms. The comparative analysis is done with existing algorithms [35, 45] for 100, 200, and 300 tasks. Table 18 depicts the obtained values from the simulation. Algorithm FUGE and TOPSIS-PSO have performed better than ACO and MACO, whereas CMODLB performed better among all the algorithms, as shown in Fig. 12.
5.3.3.3 Test III: (SA vs. GA vs. GA-S vs. GA-GELS vs. PSO vs. PSO-SA vs. PSO-GELS vs. CMODLB
The comparison of different algorithms is analyzed with similar simulation configurations. The MakeSpan for the proposed CMODLB and existing algorithms [36], i.e., SA, GA, GA-SA, GA-GELS, PSO, PSO-SA, and PSO-GELS, is depicted in Tables 19, 20, 21, and 22 for 100, 300, 500, and 1000 iterations, respectively, on 50, 100, 300, and 500 number of tasks having 10 numbers of resources. From Fig. 13a–d, it may be seen that MakeSpan for the CMODLB method decreases as there is an increase in the number of tasks as compared to SA, GA, GA-SA, GA-GELS, PSO, PSO-SA, and PSO-GELS algorithms. Figure 13 clearly shows that the proposed CMODLB method is highly efficient compared to PSO-GELS and other methods.
The involvement of efficient load balancing and task scheduling provides lower completion time and also helps in minimizing MakeSpan. The analysis shows that the proposed CMODLB algorithm is performing better in a cloud environment.
5.3.4 Comparative analysis on number of VM migrations
Load balancing among PMs is carried out by VM migrations, which consumes energy and time due to migration. Hence, it is necessary to minimize the number of migrations in the system. Figure 14 demonstrates the comparative analysis of the number of VM migrations of the CMODLB method with various other existing methods, viz. HBB-LB, WRR, and utilization. The CMODLB method took only one VM migration, whereas the utilization method took 25 VM migrations. Since VMs are balanced in the CMODLB method, there is a smaller number of VM migration leading to less PM overloading. Hence, in the CMODLB method, the number of VM migrations is low.
5.3.5 Analysis of resource utilization
In this section, the resource utilization performance of the CMODLB method is compared with DHCI and CESSC methods. Maximum utilization of resources indicates minimum wastage of cloud system resources. The analysis of resource utilization also illustrates the effectiveness of the cloud system to utilize bandwidth, energy, CPU, and memory.
Figure 15 demonstrates the comparative study on resource utilization with respect to time. From Fig. 15, it is clear that the wastage of resources in the CMODLB algorithm is less that indicates utilization of resources is maximum due to the efficient task assignment process. CMODLB method provides resource utilization above 50%, while the CESCC method is able to provide resource utilization between 28 and 50% for 50 min. The resource utilization of the DHCI method oscillates between 30 and 60%. The CMODLB method achieves 75% utilization, which is much effective than DHCI and CESCC. Load balancing, scheduling of tasks, and migration of VMs are always concerned with resources; hence, it is clear that implementing the CMODLB method will achieve better resource utilization and reduce wastage of resources.
5.3.6 Load fairness
This metric measures the fairness of the system with respect to load and is calculated by using Eq. (51). This metric should be as high as possible to achieve better performance [17]. In Fig. 16, system load is taken on X-axis, while the fairness of the system is taken on Y-axis. Here, fairness signifies the presentation of the proposed method in system load. The proposed CMODLB method is compared with the existing two-level method. The two-level method provides system fairness about 1 as constant for different system loads. The task scheduling process is not effective in the two-level method, and hence it has constant load fairness for different system loads, which makes it less efficient in heavy-load systems. However, the CMODLB method attains better performance with a heavy system load. It offers up to 1.12 system performance for 100% system load. It shows that the proposed method is reliable for heavy system load. Hence, the performance of load balancing is improved in the CMODLB method compared to the existing load balancing methods.
6 Conclusion
In this paper, to resolve load balancing issues in both VMs and PMs, a novel hybrid clustering, multi-criteria and VM migration-based approach (CMODLB) is proposed. To achieve our objectives, the cloud environment is designed with three entities: VM clustering using a load balancer and VM manager, the TOPSIS-PSO method for efficient task scheduling, and IT2FL for selection of optimal PM for VM migration. The first two entities approached load balancing at VM level, whereas the third entity maintains PM-level load balance. VM manager groups the VMs into underloaded and overloaded VMs, and balancer manages the clusters in order to preserve the uniqueness. For this purpose, BOEK-means with ANN algorithm is used. Task scheduling process allocates tasks to optimal underloaded VM using multi-objective-based existing TOPSIS-PSO algorithm. Optimal VM for task assignment is selected based on significant metrics such as execution time, transmission time, and CPU utilization.
The above two processes balance load among VMs, while VM migration intends to balance load across the PMs. VM migration aims to minimize load and energy consumption on PMs. Soft computing-based IT2F logic is incorporated to select optimal destination PM for VM migration to maintain PM load and energy-efficient cloud. The obtained experimental results show that the proposed CMODLB load balancing technique manages improved load balancing along with effective completion time, transmission time, MakeSpan, resource utilization, and load fairness. This IT2F logic method for calculating optimal destination PM for VM migration is novel and remarkable. In the future, we aim to cover load balancing with various machine learning tools and methods to improve energy efficiency which is lacking in the current proposed model. This will include storage intensive tasks and storage IOPS/transfer-based VM capacity in real-time cloud environment.
References
Sadiku NOM, Musa M, S, D Momoh, O, (2014) Cloud computing: Opportunities and challenges. IEEE Potentials 3(1):34–36
Diaz M, Martin C, Rubio B (2016) State-of-the-art challenges, and open issues in an integration of internet of things and cloud computing. J Netw Comput Appl 67:99–117. https://doi.org/10.1016/j.jnca.2016.01.010
Milani AS, Navimipour NJ (2016) Load balancing mechanisms and techniques in the cloud environments: systematic literature review and future trends. J Netw Comput Appl 71:86–98. https://doi.org/10.1016/j.jnca.2016.06.003
Zhi-H Zhan, Xiao-F Liu, Yue-Jiao Gong, Zhang J (2015) Cloud computing resource scheduling and a survey of its evolutionary approaches. ACM Comput Surv 47(4):1–33. https://doi.org/10.1145/2788397
Hua H, Guangquan X, Shanchen P, Zenghua Z (2016) AMTS: adaptive multi-objective task scheduling strategy in cloud computing. China Commun 13(4):162–171. https://doi.org/10.1109/CC.2016.7464133
Yuan H, Bi J, Tan W, Zhou M, Li BH, Li J (2017) TTSA: an effective scheduling approach for delay bounded tasks in hybrid clouds. IEEE Trans Cybern 47(11):3658–3668. https://doi.org/10.1109/TCYB.2016.2574766
Zhong Z, Chen K, Zhai X, Zhou S (2016) Virtual machine-based task scheduling algorithm in a cloud computing environment. Tsinghua Sci Technol 21(6):660–667. https://doi.org/10.1109/TST.2016.7787008
Xu X, Cao L, Wang X (2016) Resource pre-allocation algorithms for low-energy task scheduling of cloud computing. J Syst Eng Electron 27(2):457–469. https://doi.org/10.1109/JSEE.2016.00047
Sharma SCM, Rath AK (2017) Multi-Rumen Anti-Grazing approach of load balancing in cloud network. Int J Info Technol 9(2):129–138. https://doi.org/10.1007/s41870-017-0022-y
Singha A, Junejab D, Malhotra M (2015) Autonomous agent based load balancing algorithm in cloud computing. Procedia Comput Sci 45:832–841. https://doi.org/10.1016/j.procs.2015.03.168
Gutierrez-Garcia JO, Ramirez-Nafarrate A (2015) Agent-based load balancing in cloud data centers. Cluster Comput 18(3):1041–1062. https://doi.org/10.1007/s10586-015-0460-x
Chun-C L, Hui-H C, Der-J D (2014) Dynamic multiservice load balancing in cloud-based multimedia system. IEEE Syst J 8(1):225–234. https://doi.org/10.1109/JSYST.2013.2256320
Chitra DD, Uthariaraj VR (2016) Load balancing in cloud computing environment using improved weighted round robin algorithm for nonpreemptive dependent tasks. Sci World J 2016:1–14. https://doi.org/10.1155/2016/3896065
Tao D, Lin Z, Wang B (2017) Load feedback-based resource scheduling and dynamic migration-based data locality for virtual Hadoop clusters in OpenStack-based clouds. Tsinghua Sci Technol 22(2):149–159.https://doi.org/10.23919/TST.2017.7889637
Xie R, Wen Y, Jia X, Xie H (2015) Supporting seamless virtual machine migration via named data networking in cloud data center. IEEE Trans Parallel Distrib Syst 26(12):3485–3497. https://doi.org/10.1109/TPDS.2014.2377119
Mosleh Mohammed AS, Radhamani G, Hazber Mohamed AG, Hasan SH (2016) Adaptive cost-based task scheduling in cloud environment. Sci Program 2016:1–9. https://doi.org/10.1155/2016/8239239
Liu Y, Li C, Li L (2016) Distributed two-level cloud-based multimedia task scheduling. Automat Contr Comput Sci 50(3):41–150. https://doi.org/10.3103/S0146411616030044
Shi L, Zhang Z, Robertazzi T (2017) Energy-aware scheduling of embarrassingly parallel jobs and resource allocation in cloud. IEEE Trans Parallel Distrib Syst 28(6):1607–1620. https://doi.org/10.1109/TPDS.2016.2625254
Li Y, Chen M, Dai W, Qiu M (2017) Energy optimization with dynamic task scheduling mobile cloud computing. IEEE Syst J 11(1):96–105. https://doi.org/10.1109/JSYST.2015.2442994
Keng-M C, Pang-W T, Chun-W T, Chu-S Y (2015) A hybrid meta-heuristic algorithm for VM scheduling with load balancing in cloud computing. Neural Comput Appl 26(6):297–1309. https://doi.org/10.1007/s00521-014-1804-9
Eswaran S, Rajakannu M (2017) Multiservice load balancing with hybrid particle swarm optimization in cloud-based multimedia storage system with QoS provision. Mobile Netw Appl 22(4):760–770. https://doi.org/10.1007/s11036-017-0840-y
Dhinesh Babu LD, Venkata Krishna P (2013) Honey bee behavior inspired load balancing of tasks in cloud computing environments. Appl Soft Comput 13:2292–2303. https://doi.org/10.1016/j.asoc.2013.01.025
Negi S, Panwar N, Vaisla K S, Rauthan MMS (2020) Artificial Neural Network Based Load Balancing in Cloud Environment. Advances in Data and Information Sciences. Lecture Notes in Networks and Systems, 94. /https://doi.org/10.1007/978-981-15-0694-9_20.
Jeyakrishnan V, Sengottuvelan P (2017) A Hybrid Strategy for Resource Allocation and Load Balancing in Virtualized Data Centers Using BSO Algorithms. Wireless Pers Commun 94(4):2363–2375. https://doi.org/10.1007/s11277-016-3481-8
Polepally V K, Chatrapati K S (2017) Dragonfly optimization and constraint measure-based load balancing in cloud computing. Cluster Computing. Springer.https://doi.org/10.1007/s10586-017-1056-4
Zhao J, Yang K, Wei X, Ding Y, Hu L, Xu G (2016) A Heuristic Clustering-based Task Deployment Approach for Load Balancing Using Bayes Theorem in Cloud Environment. IEEE Trans Parallel Distrib Syst 27(2):305–316. https://doi.org/10.1109/TPDS.2015.2402655
Tsakalozos K, Verroios V, Roussopoulos M, Delis A (2017) Live VM Migration under Time-Constraints in Share-Nothing IaaS-Clouds. IEEE Trans Parallel Distrib Syst 28(8):2285–2298. https://doi.org/10.1109/TPDS.2017.2658572
Kansal Nidhi J, Chana I (2016) Energy-aware Virtual Machine Migration for cloud computing—a firefly optimization approach. J Grid Comput 14(2):327–345. https://doi.org/10.1007/s10723-016-9364-0
Farahnakian F, Pahikkala T, Liljeberg P, Plosila J, TrungHieu N, Tenhunen H (2016) Energy-aware VM Consolidation in Cloud Data Centers Using Utilization Prediction Model. IEEE Transactions on Cloud Computing (99).https://doi.org/10.1109/TCC.2016.2617374
Patel G, Mehta R, Bhoi U (2015) Enhanced Load Balanced Min-Min algorithm for Static Meta-task Scheduling in Cloud Computing. Procedia Computer Science (Elsevier). https://doi.org/10.1016/j.procs.2015.07.385
Lakraa AV, Yadav DK (2015) Multi-Objective Tasks Scheduling Algorithm for Cloud Computing Throughput Optimization. Procedia Computer Science, Elsevier 48:107–113. https://doi.org/10.1016/j.procs.2015.04.158
Zhang P, Zhou Meng C (2017) Dynamic Cloud Task Scheduling Based on a Two-Stage Strategy. IEEE Trans Autom Sci Eng 99:1–12. https://doi.org/10.1109/TASE.2017.2693688
Zuo X, Zhang G, Tan W (2014) Self-Adaptive Learning PSO-Based Deadline Constrained Task Scheduling for Hybrid IaaS Cloud. IEEE Trans Autom Sci Eng 11(2):564–573. https://doi.org/10.1109/TASE.2013.2272758
Awada AI, El-Hefnawyb NA, Abdelkader HM (2015) Enhanced Particle Swarm Optimization for Task Scheduling in Cloud Computing Environments. Procedia Comput Sci Elsevier 65:920–929. https://doi.org/10.1016/j.procs.2015.09.064
Panwar N, Negi S, Rauthan MMS, Vaisla KS (2019) TOPSIS–PSO inspired non-preemptive tasks scheduling algorithm in cloud environment. Clust Comput. https://doi.org/10.1007/s10586-019-02915-3
Pooranian Z, Shojafar M, Abawajy Jemal H, Abraham A (2013) An efficient meta-heuristic algorithm for grid computing. J Comb Optim, Springer 30(3):413–434. https://doi.org/10.1007/s10878-013-9644-6
Brochu E, Cora Vlad M, Freitas Nando D (2013) A Tutorial on Bayesian Optimization of Expensive Cost Functions with Application to Active User Modeling and Hierarchical Reinforcement Learning. https://arxiv.org/abs/1012.2599
Nyikosa F M, Osborne M A, Roberts S J (2018) Bayesian Optimization for Dynamic Problems. https://arxiv.org/abs/1803.03432
Wagner C (2013) Juzzy – A Java based Toolkit for Type-2 Fuzzy Logic. IEEE. Symposium on Advances in Type-2 Fuzzy Logic Systems (T2FUZZ). https://doi.org/10.1109/T2FZZ.2013.6613298
Mendel JM, John RI, Liu F (2006) Interval Type-2 Fuzzy Logic Systems Made Simple. IEEE Trans Fuzzy Syst 14(6):808–821
Kasper Fredenslund (2018) March 25. https://kasperfred.com/series/introduction-to-neural-networks/computational-complexity-of-neural-networks
Baptista R, Poloczek M (2018) Bayesian optimization of combinatorial structures. In: Proceedings of the 35th International Conference on Machine Learning, Stockholm, Sweden, PMLR. 80. https://arxiv.org/abs/1806.08838
Ren Q, Balazinski M, Baron L (2011) Type-2 TSK fuzzy logic system and its type-1 counterpart. Int J Comput Appl 20(6):0975–8887. https://doi.org/10.5120/2440-3292
Buyya R, Ranjan R, Calheiros R N (2019) Modeling and Simulation of Scalable Cloud Computing Environments and the CloudSim Toolkit: Challenges and Opportunities. High Performance Computing & Simulation HPCS’09. 1–11. https://doi.org/10.1109/HPCSIM.2009.5192685
Shojafar M, Javanmardi S, Saeid A, Nicola C (2015) FUGE: a joint meta-heuristic approach to cloud job scheduling algorithm using fuzzy theory and a genetic method. Clust Comp 18(2):829–844
Chen Y (2019) Study on Centroid Type-Reduction of Interval Type-2 Fuzzy Logic Systems Based on Noniterative Algorithms. Compl Hindwai 2019:1–12. https://doi.org/10.1155/2019/7325053
Mendel JM (2013) On KM algorithms for solving type-2 fuzzy set problems. IEEE Trans Fuzzy Syst 21(3):426–446
Liang Q, Mendel J (2000) Interval Type-2 fuzzy logic systems: theory and design. IEEE Trans Fuzzy Syst 8:535–550
Singh H, Tyagi S, Kumar P (2020) Crow–penguin optimizer for multiobjective task scheduling strategy in cloud computing. Int J Commun Syst 33(5):e4467. https://doi.org/10.1002/dac.4467
Prassanna J, Venkataraman N (2019) Threshold based multi-objective memetic optimized round robin scheduling for resource efficient load balancing in cloud. Mobile Netw Appl 24:1214–1225. https://doi.org/10.1007/s11036-019-01259-x
Neelima P, Rama Mohan Reddy A (2020) An efficient load balancing system using adaptive dragonfly algorithm in cloud computing. Cluster Comput 23:2891–2899. https://doi.org/10.1007/s10586-020-03054-w
Acknowledgment
The first author (Sarita Negi) acknowledges Prof. Man Mohan Singh Ruthann, Dr. Rohit Mahar, and the Department of Computer Science and Engineering, H N B Garhwal University (Srinagar Garhwal), Uttarakhand, for their immense support and resources.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Negi, S., Rauthan, M.M.S., Vaisla, K.S. et al. CMODLB: an efficient load balancing approach in cloud computing environment. J Supercomput 77, 8787–8839 (2021). https://doi.org/10.1007/s11227-020-03601-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11227-020-03601-7