Abstract
Based on locally indistinguishable orthogonal product states, we propose a novel multiparty quantum key agreement (QKA) protocol. In this protocol, the private key information of each party is encoded as some orthogonal product states that cannot be perfectly distinguished by local operations and classical communications. To ensure the security of the protocol with small amount of decoy particles, the different particles of each product state are transmitted separately. This protocol not only can make each participant fairly negotiate a shared key, but also can avoid information leakage in the maximum extent. We give a detailed security proof of this protocol. From comparison result with the existing QKA protocols, we can know that the new protocol is more efficient.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Key agreement (KA) is an important branch of cryptography, which was first proposed by Diffie and Hellman [1]. In a KA protocol, each participant fairly contributes to the generation of a shared key and any nontrivial subset of the participants cannot decide a shared key. Ever since the concept of KA was put forward, many scholars focused on extending the two-party Diffie–Hellman protocol to a multiparty case and some efficient KA protocols [2,3,4,5] were proposed. As we know, the security of classical cryptosystems including KA protocols is mostly based on computation complexity. However, with the rapid development of quantum computation, classical cryptosystems are confronted with more and more austere challenges.
Fortunately, quantum cryptography, which is based on the principle of quantum mechanical (such as Heisenberg uncertainty principle and quantum no-cloning theorem), can provide unconditional security. In the past twenty years, many kinds of quantum cryptographic protocols, such as quantum key distribution (QKD) [6,7,8,9], quantum secret sharing (QSS) [10, 11], quantum secure direct communication (QSDC) [12,13,14,15,16,17], quantum private comparison (QPC) [18, 19], quantum private query (QPQ) [20,21,22,23,24] and quantum signature [25,26,27,28,29,30,31,32] have been proposed.
The first QKA protocol was proposed by Zhou et al. [33]. However, Tsai et al. [34] found that it is not a fair QKA protocol since one participant can fully determine a shared key alone without being detected by other participants. Chong et al. [35] proposed the first two-party QKA protocol, which has high qubit efficiency. Later, Shi et al. [36] presented a QKA protocol, which is based on EPR pairs and entanglement swapping. In Ref. [37], Liu et al. pointed out that Shi et al.’s protocol cannot resist the participant attack and they presented a multiparty quantum key agreement with single particles. Huang et al. [38] proposed a quantum key agreement which is based on EPR pairs and single-particle measurements. It is a pity that Huang et al’s protocol cannot be extended to multiparty case. In Ref. [39], the multiparty QKA protocols are divided into three categories. The authors pointed out that the second category [40,41,42,43,44] and the third category [45] are unfair. They also showed that the first category [37, 46, 47] is not efficient. Hence, how to design a fair, secure and efficient QKA protocol is an important research topic at present.
The local distinguishability of orthogonal product states is a hot topic in the field of quantum information. Many properties about the local distinguishability of orthogonal product states were proposed [48,49,50,51,52,53,54,55,56]. In a \(d\otimes d\) \((d\ge 3)\) quantum system, Yu et al. [51] gave \(2d-1\) orthogonal states that cannot be perfectly distinguished by local operations and classical communications (LOCC) and conjectured that any set of no more than \(2(d-1)\) product states can be perfectly distinguished by LOCC. Wang et al. [52] proved that \(3(m+n)-9\) orthogonal product states are locally indistinguishable in an \(m\otimes n\) quantum system, where \(m\ge 3\) and \(n\ge 3\). Recently, Zhang et al. [53] proved a smaller set with only \(2n-1\) orthogonal product states that are locally indistinguishable in \(m\otimes n\) (\(3\le m \le n\)). Xu et al. [54,55,56] gave different methods to construct a set of orthogonal product states that cannot be perfectly distinguished by LOCC both in a bipartite quantum system and a multipartite quantum system. However, there exist only a few results about the application of the local distinguishability of orthogonal product states at present. In Ref. [57], a novel QKD protocol based on locally indistinguishable orthogonal product states was proposed. This is the first time that the local indistinguishability is used to design a QKD protocol. Later, Zhao et al. [58] proposed a new QKD protocol based on locally distinguishable orthogonal product states, which is easier to carry out in practice. Yang et al. [59] presented a quantum secret sharing protocol, which is based on local indistinguishable orthogonal product states. In fact, the generation of an orthogonal product state is much easier than the generation of an entangled state. Moreover, the cryptographic protocols, which are designed based on orthogonal product states, have high efficiency [57,58,59]. Thus, it is an interesting thing to design a QKA protocol based on locally indistinguishable orthogonal product states since no one has ever done.
In this paper, we propose a novel QKA protocol that is based on local indistinguishable orthogonal product states. In the protocol, the two different particles of each product state are transmitted, respectively, which can ensure enough security under the condition of reducing the number of the detected particles. That is, the new protocol has high efficiency. The rest of the paper is organized as follows. In Sect. 2, some fundamental preliminaries are introduced. In Sect. 3, we propose our multiparty QKA protocol. In Sect. 4, the properties of our protocol such as security and efficiency are discussed. At last, a short conclusion is given in Sect. 5.
2 Preliminaries
In this section, we introduce some preliminaries that are used in what follows.
We say a set of orthogonal states is locally indistinguishable if it cannot be perfectly distinguished by LOCC [60].
Theorem 1
The following orthogonal product states in Eq. (1) cannot be perfectly distinguished by LOCC no matter who goes first.
Here one party goes first [60] means that he is the first person to perform a nontrivial measurement upon the system. The proof of Theorem 1 is given in the “Appendix.”
3 Multiparty QKA protocol
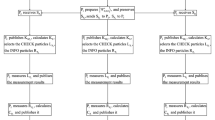
Now, we introduce our n-party QKA protocol that is based on the eight local indistinguishable orthogonal product states. Suppose that the n participants are \(A_{1}, A_{2}, \ldots , A_{n}\). The detailed process of the protocol is as follows.
-
(1)
\(A_{i}\) generates a random 3l-bit string \(K_{i}\) as his secret key, where \(i=1,2,\ldots ,n\).
-
(2)
\(A_{i}\) successively divides his secret \(K_{i}\) into l groups (each group has 3 bits). For each group, \(A_{i}\) encodes it as a product state according the following rules:
$$\begin{aligned}&000:\,\,\longmapsto |\psi _{1}\rangle =\frac{1}{\sqrt{2}}(|0\rangle +|1\rangle )_{1}|1\rangle _{2},\nonumber \\&001:\,\,\longmapsto |\psi _{2}\rangle =\frac{1}{\sqrt{2}}(|0\rangle -|1\rangle )_{1}|1\rangle _{2},\nonumber \\&010:\,\,\longmapsto |\psi _{3}\rangle =\frac{1}{\sqrt{2}}(|0\rangle +|2\rangle )_{1}|2\rangle _{2},\nonumber \\&011:\,\,\longmapsto |\psi _{4}\rangle =\frac{1}{\sqrt{2}}(|0\rangle -|2\rangle )_{1}|2\rangle _{2},\nonumber \\&100:\,\,\longmapsto |\psi _{5}\rangle =\frac{1}{\sqrt{2}}|2\rangle _{1}(|0\rangle +|1\rangle )_{2},\nonumber \\&101:\,\,\longmapsto |\psi _{6}\rangle =\frac{1}{\sqrt{2}}|2\rangle _{1}(|0\rangle -|1\rangle )_{2},\nonumber \\&110:\,\,\longmapsto |\psi _{7}\rangle =\frac{1}{\sqrt{2}}|1\rangle _{1}(|0\rangle +|2\rangle )_{2},\nonumber \\&111:\,\,\longmapsto |\psi _{8}\rangle =\frac{1}{\sqrt{2}}|1\rangle _{1}(|0\rangle -|2\rangle )_{2}. \end{aligned}$$(2)Thus, the Key \(K_{i}\) of \(A_{i}\) is encoded as a sequence of product states, \(S_{i}\).
-
(3)
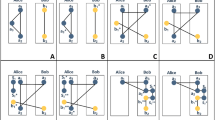
\(A_{i}\) generates \(n-1\) same quantum sequences \(S_{i}\). For simplicity, we denote these sequences as \(S_{i1}\), \(S_{i2}\), \(\ldots \), \(S_{i,i-1}\), \(S_{i,i+1}\), \(\ldots \), \(S_{in}\) (See Fig. 1), where \(i=1,2,\ldots ,n.\)
-
(4)
For \(S_{ij}\), \(A_{i}\) picks out the first particle of each product state to form the sequence \(S_{ij}^{(1)}\) and the second one of each product state to form the sequence \(S_{ij}^{(2)}\). \(A_{i}\) generates rl decoy particles which are randomly in one of the four states \(\{|+y\rangle ,\,|-y\rangle ,\,|+\rangle ,\,|-\rangle \}\) and randomly inserts them into \(S_{ij}^{(1)}\) and \(S_{ij}^{(2)}\), where r is the detection rate, \(i=1,2,\ldots ,n\); \(j\in \{1,2,\ldots ,i-1,i+1,\ldots ,n\}\) and
$$\begin{aligned} |+y\rangle= & {} \frac{1}{\sqrt{2}}(|0\rangle +i|1\rangle )\nonumber \\ |-y\rangle= & {} \frac{1}{\sqrt{2}}(|0\rangle -i|1\rangle )\nonumber \\ |+\rangle= & {} \frac{1}{\sqrt{2}}(|0\rangle +|1\rangle )\nonumber \\ |-\rangle= & {} \frac{1}{\sqrt{2}}(|0\rangle -|1\rangle ). \end{aligned}$$(3)It should be noted that the i of Eq. (3) is imaginary unit. Now, we denote the new sequences as
$$\begin{aligned} \overline{S}_{i1}^{(1)},\overline{S}_{i1}^{(2)},\overline{S}_{i2}^{(1)}, \overline{S}_{i2}^{(2)},\ldots ,\overline{S}_{i,i-1}^{(1)},\overline{S}_{i,i-1}^{(2)}, \overline{S}_{i,i+1}^{(1)},\overline{S}_{i,i+1}^{(2)}, \ldots ,\overline{S}_{i,n}^{(1)},\overline{S}_{i,n}^{(2)}. \end{aligned}$$ -
(5)
\(A_{i}\) sends the sequence \(\overline{S}_{ij}^{(1)}\) to \(A_{j}\) (see Fig. 2), where \(i=1,2,\ldots ,n;\) and \(j=1,2,\ldots ,i-1,i+1,\ldots ,n.\)
-
(6)
After all the participants claim that they have received all the sequences that were sent to them, they begin to start the first eavesdropping detection. For the sequence \(\overline{S}_{ij}^{(1)}\), which was sent to \(A_{j}\) by \(A_{i}\), \(A_{i}\) announces the positions and the corresponding bases of the decoy particles. Then, \(A_{j}\) measures the decoy particles with the correct bases and randomly announces half of the measurement results. \(A_{i}\) publishes the initial states of the left half of the decoy particles. At last, they check whether or not the measurement results and the initial states are consistent. If there exists no error, they continue to carry out the protocol; otherwise, they abandon the protocol.
-
(7)
\(A_{i}\) sends the sequence \(\overline{S}_{ij}^{(2)}\) to \(A_{j}\) (Fig. 3), where \(i=1,2,\ldots ,n;\) \(j=1,2,\ldots ,i-1,i+1,\ldots ,n.\) After all the participants claim that they have received all the sequences that were sent to them, they make the second eavesdropping detection as they do in step (6). If there exists no error, they continue to carry out the protocol; otherwise, they abandon the protocol.
-
(8)
\(A_{j}\) recovers the sequence \(S_{ij}\) according to the remaining sequences \(S_{ij}^{(1)}\) and \(S_{ij}^{(2)}\), where \(i=1,2,\ldots ,j-1,j+1,\ldots ,n\) and \(j=1,2,\ldots ,n.\) Then \(A_{j}\) measures each product state of \(S_{ij}\) with the following basis
$$\begin{aligned} \{|\psi _{1}\rangle ,|\psi _{2}\rangle ,|\psi _{3}\rangle ,|\psi _{4}\rangle ,|\psi _{5}\rangle , |\psi _{6}\rangle ,|\psi _{7}\rangle ,|\psi _{8}\rangle ,|\psi _{9}\rangle =|0\rangle |0\rangle \} \end{aligned}$$and recovers \(K_{i}\) according to the measurement results for \(i=1,2,\ldots ,j-1,j+1,\ldots ,n\).
-
(9)
\(A_{j}\) computes the final key \(K=K_{1}\oplus K_{2}\oplus \cdots \oplus K_{n},\) where \(j=1,2,\ldots ,n.\)
\(A_{i}\) encodes his key as the quantum sequences to be transmitted. Here \(S_{ij}\) is the quantum sequence of product states, and \(S_{ij}=S_{it}\) for \(j\ne t\). \(S_{ij}^{(k)}\) is the quantum sequence generated by the k-th particle of every product state of \(S_{ij}\) and \(\overline{S}_{ij}^{(k)}\) is generated by inserting decoy particles into \(S_{ij}^{(k)}\) for \(k=1,2\)
Through the above steps, each participant can get the final key K.
4 Security and efficiency analysis of the proposed QKA protocol
In this section, we will give a detailed analysis of the security and efficiency of the new protocol. For the security analysis, we consider the outside attacks and the participants’ attacks.
4.1 Security analysis
Now, we prove that our QKA protocol is secure.
4.1.1 Outside attacks
Here we firstly consider the collective attack since the particles in the sequences are product states. In fact, the opportunity for an outside eavesdropper to obtain the information of the key is between step (5) and step (7). Because the positions and the bases of the decoy particles are unknown to the eavesdropper before the sender announces the corresponding information in step (6), an outside eavesdropper can perform the most general attack as follows. Firstly, he intercepts the transmitted sequences. Secondly, he performs a collective operation U on each intercepted particle and an additional particle \(|\theta \rangle \) which is prepared by him. Finally, he sends the operated particles to the receivers. Without loss of generality, suppose that the operation U holds:
where
If the eavesdropper wants to extract the encoded information precisely, the three reduced density matrices
must be discriminated precisely, which means
for \(i,j,t=0,1,2.\) Therefore, the unitary transformation U on the decoy particles and the additional particles has the universal form
where \(\tau =1,-1,i,-i.\) So the reduced density matrix of the receiver’s system is
It is easy to see that the density matrix has nothing to do with the variable \(\tau \), which means the subsystems of the states on the decoy positions in the receiver’s hand are identical. Thus, the error rate in the detection stage is maximized. That means that an outside eavesdropper cannot steal the secret without introducing any error.
Finally, Eve may choose the delay-photon Trojan horse attack [61, 62] and the invisible particle eavesdropping Trojan horse attack [63]. We can use the photon number splitter find the multi-photon signals and the quantum filter to filter out the invisible particles [61,62,63]. Therefore, our protocol can resist these two kinds of Trojan horse attacks.
4.1.2 Participants’ attacks
Without loss of generality, suppose \(A_{1}\) is a dishonest participant. He has two different methods to cheat other participants. The first one is to extract the key information encoded in the sequences that he receives before he sends the sequences that he generates to other participants. The second one is that he announces different positions of the decoy particles in his favor.
For the first method, he cannot get any useful information before he sends the sequences that he generates to other participants. In fact, each participant encodes his own key information as a quantum sequence of product states. The quantum sequence is divided into two sequences. And the two sequences are sent to other participants separately after decoy particles are inserted. Only all the participants announce that they have received all the first sequences of other participants, they start to the first check eavesdropping. If there is no error, they send the second sequences to each of other participants. Thus, \(A_{1}\) cannot get any information according to the sequences that he receives before he sends the first sequence to all the other participants. This is because the key information is encoded as a sequence of product states that cannot be perfectly distinguished by LOCC and the two particles of each product state are transmitted separately.
For the second method, \(A_{1}\) publishes different positions of the decoy particles, i.e., some encoded particles become decoy particles and some decoy particles become encoded particles. For simplicity, we give an example to show our protocol is secure. Without loss of generality, suppose \(A_{1}\) chooses his key \(K_{1}=010\, \,101\, \,011\, \,110\). Thus he encodes \(K_{1}\) as the sequence of product states, S, according to Eq. (2), where \(S=\{|\psi _{3}\rangle ,\,|\psi _{6}\rangle ,\,|\psi _{4}\rangle ,\,|\psi _{7}\rangle \}\).
-
(1)
\(A_{1}\) generates the product sequence S and divides it into two sequences \(S_{1}\) and \(S_{2}\), where \(S_{1}=\{\frac{1}{\sqrt{2}}(|0\rangle +|2\rangle ),\,|2\rangle ,\,\frac{1}{\sqrt{2}} (|0\rangle -|2\rangle ),\,|1\rangle \}\) and \(S_{2}=\{|2\rangle ,\,\frac{1}{\sqrt{2}}(|0\rangle -|1\rangle ),\,|2\rangle ,\, \frac{1}{\sqrt{2}}(|0\rangle +|2\rangle )\}\).
-
(2)
\(A_{1}\) generates four decoy particles \(|-y\rangle ,\,|+\rangle ,\,|-\rangle ,\,|+y\rangle ,\,\) and inserts them into \(S_{1}\) and \(S_{2}\) to get \(S'_{1}\) and \(S'_{2}\), respectively, where \(S'_{1}=\{\frac{1}{\sqrt{2}}(|0\rangle +|2\rangle ),\,|-y\rangle ,\,|2\rangle ,\,|+\rangle ,\,\frac{1}{\sqrt{2}} (|0\rangle -|2\rangle ),\,|1\rangle \}\) and \(S'_{2}=\{|2\rangle ,\,|-\rangle ,\,\frac{1}{\sqrt{2}}(|0\rangle -|1\rangle ),\,|2\rangle ,\, \frac{1}{\sqrt{2}}(|0\rangle +|2\rangle ),\,|+y\rangle \,\}\).
-
(3)
\(A_{1}\) sends the sequence \(S'_{1}\) to an honest participant \(A_{i}\). Suppose that \(A_{1}\) announces the second particle and the fifth particle of \(S'_{1}\) are decoy particles, i.e., the fifth particle \(\frac{1}{\sqrt{2}}(|0\rangle -|2\rangle )\) is an encoded particle while it is announced a decoy particle.
Now, we consider the probability of the measurement outcomes of \(A_{i}\), when he measures the fifth particle with the basis \(\{|+y\rangle ,\,|-y\rangle \}\) or \(\{|+\rangle ,\,|-\rangle \}\). In fact,
thus, we have
That is, if \(A_{i}\) measures the fifth particle, \(\frac{1}{\sqrt{2}}(|0\rangle -|2\rangle )\), with the basis \(\{|+y\rangle ,\,|-y\rangle \}\), he will get \(|+y\rangle \) or \(|-y\rangle \) with the same probability \(\frac{1}{4}\); if he measures it with the basis \(\{|+\rangle ,\,|-\rangle \}\), he will get \(|+\rangle \) or \(|-\rangle \) with the same probability \(\frac{1}{4}\). Therefore, if \(A_{i}\) lets \(A_{1}\) publish the identity of the fifth particle, the error probability of \(A_{1}\) is \(\frac{3}{4}\). So if the decoy particles are enough, \(A_{i}\) can find \(A_{1}\)’s deception. This means that the second method cannot cheat an honest participant without being found.
According to the above analysis, the proposed QKA protocol is secure against both outside attacks and participants’ attacks.
4.2 Efficiency analysis
In Refs. [47, 64], quantum efficiency is introduced to judge the efficiency of QKA protocol. For QKA protocols with classical bits exchanged, quantum efficiency is
where c represents the total number of the agreement classic bits, q is the total number of the particles generated in the protocol and b represents the total number of classic bits exchanged for decoding of the message (classical bits utilized for eavesdropping check are not counted).
According to Eq. (9), we computer the efficiency of our QKA protocol. For comparison with the existing protocols, we take the three-party case as an example to calculate the efficiency of our protocol. If a 3l-bit agreement key is generated by our (three-party) protocol, every party needs to generated two quantum sequences to each of the other two parties. The two quantum sequences contain 2l particles (which come from l product states), \(2m_{1}\) decoy particles for detecting the delay-particle Trojan horse attack and \(2m_{2}\) decoy particles for detecting general eavesdropping attacks. Thus every party needs to send \(2\times (2l+2m_{1}+2m_{2})\) particles to the other two parties. Therefore \(c=3l\) and \(q=3\times 2\times (2l+2m_{1}+2m_{2})\). Since our protocol needs no classic bits exchanged for decoding the encoded information, the quantum efficiency of our protocol (three-party case) is
Suppose that \(4m_{1}=m_{2}=l\) (here the value is same as Ref. [47] for comparison), we have \(\eta =11.11\%\). According to Ref. [47], we can get the efficiencies of other existing protocol under a same standard.
It should be noted that the data of Table 1 (except that of our protocol) come from Ref. [47].
From Table 1, it can be easily seen that the efficiency of our protocol is higher than that of other protocols (except XWGQ’s protocol. However, our new protocol is more secure than XWGQ’s protocol since the latter is an unfair QKA protocol [39]). That is, our new protocol is efficient.
5 Conclusions
The local distinguishability of orthogonal product states has got a lot of attention in the past two decades [51,52,53,54,55,56]. There exist only a few research results about the application of local indistinguishable orthogonal product states. In this paper, we proposed a QKA protocol based on local indistinguishable orthogonal product states. The new protocol can decrease the use of decoy particles without reducing the security since the different particles of each product states are transmitted separately. On the other hand, it can enhance the security with a same detection rate when compared with other QKA protocols [39].
References
Diffie, W., Hellman, M.: New direction in cryptography. IEEE Trans. Inf. Theory 22, 644–654 (1976)
Ingemarsson, I., Tang, D.T., Wong, C.K.: A conference key distribution system. IEEE Trans. Inf. Theory 28, 714–719 (1982)
Steiner, M., Tsudik, G., Waidner, M.: Key agreement in dynamic peer groups. IEEE Trans. Parallel Distrib. Syst. 11, 769–780 (2000)
Mitchell, C.J., Ward, M., Wilson, P.: Key control in key agreement protocols. Electron. Lett. 34(10), 980–981 (1998)
Ateniese, G., Steiner, M., Tsudik, G.: New multiparty authentication services and key agreement protocols. IEEE J. Sel. Areas Commun. 18(4), 628–639 (2000)
Wang, T.Y., Wen, Q.Y., Chen, X.B.: Cryptanalysis and improvement of a multi-user quantum key distribution protocol. Opt. Commun. 283(24), 5261–5263 (2010)
Salas, P.J.: Security of plug-and-play QKD arrangements with finite resources. Quantum Inf. Comput. 13, 861–879 (2013)
Deng, F.G., Long, G.L., Liu, X.S.: Two-step quantum direct communication protocol using the Einstein–Podolsky–Rosen pairblock. Phys. Rev. A 68, 042317 (2003)
Cui, Y.J.: Uniqueness of solution for boundary value problems for fractional differential equations. Appl. Math. Lett. 51, 48–54 (2016)
Qin, S.J., Gao, F., Wen, Q.Y., et al.: Improving the security of multiparty quantum secret sharing against an attack with a fake signal. Phys. Lett. A 357, 101–103 (2006)
Gao, F., Guo, F.Z., Wen, Q.Y., et al.: Quantum key distribution without alternative measurements and rotations. Phys. Lett. A 349, 53–58 (2006)
Long, G.L., Liu, X.S.: Theoretically efficent high capacity quantum key distribution scheme. Phys. Rev. A 65, 032302 (2002)
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Deng, F.G., Long, G.L.: Secure direct communication with a quantum one-time pad. Phys. Rev. A 69, 052319 (2004)
Gao, F., Qin, S.J., Wen, Q.Y., Zhu, F.C.: Cryptanalysis of multiparty controlled quantum secure direct communication using Greenberger–Horn–Zeilinger state. Opt. Commun. 283, 192–195 (2010)
Huang, W., Zuo, H.J., Li, Y.B.: Cryptanalysis and improvement of a multi-user quantum communication network using type entangled states. Int. J. Theor. Phys. 52, 1354–1361 (2013)
Lin, S., Wen, Q.Y., Zhu, F.C.: Quantum secure direct communication with \(\chi \)-type entangled ststes. Phy. Rev. A 78, 064304 (2008)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11, 373–384 (2011)
Liu, W., Wang, Y.B., Jiang, Z.T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun. 284, 3160–3163 (2011)
Martini, F.D., Giovannetti, V., Lloyd, S., Maccone, L., et al.: Experimental quantum private queries with linear optics. Phys. Rev. A 80, 010302 (2009)
Jakobi, M., Simon, C., Gisin, N., Bancal, J.D., et al.: Practical private database queries based on a quantum-key-distribution protocol. Phys. Rev. A 83, 022301 (2011)
Gao, F., Liu, B., Huang, W., Wen, Q.Y.: Postprocessing of the oblivious key in quantum private query. IEEE. J. Sel. Top. Quantum 21, 6600111 (2015)
Wei, C.Y., Wang, T.Y., Gao, F.: Practical quantum private query with better performance in resisting joint-measurement attack. Phys. Rev. A 93, 042318 (2016)
Wei, C.Y., Cai, X.Q., Liu, B., et al.: A generic construction of quantum-oblivious-key-transfer-based private query with ideal database security and zero failure. IEEE Trans. Comput. 67(1), 2–8 (2018)
Zeng, G.H., Keitel, C.H.: An arbitrated quantum signature algorithm. Phys. Rev. A 65, 042312 (2002)
Lee, H., Hong, C.H., Kim, H., et al.: Arbitrated quantum signature scheme with message recovery. Phys. Rev. A 321, 295–300 (2004)
Wen, X.J., Niu, X.M., Ji, L.P.: A weak blind signature scheme based on quantum cryptography. Opt. Commun. 282, 666–669 (2009)
Wang, T.Y., Wen, Q.Y.: Fair quantum blind sigantures. Chin. Phys. B 19, 060307–060311 (2010)
Wen, X.J., Tian, Y., Niu, X.M.: A group signature scheme based on quantum teleportation. Phys. Scr. 81, 055001–055006 (2010)
Liu, F., Qin, S.J., Su, Q.: An arbitrated quantum signature scheme with fast signing and verifying. Quantum Inf. Process. 13, 491–502 (2014)
Xu, G.B., Zhang, K.J.: A novel quantum group signature scheme without using entangled states. Quantum Inf. Process. 14, 2577–2587 (2015)
Xu, G.B.: Novel quantum proxy signature without entanglement. Int. J. Theor. Phys. 54(8), 2605–2612 (2015)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40, 1149–1150 (2004)
Tsai, C., Hwang, T.: On quantum key agreement protocol. Technical report, C-S-I-E, NCKU, Taiwan, ROC (2009)
Chong, S.K., Tsai, C.W., Hwang, T.: Improvement on quantum key agreement protocol with maximally entangled states. Int. J. Theor. Phys. 50(6), 1793–1802 (2011)
Shi, R.H., Zhong, H.: Multi-party quantum key agreement with bell states and bell measurements. Quantum Inf. Process. 12, 921–932 (2013)
Liu, B., Gao, F., Huang, W., Wen, Q.Y.: Multiparty quantum key agreement with single particles. Quantum Inf. Process. 12, 1797–1805 (2013)
Huang, W., Wen, Q.Y., Liu, B., Fei, G., Sun, Y.: Quantum key agreement with EPR pairs and single-particle measurements. Quantum Inf. Process. 13(3), 649–663 (2014)
Liu, B., Xiao, D., Jia, H.Y., Liu, R.Z.: Collusive attacks to circle-type multi-party quantum key agreement protocols. Quantum Inf. Process. 15, 2113 (2016)
Sun, Z.W., Zhang, C., Wang, B.H., et al.: Improvements on multiparty quantum key agreement with single particles. Quantum Inf. Process. 12(11), 3411–3420 (2013)
Shukla, C., Alam, N., Pathak, A.: Protocols of quantum key agreement solely using Bell states and Bell measurement. Quantum Inf. Process. 13(11), 2391–2405 (2014)
Zhu, Z.C., Hu, A.Q., Fu, A.M.: Improving the security of protocols of quantum key agreement solely using Bell states and Bell measurement. Quantum Inf. Process. 14(11), 4245–4254 (2015)
Sun, Z.W., Yu, J.P., Wang, P.: Efficient multi-party quantum key agreement by cluster states. Quantum Inf. Process. 15, 373–384 (2016)
Sun, Z.W., Zhang, C., Wang, P., Yu, J.P., Zhang, Y., Long, D.Y.: Multi-Party quantum key agreement by an entangled six-qubit state. Int. J. Theor. Phys. 55(3), 1920–1929 (2016)
Xu, G.B., Wen, Q.Y., Gao, F., Qin, S.J.: Novel multiparty quantum key agreement protocol with GHZ states. Quantum Inf. Process. 13(12), 2587–2594 (2014)
Yin, X.R., Wen, W.P., Shen, D.S., et al.: Three-party quantum key agreement with Bell states. Acta Phys. Sin. 62(17), 170304 (2013)
He, Y.F., Ma, W.P.: Quantum key agreement protocols with four-qubit cluster states. Quantum Inf. Process. 14(9), 3483–3498 (2015)
Yang, Y.H., Gao, F., Xu, G.B., Zuo, H.J., Zhang, Z.C., Wen, Q.Y.: Characterizing unextendible product bases in qutrit-ququad system. Sci. Rep. 5, 11963 (2015)
Ma, H.J., Jia, Y.M.: Stability analysis for stochastic differential equations with infinite Markovian switchings. J. Math. Anal. Appl. 435, 593–605 (2016)
Wang, Z., Huang, X., Shi, G.D.: Analysis of nonlinear dynamics and chaos in a fractional order financial system with time delay. Comput. Math. Appl. 62, 1531–1539 (2011)
Yu, S.X., Oh, C.H.: Detecting the local indistinguishability of maximally entangled states (2015). arXiv:1502.01274v1 [quant-ph]
Wang, Y.L., Li, M.S., Zheng, Z.J., Fei, S.M.: Nonlocality of orthogonal product-basis quantum states. Phys. Rev. A 92, 032313 (2015)
Zhang, Z.C., Gao, F., Cao, Y., Qin, S.J., Wen, Q.Y.: Local indistinguishability of orthogonal product states. Phys. Rev. A 93, 012314 (2016)
Xu, G.B., Wen, Q.Y., Qin, S.J., Yang, Y.H., Gao, F.: Quantum nonlocality of multipartite orthogonal product states. Phys. Rev. A 93(3), 032341 (2016)
Xu, G.B., Yang, Y.H., Wen, Q.Y., Qin, S.J., Gao, F.: Locally indistinguishable orthogonal product bases in arbitrary bipartite quantum system. Sci. Rep. 6, 31048 (2016)
Xu, G.B., Wen, Q.Y., Gao, F., Qin, S.J., Zuo, H.J.: Local indistinguishability of multipartite orthogonal product bases. Quantum Inf. Process. 16, 276 (2017)
Guo, G.P., Li, C.F., et al.: Quantum key distribution scheme with orthogonal product states. Phys. Rev. A 64, 042301 (2001)
Zhao, Q.Y., Zhang, D.X., Li, X.Y.: Quantum key distribution protocol using orthogonal product quantum states. J. Univ. Electr. Sci. Technol. China 37(3), 401–403 (2008)
Yang, Y.G., Wen, Q.Y., Zhu, F.C.: An efficient quantum secret sharing protocol with orthogonal product states. Sci. China Phys. Mech. 50, 331–338 (2007)
Walgate, J., Hardy, L.: Nonlocality, asymmetry, and distinguishing bipartite states. Phys. Rev. Lett. 89, 147901 (2002)
Deng, F.G., Li, X.H., Zhou, H.Y., Zhang, Z.J.: Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A 72, 044302 (2005)
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74, 054302 (2006)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351, 23–25 (2006)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85, 5635–5638 (2000)
Acknowledgements
This work is supported by NSFC (Grant Nos. 61402148, 61601171) and Project of Science and Technology Department of Henan Province of China (172102210275).
Author information
Authors and Affiliations
Corresponding author
Appendix: a proof of Theorem 1
Appendix: a proof of Theorem 1
Proof
Now we prove the states (1) cannot be perfectly distinguished by LOCC if the first party goes first. If so, then by their symmetry these states cannot be perfectly distinguished with the second party going first.
Suppose that the first party performs a general measurement with a set of \(3\times 3\) POVM elements \(\{M^{\dag }_{k}M_{k};\,k=1,2,\ldots ,l_{1}\}\), where
under the basis \(\{|0\rangle ,|1\rangle ,|2\rangle \}\).
It is noted that the postmeasurement states must be pairwise orthogonal for making further discrimination feasible. That is, the states that are orthogonal on the first side should maintain the orthogonality on the first side after the measurement.
For the states \(|\psi _{1}\rangle \) and \(|\psi _{5}\rangle \), we can get
i.e.,
Thus,
For the states \(|\psi _{2}\rangle \) and \(|\psi _{5}\rangle \), we can get
i.e.,
Thus,
So, we have
For the states \(|\psi _{3}\rangle \) and \(|\psi _{7}\rangle \), we can get
i.e.,
Thus,
For the states \(|\psi _{4}\rangle \) and \(|\psi _{7}\rangle \), we can get
i.e.,
Thus,
So, we have
For the states \(|\psi _{1}\rangle \) and \(|\psi _{2}\rangle \), we can get
i.e.,
Thus,
So, we have
For the states \(|\psi _{3}\rangle \) and \(|\psi _{4}\rangle \), we can get
i.e.,
Thus,
So, we have
This means that any of the POVM elements of the first party should be in the form
Consider the states \(|\psi _{5}\rangle \) and \(|\psi _{7}\rangle \). If the first party distinguishes the states outright then for one of states \(|\psi _{5}\rangle \) and \(|\psi _{7}\rangle \), \(\langle \psi _{i}|M_{k}^{\dag }M_{k}\otimes (I_{3\times 3})^{\otimes 4}|\psi _{i}\rangle =0.\) But given (25), \(\langle \psi _{i}|M_{k}^{\dag }M_{k}\otimes (I_{3\times 3})^{\otimes 4}|\psi _{i}\rangle =m_{00}^{k}.\) Thus, \(m_{00}^{k}=0\) and, since POVM elements must be positive, \(M_{k}^{\dag }M_{k}\) is the null matrix.
According to the above analysis, all of the first party’s POVM elements must be proportional to the identity. Thus, the first party cannot go first and by the symmetry of states (1), neither can the second party. Therefore, these states are locally indistinguishable. This completes the proof. \(\square \)
Rights and permissions
About this article
Cite this article
Jiang, DH., Xu, GB. Multiparty quantum key agreement protocol based on locally indistinguishable orthogonal product states. Quantum Inf Process 17, 180 (2018). https://doi.org/10.1007/s11128-018-1951-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-018-1951-5