Abstract
As is known to all that entities authentication can provides secure communication for QSS protocol. In this paper, the authors propose a novel semi-quantum secret sharing (SQSS) scheme where identity authentication is adopted to verify the identification of partners in communication based on GHZ-type states. Any related quantum operations can be performed by the quantum Alice, however, classical partners can only perform classical operations on the transmitted qubits as well as unitary transformation. In addition, the paper also shows that the protocol is secure resist some eavesdropping attacks.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Quantum cryptography is a new discipline that combines quantum physics with cryptography, which is a new cryptographic structure that can implement quantum cryptography by applying quantum physics, and it mainly involves the quantum key distribution (QKD) [1, 2], quantum identity authentication (QIA) [3, 4], quantum secure direct communication (QSDC) [5, 6] and quantum secret sharing (QSS) [7,8,9], etc. The fundamental idea of QSS is that the sender Alice can split a secret message into several parts and sends them to every receiver so that the secret message can not be restructured by each of the individual. QSS has three intentions: distributing secret keys, sharing classical secret messages and sharing quantum secrets (unknown quantum states) among amount of parties. In 1999, Hillery et al. [7] proposed the first QSS protocol that can safely share secret information by using three-particle GHZ entangled states as a quantum resource. However, existing QSS protocols require users to have full quantum capabilities. Obviously, it is unrealistic that each participant has the high quantum resource and preparation or measuring of the capability of an arbitrary quantum state. To resolve these problems, Boyer et al. [10] first put forward the concept of a semi-quantum cryptography scheme based on the BB84 protocol in 2007. Then in 2009, Boyer et al. [11] further improved the semi-quantum concept by using single photons as quantum resources. Since then, semi-quantum idea has been applied to different quantum information processing work, such as semi-quantum key distribution (SQKD) [12, 13], semi-quantum secure direct communication (SQSDC) [14] and semi-quantum secret sharing (SQSS) [15,16,17] etc. Moreover, the introduction of the idea of semi-quantum into QSS makes the QSS protocol more easily to be implemented in the actual systems while saving quantum resources. The characteristics of SQSS has been constantly attracting scholars to study and discuss in-depth, and now there are many valuable research results has been acheived. In 2010, Li et al. [15] put forward to two SQSS schemes by using maximally entangled GHZ states, only one of which has all quantum capabilities. In 2016, Gao et al. [17] presented a multi-party SQSS scheme by using Bell states as quantum resources.
Furthermore, identity authentication can provide secure communication for QSS protocol. It is the procedure of verifying the identification of partner in communication, to protect a communication from malicious attacker pretending to be a legitimate partner. In 2004, Nguyen [18] proposed a quantum dialogue (QD) protocol to achieve the process of quantum identity authentication, in which the sender and the receiver can exchange their secret message simultaneously. Since then, many QD protocols have been proposed [19,20,21].
Based on the above analysis, the authors realized that although the previous SQSS protocol could withstand most attacks, eavesdroppers may still launch special attacks provided that the user does not verify the identity of the other party during the security check. Thus the authors proposed a new SQSS scheme in which two classical partners Bob and Charlie, can simultaneously perform mutual identity authentication by using three-particle entangled states (GHZ-type states). The idea of entities authentication in the proposed QSS scheme was inspired by the protocols in Ref. [22]. The difference between our protocol and the protocol in Ref. [10] is that in the authors’ protocol, the classical Bob and Charlie can also apply the classical unitary transformation \({U \in \left \{ {I,x,y,z} \right \}}\) (where I is a 2 ×2 unit matrix, x, y, z are the usual Pauli matrices) on the qubits respectively. It’s well-known that they construct a complete basis of any 2 ×2 matrices. And the authors’ protocol is more efficient than the previous protocol. Finally, the result shows that the proposed SQSS scheme can efficiently resist intercept-resend attack, modification attack and Trojan horse attack.
The rest of this paper is organized as follows: In Section 2, we proposed a SQSS scheme based on GHZ-type states. In Section 3, we gave an example to further explain our scheme. In Section 4, we analyzed the security of the scheme from multiple angles. In Section 5, the proposed SQSS scheme is comprehensively compared with other existing schemes. Finally, Section 6 we drew the conclusion.
2 The Proposed SQSS Scheme
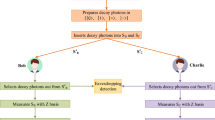
Assume that the sender Alice wants to share a secret with two classical agents Bob and Charlie. The protocol includes two phases: the first phase is identity authentication phase and the second one is SQSS phase. In the first phase, a QD protocol is considered between Bob and Charlie for authenticating the identity of each other similar as Ref. [18]. The difference between the protocol and the protocol in Ref. [10] is that Alice prepares N GHZ-type states, she takes each particle from each state to form three ordered sequences SA, SB, SC. Alice sends SB sequence to Bob, and sends SC sequence to Charlie, then Bob and Charlie can use the measurement result of Alice to determine the initial states of the Bell states in the identity authentication phase. In the second phase, Alice shares a message among Bob and Charlie. The proposed protocol proceeds in the following steps (See Fig. 1):
Step 1
Alice generates N three-particle GHZ-type entangled states, and each one is in the state
Where subscript A represents the 1st particle of each state, B describe as the 2nd particles of each state, and C represents the 3rd particles of each state. She divides these states into three ordered sequences of qubits:SA = {A1, A2,⋯, AN}, SB = {B1, B2,⋯, BN}, SC = {C1, C2,⋯, CN}. Then Alice sends sequence SB, SC to Bob and Charlie respectively, and retains the quantum sequence SA for herself.
Step 2
After receiving SB from Alice, Bob informs Alice that she has received the SB. Bob randomly selects n1 (n1 < N/2) qubits from the received sequence SB as the checking state, called CB1, and then informs Alice the positions of CB1 via a public classical channel. Once the position of CB1 is received, Alice selects the particle composition sequence CA1 at the corresponding position in SA, and using Z-basis {|0〉,|1〉} to measure CA1 to obtain the measurement result \({{R_{{C_{A1}}}}}\). Then, Alice sends \({{R_{{C_{A1}}}}}\) to Bob through the public classic channel. According to the \({{R_{{C_{A1}}}}}\), Bob can deduce whether the particle B and particle C at the corresponding positions are in state \({\left | {\mathop \varphi \nolimits ^ + } \right \rangle = \frac {{\left ({\left | {00} \right \rangle + \left | {11} \right \rangle } \right )}}{{\sqrt 2 }}{\text { or }}\left | {\mathop \psi \nolimits ^ + } \right \rangle = \frac {{\left ({\left | {01} \right \rangle + \left | {10} \right \rangle } \right )}}{{\sqrt 2 }}}\). Then Bob randomly chooses one of the four unitary operations {U00, U01, U10, U11}, to be applied on CB1. Next, the position of CB1 will be announced to Charlie.
Step 3
According to the positions announced from Bob, Charlie chooses the corresponding photons in SC, called CC1, and measures CC1 using Z-basis {|0〉,|1〉} to obtain the measurement result, \({{R_{{C_{C1}}}}}\). Charlie also selects n1 (n1 < N/2) photons as checking photons, called CC2, from the remaining SC. Charlie announces the positions of CC2 to Alice. Alice takes the action similar to step 2 to choose the corresponding photons in SA, called CA2, and measures CA2 using Z-basis {|0〉,|1〉} to obtain the measurement result, \({{R_{{C_{A2}}}}}\). Then Alice sends \({{R_{{C_{A2}}}}}\) to Charlie via a public classical channel. Upon receiving the \({{R_{{C_{A2}}}}}\), according to Alice’s measurement result being 0 or 1, Charlie can determine that particle B and particle C in the corresponding entangled state collapse into entangled state \({\left | {\mathop \varphi \nolimits ^ + } \right \rangle = \frac {{\left ({\left | {00} \right \rangle + \left | {11} \right \rangle } \right )}}{{\sqrt 2 }}{\text { or }}\left | {\mathop \psi \nolimits ^ + } \right \rangle = \frac {{\left ({\left | {01} \right \rangle + \left | {10} \right \rangle } \right )}}{{\sqrt 2 }}}\), and randomly applies one of the four unitary operations {U00, U01, U10, U11} on CC2. Finally, Charlie sends \({{R_{{C_{C1}}}}}\) and announces the positions of CC2 to Bob.
Step 4
Upon receiving measurement result \({{R_{{C_{C1}}}}}\) and the positions of CC2, Bob first measures CB1 using Z-basis {|0〉,|1〉} to obtain the measurement result \({{R_{{C_{B1}}}}}\). Then, Bob checks whether \({{R_{{C_{B1}}}}}\) and \({{R_{{C_{C1}}}}}\) have deterministic correlation according to \({{R_{{C_{A1}}}}}\), as follows. If the ith bit of \({{R_{{C_{A1}}}}}\) is 0, the ith bit of \({{R_{{C_{C1}}}}}\) and \({{R_{{C_{B1}}}}}\) are the same, otherwise, the result of the ith bit of \({{R_{{C_{C1}}}}}\) and \({{R_{{C_{C1}}}}}\) is opposite, where i = 1,2,⋯, n1. If it exists correlation, Bob trusts there is no eavesdropper during the transmission of SB and simultaneously the identity of Alice is authenticated. Otherwise, they stop this communication. Subsequently, Bob selects the corresponding photon in the remaining sequence SB, called CB2, according to the position of CC2, and uses the Z-basis {|0〉,|1〉} to measure CB2 to obtain the measurement result \({{R_{{C_{B2}}}}}\). Finally, Bob sends \({{R_{{C_{B2}}}}}\) to Charlie through the public classic channel.
Step 5
Upon receiving measurement result \({{R_{{C_{B2}}}}}\), Charlie first measures CC2 to obtain the measurement result \({{R_{{C_{C2}}}}}\). Then, Alice checks whether \({{R_{{C_{C2}}}}}\) and \({{R_{{C_{B2}}}}}\) have deterministic correlation according to \({{R_{{C_{A2}}}}}\). Similar to step 4, if it exists correlation, Charlie trusts there is no eavesdropper during the transmission of SC and simultaneously the identity of Bob is authenticated. Otherwise, they stop this communication. After that, sequences SA, SB and SC remove the authenticated particles, and the remaining sequences convert to \({{S^{\prime }_{A}}}\), \({{S^{\prime }_{B}}}\) and \({{S^{\prime }_{C}}}\), respectively.
Step 6
Next, Alice shares the secret message with Bob and Charlie using \({{S^{\prime }_{B}}}\) and \({{S^{\prime }_{C}}}\).
-
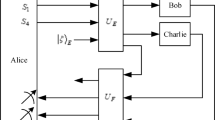
(i) Bob randomly selects particles in \({{S^{\prime }_{B}}}\) to measure with Z-basis and prepares new identical quantum states to send to Alice (called SHARE); or Bob returns the particles without any interference (called CHECK). The resent qubits are reordered via different delay lines. At the same time, Charlie does the action similar to Bob. It is important to note that at least one particle in the same position in \({{S^{\prime }_{B}}}\) and \({{S^{\prime }_{C}}}\) is measured by both Bob and Charlie, and if there is no such photon, the scheme will be aborted and restarted.
-
(ii) Alice receives and restores the qubits reflected by Bob and Charlie in quantum memory, and announces that she has received their reflected particles publicly. Alice asks Bob and Charlie to announce the actions they take on each particle and the order of the particles.
-
(iii) For each particle in \({{S^{\prime }_{A}}}\), Alice will take four different ACTIONs according to the actions performed by Bob and Charlie, as illustrated in Table 1.
ACTION 1: Alice measures her own qubit in the Z-basis {|0〉,|1〉}.
ACTION 2: Alice combines her qubit with Charlie’s reflected qubit and performs a Bell measurement.
ACTION 3: Alice combines her own qubit with Bob’s reflected qubit and performs a Bell measurement.
ACTION 4: Alice combines her own qubit with the two reflected qubits and performs an appropriate three-particle measurement.
-
(iv) Alice evaluates the probability of error. If the probability exceeds the preset threshold, then the communication step terminates. Otherwise, the protocol continues. Bob can work with Charlie to get the Shared key:
$$S = {R_{B}} \oplus {R_{C}}$$
Here RB, RC represent the measurement results of Bob and Charlie respectively. ⊕ represents the XOR operation.
3 An Example
In this section, the authors give an example to show our scheme.
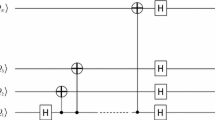
Assume the sequence generated by Alice is \(\left \{ {{|}}\phi \rangle _{1},{{|}}\phi {\rangle _{2}},{{|}}\phi {\rangle _{3}},{{|}}\phi {\rangle _{4}},{{|}}\phi {\rangle _{5}},{{|}}\phi {\rangle _{6}},\right .\) \(\left .{{|}}\phi {\rangle _{7}},{{|}}\phi {\rangle _{8}}\right \}\). Alice takes each particle from each state to form three ordered sequences SA = {a1, a2, a3, a4, a5, a6, a7, a8}, SB = {b1, b2, b3, b4, b5, b6, b7, b8}, SC = {c1, c2, c3, c4, c5, c6, c7, c8}. Alice sends SB sequence to Bob, and sends SC sequence to Charlie. After receiving SB, we can assume that Bob randomly selects n1 = 3 (n1 < 4) qubits in SB to form checking sequence CB1 = {b1, b2, b3 }, and then Bob announces the positions of CB1 to Alice. Alice takes the corresponding qubits to form CA1 = {a1, a2, a3 } and measures each selected qubits in Z-basis. Assume that the measurement result \({{R_{{C_{A1}}}} = \{ {\text { 0}},0,{\text {1 }}\} }\) and Bob takes unitary operations U00, U11, U10 on CB1, then the state of corresponding particle B and particle C is {|φ〉1+,|φ〉2+,|ψ〉3+ }. Bob informs Charlie the positions of CB1. Charlie selected the corresponding particles in SC to form \({{C_{C1}} = \left \{ {{c_{1}},{c_{2}},{c_{3}}} \right \}}\), and measured them with Z-basis to get the measurement results \({{R_{{C_{C1}}}}}\) and then Charlie randomly selects n2 = 3 (n2< 4) qubits in remaining sequence SC to form checking sequence CC2 = {c4, c5, c6 }. Assume that \({{R_{{C_{_{A2}}}}} = \{ {\text { }}1,1,{\text {0 }}\} }\), the unitary operations of Charlie is U11, U01, U00. Then Charlie sends \({{R_{{C_{C1}}}}}\) and the positions of CC2 to Bob. Next, Bob authenticates the identity of Charlie. If it is valid, Bob sends \({{R_{{C_{B2}}}}}\) to Charlie. Charlie authenticates the identity of Bob, and then Alice shares the secret message with Bob and Charlie using \({{S^{\prime }_{B}}{\text { = \{ }}{{\text {b}}_{7}}{\text {,}}{{\text {b}}_{8}}{\text {\} }}}\) and \({{S^{\prime }_{C}}{\text { = \{ }}{c_{7}}{\text {,}}{c_{8}}{\text {\} }}}\). If only the 8th particle is measured by both Bob and Charlie and RB8 = 1, RC8 = 0, remaining photon is for checking. Finally, Bob and Charlie can get S = 1 according to S = RB8 ⊕ RC8.
4 Security Analysis
In this section, the authors analyze the security of the proposed SQSS protocol. There are three probability attacks: (1) intercept-resend attack; (2) Modification attack; (3) Trojan horse attack. The outside attacks are much less threatening than internal attacks because dishonest participants already know shadows of the secret. Therefore, in the following security analysis, the authors focus on the attack of the internal dishonest participants. Suppose Bob is a dishonest participant in the proposed SQSS scheme.
4.1 Intercept-Resend Attack
In the proposed SQSS scheme, dishonest participant, Bob can know the positions of CC2 and sends the measurement result \({{R_{{C_{B2}}}}}\) to Charlie. Alice also sends the measurement result \({{R_{{C_{A2}}}}}\) to Charlie. When dishonest participant Bob adopts a intercept-and-resend attack, there are two potential scenarios:
-
(i) In identity authentication phase, Bob intercepts \({{R_{{C_{A2}}}}}\) and re-sends a new sequence composed of \({\left | 0 \right \rangle }\) and \({\left | 1 \right \rangle }\) to Charlie. He can get the corresponding states of particle B and particle B. However, he will be detected in Step 5, because Bob does not know the unitary operations \({{U_{xy}} = \left \{ {{U_{00}},{U_{01}},{U_{10}},{U_{11}}} \right \}}\), which Charlie takes on the particle C. The probability for Bob to know the right unitary operation is 1/4, but the probability for Bob to finish the identity authentication is 1/2, and the reason is that when Charlie chooses U00 and U01, the results that Bob prepares are the same and when Charlie chooses U10 and U11, the results that Bob prepares are the same. Consequently, the probability of detecting Bob’s attack is \({1 - {\left ({\frac {1}{2}} \right )^{{n_{2}}}}}\), If n2 is large enough, the probability of detecting Bob’s attack is 1.
-
(ii) In SQSS phase, Bob intercepts SC and re-sends a new sequence SE randomly composed of \({\left | 0 \right \rangle }\) and \({\left | 1 \right \rangle }\) to Charlie and then Bob intercepts \({{R_{{C_{A2}}}}}\) and re-sends a new sequence composed of \({\left | 0 \right \rangle }\) and \({\left | 1 \right \rangle }\) to Charlie. He can get the corresponding states of particle B and particle C. However, he will be detected in Step 5, because Bob does not know the unitary operations \({{U_{xy}} \in \left \{ {{U_{00}},{U_{01}},{U_{10}},{U_{11}}} \right \}}\), which Charlie takes on the particles in SE. The probability for dishonest participant Bob to finish the identity authentication is 1/2. Consequently, the probability of detecting Bob’s attack is \({1 - {\left ({\frac {1}{2}} \right )^{{n_{2}}}}}\), If n2 is large enough, the probability of detecting Bob’s attack converges to 1. Accordingly, the proposed SQSS scheme is secure against intercept-resend attack.
4.2 Modification Attack
In the modification attack, the attacker eve deliberately modified the content of the transmitted photon, so that the correspondent could obtain a false or wrong key message without being discovered. In the identity authentication phase, Eve can perform unitary operations on the particles in the sequence SC, so as to modify the particles held by Charlie without being detected. After receiving \({{R_{{C_{A2}}}}}\), Charlie can know each state of corresponding particle B and particle C. Undoubtedly, Charlie will detect Eve in step 5. Since Charlie knows the \({{R_{{C_{A2}}}}}\) and \({{R_{{C_{B2}}}}}\), he measures sequence CC2, expecting that \({{R_{{C_{C2}}}}}\) and \({{R_{{C_{B2}}}}}\)have deterministic correlation. In the SQSS phase, Eve can perform unitary operations on the particles in the sequence \({{S^{\prime }_{C}}}\), so as to modify the particles held by Charlie without being detected. However, Alice knows initial states, after she received the sequence sent from Bob and Charlie, Eve will be detected. Therefore, the proposed SQSS scheme can resist modification attack efficiently.
4.3 Trojan Horse Attack
In the SQSS scheme, the dishonest participant, Bob, can attach some invisible photons to each particle of SC transmitted from Alice to Charlie, and inserting some delay photons in the same time window to each particle of SC. By adding a wavelength filter (WF) before all devices and a photon number splitter (PNS) [23, 24], it can resist the attack.
5 Performance Evaluation and Comparisons
In the section, comparisons are made between the proposed QSS scheme and the schemes in Refs. [15, 26] and [27,28,29,30,31]. Table 2 show the comparison results, in which the information-theoretical efficiency [25] is defined as η = bs/qt + bt, where bs denotes the secret information bits transmitted, qt denotes the total qubits used (qt = qc + d Where qc denotes the number of qubits used to simultaneously send messages and d denotes the number of qubits used for checking sequence.) and bt denotes the classical bits exchanged between Alice and Bob.
5.1 Comparison with Ref. [15]
Li et al. [15] proposed a semi-quantum secret sharing scheme based on entangled states, which showed that Alice shared secrets with two classic parties by using the maximum entangled GHZ state. Behind the perfect scheme, however, there is an attack threat that cannot be defended against the Trojan horse attack. Compared with Li et al.’s scheme, in the autors’ scheme, in order to detect Trojan horse attacks, Alice (Bob) can use wavelength filter (WF) to remove the hidden photons and consume decoy photons in photon splitting (PNS) to detect delayed photons. In addition, the authors did not insert decoy particles as safety detection particles.
5.2 Comparison with Ref. [26]
Tsai et al. [26] proposed a semi-quantum secret sharing scheme based on the W states, which uses the characteristics of semi-quantum to reduce the consumption of quantum resources. Although this scheme improves the efficiency of qubits, there is a security problem of dishonest participants. In other words, the efficiency of qubits is improved at the expense of security. In our proposal, the authors introduce quantum identity authentication technology to comprehensively improve the efficiency of qubits under the premise of ensuring the security.
5.3 Comparison with Refs. [27,28,29,30,31]
Based on the EPR states proposed by Gao et al. [28] aimed at the efficient multi-party quantum secret sharing protocol, Hwang et al. [27] pointed out that this protocol had a low utilization rate of qubits. Therefore, Hwang et al. proposed a multi-partied quantum secret sharing protocol based on the GHZ states, which effectively solved the problem of qubit utilization. Later, Liu et al. found that the protocol proposed by Hwang et al. had security loopholes. Therefore, Liu et al. [29] proposed an improved scheme to detect the presence of eavesdroppers by inserting a single photon to deceive it. After that, Xie et al. [30] applied the semi-quantum technology to the quantum secret protocol and proposed a novel semi-quantum secret sharing scheme. Subsequently, Yin et al. [31] continued to improve based on the scheme of Xie et al. and made a phased contribution to improving the efficiency and safety of qubits.
Communication security is an eternal topic for mankind. Based on the advantages and disadvantages of the previous scheme, the authors innovatively proposed a semi-quantum secret sharing scheme based on identity authentication technology. Compared with the previous one, the authors’ scheme has perfectly applied the identity authentication technology to the SQSS scheme. It enables to resist the various attacks to prevent the information leakage thus ensure the security of communication.
6 Conclusions
In this paper, the authors have proposed an authenticated SQSS protocol based on GHZ-type sates. Before sharing the secret message, participant Bob and Charlie has performed mutual authentication with each other. Eventually, the participants Bob and Charlie perform the XOR operation to deduce Alice’s sharing secret. Simultaneously, it shows that the proposed SQSS protocol can efficiently resist intercept-resend attack, modification attack and Trojan horse attack. In addition, since the proposed SQSS protocol does not require all participants to have quantum capabilities, secret sharing can be achieved at a lower cost. Performance evaluation shows that the qubits efficiency is higher than most existing schemes.
References
Shor, P.W., Preskill, J.: Simple Proof of Security of the BB84 Quantum Key Distribution Protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Margarida, P., Go, K., Akihiro, M., et al.: Quantum key distribution with correlated sources. Science advances. 37(6) (2020)
Chang, H., Jino, H., Jin, G.J.: Quantum identity authentication with single photon. Quantum Inf. Process. 16(10), 236 (2017)
Zhang, S., et al.: A novel quantum identity authentication based on Bell states. Int. J. Theor. Phys. 59(1), 236-249 (2020)
Zhang, W., et al.: Quantum Secure Direct Communication with Quantum Memory. Phys. Rev. A.118(22), 220501 (2017)
Cai, J., Pan, Z., Wang, T.J., et al.: High-capacity quantum secure direct communication using hyper-entanglement of photonic qubits. Int. J. Theor. Phys. 14(8) (2016)
Hillery, M., Buoek, V., Berthiaume A.: Quantum secret sharing. Phys. Rev. A. 59(3), 1829-1834 (1999)
Qin, H.W., Dai, Y.: Efficient quantum secret sharing. Quantum Inf. Process. 15(5), 2091–2100 (2016)
Deng, F.G., et al.: Efficient high-capacity quantum secret sharing with two-photon entanglement. Phys. Lett. A. 372(12), 1957-1962 (2008)
Boyer, M., Kenigsberg, D., Mor, T.: Quantum key distribution with classical bob. Phys. Rev. Lett. 99(14), 140501 (2007)
Boyer, M., Gelles, R., Kenigsberg, D., et al.: Semi-quantum key distribution. Phys. Rev. A. 79(3), 32341-32341 (2009)
Zhu, K.N., Zhou, N.R., Wang, Y.Q., et al.: Semi-Quantum Key Distribution Protocols with GHZ States. Int. J. Theor. Phys. 57(6) (2018)
Zhou, N.R., Zhu, K.N., Zou, X.F.: Multi-Party Semi-Quantum Key Distribution Protocol With Four-Particle Cluster States. Annalen Der Physik. 531(8) (2019)
Zou, X.F., Qiu, D.W.: Three-Step semi-quantum secure direct communication protocol. Science China Phys. Mech Astron. 57(9), 1696-1702 (2014)
Li, Q., Chan, W.H., Long, D.Y.: Semi-quantum secret sharing using entangled states. Phys. Rev. A. 82(2), 2422-2427 (2010)
Lin, J., Yang, C.W., Tsai, C.W., Hwang, T.: Intercept-resend attacks on semi-quantum secret sharing and the improvements. Int. J. Theor. Phys. 52(1), 156-162 (2013)
Gao, G., Wang, Y., Wang, D.: Multiparty semiquantum secret sharing based on rearranging orders of qubits. Mod. Phys. Lett. B. 30, 10 (2016)
Nguyen, B.A.: Quantum dialogue. Phys. Rev. A. 328(1), 6-10 (2004)
Shi, G.F., Xi, X.Q., Hu, M.L., et al.: Quantum secure dialogue by using single photons. Opt. Commu. 283(9), 1984-1986 (2010)
Shen, D., Ma, W., Yin, X., et al.: Quantum Dialogue with Authentication Based on Bell States. Int. J. Theor. Phys. 52(6), 1825-1835 (2013)
Yin, A.H., Lin, W.B., Fan., P.: Controlled quantum dialogue scheme based on different unspecific two-particle entangled state. Mod. Phys. Lett. A. 35(2),175-179 (2019)
Lin, C.Y., Yang, C.W., Hwang, T.: Authenticated Quantum Dialogue Based on Bell States. Int. J. Theor. Phys. 54(3),780-786 (2015)
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A, 74(5) (2006)
Zheng, T., Zhang, S., Gao, X., et al.: Practical quantum private query based on Bell state. Mod. Phys. Lett. A. 74(24), 592 (2019)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85(26), 5635-8 (2000)
Tsai, C.W., Yang, C.W., Lee, N.Y.: Semi-quantum secret sharing protocol using w-state. Mod. Phys. Lett. A. 34(27), 1950213 (2019)
Hwang, T., Hwang, C.C., Li, C.M.: Multiparty quantum secret sharing based on GHZ states. Phys. Scr. 83, 045004 (2011)
Gao, G.: Multiparty quantum secret sharing using two-photon three-dimensional Bell states. Commun. Theor. Phys. 52, 421-4 (2009)
Liu, X.F., Pan, R.J.: Cryptanalysis of quantum secret sharing based on GHZ states. Phys. Scr. 84(4), 045015 (2011)
Xie, C., Li, L.Z., Qiu, D.W.: A Novel Semi-Quantum Secret Sharing Scheme of Specific Bits. Int. J. Theor. Phys. 54(10), 3819-3824 (2015)
Yin, A.H., Tong, Y.: A novel semi-quantum secret sharing scheme using entangled states. Mod. Phys. Lett. B. 32(22) (2018)
Acknowledgements
This work is supported by the National Natural Science Foundation of China under Grant No. 61762039.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Yin, A., Chen, T. Authenticated Semi-Quantum Secret Sharing Based on GHZ-Type States. Int J Theor Phys 60, 265–273 (2021). https://doi.org/10.1007/s10773-020-04688-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-020-04688-7