Abstract
Traditional and modern cryptosystems purely rely on mathematics and their algorithms based on fundamental process of factoring large integers into their primes, which is said to be intractable. But this type of cryptography vulnerable to both evolutions in mathematics and development of high computing power which can easily reverse one way functions. Now the requirement is to design a new mechanism whose reverse computation is not possible for any system. The robust security mechanism is necessary. The combination of quantum mechanism and cryptography make it possible to develop such a secure communication systems that utilized different energy spectra for the transmission of information. The combination of quantum mechanics and cryptography gives birth to quantum cryptography. Quantum cryptography is one of the most remarkable application of quantum information theory. To measure the quantum state of any system is not possible without disturbing that system. The facts of quantum mechanics on traditional cryptosystems leads to a new protocol, algorithms and achieving maximum security for systems. The aim of this article is to apply quantum spinning and rotation along with finite state machine to develop an efficient cryptosystems for text encryption and decryption.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In regular daily existence, there are numerous circumstances when it is important to hide the actual contents of secret information transmitted over an insecure line of communication. Many traditional cryptosystems were utilized to perform these tasks in order to encrypt the confidential information. However, in a near future all these classical cryptosystems merely computational secure. The existing classical cryptographic algorithms fundamentally rely on limited computationally development of computer power and mathematical structures. Traditional cryptography experiences key distribution issue, how to convey the key safely between two sets of clients. For quite a long time, it was trusted that the main plausibility to take care of the key dissemination issue was to send some physical medium. With the advancement of technologies, this criterion is obviously unconventional. Moreover, it is even impossible to validate the authentication, integrity and non-repudiation of the transmitted digital contents. Public key cryptography addressed this issue in a quite decent way, yet these algorithms are moderate and cannot be utilized to scramble a lot of information at the same time. Asymmetric key cryptography endures in light of the fact that despite the fact that restricted capacities have not been yet switched with innovative and mathematical advances it is conceivable. The development of quantum cryptography can truly debilitate their security. Previously, there has been a decent arrangement of another cryptographic strategy whose security depends on the principal laws of quantum information science and quantum cryptography. The principle accomplishment is that it can tackle the issue of key distribution. From the reasonable perspective, it is fascinating that quantum cryptography may properly be acknowledged by methods for quantum optics and the optical fiber fills in as a transmission channel [9, 10]. To encode data for instance polarization (disparity, division) or different phases can be utilized. The fundamental principle of quantum mechanism is that the light waves are comprised of a huge number of discrete quanta called photons which are mass less and have energy, momentum and angular momentum called spinning. The spinning of photon conveys the polarization. These photons are unified much like atoms, it simply that they are units of lights [8] .
Photon polarization describes how light photons can have polarized in specific directions. Photon filter with the correct polarization can only detect a polarized photon. The one way characteristics of photons along with the Heisenberg uncertainty principle make quantum cryptography an attractive option to ensure the privacy and defeating eavesdroppers [2]. Some particles, like electrons, neutrinos and quarks have half integer internal angular momentum also called spin . We develop a spinor representation in this paper for spin 1/2 to give a new direction to cryptography via spinning operators of quantum mechanics [1], [3]− [7]. We have shown here, not only the keys but the message can also be encrypted via this technique. The important aspect of our suggested algorithm is phase information, because phase is used to encrypt and decrypt the keys and message. To achieve maximum security, we use different phases for key and message. To decrypt the message, first we have to decrypt the keys by using phase information and then by using keys with phase information of message to decrypt the message.
The rest of the paper is organized as follow. We have added basic definition of finite state machine in Section 2. The derivation of rotation operator is given in Section 3. The proposed quantum spinning and rotations based algorithm illustrate with example and sensitivity analysis are given in Section 4. Finally, conclusion is given in Section 5.
2 Finite State Machine
Finite state automation (FSA) or finite state machines (FSM) are models of behaviors for a system or a complex object, with a limited number of defined modes or conditions, where mode transitions change in circumstances [7].
A DFA (deterministic finite automation) is quintuple M = (X, \(\sum ,~q_{0},\wp ,\digamma ),~\)where
- X :
-
is state of finite sets,
- \(\sum \) :
-
is input symbols of finite set,
- q 0 :
-
is start state indicated by an arrow \(\rightarrow ,\)
- ℘ :
-
is transition function \(\wp :X\times \sum \rightarrow X,\) i.e.,, ℘(q0,a) = qi ∈ X,
- \(\digamma \subset X\) :
-
is a finite set of final set of final states.
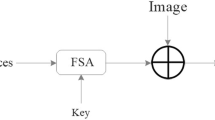
The input symbols can be letters or digits. We say that a string M is accepted by DFA (Deterministic Finite Automaton-self operating machine), if the set of languages accepted by a DFA ‘X’ is denoted by L(X). In DFA, there is only one transition out of each state on the same input symbol. NDFA (Nondeterministic Finite Automaton) can also be considered here as a mathematical model. In NDFA, we considered here a Moore machine and we use NDFA in our algorithm. In Moore machine, the output depends on the transitions (Fig. 1).
3 Derivation of Rotation Operators
The laws of physics not depend on what axis we choose for our coordinate system (rotational symmetry). If we make an infinitesimal rotation (through and angle dϕ) about ther −axis, we get the transformed coordinates [5],
Apply Taylor series on (1) to expand the function.
where his internal angular momentum. A finite rotation can be made by applying the operator for an infinitesimal rotation over and over. Let 𝜃r = ndϕ, then
If we make an infinitesimal rotation about the q −axis, we get the transformed coordinates
Apply Taylor series on (3) to expand the function given below
A finite rotation can be made by applying the operator for an infinitesimal rotation over and over. Let 𝜃q = ndϕ, then
If we make an infinitesimal rotation about the p −axis, we get the transformed coordinates
Apply Taylor series on (5) to expand the function.
A finite rotation can be made by applying the operator for an infinitesimal rotation over and over. Let 𝜃p = ndϕ, then
3.1 Derive Spin \(\frac {1}{2}~\)Operators
We use eigenstates of Sr as the basis states [6]
It must be diagonal, since the basis states are eigenvectors of the matrix. Now to perform the raising and lowering operators [6], we have
Now we can calculate Sp and Sq.
The Pauli spin matrices are defined as [4],
Compare (7)-(8) and (9) with (10) to get σ(Pauli matrices).
These are traceless Hermitian matrices, and HCode \(\sigma _{p}^{2}=\sigma _{q}^{2}=\sigma _{r}^{2}=I\) (identity) [1]. Now put (10) in (2), (4) and (6) to get rotation operators with respect to σ.
Now deriving the rotation operators of (11) with the help of (12) [6].
4 Proposed Algorithm
We have derived the rotation operators around p,q and r axis. By using the results, we encrypt the key and message by following algorithm. We ignore the imaginary numbers and used real axis for calculations.
Let entangle 2 × 2 matrices of (16) to form the set A of 4 × 4 entangle matrices. The elements of the set A are:
4.1 Encryption
-
1.
Define the phase for defined rotation matrices (known to sender and receiver only),
-
2.
Convert the message into numeric vector of order 4 × n, say M,
-
3.
Define finite state machine,
-
4.
Decide a key for secret communication,
-
5.
Convert they key into binary,
-
6.
Start with left most bit for encryption of message with rotation matrices and add one by one the key bits towards right and convert to decimal at each step and mod the key to 24. Round of encryption depends on key length,
-
7.
Convert the numeric matrix into alphabets at each step to get different ciphers,
-
8.
Finally, cipher alphabets received by using the full length of the key, say Mc.
4.2 Decryption
-
1.
Enter the phase where the message was encrypted,
-
2.
Convert alphabetical cipher message into numeric matrix of order 4 × n, say Mc,
-
3.
Enter the key for which the message encrypted and convert it into binary,
-
4.
Now start with full length key under mod 24 and operate the cipher with inverse rotation matrices and then subtract 1 by 1 bit from right side under mod 24 to operate with rotation matrices,
-
5.
The final numeric vector obtained by performing the inverse rotation matrix of left most bit with previous cipher,
-
6.
Convert the numeric matrix into alphabetical vector to get original message.
4.3 Example
Let us consider a message ‘INCOMPREHENSIBLE’ to be encrypted and decrypted at phase 𝜃 = 320∘ with key 59.
4.3.1 Finite State Machine
The mathematical expression of finite state machine which will be used in our proposed algorithm is given below
4.3.2 Encryption
The following components are basic requirement for the encryption of plain text ‘INCOMPREHENSIBLE’ (see Table 1).
We are now utilizing the fundamental components which are selected in Table 1, by transforming the plaintext into a ciphertext. A comprehensive procedure of our proposed encryption algorithm is given in Table 2.
4.3.3 Decryption
The decryption is an inverse process of encryption to transform the ciphertext into a plaintext. The fundamental steps in decryption of information in proposed algorithm are same but apply in a reverse way (see Tables 3 and 4).
4.4 Sensitivity Analysis
We have applied, our designed algorithm on different texts in which some texts shown in Table 5. By changing the phase, key or both lead to change the cipher. The beauty and versatility of designed algorithm is to change any term (either key or phase) lead to change the cipher and it is not possible to retrieve the plaintext exactly. The reverse process of this scheme by knowing the key is not possible because phase 𝜃 has infinite points.
5 Conclusion
The efficiency of designed algorithm test on texts, by changing the phase only 0.010 lead to change the cipher. Both parties can do secure data transmission with limited key space in very short time and can encrypt/ decrypt data character by character in defined range of phases. The above results of plain texts have different ciphers clarified that by changing either key or phase to get different results. We can create million of ciphers by changing phases of one original plain text. In this paper, the algorithm refers symmetric cryptography. The described algorithm refers to half spinning, so the points in between − 720∘to720∘ are infinite and possible combinations of rotation matrices are 24!. It is not possible for any machine to store infinite points in each of 24! matrices. All of these rotation matrices become the identity matrix for rotations through 720∘ and are minus the identity for rotations through 360∘. The purpose of using FSM is to enhance the security.
References
Wheeler, N.: Spin Matrices for Arbitrary Spin. Reed College Physics Department, Portland (2000)
Aditya, J., Shankar Rao, P.: Quantum cryptography, Proceedings of computer society of India (2005)
Man, P.P.: Wigner active and passive rotation matrices applied to NMR tensor. Concepts Magn. Reson. Part A 45A(1), 26 (2017)
Zwiebach, B.: Spin one-half, bras, kets and operators, MIT Physics Department (2013)
Drakos, N., Moore, R.: Quantum Physics, Derive the expression for rotation operator (1996)
Drakos, N., Moore, R.: Quantum Physics Spin 1/2 and Derive Spin 1/2 rotation matrices and operators (1996)
Kumar, R., Sekhar, C.: An ElGamal encryption scheme of Pauli spin 1/2 matrices and finite machines. International Journal of Mechatronics Electrical and Computer Technology 5(18), 2577–2584 (2015)
Rubya, T., Prema Latha, N., Sangeetha, B.: A survey on recent security trends using quantum cryptography. International Journal on Computer Science and Engineering 02(09), 3038–3042 (2010)
Buchmann, J., Braun, J., Demirel, D., Geihs, M.: Quantum cryptography: a view from classical cryptography. Quantum Sci Technol. 2, 1–4 (2017)
Lopes, M., Sarwade, N.: Cryptography from quantum mechanical viewpoint. International Journal on Cryptography and Information Security 4(2), 13–25 (2014)
Acknowledgments
One of the authors Dr. Majid Khan is highly thankful to Vice Chancellor Engineer Imran Rahman, Institute of Space Technology, Islamabad Pakistan, for providing a decent atmosphere for research and development.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Waseem, H.M., Khan, M. Information Confidentiality Using Quantum Spinning, Rotation and Finite State Machine. Int J Theor Phys 57, 3584–3594 (2018). https://doi.org/10.1007/s10773-018-3872-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-018-3872-6