Abstract
The restricted battery of the sensors has always been a bottleneck for the WSNs. To withstand the network life for a elongated period, the network can be partitioned into clusters. To boost the network routine, a three-level heterogeneous clustering procedure is proposed in this paper. The three levels of heterogeneity split the sensors into three diverse groups using their energies. The proposed protocol picks the most competent nodes as cluster head (CH) by utilizing the threshold and energy factors. The competent picking of CH helps in uplifting the performance of the whole network routine and improves the functioning of the network. The proposed scheme is simulated using the MATLAB simulator and the results are contrasted with the conventional approaches to illustrate the advantages of proposed protocol over other techniques.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
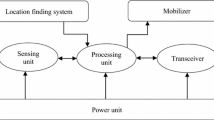
A WSN entails of a huge quantity of tiny, little power and cost, spatially distributed, communicating nodes (Ramar and Rubasoundar 2015; Tan and Körpeoǧlu 2003; Kumar and Rajkumar 2014; Ali et al. 2019; Marappan and Rodrigues 2016; Goyal and Tripathy 2012; Zytoune et al. 2010; Kia and Hassanzadeh 2019; Al-Karaki and Kamal 2004). These sensor nodes are connected wirelessly, self-organize themselves, and cooperate to perform application-oriented tasks (Priyadarshi et al. 2010, 2017, 2020; Rawat and Chauhan 2018a, b). Broadly, a WSN comprises of three subsystems, namely sensing, processing, and communication (Panag and Dhillon 2018; Hani and Ijjeh 2013; Singh et al. 2017; Aderohunmu and Deng 2009;Priyadarshi et al. 2018). In the sensing subsystem, sensor nodes acquire the data by sensing the physical constraints such as, pressure, temperature, and humidity, etc. Analog to Digital Converter (ADC) converts the sensed analog signal (data) into a digital signal and passes it to the processing subsystem. In addition to this, the sensing subsystem can perform the amplification and filtration depending upon the type of sensors and data acquisition strategy used (Zaki et al. 2014; Huang et al. 2018; Jana 2015; Osamy et al. 2018; Zhao et al. 2018; Azad and Sharma 2013). The processing subsystem processes the raw data into useful information. The communication subsystem sends the processed data to the high-end processing center, called Base Station (BS) (Priyadarshi and Gupta 2019; Priyadarshi et al. 2019; Kumar et al. 2020; Soni et al. 2020; Priyadarshi et al. 2019). The BS may be linked through end-user via wired connection or the Internet (Li and Li 2018; Darabkh et al. 2018; Muthukumaran et al. 2018; Hu et al. 2008; Singh and Sharma 2015; Dietrich et al. 2009). Depending upon the application requirements, nodes may or may not be equipped with mobilizer (for mobile network) and location finding systems like GPS (Geographic Positioning System), etc. The clustering strategy in WSN can be applied for boosting the network performance (Rawat et al. 2020; Priyadarshi and Bhardwaj 2020; Priyadarshi et al. 2018, 2019, 2020; Sharma et al. 2020). The nodes are prearranged into clusters, and a leader is assigned to each cluster called a cluster head (CH) (Goyal and Tripathy 2012; Rawat et al. 2020; Priyadarshi and Bhardwaj 2020; Priyadarshi et al. 2018, 2019, 2020; Sharma et al. 2020; Batra and Kant 2016; Mosavvar and Ghaffari 2019; Karray et al. 2014; Hadi 2019). The CH handles all the activities related to clustering, such as data collection and data forwarding (Priyadarshi et al. 2018a, b, 2019). The nodes in the network can be of analogous or disparate energy depending upon the application (Batra and Kant 2016; Singh and Verma 2017; Zhang and Chen 2019; Smaragdakis et al. 2004; Dhand and Tyagi 2016; Anurag et al. 2020).
In this paper, a three-level heterogeneous clustering scheme is proposed. The heterogeneous network provides disparate energy for various groups of nodes. The proposed protocol selects the CH from the different heterogeneous nodes using the parameters such as energy (average and residual), rounds, and CH probability. The proposed technique prolongs the network lifespan by selecting the most eligible node as CH using the threshold and other criteria of energy (Fig. 1).
2 Routing issues in WSN
The routing techniques in WSN facilitate in uplifting the network performance. The routing involves diverse issues that are required to be handled for performance enrichment (Ali et al. 2019). Some of the issues allied to routing in WSN are.
2.1 Resource constraints
Sensor nodes are battery functioned. Therefore, battery capacity is a critical resource of WSN. Further, sensor nodes are provided with restricted memory and processing abilities. These constraints impose many challenges to the protocol design of the WSN. Especially, routing algorithms should be energy efficient for the prolonged network lifetime.
2.2 Scalability
The network size and node density depends on the application’s requirements. Network performance should not be affected significantly with respect to change in node count and network size. Routing algorithms designed for WSN should be scalable.
2.3 Fault tolerance
In WSN, the rate of change of topology is very fast due to battery drainage, node failure due to environmental conditions, hardware failure, addition and deletion of the sensor nodes, etc. Fault tolerance means the ability of the network to function properly in the presence of faulty nodes. The fault tolerance level varies depending upon the application to be developed. Therefore, fault tolerance should be addressed during the protocol design.
2.4 Joint signal processing
Data sensed by the sensor nodes may have redundancy. Joint signal processing techniques like data aggregation or fusion, beam forming helps in reducing the data to be communicated to the BS. With this, energy is saved, and as well as data may be converted into meaningful information. Routing protocols using joint signal processing increase the network lifetime considerably.
2.5 Security
For some applications like enemy tracking, security surveillance, a secure connection is a significant concern. In these applications, sensor nodes may be physically damaged, or some malicious node may be placed for getting unauthorized access of data. Because of resource constraints, existing security techniques create overhead and hamper the performance of the network. Therefore, routing protocols should be secure, lightweight, and energy-efficient.
2.6 Localization and coverage
Certain applications involve sensor nodes to be installed in hostile and unattended environments. For the reliable delivery of the data to the BS, nodes should be connected and accurately localized by the GPS (Geographic Positioning System) system or by some location finding methods. Several routing techniques presume that nodes are furnished with a GPS devices or certain location finding technique.
2.7 QoS
The interpretation of QoS for WSNs is highly application dependent. QoS requirements can be seen from two perspectives: application-specific and network specific. Application specific QoS parameters are observation accuracy, coverage, number of alive nodes, and exposure. Network-specific QoS parameters depend upon the data delivery models, i.e., query-driven, event-driven, or continuous delivery models. QoS support in WSN faces many challenges, such as resource constraints, redundant data, heterogeneity, scalability, etc. Since QoS support is a critical parameter for WSNs, therefore, protocol design should also consider QoS control and assurance mechanisms (Fig. 2).
3 Related work
In Gnanambigai et al. (2013), the sensing area is divided into the quadrants to perform the clustering. The clusters are created in the four quadrants, and the CH of assorted clusters corresponds using the request packets transfer. This approach results in increased delays and congestion. The change of the CH role is not performed in each round. The CH is changed only when the CH energy falls below a definite level. The partition of the quadrant is performed using the node location by the nodes.
In Heinzelman et al. (2000), the clustering strategy in this approach is portioned into two stages. The nodes are alienated into clusters, and a cluster head (CH) is nominated in each cluster in the first stage. This phase is called a setup stage. The CH collects node information from cluster and aggregates the gathered information for transmitting it to BS. In the next stage, i.e., the steady stage, the information gathered by the CH is transferred to the base station (BS). The node energy is not exploited in this approach during the CH selection and uses the random selection policy for the clustering process, which makes it less efficient in terms of energy utilization.
In Smaragdakis et al. (2004), the author proposed a heterogeneous clustering approach for electing the CH. The nodes are separated into categories on the basis of their energies. The additional energy is provided to some nodes in the network. The extra energy nodes help in increasing the life of the network. This approach uses the probability model for nominating the CH. The methodology engaged in this approach does not deliberate the energy of nodes for executing the clustering phases, which fallouts in a reduced network lifespan.
In Qing et al. (2006), the CH determination is performed using the energies (average and initial) of the nodes for the enhancement of network performance. This approach uses the heterogeneous network having different types of nodes with dissimilar energies. The CH selection process used in this protocol uses probability and node energy. The nodes in this approach produce redundant data while sensing the environment, which wastes the network energy. The CH selected using the probability method acts as an aggregator and aggregates the gathered data to reduce the redundant data.
In Salim et al. (2014), the protocol works on energy gap reduction amongst CH and cluster nodes. The tasks related to the network are scattered amid all the nodes and CH. The uniform distribution of energy among the sensors increases network performance. The scalability and message overhead makes this protocol less efficient.
In Lei et al. (2008), the CH selects the other CH as relays to communicate the data. The criteria for relay selection are BS distance and energy. This approach works better for the large sensing area. The relays help in uniform distribution of energy as the choosing criteria for relays are energy and distance.
For solving the intracluster communiqué in large networks, the concept of the far zone was introduced in Katiyar et al. (2011). The role of the zone leader is assigned to higher energy sensors. It works on solving the problem of uneven cluster size. It faces the issues of scalability and complexity while performing network actions.
4 Energy model of WSN
The energy model used for the proposed approach is used for the communication of data, i.e., transmission and reception. The model is alienated into two portions one for data sending and others for data reception. Both the data sender and data receiver parts are parted from each other by a distance d (Priyadarshi et al. 2019; Smaragdakis et al. 2004; Katiyar et al. 2011). The equations for the transmission and reception of data re given as:
Table 1 displays the symbols employed in the energy model of proposed protocol along with the meaning of various symbols (Fig. 3).
5 Proposed protocol
The clustering approach in WSN has a substantial effect on extending the network lifespan. The nodes in clustering are alienated into diverse groups, which make it competent for the congregation and broadcast of data. The sensors in clusters sense the information in the working area and frontward that information to the CH. The CH transport that gathered records to the BS. The CH determination in the proposed approach has an extremely necessary part in defining the network performance. In this paper, a clustering methodology grounded on three-level heterogeneity is proposed. The sensors in the proposed protocol are classified into three diverse node sets (normal, middle, and super) using their energies. The CH determination in the proposed protocol is reliant on the three-level heterogeneity model and energy of heterogeneous nodes. The clustering procedure in the proposed technique begins with the generation of random number in the range [0, 1]. The random value is matched with the threshold for the CH determination. The nodes which fulfill the threshold norms get the CH role. The threshold is used for all the levels of heterogeneity for the CH determination. The three levels in the proposed approach compose the network efficiency and facilitate the network in surviving for a longer time duration. Figure 4 shows the steps followed by the proposed scheme.
The basic threshold for the proposed scheme is given as (Tables 2, 3):
The extra energy due to the heterogeneous nodes uplifts the entire network energy. The proposed approach considers the energy of nodes for the CH determination. The threshold function used in the proposed method considers the round number, node energy, and CH determination probability for choosing the CH amid a variety of nodes.
The CH determination probability of a mixture of heterogeneous nodes (middle, super, and normal) is given as (Table 4):
The energy of the super node is superior to the middle and normal nodes. Due to the heterogeneous character of the nodes, the primary energy assigned to the nodes is different.
\( E_{sup} ,E_{mid} ,\;and\;E_{norma} \) are energies of super, middle, and normal nodes. The first step in the clustering segment of the proposed protocol begins with the production of a random value. The assessment of that value is performed with the threshold.
The threshold for the three-level heterogeneous nodes is represented as (Table 5):
The threshold function (normal node) is calculated as:
The threshold function (middle node) is calculated as:
The threshold function (super node) is calculated as:
If the threshold criteria are not satisfied by a node in a round, at that point, the subsequent node is given the opportunity, and a similar course of action is rehashed yet again for the next node.

6 Simulation and results
The assessment of existing approaches is performed with the proposed protocol for analyzing the working performance in terms of various performance parameters (network life, stability period, and CH count). The proposed approach is simulated using the MATLAB simulator. The parameters used for the simulation of the proposed protocol are shown in Table 6.
In Fig. 5, the survival of the nodes is shown in different rounds. The energy in the network is depleted in performing diverse network activities. The proposed approach utilizes the energy levels of nodes and CH probability in the clustering phases to help the network in sustaining for the higher rounds. The network survived for 3073, 3134, 3475, 5743 rounds in LEACH, SEP, DEEC, and proposed protocol. The graph can be analyzed to showcase the efficacy of the proposed protocol for improving the network life.
Figure 6 shows the nodes (dead) in different rounds to showcase the stability of the network. The proposed protocol has taken advantage of the node energy and CH probability to lift the stability region of the network. The stability region is maintained for 1037, 1278, 1820, and 2746 rounds in LEACH, SEP, DEEC, and proposed protocol. The results demonstrates the competence of the proposed protocol in making the network more stable and efficient.
Figure 7 shows the investigation of the CH formed in different rounds. The CH generated in proposed schemes is higher in comparison to other existing approaches. The CH selection using the energy parameters makes the CH count uniform in the network. The nodes are given equal opportunity for the CH competition, and each node can exploit their energy and probability values of winning the CH election.
Figure 8 showcases the performance of the different protocols in comparison to the proposed approach. The node’s status in different rounds is examined in the figure. The round number in which first, half, and last node (fnd, hnd, and lnd) loss all their energy and become dead are shown for different protocols. The proposed technique has delineated better results in each round, and it showcases the efficacy by improving network performance.
7 Conclusion
The proposed protocol is designed for performing the clustering in the three-level heterogeneity model. The nodes in this paper are categorized into three types according to their energy levels. The different energies of nodes assist in augmenting the lifespan of the network. The nodes of all the types are given the chance for becoming the CH. The proposed protocol primarily focuses on the efficient CH selection for escalating the system performance. It uses the probability dependent thresholds and energy of sensors for the competent CH determination. The three-level heterogeneity model applied for the clustering assists the network to stay alive for a longer extent, which improves the inclusive performance of the network.
References
Aderohunmu F, Deng J (2009) An enhanced stable election protocol (SEP) for clustered heterogeneous WSN
Ali SM, Sattar SA, Khan NSA, Rao DS (2019) Wireless sensor networks routing design issues: a survey. Int J Comput Appl 975:8887
Al-Karaki JN, Kamal AE (2004) Routing techniques in wireless sensor networks: a survey. IEEE Wirel Commun 11(6):6–28. https://doi.org/10.1109/MWC.2004.1368893
Anurag A, Priyadarshi R, Goel A, Gupta B (2020) 2-D coverage optimization in wsn using a novel variant of particle swarm optimisation. In: 2020 7th international conference on signal processing and integrated networks (SPIN), pp 663–668. https://doi.org/10.1109/spin48934.2020.9070978
Azad P, Sharma V (2013) Cluster head selection in wireless sensor networks under fuzzy environment. ISRN Sens Netw 2013:1–8. https://doi.org/10.1155/2013/909086
Batra PK, Kant K (2016) LEACH-MAC: a new cluster head selection algorithm for Wireless Sensor Networks. Wirel Netw 22(1):49–60. https://doi.org/10.1007/s11276-015-0951-y
Darabkh KA, Al-Rawashdeh WS, Hawa M (2018) MT-CHR: a modified threshold-based cluster head replacement protocol for wireless sensor networks R. Comput Electr Eng 72:926–938. https://doi.org/10.1016/j.compeleceng.2018.01.032
Dhand G, Tyagi SS (2016) Data aggregation techniques in WSN: survey. Procedia Comput Sci 92:378–384. https://doi.org/10.1016/J.PROCS.2016.07.393
Dietrich I, Dressler F, Dietrich I, Dressler F (2009) On the lifetime of wireless sensor networks. ACM Trans Sens Netw ACM Trans Sens Netw 5(1):1–39. https://doi.org/10.1145/1464420.1464425
Gnanambigai J, Rengarajan N, Anbukkarasi K (2013) Q-leach: an energy efficient cluster based routing protocol for Wireless Sensor Networks. In: 7th International conference on intelligent systems and control, ISCO 2013, pp 359–362. https://doi.org/10.1109/isco.2013.6481179
Goyal D, Tripathy MR (2012) Routing protocols in wireless sensor networks: a survey. In: 2012 Second international conference on advanced computing and communication technologies, pp 474–480. https://doi.org/10.1109/acct.2012.98
Hadi K (2019) Analysis of exploiting geographic routing for data aggregation in wireless sensor networks. Procedia Comput Sci 151:439–446. https://doi.org/10.1016/j.procs.2019.04.060
Hani RMB, Ijjeh AA (2013) A survey on LEACH-based energy aware protocols for wireless sensor networks. J Commun. https://doi.org/10.12720/jcm.8.3.192-206
Heinzelman WR, Chandrakasan A, Balakrishnan H (2000) Energy-efficient communication protocol for wireless microsensor networks. In: Proceedings of the 33rd annual Hawaii international conference on system sciences, pp 10. IEEE
Hu J, Jin Y, Dou L (2008) A time-based cluster-head selection algorithm for LEACH. In: 2008 IEEE symposium on computers and communications, pp 1172–1176. https://doi.org/10.1109/iscc.2008.4625714
Huang J, Ruan D, Meng W (2018) An annulus sector grid aided energy-efficient multi-hop routing protocol for wireless sensor networks. Comput Netw 147:38–48. https://doi.org/10.1016/J.COMNET.2018.09.024
Jana APK (2015) A distributed algorithm for energy efficient and fault tolerant routing in wireless sensor networks. Wirel Netw 21(1):251–267. https://doi.org/10.1007/s11276-014-0782-2
Karray F, Jmal MW, Abid M, Bensaleh MS, Obeid AM (2014) A review on wireless sensor node architectures. In: 2014 9th international symposium on reconfigurable and communication-centric systems-on-chip. https://doi.org/10.1109/recosoc.2014.6861346
Katiyar V, Chand N, Gautam GC, Kumar A (2011) Improvement in LEACH protocol for large-scale wireless sensor networks. In: 2011 international conference on emerging trends in electrical and computer technology, ICETECT 2011, pp 1070–1075. https://doi.org/10.1109/icetect.2011.5760277
Kia G, Hassanzadeh A (2019) A multi-threshold long life time protocol with consistent performance for wireless sensor networks q. AEUE Int J Electron Commun 101:114–127. https://doi.org/10.1016/j.aeue.2019.01.034
Kumar SM, Rajkumar N (2014) SCT based adaptive data aggregation for wireless sensor networks. Wirel Pers Commun 75(4):2121–2133. https://doi.org/10.1007/s11277-013-1457-5
Kumar S, Soni SK, Priyadarshi R (2020) Performance analysis of novel energy aware routing in wireless sensor network. In: International conference on nanoelectronics, circuits and communication systems, pp 503–511
Lei Y, Shang FJ, Long Z, Ren Y (2008) An energy efficient multiple-hop routing protocol for wireless sensor networks. In: Proceedings—the 1st international conference on intelligent networks and intelligent systems, ICINIS 2008, pp 147–150. https://doi.org/10.1109/icinis.2008.69
Li L, Li D (2018) An energy-balanced routing protocol for a wireless sensor network. J Sens
Marappan P, Rodrigues P (2016) An energy efficient routing protocol for correlated data using CL-LEACH in WSN. Wirel Netw 22(4):1415–1423. https://doi.org/10.1007/s11276-015-1063-4
Mosavvar I, Ghaffari A (2019) Data aggregation in wireless sensor networks using firefly algorithm. Wirel Pers Commun 104(1):307–324. https://doi.org/10.1007/s11277-018-6021-x
Muthukumaran K, Chitra K, Selvakumar C (2018) An energy efficient clustering scheme using multilevel routing for wireless sensor network R. Comput Electr Eng 69:642–652. https://doi.org/10.1016/j.compeleceng.2017.10.007
Osamy W, Salim A, Khedr AM, Salim A (2018) An information entropy based-clustering algorithm for heterogeneous wireless sensor networks. Wirel Netw. https://doi.org/10.1007/s11276-018-1877-y
Panag TS, Dhillon JS (2018) Dual head static clustering algorithm for wireless sensor networks. AEU Int J Electron Commun 88:148–156. https://doi.org/10.1016/j.aeue.2018.03.019
Priyadarshi R, Bhardwaj A (2020) Node non-uniformity for energy effectual coordination in WSN. Accessed 22 Apr 2020. https://ijits-bg.com/contents/IJITS-No4-2017/2017-N4-01.pdf
Priyadarshi R, Gupta B (2019) Coverage area enhancement in wireless sensor network. Microsyst Technol. https://doi.org/10.1007/s00542-019-04674-y
Priyadarshi R, Gupta B, Anurag A (2010) Wireless sensor networks deployment: a result oriented analysis. Wirel Pers Commun. https://doi.org/10.1007/s11277-020-07255-9
Priyadarshi R, Tripathi H, Bhardwaj A, Thakur A, Thakur A (2017) Performance metric analysis of modified LEACH routing protocol in wireless sensor network. pdfs.semanticscholar.org. Accessed 22 Apr 2020. https://pdfs.semanticscholar.org/efaa/5ad2cd828d8eddeee06c704525e87c204a85.pdf
Priyadarshi R, Rawat P, Nath V (2019a) Energy dependent cluster formation in heterogeneous wireless sensor network. Microsyst Technol 25(6):2313–2321. https://doi.org/10.1007/s00542-018-4116-7
Priyadarshi R, Singh L, Singh A (2018) 5th international, and undefined 2018, A novel HEED protocol for wireless sensor networks. ieeexplore.ieee.org, Accessed 22 Apr 2020. https://ieeexplore.ieee.org/abstract/document/8474286/
Priyadarshi R, Singh L, Singh A, Thakur A (2018) SEEN: stable energy efficient network for wireless sensor network. ieeexplore.ieee.org. Accessed 22 Apr 2020. https://ieeexplore.ieee.org/abstract/document/8474228/
Priyadarshi R, Soni SK, Nath V (2018c) Energy efficient cluster head formation in wireless sensor network. Microsyst Technol 24(12):4775–4784. https://doi.org/10.1007/s00542-018-3873-7
Priyadarshi R, Yadav S, Bilyan D (2019) Performance analysis of adapted selection based protocol over LEACH protocol. In: Smart computational strategies: theoretical and practical aspects. Springer, Singapore, pp 247–256
Priyadarshi R, Yadav S, Bilyan D (2019) Performance and comparison analysis of MIEEP routing protocol over adapted LEACH protocol. In: Smart computational strategies: theoretical and practical aspects. Springer, Singapore, pp 237–245
Priyadarshi R, Soni SK, Sharma P (2019d) An enhanced GEAR protocol for wireless sensor networks. Lecture Notes Electr Eng 511:289–297. https://doi.org/10.1007/978-981-13-0776-8_27
Priyadarshi R, Singh L, Kumar S, Sharma I (2020) A hexagonal network division approach for reducing energy hole issue in WSN. Accessed 22 Apr 2020. http://www.ijpam.eu
Priyadarshi R, Gupta B, Anurag A (2020b) Deployment techniques in wireless sensor networks: a survey, classification, challenges, and future research issues. J Supercomput. https://doi.org/10.1007/s11227-020-03166-5
Qing L, Zhu Q, Wang M (2006) Design of a distributed energy-efficient clustering algorithm for heterogeneous wireless sensor networks. Comput Commun 29(12):2230–2237. https://doi.org/10.1016/j.comcom.2006.02.017
Ramar C, Rubasoundar K (2015) A survey on data aggregation techniques in wireless sensor networks. Int J Mob Netw Des Innov 6(2):81. https://doi.org/10.1504/IJMNDI.2015.072843
Rawat P, Chauhan S (2018a) Performance analysis of RN-LEACH protocol over LEACH protocol 1. Int J Futur Gener Commun Netw 11(5):1–10. https://doi.org/10.14257/ijfgcn.2018.11.5.01
Rawat P, Chauhan S (2018) Energy efficient clustering in heterogeneous environment. In: Proceedings of the international conference on inventive communication and computational technologies, ICICCT 2018, pp 388–392. https://doi.org/10.1109/icicct.2018.8473296
Rawat P, Chauhan S, Priyadarshi R (2020) Energy-efficient clusterhead selection scheme in heterogeneous wireless sensor network. J Circuits Syst Comput. https://doi.org/10.1142/s0218126620502047
Salim A, Osamy W, Khedr AM (2014) IBLEACH: intra-balanced LEACH protocol for wireless sensor networks. Wirel Netw 20(6):1515–1525. https://doi.org/10.1007/s11276-014-0691-4
Sharma I, Kumar S, Priyadarshi R, Singh L (2020) Energy efficient leach routing in wireless sensor network. Accessed 22 Apr 2020. https://www.researchgate.net/publication/323995198
Singh SP, Sharma SC (2015) A survey on cluster based routing protocols in wireless sensor networks. Procedia Comput Sci 45:687–695. https://doi.org/10.1016/J.PROCS.2015.03.133
Singh R, Verma AK (2017) Energy efficient cross layer based adaptive threshold routing protocol for WSN. AEU Int J Electron Commun 72:166–173. https://doi.org/10.1016/J.AEUE.2016.12.001
Singh S, Malik A, Kumar R (2017) Energy efficient heterogeneous DEEC protocol for enhancing lifetime in WSNs. Eng Sci Technol an Int J 20(1):345–353. https://doi.org/10.1016/J.JESTCH.2016.08.009
Smaragdakis G, Matta I, Bestavros A (2004) SEP: a stable election protocol for clustered heterogeneous wireless sensor networks. In: Second international workshop on sensor and actor network protocols and applications (SANPA 2004), pp 1–11. https://doi.org/10.3923/jmcomm.2010.38.42
Smaragdakis G, Matta I, Bestavros A (2004) SEP: a stable election protocol for clustered heterogeneous wireless sensor networks
SK Soni, S Kumar, R Priyadarshi (2020) Energy-aware clustering in wireless sensor networks. In: International conference on nanoelectronics, circuits and communication systems, pp 453–461
Tan HÖ, Körpeoǧlu I (2003) Power efficient data gathering and aggregation in wireless sensor networks. ACM SIGMOD Rec 32(4):66. https://doi.org/10.1145/959060.959072
Zaki FW, Rizk R, Farouk F (2014) Multi-level stable and energy-efficient clustering protocol in heterogeneous wireless sensor networks. IET Wirel Sens Syst 4(4):159–169. https://doi.org/10.1049/iet-wss.2014.0051
Zhang J, Chen J (2019) An adaptive clustering algorithm for dynamic heterogeneous wireless sensor networks. Wirel Netw 25(1):455–470. https://doi.org/10.1007/s11276-017-1648-1
Zhao Z, Xu K, Hui G, Hu L (2018) An energy-efficient clustering routing protocol for wireless sensor networks based on AGNES with balanced energy consumption optimization. Sensors. https://doi.org/10.3390/s18113938
Zytoune O, Fakhri Y, Aboutajdine D (2010) Lifetime maximisation algorithm in wireless sensor network. Int J Ad Hoc Ubiquitous Comput 6(3):140. https://doi.org/10.1504/IJAHUC.2010.034967
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Priyadarshi, R., Rawat, P., Nath, V. et al. Three level heterogeneous clustering protocol for wireless sensor network. Microsyst Technol 26, 3855–3864 (2020). https://doi.org/10.1007/s00542-020-04874-x
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00542-020-04874-x