Abstract
The optimal usage of scarce and inadequate resources is the current need of wireless sensor networks (WSNs). Reducing power consumption and increasing WSN’s lifetime can contribute to this. Energy-efficient algorithms should be proposed for effective routing, as a lot of energy is consumed during the communication between sensor nodes. A principal practice followed to bring down energy consumption is, combining together in-network data aggregation and standardized routing. Numerous conventional data aggregation algorithms exist, and each of these have their own disadvantages like delayed delivery of packets, time constraints, or high costs. The most suitable solution can therefore be achieved via optimization alone. The current research seeks to address these challenges faced in the wireless network by using the dual-cluster heads technique based on Krill Herd Optimisation (DC-KHO) Routing algorithm. Since the existing wireless routing approaches choose a random path for data transmission, the end- to- end delay, which is directly proportional to energy consumption, is high. So, the current study chooses an optimized path by calculating its path trust value using the devised krill herd maximization algorithm. The proposed DC-KHO algorithm is energy- efficient, and invariably amplifies the network’s lifetime. The study’s results reveal the ability of the proposed method in overcoming the challenges faced in transmission time, residual energy and computational time. Further, the method increases the life span of the network by 64.58%, when a 9 V battery is used for the nodes.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Wireless sensor networks (WSNs) are a thriving area for innovation and development, owing to the massive growth in embedded systems and wireless communications (Zhou et al. 2011; Kumar et al. 2009). A WSN has a sensing field, which comprises of some base-stations and a fixed set of sensor nodes. Hop-by-hop communication is employed for assembling data from the network, and delivering it to the corresponding base station. Some of the issues faced by the wireless sensor networks are a dynamic topology, bandwidth limitation, routing, power consumption and synchronization (Liu et al. 2007; Kandris et al. 2009).
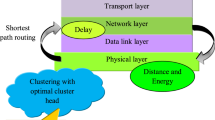
Major portion of the total energy is consumed during the communication of data between the nodes of the WSNs. The frequency of data transfer between the nodes can be reduced by in-network data aggregation and clustering (Khan et al. 2012). The application’s requirements, and its relative energy usage, determine the data aggregation method to be chose (Xiang and Luo 2011; Al-karaki et al. 2009). The progress of the aggregation of data carried out by the data aggregators and cluster heads is depicted in Fig. 1.
Clustering is an effective energy conservation technique in WSNs. Sensor nodes are grouped into clusters, and cluster heads (CHs) are elected for each of these clusters (Feng et al. 2010). The CHs are responsible for the distribution and efficient allocation of tasks among the cluster members.
After clustering, a routing algorithm which can lower the rate of consumption of energy, and increase the life span of networks should be chosen (Behera et al. 2019). Several routing algorithms have been designed. However, each of these have their own set of disadvantages, and hence do not provide an ideal solution for the problem.
Therefore, optimization of the solutions derived so far is required (Xiong et al. 2010; Karaboga and Basturk 2008). In the recent years, optimization techniques inspired by natural phenomena have opened up new ways to solve clustering issues (Ari et al. 2017). One such is the Krill herd algorithm.
The current study proposes a dual-cluster heads formation technique based on Krill Herd Optimisation (DC-KHO) Routing algorithm to facilitate the efficient utilization of network energy.
As even minimal distance between the sink holes highly increases energy consumption, the Krill Herd Optimisation algorithm selects primary and secondary clusters. This clustering is based on the cluster size, and the distance between nodes and sink nodes. This kind of hierarchical mechanism avoids the re-selection of the cluster head nodes that have been previously selected. It also balances the amount of energy consumed by the network.
The KH optimization thus provides a solution to the problem of cluster head nodes under heavy load. This, in turn, extends the survival time of the cluster nodes.
The outline of the construction of this paper is given as follows: Sect. 2 summarizes the related work. Section 3 gives information about problem formulation. Section 4 explains the proposed algorithm. Section 5 displays the experimental outcomes and analyses, and Sect. 6 concludes the paper.
2 Related work
Tang et al. proposed an energy efficient MAC protocol called PW-MAC (Predictive-Wakeup MAC) for WSNs (Johnson 2011). This protocol enables senders to forecast receiver wakeup times so as to lower energy consumption. However, in real time applications, it faces a lot of challenges like unpredictable hardware, operating system and clock drift.
Ben-Othman and Yahya developed an Energy Efficient and QoS based multiparty routing protocol (Comput et al. 2010). It was successful in extending the lifetime of the network, and in minimizing the delay of sensitive traffic in reaching the sink node.
Dong et al. proposed an approach called Reliability and Multi Encounter Routing (RMER) (Dong et al. 2016). This new event data approach for aggregation, is used for building reliability and meeting energy efficiency. By sending data to the sink node, this approach converges the multiple paths of event monitoring nodes. As a result, the network life span is increased, and the energy consumption is greatly reduced. The results showed that RMER increased the energy efficiency by 51% and the network lifetime by 23%.
Villas et al. proposed a new approach called DRINA, which stands for Data Routing for In-network Aggregation (Villas et al. 2013). This algorithm was found to be more scalable. It incurred lesser communication costs, and was efficient in delivery when compared to the well-known routing protocols- InFRA and SPT.
Kuila and Jana proposed two algorithms for efficiently using energy for clustering and routing in WSNs (Kuila and Jana 2014). These include PSO based routing and clustering algorithms. The former reduced the transmission distance and cluster heads, while the latter balanced the energy consumption of the cluster heads. The results showed the superiority of these algorithms over the existing algorithms.
Thein and Thein proposed an energy efficient optimal cluster-head selection algorithm for distributing the load among all other nodes (Energy et al. 2010). The experimental results showed that the proposed protocol brought down energy consumption, achieved higher efficiency, and effectively prolonged the network’s life time.
Guo et al. proposed a hybrid metaheuristic approach called HS/FA by hybridizing harmony search (HS) and firefly algorithms (FA) (Wang and Guo 2013). It was intended to solve function optimization issues. The experimental results revealed HS/FA to be better than nine different optimization methods, including the standard FA.
Shengchao Su, Shuguang Zhao proposed a hierarchical hybrid approach using genetic and PSO algorithm for distributed clustering in large scale WSNs (Su and Zhao 2017). Two levels of clusters are being formed and GA is used for lower level clusters and PSO is used for upper level clustering which provides faster convergence. The results show that proposed approach effectively reduces energy consumption hence increases network lifetime.
Jyoti et al. proposed genetic algorithm based optimized leach protocol for energy efficient WSNs (Bhola et al. 2019). Cluster heads are formed by using hierarchical leach protocol and GA is used to find the optimal route by using fitness function. Result shows that proposed LEACH-GA reduces energy consumption rate by 17.39%.
Vishal Kumar et al. proposed an Ant Colony Optimization (ACO) based self-organized energy efficient algorithm for WSNs (Arora 2019). Cluster heads are selected by maximal residual energy then members join with the cluster head. Multiple paths are being created between cluster head and members using ACO algorithm. Then a dynamic energy efficient optimized route is selected. Results show that proposed approach prolongs network lifetime.
3 Problem formulation
In the clustering and routing algorithm in WSNs, data from each cluster is forwarded to their respective cluster head nodes. The cluster head, which acts both as an aggregator and backbone router, consumes high amounts of energy than the other nodes in the cluster. This is because data is sent to the sink node via single or multiple hops. This undesirable amount of energy consumption leads to a lack of balance in the network energy. If the data is routed on the worst path, the energy consumption will be further increased. To fix this issue, and to productively lower the energy used by the cluster heads, a dual-cluster based Krill Herd Optimization algorithm is proposed.
4 Proposed duel cluster technique based on Krill Herd Optimization (DC-KHO) algorithm
Routing protocols which are employed in wired networks differ from those used in wireless networks. The conventionally used wireless network routing protocols are proactive routing, on-demand routing, hybrid routing, etc. In order to cope up with energy constrained environment and to reduce unbalanced energy consumption, this paper puts forth an optimization technique and an algorithm for wireless sensor network routing.
The WSN comprises of randomly deployed nodes.
In the proposed optimized routing, initially the deployed nodes in the network \( X \) are clustered using the initial centroid algorithm. The primary centroids (aka initial centroids) aggregate the sensed data, and the secondary centroids provide details of the Path trust value for each path. Kill Herd Optimization enables figuring out the optimized trust esteem. Now, the aggregated data is then moved ahead through the established optimized path. The square outline of the proposed trust-based Krill optimized data aggregation is given in Fig. 2.
4.1 Initial centroids through pillar k means algorithm
The method of grouping the sensor nodes \( \left( X \right), \) is one of the critical strategies for extending the lifespan of the system in wireless sensor networks (WSNs). Grouping of nodes into clusters, and the election of cluster heads (CHs) for each cluster are performed. A noteworthy test in WSNs is the selection of appropriate cluster heads.
Cluster-related network communication structures permit more effective usage of resources. A cluster related structure assists in making the network topology more efficient. This in turn eliminates unnecessary communications.
A cluster is generally created with one principal cluster head. The nodes connected to the head are controlled by the cluster head. In the proposed methodology, the number of nodes in the network \( X \) are initially clustered using the pillar K-means algorithm.
This system applies K-means clustering after optimization by pillar algorithm. The pillar algorithm has been very powerful in positioning the initial centroids. It ensures that the placement of the underlying centroids are as far as possible from each other. The initial centroids in the clusters are known as primary cluster heads. These are used for data aggregation within cluster. The node which has the highest residual energy within the cluster will be elected as secondary cluster head. The secondary cluster head will serve as the virtual backbone for optimizing routing.
4.1.1 Pillar k means algorithm
Let \( S^{\prime} = \left\{ {s_{1} , s_{2} ,s_{3} , \ldots s_{n} } \right\} \) be the sensor nodes, k be the number of clusters, \( C = \left\{ {c_{1} , c_{2} ,c_{3} , \ldots c_{k} } \right\} \) be the initial centroids, \( SS^{\prime} \subseteq S^{\prime} \) be the recognition for \( S^{\prime} \) which have been already chosen in the series of process, \( MD = \left\{ {s_{1} , s_{2} ,s_{3} , \ldots s_{n} } \right\} \) be the gathered distance metric, \( M = \left\{ {s_{1} , s_{2} ,s_{3} , \ldots s_{n} } \right\} \) be the distance metric for every iteration, and m be the mean of \( S' \).The pseudo code of pillar k means is given in Algorithm 1.

In the proposed methodology, the number of nodes in the network \( \left( X \right) \) are initially clustered using the pillar K-means algorithm. The algorithm allows the positioning of the centroids far away on the distribution, and this results in efficient clustering. After the formation of clusters, the initial centroids, which act as both aggregators and routers, are allowed to act only as aggregators. This is because, if those act with their dual purpose, they cause the premature death of the nodes. Now, the node with the highest residual energy within each cluster is elected for the calculation of trusted path.
4.1.2 Data aggregation
Data aggregation is an important procedure in WSN. It eradicates the redundancy of gathered data to minimize communication costs, and to save energy. In the proposed DC-KHO, the primary cluster heads (aka initial centroids) perform the aggregator role. That is, they aggregate the data obtained from their cluster members, and then transfer the data to the next level cluster head in the hierarchical clustering architecture.
4.2 Trusted path calculation
Trust gives an idea of the level of dependability of the previous node in performing a particular action. It is signified as the assurance level of a node in getting the assigned task accomplished in a given duration of time. This information is provided by one node about another node. It is evaluated by maintaining a track of its past transactions or connections with the nodes. In the proposed method, the trusted path is evaluated by Eq. (1).
where, \( T_{p} \) is the path trust, is the intensity of discrete trust, and \( Z_{i} \) is calculated by the Eq. (2).
where, \( Z_{i} \) is the trust of every node and \( \alpha_{t} \) is computed by the Eq. (3)
Here, t is the data transmission time between cluster heads.
4.2.1 Path optimization utilizing Krill Herd Optimization Algorithm
Krill herd (KH) has been an innovative meta-heuristic swarm intelligence optimization technique for rectifying optimization issues. After obtaining the trust value of each path available, path optimization is implemented through Krill Herd Optimization (KHO) algorithm. This helps acquire the pre-eminence path to routing in the WSN. By using the KH algorithm, the pseudo code in path optimization is obtained.
The algorithm commences with the population (\( T_{p} \)) initialization. Fitness value is assayed for every krill individual on the basis of the computed path trust (\( T_{p} \)). This is iterated to order the krill individuals from the finest to the worst. After this, motion updating (foraging, random diffusion, induced movement) is calculated for each krill individual.

4.2.1.1 Foraging motion update
The foraging update is executed by,
where, \( V_{f} \) is the foraging speed, \( \omega_{f} \) is the inertia weight, \( \beta_{x}^{best} \) is the most accurate demonstration of the \( x^{th} \) krill individual so far.
4.2.1.2 Induced movement update
Induced movement is the motion induced by other krill individuals. It is presented by:
In which, \( M_{\text{max} } \) is the optimum induced speed, \( \omega_{n} \) is the inertia weight, \( \alpha_{x}^{total} \) is the local impact the \( x^{th} \) krill individual hold on its neighbours, and \( \alpha_{x}^{t\arg et} \) is the best solution in the \( x^{th} \) krill individual.
4.2.1.3 Physical diffusion update
The third movement is physical diffusion. It is the random diffusion of the krill individuals. It is given by,
In which \( D_{\text{max} } \) is the optimum diffusion speed, and \( \delta \) is the haphazard directional vector in [− 1, 1].
In the three formerly noted movements, the position of the \( x^{th} \) krill in the interval \( t^{1} \) to \( t^{1} + \Delta t^{1} \) is found using divergent parameters. It is given by,
where, \( \Delta t^{\prime} \) is one of the most salient constants and should be calibrated with the provided real-world maximization.
On the basis of the above-mentioned condition, krill individual’s position is restructured for assaying the objective function, which is identifying the greatest krill (which is the finest solution). After this, the individuals in the Krill population are arranged from the best to the worst. Then, the motion updates and position of each krill individual is computed. This presents the optimized path. Once the optimized path is figured out, the aggregated data will be transmitted over that.
The flow diagram of the KHO algorithm is demonstrated in Fig. 3.
5 Results and discussion
The performance of the proposed DC-KHO is validated by implementing it in MATLAB. The simulation parameters are given in Table 1. For examining the proposed task performance, we have computed divergent parameters like energy consumption for primary and secondary cluster heads, data transmission time, computational time, remaining energy, and network lifespan. These are compared with the existing routing algorithms that do not incorporate optimized path data aggregation.
Figure 4 shows the proposed DC-KHO and cluster head routing without optimized path (indicated here as without KH). From the graph, we can see that the energy consumption of DC-KHO cluster head is less than the existing algorithm without KH. Since it does not take into consideration the continuous and redundant cluster head node selection, it improves energy usage rate early in the process.
Compared with the previously existing algorithm without KH, the partial load of the primary cluster head is gradually decreased by the selection of the secondary-cluster head in the DC-KHO. Further, considering the energy consumption of the sub-cluster head and the communication costs, an appropriate multi-hops routing path is selected. This process aids in effectively decreasing the energy consumption by the cluster head. Altogether, the amount of energy consumed by the DC-KHO algorithm cluster head is low.
Figures 5 and 6 display the energy consumption comparison analysis for primary cluster head (Aggregator) and secondary cluster head (back bone of the optimized path). And the results shows that DC-KHO consumes less energy for aggregation and routing.
In Fig. 7, the computation time of Krill Herd Optimization algorithm is compared with that conventional routing algorithm. The x-axis represents the number of iterations, and y-axis corresponds to the computation time in seconds. The comparison graph shows that the computation time of path construction for different iterations is low in case of the proposed DC-KHO when compared to that of the cluster head routing algorithm without KH.
Figure 8, presents the data of the survival nodes against different number of iterations for the cluster head routing algorithm without KH and DC-KHO algorithms. It is seen that the lifespan of the nodes is shorter in case of cluster head routing algorithm without KH because of the repeated selection of same cluster head for routing. As there is quick energy burn up of the head nodes, the nodes are susceptible to premature death as a result of the quick energy burning up of head nodes. To overcome this drawback, the proposed DC-KHO uses a different technique to select the cluster head nodes.
This method effectively prolongs the survival of head nodes by balancing the energy consumption. Remaining energy is calculated by using the following formula,
where, \( E_{R} \) is the remaining energy, \( E_{n} \) is the node initial energy and \( E_{c}^{t} \) is the amount of energy consumed by node i in time t.
Figure 9 shows the data transmission time of proposed DC-KHO. The transmission time \( T_{d} \) is calculated using Eq. 11
where \( T_{d} \) is the data transmission time, \( S_{d} \) is the size of the data, \( {\text{and}}\,R_{b} \) is the bit rate.
In the comparison graph given in Fig. 9, the X-axis represents the number of iterations, and the Y-axis represents data transmission time in seconds.
Figure 10 shows the network lifetime comparison of the proposed DC-KHO algorithm. Network life time is defined as the sustainability of nodes for providing monitoring coverage with the minimum threshold. The graph shows that the network lifetime of DC-KHO is higher than its counterpart algorithm without KH. This is because DC-KHO uses two different cluster heads for aggregation and routing, besides choosing the optimized path.
In Table 2, a comparison of the performance of the proposed DC-KHO and the conventional routing protocol has been made. Calculated values of average computational time, average data transmission time and average energy consumption are given. The results show that the values for the above-mentioned components are lower in case of the proposed DC-KHO, than that of the conventional routing algorithm without KH.
6 Conclusion
If the topology is not standardized, there is an enormous amount of energy consumption even with minimal distance between the sink holes. To facilitate improved utilization of network energy, and to make the energy consumption balanced in the network, a novel DC-KHO is proposed. With two different cluster heads formation for aggregation and routing, DC-KHO makes the energy consumption balanced. Further, for enabling efficient routing, the Krill Herd Optimization algorithm is used. It identifies the optimized path via calculating path trust value for each path. DC-KHO consumes less energy for unmanned real-time WSN applications, and hence invariably increases the network lifetime. The experimental results show that the DC-KHO algorithm predominantly saves transmission time, residual energy and computational time in comparison with the existing schemes. Finally, with DC-KHO the life span of the network increases by 64.58%, when a 9 V battery is used for the nodes. In future this work may be extended to support mission critical applications by introducing evolutionary optimization algorithms to reduce number of iterations further.
Change history
16 June 2022
This article has been retracted. Please see the Retraction Notice for more detail: https://doi.org/10.1007/s12652-022-04186-0
References
Al-karaki JN, Ul-mustafa R, Kamal AE (2009) Data aggregation and routing in wireless sensor networks: optimal and heuristic algorithms. Comput Networks 53:945–960. https://doi.org/10.1016/j.comnet.2008.12.001
Ari AAA, Damakoa I, Gueroui A et al (2017) Bacterial foraging optimization scheme for mobile sensing in wireless sensor networks. Int J Wirel Inf Netw 24:254–267. https://doi.org/10.1007/s10776-017-0359-y
Arora VK (2019) ACO optimized self-organized tree-based energy balance algorithm for wireless sensor network. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-019-01186-5
Behera TM, Mohapatra SK, Samal UC et al (2019) Residual energy-based cluster-head selection in WSNs for IoT application. IEEE Internet Things J 6:5132–5139. https://doi.org/10.1109/JIOT.2019.2897119
Bhola J, Soni S, Kaur G (2019) Genetic algorithm based optimized leach protocol for energy efficient wireless sensor networks. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-019-01382-3
Comput JPD, Ben-othman J, Yahya B (2010) Energy efficient and QoS based routing protocol for wireless sensor networks. J Parallel Distrib Comput 70:849–857. https://doi.org/10.1016/j.jpdc.2010.02.010
Dong M, Ota K, Liu A (2016) RMER: reliable and Energy-efficient data collection for large-scale wireless sensor networks. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2016.2517405
Energy A, Selection EC, Networks WS, Studies C (2010) 2010 International conference on intelligent systems, modelling and simulation Ma Chaw Mon Thein Thandar Thein, pp 287–291. https://doi.org/10.1109/ISMS.2010.60
Feng X, Zhenzhen X, Lin Y, Weifeng S, Mingchu L (2010) Prediction-based data transmission for energy conservation in wireless body sensors. In: 2010 The 5th Annual ICST Wireless Internet Conference (WICON). IEEE, pp 1–9
Johnson DB (2011) PW-MAC: an energy-efficient predictive-wakeup mac protocol for wireless sensor networks, pp 1305–1313
Kandris D, Tsioumas P, Tzes A, Nikolakopoulos G, Vergados DD (2009) Power conservation through energy efficient routing in wireless sensors networks. Sensors (Basel). https://doi.org/10.3390/s90907320
Karaboga D, Basturk B (2008) On the performance of artificial bee colony (ABC) algorithm. Appl Soft Comput 8:687–697. https://doi.org/10.1016/j.asoc.2007.05.007
Khan R, Madani SA, Hayat K, Khan SU (2012) Clustering-based power-controlled routing for mobile wireless sensor networks. Int J Commun Syst. https://doi.org/10.1002/dac
Kuila P, Jana PK (2014) Engineering Applications of Artificial Intelligence Energy efficient clustering and routing algorithms for wireless sensor networks: particle swarm optimization approach. Eng Appl Artif Intell 33:127–140. https://doi.org/10.1016/j.engappai.2014.04.009
Kumar D, Aseri TC, Patel RB (2009) EEHC: energy efficient heterogeneous clustered scheme for wireless sensor networks. Comput Commun 32:662–667. https://doi.org/10.1016/j.comcom.2008.11.025
Liu G, Li Z, Zhou X, Li S (2007) Transmission power control for wireless sensor networks. In: 2007 Int Conf Wirel Commun Netw Mob Comput WiCOM 2007 12:2596–2599. https://doi.org/10.1109/WICOM.2007.646
Su S, Zhao S (2017) A hierarchical hybrid of genetic algorithm and particle swarm optimization for distributed clustering in large-scale wireless sensor networks. J Ambient Intell Humaniz Comput. https://doi.org/10.1007/s12652-017-0619-9
Villas LA, Boukerche A, Ramos HS et al (2013) DRINA: a lightweight and reliable routing approach for in-network aggregation in wireless sensor networks. IEEE Trans Comput 62:676–689
Wang G, Guo L (2013) A novel hybrid bat algorithm with harmony search for global numerical optimization. J Appl Math 2013:1–21. https://doi.org/10.1155/2013/696491
Xiang L, Luo J (2011) Compressed data aggregation for energy efficient wireless sensor networks. SECON. https://doi.org/10.1109/SAHCN.2011.5984932
Xiong YLN, Vasilakos YZAV, Jia JGY (2010) Multi-layer clustering routing algorithm for wireless vehicular sensor networks. IEEE Commun. https://doi.org/10.1049/iet-com.2009.0164
Zhou H-Y, Luo D-Y, Gao Y, Zuo D-C (2011) Modeling of node energy consumption for wireless sensor networks. Wirel Sens Netw 03:18–23. https://doi.org/10.4236/wsn.2011.31003
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article has been retracted. Please see the retraction notice for more detail: https://doi.org/10.1007/s12652-022-04186-0"
About this article
Cite this article
Visu, P., Praba, T.S., Sivakumar, N. et al. RETRACTED ARTICLE: Bio-inspired dual cluster heads optimized routing algorithm for wireless sensor networks. J Ambient Intell Human Comput 12, 3753–3761 (2021). https://doi.org/10.1007/s12652-019-01657-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-019-01657-9