Abstract
As the technology is progressing rapidly, the spectrum sensing and the mobility of wireless nodes have become a concern to address the issues in cognitive radio networks (CRNs). We propose an energy optimization technique by using the residual energy concept, and a new routing protocol EERP (Energy Efficient Routing Protocol) is being proposed with the terminal node to address the effects of energy resource limitations for CRN and to improvise network routing. The EERP protocol aids in selecting the optimum path from nearby nodes among potential transmission channels in the proposed work. The protocol’s local route maintenance technique will be strengthened if the path has been damaged. This intern decreases retransmission and boosts routing effectiveness even more. Additionally, by choosing the fault path as a result of energy exhaustion, this can stop the link transmission process. The low-energy adaptive clustering hierarchy (LEACH) technique has undergone a thorough investigation and comparison. Based on the results, it is concluded that the EERP can balance the load, safeguard low-energy nodes, lengthen network survival times, and further cut down on packet loss rates and data delivery packet delays.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introductıon
Regarding energy economy and the smallest hop count in the routing protocol, the routing protocol in wireless sensor networks is crucial. The terminal node in a cognitive radio network, which may have any number of mobile nodes, often uses a battery to supply power and ensures it can communicate over extended distances. In cognitive radio networks, energy resources play a key part in this. One node in a network loses energy, which means that node cannot continue to participate in the data transmission process and is referred to as a dead node. Numerous issues, including data interruption faults in the link and excessive energy consumption, could be brought on by these dead nodes. We can create a forwarding link node that is positioned in the middle of the nodes to address this issue, but this would result in congestion at the data points and a bigger degree of transmission loss as a result of the link cluster head’s energy exhaustion. Additionally, it has been found that routing protocols that disregard the energy component use a lot of energy and are expensive.
These days, there is a lot of room for energy-saving methods, such as sensor networks with clusters and a hierarchical routing protocol to lengthen the lifetime of the network. It is noted that the energy state of the cluster heads and sensor nodes has not been taken into account in the LEACH protocol. To address this problem, various researchers have proposed various techniques, such as orthogonal frequency-division multiplexing (OFDM) type of sensors and optimal sleep–wake scheduling, but these have not had an impact and also have an issue with increased packet delay, because each of the sensor nodes has its own energy state.
In this work, we suggest an energy-efficient routing protocol for cognitive radio networks based on the comparative analysis conducted in this article. This protocol primarily focuses on enhancing network performance at various levels of energy stages, such as normal, warning, and dangerous stage. In the suggested study, we have concentrated on the node’s energy consumption and the network lifespan residual energy model. Additionally, we conducted a comparison of the proposed EERP with the LEACH protocol and found certain advantages including lower energy consumption, a longer network survival time, a decrease in packet loss rate and packet delay of data delivery, and protection of low-energy nodes.
2 Related Work
The network throughput would drastically decrease as a result of such uncooperative behavior. We suggest a credit-based Secure Incentive Protocol (SIP) to encourage collaboration across mobile nodes with different objectives in order to solve this issue (Zhang et al. 2007). In addition to introducing energy-efficient uneven clustering protocol to APTEEN, the strategy also integrates cross-layer design methodology with routing and spectrum allocation. Ant colony algorithm is used to complete inter-cluster path search, which reduces the workload of the cluster head (Wang and Wang 2019). NP-complete optimization issue with an EQS route is serving as a workable solution. We develop a new deep reinforcement learning model that supports the DRQR protocol to create EQS routes in real time through offline training as opposed to online training as most literature research does in order to address this issue (Tran et al. 2022).
In order to accomplish efficient routing protocol operation in terms of maximum energy conservation, maximum-possible routing pathway setups, and minimal delays, a signaling mechanism and an energy-efficient system were developed based on a simulation scenario (Mastorakis et al. 2014). In order to address bandwidth constraints and battery life issues in wireless sensor networks, cognitive radio technology is being studied (Srividhya and Shankar 2022). The energy utility function is optimized by customizing the sensing period, sensing threshold, and number of collaborating SUs at the same time with the restriction of offering adequate protection for the primary user (PU) (Wu et al. 2014). But without considering energy efficiency, low-energy adaptive clustering hierarchy (LEACH) has been included into CWSN. The fact that node energy is finite and cannot be increased is one of the shortcomings of CWSN. To increase energy efficiency and increase the lifespan of CWSN, an efficient routing (Ge et al. 2018) protocol is required. In the CWSN, it is crucial to minimize energy use during data transmission. Along with the research work, an enormous work as in Bolla and Shivashankar (2017), Jijesh et al. (2021), Shankar et al. (2020), Palle et al. (2020), Bolla and Shankar (2020), Ding et al. (2017), Wang et al. (2013), Shome et al. (2021), and Ibrahim et al. (2022) is helpful in carrying out the work.
3 System Model for Energy Consumption of CRNs
As per the LEACH protocol, a system model for consumption of the energy for sending the nodes is discussed in Fig. 2 as follows.
In Fig. 2, we assume that the distance from transmitting node to receiving node is given by a variable d and energy consumption for the amplifier is \(E_{{{\text{amp}}}}\). Energy to receive the signal is \(E_{{{\text{min}}}}\) and the relation between \(E_{{{\text{amp}}}}\) and \(E_{\min }\) is given in Eq. 1.
where the value of n can be 2 or 4 and k is a constant. For instance, \(n = 2\) and \(k = 1\), then lifetime analyzed to lifetimes how outperforms lifetime down on 1 can be rewritten as in Eq. 2.
To calculate the energy transfer parameters and receiver parameters, we use \(E_{TX}\) and \(E_{RX} ,\) respectively, where ETR is the computational energy. And it is given by Eq. 3.
For sending or receiving of \(L\) bits of data, then we use Eqs. 4–6.
Further, residual energy (R) can be calculated based on the percentage of ratio given below as follows as in Eq. 7.
4 Routing Protocol
In the proposed work, we have focused on the residual energy, and based on this, the routing strategy has been proposed. To understand clearly, for instance, a link is said to be free if its R (overall) residual energy is more than zero. If not, the link is not free. The routing path has been established on the residual energy (with greater ER). It is essential for distributing the network’s load. It is not assumed that the nodes will be sent if their leftover energy is in the danger stage. A prolonged survival time can be considered only for the source and destination nodes.
In this article, we have assumed two thresholds T1 and T2 are the node’s relative residual energy values are thought to be, and the energy within the node has been separated into three stages. Stage 1: Normal stage (TS1), Stage 2: warning stage (TS2), Stage 3: danger stage (TS3). T1 is smaller than T2. As per Eqs. 8–10, the proportion of remaining energy T is compared with T1 and T2.
According to the equations above, the node is safeguarded and is not transmitted when it is in a dangerous stage.
4.1 Route Request
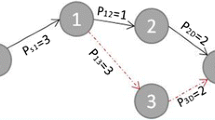
Any node that needs to transfer data must first check the availability of the routing database to see if a valid route is present. It must first send a route request (RREQ) message to connect with the closest node. According to Fig. 1, the RREQ is made up of the source ID, sequence number, destination ID, residual energy message, and relative residual energy value.
When the RREQ message is received by the intermediate nodes which are the neighboring nodes from the source node, then the protocol has to first verify the corresponding route concerning the routing table, and as per the requirements, the effective routing table is updated to overcome the loop generation sequence (14, 15, and 16). The process of continuous forwarding of the RREQ is continued until the route to the destination node appears. The node that is being forwarded will obtain the information of the energy from the RREQ message format. With the acquired information, it compares it with its energy information, and then it decides and checks whether the information in the routing table needs to be updated or not. The relationship between the old and new energy levels is as follows, and the \(E\,\left( {{\text{new}}} \right) \) is as in Eq. 11.
The new energy E(new) is
4.2 Route Discovery
The route discovery process is complete once the RREQ can be delivered to the source node. If the intermediate node has the destination node, the RREQ message is forwarded to the source, for example. The destination node will check the energy level information (E) with the threshold residual energy, say \(T_{1}\) and \(T_{2}\), after receiving the RREQ. The method of establishing the current link and completing the routing is based on these thresholds, and after a little wait, the RREQ source node receives a message indicating that the route discovery procedure is finished.
4.3 Route Establishment and Route Maintenance
In the proposed work, when the residual energy of a node is exhausted, then the node needs to find out the next-hop possible route sensing node. This involves the following two phases.
-
Phase 1: To select the neighboring sensing node, the node with the comparatively largest residual energy is used.
-
Phase 2: To pick up the neighboring sensing node for the next hop to transmit the data, we need to compare the neighbor sensing node residual energy with the predefined threshold value (E).
-
Phase 3: If the energy of the chosen neighboring sensing node is below the predefined threshold, we will reduce the predetermined threshold (E) and reselect the next-hop node.
Based on the three steps, the routing between the source node and destination node can be determined, previously described by taking into account the residual energy levels. But in order to maintain the route, the following route maintenance technique is used.
Once the route from source to destination has been established, the path is referred to as an active path. In the event that the source node has changed locations during data transmission, the route discovery process needs to be restarted. A route error (RERR) message is provided to the source node if the destination node or any intermediary nodes move.
There are two categories of route maintenance in this situation. During the source route rediscovery procedure, the source node must first broadcast the RREQ message to its neighbors along with the destination node sequence number, residual energy, and relative residual energy. In order to repair the damaged link by using another intermediate node, attention must be given with the upkeep of the intermediate nodes. In order to reestablish the path to the destination node, the corresponding intermediate nodes broadcast the RREQ message to their nearby nodes. When the path between the source node and the destination node is re-established, this operation can be finished.
5 Performance Analysis
Researchers have been able to assess the suggested routing protocol’s performance in terms of typical energy usage, packet loss rate, and network longevity by contrasting it with the LEACH protocol. The comparative analysis of the above-mentioned metrics for the existing and the proposed works is presented as follows in Fig. 2.
5.1 Packet Loss Rate
This metric is helpful for tracking the effectiveness of cognitive radio networks. As per the results obtained, we observed that the packet loss rate of sensing the node is rising. This is due to the reason that the death date in the network nodes has been increased. The proposed work has a smaller packet loss rate because of the energy consumption optimization mechanism using residual energy concept, and further due to the maintenance of the lifetime analyzed to lifetime show out performs lifetime drop-down quality lifetime analyzed to lifetimes how outperforms lifetime of communication in the network as in Fig. 3.
5.2 Network Lifetime
This is often determined by how long the network’s sensing nodes survive. From the results obtained in Fig. 4 it is observed that as the network working hours increases with time.
The survival rate of network nodes has decreased, but the proposed protocol has a better number of live nodes than the existing protocol.
6 Conclusion
The research work proposed in the article is mainly focused on improvising the network lifetime in CRNs. As per the study carried out, in order to assess the proposed work, we assessed the two energy consumption optimization routing protocols, taking into account the network lifetime, node energy consumption, and packet loss rate. We found that the LEACH protocol performs better for CRNs. Overall, the outcomes show that the suggested approach performs better than the existing methodology. The energy consumption appears to have a rather positive impact on the network lifetime and consumption of energy is drop-down by about 5%, the live nodes concerned has been improved by about 13%, and the loss rate has been reduced by about 6%.
References
Bolla DR, Shankar S (2020) A robust QSCTA-EDRA routing protocol for cognitive radio sensor networks. Int J Commun Netw Distrib Syst 25(4):385–413. https://doi.org/10.1504/IJCNDS.2020.110523
Bolla DR, Shivashankar (2017) An efficient protocol for reducing channel interference and access delay in CRNs. In: 2017 2nd IEEE international conference on recent trends in electronics, information & communication technology (RTEICT), pp 2247–2251. https://doi.org/10.1109/RTEICT.2017.8257000
Ding H, Fang Y, Huang X, Pan M, Li P, Glisic S (2017) Cognitive capacity harvesting networks: architectural evolution toward future cognitive radio networks. IEEE Commun Surv Tutor 19(3):1902–1923. https://doi.org/10.1109/COMST.2017.2677082
Ge Y, Wang S, Ma J (2018) Optimization on TEEN routing protocol in cognitive wireless sensor network. J Wirel Commun Netw 2018:27. https://doi.org/10.1186/s13638-018-1039-z
Ibrahim NK, Sali A, Karim HA, Ramli AF, Ibrahim NS, Grace D (2022) Multiple description coding for enhancing outage and video performance over relay-assisted cognitive radio networks. IEEE Access 10:11750–11762. https://doi.org/10.1109/ACCESS.2022.3146396
Jijesh JJ, Jinesh JJ, Bolla DR, Sruthi PV, Dileep MR, Keshavamurthy D (2021) Development of food tracking system using machine learning. In: 2021 5th international conference on electrical, electronics, communication, computer technologies and optimization techniques (ICEECCOT), pp 802–806. https://doi.org/10.1109/ICEECCOT52851.2021.9708031
Mastorakis G et al (2014) Energy-efficient routing in cognitive radio networks. In: Resource management in mobile computing environments. modeling and optimization in science and technologies, vol 3. Springer, Cham. https://doi.org/10.1007/978-3-319-06704-9_14
Palle SS, Jijesh JJ, Bolla DR, Penna M, Sruthi PV, Alla G (2020) Modernized compartment with safety measures in railways. In: 2020 international conference on recent trends on electronics, information, communication & technology (RTEICT), 2020, pp 363–367. https://doi.org/10.1109/RTEICT49044.2020.9315565
Shankar S, Penna M, Bolla DR, Murthy K, Jijesh JJ, Navyashree HA (2020) Real time image classification based smart railway platform using convolutional neural network. In: 2020 international conference on recent trends on electronics, information, communication & technology (RTEICT), pp 398–402. https://doi.org/10.1109/RTEICT49044.2020.9315555
Shome A, Dutta AK, Chakrabarti S (2021) BER performance analysis of energy harvesting underlay cooperative cognitive radio network with randomly located primary users and secondary relays. IEEE Trans Veh Technol 70(5):4740–4752. https://doi.org/10.1109/TVT.2021.3073025
Srividhya V, Shankar T (2022) An energy efficient distance-based spectrum aware hybrid optimization technique for cognitive radio wireless sensor network. J Inst Eng India Ser B. https://doi.org/10.1007/s40031-022-00837-0
Tran T-N, Nguyen T-V, Shim K, da Costa DB, An B (2022) A deep reinforcement learning-based QoS routing protocol exploiting cross-layer design in cognitive radio mobile ad hoc networks. IEEE Trans Veh Technol. https://doi.org/10.1109/TVT.2022.3196046
Wang C, Wang S (2019) Research on uneven clustering APTEEN in CWSN based on ant colony algorithm. IEEE Access 7:163654–163664. https://doi.org/10.1109/ACCESS.2019.2950855
Wang J, Huang A, Wang W, Quek TQS (2013) Admission control in cognitive radio networks with finite queue and user impatience. IEEE Wirel Commun Lett 2(2):175–178. https://doi.org/10.1109/WCL.2012.122612.120918
Wu X, Xu JL, Chen M et al (2014) Optimal energy-efficient sensing in cooperative cognitive radio networks. J Wirel Commun Netw 2014:173. https://doi.org/10.1186/1687-1499-2014-173
Zhang Y, Lou W, Liu W et al (2007) A secure incentive protocol for mobile ad hoc networks. Wirel Netw 13:569–582. https://doi.org/10.1007/s11276-006-6220-3
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Reddy Bolla, D., Ramesh Naidu, P., Jijesh, J.J., Vinay, T.R., Srikanth Palle, S., Keshavamurthy (2024). Designing Energy Routing Protocol with Energy Consumption Optimization in Cognitive Radio Networks. In: Shetty, N.R., Prasad, N.H., Nagaraj, H.C. (eds) Advances in Communication and Applications . ERCICA 2023. Lecture Notes in Electrical Engineering, vol 1105. Springer, Singapore. https://doi.org/10.1007/978-981-99-7633-1_6
Download citation
DOI: https://doi.org/10.1007/978-981-99-7633-1_6
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-7632-4
Online ISBN: 978-981-99-7633-1
eBook Packages: EngineeringEngineering (R0)