Abstract
Unmanned air vehicles (UAVs) has shown great potential to enable numerous applications ranging from industry verticals to public safety communications. However, various challenges also arises with its integration into the existing terrestrial networks such as efficient UAV positioning, power allocation, trajectory design, and resource allocation. The existing conventional optimization solutions are not intelligent enough to overcome those challenges. Thus, real-time optimization and machine learning assisted solutions, and emerging technologies are required to overcome those challenges. To address those challenges, we summarized key technologies and research directions for UAV deployment at the edge or in the cell center, the power allocation and localization schemes, and the federated learning solutions.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
1 Machine Learning for Wireless Communications
The worldwide requirement for data traffic has endured around 1000\(\times \)-fold increase over the previous years [1]. Due to the development of modern wireless communication networks, data traffic requirements are supposed to increase the capacity of future networks. In addition to a notable increase in data traffic, the latest communications applications, such as autonomous networks, wearable gadgets, Internet of Things (IoT) devices, and cellular-connected unmanned air vehicles (UAVs) communications, continuously develop and produce immense data traffic with diverse requirements as shown in Fig. 1.
This development in communication applications demands an undeniable need for intelligent service, processing, and optimization of future communication systems. Using machine learning (ML), also known as artificial intelligence, into the design, planning, and optimization of future communication networks. The concept of ML has a lengthy and flourishing history. For instance, the use of neural networks (NN) for intelligent systems instead of utilizing a simple single-layer design to affect the state of one neuron. The idea of ML has established its powerful benefits in numerous fields, including robotics, computer vision, communications, and signal processing, where it is hard to find a detailed mathematical design for the characteristic pattern. In such areas, ML is considered a potential factor that does not demand any comprehensive model specification. The traditional methods that mainly depend on models and theories show weaknesses due to the extensive complexity of communication systems. Hence, research on ML for communication systems, particularly wireless communications, is currently encountering magnificent growth. For intelligent processing in a variety of scenarios, the emerging structure of ML acts as an enabler. The latest ML methods give a wide range of opportunities to develop intelligent communication systems that assists in addressing numerous challenges related to signal processing, classification, detection, channel estimation, resource allocation, routing protocols, configuring transport protocol, and user behavior interpretation. Various types of ML schemes have different usage in radio communication systems. It breaks the levels according to the kind of supervision demanded for training the ML models. Following are the three major categories of ML models.
1.1 Supervised Learning
Supervised learning model uses sample data with perceived results to estimate the output. Every sample data value is mapped to a single result value. The main purpose is to feed and train the model using sample data as input and with already known outcomes. After that, the already trained model predicts the results of the new input samples. Supervised learning is successful when there is a large amount of data to train the model. Hence, supervised learning is practical in deploying 6G to cope with rising traffic requirements. ML-based supervised learning collects performance computations such as throughput, outage probability, signal-to-interference and noise ratio, and pathloss for specific frequencies and bandwidth. ML-based supervised learning is used to predict the various performance matrix that a user will experience and adjust the different parameters accordingly [2]. ML-based supervised learning is adopted to train the models for pathloss prediction by considering channel state information (CSI) and approximate objective functions for associate propagation loss for 6G wireless systems.
1.2 Unsupervised Learning
An unlabeled collection of data is used to train the model with different characteristics and the system endeavors to identify subgroups with related features between the variables without having human involvement. Various schemes like generative deep neural network (DNN) and K-means clustering are advantageous when arranging devices for edge computing in a system. ML-based unsupervised learning is advantageous for uncertainty and detecting various faults in a system. It collects data in batches at data collection centers to decrease redundant data travel between distributed storage centers. It minimizes the latency by grouping nodes to automatically determine the node with low powers that must be promoted to nodes with more power for resource management in ultra-dense small cells.
1.3 Reinforcement Learning
Reinforcement Learning (RL) constantly works in probabilistic situations of wireless systems. In order to obtain excellent performance, the network parameters are modeled by using a Markov decision process (MDP) as shown in Fig. 2. RL continuously communicates with the environment, calculating the decisions at periodic intervals of time. The RL model needs to determine action at each point, obtained at the current state, to which the model provides a positive or a negative reward and updates the state. The rewards are associated with SINR and data rate. The RL is a data-driven approach that is not completely modeled from physics and mathematical-based modeling. Undoubtedly, wireless communication networks are human-made with lots of compositions that lack fast learning and transparency. Moreover, the state transition probability is free of all prior actions and states. While we require to optimize the system, the RL holds a record of all probabilities and their outcomes to obtain the absolute optimum decision. The principal grounds for RL to be applied to a radio communication system problem consist of (i) the signaling for obtaining the valuable data sets required to accurately operate the system is too complicated, (ii) the mathematical analysis of the wireless environment is considerably complicated to use in an agent and (iii) the desired results of RL is presented as a scalar reward. For example, the extensive machine-type communication and cell deployment (mainly small cells) where comprehensive system preparation is not achievable. We also summarized and compared key features of these three ML schemes in Table 1.
2 Cellular-Connected UAVs for Emergency Communications
UAVs have applications in numerous fields ranging from civil to vertical industries as they can enhance coverage while supporting high mobility. UAVs also helps in enabling real-time sensing applications and emergency communications [3]. UAVs are getting popularity in provisioning emergency communications to the users in disaster-hit areas by serving as an aerial base station (ABS) [4]. UAVs can assist in carrying medical and food supplies to unreachable regions. With the assistance of ABS deployment, an emergency communication network is established to prevent further human lives and losses by connecting the victims with the emergency relief providing personals. Since, it is hard for a communication service provider to deploy a ground base station (BS) in a short time. Therefore, ABS are deployed to enable emergency communications or to increase the coverage of the functional BS as shown in Fig. 3.
Providing cellular connectivity to UAVs has enabled a plethora of applications ranging from online video streaming to enable emergency communications [5]. The Third Generation Partnership Project (3GPP), an industry-led consortium that standardises cellular networks, has been actively involved in identifying the key requirements, technologies, and protocols for aerial communications. To use enhanced Long Term Evolution (LTE) support for aerial vehicles, 3GPP successfully completed the first report in 2017 that led to 3GPP Release 15 Technical Report TR 36.777. That report highlighted the necessary requirements for UAVs to optimize their operations.
In 2019, 3GPP TR 22.829 identifies several UAV-enabled applications and use cases to improve and support 5G communications and networking technologies. During 2020 in Release 17, 3GPP mainly focused on two aspects: (1) infrastructure to support the connectivity and tracking in TR 23.754, and (2) application architecture to support UAV operations in TR 23.755 [6]. However, in order to provide UAVs with reliable wireless connectivity along with secure operation, a lot of challenges must be addressed, including interference management, mobility and handover management, and malware attacks prevention.
To enable these applications, multiple UAVs are required for zone monitoring during disaster situation. In addition, mutiple UAVs system can boost the system efficiency through joint effort. However, number of challenges exists in multiple UAVs system that includes localization, data processing at the edge, and trajectory planning and 3D ABS placement optimization [7, 8]. When compared to normal operating conditions, user association plays a significant role in emergency scenarios. In the case of a disaster, when the traditional terrestrial base station (TBS) is out of service, it becomes necessary to deploy UAVs in that area. Enabling device-to-device (D2D) communications [9, 10], in addition to UAV deployment, could help to improve coverage. The user association for numerous types of base stations is the key challenge in co-existing D2D and UAVs network. To address this issue, the authors in [11] explored how to solve the user association problem for UAV-enabled networks using D2D connections by maximizing the weighted sum rate of UAV users and total D2D users. This difficult problem is tackled by presenting a learning-based clustering technique, which yielded sub-optimal results while being substantially simpler. As a consequence, this technique can be used to improve public safety wireless networks in the future.
In public safety communications, edge computing represents a paradigm change. Time taken to complete task is greatly minimize by placing edge computing centers in UAVs, which would minimize response time to consumers and save their lives. This strategy was described in [12], where the authors used user association, UAV trajectory, and user power to maximize offloaded bits from users to UAVs while considering the UAV’s energy constraints and the users’ QoS constraints. The trajectory of the UAV is significantly affected by various elements such as energy, flight time, and user needs.
UAVs equipped with Intelligent Reflecting Surface (IRS) are used in hazardous communication environments to provide public safety users with customizable services, quick deployment, low latency, coverage assurance, and a large amount of energy. UAVs-IRS defend mission-critical, high-priority public safety users from risks such as terrorism, natural disasters, and technological accidents. This communication helps to communicate and send the information (e.g., voice, data, and video) which improves the cooperation among of public safety users [13]. Due to malicious assaults or natural disasters [14], the BSs may be destroyed, leaving high-priority public safety users’ without coverage. UAVs-IRS provide a direct or multi-hop by acting as a relay communication situation to address this issue [15]. When UAVs-IRS are used in conjunction with public safety networks, overall system congestion and communication coverage gaps are reduced. Adding flexible UAVs-IRS relays to disaster zones reduces the public safety users’ outages dramatically. The coverage of public safety users’ is significantly boosted after deploying UAVs-IRS relaying systems. UAVs-IRS can simultaneously give coverage to adjacent public safety users’ and act as a relay to cover users that are positioned at a great distance by optimizing IRS reflection angle and phase shifts [16].
We summarize recent works related to UAV communications that covers various aspects such as ABS placement schemes, localization approaches, and artificial intelligence (AI)-assisted communications in Table 2.
3 ABS Placement, Power Allocation, and Localization for Emergency Communications
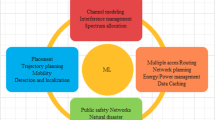
UAV-assisted communication infrastructure can provide high performance, capacity enhancements, and extended network coverage [32, 33]. They can explicitly provide mission-critical communications tasks with the facility of autonomous operations. Furthermore, UAVs play an important role in the distribution of critical information on the fringes of the fighting area as well as in the implementation of cellular networks. To provide the coverage extension, UAVs as a flying adhoc network (FANET) has gain the popularity [34]. We summarized some of the use cases to enable public-safety communications in Fig. 4.
A variety of future FANET communication architectures have been investigated including existing wireless technologies in the literature. However, selection of key communication technologies, architecture and core technology is truly a tedious problem to handle in FANET [35]. For instance, in [36] the authors presented a hybrid communication model, where they adopted features of 802.11 to meet high data rate requirements and 802.15.1 for low power consumption to enable FANET communications. This architecture considerably improved the network performance and reduced infrastructures costs.
In [37], the authors presented the advantage of coordination between UAVs and wireless sensor networks (WSNs). These two networks can support a wide range of applications, including search and rescue, navigation, control and recognition. The authors presented the solution for coverage enhancement using WSN-empowered UAV networks and argued that an efficient selection of way-points can solve several coverage issues.
To achieve high throughput gain during emergency situation, the authors in [38], presented the solution to optimally place the UAVs as an ABS in the disaster-hit areas. They achieved the improved average as well as an edge throughput. Similarly, the authors in [31] summarized the key contributions of ABS to enable public safety communications by targeting energy efficiency perspective. Moreover, they also proposed the ABS-assisted architecture that can assist the emergency users by enabling emergency communication services.
To enhance the users’ coverage and improve their connection, the matching game algorithm is proposed in [39]. Moreover, they also propose a medium access control framework to optimize emergency efficiency and priorities emergency communications users. The simulation results proved the efficacy of the proposal within the affected areas. In [40], the authors presented a solution for different path loss models and deployment situations to enable ABS-assisted public safety communications in heterogeneous networks. By system-level simulations, the authors proved that they successfully improved the system performance by reducing the co-channel interference.
For ABS-aided relay system to enable emergency communications [41], the authors in [42] presented the joint optimisation of real-time ABS deployment and resource allocation scheme by proposing a fast K-means-based user clustering model. They also provided the centralized and distributed models to maximise the energy efficiency of the considered network under the tight QoS constraints. Numerical results verified the effectiveness of the proposed scheme.
To solve the challenge of path planning during disaster situation with limited battery and unknown user distribution constraints, the authors in [43] converted this challenge into multi-armed bandit problem. Then to efficiently solve this problem, they proposed two path planning algorithms which significantly enhanced performance in terms of number of served users.
The back-haul-aware optimization problem is presented in [44] to minimize the delay and search the ABS optimum altitude to maximize the users’ coverage. They selected the optimum altitude by considering the minimum transmit power constraint. In [45], the authors jointly optimized the user association, resource allocation and 3D UAV placement to maximize the downlink sum-rate. They divided the problem into the three sub-problems and proposed the iterative solution that significantly enhanced the sum rate by reducing the co-channel interference. In [46], the authors targeted to maximize the network throughput by jointly optimizing the transmit power and UAV trajectory subject to the mobility constraints. They proved that the proposed scheme achieved notable throughput gains as compared to the conventional static relaying system.
In [47], to jointly optimize the ABS elevation and power control with the goal of reducing the concentrated outage probability, an iterative algorithm centered on the block coordinate descent (BCD) technique was proposed. Simulation results revealed that the outage probability was considerably reduced. In [48], the author proposed a framework that optimizes UAV trajectory and transmits power in order to improve the minimum throughput among UAV aided users. An iterative algorithm was proposed with the goal of reducing access delay and improving throughput.
Localization of the users is key during the disaster situation. To address this challenge, the authors in [49] presented a solution to transmit the discovery message over an ABS-to-user link. Simulation results proved that by using root-MUSIC algorithm the localization accuracy has been significantly improved. Similarly, in [50] data routing mechanism for localization in GPS-denied areas. The proposal focused on weighted centroid localization technique, where the position of unknown ABS are calculated using fuzzy logic. The proposed idea improves the localization efficiency by reducing the energy consumption and improving the lifetime.
4 Federated Learning for UAVs-enabled Public Safety Networks
UAVs as an ABS play key role in coverage improvement, capacity enhancement, and improving energy efficiency. During public safety communications, UAVs act as mobile terminal to enable applications like real-time video streaming for security personals. Here, UAV that act as an aggregator to globally train the model by collecting the locally trained model from the users, as shown in Fig. 5.
To efficiently implement this system, recently deep learning approaches has gained popularity to process the huge amount of received data. However, most of those processing are cloud centric, that in turn consumes huge power, consumes more bandwidth, introduce communication delay, and may pose security threats as it may contain UAV location and identity [51]. We compare the federated learning (FL) with the existing distributed and centralized learning schemes in terms of cost, accuracy, and latency in Table. 3.
To overcome those challenges, recently Google introduced federated deep learning (FDL) or distributed deep learning concept [52] that has attracted huge popularity in communications, and specially in UAV communications during public safety, where only the locally trained models will be shared with the centralized entity for aggregation. This in turn significantly reduced the latency and power consumption as compared to centralized cloud processing as shown in Fig. 6 .
In FDL, deep neural network is collaboratively trained at the edge devices (UAVs in our case). Afterwards, the trained model is shared with the cloud to aggregate and create a global model. There are three main steps involved in this process; (1) training initialization, where as per requirements of the targeted application, hyper-parameters, initial global model, etc., are broadcasted to the UAVs by federated learning (FL) server, (2) each UAV collect new data and update parameters of local model based on the global model. Each UAV tries to optimize their parameters, and then shared those trained parameter with FL server, (3) after receiving those local parameters from UAVs, FL server aggregates them using the FederatedAveraging algorithm [53] and sends back the updated model parameters to UAVs. At FL server, the received parameters are optimized by minimizing the global loss function. More details about those steps are summarized in [51].
In public safety communications, UAVs have to execute various tasks that ranges from trajectory planning to target recognition. To address this challenge, the authors in [54] presented framework to implement FL algorithms for UAV swarms. In UAV swarm, one UAV as a leader gather the locally trained data from each of the following UAV, generate global FL model, and then transmit it among the followers UAVs. In order to optimize the the convergence rate of FL, joint power allocation and scheduling scheme was proposed by taking care of energy and delay constraints. Simulation results proved the effectiveness of the proposal by significantly reducing the communication rounds as compared to the baseline schemes.
Mobile crowd-sensing is key for successful implementation of emergency communications as it assists in indoor positioning and environment monitoring. Moreover, the combination of UAVs with AI has open ways for efficient mobile crowd-sensing [55]. However, the conventional existing AI models may arise serious security and privacy threats. To overcome this threat, FL proved a promising solution because of opening the possibilities of collaborative learning and training of the model without exposing the sense data. To improve this security further, the in this paper the authors introduced blockchain-based learning architecture that improves the privacy of local models. Results proved that the security was improved by introducing effective solution of model sharing as compared to the baseline schemes.
In [56], to reduce the processing load in multi-UAV networks the authors proposed an asynchronous federated learning (AFL) framework to enable asynchronous distributed computing that disallows transmitting the raw data to UAV servers and trained them locally. Moreover, to further improve the efficiency and maintain quality of service the device selection strategy was also introduced. The authors improved the convergence speed and accuracy considering asynchronous advantage actor-critic for joint device selection, UAVs placement, and resource management scheme [57].
In disaster hit areas, the thorough inspection of local updates at UAVs is necessary to guarantee privacy. To overcome this challenge, the authors in [58] combined blockchain with FL and replaced the centralized FL platform with a UAV-assisted FL with blockchain at edge. Results verified that the proposed framework was suitable to enable intelligent disaster communications that consumes less energy.
5 Conclusion
In this chapter, we have summarized the key technologies related to intelligent UAVs to enable public safety communications and also discuss future research directions for researchers. We have concluded that the intelligence plays key role in improving the UAVs performance in terms of coverage, throughput, mobility management, and computation at the edge to enable public-safety communications.
References
Saad W, Bennis M, Chen M (2019) A vision of 6G wireless systems: applications, trends, technologies, and open research problems. IEEE Network 34(3):134–142
Kaleem Z, Ali M, Ahmad I, Khalid W, Alkhayyat A, Jamalipour A (2021) Artificial intelligence-driven real-time automatic modulation classification scheme for next-generation cellular networks. IEEE Access 9:155584–155597
Nguyen LD, Duong TQ, Hoang TD (2022) Real time convex optimisation for 5G networks and beyond. Telecommunications series. Institution of Engineering & Technology
Shahzadi R, Ali M, Khan HZ, Naeem M (2021) UAV assisted 5g and beyond wireless networks: a survey. J Netw Comput Appl 103114
Challita U, Ferdowsi A, Chen M, Saad W (2019) Machine learning for wireless connectivity and security of cellular-connected UAVs. IEEE Wirel Commun 26(1):28–35
Aly Sabri Abdalla and Vuk Marojevic (2021) Communications standards for unmanned aircraft systems: the 3GPP perspective and research drivers. IEEE Commun Stan Mag 5(1):70–77
Hentati AI, Fourati LC (2020) Comprehensive survey of UAVS communication networks. Comput Stand Interfaces 103451
Shakoor S, Kaleem Z, Do D-T, Dobre OA, Jamalipour A (2020) Joint optimization of UAV 3D placement and path loss factor for energy efficient maximal coverage. IEEE Internet Things J
Kaleem Z, Qadri NN, Duong TQ, Karagiannidis GK (2019) Energy-efficient device discovery in D2D cellular networks for public safety scenario. IEEE Syst J 13(3):2716–2719
Hayat O, Kaleem Z, Zafarullah M, Ngah R, Hashim SZM (2021) Signaling overhead reduction techniques in device-to-device communications: paradigm for 5G and beyond. IEEE Access 9:11037–11050
Cheng F, Li D, Jiang F, Zhao N (2019) Learning-based user association in multi-UAV emergency networks with ground D2D. In: IEEE international conference on communications workshops (ICC Workshops), pp 1–5. IEEE
Qian Y, Wang F, Li J, Shi L, Cai K, Shu F (2019) User association and path planning for UAV-aided mobile edge computing with energy restriction. IEEE Wirel Commun Lett 8(5):1312–1315
Li Y, Yin C, Do-Duy T, Masaracchia A, Duong TQ (2021) Aerial reconfigurable intelligent surface-enabled URLLC UAV systems. IEEE Access 9:140248–140257
Anwar MZ, Kaleem Z, Jamalipour A (2019) Machine learning inspired sound-based amateur drone detection for public safety applications. IEEE Trans Veh Technol 68(3):2526–2534
Ma D, Ding M, Hassan M (2020) Enhancing cellular communications for UAVs via intelligent reflective surface. In: IEEE wireless communications and networking conference (WCNC), pp 1–6
Khalid W, Heejung Yu, Do D-T, Kaleem Z, Noh S (2021) RIS-aided physical layer security with full-duplex jamming in underlay D2D networks. IEEE Access 9:99667–99679
Mittal P, Sharma A, Singh R (2020) Deep learning-based object detection in low-altitude UAV datasets: a survey. Image Vis Comput 104046
Sharma A, Vanjani P, Paliwal N, Wijerathna Basnayaka CM, Jayakody DNK, Wang H-C, Muthuchidambaranathan P (2020) Communication and networking technologies for UAVS: a survey. J Netw Comput Appl 102739
Masood A, Scazzoli D, Sharma N, Le Moullec Y, Ahmad R, Reggiani L, Magarini M, Alam MM (2020) Surveying pervasive public safety communication technologies in the context of terrorist attacks. Phys Commun 41:101109
Gupta L, Jain R, Vaszkun G (2015) Survey of important issues in UAV communication networks. IEEE Commun Surv Tutor 18(2):1123–1152
Kumbhar A, Koohifar F, Güven I, Mueller B (2016) A survey on legacy and emerging technologies for public safety communications. IEEE Commun Surv Tutor 19(1):97–124
Vattapparamban E, Güven I, Yurekli AI, Akkaya K, Uluağa S (2016) Drones for smart cities: issues in cybersecurity, privacy, and public safety. In: 2016 international wireless communications and mobile computing conference (IWCMC), pp 216–221. IEEE
Wei Yu, Hansong X, Nguyen J, Blasch E, Hematian A, Gao W (2018) Survey of public safety communications: user-side and network-side solutions and future directions. IEEE Access 6:70397–70425
Yan C, Lingang F, Zhang J, Wang J (2019) A comprehensive survey on UAV communication channel modeling. IEEE Access 7:107769–107792
Alsamhi SH, Ma O, Ansari MS, Almalki FA (2019) Survey on collaborative smart drones and internet of things for improving smartness of smart cities. IEEE Access 7:128125–128152
Park S, Kim HT, Lee S, Joo H, Kim H (2021) Survey on anti-drone systems: components, designs, and challenges. IEEE Access 9:42635–42659
Akbari Y, Almaadeed N, Al-maadeed S, Elharrouss O (2021) Applications, databases and open computer vision research from drone videos and images: a survey. Artif Intell Rev 54(5):3887–3938
Popescu D, Stoican F, Stamatescu G, Chenaru O, Ichim L (2019) A survey of collaborative UAV-WSN systems for efficient monitoring. Sensors 19(21):4690
Bithas PS, Michailidis ET, Nomikos N, Vouyioukas D, Kanatas AG (2019) A survey on machine-learning techniques for UAV-based communications. Sensors 19(23):5170
Zhi Y, Zhangjie F, Sun X, Jingnan Yu (2020) Security and privacy issues of UAV: a survey. Mob Netw Appl 25(1):95–101
Shakoor S, Kaleem Z, Baig MI, Chughtai O, Duong TQ, Nguyen LD (2019) Energy efficiency perspective. Role of UAVs in public safety communications. IEEE Access 7:140665–140679
Ali I, Kaleem Z, Khan S, Satti MA, Uddin Z (2020) Cognitive radios real-time implementation on software defined radio for public safety communications. Telecommun Syst 74(1):103–111
Duong TQ, Kim KJ, Kaleem Z, Bui M-P, Vo N-S (2021) UAV caching in 6G networks: a survey on models, techniques, and applications. Phys Commun 101532
Usman Q, Chughtai O, Nawaz N, Kaleem Z, Khaliq KA, Nguyen LD (2021) A reliable link-adaptive position-based routing protocol for flying ad hoc network. Mob Netw Appl 1–20
Kaleem Z, Yousaf M, Qamar A, Ahmad A, Duong TQ, Choi W, Jamalipour A (2019) UAV-empowered disaster-resilient edge architecture for delay-sensitive communication. IEEE Netw 33(6):124–132
Khan MA, Qureshi IM, Khanzada F (2019) A hybrid communication scheme for efficient and low-cost deployment of future flying ad-hoc network (fanet). Drones 3(1):16
Sayeed M, Kumar R et al (2018) An efficient mobility model for improving transmissions in multi-UAVS enabled WSNS. Drones 2(3):31
Merwaday A, Guvenc I (2015) UAV assisted heterogeneous networks for public safety communications. In: IEEE wireless communications and networking conference workshops (WCNCW), 329–334
Ali K, Nguyen HX, Vien Q-T, Shah P, Raza M (2020) Deployment of drone-based small cells for public safety communication system. IEEE Syst J 14(2):2882–2891
Kumbhar A, Guven İ, Singh S, Tuncer A (2018) Exploiting LTE-advanced HetNets and FeICIC for UAV-assisted public safety communications. IEEE Access 6:783–796
Do D-T, Nguyen T-TT, Le C-B, Voznak M, Kaleem Z, Rabie KM (2020) UAV relaying enabled NOMA network with hybrid duplexing and multiple antennas. IEEE Access 8:186993–187007
Do-Duy T, Nguyen LD, Duong TQ, Khosravirad SR, Claussen H (2021) Joint optimisation of real-time deployment and resource allocation for UAV-aided disaster emergency communications. IEEE J Sel Areas Commun 39(11):3411–3424
Lin Yu, Wang T, Wang S (2019) UAV-assisted emergency communications: an extended multi-armed bandit perspective. IEEE Commun Lett 23(5):938–941
Kumar S, Suman S, De S (2018) Backhaul and delay-aware placement of UAV-enabled base station. In: IEEE conference on computer communications workshops (INFOCOM WKSHPS), pp 634–639. IEEE
Yin S, Li L, Yu FR (2020) Resource allocation and basestation placement in downlink cellular networks assisted by multiple wireless powered UAVs. IEEE Trans Veh Technol 69(2):2171–2184
Zeng Y, Zhang R, Lim TJ (2016) Throughput maximization for UAV-enabled mobile relaying systems. IEEE Trans Commun 64(12):4983–4996
Wang L, Bo H, Wang F, Chen S, Cui J (2020) Joint altitude, power control, and bandwidth allocation optimization for unmanned aerial vehicle-enabled reliable communications. Trans Emerg Telecommun Technol 31(7):e3983
Ji J, Zhu K, Niyato D, Wang R (2020) Joint cache placement, flight trajectory, and transmission power optimization for multi-UAV assisted wireless networks. IEEE Trans Wirel Commun 19(8):5389–5403, e3983
Masood A, Sharma N, Mahtab Alam M, Le Moullec Y, Scazzoli D, Reggiani L, Magarini M, Ahmad R (2019) Device-to-device discovery and localization assisted by UAVs in pervasive public safety networks. In: Proceedings of the ACM MobiHoc workshop on innovative aerial communication solutions for FIrst REsponders network in emergency scenarios, pp 6–11
Khelifi F, Bradai A, Singh K, Atri M (2018) Localization and energy-efficient data routing for unmanned aerial vehicles: fuzzy-logic-based approach. IEEE Commun Mag 56(4):129–133, e3983
Brik B, Ksentini A, Bouaziz M (2020) Federated learning for UAVs-enabled wireless networks: use cases, challenges, and open problems. IEEE Access 8:53841–53849, e3983
Bonawitz K, Eichner H, Grieskamp W, Huba D, Ingerman A, Ivanov V, Kiddon C, Konečnỳ J, Mazzocchi S, Brendan McMahan H et al (2019) Towards federated learning at scale: system design. arXiv:1902.01046
McMahan B, Moore E, Ramage D, Hampson S, Aguera y Arcas B (2017) Communication-efficient learning of deep networks from decentralized data. In: Artificial intelligence and statistics, pp 1273–1282. PMLR
Zeng T, Semiari O, Mozaffari M, Chen M, Saad W, Bennis M (2020) Federated learning in the sky: joint power allocation and scheduling with UAV swarms. In: IEEE international conference on communications (ICC), pp 1–6
Wang Y, Zhou S, Zhang N, Benslimane A (2021) Learning in the air: secure federated learning for UAV-assisted crowdsensing. IEEE Trans Netw Sci Eng 8(2):1055–1069, e3983
Yang H, Zhao J, Xiong Z, Lam K-Y, Sun S, Xiao L (2021) Privacy-preserving federated learning for UAV-enabled networks: Learning-based joint scheduling and resource management. IEEE J Sel Areas Commun 39(10):3144–3159, e3983
Kaleem Z, Khaliq MZ, Khan A, Ahmad I, Duong TQ (2018) PS-CARA: context-aware resource allocation scheme for mobile public safety networks. Sensors 18(5):1473
Pokhrel SR (2020) Federated learning meets blockchain at 6g edge: a drone-assisted networking for disaster response. In: Proceedings of the 2nd ACM MobiCom workshop on drone assisted wireless communications for 5G and beyond, pp 49–54
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this chapter
Cite this chapter
Kaleem, Z., Ahmad, I., Duong, T.Q. (2022). Intelligent Unmanned Air Vehicles for Public Safety Networks: Emerging Technologies and Research Directions. In: Kaleem, Z., Ahmad, I., Duong, T.Q. (eds) Intelligent Unmanned Air Vehicles Communications for Public Safety Networks. Unmanned System Technologies. Springer, Singapore. https://doi.org/10.1007/978-981-19-1292-4_1
Download citation
DOI: https://doi.org/10.1007/978-981-19-1292-4_1
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-1291-7
Online ISBN: 978-981-19-1292-4
eBook Packages: EngineeringEngineering (R0)