Abstract
Remote healthcare monitoring systems are commonly used to manage patient diagnostic data. These systems are subjected to data privacy and security, reliability, etc. A new technique is introduced in this paper to solve privacy and security issues. Using Discrete Wavelet Transforms (DWT), EKG steganography technique is implemented in the proposed method. This method is based on the techniques of encryption and decryption. Encryption is used to hide the EKG signal within an image and to extract the EKG signal from the encrypted image, decryption is used. Subsequently, a prominent amount of raw EKG time series signal information is given as inputs for convolution neural networks (CNN). The representative and key characteristics used to classify the module autonomously are learned. Thus, the features are learned directly from the prominent time domain EKG signals by using a CNN. Trained characteristics can efficiently substitute the hand-crafted characteristics of the time-consuming user and traditional ad hoc characteristics. Using GoogLeNet CNN we have achieved an accuracy of 0.90625 .
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Cardiovascular disease (CVD), which was mentioned as the underlying cause of death, accounted for roughly 1 in 3 fatalities in the US in 2016. Between 2013 and 2016, there was some type of cardiovascular disease among 121.5 million American adults. Between 2014 and 2015 there were 351.2 billion dollars in direct and indirect expenses (Direct costs of 213.8 billion dollars and lost productivity/mortality of 137.4 billion dollars) [1] for complete cardiovascular diseases and stroke. On an average, for every forty seconds, an American is said to have a heart attack.
Cardiovascular disease is plaque build-up that causes blockages within the body’s major blood vessels. These blood vessels may include heart arteries (coronary heart disease), brain (cerebrovascular disease) and legs (arterial peripheral disease). Cardiovascular disease can be responsible for heart attacks, strokes and death (Fig. 1).
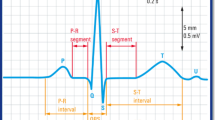
An electrocardiogram (EKG) is a test that uses detectors that are positioned over the chest on the skin to detect electrical activity in the core. These test scans are conducted during rest or exercise and can detect a variety of heart problems, particularly when conducted during exercise, including coronary heart disease.
Electrocardiographs uses electrodes to record the cardiac activity on the skin as small voltages of the order of one millivolt (mV). The variations in voltage vary with variation of heart activity. The twelve leads provide a clear view of the electrical activity of the heart as EKG wave forms which vary in amplitude and polarity of the P waves, QRS complex, and T waves.
Image encryption is commonly used in open internet works to secure data transmission. Before it is transferred or stored, we need to encrypt the information in order to secure the same from different attacks and for data integrity [2]. Governments, armies, economic institutions, hospitals and private companies deal with confidential pictures of their patients, geographies, enemies, products and economic statuses. Most of this data is now being gathered and stored on electronic computers and transferred to another computer through the network.
Keeping images protected is primarily intended to preserve confidentiality, integrity and authenticity. Cryptography is the study of secret messages from one party to another being transmitted safely [3]. It plays an significant role in ensuring data confidentiality while transferring information through the internet in particular. Confidentiality, authentication, integrity and non-repudiation are some particular safety requirements in the context of any application-to-application communication.
Cryptography is a technique of defending image-based secrets with a computation free process of decoding. In many applications such as: medical picture, confidential video conferencing, defence database, mobile computing, private communication, etc. The safety of digital pictures has become extremely crucial.
Recently, convolutional neural networks (CNNs) have gained considerable interest in multidimensional signal processing issues due to their impregnable capabilities and functionality for various applications, such as image and video recognition, object detection, computer vision classification, and data analysis of time series data.
One of CNN’s applications is the classification of time series challenges. It deals in particular with a prominent quantity of information used in various applications in health care systems, bioinformatics, activity recognition, etc. Conventional methods for classifying time series data are highly dependent on the features extracted, but to capture the inherent characteristics of time series data is hard to obtain all the fundamental, proper and key characteristics. We encrypt and decrypt the data securely and predict the type of EKG using Layer based CNN.
2 Methodology
The research aims to develop safe EKG system transmission to safeguard the acquisition, diagnosis, visualization and storage of EKG. The system is user-friendly so that it can be readily used by medical practitioners and scientists and will assist them in further research and diagnosis.
EKG signals were acquired from the 360 Hz sampling frequency MIT-BIH Arrhythmia database. The system will be able to perform EKG signal diagnosis after processing the raw EKG signal and then display the outcome on the screen. The system will alert the scientist or medical practitioner to further diagnosis if the outcome is critical.
Since patient information plays a crucial role in medical diagnosis and therapy, each patient has private medical information at the same moment. Data authentication is essential to guarantee that the patient is not handled incorrectly owing to inaccurate medical information. By using this technique, the EKG signal will be encrypted and decrypted so that only the medical practitioner can comprehend the outcome.
2.1 Discrete Wavelet Transformation (DWT)
The Discrete Wavelet Transformation (DWT) is a linear transformation operating with an integer power of 2 on data vectors, and transforms it into the same length of a numerically distinct vector. It divides information into different frequency parts and matches each element based on the scale. The Fig. 2 below represents filtering cascade, followed by a sub sampling factor of 2 [4] (Fig. 3).
Low frequency filtering activities and High frequency filtering activities are referred to as L and H, respectively, down sampled by the factor of 2 which is denoted by 2. Equations (1) and (2) represents outcomes of the filters.
\(a_k\) components are used for scaling and \(d_k\) components, known as wavelet coefficients, are used for determining the transform output. H[n] is high pass filter coefficient and L[n] is low pass filter coefficient. On scale k+1 the number of ‘a’ and ‘d’ elements on scale k is only half.
The DWT algorithm is comparable for two-dimensional images. For all Image rows, the DWT is executed first and then all the columns [4].
First, signal in the wavelet transformation is decomposed by a low pass filter (LPF) and followed by high pass filter (HPF) filter. Half the components of the frequency were filtered out at the input of the filter and can therefore be sampled down [5]. The original input signal is then rebuilt by the inverse procedure of this decomposition [6].
DWT has an impact on day-to-day processing of image, such as enhancing quality of fingerprint [7], Optimizing watermarking of gray- scale image [8], etc. DWT is used in our present implementation to highlight the different frequency planes in the pictures [9].
2.2 Encrypting EKG Using Discrete Wavelet Transformation (DWT)
In our work, G-plane of a colour picture was selected for performing DWT. The basic and oldest wavelet system is Harr wavelet, A square wave group with an interval range of 1[ 0,1). It is used in many applications, such as the estimation of the SNR of cardiovascular bio-signal, in various theorems of convergence, etc. The higher frequency component hHH plane was divided and the peaks of EKG information were extracted and combined with coefficients in the same plane. This modified hHH plane was used to perform IDWT operation and a modified G-plane was produced. In the original image, this plane was replaced and the colour image containing the Peaks of EKG information was generated. Block diagram to embed the EKG information peaks is shown below. (Fig. 4).
The colour picture obtained was divided while recovering and the G-plane was divided. On this plane, DWT was conducted and the modified higher frequency component hHH plane was removed. Peaks of EKG information are retrieved by dividing the modified G-plane’s coefficients by the original values of hHH. Block diagram below represents the recovery of the Peaks of EKG information (Fig. 4).
2.3 Convolutional Neural Networks(CNNs)
Create EKG signals with time-frequency depictions. These representations are known as scalograms. The absolute value of a signal’s CWT coefficients is a scalogram.
Pre-calculate a CWT filter bank for creating the scalograms. The preferred method for obtaining the CWT of many signals using the same parameters is to precompute the CWT filter bank [10]. Load the scalogram images as an image data store. Split the images into two groups at random, one for training and the other for validation. Use 80% of the images for training, and the rest for validation. For reproducibility purposes, we set the default value to the random seed [11].
Load the neuralnetwork pre-trainedby GoogLeNet. Extract the network layer graph and plot the layer graph [12]. Each layer in the network architecture can be considered a filter. The previous layers recognize more prevalent image characteristics like blobs, edges, and colors. In order to distinguish categories, the subsequent layers concentrate on more particular characteristics.
Replace the last four layers of the network to retrain GoogLeNet to our EKG classification problem. pool5-drop 7 \(\times \) 7 s1’ is a dropout layer, the first of the four layers [12]. With a specified probability, a dropout layer randomly sets input components to zero. To assist avoid over fitting, the dropout layer is used. The default likelihood is 0.5.
Add four new layers to the layer graph: a dropout layer with a 60% dropout probability, a fully connected layer, a softmax layer, and an output classification layer. Set the final fully connected layer to the same size as the new data set’s number of classes. In order to learn more quickly in the new layers than in the layers transferred, the learning rate factors of the fully connected layer increase. Store image dimensions of GoogLeNet in inputSize.
Neural network training is an iterative process involving minimizing a loss function. A gradient descent algorithm is used to minimize the loss function. The gradient of the loss function is assessed in each iteration and the weights of the downward algorithm are updated.
Use validation data to evaluate the network. The accuracy is the same as that recorded on the training visualization figure for validation precision. The scalograms were divided into collections for training and validation. To train GoogLeNet, training collections is used. The perfect way to assess the training outcome is to have the information classified by the network that it has not seen. We considered the accuracy of computed validation as the accuracy of the network.
3 Simulation and Results
The EKG data have been embedded in the hHH plane and the image results are as follows.
Scalograms are created using wavelet-based time-frequency representation model of EKG signals. RGB images are produced from the scalograms. Using the images, the profound CNNs are achieved. There was also exploration of activations of distinct network layers. We have divided the image database into two groups, one for training and another one for validation. 80% of the database has been used for training, and the remainder for validation i.e. 130 images for training and 32 images for validation (Figs. 5, 6, 7, 8, 9).
4 Conclusion
A method of data encryption of EKG signals using wavelet transform is presented. The data for the EKG signal is obtained from physio-net. The wavelet packet decomposition is suggested to decompose the image. The encryption method is introduced to conceal personal information from the patient. Private patient information is integrated within the Image. Encrypted EKG signal is therefore generated by decomposition of the inverse wavelet. The extraction method that distinguishes the image and the EKG signal is then implemented.
The architecture of Deep CNN is then suggested as a methodology for learning features. The proposed CNN network is able to use raw EKG time series signals to acquire and scale down sample features through input vector convolutions with their related weights as well as to determine optimal outputs among nearby neurons.
References
https://healthmetrics.heart.org/at-a-glance-heart-disease-and-stroke-statistics-2019/
Ibrahim, R., Kuan, TS.: PRIS: image processing tool for dealing with criminal cases using steganography technique. In: 2011 Sixth International Conference on Digital Information Management (ICDIM), pp. 193–198, 26–28 September 2011
Liu, T., Pang, C.: Eye-gaze tracking research based on image processing. In: Congress on Image and Signal Processing, CISP 2008, vol. 4, pp. 176–180, 27–30 May 2008
Ye, Z., Mohamadian, H., Ye, Y.: Quantitative effects of discrete wavelet transforms and wavelet packets on aerial digital image denoising. In: 2009 6th International Conference on Electrical Engineering, Computing Science and Automatic Control, CCE, pp. 1–5, 10–13 January 2009
Hasan, M.M., Singh, S.S.: PAPR analysis of FFT and wavelet based OFDM systems for wireless communications. UITS, Dhaka January 2009
Moholkar. S.V., Deshmukh. A.: PAPR analysis of FFT and wavelet based OFDM systems. Int. J. Electron. Commun. Comput. Eng. 5(4) (2014). Technovision. ISSN 2249–071X
Wang, J.-W., Le, N.T., Wang, C.-C., Lee, J.-S.: Enhanced ridge structure for improving fingerprint image quality based on a wavelet domain. IEEE Signal Process. Lett. 22(4), 390–394 (2015)
Ali, M., Wook, A.: Comments on optimized gray-scale image watermarking using DWT-SVD and Firefly algorithm. Short Commun. Expert Syst. Appl. 42, 2392–2394 (2015)
Tang, H., Tong, D., Dong, B., Dillenseger, J.: A new stationary gridline artifact suppression method based on the 2D discrete wavelet transform. Med. Phys. 42, 1721 (2015). https://doi.org/10.1118/1.4914861
Li, T., Zhou, M.: ECG classification using wavelet packet entropy and random forests. Entropy. 18(8), 285 (2016)
Maharaj, E., Alonso, A.: Discriminant analysis of multivariate time series: application to diagnosis based on ECG signals. Comput. Stat. Data Anal. 70, 67–87 (2014)
Russakovsky, O., Deng, J.: Imagenet large scale visual recognition challenge. Int. J. Comput. Vis. 115(3), 211–252 (2015)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
D, T.K., Srinivasan, R.L., N R, R. (2019). Encryption by Heart (EbH) for Secured Data Transmission and CNN Based EKG Signal Classification of Arrhythmia with Normal Data. In: Shankar Sriram, V., Subramaniyaswamy, V., Sasikaladevi, N., Zhang, L., Batten, L., Li, G. (eds) Applications and Techniques in Information Security. ATIS 2019. Communications in Computer and Information Science, vol 1116. Springer, Singapore. https://doi.org/10.1007/978-981-15-0871-4_23
Download citation
DOI: https://doi.org/10.1007/978-981-15-0871-4_23
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-15-0870-7
Online ISBN: 978-981-15-0871-4
eBook Packages: Computer ScienceComputer Science (R0)