Abstract
Digital watermarking at the least significant bit (LSB) for copyright protection is proposed in this paper based on the saliency map. The projected algorithm can embed more information into less perceptive areas within the original image determined by Itti-Koch saliency map. It gives a concept of the areas which has excellent data hiding capacity in an image. The area/region with less perceptibility denotes the most insignificant region from the aspect of visibility in an image, so any modification within these areas will be less evident to any observer. Here the algorithm is being evaluated by means of imperceptibility and robustness. Thus images embed with a watermark will project higher bit capacity.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Digital watermarking
- LSB
- Copyright protection
- Itti-Koch saliency map
- Data hiding capacity
- Imperceptibility
1 Introduction
With the advancement of technology in today’s world, new ideas are coming up every day—both constructive and destructive. These days, digital information can be replicated and reproduced with an ease. To prevent this treachery, few methods are implemented to retain the originality and digital watermarking is one of them [1]. It is a proficient mechanism for copyright protection of digitalized information. In this process data is hidden within an object by some unique ways so that others can’t reach to the original data and later on the data can be extracted by the owner itself [1, 2].
The proposal of this paper is regarding digital image watermarking technique based on Itti-Koch saliency map of an image in which the watermark will be implanted in the less prominent areas of that image. Saliency map signifies visual saliency of a consequent visual sense topographically. It facilitates in evaluating the imperceptibility of an image along with its data embedding capacity. In this proposed technique data hiding is the maximum at those positions where perceptibility is low [3, 4]. By adaptive least significant bit (LSB) substitution technique, the watermark is implanted within the original image [5]. As the bits of watermark are implanted at least significant locations of image, imperceptibility is superior. The data is hidden at numerous places and more than one time to improve the robustness and data hiding capacity [2].
This preliminary introduction about the proposed work is followed by some other sections like description of steps of watermark embedding and the extraction, followed by experimental results and discussions, finally conclusion and reference.
2 Watermark Embedding and Extraction
The process of digital image watermarking proposed here aims to attain the trade-off between robustness and imperceptibility of the watermarked image i.e. the original image embedded with the watermark, through increasing the data hiding capacity by embedding multiple copies of the logo in an effective way [5].
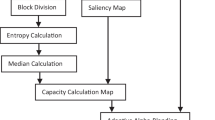
Figure 1 shows the process of encrypting a watermark in an image:
At first the Saliency Map of the original image is produced. Here Itti-Koch algorithm has been followed to produce the map. Hiding capacity estimation is done based on the previous map and main regions where the watermarks can be hidden are approximated. Based on the hiding capacity of the image, the watermark is embedded into it by adaptive LSB replacement process. More bits of the original image are replaced by the bits of the watermark where the original image is more inconspicuous. Thus the Watermarked image is obtained.
Figure 2 provides a scheme of the process of decoding a watermark form a watermarked image.
Saliency map of the original image is produced and hiding capacity estimation of the original image is done as it was done in the encoding process. On the basis of original image & hiding capacity in the original image, LSB is extracted from the pixels of the watermarked image. Adaptive symmetry of the bits of the same order, extracted from different regions of the watermarked image derived from saliency, is computed to retrieve the binary watermark.
2.1 Watermark Embedding and Extraction
The architecture for Itti-Koch model [6] is presented in Fig. 3.
The model unites multi-scale image features into a solo topographical saliency map in a bottom-up approach. Visual pre-processing (presented within the marked enclosure), for every pixel in the pyramid, three color channels R, G, B are generated. Four Gaussian pyramids R(\( \sigma \)), G(\( \sigma \)), B(\( \sigma \)), I(\( \sigma \)) are created from these color channels, where I = \( \frac{{{\text{r}} + {\text{g}} + {\text{b}}}}{3} \), r, g and b are the colors. The projected approach utilizes grayscale images, to obtain the saliency map. Therefore all the three color channels are assigned as gray channels.
In mammals the sensitivity of intensity and contrast is detected by the neurons that are sensitive either to dark centers on bright surroundings or vice versa, is computed in a set of six maps and the center-surround is implemented here as the difference between center and surround scales.
Orientation feature maps encode local orientation contrast between the centers and surround scales. The feature maps are combined into three conspicuity maps, \( {\bar{\text{I}}} \) for Intensity, \( {\bar{\text{C}}} \) for Color, \( {\bar{\text{O}}} \) for Orientation. This three conspicuity maps are normalized and summed to find out the ultimate output \( S \), the saliency map.
2.2 Hiding Capacity Estimation
From the produced saliency map, a hiding capacity estimation map is prepared by using high embedding potency in less perceptible saliency areas and a low embedding potency in areas of more perceptible saliency areas, to acquire enhanced watermark invisibility and to improve the hiding capacity of the embedded watermark.
where \( {\mathcal{S}}_{m} \) is the Saliency map of original gray-scale image \( I_{{o_{m} }} \).
2.3 Encoder and Decoder
Let the original gray-scale image be \( I_{{o_{m} }} \) of size \( {\text{C}} \times {\text{D}} \) and \( \mathcal{W}_{b} \) be the binary watermark with size of \( {\text{P}} \times {\text{Q}} \) and illustrated as:
\( \mathcal{D}_{b} \) is the function for Decimal to Binary conversion and \( \mathcal{B}_{d} \) is the function of converting Binary to Decimal.
The adaptive LSB watermarking is defined as functions \( (\mathcal{F}_{enc} ,\mathcal{F}_{dec}) \).
where \( \mathcal{M} \,\le\, 7 \,-\, (4 \,+\, m){\text{ and }} \mathcal{M} \) is a positive integer with \( m \,=\, \{ 0,1,2,3\} \)
The watermark is implanted only once for every region i.e. \( \mathcal{S}_{{temp_{m} }} \).
So here,
\( I_{w} \) is the watermarked image of size \( C \times D \).
Likewise, for decrypting the watermark, \( \mathcal{S}_{{temp_{m} }} ,I_{{o_{m} }} \;{\text{and }}I_{w} \) are compared to get the region where the watermark has been concealed for every value of \( m \). Let the region be
Now if \( Count_{m} \) be the function to count binary ‘0’ and ‘1’ in LSBs of each pixel of \( \mathcal{E}_{wm} \) in the following manner and the function returns the value of majority to \( \mathcal{C}_{{bit_{m} }} \) where
Then,
For \( m = 0 \) and \( \mathcal{S}_{temp} = 0 \);
For \( m = 1 \) and \( \mathcal{S}_{{temp_{m} }} = 0.25; \)
\( Count \) be the function to count binary ‘0’ and ‘1’ for value at the same positions for \( \mathcal{C}_{{bit_{3} }} ,\mathcal{C}_{{bit_{2} }} ,\mathcal{C}_{{bit_{1} }} \) and the function returns the value of majority to
Then,
where \( \mathcal{C} \) is the decrypted binary watermark.
Hence, following the above processes we get:
3 Results and Discussion
The segment reports the experimental outcomes which have been evaluated through comparative study between the earlier methods and the proposed technique. To study the performance of the proposed algorithm by means of imperceptibility, robustness and hiding capacity, four regularly accessible grayscale test images of size 256 × 256 and single binary watermark image of dimension 16 × 16 are used. The binary watermark image is given in Fig. 4 and the test gray scale images are given in Fig. 5. Figure 6 shows the saliency maps for original grayscale images and Fig. 7 stands for hiding capacity estimation based on the saliency maps where different shades represent different hiding capacity. The black region represents the less perceptible saliency region whereas the white region represents the most perceptible saliency region. Figure 8 illustrates the watermarked Images.
Imperceptibility, in this context, refers to the invisibility of the embedded watermark in the test or original images without corrupting the perceptual quality of watermarking [2, 4, 5]. Table 1 tabularizes the number of quality measures required to check the imperceptibility of the watermarks in the watermarked images.
A considerable degradation of quality or information loss will occur if any means of intentional or unintentional processing is applied on the image. Table 2 presents the average results of performance against different attacks comparing the original watermark and the watermark extracted from the watermarked images under attack. Figure 9 provide recovered watermarks after different image impairments.
To validate the performance of the proposed scheme, a comparison among different algorithms is presented in Table 3. The assessment verifies that the projected approach offer improved imperceptibility and better capacity.
4 Conclusion
In proposed technique saliency map is used as a classifier to distinguish feature of an image based on perceptibility which helps to secure imperceptibility along with robustness of an image. The experimental conclusion implies that the algorithm stand against various attacks with superior hiding capacity. Comparison of the technique with some state of the art technique recommends that projected scheme can be an efficient tool for copyright protection and authentication. Other algorithms may be used in future other than LSB replacement to increase the effectiveness of the watermarking efficiently.
References
Mohanty, S.P.: Digital watermarking: a tutorial review. Report, Department of Electrical Engineering, Indian Institute of Science, Bangalore, India (1999)
Basu, A., et al.: Robust visual information hiding framework based on HVS pixel adaptive LSB replacement (HPALR) technique. Int. J Imaging Robot. 6(A11), 71–98 (2011)
Itti, L., Koch, C.: A saliency-based search mechanism for overt and covert shifts of visual attention. Vision. Res. 40(10–12), 1489–1506 (2000)
Itti, L., Koch, C.: Computational modeling of visual attention. Nat. Rev. Neurosci. 2(3), 194–203 (2001)
Basu, A., Sarkar, S.K.: On the implementation of robust copyright protection scheme using visual attention model. Inf. Secur. J. Global Perspect. 22(1), 10–20 (2013)
Itti, L., Koch, C., Niebur, E.: A model of saliency-based visual attention for rapid scene analysis. IEEE Trans. Pattern Anal. Mach. Intell. 20(11), 1254–1259 (1998)
Chang, C., et al.: Finding optimal least significant-bit substitution in image hiding by dynamic programming strategy. Pattern Recogn. 36, 1583–1595 (2003)
Huan, Xu, et al.: Near-optimal solution to pair-wise LSB matching via an immune programming strategy. Inf. Sci. 180, 1201–1217 (2010)
Mielikainen, Jarno: LSB matching revisited. IEEE Signal Process. Lett. 13(5), 285–287 (2006)
Yang, C.H.: Inverted pattern approach to improve image quality of information hiding by LSB substitution. Pattern Recogn. 41, 2674–2683 (2008)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2015 Springer India
About this paper
Cite this paper
Basu, A., Talukdar, S., Sengupta, N., Kar, A., Chakraborty, S.L., Sarkar, S.K. (2015). On the Implementation of a Saliency Based Digital Watermarking. In: Mandal, J., Satapathy, S., Kumar Sanyal, M., Sarkar, P., Mukhopadhyay, A. (eds) Information Systems Design and Intelligent Applications. Advances in Intelligent Systems and Computing, vol 339. Springer, New Delhi. https://doi.org/10.1007/978-81-322-2250-7_44
Download citation
DOI: https://doi.org/10.1007/978-81-322-2250-7_44
Published:
Publisher Name: Springer, New Delhi
Print ISBN: 978-81-322-2249-1
Online ISBN: 978-81-322-2250-7
eBook Packages: EngineeringEngineering (R0)