Abstract
Wrong medication is an important problem of the citizens of many countries. Using contemporary technologies like UHF Gen-2 RFID tags helps decreasing the medication errors, experienced by many. As UHF Gen-2 tags have limited capacity, cryptographic algorithms cannot be accommodated. The only available functions PRNG and CRC cannot be used instead of cryptographic algorithms. To overcome the known weaknesses, various grouping protocols have been proposed. But, each protocol has some deficiencies. Two of those protocols are covered in this study. Some of their common deficiencies are studied and solutions are suggested.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Patient safety
- Medication error
- RFID
- UHF tag
- EPC Gen 2
- NFC
- ISO 18000-6
- Authentication
- Group proofing protocol
1 Introduction
It is reported that 78 % of the participants in the Eurobarometer survey, on the perception of medical errors, have voted wrong medication as an important problem, in their country [1]. The poll indicates that 23 % of the participants have been directly or indirectly affected, by a medical error. 18 % reported that they experienced a serious medical error, in a hospital. This contradicts the major patient safety goal of avoiding harm caused, during medical care [2]. The need for better patient safety is stated in many works [3, 4].
The medication error definition is given as errors in drug ordering, transcribing, dispensing, administering, or monitoring [2]. This work is concerned with correct drug administering of an inpatient, at the correct time; i.e. drug administration free of humanerrors due to patient-drug pack mismatch. Many technologies are used in hospital automation systems, from high-end servers, to personal digital assistants (PDA), tablets, automatic medicine dispensers (AMD) and recently radio frequency identification (RFID) tags. Doctors and nurses are the users of these technologies and they have tablets, which they know how to use. Some of these tablets even have an integrated tag reader. On the other hand, the patients are the subjects who need to be tracked, correctly. RFID tags are one of the best tools available for identification and tracking of subjects. For example, one of the biggest chain stores of U.S.A., the Walmart, started using RFID tags on its goods, in 2005 [5]. Walmart has gradually replaced traditional paper barcodes with RFID tags. Recently, passive UHF RFID tags have been proposed in inpatient medication. Passive tags are named as such because; they have no battery but are energized by the reader that approaches to read the ID inside the tag. These tags are used as bracelets for inpatients and as tags on medicine packs. Passive UHF tags are preferred because of their low cost and long reading distance, but they have limited resources and lack security primitives. A specific type of passive UHF tag can be read from a few meters. As many as hundreds of tags, can be read per second. According to ISO 18000-6 and EPC Global Class 1 Generation 2 (Gen-2) standards written for UHF tags, they contain only a 16 bit pseudo random number generator (PRNG), a CRC and an XOR function to obscure their messages [6, 7]. Therefore, the capture of the Electronic Product Code (EPC), i.e. the ID of the tag, is not difficult.
A typical RFID set up used in patient identification consists of a back-end database server (server), a reader and a tag (Fig. 1). The server has all the information about a subject: personal information, the unique identification number (ID) of the inpatient’s wristband tag, the ID of the tag on the inpatient’s medicine pack and the pre-shared secrets used for authentication (also stored in the tags).
In the rest of this paper, Sect. 2 summarizes previous work. Sections 3 and 4 demonstrates weaknesses of two latest proposals. Section 5 questions the use of Gen-2 tags and, proposes another type of tag that is better suited for healthcare. Some critical capabilities and characteristics of the two tag types are also compared, in Sect. 5. Section 6 concludes and has the future work.
2 Related Work
Juels et al.’s work [8] is one of the first in identification of a group of objects, using RFID tags. In this work, a grouping proof is defined as the simultaneous reading of two tags at a given timestamp. Other grouping proofs have also been proposed for tags [9]. The weaknesses and recommended security enhancements for grouping proofs in general can be found in [10].
Two of the first proposals to use RFID tags in patient medication were made by Wu et al. and Sun et al. [11, 12]. These pioneering work in inpatient medicine administration, lacked detailed description and advocated the use of personal computers as mobile devices and paper barcodes. Barcodes have limited capabilities and there are disadvantages of their use in patient safety [13].
A proposal where both the inpatient and the medicine are identified by low-cost RFID tags conforming to Gen-2 standard was made by Huang and Ku [14]. The inpatient is assumed to have a wristband with an embedded RFID tag. The inpatient’s medicine container is also marked with a Gen-2 tag. Unfortunately, the security flaws in the grouping proof are demonstrated by Chien et al. [15]; whom suggested an alternative protocol, which is shown to be also vulnerable [16]. The grouping proof protocol schemes, suggest evidence to be generated after the administration of medicine. The evidence is verified later, in the HIS server. False evidence generation, interference with evidence generation procedure, exposure of critical information during evidence creation are some of the problems encountered. The issues arise, because the unsecured messages through the air are eavesdropped by adversaries.
Apart from the above, we demonstrate further weaknesses in two recent works, in Sects. 3 and 4. The two works are specifically chosen because, their authors try to rectify previous vulnerable schemes, but fail because, they do not consider the algebraic attacks outlined in previous works due to non-availability of security primitives, in Gen-2 tags. The works fail because, they do not consider the enhancements neither in [10], nor the algebraic attacks outlined in [17].
3 Case Study I
Our assumptions for both case studies are as follows. While the reader and the server communicate over a secure channel, the tag and the reader’s channel is insecure. The tag has limited resources but the reader has unlimited resources. Therefore, the reader is assumed to support cryptographic algorithms but the tag cannot. The reader is not trusted and a counterfeit reader can be used in the system. Another assumption is that our attacker can listen to the messages between the tag and the reader over the air. The final assumption is the attacker has only passive attack abilities.
The work by Yen et al. analyses some weaknesses of a previous work [16]. The analyzed proposal is the Inpatient Safety RFID System (IS-RFID) of Peris et al. [18]. Skipping the details, the Safe Drug Administration Procedure (SDAP) and the Evi-dence Generation Procedure (EGP) are analyzed. The inexistence of the pre-shared secrets in the SDAP is criticized, but no attack is demonstrated. The EGP is also criti-cized for not being signed by the inpatient, which allows the hospital to re-generate false evidence without inpatient’s awareness. Yen’s proposed rectified scheme is shown in Fig. 2. We demonstrate a disclosure attack on Yen’s rectified scheme, which also succeeds in IS-RFID. The attack will show that all protocols based on obscuring the ID of a tag by the use of the PRNG of a Gen-2 tag are vulnerable.
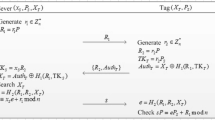
Yen’s proposed offline scheme [16]
Yen proposes one offline and one online solution. Two schemes are the same, except in the online version, the inpatient’s tag is authenticated online by the server, via the nurse PDA. The notation used in Fig. 2 is explained below:
\(\mathrm{ID}_n\), \(\mathrm{ID}_{Pi}\) | ID of a nurse and the tag ID on ith inpatient wristband. |
\(\mathrm{ID}_{ui}\) | Tag ID on a unit dose medicine pack of ith inpatient. |
\(\mathrm{ID}_{uj}\) | Tag ID multiple unit dose medicine packs, j=1,2 ...y. |
\(\mathrm{K}_{Pi}\), \(\mathrm{K}_{ui}\) | Tag key of ith inpatient wristband and ith inpatient’s |
unit dose pack. | |
\(\mathrm{K}_{uj}\) | Tag key of multiple unit dose medicine packs, j=1, ...y. |
\(\mathrm{t}_b\) | Timestamp generated by server. |
\(\mathrm{r}_b\), \(\mathrm{r}_n\), \(\mathrm{r}_p\), \(\mathrm{r}_{uj}\) | Random number generated by server, nurse PDA, inpatient’s |
tag, and jth unit dose, respectively. | |
PRNG() | 16-bit pseudo-random number generation function. |
y | Number of unit doses for ith inpatient. |
\(\mathrm{Rk}_i\) | Key validation value for ith inpatient. |
\(\mathrm{Rk}_{iy}\) | Key validation value for ith inpatient’s unit doses. |
\(\mathrm{e}_i\) | Evidence generated by a nurse for ith inpatient. |
\(\mathrm{m}_{uj}\) | Partial evidence generated by unit-dose tag j, j=1,2 ...y. |
\(\mathrm{m}_{Pi}\) | Partial evidence generated by ith inpatient’s tag. |
\(\mathrm{m}_n\) | Medication evidence generated by a nurse. |
\(\mathrm{Sign}_n\)(m\(_n\)) | Signature function of nurse, that signs evidence \(\mathrm{m}_n\). |
\(\mathrm{Sign}_{Pi}\)(m\(_{Pi}\)) | Signature function of ith inpatient, that signs evidence \(\mathrm{m}_{Pi}\). |
Before starting the round, the nurse makes a request with her ID and downloads all inpatient records from the HIS. The \(\mathrm{daT}_a\) also include the timestamp \(\mathrm{t}_b\) to supervise the time of drug administration. Validation values \(\mathrm{RK}_i\) and \(\mathrm{RK}_{iy}\) are formed by using the pre-shared key of the inpatient’s tag and the corresponding unit-dose key, respectively. The nurse starts the round and sends the same request both to the inpatient and the unit-dose tags, with a reader equipped PDA. Using the HIS nonce r\(_b\), the inpatient tag replies with PRNG(\(\mathrm{ID}_{Pi} \oplus \) \(\mathrm{r}_b \oplus \) \(\mathrm{K}_{Pi}\)) and every unit-dose tag replies with {PRNG(\(\mathrm{ID}_{uj} \oplus \) \(\mathrm{r}_b\)), PRNG(\(\mathrm{K}_{uj} \oplus \) \(\mathrm{r}_b\))}, where j=1,2, ...,y. Upon receiving the replies, the PDA matches the inpatient tag’s reply with \(\mathrm{RK}_i\) to identify and authenticate the inpatient. Next, the PDA uses the \(\mathrm{RK}{_iy}\) to identify and authenticate the unit-dose packs. If all matching is good, the PDA generates its own nonce \(\mathrm{r}_n\) and sends it with the timestamp of the HIS to every unit-dose pack. The unit-dose packs generate their own nonce and use it together with nurse PDA’s nonce to prepare a partial medication evidence \(\mathrm{m}_{uj}\) = PRNG[PRNG (\(\mathrm{ID}_{uj}\)) \(\oplus \) \(\mathrm{r}_{uj} \oplus \) PRNG(\(\mathrm{t}_b\)) \(\oplus \) \(\mathrm{r}_n \oplus \)PRNG (\(\mathrm{K}_{uj}\))], where j=1, 2, ..., y. Each unit-dose sends back its reply to the nurse PDA. The PDA stores every nonce \(\mathrm{r}_{uj}\) sent and calculates \(\mathrm{m}_{xu}\), by XORing every \(\mathrm{m}_{uj}\). The value \(\mathrm{m}_{xu}\) is sent to inpatient’s tag. The inpatient’s tag prepares its partial evidence \(\mathrm{m}_{Pi}\) = PRNG(PRNG(\(\mathrm{ID}_{Pi}\))\(\oplus \) \(\mathrm{r}_{P} \oplus \)PRNG(\(\mathrm{K}_{Pi}\))\(\oplus \) \(\mathrm{m}_{xu}\)), after generating a nonce reply \(\mathrm{r}_P\). Finally the inpatient tag signs its evidence \(\mathrm{Sign}_{Pi}\)(\(\mathrm{m}_{Pi}\)) and sends the tuple {\(\mathrm{r}_P\), \(\mathrm{m}_{Pi}\), \(\mathrm{Sign}_{Pi}\)(\(\mathrm{m}_{Pi}\))} to the nurse PDA. Upon receiving the final partial evidence, the nurse PDA prepares a final medication evidence m\(_n\). The evidence is signed and saved in the PDA, as \(\mathrm{m}_n\), \(\mathrm{Sign}_n\)(\(\mathrm{m}_n\)). At the end of the round, the nurse returns to the nurse station and uploads all of the drug administration evidence to the HIS. It is the duty of HIS to check and find if there have been any medication errors.
Neither the inpatient’s tag nor the nurse PDA digital signature functions are explained. The assumption of inpatient’s tag having the computational ability of generating digital signatures is way out of the ISO 18000-6 and Gen-2 standards [6, 7]. But, even this assumption cannot save the scheme.
3.1 Disclosure Attack Scenario on Yen’s Protocol
The 16 bit PRNG function of the Gen-2 tags is public and available [19]. According to Yen, any PRNG(x) is calculated for a given input x; e.g. using (ID\(_{Pi}{\oplus }\mathrm{{r}}_b\oplus \)K\(_{Pi}\)) as input, a deterministic output PRNG(\(\mathrm{ID}_{Pi}\oplus \mathrm{r}_b{\oplus }\mathrm{K}_{Pi}\)) is obtained and matched with \(\mathrm{R}_i\). Therefore, a table of \(\mathrm{2}^{16}\) (65,536) possible inputs against calculated outputs can be prepared beforehand, as in Table 1. Looking at the table, the corresponding output of an input or the corresponding input of an output can be found, easily. PRNG may produce the same output for the distinct values, but this shows the weakness of the PRNG which is not a desirable property. In that case much more trial and errors are needed.
The inpatient desired to be administered wrong medication is the “target". Another inpatient whose identity is going to be illegally given to the target is called the “conveyor". The goal is to cause repeated switch of medicine administrations of the target and conveyer, without getting detected. After exposing the (\(\mathrm{ID}_{Pi} \oplus \mathrm{K}_{Pi}\)) of the conveyer and the target; the identities are switched and detection is avoided.
An adversary/attacker acts as a visitor and goes near the conveyer with a rogue reader. Rogue or untrusted readers are assumed to be always present in open environments [16, 18]. The attacker sends a request request, \(\mathrm{r}_a\), where \(\mathrm{r}_a\) is the attacker’s constant nonce. The tag answers with PRNG(\(\mathrm{ID}_{Pi} \oplus \mathrm{r}_a \oplus \mathrm{K}_{Pi}\)). The output column of the table is searched and the corresponding input; e.g. input1, is found: input1 = (\(\mathrm{ID}_{Pi} \oplus \mathrm{r}_a \oplus \mathrm{K}_{Pi}\)). Then, (\(\mathrm{ID}_{Pi} \oplus \mathrm{K}_{Pi}\)) = \(input1 \oplus \mathrm{r}_a\). (\(\mathrm{ID}_{Pi} \oplus \mathrm{K}_{Pi}\)) is constant for any given inpatient; therefore any inpatient is uniquely identified. Using the replies of the unit-dose packs with Table 1 and XORing each {PRNG(\(\mathrm{ID}_{uj} \oplus \mathrm{r}_a\)), PRNG(\(\mathrm{K}_{uj} \oplus \mathrm{r}_a\))} with \(\mathrm{r}_a\), all values of ID\(uj\) and \(\mathrm{K}uj\) are exposed for j = 1, 2, ..., y. The same attack is repeated at the target. At the end, both the target and conveyor’s (\(\mathrm{ID}_{Pi} \oplus \mathrm{K}_{Pi}\)), \(\mathrm{ID}uj\) and \(\mathrm{K}uj\) are captured.
Next, the evidence generation procedure of the target and conveyor are eavesdropped for just one round. The messages {\(\mathrm{r}_{uj}\), \(\mathrm{m}_{uj}\)} of the unit-dose packs in Fig. 2 are recorded, by the attacker. The value of \(\mathrm{m}_{xu}\), sent to the conveyor is also recorded. The final reply {\(\mathrm{r}_P\), \(\mathrm{m}_{Pi}\), \(\mathrm{Sign}_{Pi}\)(m\(_{Pi}\))} of the conveyor is analyzed next. The values not known in m\(_{Pi}\) = PRNG(PRNG(ID\(_{Pi}\)) \(\oplus \) r\(_P\) \(\oplus \) PRNG(K\(_{Pi}\))\(\oplus \)m\(_{xu}\)) are PRNG (ID\(_{Pi}\)) and PRNG(K\(_{Pi}\)). But the value [PRNG(ID\(_{Pi}\))\(\oplus \)PRNG(K\(_{Pi}\))] is constant and can be exposed. Looking at the output column of Table 1, a match for the value of m\(_{Pi}\) is found, e.g. output1. Using output1, [PRNG(ID\(_{Pi}\))\(\oplus \)PRNG(K\(_{Pi}\))] = output1\(\oplus \)r\(_P\) \(\oplus \)m\(_{xu}\) is obtained. The only unknown left is Sign\(_{Pi}\)(m\(_{Pi}\)). The available functions in a Gen-2 tag are PRNG, CRC and XOR operation. Therefore, the assumed out-of-standard, digital signature is most likely to be a deterministic function that has its own 65,536 (216) entry table. Whatever it is, it has to be public and readily available to all tags. Either we have the function and we can construct Sign\(_{Pi}\)(m\(_{Pi}\)) out of m\(_{Pi}\) or the attacker records the m\(_{Pi}\), Sign\(_{Pi}\)(m\(_{Pi}\)) pairs, as a table called Table X. Therefore, the attacker has the m\(_{Pi}\), Sign\(_{Pi}\)(m\(_{Pi}\)) pair. The same is repeated near the target.
The attacker takes the exposed values (ID\(_{Pi} \oplus \)K\(_{Pi}\)), [PRNG(ID\(_{Pi}\)) \(\oplus \) PRNG (K\(_{Pi}\))], Sign\(_{Pi}\)() function or Table X, for the target and conveyor and writes them into two different tag emulators, at a private location. Such a hardware device emulating an RFID tag is the Chameleon [20]. We do not intend to implement any, but there are works on RFID tag emulators [21]. The difference from the real tag is that the emulator uses the XORed (ID\(_{Pi} \oplus \) K\(_{Pi}\)), [PRNG(ID\(_{Pi}\))\(\oplus \)PRNG(K\(_{Pi}\))] values instead of individual values to form its replies.
In the final step of the attack, the tag emulator of the target is placed next to the conveyor and the emulator of the conveyor is placed next to the target. Hence, the switch of the identities is completed. The nurse cannot notice the presence of the switch, because she does not come close to the UHF tags. When the nurse follows normal procedure, the rogue tags generate correct RK\(_i\), RK\(_iy\) and partial evidences. The nurse administers wrong medicine to both patients, signs the evidence and sends them to the HIS. The HIS cannot detect the switch and wrong medication is repeated until the target and impatient show diverse symptoms.
Yen’s protocol has another weakness, as well. Blocking {t\(_b\), r\(_n\)} or m\(_{xu}\), and sending bogus instead stop the medication procedure. The medication in a clinic can be disrupted with a strong, bogus transmission.
4 Case Study II
A second work criticizing a previous proposal which uses Gen-2 RFID tags is by Wu et al. [22]. Wu criticizes Yu et al.’s proposal for being based on a fully analyzed protocol [23]. We leave the study of Yu’s proposal outside the scope of this work, because we would like to concentrate on Wu’s rectified protocol. Wu’s proposal is summarized in Fig. 3. The proposal also uses the 16-bit PRNG function of Gen-2 tags to form authenticators and prove the simultaneous existence of two tags, in the same electromagnetic field.
At the beginning the server pre-shares secrets X\(_a\) and X\(_b\) with tags T\(_a\) and T\(_b\), respectively. Typically, the reader challenges both the inpatient and unit-dose tag with the same timestamp, t. Both tags reply with their index-pseudonym (IDS), a nonce and a tag authenticator; {IDS\(_a\), r\(_a\), v\(_a\)} and {IDS\(_b\), r\(_b\), v\(_b\)} respectively. The index-pseudonym is a pseudo ID of the tag that is an updated version of constant ID, every round. The reader is online with the back-end server and sends the tag replies together with the timestamp to the server. If verification is good, the server sends two keys K\(_a\), K\(_b\) to the reader. Without waiting for a reply, the server immediately updates IDS\(_a\) and IDS\(_b\). Using the key Ka, the reader calculates its authenticator \(\alpha _a\) and sends {\(\alpha _a\), IDS\(_b\), t} to tag T\(_a\). T\(_a\) calculates its own \(\alpha ^{'}_{a}\) and matches it with the received \(\alpha _a\). If they are a match, T\(_a\) prepares \(\beta _a\) and partial evidence ma and sends them to the reader. Then, T\(_a\) updates. The reader verifies \(\beta _a\) and then prepares its authenticator \(\alpha _b\) and sends {\(\alpha _b\), IDS\(_a\), m\(_a\)} to tag T\(_b\). Using its own key, T\(_b\) verifies \(\alpha _b\); then, computes its second authenticator \(\beta _b\), partial evidence mb and sends them to the reader. Then, T\(_b\) updates its IDS\(_b\). Upon receiving {\(\beta _b\), mb}, the reader verifies \(\beta _b\) and then concludes that T\(_a\) and T\(_b\) exist in the field, simultaneously. Finally, the reader accumulates {IDS\(_a\), IDS\(_b\), t, m\(_a\), m\(_b\)} in a tuple, as a proof and, sends it to the back-end server. Notice that the reader does not update, at the end.
Wu uses a random permutation function F while calculating the authenticators and partial evidences. Wu claims F to be a one way function that uses only the PRNG and XOR operation available in a Gen-2 tag. The implementation of F function is shown by an example. Let M = (m\(_0\), m\(_1\), m\(_2\), m\(_3\)), C = (c\(_0\), c\(_1\), c\(_2\), c\(_3\)), D = (d\(_0\), d\(_1\), d\(_2\), d\(_3\)), E = (e\(_0\), e\(_1\), e\(_2\), e\(_3\)), where m\(_i\), c\(_i\), d\(_i\), e\(_i\) and \(\gamma \) are all 16-bit numbers. Function \(\gamma \) = P(E) = PRNG(PRNG(PRNG(PRNG(e\(_0\))\(\oplus \)e\(_1\))\(\oplus \)e\(_2\))\(\oplus \)e\(_3\)). For C = F(M); c\(_0\) = P(m\(_0\), m\(_1\), m\(_2\), m\(_3\)), c\(_1\) = P(m\(_1\), m\(_2\), m\(_3\), m\(_0\)), c\(_2\) = P(m\(_2\), m\(_3\), m\(_0\), m\(_1\)), c\(_3\) = P(m\(_3\), m\(_0\), m\(_1\), m\(_2\)). In brief, F(M) is a total of 16 nested PRNG and 12 XOR operations. Since F is a public function, for any known input, F(x) can be calculated. Therefore, a table similar to that of Table 1 in Sect. 3.1 can be prepared. Only the preparation of the table -called Table X- is computationally more intensive than the preparation of Table 1, but it will have 216 (65,536) possible inputs and corresponding outputs as Table 1. Referring to the input and output columns of Table X is no different than that of Table 1 and takes very short time. Additionally, F(F(x)) is the application of F function on the result of F(x), i.e. 32 PRNG and 24 XOR operations.
The scheme of work [22]
4.1 Attacks on Wu’s Scheme
Exposure Attack. The exposure attack on the protocol is similar to the attack in Sect. 3.1. The adversary challenges the tags, with a bogus timestamp t. In the replies of tags, the IDS and nonce values are recorded, then the authenticators v\(_a\) and v\(_b\), are analyzed.
Referring to the hypothetical Table X, the value of v\(_a\) is used as an output and the corresponding input -called input\(_va\)- is read. From Fig. 3:
The nonces r\(_a\), r\(_b\), IDS\(_a\), IDS\(_b\) and the timestamp t are in clear text and the value of F(t) is found from the output column of Table X. Hence, by XORing the found input\(_va\) with the known values F(Y\(_a\)) is exposed (Eq. 2). Using the exposed F(Y\(_a\)) in the output column of Table X, the value in the input column gives Y\(_a\). Following the same steps Y\(_b\) is also exposed. The eys K\(_a\), K\(_b\) are calculated using the newly exposed Y\(_a\) and Y\(_b\), the nonces r\(_a\) and r\(_b\). Next, the updated values of Y\(_a\) and Y\(_b\) are also exposed. The updated values of IDS\(_a\) and IDS\(_b\) depend on the current values and the updated values of Y\(_a\) and Y\(_b\), exposed in the previous step. Thus, the adversary also obtains the updated values of IDS\(_a\), IDS\(_b\). Without eavesdropping any message exchanges the adversary captures Y\(_a\), Y\(_b\), K\(_a\), K\(_b\) and updated values of Y\(_a\), Y\(_b\), IDS\(_a\), IDS\(_b\).
The attack continues by eavesdropping one complete round. When the reader sends {\(\alpha _a\), IDS\(_b\), t} to Ta, the attacker waits for the reply {\(\beta _a\), m\(_a\)}. Using the value of \(m_{a}\) in the output column, a corresponding input – call it input \(m_{a}\) - is read:
Hence, the pre-shared secret X\(_a\) is captured (Eq. 4). The message {\(\alpha _b\), IDS\(_a\), m\(_a\)} is of no importance because its terms are captured values. The reply {\(\beta _b\), m\(_b\)} of T\(_b\) gives away the pre-shared secret X\(_b\), after a similar analysis of m\(_b\), as in m\(_a\). Hence, the adversary has the shared secrets X\(_a\) and X\(_b\), necessary for the creation of rogue tags. The rest of the attack is the same as in Sect. 3.1. The attacker loads the captured values into two rogue tags, switching the identities of the target and conveyor. The result is wrong medication of a targeted inpatient, possibly causing deadly conditions.
De-synchronization Attack. The protocol of Fig. 3 is also vulnerable to de-synchronization attack, at many points. De-synchronization happens when one of the partners of the message exchange update some shared terms to new values, while the other does not. If the old values are not stored, then there is no way for mutual authentication to take place, with mismatched values. For example, consider the moment when the reader sends the messages {IDS\(_a\), r\(a\), v\(_a\)} and {IDS\(_b\), r\(b\), v\(_b\)}, to the server. After calculating and sending the keys, the server updates. If the reader does not get the keys (loss of power), or cannot continue communication with the tags, then the server is de-synchronized with the tags; because the tags have not been updated. During the retry, the reader obtains and sends the old {IDS\(_a\), r\(a\), v\(_a\)} and {IDS\(_b\), r\(b\), v\(_b\)}. The server never finds the old values in its database to verify the tags. In total, there are four instances that can cause de-synchronization: the reply of the server to the reader, the message exchange between the reader and T\(_a\), the message of reader to T\(_b\). Extra care is necessary in protocols that use updating, because de-synchronization halts medication.
4.2 Computational Load of Wu’s Scheme on Gen-2 Tags
Looking at Fig. 3, the most intensive computations in tags take place, after receiving authenticator (\(\alpha _a\), \(\alpha _b\)) of the reader. Counting the number of F function and XOR operations from the instant of computing Ka until sending {\(\beta _a\), m\(_a\)} (assuming update can take place after sending {\(\beta _a\), m\(_a\)}); Ta has a larger computational load with nine F function and seven XOR operations. Every F function involves sixteen PRNG and twelve XOR operations. Hence, Ta makes 144 PRNG and 115 XOR operations. A PRNG consumes around 190 clock cycles to produce a random number [24]. Assuming a 16-bit architecture, each XOR operation takes one clock. In total, Ta spends 27,475 (144\(\times \)190+115) clock cycles in computations. This is around 26 times more than an 8-bit AES implementation, which consumes 1032 clock cycles [25]. In other words, Wu’s proposal cannot meet the limits, as it exceeds 220 clock cycles [26].
5 Discussions
As demonstrated, Yen’s and Wu’s schemes are as vulnerable as their predecessors, which contradict the major safety goals [2, 4]. Wu’s scheme cannot fit in a Gen-2 tag, is vulnerable and has the same characteristics of Wu’s and Yen’s protocols; therefore, it will not be discussed any further. The reason of the disclosure of critical data by our attacks is a result of using the only available function PRNG, as an encryption function. To the best of our knowledge there is no formal proof of using a PRNG as an encryption or hashing algorithm [19]. For patient safety, confidentiality of critical data has to be provided by true encryption. In other words, an alternative with stronger cryptographic primitives is necessary, instead of the 16-bit PRNG function of ISO 18000-6 or EPC Gen-2 tags, which are used for commercial goods in supply chains. Bit size of PRNG can be extended to 64 or more bits to increase the search space of the unknowns given as input to the PRNG which makes creating a table and searching through the table unaffordable. Even more, PRNG function can be replaced by a better cryptographic function. But these extensions mean to change the EPC Gen2 standard.
5.1 Ambiguities and Disadvantages of Yen’s Proposal
Yen’s proposal carries over the ambiguities of the work it criticizes. Even if PRNG is accepted as the only viable option, a special tag is required to calculate values like PRNG(ID\(_{Pi} \oplus \)r\(_b \oplus \) K\(_{Pi}\)), because in regular EPC Gen 2 tags PRNG function doesn’t have any input parameters. Another unexplained assumption is the digital signing ability of the tags. This assumption is highly questionable as the only available option is a PRNG and suggesting its use in digital signing is totally unacceptable. An unconsidered but possible scenario is the presence of more than one inpatient, in the same room. UHF tags are read in numbers from a few meters away. Thus, it is not possible to identify which inpatient’s tag is read, if there are many in a room. With equal distance from two inpatients, a nurse can give the other patient’s medicine to the intended patient. The aftermath of a complication at an inpatient is not considered, either. The medication responsibility of other inpatients, while a previous inpatient is going through a complication, is ambiguous. The continuation of medication with the same PDA, by a second nurse is not good. If a wrong medication is detected, the first nurse is falsely blamed. Using a second nurse PDA causes a discontinuation of the inpatient tuples and requires server intervention; since every nurse downloads inpatient data with her own PDA/password.
In their security analysis, Yen et al. claim that data confidentiality of their protocol is guaranteed. However, the identities and keys of the inpatients are exposed after our full disclosure attack, even though they are not transferred in plaintext.
Not only that, Yen’s system has disadvantages, as well. A disadvantage is dedicating a PDA for every nurse, which is neither widely available nor cheap. UHF readers in the form of PDAs are uncommon and expensive. This increases the overall cost in hospitals, where there are many clinics and many shifts. Finally, the lack of consideration of Health Level 7 (HL7) standards is another disadvantage, because any incompliant solution is unlikely to be endorsed [27]. Not paying attention to HL7 standards is partly the reason of vulnerabilities; especially the mutual authentication requirement. Various attacks on ISO 18000-6 RFID are explained in detail [10, 17, 28]. In brief, there are four types of attacks: Interception, interruption, modification and fabrication attacks. Each attack has some counter measures, but they are not enough to guarantee patient safety, simply because of the limited resources of the tags, in question.
5.2 Security Vulnerabilities of Wu’s Scheme
In their security evaluation, Wu et al. [22] defends that impersonation, ID-Theft and clone attacks cannot be launched against their protocol. Contrarily, our full disclosure attack exposes the secret keys, which opens the avenue to generating false grouping proof evidence. Not only that, our attack demonstrates how a fake tag (clone) can be devised to alter the identity of an impatient. Therefore, their clone attack evaluation is also unsatisfactory. Besides the successful impersonation and clone attacks, a de-synchronization attack is demonstrated above, an attack type they fail to evaluate in their analysis.
5.3 Suitable Technology for Patient Safety: NFC
A viable alternative technology is the near field communication (NFC) tags, because they possess the desired characteristics and cryptographic primitives. For example, Mifare DesFire version EV1 (EV1) tag has a built in AES engine [29]. If this feature existed in ISO 18000-6 tags, both of our PRNG table attacks would have been ineffective. Definitely, the existence of an AES engine provides better patient data safety. Another important characteristic that would have prevented our attacks is the operating distance. EV1 is read from a distance of 20–100 mm, therefore the nurse has to approach intentionally very close to an inpatient. Such a physical requirement removes the danger of eavesdropping by an adversary from meters away and the danger of reading a rogue tag.
The characteristics of EPC Gen-2 and EV1 tags that impact medicine administration are compared, in Table 2. Apart from the encryption and reading distance advantages, the NFC tags have other advantages over the EPC Gen-2 tags. Data integrity of the exchanged messages is an important security characteristic. Any multiple changes in the transmitted messages should be detected. As observed from the table, EV1 provides better data integrity algorithms. But, a property where EPC Gen-2 technology performs better is the number of tags read per second. A nurse can read only maximum one NFC tag/s, because physically she has to approach and momentarily touch the tag. But, this does not provide an advantage over NFC tags because; there is no hurry to read many inpatient tags. The memory capacity of EV1 tags surpasses the EPC Gen-2 tags. This is important because future protocols and schemes have a better chance to be accommodated on a spacious EV1 tag. User developed security applications or extended secrets can be stored in EV1. The ISO standards of the two technologies are different. But, the ISO 14443A standard is meant for the smartcards, clearly a higher class technology than the ISO 18000-6 standard.
Another important parameter of the EV1 is its 3-way mutual authentication. As given in Fig. 4, a new session key is created for each session through a pre-shared key. Simply, the authentication is based on the verification of the exchanged encrypted nonces.
The use of strong cryptographic primitives instead of a simple 16-bit PRNG function increases the security level but also leads to other hardware requirements. Therefore, one would expect to see a considerably more expensive cost for the higher NFC technology solution. But, this is not the case. The NFC tag prices are higher than the UHF tags, but the total cost for a complete solution is not. In his cost analysis, Peris et al. calculate a total cost for a floor with 5000 inpatients/year, 3 unit-dose/day, 3 nurses on each floor and an average hospital with 8 floors [18]. The cost of the HIS and AMD are excluded, because those are included in the overall cost of the hospital. The cost of an EPC Gen-2 tag is given as $0.5/tag, including the plastic package of each unit-dose. Every nurse is equipped with a PDA, astonishingly priced at $300. The total number of tags used for the inpatients and the unit doses is 20,000/year; mistakenly taken as 15,000/year by Peris et al. In the end, Peris et al. conclude with a cost of $70,000/year, for his proposal. An NFC tag costs $0.421 to $0.825, depending on the size of the order. Hence, the NFC tags are more expensive than EPC Gen-2 tags, as expected. But, to the best of our knowledge, a mobile UHF Gen-2 reader is around $1027. On the other hand, a popular NFC enabled tablet (Google Nexus 7) costs around $199. Therefore, there is a 5:1 price ratio, in favor of NFC readers. Obviously, even with the most expensive NFC tag, our solution ($21,300) is less expensive than that of Peris et al.’s.
6 Conclusion
The weaknesses of ISO-18000-6 or Gen-2 tags in safe drug administration are obvious, following the various attacks presented in this and previous work. As demonstrated the analyzed protocols fail their data confidentiality claims. The use of PRNG as an encryption algorithm is a major drawback. On the other hand, those proposals that try to provide stronger encryption by nested PRNG operations, cannot meet the time limits of RFID tags. With so many weaknesses and disadvantages, EPC Gen-2 type tags cannot increase inpatient medication safety.
There is a need for tags with cryptographic primitives, intentional tag reading characteristics and longer key sizes. State of the art NFC tags are a viable alternative. The previous works suggest the use of non-standard operations and special equipment. The contemporary, less expensive and widely available NFC enabled tablets are better suited for the job. The comparison of EPC Gen-2 and NFC tag technologies indicate that NFC is a better viability. Currently, a proposal using the NFC technology and strong security is underway, in our lab. An authentication based on EV1 mutual authentication structure will be the future work. Another alternative to increase the security is using public-key cryptography as indicated in [30], but the huge clock cycle (66,048) of using that alternative affects usability of the system.
References
Eurobarometer 2006 survey on medical errors. Technical Report, October 2005 (2006)
Kaushal, R., Bates, D.W., Landrigan, C., McKenna, K.J., Clapp, M.D., Federico, F., Goldmann, D.A.: Medication errors and adverse drug events in pediatric inpatients. JAMA 285(16), 2114–2120 (2001)
Reporting, E., Meaders, S., Hickner, J., Kuo, G.M., Fagnan, L.J., Forjuoh, S.N., Stevens, B.K., Pace, W.D., Hamlin, B.N., Scherer, H., Hudson, B.L., Oppenheimer, C.C.: Field test results of a new ambulatory care medication error and adverse drug. Ann. Family Med. 8, 517–525 (2010)
2010 National Patient Safety Goals (NPSGs) (2010)
Wal-Mart details its RFID journey. http://www.computerworld.com/s/article/109132/Wal_Mart_details_its_RFID_journey
Information technology - Radio frequency identification for item management - Part 6: Parameters for air interface communications at 860 MHz to 960 MHz. http://www.iso.org/iso/iso_catalogue/catalogue_tc/catalogue_detail.htm?csnumber=46149
Prop, E.I.: EPC Global Class1 Gen2 RFID Specifications, December 2005 (2006)
Juels, A.: Yoking-proofs for RFID tags. In: Second IEEE Annual Conference on Pervasive Computing and Communications Workshops, pp. 14–17, 138–143. IEEE Press, New York (2004)
Saito, J., Sakurai, K.: Grouping proof for RFID tags. In: Conference on Advanced Information Networking and Applications, pp. 621–624. Taichung (2005)
Peris-Lopez, P., Orfila, A., Hernandez-Castro, J.C., van der Lubbe, J.C.: Flaws on RFID grouping-proofs. Guidelines for future sound protocols. J. Netw. Comput. Appl. 34(3), 833–845 (2011)
Wu, F., Kuo, F., Liu, L.W.: The application of RFID on drug safety of inpatient nursing healthcare. In: 7th International Conference on Electronic Commerce, pp. 85–92, New York (2005)
Sun, P.R., Wang, B.H., Wu, F.: A new method to guard inpatient medication safety by the implementation of RFID. J. Med. Sys. 32, 327–332 (2008)
Chen, C.-L., Wu, C.-Y.: Using RFID yoking proof protocol to enhance inpatient medication safety. J. Med. Sys. 36, 2849–2864 (2012)
Huang, H.H., Ku, C.Y.: A RFID grouping proof protocol for medication safety of inpatient. J. Med. Sys. 33(6), 467–474 (2008)
Chien, H.Y., Yang, C.C., Wu, T.C., Lee, C.F.: Two RFID-based solutions to enhance inpatient medication safety. J. Med. Sys. 35(3), 369–375 (2011)
Yen, Y.C., Lo, N.W., Wu, T.C.: Two RFID-based solutions for secure inpatient medication administration. J. Med. Sys. 36(5), 2769–2778 (2012)
van Deursen, T., Radomirović, S.: Algebraic attacks on RFID protocols. In: Markowitch, O., Bilas, A., Hoepman, J.-H., Mitchell, C.J., Quisquater, J.-J. (eds.) WISTP 2009. LNCS, vol. 5746, pp. 38–51. Springer, Heidelberg (2009)
Peris-Lopez, P., Orfila, A., Mitrokotsa, A., van der Lubbe, J.C.A.: A comprehensive RFID solution to enhance inpatient medication safety. Int. J. Med. Inform. 80, 13–24 (2011)
Wickboldt, A.K., Piramuthu, S.: Patient safety through RFID: vulnerabilities in recently proposed grouping protocols. J. Med. Sys. 36(2), 431–435 (2012)
Kasper, T., von Maurich, I., Oswald, D., Paar, C.: Chameleon: a versatile emulator for contactless smartcards. In: Rhee, K.-H., Nyang, D. (eds.) ICISC 2010. LNCS, vol. 6829, pp. 189–206. Springer, Heidelberg (2011)
Redemske, R., Fletcher, R.: Design of UHF RFID emulators with applications to RFID testing and data transport. In: Fourth IEEE Workshop on Automatic Identification Advanced Technologies (AutoID 2005), pp. 193–198 (2005)
Wu, S., Chen, K., Zhu, Y.: A secure lightweight RFID binding proof protocol for medication errors and patient safety. J. Med. Sys. 36(5), 2743–2749 (2012)
Yu, Y.C., Hou, T.W., Chiang, T.C.: Low cost RFID real lightweight binding proof protocol for medication errors and patient safety. J. Med. Sys. 36(2), 823–828 (2012)
Peris-Lopez, P., Hernandez-Castro, J.C., Estevez-Tapiador, J.M., Ribagorda, A.: LAMED—A PRNG for EPC Class-1 Generation-2 RFID specification. Comput. Stand. Interfaces 31(1), 88–97 (2009)
Feldhofer, M., Wolkerstorfer, J.: Hardware implementation of symmetric algorithms for RFID security. In: Kitsos, P., Zhang, Y. (eds.) RFID Security, pp. 373–415. Springer, New York (2009)
Martín, H., Millán, E.S., Entrena, L., César, J., Castro, H.: AKARI-X: a pseudorandom number generator for secure lightweight systems. In: 17th IEEE IOLTS, pp. 228–233 (2011)
Health Level Seven International. http://www.hl7.org/implement/standards/index.cfm?ref=nav
Hawrylak, P.J., Schimke, N., Hale, J., Papa, M.: Security risks associated with radio frequency identification in medical environments. J. Med. Sys. 536(6), 3491–3505 (2012)
Mifare DesFire EV1 Leaflet. http://www.nxp.com/products/identification_and_security/smart_card_ics/mifare_smart_card_ics/mifare_desfire/
Oren, Y., Box, P.O.: A low-resource public-key identification scheme for RFID tags and sensor nodes a brief description of the protocol. In: WiSec 2009, pp. 59–68 (2009)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2013 Springer-Verlag Berlin Heidelberg
About this paper
Cite this paper
Özcanhan, M.H., Dalkılıç, G., Utku, S. (2013). Is NFC a Better Option Instead of EPC Gen-2 in Safe Medication of Inpatients. In: Hutter, M., Schmidt, JM. (eds) Radio Frequency Identification. RFIDSec 2013. Lecture Notes in Computer Science(), vol 8262. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-41332-2_2
Download citation
DOI: https://doi.org/10.1007/978-3-642-41332-2_2
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-642-41331-5
Online ISBN: 978-3-642-41332-2
eBook Packages: Computer ScienceComputer Science (R0)