Abstract
External disturbances, such as interference, have a significant impact on the functionality of radio detection and ranging (radar) systems, which are employed for the identification, ranging, and imaging of target objects. As radar systems are increasingly adopted across various sectors for different applications, it is essential to handle interference issues appropriately to mitigate false detections, poor signal-to-noise ratio (SNR), and reduced resolution. In the current paper, we introduce a Long Short-Term Memory (LSTM)—based multi-layer recurrent neural network (RNN) to tackle interference problems in a multi-radar setting. In the simulation, a 4-layered LSTM-RNN is trained with 50 different chirp rate interference signals. The efficiency of the introduced interference mitigation technique is evaluated by testing the randomly selected coherently interfered signals, non-coherently interfered signals, and a combination of both on the trained model. The LSTM-RNN effectively suppresses ghost targets in the range profile in the case of coherently interfered signals. Furthermore, the LSTM-RNN enhances the signal-to-interference noise ratio (SINR) by > 18dB in all cases. Thus, the proposed LSTM-RNN offers a promising solution to improve the accuracy and reliability of radar operation in multi-radar environments.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
In today’s context, radio detection and ranging systems (radars) are extensively utilized across various domains, ranging from remote sensing, defense, agriculture, industry, and automotive to consumer electronics [1,2,3]. With the growing number of radar deployments, signals originating from external radars often referred to as interferers, spoofers or intruders can introduce disturbances to the legitimate radar, also known as victim radar (VR). One significant disturbance is the signal arising from the interferer radar (IR) which is operating at the same or nearby frequency band as the VR. The IR signal can significantly impact the performance of the VR by adding external noise, introducing ghost signals, and deteriorating the waveform of the VR. In a multi-radar scenario, these degradations can lead to a poor detection capability of the VR and impose threats to the safe and secure operation of radar systems. Consequently, effective interference handling becomes crucial.
To address the effect of external interference/intrusion in radar systems, various methods have been proposed, such as the development of noise waveform-based radars [4, 5], interference-tolerant waveforms [6, 7], wavelet denoising techniques [8], adaptive beamforming techniques [9, 10], and more. Additionally, recently deep learning (DL)-based interference mitigation techniques have gained attention to the radar research community, as these techniques can reconstruct the echo signal by suppressing the interference and can be applied regardless of the VR and IR signal types [11,12,13,14,15]. Among different DL techniques, convolution neural networks (CNN) based interference mitigation techniques utilize the range-Doppler map technique, which minimizes the interference after the range-Doppler measurement [11, 12]. In general, the IR signals corrupt the VR signal and create temporal gaps in the time domain signal. Consequently, recurrent neural network (RNN) based solutions are effective in addressing this kind of temporal problem. Most previously reported RNN-based techniques involve detecting the interference corrupted segments in the signal, followed by interference mitigation steps [13,14,15]. However, interference detection may not be robust if the interference corrupts the signal smoothly or uniformly without creating substantial gaps. Therefore, a robust interference mitigation mechanism is always favored, which can mitigate the interference irrespective of the interference type.
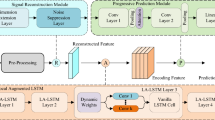
Figure 1 presents the overall functional diagram. To demonstrate the robustness of the proposed scheme, in the simulation environment, we generate a VR linear frequency modulated (LFM) transmission signal (Tx Signal) with a bandwidth of 4GHz (4GHz–8GHz). We used this signal to detect 2 objects located 3m away from the radar sensor, with a 4cm separation between each object. In the current paper, we introduce and present a robust LSTM-based RNN (LSTM-RNN) to suppress the interference signals from the received echo. For the training purpose, the received echo serves as the reference signal to the 4-layered LSTM-RNN. Each object was detected using 50 different IR LFM signals with varying chirp rates, which were subsequently used as an input signal to train the LSTM-RNN. In the testing phase, randomly interfered signals are evaluated. The interference-suppressed echo signal is retrieved by using the previously trained model. In general, IR signals can be categorized as coherent (having the same chirp rate as the VR) and incoherent (having a different chirp rate than the VR). The performance of the proposed LSTM-RNN is evaluated by calculating the range profiles for scenarios involving coherently interfered VR signals, incoherently interfered VR signals, and a combination of both. The proposed 4-layered LSTM-RNN structure mitigates coherent interference cases by suppressing the ghost target in the range profile. Furthermore, it enhances the signal-to-interference noise ratio (SINR) by > 18dB in all cases, thereby indicating its robustness in mitigating interference including different chirp rate interference signals.
2 Signal Model and Interference Effect Analysis
Among various types of radar waveforms, LFM is the most common one which can be represented as [1]
where \(A_{tx}\) is the amplitude of the transmitted signal, \(f_c\) is the center frequency, \(B\) is the operating bandwidth, \(\alpha_{tx} { }\) is the chirp rate of the signal which is equal to \(\frac{B}{T}\), and \(T\) is the time period. For the time period of \(0 \le t \le T,\) the frequency of the transmitted signal linearly increases from \(f_c - \frac{B}{2}\) to \(f_c + \frac{B}{2}\). When the transmitted signal is reflected from the target of \(K\) number of stationary objects, the received signal, \({ }R_x \left( t \right)\) is represented as
where \(A_{Rk}\) and \({ }\tau_{dk} { }\) represent the amplitude of the signal reflected from the kth objects and the time delay resulted by the relative range between the radar receiver and the kth target object, respectively. The LFM signal’s range resolution is its ability to distinguish the two target entities’ separation distance, which is proportional to the frequency shift. Hence, the range resolution can be expressed as \(\Delta R = \frac{c}{2B}\), and is a function of the bandwidth.
Next, we consider the case where the interference radar (IR) LFM signal, which acts on the receiver, can be expressed as,
where \({A}_{Iy}\) is the amplitude of the \({y}^{th}\) IR signal, \({\alpha }_{Iy}\) is the chirp rate of the IR signal, and \({\tau }_{Iy}\) is the delay of the IR signal to the victim radar (VR) signal. The chirp rate of the IR signal is given by \({\alpha }_{Iy}=\frac{{B}_{Iy}}{{T}_{Iy}}\), where \({B}_{Iy}\) and \({T}_{Iy}\) are bandwidth and the time period of \({y}^{th}\) IR signal, respectively. When the chirp rate of the VR signal and IR signal are equal, i.e., \({\alpha }_{Iy}={\alpha }_{tx}\) it is known as a coherent interference, and when they are different, \({\alpha }_{Iy}\ne {\alpha }_{tx}\), we considered it as a noncoherent interference. In the presence of IR signal, whether it is coherent or non-coherent, the output of the receiver is the mixture of the echo signal from the transmitted signal and the IR signal. For simplification, we consider a single VR and IR source. The beating frequency due to the IR signal \({R}_{I}\left(t\right)\), after the de-chirping is given by,
Figure 2 illustrates the LFM VR signal and the de-chirping of the signal at the receiver in the appearance of an IR signal with the same/various chirp rate. In Fig. 2 (a-i), the IR signal has the same chirp rate as that of the VR, i.e., \({\alpha }_{Iy}={\alpha }_{tx}\), resulting in two constant beat-frequencies \({f}_{bo}\) and \({f}_{bi}\), observed at the receiver’s output as they fall inside the bandwidth of the receiver as shown in Fig. 2a-ii. These two constant beat frequencies will result in two ranges, giving the information of the existence of two target objects, one of which is a ghost target object, as illustrated in the range profile of Fig. 2a-iii.
In Fig. 2b-i, the chirp rates are \({\alpha }_{Iy}\ne {\alpha }_{tx}\), leading to the observation of a constant beat frequency, \({f}_{bo},\) caused by the actual target object, along with a varying beat frequency \({f}_{bi}\left(t\right)\) as shown in Fig. 2b-ii. The varying beat frequency within the receiver bandwidth adds additional undesired frequency bins in the received signal and adds additional noise floor in the range profile as illustrated in Fig. 2b-iii. Both the interferences, whether coherent, Fig. 2a, or non-coherent, Fig. 2b, severely degrade the performance of the VR’s detection capability in a multi-radar environment either by introducing ghost targets or by significantly reducing the SNR. The illustration of Fig. 2 is for a case of 1 object detection and 1 interference signal acting in the received echo. However, in practical scenarios, multiple object detection should be carried out along with the various interference signals. Various approaches can be implemented to minimize the effect of IR signals in a VR signal while operating in a multi-radar environment. In this manuscript, our focus is on analyzing and mitigating interference through an LSTM-RNN based DL technique, which can provide similar output performance for detecting target objects in both interference and non-interference scenarios, in terms of range resolution, SNR, and detection capability.
3 LSTM-RNN Architecture
In the training process of the LSTM-RNN we assume that the echo signal without the interference is known. Therefore, the desired purpose of the training is to develop the model that correctly identifies the interference in the echo and successfully removes it. The LSTM-RNN based training model consists of the control mechanism with three gates regulating the passage of data within the cell allowing the network to learn long-range dependencies more effectively. Additionally, it avoids the exploding and vanishing gradient problem for the large number of input data samples. Thus, the LSTM-RNN can significantly enhance the ability of radar systems to detect and remove the interference signals at the receiver side and recover the corrupted samples.
As illustrated in Fig. 3a, the corrupted sample (\({x}_{n}\)), can be recovered based on the preceding samples \({x}_{1}\), \({x}_{2}\), …, \({x}_{n-1}\). Figure 3b illustrates the LSTM unit, which consist of the Forget Gate (\({\Gamma }_{F}\)), the Input Gate (\({\Gamma }_{I})\), , and the Output Gate (\({\Gamma }_{out}\)), and can be described as
where \(\sigma \) is the sigmoid activation function, \(tanh\) is the hyperbolic tangent activation function, \({x}_{n}\) is the input sample, \({h}_{n-1}\) is the previous value of the short-term memory, \({\omega }_{0}\)—\({\omega }_{7}\) are corresponding weights, and \({b}_{1}\)—\({b}_{4}\) are corresponding biases. The Forget Gate is the first stage in a LSTM unit. This stage determines the percentage of the previous long-term memory to remember. As can be seen in (5), the Forget Gate uses the sigmoid activation function which turns any input into a value within the range of 0 to 1. If the output of the function is 0, the previous long-term memory will be completely forgotten. On the other hand, if the output is equal to 1 the long-term memory remains unchanged. The next stage of the unit is the Input Gate. This gate contains both sigmoid and hyperbolic tangent activation functions, as illustrated in (6). The \(tanh\) function part of the Input Gate combines the input and the previous short-term memory to determine a potential long-term memory. The \(\sigma \) function part determines the percentage of the potential long-term memory to add to the current long-term memory. Overall, this part of the LSTM unit updates the current long-term memory. The final part of an LSTM unit is the Output Gate. This stage, in turn, updates the short-term memory by passing the updated long-term memory to the \(tanh\) activation function and using the \(\sigma \) function. Thus, the new short-term memory is the output of the entire LSTM unit. By utilizing these Gates, the new long-term and short-term memories are calculated using the following equations:
4 Methodology, Results and Discussions
Figure 4 demonstrates the steps of investigation. Overall, after preparing the VR and IR signals, we train the LSTM-RNN with various interference signals and test the trained network with different coherent and non-coherent interference signals. The last step in our investigation is the evaluation of the system performance by calculating SINR and peak to sidelobe level (PSL).
Table 1 illustrates the parameters for VR and IR signals. The VR signal is generated with a 1µs time period and a 4GHz bandwidth. The VR signal is used to detect objects, and the received echo serves as the output label for the LSTM-RNN. The AWGN noise equivalent to the SNR of 20dB is added to the received echo. To train the LSTM-RNN, the input signal is obtained by applying various chirp rate LFM interference signals to the echo signal. In the training set, the echo signal is mixed with 50 different interference signals with varying chirp rates ranging from 1GHz/µs to 10GHz/µs. All the signals prior to applying to LSTM-RNN, were normalized using zero mean and unit variance normalization functions. For the training step, the mean square error (MSE) values in each iteration were minimized applying the Adam optimization algorithm [16] with a starting learning rate of 0.01. For the testing purpose, we apply different interference signals than the training phase to ensure the trained model works properly for various interference signals with different parameters. Used training parameters and hyper-parameters are provided in Table 2.
With the use of 4 layers and a learning rate of 0.01, the optimum number of hidden units (50) was obtained by simulating the LSTM-RNN and selecting the hidden unit number that resulted in the minimum MSE. The optimization function in the training process minimizes the loss function, which calculates the error between the LSTM-RNN output (echo with interference suppression) and the expected output (echo without interference). In the radar systems, external interference generally causes two major problems (a) increment in noise floor and (b) appearance of ghost targets in the range profile. SINR and PSL values provide quantitative measure of the radar detection performance by identifying these problems.
To evaluate the performance with and without interference mitigation, the SINR calculation was performed, which is given as
where, \(\tilde{S }\) is the interference-suppressed echo signal, and \(S\) is the echo signal without the interference. In radar, range resolution determines the minimum separation distance between objects that can be distinguished by the radar waveform. This is determined by calculating the delay between the transmitted and received echo. In this paper, we calculate the range resolution by cross-correlating the transmitted signal with the received echo. The PSL power in the range profile is evaluated by determining the difference in the cross-correlated power (\({\left|C-Corr.\right|}^{2}\)) between the detected object’s peak with the sidelobe peak, denoted as (PSL).
Figure 5a-c shows examples of the amplitude-time diagrams of the echo signal (label), interference corrupted signal (input), and the output signal after the interference mitigation, respectively. As illustrated in Fig. 5b, the interference corrupts the signal in the time domain.
Figure 6 shows the frequency-time diagrams at various stages in the training phase. Figure 6a depicts the echo signal (label), whereas Fig. 6b demonstrates the interference corrupted signal (input), and Fig. 6c represents the output signal after the interference mitigation.
Figure 7 shows the range profile results for different test scenarios. The coherent and non-coherent types of interference signals are added to the victim echo signals for the test purposes. In Fig. 7, Fig. 7i represents the interfered test signal input to the trained LSTM-RNN, Fig. 7ii represents the recovered test signal with the previously trained model and Fig. 7iii shows the range profile acquired using interference-recovered signal.
Figure 7a is the case for coherent interference, while Fig. 7b corresponds to the case of both coherent and non-coherent interferences. As can be seen, in the case of coherent interference (Fig. 7a), the ghost target does not appear in the range profile. For both cases, a PSL > 15dB is obtained. The SINR was calculated using (10). With 25 runs, it is confirmed that the presented LSTM-RNN network can recover the test signal with a SINR of > 18dB in the presence of AWGN noise equivalent to the SNR of 20dB.
5 Conclusions
In this paper, we presented LSTM-RNN based interference mitigation method that can be applied to mitigate both coherent and non-coherent interferences in the multi-radar setup. The LSTM-RNN is trained with 50 different chirp rates of interference signals. The trained model is then used to recover the interference corrupted signal in the testing phase. With 25 tests, it is confirmed that the presented LSTM network can recover the echo signal, with the SINR > 18dB. Additionally, with the recovered signal, the PSL > 15dB is obtained for all test cases. These results indicate that the presented LSTM-RNN can be used to effectively mitigate the interference in multi-radar environments. The interference mitigation in multi-radar environment holds vital importance in the radar application area such as autonomous vehicle. We plan to further investigate the effectiveness of the proposed LSTM-RNN in experimental data. Additionally, with experimental data we will investigate the optimum values of parameters and hyper-parameters of the proposed LSTM-RNN by considering sufficient number of interference signals for training.
References
Parker, M.: Radar Basics, Digital Signal Processing 101. 2nd edn., pp. 231–240. Newnes (2017)
Gurbuz, Z., Griffiths, H., Charlish, A., Rangaswamy, M., Greco, M., Bell, K.: An overview of cognitive radar: past, present, and future. In: IEEE aerospace and electronic systems magazine, 34(12), 6–18 (2019)
Bilik, I., Longman, O., Villeval, S., Tabrikian, J.: The rise of radar for autonomous vehicles: signal processing solutions and future research directions. IEEE Signal Process. Magazine 36(5), 20–31 (2019)
Xu, Z., Shi, Q.: Interference mitigation for automotive radar using orthogonal noise waveforms. IEEE Geosci. Remote Sensing Lett. 15(1), 137–141 (2018)
Galati, G., Pavan, G., Wasserzier, C.: Signal design and processing for noise radar. EURASIP J. Adv. Signal Process 52 (2022)
Skaria, S., Al-Hourani, A., Evans, R., Sithamparanathan, K., Parampalli, U.: Interference mitigation in automotive radars using pseudo-random cyclic orthogonal sequences. Sensors 19(20), 4459 (2019)
Uysal, F.: Phase-coded FMCW automotive radar: system design and interference mitigation. IEEE Trans. Veh. Technol. 69(1), 270–281 (2020)
Lee, S., Lee, J., Kim, S.: Mutual interference suppression using wavelet denoising in automotive FMCW radar systems. IEEE Trans. Intell. Transp. Syst. 22(2), 887–897 (2021)
Choi, Y.: Adaptive nulling beamformer for rejection of coherent and noncoherent interferences. Signal Process. 92(2), 607–610 (2012)
Lee, T., Lin, T.: Coherent interference suppression with complementally transformed aadaptive beamformer. IEEE Trans. Antennas Propag. 46(5), 609–617 (1998)
Rock, J., Toth, M., Messner, E., Meissner, P., Pernkopf, F.: Complex signal denoising and ınterference mitigation for automotive radar using convolutional neural networks. In: 22th International conference on ınformation fusion (FUSION), pp. 1–8, Ottawa, ON, Canada (2019). https://doi.org/10.23919/FUSION43075.2019.9011164
Fuchs, J., Dubey, A., Lübke, M., Weigel, R., Lurz, F.: Automotive radar ınterference mitigation using a convolutional autoencoder. IEEE Int. Radar Conf. (RADAR), pp. 315–320, Washington, DC, USA (2020). https://doi.org/10.1109/RADAR42522.2020.9114641
Mun, J., Ha, S., Lee, J.: Automotive radar signal ınterference mitigation using RNN with self attention. In: ICASSP IEEE ınternational conference on acoustics, speech and signal processing (ICASSP), pp. 3802–3806, Barcelona, Spain (2020). https://doi.org/10.1109/ICASSP40776.2020.9053013
Hille, J., Auge, D., Grassmann, C., Knoll, A.: FMCW radar2radar ınterference detection with a recurrent neural network. In: IEEE radar conference (RadarConf22), pp. 1–6, New York City, NY, USA (2022). https://doi.org/10.1109/RadarConf2248738.2022.9764236
Rameez, M., Javadi, S., Dahl, M., Pettersson, M.: Signal reconstruction using Bi-LSTM for automotive radar ınterference mitigation. In: 18th European radar conference (EuRAD), pp. 74–77, London, United Kingdom (2022). https://doi.org/10.23919/EuRAD50154.2022.9784516
Kingma, Diederik, P., Ba, J.: Adam: A method for stochastic optimization. arXiv preprint arXiv:1412.6980 (2014)
Acknowledgement
This work was supported by the Nazarbayev University (NU) Collaborative Research Project (grant no. 11022021CRP15070), Faculty Development Competitive Research Grant (grant no. 021220FD0451), and the Ministry of Education and Science of the Republic of Kazakhstan (AP14871109, AP13068587).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Parajuli, H.N., Bakhtiyarov, G., Nakarmi, B., Ukaegbu, I.A. (2024). Interference Mitigation in Multi-radar Environment Using LSTM-Based Recurrent Neural Network. In: Choi, B.J., Singh, D., Tiwary, U.S., Chung, WY. (eds) Intelligent Human Computer Interaction. IHCI 2023. Lecture Notes in Computer Science, vol 14532. Springer, Cham. https://doi.org/10.1007/978-3-031-53830-8_15
Download citation
DOI: https://doi.org/10.1007/978-3-031-53830-8_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-53829-2
Online ISBN: 978-3-031-53830-8
eBook Packages: Computer ScienceComputer Science (R0)