Abstract
Chaos theory is considered as a tool for studying the systems that show divergence and disorder. After having used discrete mathematics to deduce non-convergence situations, these theories are modeled in the form of a dynamic system and are applied in several domains such as electronic, mechanic, network security, etc. In network security domain, the development of new cryptosystems based on chaos is a relatively new area of research and is increasingly relevant. The essence of the theoretical and practical efforts in this field derive from the fact that these cryptosystems are faster than conventional methods, while ensuring performance of security, at least similar. In this paper, we discuss several proposals about chaos-based cryptosystem and pseudo-random number generator (PRNG). Moreover, topology and architecture of the proposed chaos systems are detailed. Finally, in order to show the more suitable system for encryption and secure communication, a synthesis comparison is presented and considered.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
Nowadays, network communication is vulnerable to many threats and cyber-attacks and it becomes more important for network experts to safeguard the network access [1]. Among the available security mechanisms, chaos-based cryptosystems are considered one of the most effective solution that provides the integrity, the authentication and the confidentiality. Recently, the development of new cryptosystems based on chaos is a relatively new area of research and is increasingly relevant.
In [2], an Field-Programmable-Gate-Array (FPGA) implementation of image encryption purpose using two chaotic discrete time systems. The proposed two phases algorithm is executed by using the well known Arnold Cat map and the generalized logistic map, respectively. Authors in [3] initiate a systematic methodology for securing real-time video communication. The proposed chaos-based cryptosystem have been implemented on an FPGA hardware platform via Verilog Hardware Description Language (Verilog HDL). Sreenath and Narayanan [4] presents a Hardware implementation of a Pseudo chaos signal generator using three reconfigurable discrete time systems with a linear feedback shift registers (RLFSR). The proposed technique was implemented using Verilog HDL codes, then analyzed using Xilinx Plan Ahead compiler and Model-sim software. In terms of network security protocols, [5] proposed a novel chaos-based mechanism that includes Pseudo-Random Key-Generator which can be used to secure a socket-based communication. The proposed key-generator, created by solving the Lorenz chaos-system, has the main task of delivering at each opened channel a new 32-bit key that is used for encrypting/decryption the exchanged data.
In this paper, we discuss several proposals about chaos-based cryptosystem and pseudo-random number generator (PRNG). Moreover, topology and architecture of the proposed chaos systems are detailed. Finally, in order to show the more suitable system for encryption and secure communication, a synthesis comparison is presented and considered.
The remainder of this paper is structured as follows. Section 2 describes the classification of the most used chaotic systems. Section 3 shows the hardware implementations of these chaotic systems as well as their purposes. Section 4 concludes this paper.
2 Background and Description of Chaotic Systems
Due to the sensitivity and periodicity properties, chaotic systems have been involved mainly in key generation of the recently proposed cryptography schemes. Regarding their topology and mathematical model, we can classify all existing and newly proposed chaos systems in two main categories: continuous-time systems and discrete-time systems.
2.1 Continuous Time Systems
The continuous-time systems are described by a set of linear differential equation. Moreover, in order to ensure that the dynamical systems to be chaotic, the dimensions of the system’s phase space must be at least equal to three (3). In the literature, there are several well known continuous-time systems such as Lorenz [6], Chen [7], Lu [8], etc.
Lorenz System The basic form of the Lorenz 3-D system is described by the following set of equation:
where x, y and z are the state variables. a, b and c are the system parameters. The chaotic behaviour (see Fig. 1) appears for a = 10, b = 28 and c = 8/3 with the initial conditions \(x_0=0\), \(y_0=5\) and \(z_0=25\) [8].
Van-der-Pol System The Van-der-Pol oscillator as given in [9], is described in two dimensions as follows:
where x, y are the state variables, and a is the system controller. The phase portrait of the 2-D system is illustrated in Fig. 2.
Chen System Based on the 3-D Lorenz system, Chen 3-D system is proposed and described by the following set of equations:
where x, y and z are the state variables. a, b and c are the system parameters. The chaotic behaviour appears for a = 35, b = 28 and c = 8/3 [10], while the phase plan projection is shown in Fig. 3.
Lu System The Lu system is known as the bridge between Lorenz system and Chen system [8]. Thereby, the mathematical model is given as follows:
where x, y and z are the state variables. a, b and c are the system parameters. The trajectory graph of the proposed system is given in Fig. 4.
Linz-Sprott System Trying to simplify the formula of a chaotic system, Linz and Sprott [10] have proposed a new system which is defined as follows:
where x, y and z are the state variables and a is the system’s parameter. As shown in Fig. 5, the chaotic behaviour of the proposed system is achieved for a = 0.6.
Four-Wing memristive hyperchaotic System Looking for higher dimensional chaotic system, authors in [11] have proposed a novel 4-D system which is described as follows:
where x, y, z, w are the state variables. a, b, c, d, e, f, g, m, n, p, Q are the controllers of the proposed system. In order to ensure the chaotic behaviour, the controllers parameters are defined as follows: a = 0.35, b = −10, c = −0.6, d = 0.3, e = −1.6, f = 2, g = 0.1, m = 0.1, n = 0.01, p = 0.2 and Q = 0.01. The trajectory graphs corresponding to the proposed system with the associated parameters, are shown in Fig. 6.
New 3-D Continuous Time System Getting inspired from the Lorenz system [12], with only two (02) controllers, a novel 3-D system is proposed and defined as follows:
where x, y and z are the state variables. a and b are the system parameters. The chaotic behaviour of the proposed system is observed for the values a = 0.5 and b = 1 while the initial conditions are \(x_0=y_0=z_0=0\) (see Fig. 7).
New 4-D Continuous Time System In [13], another new 4-D chaotic system is proposed based on the Rossler system, and defined by the following set of equations:
where x, y, z and w are the state variables. a, b, c and d are the system parameters. By choosing a = 0.4, b = 0.6, c = 3 and d = 0.8, the chaotic behaviour of the proposed system is showed by phase plan projection (see Fig. 8).
2.2 Discrete Time Systems
The discrete time chaos system is a dynamic system which works in increments and takes the conditions at a given time t to change these conditions at a later time \(t+\Delta {t}\). Hence, unlike the mathematical model of the continuous time systems, discrete time maps are described mathematically by an iterated function. Moreover, the dimension of the system’s phase space could be only equal to one (01) to show chaos behaviour.
Logistic Map In the literature, many proposals have used the well known logistic map such as in [14] for PRNG, [2] for image encryption,[15] for chaotic signal generating, etc. The mathematical description of this map is given as follows:
where \(x_{i}\) is the state variable and a is the system controller.
To ensure the chaotic behaviour (see Figs. 9 and 10) of this system, a should be in the interval \([3.57-4]\).
Hénon Map A simple 2-D with quadratic non-linearity, Hénon system was the first map to show strange attractor with a fractal structure [16]. The mathematical description of this map is given as follows:
where \(x_{i}\) and \(y_{i}\) are the state variables and a, b are the system controllers.
The obtained strange attractor of this map, is shown in Fig. 11 while the controllers are a = 1.4 and b = 0.3.
Rene-Lozi Map By introducing the absolute value in the Hénon map, the Rene-Lozi map used in [17] for stream cipher purpose, is described as follows:
where \(x_{i}\) and \(y_{i}\) are the state variables and a, b are the system controllers.
Similarly to the Hénon map, it has been shown that for a = 1.4 and b = 0.3, chaotic behaviour of this map can appear (see Fig. 12).
Bernoulli Map Unlike all the discrete time maps, Bernoulli map is composed of two piece-wise linear parts which are separated by a discontinue space of points [11] (see Fig. 13).
Mathematically, the Bernoulli map is defined as follows:
where \(x_{i}\) is the state variable and a is the control parameter.
The chaotic status of this map is ensure for all the values of the parameter a inside the interval \(]1.4 - 2]\) (see Fig. 14).
Sine Map The sine map is qualitatively similar to the logistic map, and the superficial similarity has resulted in a much deeper connection.
As indicated by its name, the sine map is defined by a sine function as follows:
where \(x_{i}\) is the state variable and a is the system parameter. The projection graph which proves the behaviour of this map is shown in Fig. 15.
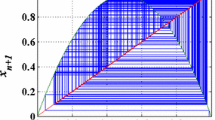
Tent Map Regarding the slope of its mathematical function, tent map with only one state variable, is considered as a slope of two (02) model. Without any control parameter, the tent map is defined as follows:
where \(x_{i}\) is the state variable. Moreover, the trajectory graph of the tent map is shown in Fig. 16.
All these systems have been used mainly for either generating random numbers, cipher keys or chaotic signals. They differ from each other in terms of dimension, control parameters and the purpose of use. In Table 1 we summarize all these differences obtained regarding our study.
3 Hardware Implementations and Applications
FPGA-based prototyping is specifically geared toward meeting the design and verification demands created by the complexities of low and constrained resources devices. Moreover, FPGA-based prototyping allows designers to develop and test their systems and provides software developers early access to a fully functioning hardware platform long before silicon is available. In order to be implemented on FPGA, the continuous time systems need to be discredited numerically using some popular methods such as Euler and Runge-Kutta (RK) methods. Euler’s method is a straight-forward method that estimates the next point based on the rate of change at the current point and it is easy to code [19]. It is called also a single step method. While RK methods are actually a family of schemes derived in a specific style. Higher order accurate RK methods are multi-stage because they involve slope calculations at multiple steps at or between the current and next discrete time values [20]. The next value of the dependent variable is calculated by taking a weighted average of these multiple stages based on a Taylor series approximation of the solution. The weights in this weighted average are derived by solving non-linear algebraic equations which are formed by requiring cancellation of error terms in the Taylor series. Developing higher order RK methods is tedious and difficult without using symbolic tools for computation. The most popular RK method is RK4 since it offers a good balance between order of accuracy and cost of computation. RK4 is the highest order explicit Runge-Kutta method that requires the same number of steps as the order of accuracy (i.e. RK1 = 1 stage, RK2 = 2 stages, RK3 = 3 stages, RK4 = 4 stages, RK5 = 6 stages, \(\ldots \)). Beyond fourth order the RK methods become relatively more expensive to compute. Among all the studied proposals, we have synthesised a brief comparison that includes mainly the used FPGA technology and the consumed resources. Table 2 summarizes the difference between different proposals regarding the chosen system as well as the resource consumption. However, we found that in the single-precision and the double-precision operations, there are more than \(10^{-6}\) differences in less than 100 iterations, and the difference reaches more than one digit after 1000 iterations [21]. This is because the binary has a round-off error, so the binary cannot strictly obey the commutative law or the distribution law in floating-point operations.
4 Conclusion
In this paper, we discuss several proposals about chaos-based cryptosystem and pseudo-random number generator (PRNG). Moreover, topology and architecture of the proposed chaos systems are detailed. Finally, in order to show the more suitable system for encryption and secure communication, a synthesis comparison is presented and considered.
References
B. Bouteghrine, M. Rabiai, C. Tanougast, S. Sadoudi, FPGA implementation of Internet key exchange based on chaotic cryptosystem, in 10th IEEE International Conference on Intelligent Data Acquisition and Advanced Computing Systems: Technology and Applications (IDAACS) (Metz, France, 2019), pp. 384–387
B. Baruah, M. Saikia, An FPGA implementation of chaos based image encryption and its performance analysis. IJCSN Int. J. Comput. Sci. Netw. 5, 5 (2016) (Unpaginated)
S. Chen, S. Yu, J. Lu, G. Chen, J. He, Design and FPGA-based realization of a chaotic secure video communication system. IEEE Trans. Circuits Syst. Video Technol. 28(9), 2359–2371 (2017)
H. Sreenath, G. Narayanan, FPGA implementation of pseudo chaos-signal generator for secure communication systems, in 2018 International Conference on Advances in Computing, Communications and Informatics (ICACCI) (Bangalore, India, 2018), pp. 804–807
B. Bouteghrine, M. Rabiai, C. Tanougast, S. Sadoudi, Hardware implementation of secured socket communication based on chaotic cryptosystem, in 2019 International Conference on Cyber Security and Protection of Digital Services (Cyber Security) (Oxford, UK, 2019), pp. 1–4
A. Qi, C. Han, G. Wang, Design and FPGA realization of a pseudo random sequence generator based on a switched chaos, in 2010 International Conference on Communications, Circuits and Systems (ICCCAS) (Chengdu, China, 2010), pp. 417–420
J. Lu, X. Wu, X. Han, J. Lu, Adaptive feedback synchronization of a unified chaotic system. Phys. Lett. A 329(4–5), 327–333 (2004)
M.S. Azzaz et al., FPGA implementation of new real-time image encryption based switching chaotic systems, in IET Irish Signals and Systems Conference (ISSC 2009), vol. 56. (Dublin. Ireland, 2009)
M. Tuna, A novel secure chaos-based pseudo random number generator based on ANN-based chaotic and ring oscillator: design and its FPGA implementation. Analog Integr. Circ. Sig. Process 105(2), 167–181 (2020)
A. Senouci et al., FPGA based hardware and device-independent implementation of chaotic generators. AEU-Int. J. Electron. Commun. 82, 211–220 (2017)
F. Yu et al., Design and FPGA implementation of a pseudo-random number generator based on a four-wing memristive hyperchaotic system and Bernoulli map. IEEE Access 7, 181884–181898 (2019)
I. Koyuncu et al., Design, FPGA implementation and statistical analysis of chaos-ring based dual entropy core true random number generator. Analog Integr. Circ. Sig. Process. 102(2), 445–456 (2020)
C.H. Yang, Y.S. Chien, FPGA implementation and design of a hybrid Chaos-AES color image encryption algorithm. Symmetry 12(2), 189 (2020)
M. Garcia-Bosque et al., Chaos-based bitwise dynamical pseudorandom number generator on FPGA. IEEE Trans. Instrum. Measur. 68(1), 291–293 (2018)
Z. Hua, B. Zhou, Y. Zhou, Sine-transform-based chaotic system with FPGA implementation. IEEE Trans. Industr. Electron. 65(3), 2557–2566 (2017)
A.M. Atteya, A.H. Madian, A hybrid Chaos-AES encryption algorithm and its implemention based on FPGA, in IEEE 12th International New Circuits and Systems Conference (NEWCAS), vols. 217–220 (Quebec, Canada, 2014)
L. Merah et al., FPGA hardware co-simulation of new chaos-based stream cipher based on Lozi map. Int. J. Eng. Technol. 9(5), 420–425 (2017)
Y. Mao, L. Cao and W. Liu, Design and FPGA implementation of a pseudo-random bit sequence generator using spatiotemporal chaos, in 2006 International Conference on Communications, Circuits and Systems (Guangzi, China, 2006), pp. 2114–2118
D.I. Lanlege et al., Comparison of Euler and Range-Kutta methods in solving ordinary differential equations of order two and four. Leonardo J. Sci. 32, 10–37 (2018)
S.C. Palligkinis, G. Papageorgiou, I.T. Famelis, Runge-Kutta methods for fuzzy differential equations. Appl. Math. Comput. 209, 97–105 (2009)
C.H. Yang, H.C. Wu, S.F. Su, Implementation of encryption algorithm and wireless image transmission system on FPGA. IEEE Access 7, 50513–50523 (2019)
P. Dabal, R. Pelka, A chaos-based pseudo-random bit generator implemented in FPGA device, in 14th IEEE International Symposium on Design and Diagnostics of Electronic Circuits and Systems (Cottbus, Germany, 2011), pp. 151–154
R. Hobincu, O. Datcu, FPGA implementation of a chaos based PRNG targetting secret communication, International Symposium on Electronics and Telecommunications (ISETC), Timisoara. Romania 1–4, 2018 (2018)
E. Tlelo-Cuautle et al., FPGA realization of a chaotic communication system applied to image processing. Nonlinear Dyn. 82(4), 1879–1892 (2015)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Bouteghrine, B., Tanougast, C., Sadoudi, S. (2022). A Survey on Chaos-Based Cryptosystems: Implementations and Applications. In: Skiadas, C.H., Dimotikalis, Y. (eds) 14th Chaotic Modeling and Simulation International Conference. CHAOS 2021. Springer Proceedings in Complexity. Springer, Cham. https://doi.org/10.1007/978-3-030-96964-6_6
Download citation
DOI: https://doi.org/10.1007/978-3-030-96964-6_6
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-96963-9
Online ISBN: 978-3-030-96964-6
eBook Packages: Physics and AstronomyPhysics and Astronomy (R0)