Abstract
e-Learning is associated with the usage of different network devices to ensure user educational performance. Its platforms are rising as digital media has reinvented business organisations. e-Learning options include warehouses for ever more learners with accessible and usable material. Consequently, e-learning remedies collect a garage. e-Learning projects are commonly supplied with cloud technology as a hybrid cloud/PaaS cloud environment. However, a variety of malicious software and attackers have been the obvious target for such famous e-learning programmes. Such cyber hackers try unauthorization from such not-so-reliable e-learning platforms to a variety of sensitive data including user names, address, credit/debit card identification, etc. Safeguarding of students and teachers from unlawful attacks is an essential component of e-learning. Identifying the evolving types of malware that target these cloud-based tech applications, with a focus on e-learning solutions that use Digital-supervised learning. The article also examines the important methods and techniques of both the assault and also some ideas for vulnerability scanning based on artificial intelligence with 92.77% of the outcomes.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- IoT
- Information security
- Malware
- API calls
- Artificial intelligence
- Cyber security
- e-Learning
- Cloud
- Supervised learning
1 Introduction
Suspect technologies were also harmful mobile apps designed to quickly develop viruses, worms or malware targeting remote servers, accessing multiple browsers, etc. [1]. FireEye has launched innovative tools for the detection of new cyber threats, safe consumer intelligence, sensitive details and corporate information. FireEye is a development software firm listed on the Nasdaq market.
From its ground station surveillance system, the company invented a new malware barricade remedy which is available for enhanced customer expenses.
In contrast to viruses, worms and Trojans, the definition of harmful malware is not transparent to the computer, so the disruptive payload of the program often comes from the direct order of the user [2].
Developer: Building company apps seek to produce brand new malicious software, Trojans. The heart, devices and/or harmful information of the program can be unsafe.
SHAT: Such programs are configured for the objectives of denial-of-service (DoS) attack and for user’s computer. Several requests will be submitted by the program to the expected system endpoint, as well as a denial-of-service attack will be rendered if this computer is not able to manage such demands sufficiently [3].
Alert of leaking: Fraudsters also abuse the e-mail channels of such systems with meaningless e-mails.
Skulls: Other sites – like IRC – are also used by hackers for swamping.
Online messaging broadcasts with pointless IM: Hackers occasionally deluge irrelevant e-mails from these initiatives, including the ICQ, Myspace, AOL chat program, ask.com fax machine, WhatsApp, etc. [4].
Mails of inundation: Hackers have been known to utilise notice flooders to inundate ineffective e-mail channels [5]. The YouTube tutorial can be used to add new users to the visitor network list to remove computer logs information that mask malicious people’s involvement. The initiatives of HackTool are used to target remote network machines by suspicious users [6].
Bollocks: Scam does not harm their Mac initiatives. Alternatively, they give you e-mails informing you whether damage has been done or is being achieved – or that a threat that probably doesn’t really exist is cautioned against.
Fare evader spammer: Spoofer apps override the group e-mail that offers an acknowledgement or service request for several purposes to prevent the recipient being identified by the recipient troll programs which are not enabled by fare evader.
Simulated method: Those implementations can also be used to modify such ransomware and try and prevent a malware protection alternative from detecting detrimental software.
2 Related Work
J. O. Aslan – Spyware means malicious programs which are installed on a software system and which have no owner’s permission [7]. It carries out harmful actions such as stolen sensitive data and is facilitated by digital installation. In the past, exploited software released a state-of-the-art technology that could bypass virus protection, IDS and web server implementation. This uncertainty is one of the biggest challenges in the field of cyber safety [8] due to communication systems and computer-based apps. This section provides a methodology used to research the common detecting and sensing method, apply certain approaches to good virus protection and benevolent software and contrast their data gathered. The study would in fact inform consumers about the analysis and identification of current and new viruses [9]. A research paper has been researched and stored in different web browsers, 100 spyware and 100 unhealthy application samples from different sources. It is apparent from the test results that only one device can hardly find malware. The combined precision and detection rate was doubled [10] thanks to dynamic and static management software.
B. N. Sanjay – Malicious software applies to any illegal technology-dangerous connections or server. Data mining has been a big subject besides advanced threat research, despite the occasional days with computers. Throughout the course of time, several different malware forms have been created to be searched for and overlooked by virus protection software [11]. Malicious software threats have traditionally passed to the device in a way that is done for the purpose of executing malicious operations, as we typically know. Fileless ransomware is built to exist in memory alone but rather to reach file posts. This is all designed to make coroner response infection difficult for an attacker. Currently, fingerprints can’t allow this form of assault to be identified. This essay discusses in considerable depth of the technical features of fileless ransom-ware and related assaults.
A. Tyagi –The whole report seeks to reassure the purchaser of the application mechanism for ‘URL network security’. The entire device stops users from falling victim to the move from uploading threats [12]. Because the domain name is accepted as a structure text file extension by this tool. It lists but also tests documents obtained by the malicious software detector online and obtains guidance for visualizing the server database. Such documents are illustrated graphically as malevolent knowledge. MD5 main is the device used. The article suggests five plugins for a more detailed computer study [13].
3 Theoretical Background
3.1 Artificial Intelligence to Protect Cyber Security Attack on Cloud E-Learning Tools (AiPCE)
Throughout the research, the vulnerability was discovered in a web server assigning the e-learning to server computers [14] and was taught unattended. There really is no feed reverse scheme in transferring classification to foretell the production of the training stage. The infrastructure itself learns any correlation among both structures such as similarity, crease, functionality and categorization Throughout the methods assigned to a Linux environment in the input executable, the infrastructure learns any link between two structures such as resemblance, crease, functionality, and categorisation [15]. Uncontrolled training can precisely introduce the different input sequence similar to the approach already learnt, and the system can understand progressively which functionalities are of benefit to the excellent binary format, such as grouping, evaluation of the main components and surveying of functions.
Consider a client has assembled an application with no security openings and is utilizing a PaaS supplier to host their application. Their application relies upon the parts of their PaaS provider to be functional. These conditions may straightforwardly include database, storage, a web server and a code container. The most common scenario would be a denial-of-service attack that makes communication with your application impossible because the provider’s network has been overloaded. Another vector is being a victim of a denial-of-service attack. A cloud provider likely uses virtual machines which run on real physical hosts which actually means shared resources. The kinds of resources include systems which can get overloaded in some demanding situations. If the purpose of an assault is one consumer, it is very likely that a consumer would also suffer greatly from the same assault. Walmart’s online services houses both a potentially contested domain and a secure e-news aggregation site leveraging common tools for purposes of analysis assume. When a broad community wishes to visit the web that has been attacked, any participant of that party sends proxy servers on a continuing basis before the website fulfils the criteria indefinitely. As the e-news aggregation site started hosting on a same natural machine, it is also a perpetrator and inaccessible. Suppliers can lessen the risk of such an assault by relatively allocating wealth and that of other customers or clients can also utilize various geographic sites (Multi-AZ is going to host). Cyber-attacks are straightforwardly multi-source DOS assaults and a bigger-scale attack. A side-channel attack, the whole style with attack, has the authority to satisfy two or more protected customers, rationally differentiating but just not physically, with most private clouds using vms. In case an attacker can determine and then get an unremarkable physical host assigned to one of everyone’s window servers from the loss, they may be able to crack off from everyone’s sandbox or to use unreasonable amounts of resources. This lack of energy will contribute to a reaction or unavailability of the victim’s network. The intruder will use minor vulnerabilities in an unfavourable circumstance to manipulate the quantum object and jeopardize the traffic of his hostages.
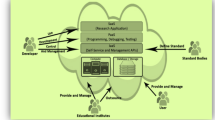
AI – quantum computing – is a highly reliable and rapidly growing approach to probability value tracking in the distributed cloud on video surveillance. The features of AI network-based are data analysis, creativity and innovation. Historically, intrusion prevention has been primarily extended to ANNs, foggy systems, automated immune cells, GA or expert systems. The following articles give a description of the uses of AI techniques for threat management and protection. This document outlines the techniques for mapping raw data into information through regulated training. It has used values that the supervisor has defined. A recurring algorithm (encoder-decoder) and a cognitive feed system (FFNN) were also two principal approaches of deep classification. The multi-layer feed forward (MLFF) NN and probability density function (RBF) are good instances of giving forward machine learning. The RBF categorization is based on the assessment of the location among both inserts and number of hidden centres. The RBF is best for broad cloud-based e-learning systems compared to the MLFF backward propagation (BP), since it is very fast. On the cloud software service running virtual host machines, Fig. 1 depicts the Artificial Intelligence to Protect Cyber Security Attack on Cloud E-Learning Tools (AIPCE) cross-malware detection flowchart.
Uncontrolled learning has no supervisor, and the course only uses extracted features. Unmonitored learning resembles a numerical grouping, where similarities are used to identify different input groups. Two widely known forms of transfer classification are SOM and the integrated amplification model. SOM is an outlier and a misappropriation-detection deacon-neural net technique. However, the study shows that ART has a greater detectability on both online and physical data, evaluated by comparing the vulnerability scanning premised to ART and SOM.
Semisupervised trying to learn: A mixture of controlled and unattended teaching strategies is used in droplet interference object tracking’s supervised classification method. Many output layers are also presented in a dataset alongside classified data in this specific technique. This technique can also be used with less annotated images even before classification is affordable. The semi-controlled approach will function as a controlled or unregulated training depends on the cost with annotated images.
In order to never present the right input/output outfits, learning algorithm is inherently different from the typical monitored learning process. There is therefore clearly no punishment to suboptimal behaviour. The main emphasis is on online productivity, which requires a good equilibrium between existing data and unidentified region. The discovery and manipulation of the trade in enhancement education have been most extensively explored through the issue of multi-armed bandits and finite MDPs.
Pseudocode: Intelligence-supervised training to recognize vulnerabilities in SaaS method
Input to on-demand AI with supervised learning method anomaly detection method: data
Application of data set with R features output – an array of R classification models of each application process
For each feature where i = 0, 1, 2….n to perform for each application.
-
If (PaaS - Process)
-
Change (.Process permission)
-
getAll (all available Threads on Selected Process)
-
If (open Thread)
-
Create new memory using virtual allocation
-
Identify all statements performing injection
-
Apply AI-supervised learning to find malicious thread move into array of process information tables
-
For each application process maintain separate row in database table
-
Else
-
Invalid application process
-
Else
-
No injection Found
-
Exist
-
End
-
For each
-
Return.
4 Results and Comparison
Cloud-based known attacks were briefly discussed. Cloud-based known attacks were briefly discussed. The centralized, transparent cloud computers and infrastructure system is an enticing option for intruders’ future cyber-attacks. Thanks to their accessibility and their unique design, conventional vulnerability scanning (IDPS) is mostly ineffective. Detection techniques, explicitly training data, svm training, unattended education and strengthened trying to learn, are addressed in machine learning. The best usage for online e-learning as well as other PaaS/SaaS tools is accomplished by utilizing AI-IDS or other risk reduction programs. Insect Masters was such a technique to identify assaults against host-based technology.
It utilizes a sweet pot method for OS procedures not dependent on low-level OS specifics, and thus regular OS processes are exposed as a malicious software trap. Throughout Bee Master no disadvantages are apparent in the low-level OS-dependent strategies. Bee apprentice can also be quantitatively tested for independent OS detection. The harmful runtime obtained from clients of Community Ransomware Container Review Programs is checked and returned to clients in a place called a debugger. Such devices are rising substantially and provide an Internet access to obtain central control and download data. It involves risks which can be identified by attackers when using this structure as just a malware communication. The IP address of an online sandbox is revealed by an attacker who distributes the executable, distributes it to Blacklisted users, and uses it against the analysis system. Table 1 provides the malware identification in PaaS/SaaS using AI and supervised learning.
5 Conclusion
Also in developed areas of the world, online shopping is growing regular. Thanks to its diverse design and existence, cloud based e-learning platforms pose a kind of obstacle to protect researchers. An efficient framework for vulnerability scanning is a crucial tool to secure the cloud from assaults. The usage of artificial technologies provides numerous benefits, owing to its capacity to learn and resilience. An IDS focused on artificial insight is adaptable to shifts in the world and equipped to identify even unexpected threats. The smart IDS will also operate in high-speed public cloud. Intelligence-supervised learning throughout this work has been used to allow users to upload in cloud SaaS methods. In addition, the study will be extended to classify potential attacks on diverse environments.
References
Aslan, Ö., Samet, R.: Investigation of possibilities to detect malware using existing tools. In: 2017 IEEE/ACS 14th International Conference on Computer Systems and Applications (AICCSA), Hammamet, pp. 1277–1284 (2017). https://doi.org/10.1109/AICCSA.2017.24
Priya, R., Jayanthi, J.: Security attacks and threats in e-learning. Int. J. Emerg. Technol. Comput. Sci. Electr. (IJETCSE). 21(3) (2016) ISSN: 0976-1353
Chou, T.-S.: Security threats on cloud computing vulnerabilities. Int. J. Comput. Sci. Inform. Technol. (IJCSIT). 5(3), 87 (2013)
Schultz, M.J.: A Survey of Cloud Security Issues and Offerings. http://www.cse.wustl.edu/~jain/cse571-11/ftp/cloud/index.html
Sanjay, B.N., Rakshith, D.C., Akash, R.B., Hegde, D.V.V.: An approach to detect fileless malware and defend its evasive mechanisms. In: 2018 3rd International Conference on Computational Systems and Information Technology for Sustainable Solutions (CSITSS), Bengaluru, India, pp. 234–239 (2018). https://doi.org/10.1109/CSITSS.2018.8768769.
Tyagi, A., Ahuja, L., Khatri, S.K., Som, S.: Prevention of drive by download attack (URL Malware Detector). In: Third International Conference on Inventive Systems and Control (ICISC), Coimbatore, India, pp. 114–118 (2019). https://doi.org/10.1109/ICISC44355.2019.9036341
Shabtai, A., Tenenboim-Chekina, L., Mimran, D., Rokach, L., Shapira, B., Elovici, Y.: Mobile malware detection through analysis of deviations in application network behaviour. Comput. Secur. Department of Information Systems Engineering, Ben-Gurion University of the Negev, Beer-Sheva, Israel in ScienceDirect. Elsevier. 43, 1–18 (2014)
Aung, Z., Zaw, W.: Permission-based android malware detection. Int. J. Sci. Technol. Res. 2(3) (2013) ISSN 2277-8616
Kapse, G., Gupta, A.: Detection of malware on android based on application features. Int. J. Comput. Sci. Inform. Technol. (IJCSIT). 6(4), 3561–3564 (2015) ISSN 0975-9646
Cen, L., Gates, C., Luo, S., Li, N.: A probabilistic discriminative model for an-droid malware detection with decompiled source code. IEEE Trans. Dependable Secure Comput. 12(4) (2015)
Siddiqui, M., Wang, M.C., Lee, J.: Detecting internet worms using data mining techniques. J. Syst. Cybern. Inf. 6(6) ISSN: 1690-4524 (2008)
Singh, A.P., Handa, S.S.: Malware detection using data mining techniques. Int. J. Adv. Res. Comput. Commun. Eng. 4(5) (2015)
Anand, R., Veni, S., Geetha, P., Rama Subramoniam, S.: Extended morphological profiles analysis of airborne hyperspectral image classification using machine learning algorithms. Int. J. Intell. Netw. 2, 1–6 (2021)
http://resources.infosecinstitute.com/android-malware-analysis-2/
Siddiqui, M., Wang, M.C., Lee, J.: A survey of data mining techniques for malware detection using file features. In: Proceedings of the 46th Annual Southeast Regional Conference on XX. ACM (2010) https://securityintelligence.com/diy-android-malware-analysis-taking-apart-obad-part-1/
Author information
Authors and Affiliations
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Arul, E., Punidha, A. (2022). Artificial Intelligence to Protect Cyber Security Attack on Cloud E-Learning Tools (AIPCE). In: Ramu, A., Chee Onn, C., Sumithra, M. (eds) International Conference on Computing, Communication, Electrical and Biomedical Systems. EAI/Springer Innovations in Communication and Computing. Springer, Cham. https://doi.org/10.1007/978-3-030-86165-0_3
Download citation
DOI: https://doi.org/10.1007/978-3-030-86165-0_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-86164-3
Online ISBN: 978-3-030-86165-0
eBook Packages: EngineeringEngineering (R0)