Abstract
The main feature in the development of Internet of Things (IoT) applications is the necessity of conjoint servicing of heterogenous data streams over existent network infrastructure. This trend has been recognized and supported by 3GPP with introducing of NarrowBand IoT (NB-IoT) technology, which allows to use the same resource by 3GPP LTE high-end equipment and NB-IoT low-end devices. The need of sharing the limited amount of available resource efficiently emphasizes the importance of theoretical study of formulated problem. The model of resource allocation and sharing for conjoint servicing of real time video traffic of surveillance cameras and NB-IoT data traffic of smart meters and actuators over LTE cell facilities is constructed. In the model the access control is used to create the conditions for differentiated servicing of coming sessions. All random variables used in the model have exponential distribution with corresponding mean values but the obtained results are valid for models with arbitrary distribution of service times. Using the model the main performance measures of interest are given with help of values of probabilities of model’s stationary states. The recursive algorithm of performance measures estimation is suggested. The model and derived algorithms can be used for study the scenarios of resource sharing between heterogenous data streams over 3GPP LTE with NB-IoT functionality.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The essential trend in the development of telecommunications is growth of the volumes and the diversity of Internet of Things (IoT) applications. The IoT can be typically defined as a network of multiple physical smart objects (vehicles, actuators, sensors, etc.) which have ability to produce, process and exchange data without involvement of human beings [1,2,3,4,5,6]. These digital devices have low storage capabilities and processing capacities and aim more at reliability of information delivery to the data centers for collecting and proceeding. Together with usage of low-traffic smart meters we see the growing impact of multimedia traffic, for example collected by video surveillance systems deployed for security and safety reasons [7]. This trend has been recognized and supported by 3GPP with developing of NarrowBand IoT (NB-IoT) technology, which allows to use the same spectrum by 3GPP LTE high-end equipment and NB-IoT low-end devices [2, 3]. By providing the technical instruments that can be used for radio resources sharing between LTE and NB-IoT technologies, 3GPP does not formulate the concrete solutions on how these resources should be shared. This problem can be solved by mathematical modeling with taking into account the features of traffic streams forming and accepting for servicing [7,8,9,10].
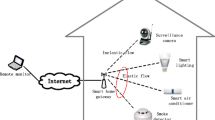
In this paper we address the above mentioned challenges by constructing an analytical framework for modeling the process of resource sharing for an operator planning to create and exploit surveillance system. The system consists of numerous video cameras to perform video monitoring and a large number of smart meters. Both network segments collecting and transfer heterogenous data streams to analytical centers over existent infrastructure of LTE network (see Fig. 1).
The proposed model generalizes the results of [7,8,9,10] by considering arbitrary number of traffic streams created by video cameras (LTE-devices) and one traffic stream originated from NB-IoT devices. In the model the access control is used to create the conditions for differentiated servicing of coming sessions. All random variables used in the model have exponential distribution with corresponding mean values but the obtained results are valid for models with arbitrary distribution of service times. Three scenarios of resource sharing by coming traffic streams are considered: Slicing when resources are strictly divided among LTE and NB-IoT devices traffic streams; Fully shared, when resources are fully shared and Access controlled, when the access to resource is restricted depending on the amount of resource occupied by corresponding traffic stream.
The rest of the paper is organized as follows. In Sect. 2 the mathematical description of the model will be presented. Here the system of state equations that relates the model’s stationary probabilities is outlined and main performance measures are defined. In Sect. 3 the recursive algorithm of characteristics calculation is formulated. Next section is devoted to the discussion of approachers that alow to increase the effectiveness of recursive algorithm. Numerical assessment of the suggested scenarios of resource sharing is performed in Sect. 5. Conclusions are drawn in the last section.
2 Model Description
We consider an LTE cell with a base station placed in its center and formalize the process of resources sharing. The volume of available radio resources of LTE cell in uplink direction given by network slicing for serving traffic streams originated by surveillance cameras and NB-IoT sensors is measured in units of its smallest granularity. It is clear that the smallest requirement has NB-IoT device session so we can call it NB-IoT resource unit or simply resource unit. Let us suppose that total amount of given resource units is a function of the number of resource blocks (RB) and denote by v, the total number of resource units and by c denote the transmission speed provided by one unit.
Let us suppose that surveillance cameras are varying in quality. It means that corresponding traffic sessions produced by cameras are varying by volume. To take into account this property we consider n types of traffic sessions. Let us suppose that LTE devices traffic sessions of type k are coming after random time having exponential distribution with parameter \(\lambda _k\), each session requires \(b_k\) resource units for servicing and occupies this resource for random time having exponential distribution with parameter \(\mu _k\), \(k=1,\ldots ,n\). It is suggested that blocked LTE devices sessions are lost without resuming. Let us suppose that traffic sessions produced by NB-IoT devices are coming after random time having exponential distribution with parameter \(\lambda _d\), each session requires \(b_d\) resource units for transmitting of files having exponential distribution with mean F. The service time of NB-IoT session has exponential distribution with mean value \(\frac{F}{b_d}\) and parameter \(\frac{b_d}{F}\). It is suggested that blocked LTE devices sessions are lost without resuming.
Let us formalize scenarios of resource sharing by coming traffic streams. The simplest scenario corresponds to the case when all v resource units are strictly divided among LTE devices sessions and NB-IoT devices sessions. Let us denote by \(v_{\ell }\) the number of resource units that is given for exclusive usage to LTE devices sessions and by \(v_b =v-v_{\ell }\) we denote the number of resource units given for exclusive usage to NB-IoT devices sessions correspondingly. By varying the values of \(v_{\ell }\) and \(v_b\) we can give the priority in resource usage to the chosen traffic type but as we show later this way of resource sharing greatly decreases the usage of resource unit.
Next scenario is related with access control. Let us denote for k-th flow of LTE devices sessions by \(c_k\) the maximum allowed number of traffic sessions that can be on service at the same time. In a similar way let us denote for NB-IoT devices sessions by \(c_d\) maximum allowed number of traffic sessions that can be on service at the same time. For this type of resource usage the traffic session of k-th flow can be blocked for two reasons: (1) if \(v_k=c_kb_k\) resource units have already been occupied by sessions from the k-th flow or (2) if total number of busy resource units is greater than \(v-b_k\). The same is true for NB-IoT devices sessions. The coming session of this type can be blocked for two reasons: (1) if \(v_d=c_db_d\) resource units have already been occupied by NB-IoT devices sessions or (2) if total number of busy resource units is greater than \(v-b_d\). We show later that by using the access control (by choosing the values of \(v_k\), \(k=1,\ldots ,n\) and \(v_d\)) we can give the priority in resource usage to chosen traffic type and increase the usage of resource unit compare to static scenario.
The last scenario corresponds to the case when resources are fully shared without giving priority to some traffic streams. In this case we usually increase the usage of resource unit compare to formulated above scenarios but we are not able to reach the same level of sessions losses for all type of traffic streams considered in the model. All three formulated scenarios can be modeled by proper choosing of v and access boundaries \(v_k\), \(k=1,\ldots ,n\) and \(v_d\) so further we will study only model of resource sharing based on access control.
Let us denote by \(i_{k}(t)\) the number of LTE devices sessions of k-th flow being on servicing at time t, and by d(t) we denote the number of sessions of NB-IoT devices being on servicing at time t. The dynamic of a model states changing is described by Markov process
defined on the finite set of model’s states S. Let us denote by \((i_{1},\ldots ,i_{n},d)\) the state of r(t). The vector \((i_{1},\ldots ,i_{n},d)\) belongs to S when \(i_{k}\), \(k=1,\ldots ,n\), d varies as follows
Let us denote by i for state \((i_{1},\ldots ,i_{n},d)\in S\) the number of occupied resource units \(i=i_1b_1+\ldots +i_nb_n+db_d\).
Let us denote by \(p(i_{1},\ldots ,i_{n},d)\) the value of stationary probability of state \((i_{1},\ldots ,i_{n},d) \in S\). It can be interpreted as portion of time the model stays in the state \((i_{1},\ldots ,i_{n},d)\). This interpretation gives the possibility to use the values of \(p(i_{1},\ldots ,i_{n},d)\) for estimation of model’s main performance measures. Let us define for k-th flow of LTE devices traffic by \(\pi _{k}\) the portion of lost sessions and by \(m_k\) the mean number of occupied resource units. Their formal definitions are looking as follows
Here \(U_k\) is defined as subset of S having property \((i_1,\ldots ,i_n,d)\in U_k\), if \(i_k+1>c_k\) or \(i+b_k> v\). In the same way we define the performance measures of NB-IoT devices traffic servicing. They are \(\pi _{d}\) the portion of lost sessions and \(m_d\) the mean number of occupied resource units
Here \(U_d\) is defined as subset of S having property \((i_1,\ldots ,i_n,d)\in U_d\), if \(d+1>c_d\) or \(i+b_d> v\).
System of state equations is obtained after equating the intensity of transition r(t) out of the arbitrary model’s state \((i_{1},\ldots ,i_{n},d)\in S\) to the intensity of transition r(t) into the state \((i_{1},\ldots ,i_{n},d)\)
Here \(I(\cdot )\) — is indicator function. Values \(P(i_1,\ldots ,i_n)\) should be normalized.
It can be proved that r(t) is reversible Marcov process. From relations of detailed balance follows that values of \(P(i_1,\ldots ,i_n,d)\) can be found as a unique solution of the system of state equation that has a product form [11,12,13].
Here \(a_k=\lambda _k/\mu _k\) and \(a_d=\lambda _d/\mu _d\) are offered traffic expressed in Erlangs and N is a normalizing constant
3 Recursive Algorithm
The values of introduced performance measures can be found by convolution algorithm [11, 14] based on the product form (3). Let us introduce two auxiliary notions. For two vectors \(x=(x(0),x(1),\ldots ,x(a_x))\) and \(y=(y(0),y(1),\ldots ,y(a_y))\) we define the convolution operator that being applied to x, y gives vector z with components found in accordance with formula
Now let us take the k-th flow of LTE devices traffic and find the state probabilities of resource occupancy as if it was the only traffic stream offered to \(v_k\) resource units. We denote by \(P_k(i)\) the value of unnormalized probability that i resource units are occupied. We shall call \(P_k(i)\), \(i=0,1,\ldots ,v_k\), as the individual distribution of the k-th flow. Let \(P_k(0)=1\) than
In the same way we can find the individual distribution for NB-IoT devices traffic
Recursive algorithm of estimation of the \(\pi _d\) and \(m_d\) consists of making the following three steps.
-
1.
By using (5),(6) we find \(P_k(i)\), \(i=0,1,\ldots ,v_k\), \(k=1,\ldots ,n\) and \(P_d(i)\), \(i=0,1,\ldots ,v_d\).
-
2.
In order of numbering the LTE devices traffic streams we do the successive convolution of all n individual state distributions. Let us denote by \(P^{(n)}(\cdot )\) the vector obtained after convolving the all n individual distributions.
-
3.
Finally we convolve vectors \(P^{(n)}(\cdot )\) and \(P_d(\cdot )\) and obtain after normalization the system state distribution
$$\begin{aligned} P(i)=\sum \limits _{u=0}^i P_d(u)\, P^{(n)}(i-u)\, I\bigl (u\le c_d\,b_d, \, i-u \le v\bigr ),\,\, i=0,1,\ldots ,v, \end{aligned}$$(7)and values of \(\pi _d\) and \(m_d\)
$$\begin{aligned} \pi _{d}=\sum \limits _{i=v-b_d+1}^{v} P(i)+P_d(c_d\,b_d) \sum \limits _{i=c_d\,b_d}^{v-b_d}\,P^{(n)}(i-c_d\,b_d); \end{aligned}$$(8)$$ m_d=a_d(1-\pi _d). $$
The performance measures for all flows of sessions can be found after performing the above mentioned steps for each flow by putting it at the end of the convolution procedure. This action needs to perform \(n(n+1)\) convolutions.
4 Enhancements of Recursive Algorithm
Let us consider two enhancements of the used approach that can decrease the amount of computational works when calculating the performance measures for all traffic streams and improve the stability of algorithm when calculating the performance measures for large values of v. We start from the procedure that decreases the total number of convolutions by remembering the results of intermediate convolutions [15]. Let us represent the number of flows \(n+1\) in a binary form \(n+1=2^{l_1}+2^{l_2}+\cdots +2^{l_s}\) and relate with each of binary terms \(2^{l_r},\ r=1,\ldots ,s\) a binary tree consisting of \((l_r+1)\) levels where level 0 has \(2^{l_r}\) leaves and level \(l_r\) is the root of the binary tree. We accept further that all trees are numbered in decreasing order of corresponding binary groups and that levels of the same number are located on the same line. An example of such a group of trees for \(n+1=7\) is shown in Fig. 2.
Let us construct an algorithm for determining performance measures of all streams by making only \(4n-2\) convolutions.
-
1.
Number leaves and nodes of each level in the order used in Fig. 2 and relate with leaf number m, \(m=1,\ldots ,n+1\) the vector of individual state distribution of the corresponding flow of sessions (we suppose that the flow of NB-IoT devices sessions has number \((n+1)\)).
-
2.
Relate with each non-leaf node of all trees the result of convolution of vectors associated with two sons of the node considered. It can be done by \(w_1=n+1-s-I(s=1)\) convolutions (here \(I(\cdot )\)—is an indicator function).
-
3.
For the root node of the tree number r, \(r=1,\ldots ,s\), convolute all vectors associated with root nodes of the trees number \(f=1,\ldots ,s, f\ne r\) and associate the resultant vector with root node of the tree number r. It gives \(w_2=3(s-2+I(s=1))\) convolutions.
-
4.
For tree number r, \(r=1,\ldots ,s,\) associate with each node located on level j consequently for \(j=l_r-1,l_r-2,\ldots ,0\), the result of convolution of the vector associated with this node and the vector associated with his father if \(j=l_r-1\) or brother of his father if \(j<l_r-1\). This step is made if \(l_r>0\). To do this we need to perform \(w_{3}=2(n+1-s-I(s=1))\) convolutions.
-
5.
Finally, convolve each vector associated with leaf node with the vector formerly associated with his brother or with him if the considered binary group consists of one element and calculate the individual performance measures by using (8). Last step takes \(w_{4}=n+1\) convolutions.
It is easy to check that totally we need to make \(4n-2\) convolutions to find the performance measures for all streams. This is less than \(n(n+1)\) if we try to find characteristics for all flows without keeping the results of intermediate convolutions.
Next refinement of recursive algorithm devoted to analysis of cases with big values of v. In the process of construction of the model (see Sect. 2) it was supposed that the transmission speed provided by one resource unit corresponds to the requirement of NB-IoT session. Because this requirement is quite small compare to transmission speed provided by all available resource it increases the values of v up to several hundreds of resource units or even more. This leads to numerical instability of the implementation of recursive algorithm. To overcome this difficulties we construct modified version of convolution algorithm by introducing the truncation levels for individual distributions into account. Let us suppose that we a priory know the truncation levels for vectors of individual and convoluted distributions. The modified version of recursive algorithm is looking as follows.
As was done in Sect. 3 we calculate the state probabilities for each stream as if it was the only traffic stream offered to all available resource. We start the calculation procedure from the state having the maximum relative value of probability. Let us show the details on the example of the k-th flow of LTE devices traffic. We suppose that for k-th flow this state is \(i_k^*\). It is easy to verify that \(i_k^*=min(\lfloor a_k \rfloor ,c_k). \) Next we take \(P_k(i_k^*)=1\) and make recurrence in both or one (depending on the relation between \( a_k\) and \(c_k\)) directions of decreasing \(P_k(i)\) by using relations
Here \(b_k^u,b_k^l\) are correspondingly upper and lower truncation levels for the individual state distribution of the \(k-\)th stream. This calculation is made for all streams. The convolution operator that being applied for two truncated vectors x, y where \( x=(x(t_x^l),x(t_x^l+1),\cdots ,x(t_x^u)),\;\) \( y=(y(t_y^l),y(t_y^l+1),\cdots ,y(t_y^u)) \) gives vector z with components \( z(i)=\sum _{j=l(i)}^{u(i)}x(i-j) \cdot y(j),\) \(\; i=t_z^l,t_z^l+1,\cdots ,t_z^u, \) with functions u(i), l(i)
The consequence of making convolutions remains the same as in the previous case. The choice of truncation levels and estimation of the error caused by truncations can be done similar to solving the analogous problems in [15]. All random variables used in the model have exponential distribution with corresponding mean values but the obtained results are valid for models with arbitrary distribution of service times [13].
5 Numerical Assessment
By using the elaborated mathematical model and algorithms of it’s performance measures estimation we can analyze the effectiveness of suggested scenarios of resource allocation. The level of traffic load can be characterized by \(\rho \) the offered load per one resource unit. To define \(\rho \) it is necessary to find the offered load of each traffic stream considered in the model. Let us denote by \(A_k\) the offered load expressed in resource units for k-th flow of LTE devices traffic \( A_k=\frac{\lambda _k}{\mu _k}\,b_k=a_kb_k. \) Let us denote by \(A_d\) the offered load expressed in resource units for flow of NB-IoT devices sessions \( A_d=\frac{\lambda _d}{\mu _d}\,b_d=a_db_d=\frac{\lambda _d F}{b_d}. \) The value of \(\rho \) can be defined from relation \( \rho =\frac{A_1+\ldots +A_n+A_d}{v}. \)
Let us consider the model with following values of input parameters: \(v=200\) resource units (r.u.); transmission rate that is provided by one resource unit is \(c=100\) kbit/c; \(n=1\); \(b_1=10\) r.u.; \(b_d=1\) r.u.; \(F=100\) kbit; \(1/\mu _1=10\) c; \(1/\mu _d=1\) c. We begin the model’s numerical assessment with Fig. 3 that presents the values of \(\pi _1\) and \(\pi _d\) and Fig. 4 with mean values of unit usage by LTE devices traffic — \(\delta _1\) and NB-IoT devices traffic—\(\delta _d\) and the their sum \(\delta =\delta _1+\delta _d\) vs the value of \(\rho \) the offered load of one resource unit. The values of performance measures are obtained by recursive algorithm presented in Section 3 with enhancements discussed in Sect. 4. Let us suppose that both traffic flows considered in the model generate the same offered load \(A_1=A_d=\frac{v\rho }{2}\). It allows to find the intensities \(\lambda _1\), \(\lambda _d\) of sessions coming for each flow considered in the model from known values of \(\rho \). The results presented in Fig. 3 and Fig. 4 show that despite equality of offered traffic NB-IoT-devices sessions obtain priority in occupying the transmission resource that is clearly seen in overload conditions, when \(\rho >1\), (see Fig. 4).
The only way to overcome mentioned difficulties is to create the conditions for differentiated servicing of coming sessions. Three scenarios of resource sharing are compared: Slicing when resources are strictly divided among LTE devices and NB-IoT devices traffic streams, Fully shared, when resources are fully shared and Access controlled, when the access to resource is restricted depending of the amount of resource occupied by corresponding traffic stream. We compare the properties of the discussed resource allocation procedures with Fig. 5 that presents the portion of the lost LTE devices sessions vs intensity of offered NB-IoT devices sessions and Fig. 6 that presents the mean value of resource unit usage vs intensity of offered NB-IoT devices sessions.
The model input parameters are the same as was used in Fig. 3 and Fig. 4 except \(a_1=10\) Erl. For Slicing scenario \(v_{\ell }=v_{b}=100\) r.u. For Access controlled scenario \(v_1=200\) r.u., \(v_d=100\) r.u. The presented results can be summarized as follows.
-
1.
The simplest for usage Slicing scenario when resources are strictly divided among LTE devices and NB-IoT devices traffic streams can be used for achievement of prescribed values of performance indicators but have two drawbacks. The first is the high degree of sensitivity of characteristics to the value of offered load that requires a priory knowledge of the traffic intensity. The second is the lower values of resource unit usage compare to the Access controlled and Fully shared scenarios.
-
2.
Fully shared scenario have the best values of resource unit usage but allows the degradation of losses for heavy traffic especially in situation of overload (see, Fig. 4).
-
3.
Access controlled scenario outperform Slicing scenario and is free from negative features of Fully shared scenario. The suggested procedure of resource allocation is recommended for implementation over 5G mobile networks.
The usage of Access controlled scenario for solving of the problems of conjoint servicing of NB-IoT devices sessions and LTE devices sessions that was discussed above in Fig. 3 and Fig. 4 is presented in Fig. 7 and Fig. 8 for the same values of model input parameters and \(v_1=200\) r.u., \(v_d=100\) r.u.
6 Conclusion
The model of resource allocation and sharing for conjoint servicing of real time video traffic of surveillance cameras and NB-IoT data traffic of smart meters and actuators over LTE cell facilities is constructed. In the model the access control is used to create the conditions for differentiated servicing of coming sessions. All random variables used in the model have exponential distribution with corresponding mean values but the obtained results are valid for models with arbitrary distribution of service times. Using the model the main performance measures of interest are given with help of values of probabilities of model’s stationary states. The recursive algorithm of performance measures estimation is suggested.
Two enhancements of the used approach that can decrease the amount of computational works when calculating the performance measures for all traffic streams and improve the stability of algorithm when calculating the performance measures for large values of v are considered. The first enhancement is based on the remembering the results of intermediate convolutions that allows to decrease the total number of convolutions. Next refinement of recursive algorithm devoted to analysis of cases with big values of v. This leads to numerical instability of the implementation of recursive algorithm. To overcome this difficulties we construct modified version of convolution algorithm by taking into account the truncation levels for individual distributions.
The model and derived algorithms can be used for study the scenarios of resource sharing between heterogenous data streams over 3GPP LTE with NB-IoT functionality. The numerical assessment shows that simplest for usage Slicing scenario when resources are strictly divided among LTE devices and NB-IoT devices traffic streams can be used for achievement of prescribed values of performance indicators but have number of drawbacks main among them is the high degree of sensitivity of characteristics to the value of offered load. Access controlled scenario outperform Slicing scenario and is free from negative features of Fully shared scenario. The suggested procedure of resource allocation is recommended for implementation over 5G mobile networks.
The constructed analytical framework additionally offers the possibility to find the volume of resource units and access control parameters required for serving incoming traffic with given values of performance indicators. Proposed model can be further developed to include the possibility of reservation and using the processor sharing discipline for serving NB-IoT sessions traffic [16,17,18].
References
Mehmood, Y., Ahmad, F., Yaqoob, I., Adnane, A., Imran, M., Guizani, S.: Internet-of- things-based smart cities: recent advances and challenges. IEEE Commun. Mag. 55(9), 16–24 (2017)
Rico-Alvarino, A., et al.: An overview of 3GPP enhancements on machine to machine communications. IEEE Commun. Mag. 54(6), 14–21 (2016)
3GPP. Standardization of NB-IOT completed (2016). http://www.3gpp.org/news- events/ 3gpp-news/1785-nb_iot_complete
Nokia. Dynamic end-to-end network slicing for 5G. White Paper (2017)
ElHalawany, B.M., Hashad, O., Wu, K., Tag Eldien, A.S.: Uplink resource allocation for multi-cluster internet-of-things deployment underlaying cellular networks. Mob. Netw. Appl. 25(1), 300–313 (2019). https://doi.org/10.1007/s11036-019-01288-6
Malik, H., Pervaiz, H., Alam, M.M., et al.: Radio resource management scheme in NB-IoT systems. IEEE Access. 6, 15051–15064 (2018)
Begishev, V., Begishev, V., et al.: Resource allocation and sharing for heterogeneous data collection over conventional 3GPP LTE and emerging NB-IoT technologies. Comput. Commun. 120(2), 93–101 (2018)
Gudkova, I., et al.: Analyzing impacts of coexistence between M2M and H2H communication on 3GPP LTE system. In: Mellouk, A., Fowler, S., Hoceini, S., Daachi, B. (eds.) WWIC 2014. LNCS, vol. 8458, pp. 162–174. Springer, Cham (2014). https://doi.org/10.1007/978-3-319-13174-0_13
Stepanov, S., Stepanov, M., Tsogbadrakh, A., Ndayikunda, J., Andrabi, U.: Resource allocation and sharing for transmission of batched NB-IoT traffic over 3GPP LTE. In: The Proceedings of the 24th Conference of Open Innovations Association (FRUCT), pp. 422–429. Moscow Technical University of Communications and Informatics. Moscow (2019)
Stepanov, S.N., Stepanov, M.S.: Efficient algorithm for evaluating the required volume of resource in wireless communication systems under joint servicing of heterogeneous traffic for the internet of things. Autom. Remote Control 80(11), 2017–2032 (2019). https://doi.org/10.1134/S0005117919110067
Iversen, V.B.: Teletraffic Engineering and Network Planning. Technical University of Denmark (2010)
Ross, K.W.: Multiservice Loss Models for Broadband Telecommunications Networks. Springer, Heidelberg (1995). https://doi.org/10.1007/978-1-4471-2126-8
Kelly, F.P.: Blocking probabilities in large circuit-switched networks. Adv. Appl. Prob. 18, 473–505 (1986)
Iversen, V.B.: The exact evaluation of multi-service loss system with access control. Teleteknik 31(2), 56–61 (1987)
Iversen, V.B., Stepanov, S.N.: The usage of convolution algorithm with truncation for estimation of individual blocking probabilities in circuit-switched telecommunication networks. In: Ramaswami, V., Wirth, P.E. (eds.) Proceedings ITC 15, pp. 1327–1336. Elservier, Amsterdam (1997)
Stepanov, S.N., Stepanov, M.S.: Planning transmission resource at joint servicing of the multiservice real time and elastic data traffics. Autom. Remote Control. 78(11), 2004–2015 (2017)
Stepanov, S.N., Stepanov, M.S.: Planning the resource of information transmission for connection lines of multiservice hierarchical access networks. Autom. Remote Control 79(8), 1422–1433 (2018). https://doi.org/10.1134/S0005117918080052
Stepanov, S.N., Stepanov, M.S.: The model and algorithms for estimation the performance measures of access node serving the mixture of real time and elastic data. In: Vishnevskiy, V.M., Kozyrev, D.V. (eds.) DCCN 2018. CCIS, vol. 919, pp. 264–275. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-99447-5_23
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2020 Springer Nature Switzerland AG
About this paper
Cite this paper
Stepanov, S.N., Stepanov, M.S., Andrabi, U., Ndayikunda, J. (2020). The Analysis of Resource Sharing for Heterogenous Traffic Streams over 3GPP LTE with NB-IoT Functionality. In: Vishnevskiy, V.M., Samouylov, K.E., Kozyrev, D.V. (eds) Distributed Computer and Communication Networks. DCCN 2020. Lecture Notes in Computer Science(), vol 12563. Springer, Cham. https://doi.org/10.1007/978-3-030-66471-8_32
Download citation
DOI: https://doi.org/10.1007/978-3-030-66471-8_32
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-66470-1
Online ISBN: 978-3-030-66471-8
eBook Packages: Computer ScienceComputer Science (R0)