Abstract
Internet-of-Things (IoT) deployment underlaying cellular communication have been drawing increasing attention in recent years. In this work, we consider Device-to-Device (D2D) communication technology for enabling uplink transmission in multiple IoT groups/clusters at which the resource block (RB) of each cellular user is reused by multiple IoT devices (IoTDs). Joint resources and power allocation optimization problem is formulated for maximizing both the IoTDs connectivity and cell throughput under an interference constraint. A heuristic algorithm, namely greedy iterative matching (GIM), is proposed as a sub-optimal solution for the resource allocation problem while a fixed-power margin technique is used for the cellular users’ power allocation. Simulations results show that the proposed GIM algorithm provides enhanced cell throughput gain and accessibility to IoTDs. The proposed reuse model is applicable in a network at which the number of IoTDs deployed within multiple groups is larger than the available cellular reuse partners.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Internet of Things (IoT) has emerged as a promising technology for a fully connected world through which billions of objects such as sensors, machines, vehicles, and other devices to be connected to the Internet [27]. The ultimate goal for such massive connectivity is to improve utilization, enhance process efficiency, and introduce new business models in every aspect of life such as smart grids, health and environmental monitoring, security, and intelligent transportation systems [34]. Over 60 percent of IoT applications, including machine-type communication (MTC), have many unique features such as low power, short-range, long battery life, massive connectivity, and wide coverage. However, existing wireless technologies, such as Bluetooth, Wi-Fi, and ZigBee do not well support such features [10]. Recently, different technologies are introduced to support the IoT deployment especially underlaying the existence of cellular networks such as Narrow-Band Internet-of-Things (NB-IoT). NB-IoT is a promising emerging low-power, wide-area (LPWA) technologies that are released by the Third Generation Partnership (3GPP), and is adapted by Ericsson, Nokia, and Huawei as part of the fifth generation (5G) wireless systems [16]. The main noticeable feature of NB-IoT is the compatibility with existing Long-Term Evolution (LTE) functionalities, which facilitate the coexistence of such IoT deployment using existing infrastructure [16, 24]. However, a large number of devices in IoT systems yields tremendous traffic pressure and congestion in the network, which imposes critical challenges to the coexistence of NB-IoT and cellular systems.
In order to address such challenges, a combination of 5G heterogeneous network architecture [25, 35], low power transmission, and device-to-device (D2D) communication [14] features are expected to provide feasible solutions to such challenges. By offloading traffic through nearby small cells (or gateways), IoT devices can effectively reduce the power consumption and guarantee the throughput requirement and quality of service (QoS) of IoT systems. With the appropriate signaling protocols, the small-cell gateways could aggregate traffic from a large number of low-power IoT devices (IoTDs) into the existing cellular networks.
In D2D technology, communication between nodes in close proximity to each other is performed without passing the messages through the macro base station, or the evolved Node Base station (eNB). The direct D2D communication introduces benefits for the network such as lower energy consumption due to short range transmission, load balancing, traffic offloading, and better coverage for edge users [3, 14]. In order to support the operation of D2D communication, two modes are defined in LTE networks, namely the dedicated mode, known as overlay, and the reuse mode [13], known as underlay. In dedicated mode, D2D nodes share the available cellular spectrum with orthogonal sharing (i.e. a part of the available radio resources is dedicated for D2D nodes).
On the other hand, D2D nodes in the underlay cellular communication mode reuse the same resources of users’ equipment (UEs) under control of the base station [22, 37] in a non-orthogonal way, which provides efficient utilization of the available spectrum to support more users in the system. Hence, the spectrum efficiency, as well as the network throughput, can be increased under a controlled interference from D2D communication. Moreover, this type of non-orthogonal resources sharing offers different types of gains [22] such as proximity gain, hop gain, reuse gain, and pairing gain. However, interference management is needed to guarantee successful detection of the simultaneously transmitted signals at the destinations in this mode [2]. There are different resource allocation methods in D2D communication underlaying cellular networks that are described in [22, 33]. In this work, we exploit D2D reuse mode for enabling IoT devices to upload messages to a gateway by sharing the resources of a group of cellular users while guaranteeing the target rate for both UE and IoT devices.
The success of such heterogeneous architecture assuming an interplay between IoT systems and D2D communication necessitates careful resource management, power allocation, and transmission scheduling which is generally non-deterministic polynomial-time hard (NP-hard) problems [3, 10, 11]. It is worth noting that the process of resource sharing in D2D and machine to machine (M2M) networks are investigated from different perspectives in order to optimize various performance metrics and enable different applications [3, 5, 6, 10,11,12, 17,18,19,20, 23, 28, 29, 31, 32]. In the context of this work, we summarize a survey report in Table 1, which compares a group of optimization problems in terms of deployment scenario, objective, optimization variables, and the used algorithm.
The authors in [19] considered a successive convex approximation to solve a joint rate and power control problem that maximizes the network utility subject to the capacity and the primary user (PU) outage constraints in multi-hop cognitive radio networks (CRNs). By targeting a high-performance video streaming, the authors in [32] exploited D2D helper-requester pairs for achieving a high quality of experience (QoE) at high energy efficiency (EE) taking into consideration the co-channel interference over D2D communications in 5G networks. Similarly, the authors in [31] proposed a joint caching and downlink resource sharing optimization framework to efficiently deliver multimedia contents to the mobile users in a wireless multimedia sensor networks (WMSNs). Additionally, the EE maximization has recently gained a lot of attention for different networks architectures. In those schemes, the EE is targeted alone or as a joint objective with other performance metrics such as latency, sum rate maximization, etc. [17, 18, 28, 29]. The authors in [17] investigated different resource allocation schemes for EE maximization for various wireless networks. The authors in [5] investigated a sum-rate maximization problem for simultaneous spectrum access of M2M and human-to-human (H2H) communications in uplink multi-cluster underlaying cellular communication. In [6], the authors considered the dynamic allocation for M2M using a proportional integral derivative (PID) controller to mitigate M2M interference on H2H communication under data rate and fairness constraints.
In [11], the authors proposed a two time-slots downlink transmission protocol for ultra-reliable and low latency communication (URLLC) between the base station (BS) and a group of clustered IoT devices (IoTDs) within a factory system. The proximity service of D2D communication is used as a means for delivering a short-range reliable transmission mechanism from a cluster-head to IoTDs in the second time-slot. The authors in [10] adopted D2D communication technique as a mean of route extension of NB-IoT systems. In [20], the authors proposed a social-aware group formation framework to allocate resource blocks (RBs) effectively in NB-IoT solution. The authors in [3, 23] proposed resource allocation protocols to provide the required connectivity between a group of IoTDs and its associated cluster-head using D2D communication underlaying LTE networks for uplink transmission. In [12], the authors proposed a multi-antenna transceiver design and multi-hop D2D communication to guarantee reliable transmission and extend the unmanned aerial vehicles (UAV) coverage for IoT in disasters.
In this work, we consider the D2D communication technique for enabling a multi-cluster IoT deployment at which multiple groups of IoTDs are uniformly deployed in the vicinity of K cluster heads devices that works as a gateway/small-cell for the entire cluster. Each IoTD is allowed to reuse the RB of one UE for uplink transmission while the RB of each cellular user can be shared by one IoTD from each IoT group (IoTG) provided that all reuse partners can achieve their pre-defined quality-of-service (QoS) requirements. The proposed optimization problem is formulated for maximizing both the IoTDs connectivity and cell throughput under a fixed power-margin interference management scheme that is used for the cellular users’ power allocation.
By carefully allowing IoT devices to share the cellular resources, the spectrum efficiency, in terms of the total network throughput, is maximized while guaranteeing QoS. In spite of the fact that we do not investigate EE in this work, the proposed algorithm can intuitively improve the EE by limiting the transmit power of the admitted IoTDs in order to satisfy the interference constraints. This means that the admitted IoTDs are the group that can achieve QoS requirements with a low-power transmission. The major contributions in this work are listed as follows:
Investigate the throughput and access rate for a single-cell scenario with a multiple-clusters of IoT devices under a fixed power-margin interference management scheme.
Propose joint resources and power allocation optimization problem for maximizing both the IoTDs connectivity and cell throughput.
A sub-optimal heuristic algorithm, namely greedy iterative matching (GIM), is proposed as a low-complexity sub-optimal solution for the resource allocation problem.
Simulations results show that the proposed GIM algorithm provides enhanced cell throughput gain and accessibility for IoTDs compared to single IoT cluster in [3].
The rest of the paper is organized as follows. In Section 2, we describe the system model while illustrating the QoS requirements. Then, we introduce the joint optimization problem formulation and the proposed sub-optimal algorithm in Section 3. In Section 4, the performance analysis of the proposed algorithm is analyzed. Finally, the paper is concluded in Section 5.
2 System model
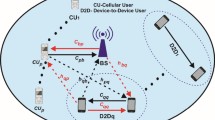
In this work, we focus on a single-cell uplink scenario, as shown in Fig. 1. We consider a group of cellular users equipment (UEs), \(\mathcal {M} = \{UE_{m} |m = 1,..., M\}\), that communicate with one BS in a traditional cellular mode. Each UE is assigned with one subcarrier with no interference among UEs.Footnote 1 There is a set of IoT gateway (IoT-GW) nodes, \(\mathcal {K} = \{IoTG_{k} |k = 1,..., K\}\), deployed within the cell, which are surrounded by a group of uniformly distributed IoTDs within a disc of radius rmax around each GW. The number of IoTDs communicating with each GW is N, where all nodes are equipped with a single antenna.
We assume that \({h_{m}^{b}}\), \(h_{m,k}^{g}\), \(h_{n,k}^{b}\), and \(h_{n,l,k}^{g}\) represent the channels between the mth UE to BS, mth UE to the kth GW, nth IoTD to BS, and nth IoTD in the lth IoTG to the kth GW, respectively. We assume a distanced based path-loss model defined as \( P_{\mu } =P_{\eta } L d_{\eta ,\mu }^{-\alpha }\), where Pη and Pμ are the transmit and received powers, respectively. dη,μ is the distance between node η and node μ, α is the path-loss exponent and L is the path-loss constant. We also assume that the BS knows the locations of the users within the cell, and so perfect channel state information (CSI) is available at the BS whose responsibility is to pair the UEs and IoTDs and optimize the power allocations. Assume that at maximum one IoTD from each IoTG is allowed to share the resources of any UE Footnote 2 provided that QoS requirements of all paired nodes are satisfied. In other words, each UE is willing to support more than one IoTD as reuse partners as long as they all can satisfy their QoS constraints assuming only one IoTD from each group at maximum is permitted per UE.
Let \({x_{m}^{u}}\) and \(x_{n,k}^{d}\) be the information symbols of the mth cellular user UEm and nth IoT device IoTDn in the kth IoT group IoTGk with the expectation \( E\{|{x_{m}^{u}}|^{2}\} = 1 \) and \( E\{|x_{n,k}^{d}|^{2}\} = 1 \). The received signals at the eNB and at the kth IoT-GW on the mth subcarrier, respectively are given by:
where Pm and Pn,k are the transmit powers of the mth UE and the nth IoTD in the kth IoTG, respectively. nb and \({n_{k}^{g}}\) are the additive white Gaussian noise (AWGN) at the eNB and the kth IoT-GW, respectively with the same distribution \(\mathcal {CN}(0,N_{o})\), where No is the noise power. am,n,k is a binary pairing coefficient which is given as follows:
We assume that the destinations (i.e., eNB and the K IoT-GW) have certain QoS constraints, Γu and Γg, that need to be satisfied in order to correctly decode the received signals from the UE and the IoTDs. In order to consider sharing the same subcarrier between one UE and a K IoTDs (one IoTD from each IoTG at maximum), a fixed-power margin (FPM) interference management scheme is adapted [3, 8, 9]. In FPM scheme, the average received powers from all UEs at eNB are controlled to the same power level denoted by \(P^{u}_{eNB}\). Therefore, based on the path-loss model, the transmit power of the mth UE, Pm, is given by:
A power margin in the signal-to-interference-plus-noise ratio (SINR) of the UE is assumed to protect the UE from excessive interference from the IoT reuse partners. This power margin (i.e., κ) is used by the eNB to determine: (1) The maximum allowable interference introduced by all paired IoTDs to avoid harmful interference to the UE. (2) The maximum power to be allocated to the IoTDs which can be derived by taking κ into account when calculating the signal-to-noise ratio (SNR) at eNB. If the IoTDs control their introduced interference perfectly, the UE achieves the required QoS (i.e., Γu) by scaling its own transmit power, Pm, by a factor of κ. In other words, in the absence of interference from the IoTDs, the UE link achieves κΓu signal-to-interference ratio (SIR), or SINR with zero interference, as follows:
where (\( P^{u}_{eNB}= \kappa {\Gamma }_{u} N_{o}\)) represents a lower bound on the received power at the BS from each UE. We consider the mth UE to be a candidate partner for the K IoTDs only if the following QoS interference constraints are satisfied (\({r_{m}^{u}} \geq {\Gamma }_{u}\) and \(r_{n,k}^{d} \geq {\Gamma }_{g} \forall \) IoTDs paired with the UE) where \({r_{m}^{u}}\) and \(r_{n,k}^{d}\) are the achievable SINR of the mth UEs and the nth IoTDs in the kth IoTG which are given as follows, respectively:
where \({I_{m}^{u}}\) and \(I_{n,k}^{d}\) are the interference from all IoTDs that reuse the mth UE subcarrier from all IoTGs, and the interference to the nth IoTD on the kth IoTG from the mth UE and all other IoTDs from other groups, which are given as follows:
Now, we would like to find the upper-bound of the interference to the cellular user by considering the SINR QoS constraint (\({r_{m}^{u}} = \frac {P_{eNB}^{u}}{{I_{m}^{u}}+N_{o}} \geq {\Gamma }_{u}\)) where the upper bound is given as as follows:
Hence, without losing generality, if we assume an equal transmit power level of all IoTDs assigned to the mth UE, the IoTDs transmit power can be derived using (8) and (10) as follows:
3 Resources allocation for IoTDs
The resource allocation in such underlay multi-cluster IoT network is a crucial process in optimizing the performance of the network. Therefore, suitable uplink resources allocation need to be controlled by eNB to manage the interference between UEs and IoTDs and between IoTDs themselves to achieve the QoS constraints for the admitted nodes. The author in [3], formulated an optimization problem that maximizes the achievable throughput gain in a single IoT group network where one IoTD is reusing the subcarrier of each UE. In the following sub-section, we formulate an optimization problem for supporting multiple IoT groups and we propose a low complexity suboptimal solution using a greedy iterative matching (GIM) algorithm.
3.1 Problem formulation
The objective of the proposed joint resource and power allocation problem is to find the sub-optimal transmit powers \(\boldsymbol {P_{nk}} = \{P_{n,k}^{*}| \forall n \in \mathcal {N} \text {and} k\in \mathcal {K}\}\) and pairing coefficients \(\{a_{m,n,k}^{*}\}\) of all admitted paired IoTDs that maximize the total cell throughput and achieve the QoS constraints for all nodes. The problem can be mathematically formulated as follows:
where
Constraints C1 and C2 ensure the QoS of all UEs and admitted IoTDs. The pairing coefficients in C3 is set to 1 if the RB of the mth UE is assigned to the nth IoTD in the kth IoTG and 0 otherwise. Constraints C4 are used to make sure that the maximum number of IoTDs in each IoTG reusing the subcarrier of any UE is one to avoid severe harmful interference between IoTDs within the same IoTG. Constraints C5 are used to make sure that each IoTD is reusing only one UE. The group of constraints in C6 is to limit the assigned powers to all IoTDs to the maximum allowed power level \(P_{d}^{max}\). This resource allocation problem is a non-convex, mixed integer non-linear program. The complexity of an exhaustive search algorithm to solve this problem is \(\mathcal {O}((ML)^{KN})\) and hence it is NP-hard for the large values of M, L, N, and L, where L is a finite set of available power levels.
3.2 Matching algorithm
In this sub-section, we try to shed light on the nature of the mixed integer non-linear program (MINLP) proposed in (12) in order to propose our solution. The proposed matching algorithm is a many-to-one matching at which multiple IoTDs (from different IoTGs) are allowed to be paired with one cellular user. Since there is only one IoTD from each IoTG is allowed to reuse the spectrum of each UE, there is at most NK possible combinations for each UE to consider. This leads us to define an M × NK cost matrix \(E^{K} = [e_{m,c(v)}^{K}]\) whose element \(e_{m,c(v)}^{K}\) represents the throughput achieved when the subcarrier of the mth UE is shared with K IoTDs in the combination c(v). c(v) represents one possible combination out of the NK possible combinations that consists of only one device from each IoTG and v is the index of this combination where v ∈{1,2,...,NK}. The throughput element, \(e_{m,c(v)}^{K}\), is given as follows:
where
and
where fn,k is a selector function that equals 1 when the nth IoTD in the kth IoT-GW is paired (i.e., exists in the combination c(v) for which the sum throughput is being calculated). For example, if we have K = 2 IoTGs with N = 2 IoTDs per group, the possible combinations of any UE will be c = {(1,1),(1,2),(2,1),(2,2)}, where \(e_{m,c(1)}^{K} = e_{m,(1,1)}^{K}\), \(e_{m,c(2)}^{K} = e_{m,(1,2)}^{K}\), and so on. Notice that all IoTDs are using the same transmit power level, \(P_{n,k} = P_{n,l} = P_{n,k}^{m}\), given in (11). By inspecting the the elements of EK, it is obvious that they are not unique in terms of the individual IoTDs since each IoTD appears in N combinations in each row. Consequently, the well-known weighted bipartite matching technique is not applicable as IoTDs will be paired with multiple UEs which violates C5. Therefore, we propose a Greedy Iterative Matching algorithm (GIM) as shown in algorithm 1 which is introduced in the following sub-section.
3.3 Greedy iterative matching algorithm (GIM)
The GIM algorithm is proposed to provide a low complexity suboptimal solution of problem (12) iteratively by pairing the maximum allowable number of IoTDs with each UE (i.e., K IoTDs) in step 2 and 3 using the initial cost matrix Ek with k = K. In steps 4 to 7, we propose a greedy matching to get a sub-optimal solution that satisfies the constraint C5 and guarantee the uniqueness of the set of IoTDs. We iteratively check the IoTDs used in best combination in Ek and match the UE in this best combination to the corresponding IoTDs. Then, we set all other elements in Ek to zero that use the same UE and IoTDs in Step 8. We also remove those nodes from the lists of unpaired nodes. If any UEs are still unpaired, this means that those UEs cannot afford the interference introduced by K IoTDs, i.e., the QoS constraints are violated. If any IoTDs are still unpaired, we iteratively repeat the process and try to pair a less number of IoTDs to the unpaired UEs until all UEs are paired or all IoTDs are paired.

A numerical example of the GIM algorithm is in Fig. 11 in Appendix where M = 4, K = 2 and N = 4. Hence, we start the GIM algorithm using the cost matrix EK = E2 where the number of rows equals to |U| = 4 and the number of columns equals to |I| = 42. In this example, maximum number of iterations is M = 4. For the first iteration, itr = 1, we search for the entry with the maximum value of throughput in the cost matrix which is \( e^{k}_{m,c(v)} = e^{2}_{4,c(7)} = 39.42\), i.e., pairing UE4 with IoTD2 from IoTG1 and IoTD3 from IoTG2. Then, in order to satisfy the design constraints in (12), we replace all entries that correspond to any of paired IoTDs and UE with zero (i.e., columns (2,1),(2,2),(2,3),(2,4),(3,3),(1,3) and (4,3)) in addition to the complete row number 4. In itr = 2, again search for the entry with the maximum value of throughput in E2 which is \(e^{2}_{2,(4,4)}=34.29\), i.e., pairing UE2 with IoTD4 from IoTG1 and IoTD4 from IoTG2. Then, replace entries with zero, i.e., (1,4), (3,4), (4,4), (4,1), (4,2) in addition to row number 2. Repeat the same procedures in itr = 3 and itr = 4 and get \(e^{2}_{3,(1,2)} = 28.59\) and \( e^{2}_{1,(3,1)}=25.66\), respectively. Consequently, the final row in Fig. 11 shows the final greedy assignment matrix where each UE is paired with a pair of IoTDs where each combination consisted of 2 IoTDs with one device from each IoTG.
4 Performance analysis and numerical results
In all simulations, UEs and IoTDs are assumed to be uniformly distributed around eNB and IoTG, respectively. The Simulation parameters follow the IEEE WiMAX 2.1 (WIMAX 802.16e) standard which is compatible and inter-operable with time division (TD) LTE which are also adopted in [3, 4, 8] for cluster D2D models. Simulation parameters are listed in Table 2.
The performance of the proposed resources allocation algorithm is measured in terms of the total cell throughput gain and the accessibility of the IoTDs. The dimensions of the matching matrix EK leads to a high complexity if an exhaustive search is used to find the best combination. Figure 2 shows the matching matrix dimension in log scale for a different number of IoTDs per each IoTG. The dimension is given by:
where j is the allowed number of paired IoTDs per one IoTG for each UE and \({C_{j}^{N}}\) is the number of j combinations from N elements. The dimensions of the matching matrix increase exponentially with increasing number of IoTGs and also increasing number of paired IoTDs per each IoTG for each UE and hence, increases the computation complexity. Figure 2 shows the variation of D as a function of the number of IoTGs for different values of the permitted number of IoTDs to be paired with each UE from each IoTG (i.e., j). On the other hand, pairing only one IoTD from each IoTG for each UE (i.e., j = 1) has a significant increase in the throughput compared with the single cluster scenario in [3] with much less complexity than higher values of j. Therefore, we assume a pairing scheme where at most one IoTD from each IoTG is paired with each UE if the QoS constraints are satisfied. Notice that the dimension D increases also with the increasing number of IoTGs per cell.
Notice that the worst case computational complexity of the proposed algorithm can be written as:
which can be reduced to \(\mathcal {O}(M N^{k})\), where M is the number of cellular users, N is the number of IoT devices in each cluster, and K is the number of clusters.
In order to reduce the computation complexity, we could assume that IoTDs that are closer than a certain threshold distance to the BS are not allowed to be reuse partners. This assumption gives a two-fold advantage, first, it helps in avoiding severe interference at the BS and reduce the number of combinations. This threshold distance can be lower-bounded using the high-SNR approximation of (6) as follows:
where the maximum number of allowed IoT interferes to each UE from all groups are assumed (i.e.,\({\sum }_{k=1}^{K} {\sum }_{n=1}^{N} a_{m,n,k} = K\)) and equal transmit power for all IoTDs. therefore, any IoTD with a distance larger than this threshold is allowed to be reuse candidate which can be recast as follows:
If we assume a threshold distance equal to dth, 1.1dth and 1.2dth, the matching algorithm execution time is reduced by 48%, 55% and 61%, while the throughput gain and the access rate for a threshold distance dth are almost the same without taking a threshold (this will be explained later in Figs. 4 to 9).
On the other hand, since we assume an equal power allocation of all IoTDs reusing the same UE, we need to determine a sub-optimal value (\(P_{n,k}^{m}=P_{d}\)) that achieves the maximum throughput. In Fig. 3, we adopted numerical simulation to find the power level that maximizes the throughput gain within the allowed range of values (i.e., Pd from 0 : 23 dBm) for different distances between eNB and IoTD-GWs. The simulation results show that increasing Pd improves the throughput gain until a certain value where the gain saturates due to the introduced interference.
Figures 4 and 5 illustrate the effect of changing the distance between any IoT-GW and eNB (400, 600, and 800 m) on the cell throughput gain and accessibility of IoTDs when the IoTGs radii are 100 m. Both figures compare the single IoT group ORA algorithm, the proposed GIM algorithm for single IoT group scenario (K = 1 GIM), and the proposed GIM algorithm for double IoT groups (K = 2 GIM). The simulation results show that the cell throughput gain and IoTDs accessibility increase with increasing the distance between eNB and IoT-GWs due to the reduced interference from IoTDs. Figure 4 reveals that throughput gain improves with the increases in the number of IoTDs due to the availability of much more combination of IoTDs that to select from. On the other hand, the results in Fig. 5 show that the access rate drops with the increase of the number of deployed IoTDs due to the assumption of a constant number of available UEs where each UE is limited to be paired with at most K IoTDs. Additionally, the proposed GIM algorithm with K = 2 has a better performance in terms of both of the cell throughput gain and accessibility of IoTDs compared to the single IoTG scenario. The simulation results show the effect of setting a distance threshold for the multiple IoT group scenario where the throughput gain and the access rates drop slightly when we increase the threshold distance. The effect appears when there is a large number of IoTDs in the system.
Figures 6 and 7 show the effect of the IoTGs radii (100, 200, and 300 m) on the throughput gain and the access rate for a fixed distance between the IoT-GW and the eNB (600 m). The simulation results show that the cell throughput gain and IoTDs accessibility increase with decreasing the radii of the IoTGs. Decreasing the radius reduces the interference from IoTDs to eNB which increases the number of paired IoTDs and the total cell throughput.
Figures 8 and 9 show the effect of the QoS constraints of the IoTDs on the throughput gain and the access rate for a fixed distance between IoT-GW and eNB (600 m) and IoTGs radii of 100 m. the simulation results show that a lower SIR increases cell throughput gain and accessibility of IoTDs, since decreasing SIR constrains for IoTDs increases the probability of pairing larger number of IoTDs while reducing interference of IoTDs on eNB and increasing the cell throughput gain.
Based on the previously presented results, the performance of the proposed GIM algorithm outperforms the optimal resource allocation (ORA) in [3] as a baseline in terms of both of the cell throughput gain and accessibility of IoTDs in the cases of a single cluster and two clusters as well.
In Fig. 10, the performance of the GIM algorithm is further compared to two multi-cluster based algorithms, namely the fixed-radio resource sharing algorithm (F-RRSA) [5] and the adaptive radio resource sharing algorithm (A-RRSA) [6]. F-RRSA aims to maximize the sum rate with a computational complexity of \(\mathcal {O}(M^{3}+KM^{3})\) while A-RRSA is built upon F-RRSA to consider the trade-off between fairness and data rate with a higher computational complexity due to the adoption of proportional integral control (PID). The simulation parameters in Fig. 10 are adopted from [5, 6] for fair comparison which are given as follows: the radius of eNB coverage is 500 m, the cluster radius is 70 m, the distance between eNB and IoT-GW is 100 m, the maximum transmission power of UEs is 24 dBm, and the D2D transmission power is 5:15 dBm. Moreover, the number of devices per cluster is 50 % of the number of UEs. The simulation results show that the proposed GIM algorithm outer performs the two other algorithms, while the F-RRSA achieves better performance compared to the A-RRSA algorithm.
5 Conclusion
In this work, we investigated a sub-optimal resources allocation scheme for multiple IoT group deployment underlaying cellular communication. The proposed greedy iterative matching (GIM) algorithm improves the cell throughput gain and IoTDs access rate compared to the single IoT group deployment scenarios. The proposed analysis and simulation results show that setting a lower-bound on how close the allowed IoT reuse partners reduces the computation complexity while preserving sufficient performance gain. As future research directions, we would like to investigate the joint EE and number of admitted IoT devices maximization in addition to the investigation of other matching algorithms to improve performance.
Notes
The orthogonality among the M UE channels can be achieved in different systems by separating them in time, frequency or code domain.
The assumption that only one IoTD at maximum from each IoTG is allowed to share the RB of each cellular user is to enforce fairness between the IoT clusters.
References
Dong Y, Hossain MJ, Cheng J (2017) Joint power control and subchannel allocation for d2d communications underlaying cellular networks: a coalitional game perspective. In: Cheng J, Hossain E, Zhang H, Saad W, Chatterjee M (eds) Game Theory for Networks. Springer International Publishing, Cham, pp 133–146
ElHalawany BM, Ruby R, Wu K (2019) D2d communication for enabling internet-of-things: outage probability analysis. IEEE Trans Veh Technol 68(3):2332–2345
Elmesalawy MM (2016) D2d communications for enabling Internet of things underlaying LTE cellular networks. Journal of Wireless Networking and Communications 6(1):1–9
Feng D, Lu L, Yuan-Wu Y, Li GY, Feng G, Li S (2013) Device-to-device communications underlaying cellular networks. IEEE Trans Commun 61(8):3541–3551
Hamdoun S, Rachedi A, Ghamri-Doudane Y (2015) Radio resource sharing for MTC in LTE-a: an interference-aware bipartite graph approach. In: Proc IEEE GLOBECOM, pp 1–7
Hamdoun S, Rachedi A, Ghamri-Doudane Y (2016) A flexible M2M radio resource sharing scheme in LTE networks within an H2H/M2M coexistence scenario. In: Proc IEEE ICC, pp 1–7
Jiang F, Wang H, Ren H, Xu S (2017) Energy-efficient resource and power allocation for underlay multicast device-to-device transmission. Future Internet 9(4):84
Kaufman B, Aazhang B (2008) Cellular networks with an overlaid device to device network. In: Proc Asilomar Conference on Signals, Systems and Computers, pp 1537–1541
Kaufman B, Lilleberg J, Aazhang B (2013) Spectrum sharing scheme between cellular users and ad-hoc device-to-device users. IEEE Trans Wireless Commun 12(3):1038–1049
Li Y, Chi K, Chen H, Wang Z, Zhu Y (2018) Narrowband internet of things systems with opportunistic d2d communication. IEEE Internet Things J 5 (3):1474–1484. https://doi.org/10.1109/JIOT.2017.2782323 https://doi.org/10.1109/JIOT.2017.2782323
Liu L, Yu W (2018) A d2d-based protocol for ultra-reliable wireless communications for industrial automation. IEEE Trans Wirel Commun 17(8):5045–5058. https://doi.org/10.1109/TWC.2018.2836937
Liu X, Li Z, Zhao N, Meng W, Gui G, Chen Y, Adachi F (2019) Transceiver design and multi-hop D2D for UAV IoT coverage in disasters. IEEE Internet Things J
Liu Z, Peng T, Xiang S, Wang W (2012) Mode selection for device-to-device (D2D) communication under LTE-advanced networks. In: IEEE International Conference on Communications (ICC)
Mach P, Becvar Z, Vanek T (2015) In-band device-to-device communication in OFDMA cellular networks: a survey and challenges. IEEE Commun Surveys Tuts 17(4):1885–1922
Meshgi H, Zhao D, Zheng R (2015) Joint channel and power allocation in underlay multicast device-to-device communications. In: Proc IEEE ICC, pp 2937–2942
Mostafa AE, Zhou Y, Wong VWS (2017) Connectivity maximization for narrowband IoT systems with NOMA. In: Proc IEEE ICC, pp 1–6
Nguyen LD (2018) Resource allocation for energy efficiency in 5g wireless networks. EAI Endorsed Transactions on Industrial Networks and Intelligent Systems 5(14):e1
Nguyen LD, Tuan HD, Duong TQ, Dobre OA, Poor HV (2018) Downlink beamforming for energy-efficient heterogeneous networks with massive MIMO and small cells. IEEE Trans Wireless Commun 17 (5):3386–3400
Nguyen MV, Duong TQ, Hong CS, Lee S, Zhang Y (2012) Optimal and sub-optimal resource allocation in multi-hop cognitive radio networks with primary user outage constraint. IET Networks 1(2):47–57
Ning Z, Wang X, Kong X, Hou W (2018) A social-aware group formation framework for information diffusion in narrowband internet of things. IEEE Internet Things J 5(3):1527–1538
Ningombam DD, Shin S (2018) Non-orthogonal resource sharing optimization for d2d communication in LTE-a cellular networks: a fractional frequency reuse-based approach. Electronics 7(10):238
Phunchongharn P, Hossain E, Kim DI (2013) Resource allocation for device-to-device communications underlaying LTE-advanced networks. IEEE Wireless Commun 20(4):91–100
Pradhan A, Basu S, Sarkar S, Mitra S, Roy SD (2018) Implementation of relay hopper model for reliable communication of IoT devices in LTE environment through D2D link. In: Proc COMSNETS, pp 569–572
Ratasuk R, Vejlgaard B, Mangalvedhe N, Ghosh A (2016) NB-Iot system for M2M communication. In: Proc IEEE WCNC, pp 1–5
Rebecchi F, de Amorim MD, Conan V, Passarella A, Bruno R, Conti M (2015) Data offloading techniques in cellular networks: a survey. IEEE Commun Surveys Tuts 17(2):580–603
Ren Y, Chuai G (2017) Low-complexity uplink resource allocation algorithm based on hypergraph clustering for d2d communications. In: Proc IEEE PIMRC, pp 1–6
Shah SH, Yaqoob I (2016) A survey: internet of things (IoT) technologies, applications and challenges. In: Proc IEEE SEGE, pp 381–385
Sheng Z, Tuan HD, Duong TQ, Poor HV (2017) Joint power allocation and beamforming for energy-efficient two-way multi-relay communications. IEEE Trans Wireless Commun 16(10):6660–6671
Sheng Z, Tuan HD, Duong TQ, Poor HV, Fang Y (2018) Low-latency multiuser two-way wireless relaying for spectral and energy efficiencies. IEEE Trans Signal Process 66(16):4362–4376
Song X, Han X, Ni Y, Dong L, Qin L (2019) Joint uplink and downlink resource allocation for D2D communications system. Future Internet 11(1):12
Vo N, Duong TQ, Guizani M, Kortun A (2018) 5g optimized caching and downlink resource sharing for smart cities. IEEE Access 6:31,457–31,468
Vo N, Duong TQ, Tuan HD, Kortun A (2018) Optimal video streaming in dense 5g networks with D2D communications. IEEE Access 6:209–223
Wang B, Chen L, Chen X, Zhang X, Yang D (2011) Resource allocation optimization for device-to-device communication underlaying cellular networks. In: Proc IEEE VTC spring, pp 1–6
Wu G, Talwar S, Johnsson K, Himayat N, Johnson KD (2011) M2m: from mobile to embedded internet. IEEE Commun Mag 49(4):36–43
Yang X, Wang X, Wu Y, Qian LP, Lu W, Zhou H (2018) Small-cell assisted secure traffic offloading for narrowband internet of thing (nb-iot) systems. IEEE Internet Things J 5(3):1516–1526. https://doi.org/10.1109/JIOT.2017.2779820
Yang Z, Huang N, Xu H, Pan Y, Li Y, Chen M (2016) Downlink resource allocation and power control for device-to-device communication underlaying cellular networks. IEEE Commun Lett 20(7):1449–1452
Yu C, Tirkkonen O, Doppler K, Ribeiro C (2009) Power optimization of device-to-device communication underlaying cellular communication. In: Proc IEEE ICC, pp 1–5
Acknowledgements
The authors would like to thank Prof. Mostafa M. Fouda for his support and help in preparing the reply letter and the revised manuscript.
Funding
The authors would like to thank Prof. Mostafa M. Fouda for his support and advice. This research was supported by Benha University research fund (Project 2/1/14). This work is partially supported by the China NSFC Grant (61872248, U1736207), Guangdong Natural Science Foundation 2017A030312008, Fok Ying-Tong Education Foundation for Young Teachers in the Higher Education Institutions of China (Grant No.161064) and GDUPS (2015). This work is partially supported by the project “PCL Future Regional Network Facilities for Large-scale Experiments and Applications (PCL2018KP001).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Basem and Omnia are equally shared authors.
Rights and permissions
About this article
Cite this article
ElHalawany, B.M., Hashad, O., Wu, K. et al. Uplink Resource Allocation for Multi-Cluster Internet-of-Things Deployment Underlaying Cellular Networks. Mobile Netw Appl 25, 300–313 (2020). https://doi.org/10.1007/s11036-019-01288-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-019-01288-6