Abstract
Cognitive radio solves the problem of scarcity of radio spectrum to a great extent in that it allows unlicensed users to coexist with licensed users. It allows effective utilization of radio spectrum by offering radio cells the ability of radio sensing and dynamic spectrum sharing. The throughput of spectrum sharing cognitive radio can be maximized by performing data transmission and spectrum sensing at the same time. Cooperative communications and networking allow distributed terminals in a wireless network. The main problem with cognitive radio is to sense the presence of primary users over a wide range of spectrum. Cooperative spectrum sensing is used here to detect those users more reliably. It is investigated whether cooperative communication for spectrum in cognitive radio enhances the efficiency of spectrum sharing. The maximum power that can be adapted by the secondary user without causing significant interference to a primary user is investigated. An algorithm is proposed for the same. Closed-form expression for ergodic throughput is derived for the systems and is compared with the conventional cognitive radio system. An expression for the outage capacity of the system is also derived for average transmit and interference power constraints under truncated channel information with fixed rate technique.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
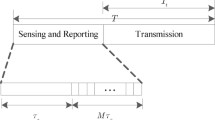
Cognitive radio networks (CRN) have attracted great attention as a solution to the problem of spectrum scarcity. A cognitive radio is a transceiver which automatically detects available channels in a wireless spectrum and accordingly changes its transmission or reception parameters so more wireless operators may run concurrently in a given spectrum band at a given place. This process is also known as dynamic spectrum management [1]. Two main approaches have been developed for cognitive radio so far regarding the method in which a secondary user accesses the licensed spectrum. With opportunistic spectrum access techniques, CRN can be granted access of spectrum secondarily, i.e., as long as it can guarantee no interference to any primary user (PU) who is using this spectrum at this time in this location. This means that cognitive radios have to periodically sense the spectrum to detect the primary user’s activity. They have to vacate the channel immediately whenever PU activity is detected [2] through spectrum sharing (SS) based on which the secondary users coexist with the primary users under the condition of protecting the latter from harmful interference [2, 3]. Recent development in this front is a hybrid technique which improves the throughput of the abovementioned methods. The sensing-throughput trade off problem becomes very significant when the hybrid approach is used to improve the throughput of spectrum sharing cognitive radio networks since the primary signals under detection are very weak and may therefore lead high sensing times that would have a detrimental effect on their achievable throughput.
In this paper, we focus on throughput maximization of spectrum sharing cognitive radio networks. So, we incorporate a set of cooperative relay networks in between the secondary user transmitter and receiver to improve the system throughput. To increase the robustness against multipath fading, parallel relay transmission has been used. In this topology, signals propagate through multiple relay paths in the same hop, and destination combines the signals received with the help of various combining schemes. It provides power gain and diversity gain simultaneously. The best available relay channel is chosen depending on the position of the primary user for data transmission by the receiver and a feedback is sent to the transmitter.
This is analyzed in more detail in Section 2. In addition, we study the problem of maximizing ergodic throughput and outage capacity of the proposed cognitive system under average transmit and interference power constraints in Sections 3 and 4. Section 5 provides the numerical results and their discussions. Finally, Section 6 presents the conclusions.
2 Proposed cooperative spectrum sharing scheme
In this section, we first describe the system model used in this paper and then propose a cooperative spectrum sharing in the single secondary user network.
2.1 A. System model
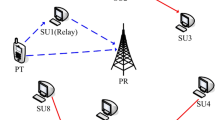
We consider the system model as depicted in Fig. 1, where the cognitive user (Su_Tx) is detecting the primary user (Pu_Tx) via the best cooperative relay, r B, which is selected among a set of all candidates denoted by {R1, R2, …,Rn}. The channels are assumed to be ergodic, stationary, and known at the secondary users with probability density function (PDF) f s1(s1), f s2(s2), and so on, respectively, whereas the noise is assumed to be circularly symmetric complex Gaussian with mean zero and variance σ 2 n , namely CN(0, σ 2 n ). Our results serve as upper bounds for the achievable rate of practical cognitive radio systems as in [2] and [4]. In the beginning, an initial spectrum sensing is performed to determine the status of the frequency band. Based on spectrum sensing decision, the secondary user transmits information using a higher transmit power, P 0, if the primary user is detected to be inactive and the secondary user transmits using a lower transmit power, P 1, otherwise. The candidate relay transmits with the same power as the secondary user. The transmit power of the primary user is P s.
2.2 B. Data formulation of the received signal
Without any loss of generality, let s be the primary user indicator, namely s = 1 implies the presence of the primary user and s = 0 implies its absence. The secondary user detector decides
as the two hypotheses.
The secondary user communicates with the receiver in two sub-slots. In sub-slot one, the primary user transmits to the primary user’s receiver, and the secondary user transmits to the best relay r B. The received signal at the best relay is given by
where the first term corresponds to the signal received from the primary user, X p represents the transmitted vector from the primary user, and X denotes the received signal from the secondary user. Finally, n b denotes the additive noise. In the absence of the primary user, the secondary user’s signal is given by
where h sb is the instantaneous channel power gain and X s is the transmitted vector from the secondary user. In the presence of the primary user, the secondary user signal is given by
During the second sub-slot, primary user uses the same power as the first sub-slot. The retransmitted signal [5] of r B is given by
where the second and third terms refer to the interference signal from other relays, and ω i and β i are scaling factors to normalize the power of the received signal.
3 Transmission rate of the proposed system
In the proposed cognitive radio system, the secondary users adapt their transmit power at the end of each frame based on the decision of spectrum sensing and transmit using higher power, P 0, when the frequency band is detected to be idle, and lower power, P 1, when it is detected to be active. The instantaneous transmission rates can be obtained by Shannon’s capacity equation given below [6]
where C is the capacity, B is the bandwidth, and SNR is the signal-to-noise ratio of the link. The term log2 (1 + SNR) is the data transmission rate. Hence, the transmission rate for the given system model when the frequency band is idle can be given as
and so on for the nth relay is given by
Here, R 01 is the transmission rate of the first relay, R02 is the transmission rate of the second relay, and so on, when the primary user is idle. Further, P 0 is the power of the secondary user when the primary user is idle and σ 2 n is the received noise power. When the frequency band is active, the transmission rate at different relays are given as
and so on for the nth relay
Here, R 11 is the transmission rate of the first relay, R 12 is the transmission rate of the second relay, and so on, when primary user is active. Further, P 1 is the power adapted by the secondary user when primary user is active and σ 2 p is the received power from the primary user.
3.1 A. Best relay selection for transmission
Noting that the channel state information (CSI) of the channel from each candidate, R i , to the primary user is denoted as h pi (k), the candidate relay (r B) with the best SNR is selected as the best relay
Hence, (8) reduces to
The whole implementation can be divided into two sub-slots: In the first sub-slot, (2k − 1), the best relay r B receives signal from both primary user and the cognitive user, and in the second sub-slot 2k, r B relays its received signal to the secondary user detector.
However, considering the fact that perfect spectrum sensing may not be achievable in practice, it is important to consider a more realistic scenario of imperfect spectrum sensing where the actual status of the primary users may be falsely detected. Therefore, four different cases of instantaneous transmission rates from the secondary user to the best relay can be considered based on the actual status of the primary user (active/idle) as follows [7]:
Now, the transmission rate from the best selected relay to the secondary user receiver in the absence of the primary user can be written as
and in presence of the primary user, (11) can be written as
Hence, the transmission rate of the entire system can be written as
The equivalent SNR of the system in absence of primary user can be calculated as
For high SNR, C = 0. Hence, (14) reduces to
The equivalent SNR of the system in presence of primary user can be calculated as
For low SNR, C = 1. Hence (16) reduces to
3.2 B. Ergodic capacity of the proposed scheme
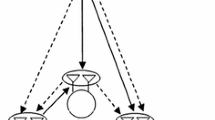
We first obtain the optimal power allocation for the proposed system subject to long-term power constraints (Fig. 2). Let \( \gamma =\frac{P\left|{h}^2\right|}{\sigma_n^2} \) denote the instantaneous received SNR without power adaptation, where h is the scalar fading coefficient, and let f (γ) denote the PDF of γ. Let P (γ) denote the power policy of the input signal and is a function of the transmitted SNR, the decision whether the primary user is present (P 1) or absent (P 0), probability of detection (P d), and probability of false alarm (P fa). Then, the received SNR with power adaptation is \( \frac{P\left(\gamma \right)}{\overline{P}} \), and the ergodic capacity is [8]
In order to keep the long-term power budget and effectively protect the primary users from harmful interference, the average (over all fading states) transmit and interference power constraint that can be formulated is considered. It should be taken into account that the transmitted power from the secondary user can take a higher value if the primary user is detected to be idle, i.e., not present and the transmitted power should take lower values if the primary user is detected to be active, i.e. present. The interference power that can be tolerated by the primary user depends on the instantaneous power gain of the primary user and the signal power from the secondary user. Hence, the corresponding power policy can be written as follows:
where P(H0) = probability that the frequency band is idle,
P(H1) = probability that the frequency band is active,
P d = detection probability,
P fa = false alarm probability,
P av = maximum average transmit power of the secondary users,
Γ 1 = maximum average interference power caused by the secondary user transmitter, and
Γ 2 = maximum average interference power caused by the candidate relay.
Finally, the optimization problem that maximizes the Ergodic throughput [9] of the proposed spectrum sharing cognitive radio system under joint average transmit and interference power constraints can be formulated as follows:
where SNReq0 ≥ 0, SNReq1 ≥ 0.
Here, the optimization problem for capacity can be solved using the Lagrangian cost function where the average transmitter power and the interference power can be used as two constraints. The Lagrangian cost function from the secondary user to the candidate relay with respect to the transmitted SNRs SNReq0 and SNReq1 is given by [10] \( \begin{array}{l}L\left({\mathrm{SNR}}_{\mathrm{eq}0},{\mathrm{SNR}}_{\mathrm{eq}1},\lambda, \mu \right)=E\ \left[P\left({\mathrm{H}}_1\right){P}_{\mathrm{d}}\ {R}_{11\mathrm{B}}+P\left({\mathrm{H}}_0\right)\ {P}_{\mathrm{fa}\ }{R}_{01\mathrm{B}}+P\right({\mathrm{H}}_1\left)\ \right(1-{P}_{\mathrm{d}}\left){R}_{10\mathrm{B}}+P\right({\mathrm{H}}_0\left)\right(1-\\ {}{P}_{\mathrm{fa}}\left){R}_{00\mathrm{B}}\right]-\lambda E\left[P\left({\mathrm{H}}_0\right)\left(1-{P}_{\mathrm{fa}}\right){\mathrm{SNR}}_{\mathrm{eq}0}+P\right({\mathrm{H}}_0\left)\ {P}_{\mathrm{fa}}\ {\mathrm{SNR}}_{\mathrm{eq}1}+P\right({\mathrm{H}}_1\left)\right(1-{P}_{\mathrm{d}}\left){\mathrm{SNR}}_{\mathrm{eq}0}+P\right({\mathrm{H}}_1\Big)\ {P}_{\mathrm{d}}\\ {}{\mathrm{SNR}}_{\mathrm{eq}1}\Big]+\lambda {P}_{\mathrm{av}}-\mu E\left[P\left({\mathrm{H}}_1\right)\ \left(1-{P}_{\mathrm{d}}\right)\ {h}_{\mathrm{s},\mathrm{D}}{\mathrm{SNR}}_{\mathrm{eq}0}+P\left({\mathrm{H}}_1\right)\ {P}_{\mathrm{d}}\ {h}_{\mathrm{s},\mathrm{D}}\ {\mathrm{SNR}}_{\mathrm{eq}1}\right]+\mu {\varGamma}_1,\end{array} \)
where the dual function can be obtained as
After forming their Lagrangian functions and applying the Karush Kuhn Tucker conditions, the optimal SNRs SNReqo and SNReq1 for a given λ, μ are given by [6, 11]
and
where
and
Here,
An approximate expression for the probability of detection over AWGN channels was presented in [12]. Here, exact closed-form expressions for both detection probability and the probability of a false alarm are defined as P d = P(y > λ|H1) and P fa = P(y > λ|H 0), respectively, where λ is the decision threshold. Based on the statistics of y, Pfa can be evaluated as
where Γ is the incomplete gamma function [13]. From the CDF of y, P d can be evaluated as
The average interference power from the candidate relay to the secondary user receiver can be written as follows:
For Rayleigh fading coefficients h B,D and h B,d , it can be easily shown that the random variable \( u=\frac{h_{B,D}}{h_{B,d}} \) follows a log-logistic distribution given by f u (u) = 1/(1 + u)2 [14]. Thus, (32) can be written as
By change of variables t = 1 + u, dt = du, (33) can be written as
where γ 0 and γ 1 are the cut-off threshold for the secondary user receiver. Further,
3.3 C. Optimal power allocation
In order to determine the optimal power allocation strategy, the optimal values of Lagrangian multipliers, λ and μ, that minimize the dual function d (λ, μ) need to be found. The ellipsoid method [13] is used here to find the optimal solution which requires the sub-gradient of the dual function d (λ, μ). The latter is given by the following algorithm: Finally, the case is considered when the power from the primary users is not known at the secondary transmitter. In this case, by considering single noise power, σ 2, at all times, the optimization problem can be formulated as follows:
4 Outage capacity of the proposed scheme
The Ergodic capacity studied in the previous section is an effective metric for fast fading channels or delay-insensitive applications [15], where a block of information can experience different fading states of the channel during transmission, whereas for slow fading channels or delay-sensitive applications, such as voice and video transmission, the outage capacity [16, 17] comprises a more appropriate metric for the capacity of the system due to the fact that only a cross-section of the channel characteristics is experienced during the transmission period of a block of information. The outage capacity, C out, is defined as the highest transmission rate that can be achieved by a communication system while keeping the probability of outage under a maximum value.
In this section, we study outage capacity of the proposed spectrum sharing a cognitive radio system and derive a power allocation strategy for a combination of different constraints on the outage capacity that include average transmit power constraints and average interference power constraints. More specifically, we will consider, as in [18], the truncated channel inversion with fixed rate (TIFR) technique, where the secondary transmitter uses the CSI to invert the channel fading, in order to achieve a constant SNR at the secondary receiver during the periods when the channels fade above a certain “cut-off” value [19]. This adaptive transmission scheme offers the advantage of non-zero achievable rates for a target outage probability \( {P}_{\mathrm{out}}={\overline{P}}_{\mathrm{out}} \), even when the fading is extremely severe such as in Rayleigh fading cases where a constant transmission rate cannot be achieved under all fading states of the channel.
As mentioned in the beginning of this section, in the TIFR technique, the secondary transmitter inverts the channel fading in order to achieve a constant rate at the secondary receiver when the channel fading is higher than a “cut-off” threshold. We define here this cut-off threshold by θ 0 when the primary users are detected to be idle and by θ 1 when the primary users are detected to be active. The respective transmit powers of the secondary user are given by
The average transmit power can be written as
where
Here, K 0 = probability that the primary user is absent,
K 1 = probability that the primary user is present, and
α = attenuation constant from candidate relay to SU receiver.
Solving (38), we have
The average interference power can be written as
4.1 A. Outage probability
Outage probability is an important performance measure that is commonly used to characterize a wireless communication system. It is defined as the probability that the instantaneous end-to-end SNR falls below a threshold. Therefore, mathematically, the outage probability is given by
4.2 B. Outage capacity
Finally, the outage capacity of the proposed spectrum sharing cognitive radio system under joint average transmit and interference power constraints for a target outage probability \( {P}_{\mathrm{out}}={\overline{P}}_{\mathrm{out}} \), is given by
where
Here, the maximum value of the outage capacity can be obtained by searching numerically for the optimal values of θ 0 and θ 1.
5 Numerical results
Earlier work ([20–28]) in spectrum efficiency for 4-G wireless communication systems discussed the effect of the four standard adaptation policies in the presence of spatial correlation, transmit and receive diversity work for single and multiple user scenarios. This work was followed by extensive work ([29–34]) on cooperative spectrum sensing in cognitive radio networks. In this section, we present numerical results for the proposed cognitive radio system incorporating cooperative relays and compare it with the conventional spectrum sharing scheme. We adopt the energy detector [14, 15] as a method of spectrum sensing, although any spectrum sensing technique [15–17] can be used under the proposed cognitive radio system. We consider Rayleigh fading channels, f s = 6 MHz, P(H0) = 0.6, σ 2 = 1, target detection probability P d = 0.9, and γ = −20 dB, where γ is the received SNR from the primary user and f s is the sampling frequency.
Figure 3 shows the power adaptation level of the secondary user depending on the received power in the absence of a primary user for different values of channel gain. From Fig. 3, it can be observed that the signal power of the secondary user reduces as the received power from the channel increases because the received power increases.
Figure 4 shows the power adaptation level of the secondary user depending on the received power in the presence of a primary user. From Fig. 4, it can be observed that the signal power of the secondary user reduces as the received power from the channel increases, because as the received power increases, the secondary user assumes that the primary user is active and close to it. To avoid harmful interference to the primary user, the secondary user reduces its signal power.
Figure 5 shows a comparison of the transmit power of the secondary user depending on the presence or absence of the primary user. It can be easily observed that the transmit power increases in the absence of the primary user. When the primary user is active, the secondary user halves its transmit power. Hence, it reduces the interference level to the primary user.
Figures 6 and 7 show Ergodic throughput vs. SNR graph of the secondary user. In Fig. 6, when the sensing decision finds the primary user idle, the SNR of the secondary user can be taken as high. Hence, a high throughput is obtained. But, the sensing decision is not always correct. It is observed from Fig. 6 that in the case of false alarm, a lower throughput is observed which will avoid harmful interferences. In Fig. 7, when the sensing decision finds the primary user active, the secondary user’s throughput reduces drastically to accommodate primary user transmission without fail.
Figures 8, 9, 10, and 11 emphasize the effect of the number of cooperative relays in the network. It is observed that as the number of cooperative relays increases, the throughput of the system improves. When the number of relays in a single stage approaches 20 or above, the throughput saturates. This improvement is achieved by selecting the best candidate relay for data transmission which causes least interference to the primary user and can support maximum data rate for the secondary user.
Figure 12 shows that probability of detection increases while increasing the secondary user’s SNR. It also can be observed from Fig. 12 that the performance of the system improves when the number of cooperative relays in the network increases. With an SNR of 6 dB and 6 relays in the stage, the detection probability tends to reach 1 which is very much achievable in real life environment. As the target detection probability, P d, increases, the probability of missed detection, P nd = 1 − P d decreases, and therefore the restriction on the transmit power, P 0, imposed by the average interference power constraint, when the primary users are detected to be idle, reduces. Hence, the secondary users under higher values of target detection probability, P d, can communicate using higher transmit power during the periods that the primary users are detected to be idle and as a result, the Ergodic throughput of the cognitive radio system increases.
Figure 13 emphasizes the negative impact on primary user transmission while a false alarm is generated. It can also be observed that interference caused by the secondary user in the maximum case is 0.1 dB which assures uninterrupted primary user transmission under any scenario.
We now consider outage capacity and the capacity under TIFR transmission policy of the proposed cognitive radio system. The target outage probability under TIFR transmission policy is presented vs. the secondary user transmitted power in Fig. 14. Figure 15 shows the outage capacity of the proposed cooperative SS scheme vs. the transmit power under different average power constraints. The target outage probability is set to \( {\overline{P}}_{\mathrm{out}}=0.1 \), and maximum peak interference, Q peak, is related to the average interference constraint Γ1 by ρ = Q peak/Γ1, as shown in [35].
6 Conclusions
In this paper, we proposed a sensing-enhanced spectrum sharing cognitive radio system that significantly improves the Ergodic capacity of spectrum sharing cognitive radio networks by implementing cooperative relay networks. In addition, we provided numerical results, which indicate that the proposed cognitive radio system can considerably improve ergodic capacity of spectrum sharing cognitive radio networks under perfect secondary signal cancelation. We studied outage capacity under different average transmit power and average interference power constraints. In addition, we provided numerical results which indicate that cooperative relaying enhance the performance of spectrum sharing cognitive radio networks. In our future research, we plan to extend this work for multiple primary users and for multiple stages of cooperative relay network. The obtained results adhere to the spectrum policy rules put forth in [36].
References
MacKenzie AB, Reed JH (2009) Cognitive radio and networking research at Virginia Tech. Proceedings of the IEEE 97(4):660–668
Mitola J, Maguire GQ Jr (1999) Cognitive radios: making software radio more personal. IEEE Personal Communications 6(4):13–18
Zhongyu H, Tao S (2008) “Adaptive CRN spectrum sensing scheme with excellence in topology and scan scheduling,”. International Conference on Sensing Technology, Tainan, Taiwan, pp 384–391
Dixit S, Periyalwar S, Yanikomeroglu H (2009) A distributed framework with a novel pricing model for enabling dynamic spectrum access for secondary users. IEEE Vehicular Technology Conference, Anchorage, AK, USA
S. Geirhofer, L. Tong, and B. Sadler, “Dynamic Spectrum access in the time domain: modeling and exploiting white space”, IEEE Communications Magazine, vol. 45, no. 5, pp. 66, May 2007.
Krishna R, Cumanan K, Xiong Z, Lambotharan S (2010) A novel cooperative relaying strategy for wireless networks with signal quantization. IEEE Transactions on Vehicular Technology 89(1):485–489
Zhao Q, Swami A (2007) A decision-theoretic framework for opportunistic spectrum access. IEEE Transactions on Wireless Communications 14(4):14–20
Ghasemi A, Sousa ES (2007) Fundamental limits of spectrum sharing in fading environments. IEEE Transactions on Wireless Communications 6(2):649–658
Gastpar M (2007) On capacity under receive and spatial spectrum-sharing constraints. IEEE Transactions on Information Theory 53(2):471–487
Musavian L, Aïssa S (2007) Ergodic and outage capacities of spectrum sharing systems in fading channels. Proceedings of IEEE GLOBECOM, Washington DC, USA, pp 3327–3331
Haykin S (2005) Cognitive radio: brain-empowered wireless communications. IEEE Journal on Selected areas in Communications 23(2):201–220
Stotas S, Nallanathan A (2011) Enhancing the capacity of spectrum sharing cognitive radio networks. IEEE Transactions on Vehicular Technology 60(8):3768–3779
Di H, Li W, Fusheng Z, Weiyao L (2012) An enhanced covariance spectrum sensing technique based on stochastic resonance in cognitive radio networks. IEEE International Symposium on Circuits and Systems, South Korea, Seoul, pp 818–821
John G. Proakis, and M. Salehi, Digital Communications, 5th edition, McGraw-Hill, pp. 366, 2008.
Shiung D, Chen KC (2009) On the optimal power allocation of a cognitive radio network. IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, Tokyo, Japan, pp 1241–1245
Lim TJ, Zhang R, Liang YC, Zeng Y (2008) GLRT-based spectrum sensing for cognitive radio. IEEE Global Telecommunications Conference, New Orleans, LA, USA
Dev K, Tewari R, Dixit M, Dutta J (2007) Finding trade-off solutions close to KKT points using evolutionary multi-objective optimization. IEEE Conference on Evolutionary Computations, Singapore
Alghamdi OA, Ahmed MZ, Abu-Rgheff MA (2010) Probabilities of detection and false alarm in multitaper based spectrum sensing for cognitive radio systems in AWGN. IEEE International Conference on Communication Systems (ICCS), Singapore, pp 579–584
Gang C, Hong-Lai L (2009) Optimal power allocation for decode and forward cooperative communication with multiple relays. IEEE Conference on Wireless Communications Networking and Mobile Computing, Las Vegas, USA
Bhaskar V (2013) Novel closed-form expressions for ergodic capacity of rate-adaptive MIMO OSFBC-OFDM systems over various adaptation policies. Wireless Personal Communications. doi:10.1007/s11277-013-1537-6
Subhashini J, Bhaskar V (2013) Capacity analysis of Rayleigh fading channels in low SNR regime for maximal ratio combining diversity due to combining errors. IET Communications 7(8):745–754
Krishna SR, Bhaskar V (2012) Spectrum efficiency for rate-adaptive MIMO OSFBC-OFDM systems over various adaptation policies. International Journal of Soft Computing and Engineering (IJSE) 2(3):81–85
Verghese R, Thai Subha S, Bhaskar V (2012) Ergodic capacity analysis and asymptotic tightness for multi-element antenna array with spatial correlation and transmit water-filling. IET Communications 6(1):22–28
Goldsmith AJ, Varaiya PP (1997) Capacity of fading channels with channel-side information. IEEE Transactions on Information Theory 43(6):1986–1992
Shyamala S, Bhaskar V (2011) Capacity of multiuser multiple input multiple output orthogonal frequency division multiplexing systems with doubly correlated channels for various fading distributions. IET Communications 5(9):1230–1236
Bhaskar V (2009) Capacity evaluation for equal gain diversity schemes over Rayleigh fading channels. International Journal of Electronics and Communications (AeUe) 63(4):235–240
Bhaskar V (2007) Spectrum efficiency evaluation for MRC diversity schemes under different adaptation policies over generalized Rayleigh fading channels. International Journal on Wireless Information Networks 14(3):191–203
Bhaskar V (2007) Spectrum efficiency evaluation for MRC diversity schemes over generalized Rician fading channels. International Journal on Wireless Information Networks 14(3):209–223
Ejaz W, Ul Hasan N, Kim HS, Azam MA (2011) Fully distributed cooperative spectrum sensing for cognitive radio ad hoc networks. IEEE Frontiers of Information Technology 37(4):9–13
Kang X, Liang YC, Garg HK, Zhang L (2009) Sensing-based spectrum sharing in cognitive radio networks. IEEE Transactions on Vehicular Technology 58(8):4649–4654
Lundén J, Koivunen V, Huttunen A, Poor HV (2007) Spectrum sensing in cognitive radios based on multiple cyclic frequencies. International Conference on Crown Castle Communications, Orlando, FL, pp 37–43
Zeng Y, Liang YC (2009) Spectrum-sensing algorithms for cognitive radio based on statistical covariances. IEEE Transactions on Vehicular Technology 58(4):1804–1815
Zhang R (2009) On peak versus average interference power constraints for protecting primary users in cognitive radio networks. IEEE Transactions on Wireless Communications 8(4):2112–2120
Ben-Tal A, Nemirovski A (2001) Lectures on modern convex optimization: analysis, algorithms, and engineering applications, Philadelphia, PA, USA. http://www.utdallas.edu/~torlak/courses/ee6391/lectures/lecture5.pdf. Accessed 01 Aug 2001
Palomar DP, Chiang M (2006) A tutorial on decomposition methods for network utility maximization. IEEE Journals on Selected areas in Communications 24(8):1439–1451
Federal Communications Commission (2002) Spectrum Policy Task Force report. Federal Communications Commission, Washington DC, pp. 02–155
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Bhaskar, V., Dutta, B. Ergodic and outage capacity maximization of cognitive radio networks in cooperative relay environment using optimal power allocation. Ann. Telecommun. 69, 621–632 (2014). https://doi.org/10.1007/s12243-013-0419-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12243-013-0419-y