Abstract
This work surveys mathematical aspects of division property, which is a state-of-the-art technique in cryptanalysis of symmetric-key algorithms, such as authenticated encryption, block ciphers and stream ciphers. It aims to find integral distinguishers and cube attacks, which exploit weaknesses in the algebraic normal forms of the output coordinates of the involved vectorial Boolean functions. Division property can also be used to provide arguments for security of primitives against these attacks. The focus of this work is a formal presentation of the theory behind the division property, including rigorous proofs, which were often omitted in the existing literature. This survey covers the two major variants of division property, namely conventional and perfect division property. In addition, we explore relationships of the technique with classic degree bounds.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In this paper we discuss the mathematical aspects of a modern technique in symmetric cryptography. This method allows to both find better attacks as well as to give stronger arguments for the security of given schemes. A large part of the research in the area of division property is devoted to making the actual computation more efficient and applicable to a larger set of primitives. In a nutshell, this part involves setting up a suitable set of equations and inequalities and ask a modern SAT or MILP solver to find solutions. While very important for the field, this aspect is not in the scope of this survey. Instead we focus on the mathematical aspects of division property. But before doing so, we start by giving a bit of context and motivation.
1.1 Symmetric cryptography
Symmetric primitives play an important role in our daily communication and protect almost all sensitive communication. The security of a symmetric primitive, be it a block cipher, a stream cipher or a permutation-based construction, can not be proven as such by current techniques. Instead, arguments for its security are always arguments why a specific attack or a class of attacks is not applicable to the given scheme. One important class of attacks are these which exploit properties of the algebraic normal form of the cipher in question. In its general form, a symmetric primitive can always be thought of as a function
that takes two bit-strings x and k of lengths n and ℓ as inputs and produces an m-bit output. The input x can be thought of as public information. It could be the message in case of a block cipher, a message and a tweak in case of a tweakable block cipher, or the initial value (IV) in case of a stream cipher. The input k is the secret key which is, as well as (an implementation of) the function F, shared between sender and receiver. The output F(x,k) can again be thought of as public and would correspond to the cipher-text in case of a block cipher, the key-stream in case of a stream cipher. It could also be an authentication tag in case of a message authentication code (MAC), or serve as both the cipher-text together with an authentication tag in case of authenticated encryption.
The fact that both the input x and the output F(x,k) are thought of as public information might seem unnatural as making both the message and the cipher text public seems to nullify the whole point of encryption. However, it is common to take a very powerful attacker into consideration that actually might have access to many, even chosen, plain-text and cipher-text pairs.
1.2 Attacks based on the ANF
As any Boolean function, each coordinate \(F_{t}: {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to \mathbb {F}_{2}\) of F, t ∈ [1,m], can be expressed by its algebraic normal form (ANF). That is, we can represent Ft uniquely as a multivariate polynomial.
There are many attacks based on specific properties of the ANF of Ft (for any coordinate t), some of them differ in details or targets, but are all based on exploitable knowledge about this ANF. One of the first attacks is based on Ft having small degree in the variables x. Indeed, if Ft has degree d, any its (d + 1)-th derivative is the constant zero function. Those attacks were coined high-order differential attacks in [1].
Integral attacks [2], make use of a similar but more fine-grained property. Initially, for integral attacks one first fixes part of the input x and then exploits a small degree of the resulting function. In terms of higher-order differentials, those can be seen as a special case where only certain (d + 1)-th derivatives vanish. However, in their most general form, integral attacks would not correspond to derivatives anymore but to a key-independent sum of cipher-texts for a well chosen subset of all plain-texts.
Cube attacks [3], instead, focus on derivatives that are simple but have not vanished yet. Here, simplicity means low algebraic degree and/or dependence only on few secret variables. Such functions can be used to recover partial information about the secret key. Cube attacks are thus always key recovery attacks, while integral properties by themselves only define a distinguisher of the primitive from a random one. While integral distinguishers can be used to mount key recovery attacks for some primitives such as block ciphers, it is not possible, for example, for stream ciphers.
1.3 Division property
One major obstacle of the attacks above is to actually find out that, e.g., the degree of a cipher is small, or, more generally, to find derivatives that vanish or have sparse ANF. The function F is naturally very complex as a whole. Almost all symmetric ciphers are composed of simple and almost identical functions F(i). Those functions F(i), called round functions, are in particular very efficient to implement and often have very simple ANFs and very low degree. Division property, in all its variants described below, is now a tool that allows to deduce information about the ANFs of F by analyzing its structure as a composition of those simple functions F(i). In its initial form, it would allow to derive better upper bounds on the degree of F (defined as the maximum degree of all its coordinates), i.e., potentially find better attacks. Later, variants were developed that allow the efficient computation of single entries in the ANF. We will discuss the mathematical aspects of the most important variants in this paper.
1.4 Brief overview of the division property variants
Yosuke Todo [4] introduced the division property as a new technique to find better integral attacks. This initial version is referred to as the conventional division property. Here, the state of a cipher is grouped into words (e.g. bytes) and the division property allows to make certain statements about the ANF of the cipher. More precisely, the conventional division property allows to determine upper bounds on the degree of the cipher by keeping track of bounds on the degree of a certain set indicator in the separate words and how those change for the basic operations that are applied in the round functions. This led to new attacks, most prominently against the block cipher MISTY1 [5, 6].
While the grouping into words allows rather efficient calculations, its information was limited and therefore Todo and Morii [7] later introduced the bit based division property as a refinement.
Both variants allow to compute a set of certain monomials (and their multiples) that do not occur in the ANF of the function Ft(⋅,k) for any key k. However, for monomials which are not contained in the set, no information is known. One of the main advantages of such a representation is that it allows to cope with the often seen key-addition of an unknown round key to the state.
In this sense the bit based division property splits the space of monomials into two distinct parts, one for which the coefficients are zero, and one for which the coefficients remain unknown.
In a next step, Todo and Morii, in the same paper extended the framework to be able to make statements about monomials of Ft(⋅,k) which are always present independently of k (i.e., the respective coefficient is the constant 1). This is referred to as the three-subset division property to highlight that now all monomials are split into three sets: one for which the coefficients in the ANF of f are known to be zero, one for which they are known to be one, and the rest for which nothing can be concluded.
In order to allow the computation of even more elements of the ANF, Hao et al. [8, 9] introduced the three-subset division property without unknown subset. This paper shifted the view from Ft(⋅,k) to Ft(⋅,⋅), i.e., the key is treated as a usual variable. They give algorithms, based on division trails introduced in [10], that allow to compute (a limited number of) ANF coefficients of Ft exactly. At least theoretically, this removes the set of monomials for which no information can be computed, hence the name.
It should be noted that the three-subset division property without unknown subset actually separates all monomials only in two sets, more precisely in one set and its complement. This concept, without the important aspect of computational hardness, was already treated by Boura and Canteaut [11] using the term parity set.
1.5 Brief comparison of division property variants and classic degree bounds
Division property can be seen as evolution and specification of classic methods of bounding the algebraic degree of iterated functions. The most powerful of the classic ones are the naive bound
the Boura-Canteaut bound [12] (extensively used in cryptanalysis, see e.g. [13])
and a more recent family of bounds based on the degrees of the involved graph indicators by Carlet [14], in particular,

where  is such that
is such that  if and only if F(x) = y.
if and only if F(x) = y.
These bounds are not always tight and thus clearly can not provide better distinguishers than the perfect division property (of course, the downside of the latter is that it is not always feasible to compute). The relationships of these bounds to the conventional division property are described in Section 5. Notably, the state-based conventional division property with ideal propagation can be viewed as a slight generalization of the Carlet’s graph indicator-based method (requiring more information about the graph indicators and yielding stronger bounds).
Table 1 summarizes the hierarchy of these classic methods and division property in terms of precision and required information.
In the table, it is assumed that the same decomposition F = F(r) ∘… ∘ F(1) of the target function F is used, and the “required information” used by the technique is given precisely for those functions F(i). The table does not include all classic degree bounds (for example, bounds based on the divisibility of the Walsh spectra of the involved functions, or requiring more specific information). The described classic degree bounds are not comparable (i.e., for each bound, there exist instances of functions where this bound is strictly better than the others) and so are grouped together. A relevant detailed study of degree bounds can be found in [14]. Furthermore, relationship of division property variants and the Boura-Canteaut bound was studied in [15].
The argumentation for the provided hierarchy is as follows:
-
(A)⇒(B): Follows from the relation of conventional division property to maximal monomials in the graph indicators of composed functions (proven in [16], see Section 5).
-
(B)⇒(C)⇒(D): Follows from inclusion of the conventional division property variants by the partial weights computations (see Section 4).
-
(D)⇒(E)⇒(F): Follows from the inclusion of bit-based division property variants: three-subset division property is simply a mix of the conventional and the perfect division property (see [15, 17]).
1.6 Outline
The parity sets and the perfect division property is described in Section 3. It is foundational for a formal description of the original (conventional) division property, which we provide in Section 4. As mentioned above, historically, conventional division property was described and applied earlier than the perfect division property. In Section 5.2, we provide a comparison of (conventional) division property with known generic degree bounds. Section 6 describes the application of perfect division property for providing security arguments of symmetric-key primitives. Finally, Section 7 concludes the work.
2 Preliminaries and notation
2.1 General notations
The integer segment (i,i + 1,…,j) is denoted by [i,j]. The all-one and all-zero vectors are denoted by \(\underline {1}\) and \(\underline {0}\) respectively. The i-th unit vector is the vector having 1 at the i-th position and 0 otherwise, it is denoted by ei.
2.2 Boolean vectors and functions
An n-bit Boolean function is a function \(f\colon {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\), where \(\mathbb {F}_{2}=\{0,1\}\) is the binary field and \({\mathbb {F}_{2}^{n}}\) is the n-dimensional vector space over \(\mathbb {F}_{2}\). The support of a Boolean function f is the set of all preimages of 1 under f. An n × m vectorial Boolean function is a function \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). The graph of F is denoted by ΓF and is given by
The bitwise logical AND and OR are denoted by \(\land \colon {\mathbb {F}_{2}^{n}}{\times \mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) and \(\lor \colon {\mathbb {F}_{2}^{n}} \times {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) respectively. The logical negation \(\lnot \) is defined by \(\lnot \colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}} \colon x \mapsto \underline {1} - x\). The inner product of \(u,v{\in \mathbb {F}_{2}^{n}}\) is defined as \(\langle {u,v}\rangle := \sum \limits _{i=1}^{n}u_{i}v_{i} ~\in \mathbb {F}_{2}\). For \(x,u{\in \mathbb {F}_{2}^{n}}\), the notation xu is a shorthand for \({\prod }_{i=1}^{n} x_{i}^{u_{i}} := {\prod }_{i\in [{1},~{n}],~ u_{i}=1} x_{i}\).
The indicator of a set \(X \subseteq {\mathbb {F}_{2}^{n}}\) is defined as  such that
such that  if and only if x ∈ X. By an abuse of notation, we will identify a set \(X\subseteq {\mathbb {F}_{2}^{n}}\) with its indicator
if and only if x ∈ X. By an abuse of notation, we will identify a set \(X\subseteq {\mathbb {F}_{2}^{n}}\) with its indicator  In particular, the degree of a set X is defined as the algebraic degree of its indicator, i.e., \(\deg \)
In particular, the degree of a set X is defined as the algebraic degree of its indicator, i.e., \(\deg \)  Conversely, we will identify a Boolean function \(f: {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\) with its support \(({f}) := \{x \in {\mathbb {F}_{2}^{n}} \mid f(x) = 1 \}\subseteq {\mathbb {F}_{2}^{n}}\), The indicator of the graph of a vectorial Boolean function F will be called shortly the graph indicator of F.
Conversely, we will identify a Boolean function \(f: {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\) with its support \(({f}) := \{x \in {\mathbb {F}_{2}^{n}} \mid f(x) = 1 \}\subseteq {\mathbb {F}_{2}^{n}}\), The indicator of the graph of a vectorial Boolean function F will be called shortly the graph indicator of F.
The symmetric difference, denoted by △, is a binary operation on sets equal to the set of elements each present in exactly one of the two input sets. It is commutative and associative, so that a symmetric difference of a collection of sets is well defined, and is equal to the set of elements each present in an odd number of the input sets.
We adapt the set-builder notation and applications of functions by defining the resulting set to be constructed from elements having odd multiplicity (i.e., ignoring elements with even multiplicity), for example:
-
for a function \(F: {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\), the notation \(\{F(x) \mid x \in {\mathbb {F}_{2}^{n}}\}\) defines the set of all vectors y in the image of F having an odd number of preimages;
-
for \(F: {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, X \subseteq {\mathbb {F}_{2}^{n}}\), the notation F(X) defines the set of all \(y \in {\mathbb {F}_{2}^{m}}\) such that there exists an odd number of x ∈ X such that y = F(x).
An exception is the partial weights vector function
(used in Section 4 and Section 5), which is explicitly defined to act on sets as the union of its applications to the individual elements.
Every Boolean function \(f: {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\) admits a unique representation as a multivariate polynomial over \(\mathbb {F}_{2}\) and n variables:
where \(\lambda _{u} \in \mathbb {F}_{2}\) are constant coefficients independent of x. This representation is called the algebraic normal form (ANF). We will say that a monomial xu belongs to the ANF of f (or simply “belongs to f(x)”) if λu = 1.
The ANF support (the set of all \(u \in {\mathbb {F}_{2}^{n}}\) such that xu is present in the ANF) of a Boolean function \(f\colon {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\) or of a subset X of \({\mathbb {F}_{2}^{n}}\) is denoted by \(\mathcal {A}(f)\) and  respectively.
respectively.
Example 1.
Let \(f: {\mathbb {F}_{2}^{4}} \to \mathbb {F}_{2}\) be given by f(x) = x1x2x4 + x3x4 + x4 and let X = supp(F). Then,
Fact 1 (See, e.g., [18]).
For any \(f: {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\) and any \(u \in {\mathbb {F}_{2}^{n}}\), the corresponding ANF coefficient λu is given by
2.3 Partial order
We use the product order (≼) on \(\mathbb {Z}^{n}\) (including \({\mathbb {F}_{2}^{n}}\) by \(\mathbb {F}_{2} \simeq \{0,1\} \subseteq \mathbb {Z}\)), where x ≼ y if and only if xi ≤ yi for all i ∈ [1n], and x ≺ y if and only if x ≼ y and x≠y.
Fact 2.
For \(x, u \in {\mathbb {F}_{2}^{n}}\), the relation x ≽ u is equivalent to the expression xu = 1; similarly, x ≼ u is equivalent to \((\lnot x)^{\lnot u} = 1\).
Proof
The expression x ≽ u means \(\bigwedge _{i=1}^{n} (x_{i} \ge u_{i})\), equivalent to \(\bigwedge _{i=1}^{n} (x_{i}^{u_{i}} = 1) = {\prod }_{i=1}^{n} x_{i}^{u_{i}} = x^{u}\). The case of x ≼ u is analogous. □
In the following, we assume that a universe set \({\Omega } \subseteq \mathbb {Z}^{n}\) is given by the context and it is of the shape
where \(k_{1},\ldots ,k_{n} \in \mathbb {Z}_{>0}\).
The logical negation is naturally generalized to operate on [0k] (where \(k \in \mathbb {Z}_{>0}\)):
Definition 1 (Lower/upper sets/closures).
The lower closure of a set \(X \subseteq {\Omega }\), denoted by ↓ X, is the set of all u ∈Ω with u ≼ x for some x ∈ X:
The upper closure of a set \(X \subseteq {\Omega }\), denoted by ↑ X, is the set of all u ∈Ω with x ≼ u for some x ∈ X:
A set X is an upper set if its upper closure is X itself. A set X is a lower set if its lower closure is X itself.
Example 2.
Let \(X = \{(0, 0, 1), (0, 1, 1)\} \subseteq {\mathbb {F}_{2}^{3}}\). Then,
Let \(Y = \{(0, 2), (2, 1)\} \subseteq [{0},{3}]^{2}\). Then,
See Fig. 1 for an illustration.
Definition 2 (Convexity).
A subset \(X \subseteq \mathbb {Z}^{n}\) is called convex, if for any \(a,b,c\in \mathbb {Z}^{n}\), a ≼ b ≼ c and a,c ∈ X imply b ∈ X.
Definition 3 (Min-/max-set).
The max-set of a set \(X \subseteq \mathbb {Z}^{n}\), denoted by Max(X), is the set of all maximal elements in X:
The min-set of a set \(X \subseteq \mathbb {Z}^{n}\), denoted by Min(X), is the set of all minimal elements in X:
Fact 3.
The operator \(\lnot \) anti-commutes with Min, Max, ↓, ↑: for any set X,
Proof
Follows from the definitions and the fact, that, for all u,v, it holds u ≼ v if and only if \(\lnot u \succeq \lnot v\). □
Definition 4 (Antichain).
A set \(X \subseteq \mathbb {Z}^{n}\) is called an antichain if all pairs of distinct elements from X are incomparable.
Fact 4.
A set \(X \subseteq \mathbb {Z}^{n}\) is a max-set (or a min-set) of some set if and only if it is an antichain.
Proof
If X is a max-set (or a min-set), then it can not contain two elements u,v such that u ≼ v (otherwise, one of them must be removed from X), and so is an antichain. Conversely, if X is an antichain, then it is the max-set of ↓ X and the min-set of ↑ X. □
2.4 Symmetric-key primitives
Symmetric cryptography plays an important role in securing our daily sensitive data. Due to their great performance advantages compared to their public-key counterparts, symmetric-key primitives are responsible for the encryption and authentication for any data that is protected.
The most important basic building blocks of symmetric cryptography are block ciphers, stream ciphers and cryptographic permutations.
A block cipher is a mapping
mapping an n-bit message x and an ℓ bit key k to an n bit cipher-text
such that for each fixed key \(k \in \mathbb {F}_{2}^{\ell }\) the restriction
is a permutation on \({\mathbb {F}_{2}^{n}}\). Common sizes for n, called the block size, are 64 and 128 and ℓ, the key-size, range from 80 to 256.
A stream cipher most commonly is based on a key stream generator
that takes as inputs an initial value IV, a key k, and produces a (very long) stream of bits
The actual encryption of a message is then performed by simply adding (in \(\mathbb {F}_{2}\)) the message with the output of the key-stream generator.
Those primitives are used in modes of operation to ensure secure encryption, authentication or a combined mode for authenticated encryption. The security of those modes can usually be proven under some assumption on the underlying primitive. One standard assumption is that it should be practically impossible to distinguish the primitive using an unknown key from a random function, or, in case of a block cipher, from a random permutation. The security of the primitive itself cannot be proven but is rather checked against known classes of attacks. The most well known statistical attacks are differential and linear cryptanalysis and their derivatives. But other large classes exist and are applicable to (reduced) versions of many ciphers. Some of the most important attacks are those that investigate the ANF of a cipher. They are described in the following parts.
Virtually all primitives deployed in practice are iterative designs. For the case of a block cipher, this means that a simple to analyze and easy and efficient to implement function is iterated a fixed, well chosen, number of times. Often, the key, or rather a round-specific part of the key, is simply added to the current state between the rounds. This constitutes what is known as a key-alternating cipher and is depictedFootnote 1 below.

Most of the symmetric primitives we are using today are not only iterative designs but also use what is known as an SP-Network as round function. In the substitution part, a non-linear layer of parallel small-sized permutations (the so-called S-Boxes) is used. The permutation part on the other hand consists of a (binary) linear layer applied to the full state. Using those ingredients when designing efficient and secure ciphers or cryptographic permutations has a long-standing history. It can be seen as having its roots already in Shannon’s seminal ideas on confusion and diffusion [20]. While certainly many alternative design strategies exist, the use of S-boxes and linear layers is arguably dominating today’s designs and include AES, SHA-3, and many of the primitives for the final round of the NIST lightweight cryptography competition.
Another design strategy we want to briefly mention are Feistel ciphers, with DES being the most prominent but by now out-dated example. Here the message is first split into two halves. The right half is input to a round function fi, that also takes the key as an input. The output of fi is added to the left half and finally both parts are swapped. The function fi are often again based on linear-layers and S-boxes, just as described above for block ciphers. Three rounds of a Feistel cipher are shown below.

2.5 Integral cryptanalysis
Integral attacks [2] and cube attacks [3] are two important attack vectors on symmetric primitives, which exploit certain properties of the involved ANF expressions. Integral attacks distinguishing the analyzed primitive from an ideal one can be applied both to block ciphers and stream ciphers. However, such distinguishers can be extended into key recovery attacks only for block ciphers. Cube attacks, on the other hand, can be used to mount key recovery in both block ciphers and stream ciphers.
To mount a distinguishing integral attack on a block cipher \(E\colon {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\), an adversary chooses a proper non-empty subset \(S \subset {\mathbb {F}_{2}^{n}}\) and a non-zero output mask \(\beta \in {\mathbb {F}_{2}^{n}}\), so that the sum
is constant zero or one, ı.e., is independent of the key k. This property can be used as a distinguisher since for a random permutation \(F \colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\), the sum \({\sum }_{x \in S} \langle \beta , F(x) \rangle \) is zero or one with a probability 1/2 each (excluding the trivial cases S = ∅ and \(S= {\mathbb {F}_{2}^{n}}\)).
An integral distinguisher can be extended into a key recovery attack in the following way. Let Ek = Gk ∘ Fk, where \(G_{k},F_{k}: {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) are bijective key-dependent parts of the cipher, and let Fk have an integral distinguisher
for all keys k. Then, it is also true that
However, under certain assumptions, for a key \(k^{\prime } \ne k\), the equation
would hold only with probability 1/2, providing a way to distinguish a wrong key \(k^{\prime }\) from the right key k. In particular, if \(\langle \beta , G_{k}^{-1}\rangle \) depends only on part of the key, the set of candidate values for this part can be reduced by checking the (1). This method can be improved by advanced techniques such as partial sums [21] or FFT-based key recovery [22].
2.5.1 Finding integral distinguishers with division property
Division property is a technique for finding integral distinguishers based on degeneracies of ANF expressions of the analyzed ciphers.
Conventional division property (Section 4) may only exhibit a monomial such that all its monomial multiples are missing in the ANF. In addition, the technique is imperfect, meaning that it does not guarantee finding a distinguisher even if it exists; nonexistence of a distinguisher can never be proven either. Roughly speaking, conventional division property does not detect cancellations of monomials in intermediate operations, which may or may not lead to distinguishers; the technique only detects cases when the given monomial can not be computed in principle, due to nonexistence of multiplication paths (the so-called ”division trails”, see Section 3.2). However, application of conventional division property is feasible for nearly all used ciphers in the literature and often yields powerful distinguishers.
Perfect variants of division property (Section 3), on the other hand, can be used to compute a chosen ANF coefficient exactly. Simply speaking, the technique counts the number of multiplication paths (division trails) for the target monomial, and the parity of the count determines the respective ANF coefficient. In practice, however, it is feasible only in some use-cases (e.g., 64-bit block ciphers) and often requires specific optimizations and fine-tuning of utilized solvers or optimization software.
2.6 Cube-based cryptanalysis
For cube attacks, we define a Boolean function \(F\colon {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to \mathbb {F}_{2}\), where the first input is public and the second input is the secret key. In the context of stream ciphers, the public input is the initialization vector and F computes a bit of the key-stream. Now, the public input is split into two parts and F decomposed as
where p,r are polynomials, \((x, y) \in {\mathbb {F}_{2}^{n}}\), and \(x^{\underline {1}}\) does not occur in the ANF of r. Recall that \(x^{\underline {1}}\) corresponds to the product of all variables in x. The polynomial p is called the superpoly. It holds that
since r vanishes. When now for a fixed y the polynomial p(y,k) has a low complexity in k, the adversary obtains information about the key or can use p to filter keys.
2.6.1 Finding cube attacks with division property
Division property is a state-of-the-art tool for finding cube attacks. Its feasibility range is much larger than classic methods based on empirical evaluation of cubes (as in [3]).
Conventional division property may be used to search for potential cube attacks. More precisely, it allows to upper-bound the shape of monomials in the superpoly p(y,k). However, it can not show that p(y,⋅) is non-trivial, i.e., that it may actually be used to recover information about the key k (otherwise, the cube key recovery attack degrades to an integral distinguisher; this actually happened in the literature [23]).
Perfect division property can recover the exact coefficients of the superpoly and guarantee a successful key recovery attack. However, its application is much more computationally intensive and is often not feasible.
3 Parity sets and perfect division property
Parity sets were introduced by Boura and Canteaut [11] to formalize rigorously Todo’s original (conventional) division property [4], which can be viewed as a union of vectorial lower bounds on the parity set of a given set. Considering propagation of parity sets directly leads to the perfect division property. While an intermediate variant called 3-subset division property was proposed by Todo and Moriai already in [7], fully perfect variants were proposed and shown feasible in practice only a few years later [8, 17, 24].
In this section, we introduce parity sets and study their properties, focusing on propagation of parity sets through functions. These constitute the key concepts behind the perfect division property and also prepare formalisation of the conventional division property (Section 4).
3.1 Parity sets
Definition 5.
Parity set [11] Let \(X \subseteq {\mathbb {F}_{2}^{n}}\). The parity set of X, denoted by \(\mathcal {U}(X)\), is the subset of \({\mathbb {F}_{2}^{n}}\) defined by
By an abuse of notation, the parity set of a Boolean function is defined as the parity set of its support.
Remark 1.
In the division property literature, parity sets correspond to the “3-subset division property without the unknown subset”. More precisely, the 3-subset division property defined in [7] included a set \(\mathbb {L}\setminus \mathbb {K}\) being a subset of \(\mathcal {U}(X)\) feasible to maintain. Later, [8] defined a set \(\tilde {\mathbb {L}}\) exactly as the parity set of X and called the variant “3-subset division property without the unknown subset”.
The parity set is equal up to negations to the support of the ANF of the set’s indicator.
Proposition 1.
[16] The following statements are equivalent characterizations of the parity set:

Proof
The first equivalence is trivial; the second equivalence follows from Fact 2; the third equivalence is proven by

where the latter condition clearly defines the coefficient of \(x^{\lnot u}\) in the ANF of  (Fact 1). □
(Fact 1). □
The second characterization, although trivial, shows an interesting formulation of the parity set as describing monomials xu that, when multiplied with the (indicator) function, produce the monomial \(x^{\underline {1}}\).
The third characterization shows a close similarity to the Möbius transform-based formulation of the ANF coefficients. The only difference is the direction of the summation: the parity set coefficients are sums of the function over supermasks, while the ANF coefficients are sums of the function over submasks.
The fourth characterization uncovers an equivalence up to negations of the ANF support and of the parity set.
Corollary 1.
[11] The mapping \(\mathcal {U}\) is involutive.
Proof
Follows from the fact the \(\mathcal {A}\) is involutive. □
Proposition 2.
The parity set operator acts linearly on the set indicator. That is, for an integer k ≥ 1 and for all sets \(X, X_{1}, \ldots , X_{k} \in {\mathbb {F}_{2}^{n}}\), it holds

This condition is also equivalent to \(X = \triangle _{i=1}^{k} X_{i}\).
Proof
Let \(X, X_{1}, \ldots , X_{k} \in {\mathbb {F}_{2}^{n}}\) be such that  Then, for any \(u \in {\mathbb {F}_{2}^{n}}\),
Then, for any \(u \in {\mathbb {F}_{2}^{n}}\),

The converse follows from the fact that \(\mathcal {U}\) is involutive. The equivalence to the symmetric difference follows from the definition and the fact that the field has characteristic 2. □
Finally, we list a few common examples of parity sets.
Corollary 2.
[11, Cor.1] Let X be a subset of \({\mathbb {F}_{2}^{n}}\), \(u \in {\mathbb {F}_{2}^{n}}\). Then,
-
1.
\(\mathcal {U}(\emptyset ) = \emptyset \).
-
2.
\(\mathcal {U}(\{u\}) = \downarrow {\{u\}}\).
-
3.
\(\mathcal {U}(\downarrow {\{u\}}) = \{u\}\).
-
4.
\(\mathcal {U}({\mathbb {F}_{2}^{n}})=\{\underline {1}\}\).
Proof
-
1.
Since
 (as a function), its ANF is empty and so must be the parity set (by Proposition 1).
(as a function), its ANF is empty and so must be the parity set (by Proposition 1). -
2.
Follows from the definition of a parity set, the product \(x^{u^{\prime }}\) equals to 1 if and only if \(u^{\prime } \preceq u\) (the necessary and sufficient condition is to have ui = 0 imply \(u^{\prime }_{i} = 0\) for all i).
-
3.
Follows from point 2 and the fact that \(\mathcal {U}\) is an involution.
-
4.
Is a special case of point 3 with \(u = \underline {1}\) and \(\downarrow {u}={\mathbb {F}_{2}^{n}}\).
□
The typical use of parity sets and perfect division property in cryptanalysis reduces to computing an ANF coefficient of a given function, as shown in the following proposition.
Proposition 3.
[24, Cor.1] Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\) be a vectorial Boolean function, so that \(F_{i}(x) = {\sum }_{u \in {\mathbb {F}_{2}^{n}}} \lambda ^{(i)}_{u} x^{u}\). For any \(u \in {\mathbb {F}_{2}^{n}}\), let
Then, \(\lambda _{u}^{(i)} = 1\) if and only if \(e_{i} \in \mathcal {U}(Y)\).
Proof
Follows from Fact 1, and Corollary 2. Indeed, it holds \(e_{i} \in \mathcal {U}(Y)\) if and only if \({\sum }_{y \in Y} y_{i} = 1\) if and only if \({\sum }_{x \in X} F_{i}(x) = 1\) and X by construction is equal to all \(x \in {\mathbb {F}_{2}^{n}}\) such that x ≼ u, matching the summing condition of Fact 1. □
3.2 Propagation of parity sets and division trails
Due to the linearity of the parity set transformation \(\mathcal {U}\) (on the set of 2n-bit vectors representing subsets of \({\mathbb {F}_{2}^{n}}\)), propagation of parity sets through a function can be decomposed into \(\mathbb {F}_{2}\)-sums of propagations of single entries through that function.
Definition 6 (Propagation [24, Def.2]).
Given \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\) and \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\), we say that the input division property u propagates to the output division property v, denoted by
(also called a transition), if
Remark 2.
Since \(\mathcal {U}\) is an involution, an equivalent formulation is that the set X having \(\mathcal {U}(X)=\{u\}\) propagates into Y = F(X) with \(v \in \mathcal {U}(Y)\).
Proposition 4.
[24, Prop.1] It holds that \(u \xrightarrow {F} v\) if and only if the ANF of Fv(x) contains xu.
Proof
Observe that \(v \in \mathcal {U}(F(\mathcal {U}(\{u\}))\) holds if and only if \({\sum }_{x \in \mathcal {U}(\{u\})} F^{v}(x) = 1\), by Definition 5. The summing condition \(x \in \mathcal {U}(\{u\})\) is equivalent to x ≼ u (see Corollary 2), making the expression equivalent to \({\sum }_{x \preceq u} F^{v}(x)\) which is exactly the condition that Fv(x) contains the monomial xu (by Fact 1). □
An interesting observation is that propagations through a bijective function F are closely related to propagations through the compositional inverse of F.
Proposition 5.
[11, Lem.3] Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) be a bijection, \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). Then,
Proof
The proof is simple in the ANF formulation from Proposition 4 by using Fact 2.
□
The proposition below shows that a vector \(b \in {\mathbb {F}_{2}^{m}}\) belongs to the output parity set if and only if the number of vectors \(a \in {\mathbb {F}_{2}^{n}}\) in the input parity set, such that a propagates to b, is odd. Before the proposition, we state the following lemma required for the proof.
Lemma 1.
Let \(X \subseteq {\mathbb {F}_{2}^{n}}\). Then, X = △u∈U(X)U({u}).
Proof
By Proposition 1, we have

Swapping the roles of X and U(X) (Proposition 2), we obtain

The lemma follows. □
Proposition 6.
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, X \subseteq {\mathbb {F}_{2}^{n}}, Y = F(X) \subseteq {\mathbb {F}_{2}^{m}}\). Then,
Proof
We recall that here Y = F(X) corresponds to the symmetric difference of sets {F(x)}x∈X. We have
where the last equivalence relies on the field having characteristic 2. By Lemma 1, the latter condition is further equivalent to
The inner sum is equal to 1 if and only if Fv(x) contains the monomial xu (using corollary 2 and Fact 1). Using Proposition 4, we conclude that the equivalent to \(v \in \mathcal {U}(Y)\) condition is that the number of \(u \in \mathcal {U}(X)\) such that \(u \xrightarrow {F} v\) holds is odd. □
In 2016, Xiang et al. [10] introduced the notion of division trails for conventional division property, and it also generalizes naturally to trails of perfect division property [17, 24]. Here, the propagation is not evaluated for a function in a single step. Instead, the definition above is generalized to the setting where F is actually given as the composition of many functions:
Definition 7 (Division/monomial Trail 10, 17, 24).
Let \(F\colon \mathbb {F}_{2}^{n_{0}} \to \mathbb {F}_{2}^{n_{r}}\) be given as
where
We call \(\left (u^{(0)},\ldots , u^{(r)}\right ), u^{(i)} \in \mathbb {F}_{2}^{n_{i}}\), a division trail over the sequence (F(i))i∈[1r] if
We denote such a trail by
Remark 3.
Hu et al. [17] called division trail a monomial trail, since each transition \(u \xrightarrow {F^{(i)}} v\) in fact defines monomials xu and yv such that yv(x) contains the monomial xu, where y = y(x) = F(i)(x).
Theorem 1.
[17, 24] Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\) be such that F = F(r) ∘⋯ ∘ F(2) ∘ F(1), where \(F^{(i)}: \mathbb {F}^{n_{i}}_{2} \to \mathbb {F}^{n_{i+1}}_{2}\). Let \(u \in \mathbb {F}_{2}^{n_{0}}, v \in \mathbb {F}_{2}^{n_{r}}\). Then,
if and only if the number of trails
is odd.
Proof
The proof is by induction on r, with the base case r = 2.
Case r = 2: We have F = F(2) ∘ F(1) and then
Case r ≥ 3: Now, we prove the induction step. Let \(r^{\prime } \ge 2\) be such that the theorem is proven up to \(r=r^{\prime }\). Consider the case \(r=r^{\prime }+1 \ge 3\). Let \(F^{(2)\prime } = F^{(r)} \circ {\ldots } \circ F^{(2)}\) so that \(F = F^{(2)\prime } \circ F^{(1)}\). By the base case, \(u \xrightarrow {F} v\) if and only if the number of \(w \in \mathbb {F}_{2}^{r_{1}}\) such that \(u \xrightarrow {F^{(1)}} w \xrightarrow {F^{(2)\prime }} v\) holds is odd. For each such w, by the induction hypothesis, we have \(w \xrightarrow {F^{(2)\prime }} v\) if and only the number of trails \(w \xrightarrow {F^{(2)}} {\ldots } \xrightarrow {F^{(r)}} v\) is odd. Therefore, the parity of the number of w such that \(u \xrightarrow {F^{(1)}} w \xrightarrow {F^{(2)\prime }} v\) holds matches the parity of the number of full trails \(u \xrightarrow {F^{(1)}} {\ldots } \xrightarrow {F^{(2)}} {\ldots } \xrightarrow {F^{(r)}} v\), and at the same time determines whether \(u \xrightarrow {F} v\) holds. □
Example 3.
[24, Cor.2] In order to determine whether the i-th output coordinate of F contains a given monomial xu, it is sufficient to compute the parity (by counting) of the number of trails
3.3 Propagation rules for basic operations
In the previous sections we have already seen that we can describe the division property of a function step by step by splitting the function in multiple parts. Especially, when it comes to real block ciphers with a block size n = 64 or n = 128 bits, we cannot compute a propagation table of size 2n × 2n.
In the following we show the propagation rules for five functional complete basic operations: the XOR operation, the AND operation, the NEGATION, the COPY operation, and a bit permutation.
Proposition 7 (XOR Propagation).
Let \(\oplus \colon \mathbb {F}_{2}^{n+1} \to {\mathbb {F}_{2}^{n}}\) be defined as
For \(u \in \mathbb {F}_{2}^{n+1}\) and \(v \in {\mathbb {F}_{2}^{n}}\), it holds that \(u \xrightarrow {\oplus } v\) if and only if
That is, either u1 or u2 can be equal to 1, which leads to v1 = 1 in that case, or u1 = u2 = 0, which leads to v1 = 0.
Proof
We write y = ⊕(x).
Case v1 = 0: Then \(u \stackrel {\oplus }{\rightarrow } v\) if and only if
contains the monomial xu, thus leading to only one possible trail with u = (0,0,v2,…,vn) and it satisfies the relation above.
Case v1 = 1: Then \(u \stackrel {\oplus }{\rightarrow } v\) if and only if
contains the monomial xu, which holds exactly for u = (1,0,v2,…,vn) and u = (0,1,v2,…,vn). □
Proposition 8 (NEGATION Propagation).
Let \(\neg _1\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) be defined as
For \(u,v \in {\mathbb {F}_{2}^{n}}\), it holds that \(u \stackrel {\neg _{1}}{\rightarrow } v\) if and only if
Proof
We denote y = ¬1(x).
Case v1 = 0: Then \(u \stackrel {\neg _{1}}{\rightarrow } v\) if and only if
contains the monomial xu, which leads to the only possible trail, where u = (0,v2,…,vn).
Case v1 = 1: Then \(u \stackrel {\neg _{1}}{\rightarrow } v\) if and only if
contains the monomial xu, which holds exactly for u = (1,v2,…,vn) and u = (0,v2,…,vn). □
Proposition 9 (COPY Propagation).
Let \(\vdash \colon {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}^{n+1}\) be defined as
For \(u \in {\mathbb {F}_{2}^{n}}\) and \(v \in \mathbb {F}_{2}^{n+1}\), it holds that \(u \stackrel {\vdash }{\rightarrow } v\) if and only if
that is, u1 = 0 leads to v1 = v2 = 0, otherwise there is at least one i ∈{1,2} such that vi = 1.
Proof
We denote y =⊩ (x). Then we have \(u \xrightarrow {\vdash } v\) if and only if
contains the monomial xu.
Case u1 = 0: This leads to the only possible trail where v = (0,0,u2,…,un).
Case u1 = 1: Here, we have the following three possible trails:
□
Proposition 10 (AND Propagation).
Let \(\odot \colon \mathbb {F}_{2}^{n+1} \to {\mathbb {F}_{2}^{n}}\) be defined as
For \(u \in \mathbb {F}_{2}^{n+1}\) and \(v \in {\mathbb {F}_{2}^{n}}\), it holds that \(u \stackrel {\odot }{\rightarrow } v\) if and only if
Proof
We denote y = ⊙(x).
Case v1 = 0: Then we have \(u \xrightarrow {\odot } v\) if and only if
contains the monomial xu, which exactly holds for u = (0,0,v2,…,vn).
Case v1 = 1: Here, we have \(u \xrightarrow {\odot } v\) if and only if
contains the monomial xu. This leads to the only possible trail where u = (1,1,v2,…,vn). □
Proposition 11 (Bit Permutation Propagation).
Let \(P\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) be defined as
where π: {1,…,n}→{1,…,n} is a permutation. For \(u,v \in {\mathbb {F}_{2}^{n}}\), it holds that \(u \xrightarrow {P} v\) if and only if P(u) = v.
Proof
Let y = P(x), then we have
which should be equal to xu, so that \(u \xrightarrow {P} v\) if and only if P(u) = v. □
Now, we take a look at an illustrating example of the trail propagation for a simple function.
Example 4 (Trail Propagation [25]).
Let \(F\colon {\mathbb {F}_{2}^{2}} \to {\mathbb {F}_{2}^{2}}\) be defined as
where P interchanges the second and third bit, so that
Figure 2 shows all trails based on the propagation rules for the input division property (1,0), i.e. x1 is contained in y1,y2 and y1y2.
3.4 Propagation through a linear map
Zhang and Rijmen [26] proved a necessary and sufficient characterization of division property transitions through a linear map. While in [26] the statement was given only for invertible maps, Hu, Wang and Wang [27] later proved that it applies to arbitrary linear maps. Although this result was proven in the framework of conventional division property (see Section 4), it can be directly translated to the perfect division property when the weights of the input and the output vectors are equal.
Theorem 2.
[26, 27] Let M be a linear map given by a linear matrix \(M \in \mathbb {F}_{2}^{m\times n}\), \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\) such that wt(u) = wt(v). Denote by Mv,u the submatrix of M with rows selected by ones of the vector v and columns selected by ones of the vector u. Then, \(u \xrightarrow {M} v\) if and only if Mv,u is invertible.
Proof
Let \(M^{\prime } = M_{v,u}\), ℓ := wt(u) = wt(v). Consider the product Mv(x):
The monomial xu is present in the ANF of Mv(x) if and only if
where Sℓ is the set of all permutations of [1ℓ]. Note that the left-hand side of the expression is exactly the expression for the permanent of the matrix Mv,u, which, for the binary field, coincides with the determinant. The theorem follows. □
It is trivial to show that wt(u) ≤wt(v) in general, but there is no known simple characterization of transitions \(u \xrightarrow {M} v\) when wt(u) < wt(v). One possibility is to decompose the map into a sequence of elementary operations and apply the XOR and COPY propagation rules (Proposition 7 and Proposition 9).
Proposition 12.
Let M be a linear map given by a linear matrix \(M \in \mathbb {F}_{2}^{m\times n}\), \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). Then, \(u \xrightarrow {M} v\) implies wt(u) ≤wt(v).
Proof
The transition \(u \xrightarrow {M} v\) means that the product Mv(x), which is equal to a sum of monomials of degree at most wt(v), contains the monomial xu. It follows that wt(u) ≤wt(v). □
4 Conventional division property
4.1 Definitions
Conventional division property, as introduced in the seminal work by Todo [4], can be viewed as a (vectorial) lower bound on (partial) weights of the parity set elements. In other words, it considers monomials in the division trails up to monomial multiples and, in addition, may also group monomials by their degrees on some words, rather than on single bit variables. While these relaxations loose precision (on the contrast to perfect division property), it makes the computational analysis easier and more often feasible.
Definition 8 (Partial weights vector).
Let \(x \in {\mathbb {F}_{2}^{n}}\) and \(k_{1},\ldots ,k_{r} \in \mathbb {Z}_{>0}\) such that k1 + … + kr = n. Define the partial weights vector of x with respect to (k1,…,kr) as
where
The universe set is then defined as Ω := [0,k1] ×… × [0,kr]. The application of wt to a set \(X\subseteq {\mathbb {F}_{2}^{n}}\) is defined as the union of the outputs of wt on individual elements:
Example 5.
Let \(x = (0, 1, 0, 1, 1, 1) \in {\mathbb {F}_{2}^{6}}\). Then,
Example 6.
Let X = {(1,0),(0,1)}. Then, wt2(X) = {1}.
Definition 9 (Conventional division property).
A set \(X \subseteq {\mathbb {F}_{2}^{n}}\) is said to satisfy division property \(\mathbb {K} \subseteq {\mathbb {F}_{2}^{n}}\) if
More generally, X is said to satisfy r-dimensional division property \(\mathbb {K}^{\prime } \subseteq [{0},{k_{1}}] \times {\ldots } \times [{0},{k_{r}}]\) if
Division property \(\mathbb {K}\) is said to be minimal if it is an antichain.
Remark 4.
Clearly, a set X satisfies division property \(\mathbb {K}\) if and only if X satisfies division property \(\text {Min}(\mathbb {K})\), which is minimal.
Remark 5.
The most “tight” division properties that a set \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfies are those with \(\uparrow \mathcal {U}(X) = \uparrow \mathbb {K}\), for example, \(\mathbb {K} := \text {Min}(\mathcal {U}(X))\).
The division property \(\mathbb {K}\) defined over \({\mathbb {F}_{2}^{n}}\) is called bit-based division property. Note that it is included in the general definition due to tw1,…,1(x) = x for all \(x \in {\mathbb {F}_{2}^{n}}\) and corresponds to the case r = n (n-dimensional division property). When r = 1, i.e., when \(\mathbb {K} \subseteq [{0},{n}]\) (1-dimensional division property), the division property is called state-based. When 1 < r < n, the division property may be called word-based if it is aligned with words (e.g. S-boxes) used in the analyzed cryptographic primitive.
From Proposition 1 it follows that conventional division property of a set defines an upper bound on the degree vectors of the monomials in the ANF of the set’s indicator. In the special case of 1-dimensional division property, this fact was given already in several initial studies [11, 13, 28]. The following proposition shows the bit-based version of this fact.
Proposition 13 ([16, Prop.4]).
A set \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfies division property \(\mathbb {K} \subseteq {\mathbb {F}_{2}^{n}}\) if and only if
More generally, a set \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfies division property \(\mathbb {K}^{\prime } \subseteq [{0},{k_{1}}] \times {\ldots } \times [{0},{k_{r}}]\) if and only if
Proof
The proposition follows from Proposition 1 (stating that \(\mathcal {U}(X) = \lnot \mathcal {A}(\lnot (X))\)), and the fact that \(\text {Max}(\mathcal {A}(X)) = \text {Max}(\mathcal {A}(\lnot X))\) and so \(\downarrow \mathcal {A}(X) = \downarrow \mathcal {A}(\lnot X)\). For the generalized version, it is left to use that \(\lnot \) and ↓ commute with wt. □
Example 7.
Consider the function
and let \(X = \text {supp}({f}) \subseteq {\mathbb {F}_{2}^{4}}\). Then, X satisfies the minimal division property
derived from the maximal monomials in  Note that the full parity set of X is given by
Note that the full parity set of X is given by
which, by Proposition 1, can be derived by negating the exponents in the ANF of
4.2 1-dimensional conventional division property
In this section, we briefly describe main properties and some special cases of 1-dimensional division property, outlined in [11] and partly in [28]. Proposition 13 states that 1-dimensional division property simply corresponds to an upper bound on the degree of a set (i.e., on the algebraic degree of its indicator function). Therefore, this case is covered by the theory of Reed-Muller codes.
For the case of 1-dimensional division property \(\mathbb {K} \in {\mathbb {F}_{2}^{n}}\), the following notation is used.
Notation 1.
Let \(n \in \mathbb {Z}_{>0}, k \in \mathbb {Z}, 0 \le k \le n\). Denote by \({D_{k}^{n}}\) the set of all vectors from \({\mathbb {F}_{2}^{n}}\) with weight at least k
Clearly, if a set X satisfies \({D_{k}^{n}}\), then X satisfies \(D_{k^{\prime }}^{n}\) for all \(k^{\prime }\) with \(0 \le k^{\prime } \le k\). Therefore, we are typically interested in the highest such value of k. In fact, this is more clear when it is concluded from Proposition 13 that a set X satisfies \({D_{k}^{n}}\) if and only if \(\deg {X} \le n-k\). We restate this result as in [11] to show the direct connection with Reed-Muller codes.
Proposition 14 ([11, Prop.1]).
Let \(X\subseteq {\mathbb {F}_{2}^{n}}\), k ∈ [0,n]. The following statements are equivalent:
-
1.
X satisfies division property \({D_{k}^{n}}\);
-
2.
the incidence vector of X belongs to the Reed-Muller code of length 2n and order n − k;
-
3.
the incidence vector of X belongs to the dual of the Reed-Muller code of length 2n and order k − 1.
In particular, a tight lower bound on the size of a set satisfying given \({D_{k}^{n}}\) follows.
Proposition 15 ([11, Prop.2]).
If a non-empty subset \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfies division property \({D_{k}^{n}}\), then
Moreover, the equality |X| = 2k holds if and only if X is an affine subspace of dimension k.
The sets satisfying division property \({D_{k}^{n}}\) for very small or very large values of k have simple characterizations.
Proposition 16 (11).
Let \(X \subseteq {\mathbb {F}_{2}^{n}}\). Then,
-
1.
X satisfies \({D_{0}^{n}}\);
-
2.
X satisfies \({D_{1}^{n}}\) if and only if its cardinality is even;
-
3.
X satisfies \({D_{2}^{n}}\) if and only if its cardinality is even and it is a zero-sum set (i.e., \({\sum }_{x \in X} x = 0\));
-
4.
X satisfies \({D_{3}^{n}}\) if and only if X and all n sets {x ∈ X∣xi = 0} (1 ≤ i ≤ n) are zero-sum sets;
-
5.
X satisfies \(D_{n-1}^{n}\) and not \({D_{n}^{n}}\) if and only if X is an affine hyperplane of \({\mathbb {F}_{2}^{n}}\).
-
6.
X satisfies \({D_{n}^{n}}\) if and only if X is empty or \(X = {\mathbb {F}_{2}^{n}}\).
Remark 6.
One might allow the division property \(D_{n+1}^{n} = \emptyset \) which only the empty set satisfies.
4.3 Propagation of conventional division property
From now on, we focus on bit-based conventional division property. Most definitions and results can be naturally generalized by applying the corresponding partial weights projection map \(\text {wt}_{k_{1},\ldots ,k_{r}}\).
Conventional bit-based division property may precisely capture the parity set up to the presence of an (unknown) constant addition. However, it is also useful in the analysis of key-less functions such as cryptographic permutations due to its high efficiency.
Proposition 17 ([11, Prop.6]).
Let X be a subset of \({\mathbb {F}_{2}^{n}}\). Then, for any \(c \in {\mathbb {F}_{2}^{n}}\),
Proof
By Proposition 13, the set \(\lnot \text {Min}(\mathcal {U}(X))\) is the set of maximal monomials in the ANF of  Clearly, this set is invariant under shifting X by a constant, therefore, we have \(\text {Min}(\mathcal {U}(X)) = \text {Min}(\mathcal {U}(X{+} c))\) and also
Clearly, this set is invariant under shifting X by a constant, therefore, we have \(\text {Min}(\mathcal {U}(X)) = \text {Min}(\mathcal {U}(X{+} c))\) and also
□
The following proposition shows that this bound is tight and can not be improved without constraining c.
Proposition 18.
For all \(X \subseteq {\mathbb {F}_{2}^{n}}\) and for all \(u \in \uparrow \mathcal {U}(X)\), there exists \(c \in {\mathbb {F}_{2}^{n}}\) such that \(u \in \mathcal {U}(X {+} c)\).
Equivalently, for all \(X \subseteq {\mathbb {F}_{2}^{n}}\) and for all \(u \in \downarrow \mathcal {A}(X)\), there exists \(c \in {\mathbb {F}_{2}^{n}}\) such that \(u \in \mathcal {A}(X {+} c)\).
Proof
The equivalence follows from Proposition 1, stating that \(u \in \mathcal {U}(X)\) if and only if \((\lnot u) \in \mathcal {A}(\lnot X)\). We prove the proposition in the ANF domain.
The proof is by contradiction. Let \(X \subseteq {\mathbb {F}_{2}^{n}}\) and \(u \in \downarrow \mathcal {A}(X)\) be such that \(u \notin \mathcal {A}(X {+} c)\) for all \(c \in {\mathbb {F}_{2}^{n}}\). Let \(v \in {\mathbb {F}_{2}^{n}}\) be minimal such that u ≺ v and \(v \in \mathcal {A}(X)\). In other words, the monomial xu is not present in the ANF of  for all c, and the monomial xv is present in the ANF of
for all c, and the monomial xv is present in the ANF of  Consider c = v+u. An arbitrary monomial
Consider c = v+u. An arbitrary monomial  is replaced in
is replaced in  by
by
Thus, the monomial xu appears in  only from monomials xt in
only from monomials xt in  that are multiples of xu (i.e., u ≼ t) having ci = 1 in positions where ti = 1,ui = 0 (i.e., ti+ui = 1). Since the chosen c is such that \(c \land u = \underline {0}\), it must be u ≼ t ≼ u + c = v. But xv is the minimal monomial multiple of xu in the ANF of
that are multiples of xu (i.e., u ≼ t) having ci = 1 in positions where ti = 1,ui = 0 (i.e., ti+ui = 1). Since the chosen c is such that \(c \land u = \underline {0}\), it must be u ≼ t ≼ u + c = v. But xv is the minimal monomial multiple of xu in the ANF of  , so that xu is added to
, so that xu is added to  exactly once (from the monomial xt = xv), and thus xu must be present in \(\mathcal {A}(X {+} c)\). □
exactly once (from the monomial xt = xv), and thus xu must be present in \(\mathcal {A}(X {+} c)\). □
Remark 7.
This proposition can be also applied in the integral distinguisher scenario (Section 2.5). That is, in the presence of an unknown constant addition in the input (e.g., a whitening key addition in a block cipher), there exist no monomials always missing in the ANF that are divisors of maximal ANF monomials. In other words, if a given monomial is not present in the ANF (for all values of the constant added in the input), then all its multiples are not present either.
We now switch to the most important component of conventional division property theory - propagation through a public function. From Proposition 6 it is clear that propagation of parity sets through a function can be derived from propagation of each single entry of the input parity set, simply by folding the respective image sets with the symmetric difference. Since conventional division property studies lower bounds of parity sets, a (generally tight) lower bound on the parity set propagation can derived as the union of lower bounds of propagated single-entry parity sets. This is based on the following simple observation: for any sets X1,…,Xt, it holds that

In order to distinguish conventional division property transitions from the perfect ones (Definition 6), we shall call them “weak” transitions. This also emphasizes that they may lose information about the involved sets.
Definition 10 (Weak transition).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). We write \(u \overset {F}{\rightharpoondown } v\) and call it a weak transition if \(u^{\prime } \xrightarrow {F} v^{\prime }\) for some \(u^{\prime } \succeq u, v^{\prime } \preceq v\).
Remark 8.
The term “weak transition” and the notation \(u \overset {F}{\rightharpoondown } v\) are introduced specifically in this survey in order to distinguish the perfect and the conventional division property transition.
Proposition 19.
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). If \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfies division property \(\mathbb {K} \subseteq {\mathbb {F}_{2}^{n}}\), then \(Y := F(X) \subseteq {\mathbb {F}_{2}^{m}}\) satisfies division property \(\mathbb {K}^{\prime } \subseteq {\mathbb {F}_{2}^{m}}\), where
Furthermore, the induced \(\uparrow \mathbb {K}^{\prime }\) can not be improved in general.
Proof
The proof is by contradiction. Assume that Y does not satisfy \(\mathbb {K}^{\prime }\). Then, there must exist \(v \in \mathcal {U}(Y) \setminus \uparrow \mathbb {K}^{\prime }\). By Proposition 6, there must exist a transition \(u \xrightarrow {F} v\) with \(u \in \mathcal {U}(X) \subseteq \mathbb {K}\), which implies a weak transition \(u \overset {F}{\rightharpoondown } v\), contradicting that \(v \in \mathcal {U}(Y)\) does not belong to \(\uparrow \mathbb {K}^{\prime }\).
We now prove the tightness by contradiction. Assume that there exists \(v \in \mathbb {K}^{\prime }\) such that, for all sets \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfying the input division property \(\mathbb {K}\), the output set Y := F(X) satisfies some division property \({\mathbb {K}^{\prime \prime }}\) such that \(v \notin \uparrow {\mathbb {K}^{\prime \prime }}\). Since division property is defined up to the upper closure ↑, we can assume without loss of generality that v is minimal in \(\mathbb {K}^{\prime }\). Therefore, there must exist \(u \in \mathbb {K}\) such that \(u \xrightarrow {F} v\). Let \(X = \mathcal {U}(\{u\})\) so that \(\mathcal {U}(X) = \{u\}\). It follows that Y := F(X) must have \(v \in \mathcal {U}(Y) \subseteq \mathbb {K}^{\prime \prime }\), leading to contradiction. □
Remark 9.
If the input division property is known to be tight (e.g., \(\mathbb {K} = \min \limits (\mathcal {U}(X))\)), then the defined output division property \(\mathbb {K}^{\prime }\) can be improved for some cases of \(\mathbb {K}\) and F. Indeed, let \(u,u^{\prime }\) be minimal in \(\mathbb {K}\), \(u\ne u^{\prime }\) such that \(u \xrightarrow {F} v\) and \(u^{\prime } \xrightarrow {F} v\) for some v that is minimal in \(\mathbb {K}^{\prime }\) (as defined in Proposition 19). Assume also that for no other vector \(w \in \mathbb {K}\) it holds \(w \xrightarrow {F} v\). Then, by Proposition 6, the two propagations cancel and so v does not belong to \(\mathcal {U}(F(X))\) for all sets X tightly satisfying \(\mathbb {K}\). Therefore, F(X) also satisfies division property \(\uparrow (\mathbb {K}^{\prime }) \setminus \{v\}\), which is tighter than \(\mathbb {K}^{\prime }\).
This idea of considering some cancellations leads to the so-called “three-subset division property” [7].
The following theorem summarizes several characterizations of the set of all weak transitions through a function. To prove it, we will use the following simple lemma.
Lemma 2 ([16, Lem.1]).
Let \(f: {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\), \(u \in {\mathbb {F}_{2}^{n}}\). Then,
and u is a minimal such vector if and only if the ANF of f contains the maximal monomial \(x^{\lnot u}\).
Proof
Let X be the support of f. By Proposition 1, (2) holds if and only if \((\lnot u) \in \mathcal {A}(\lnot X)\). Since u is minimal such vector and \(\max \limits (\mathcal {A}(\lnot X)) = \max \limits (\mathcal {A}(X))\), it follows that \(x^{\lnot u}\) is maximal in the ANF of f. □
Theorem 3 ([11, Prop.7],[16, Thm.1]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). The following statements are equivalent:
-
1.
\(u \overset {F}{\rightharpoondown } v\);
-
2.
there exist \(u^{\prime }\succeq u, v^{\prime } \preceq v\) such that \(u^{\prime } \xrightarrow {F} v^{\prime }\);
-
3.
there exist \(u^{\prime }\succeq u, v^{\prime } \preceq v\) such that \(F^{v^{\prime }}(x)\) contains the monomial \(x^{u^{\prime }}\);
-
4.
\((\lnot u, v)\) belongs to \(\uparrow \mathcal {U}({\Gamma }_{F})\);
-
5.
\((u, \lnot v)\) belongs to \(\downarrow \mathcal {A}({\Gamma }_{F})\).
Remark 10.
As the characterized set of all weak transitions is monotone, the characterizations apply to the sets of all extreme elements (characterized by maximal u and minimal v). That is, it holds that \(u \xrightarrow {F} v\) and (u,v) is (maximal,minimal) such vector, if and only if \((u, \lnot v)\) is a minimal vector in the parity set of the graph of F, if and only if \(x^{\lnot u}y^{v}\) is a maximal monomial in the ANF of the graph indicator of F.
Proof
(1 ⇔ 2) holds by definition. (2 ⇔ 3) is proved by Proposition 4. (4 ⇔ 5) is proved by the relation between \(\mathcal {A}\) and \(\mathcal {U}\) from Proposition 1 and the fact that \(\text {Max}(\mathcal {A}(X)) = \text {Max}(\mathcal {A}(\lnot X))\).
(3 ⇔ 4) will be proved by showing equality of the extreme subsets. The condition \((\lnot u, v) \in \text {Min}(\mathcal {U}({\Gamma }_{F}))\) holds if and only if
and \((\lnot u, v)\) is minimal such pair. For any fixed v, by Lemma 2, (3) holds with \(\lnot u\) minimal if and only if Sv(x) contains the monomial xu and it is maximal in the ANF of Sv. We obtain that extreme elements in the set from point 3 belong to the set from point 4, and extreme elements in the set from point 4 belong to the set from point 3. It follows that the sets of extreme elements coincide (otherwise, we could map an extreme element from one set to the other, find a covering extreme element, map back and show that the initial element could not have been extreme). □
An interesting straightforward corollary is the antisymmetry of transitions with respect to the inverse map. It is a direct analogue of Proposition 5.
Corollary 3 ([16, Prop.6]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) be a bijection, \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). Then, the transition \(u \overset {F}{\rightharpoondown } v\) is valid if and only if the transition \(\lnot v \overset {F^{-1}}{\rightharpoondown } \lnot u\) is valid.
4.3.1 Minimal and core transitions
From the characterizations given in Theorem 3 it is clear that some valid transitions may imply validity of some other transitions. Therefore, it is useful to study minimal sets of transitions that imply all others. In addition, for practical purposes, it is convenient to consider transitions which are minimal only in the output: this idea is behind the division property propagation table (DPPT), which is used to encode or evaluate the propagation of conventional division property in practice.
Definition 11.
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). A weak transition \(u \overset {F}{\rightharpoondown } v\) is called minimal (denoted \(u \overset {F}{\rightharpoondown }_{min}v\)) if there exists no \(v^{\prime } \prec v\) such that \(u \overset {F}{\rightharpoondown } v^{\prime }\).
Definition 12 (DPPT).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). The division property propagation table (DPPT) of F is the mapping \({DPPT}\colon {\mathbb {F}_{2}^{n}} \to \mathcal {P}({\mathbb {F}_{2}^{m}})\) given by
To push the idea of the minimal set of transitions further, Udovenko [16] introduced the notion of core transitions. It stems naturally from the definition of weak transitions (Definition 10).
Definition 13.
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). A weak transition \(u \overset {F}{\rightharpoondown } v\) is called a core transition (denoted \(u \overset {F}{\rightharpoondown } v\)) if there exists no weak transitions \(u^{\prime } \overset {F}{\rightharpoondown } v^{\prime }\) with \(v^{\prime } \preceq v, u^{\prime } \succeq u, (u^{\prime },v^{\prime })\ne (u,v)\).
Remark 11.
From Theorem 3 it is clear that core transitions correspond to minimal vectors of \(\mathcal {U}({\Gamma }_{F})\) or, equivalently, to maximal monomials in the ANF of the graph indicator.
Importantly, the set of core transitions fully identifies all three defined kinds of conventional division property transitions through the function and its inverse, if it exists. Of course, the same characterization can be derived from the set of maximal monomials in the ANF of the graph indicator.
Theorem 4 ([16, Thm.2]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\) and let \(\mathcal {D}_{F} := \text {Min}(\mathcal {U}({\Gamma }_{F}))\). Then,
-
1.
\(u \overset {F}{\rightharpoondown } v\) is valid if and only if \((\lnot u, v) \in \uparrow {\mathcal {D}_{F}}\);
-
2.
\(u \overset {F}{\rightharpoondown } v\) is valid if and only if \((\lnot u,v) \in \text {Min}_{2}(\uparrow {\mathcal {D}_{F}})\);
-
3.
\(u \overset {F}{\rightharpoondown } v\) if and only if \((\lnot u, v) \in \mathcal {D}_{F}\).
If, in addition, n = m and F is bijective:
-
4.
\(v \overset {F^{-1}}{\rightharpoondown } u\) if and only if \((u, \lnot v) \in \uparrow {\mathcal {D}_{F}}\);
-
5.
\(v \overset {F^{-1}}{\rightharpoondown } u\) if and only if \((u,\lnot v) \in \text {Min}_{1}(\uparrow {\mathcal {D}_{F}})\);
-
6.
\(v \overset {F^{-1}} {\rightharpoondown } u\) if and only if \((u, \lnot v) \in \mathcal {D}_{F}\).
Here, the subscript of Min defines the coordinate on which the min-set is computed (for vectors (u,v), Min1 operates on u and Min2 operates on v).
Remark 12.
Clearly, core transitions are antisymmetric in the same way as general transitions (Corollary 3). More precisely, the transition \(u \overset {F}{\rightharpoondown } v\) is valid if and only if \(\lnot v \overset {F^{-1}}{\rightharpoondown } \lnot u\) is valid (if and only if \((\lnot u, v) \in \mathcal {D}_{F}\)). However, minimal transitions are not generally antisymmetric and are dependent on the direction of F.
Proposition 20 ([16, Prop.8]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). Define the following sets:
corresponding to the sets of all invalid, minimal, and redundant weak transitions respectively (after the logical negation of the first coordinate).
The sets \(\mathbb {I}_{F}, \mathbb {M}_{F}, \mathbb {R}_{F}\) form a partition of \({\mathbb {F}_{2}^{n}}\times {\mathbb {F}_{2}^{m}}\). Moreover, \(\mathbb {I}_{F}\) is a lower set, \(\mathbb {M}_{F}\) is a convex set, \(\mathbb {R}_{F}\) is an upper set.
Proof
The sets form a partition by their construction. The set \(\mathbb {I}_{F}\) is a lower set as the complement of the upper set \(\uparrow \mathcal {D}_{F}\).
If \(\mathbb {M}_{F}\) is not convex, then there must exist pairs \((u,v) \in \uparrow \mathcal {D}_{F} \setminus \mathbb {M}_{F}\), and (u1,v1), \((u_{2},v_{2}) \in \mathbb {M}_{F}\), such that (u1,v1) ≺ (u,v) ≺ (u2,v2). Since \((u,v)\in \uparrow \mathcal {D}_{F}\), there must exist \(v^{\prime } \prec v\) such that \((u,v^{\prime })\in \mathbb {M}_{F}\). It follows that \(\uparrow \mathcal {D}_{F}\) contains \((u_{2},v^{\prime }) \succ (u,v^{\prime })\) and \(v^{\prime } \prec v \preceq v_{2}\), which contradicts that \((u_{2},v_{2})\in \mathbb {M}_{F}\).
For any fixed u, if \((u, v) \in \mathbb {R}_{F}\), then it is clear from definition of \(\mathbb {R}_{F}\) that \((u,v^{\prime }) \in \mathbb {R}_{F}\) for all \(v^{\prime } \succeq v\). Therefore, if \(\mathbb {R}_{F}\) is not an upper set, there must exist pairs \((u,v)\in \mathbb {R}_{F},(u^{\prime },v)\in (\uparrow \mathcal {D}_{F}\setminus \mathbb {R}_{F}=\mathbb {M}_{F})\) such that \(u\prec u^{\prime }\). By definition of \(\mathbb {R}_{F}\), there must exist \(v^{\prime } \prec v\) such that \((u,v^{\prime })\in \mathbb {M}_{F}\). It follows that \((u^{\prime },v^{\prime })\in \uparrow \mathcal {D}_{F}\) while \((u^{\prime },v) \in \mathbb {M}_{F}\) is such that \(v^{\prime } \prec v\), contradicting the definition of \(\mathbb {M}_{F}\). □
Note that all three sets can be derived from the set \(\mathcal {D}_{F}\) of core transitions (see Theorem 4):
4.4 Linear combinations at the input and at the output
As noticed by Lambin, Derbez and Fouque [29], the result of conventional division property propagation through a function may change significantly, if an invertible linear map is composed with the function before computing the propagation table (and its inverse is composed with the consequent function to preserve the functional equivalence of the analyzed primitive). This setting is also useful for finding integral distinguishers which take an arbitrary affine subspace as an input set, as opposed to bit-aligned cubes. In [29], it was suggested to exhaust all invertible linear maps to be composed with the analyzed function. While this is a viable approach for 4-bit S-boxes, it is hardly scalable for bigger functions. Later, Derbez and Fouque [30] showed that exhausting all possible choices of one linear component (a linear combination) is sufficient to determining whether an integral distinguisher can be found using this method. More precisely, integral distinguishers with an input affine subspace of codimension 1 can be checked. For the input side, the linear component defines the orthogonal subspace on which the inputs are fixed to a constant. For the output side, the linear component defines the output linear component which is used in the integral distinguisher. Udovenko [16] showed that these two cases are almost identical, due to the antisymmetry of transitions with respect to the inverse mapping (see Corollary 3).
Theorem 5 ([16, Thm.3]).
Let S be a permutation of \({\mathbb {F}_{2}^{n}}\), \(\alpha , u, v \in {\mathbb {F}_{2}^{n}}\), \({L_{\alpha}} \in GL_{n}(\mathbb {F}_{2})\) be such that Lα(x) = (〈α, x〉,…). Then,
Similarly,
Proof
The first statement follows from Theorem 3 (point 2). The second statement follows from Theorem 3 and Corollary 3 (using (S ∘ Lα− 1)− 1 = Lα ∘ S− 1). □
Remark 13.
In the case S is not bijective, the Boolean function \(z \mapsto \left \langle {a,S^{-1}(z)}\right \rangle \) can be replaced by \(z \mapsto {\sum }_{x ~:~ S(x) = z} \langle {a,x}\rangle \).
4.5 Propagation through a linear map
We now consider conventional division property propagation through linear maps. First, we will show that, in the case of linear maps, minimal transitions coincide with core transitions.
Proposition 21.
Let M be a linear map given by a linear matrix \(M \in \mathbb {F}_{2}^{m\times n}\), \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). Then, (i) : \(u \underset {{core}}{\overset {M}{\rightharpoondown }} v\) if and only if \(u \underset {{\min \limits }}{\overset {M}{\rightharpoondown }} v\) (ii) : only if wt(u) = wt(v). Furthermore, (iii) : \(u \underset {{\min \limits }}{\overset {M}\rightharpoondown } v\) implies wt(u) ≤wt(v).
Proof
(iii) : By definition of \(u \overset {M}{\rightharpoondown } v\), there must exist \(u^{\prime } \succeq u, v^{\prime } \preceq v\) such that \(u \preceq u^{\prime } \xrightarrow {M} v^{\prime } \preceq v\). By Proposition 12, \(u^{\prime } \xrightarrow {M} v^{\prime }\) implies \(\text {wt}(u^{\prime }) \le \text {wt}(v^{\prime })\). Therefore, we have \(\text {wt}(u) \le \text {wt}(u^{\prime }) \le \text {wt}(v^{\prime }) \le \text {wt}(v)\).
(ii) : From (iii) we already know that wt(u) ≤wt(v). Now, assume that \(u \underset {{\min \limits }}{\overset {M}{\rightharpoondown }} v\) and wt(u) < wt(v). It follows that Mv(x) contains a monomial multiple of xu. It is easy to show that there must exist \(v^{\prime } \prec v\) with \(\text {wt}(v^{\prime }) = \text {wt}(u)\) such that \(M^{v^{\prime }}(x)\) contains the monomial xu, contradicting that \(u \underset {{\min \limits }}{\overset {M}{\rightharpoondown }} v\). Indeed, all monomials in Mv(x) are multiples of some monomials from \(M^{v^{\prime }}(x)\).
(ii) : It is left to prove that, for linear maps, minimal transitions coincide with core transitions. Let \(u {\underset {{\min \limits }}{\overset {M}{\rightharpoondown }}} v\) that is not a core transition. Then, there must exist \(u^{\prime } \succ u\) such that \(u^{\prime } {\underset {{core}}{\overset {M}{\rightharpoondown }}} v\) (and \(u^{\prime } {\underset {{\min \limits }}{\overset {M}{\rightharpoondown }}} v\) as a special case). However, it is then \(\text {wt}(u) < \text {wt}(u^{\prime }) = \text {wt}(v)\), which contradicts wt(u) = wt(v) following from \(u \underset {{\min \limits }}{\overset {M}{\rightharpoondown }} v\) using (ii). □
The result of Zhang and Rijmen [26] (Theorem 2) directly applies to minimal transitions of conventional division property (as originally intended in their work). Indeed, core and minimal transitions \(u \underset {{core}}{\overset {M}{\rightharpoondown }} v\) must have wt(u) = wt(v) and also \(u \xrightarrow {M} v\), which makes Theorem 2 applicable.
Theorem 6.
Let M be a linear map given by a linear matrix \(M \in \mathbb {F}_{2}^{m\times n}\), \(u \in {\mathbb {F}_{2}^{n}}, v \in {\mathbb {F}_{2}^{m}}\). Then, \(u \underset {{core}}{\overset {M}{\rightharpoondown }} v\) if and only if \(u \underset {{\min \limits }}{\overset {M}{\rightharpoondown }} v\) if and only if Mv, u is an invertible square matrix, where Mv, u denotes the submatrix of M with rows selected by the vector v and columns selected by the vector u.
5 Upper bounds on the degree of a composition of functions
A classic problem in cryptanalysis of symmetric-key primitives is determining the algebraic degree of a block cipher (more precisely, it’s maximum over all possible keys). Low algebraic degree can be used in the higher-order differential attack, introduced by Knudsen [1]. Most, if not all, block ciphers are built from an iterative structure - a composition of simple round functions. Therefore, the problem reduces to finding upper bounds on the algebraic degree of a composition of functions.
In this section, we briefly recall classic upper bounds on the algebraic degree and describe their relations with variants of division property. While bit-based division property is much more fine-grained than a degree upper bound, computing its propagation is generally a hard problem. Degree-based bounds, on the other hand, can be usually derived using pen-and-paper, allowing quick degree estimations.
Chen, Xiang, Zeng and Zhang [15] studied relationships between the bit-/word-/state-based division property (perfect and conventional), the naive and the Boura-Canteaut degree bounds, concluding that division property is superior over those bounds. Udovenko [16] further studied relationships with the recent bounds by Carlet.
5.1 Classic methods
The most generic and straightforward upper bound is obtained by simply multiplying the degrees of composed functions. It can not be improved in general without having additional information about the functions.
Proposition 22.
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, g\colon {\mathbb {F}_{2}^{m}} \to \mathbb {F}_{2}\). Then,
The first nontrivial upper bound was obtained by Canteaut and Videau [31] under an additional constraint of divisibility of all Walsh coefficients by a power of 2.
Theorem 7 ([31, Cor.1]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, g\colon {\mathbb {F}_{2}^{m}} \to \mathbb {F}_{2}\) such that the Walsh spectrum of F is divisible by 2ℓ, for a integer ℓ ≥ 1. Then,
Remark 14.
The Walsh spectrum of \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\) is the multiset given by
Later, Boura and Canteaut [12], among other results, showed a new bound based on the degree of the inverse of one of the functions, which is a generalization of the result specific to SPN functions by Boura, Canteaut and De Cannière [32].
Theorem 8 ([12, Cor.3.2]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) be a bijection, \(g\colon {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\). Then,
This bound is quite surprising as it shows that a block cipher may need nearly twice as many rounds (compared to the naive bound) to reach full degree, as the following example shows.
Example 8.
To illustrate the idea, consider an SPN-based block cipher with 2r rounds, n-bit block and an m-bit S-box, m ≥ 3. The degree of the S-box is at most m − 1 := d. In the first half of the rounds, let us apply the naive degree bound (Proposition 22), which increases the degree bound by a factor d per round. In the second half of the rounds, let us apply the Boura-Canteaut bound, which decreases the degree “deficit” by a factor d per round. To get full degree n − 1 (degree “deficit” 1) for the full 2r-round permutation, we need dr + dr ≥ n. Let r be the smallest number such that the condition holds, i.e., 2(r − 1) rounds are not enough to reach full degree. However, using only the naive bound, the upper bound may reach full degree already after r + 1 rounds, instead of 2r: dr+ 1 ≥ 2dr ≥ n.
More detailed analysis of this phenomenon in the framework of Feistel Networks was done in [33], and in the framework of SPNs in [13].
More recently, Carlet [14] showed several bounds based on the degrees of the involved graph indicators. We reproduce here one general theorem which is particularly relevant for division property.
Theorem 9 ([14, Theorems 1, 3, 4]).
Let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}, g\colon {\mathbb {F}_{2}^{m}} \to \mathbb {F}_{2}\). Then,

More generally, let G1,…,Gr be such that \(G_{i}\colon \mathbb {F}_{2}^{m_{i-1}} \to \mathbb {F}_{2}^{m_{i}}\) and let \(g: \mathbb {F}_{2}^{m_{r}} \to \mathbb {F}_{2}\). Then,

Bounds from this theorem are not comparable to the previous bounds (in the common case of the composition of two functions). That is, for any of the classic bounds, there exists a case where it will be strictly stronger than the other bounds. A more complete study and comparison of classic bounds (excluding the division property) can be found in [14].
5.2 Formulation with conventional division property
In the seminal paper [4], Todo provides a propagation rule of conventional division property through a vectorial Boolean function.
Proposition 23 (4).
Let \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfy division property \({D^{n}_{k}}\), and let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). Then, \(F(X) \subseteq {\mathbb {F}_{2}^{m}}\) (elements with odd-multiplicity) satisfies \(D^{m}_{k^{\prime }}\) with \(k^{\prime }=\left \lceil {\frac {k}{\deg {F}}}\right \rceil \).
Since 1-dimensional division property corresponds to an upper bound on the algebraic degree of the set (i.e., we have \(\deg {X} \le n - k, \deg {F(X)} \le m - k^{\prime }\)), we can conclude the following upper bound on the degree of the output set.
Corollary 4.
Let \(X \subseteq {\mathbb {F}_{2}^{n}}, F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). Then,
This bound clearly resembles the Boura-Canteaut bound (Theorem 8). However, the proposition relates the degrees of sets, rather than the degrees of functions. Furthermore, it has \(\deg {F}\) instead of \(\deg {F^{-1}}\) in the denominator and even does not require F to be invertible. In fact, Corollary 4 can be interpreted exactly as the Boura-Canteaut when F is invertible: let  so that
so that 
The latter identity  also implies the complementary analogue of the basic upper bound (Proposition 22): \(\deg {F(X)} \le \deg {X} \cdot \deg {F^{-1}}\), which can be translated into the division property terminology.
also implies the complementary analogue of the basic upper bound (Proposition 22): \(\deg {F(X)} \le \deg {X} \cdot \deg {F^{-1}}\), which can be translated into the division property terminology.
Corollary 5 ([16, Prop.3.22]).
Let \(X \subseteq {\mathbb {F}_{2}^{n}}\) satisfy division property \({D^{n}_{k}}\), and let \(F\colon {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{n}}\) be a bijection. Then, \(F(X) \subseteq {\mathbb {F}_{2}^{n}}\) (elements with odd-multiplicity) satisfies \(D^{n}_{k^{\prime }}\) with
Remark 15.
Todo also noticed that division property \({D^{n}_{n}}\) is preserved by bijections (since the input and output sets have to be exactly \({\mathbb {F}_{2}^{n}}\)). This corollary includes this case.
The two rules from the corollaries mirror the two classic degree-based upper bounds - the naive bound and the Boura-Canteaut bound. However, division property can be more precise: instead of computing \(k^{\prime }\) solely from k and the degree of the function (or of its inverse), it can be computed from the DPPT of the function. More precisely, the value
is optimal (maximum possible) for \(k^{\prime }\), and the degree-based bounds do not always reach it (see Example 9 below). This parameter, as a function of F and k, was introduced in [28].
By Theorem 3, the value of DF(k) can be also characterized by

In other words, the 1-dimensional division property propagation table is fully characterized by the pairs of degrees (one per each variable) of maximal monomials of the graph indicator  of the considered function F. This information is more detailed then simply the degree of the graph indicator, used in the Carlet’s bound.
of the considered function F. This information is more detailed then simply the degree of the graph indicator, used in the Carlet’s bound.
5.3 Conventional division trails and indicator monomial trails
Udovenko [16] exhibited a close connection of the Carlet’s graph indicator method with conventional division property propagation. In fact, the latter can be seen as a more fine-grained variant of the former, requiring more information about the composed function, more computational effort to compute the upper bound, but (possibly) resulting in a stronger bound.
The result relies on the following representation of the graph indicator of a composition as the sum of the products of the involved indicators over all possible values of all intermediate variables.
Proposition 24 (14, 34).
Let \(G_{i}\colon \mathbb {F}_{2}^{m_{i-1}} \to \mathbb {F}_{2}^{m_{i}}\), i ∈{1,…,r}, let F = Gr ∘… ∘ G1. Then,

The following theorem shows that conventional division property trails essentially correspond to chains of monomials from the involved graph indicators.
Theorem 10 ([16, Thm.4]).
Let F, Gi be defined as above. Let I be the formal expansion (i.e., no +-cancellations) of the product

Then, I contains a monomial multiple of
if and only if there exists a valid division trail
Proof
The proof relies on Theorem 3, applied to each link in the indicator chain and division trail:



The formal expansion I contains a monomial multiple of (4) if and only if there exists a chain of monomials \(x^{u^{\prime }}y_{1}^{w^{\prime }_{1}}\), \(y_{1}^{w_{1}}y_{2}^{w^{\prime }_{2}}\), …, \(y_{r-1}^{w_{r-1}}z^{\lnot v^{\prime }}\) from the ANFs of 
 respectively such that these monomials multiply to (4). In other words, the conditions are \(u^{\prime } \succeq u, \lnot v^{\prime } \succeq \lnot v\), and
respectively such that these monomials multiply to (4). In other words, the conditions are \(u^{\prime } \succeq u, \lnot v^{\prime } \succeq \lnot v\), and
Equivalently, \(w^{\prime }_{1} \succeq \lnot w_{1}\), …, \(w^{\prime }_{r-1} \succeq \lnot w_{r-1}\). In other words,  contains a monomial multiple of
contains a monomial multiple of  contains a monomial multiple of \(y_{r-1}^{w_{r-1}}z^{\lnot v}\). By Theorem 3 (see (6)-(7) above), these are equivalent to the validity of the division trail (5). □
contains a monomial multiple of \(y_{r-1}^{w_{r-1}}z^{\lnot v}\). By Theorem 3 (see (6)-(7) above), these are equivalent to the validity of the division trail (5). □
In order to relate conventional division property propagation to Carlet’s Theorem 9, we will show that the latter can be proven in terms of the formal expansion of the graph indicator product, i.e., that it does not rely on any +-cancellations. We recall the statement.
Theorem 9. Let G1,…,Gr be such that \(G_{i}\colon \mathbb {F}_{2}^{m_{i-1}} \to \mathbb {F}_{2}^{m_{i}}\) and let \(g: \mathbb {F}_{2}^{m_{r}} \to \mathbb {F}_{2}\). Then,

Proof
Let \(F := g {\circ} G_{r} {\circ} {\ldots } {\circ} G_{1} : {\mathbb {F}_{2}^{n}} \to \mathbb {F}_{2}\). We will use the fact that the indicator of a Boolean function y = f(x) is simply y+f(x). We have

where d is the maximum integer such that the monomial \(x^{d} y_{1}^{ \underline {1}}{\ldots } y_{r}^{ \underline {1}}\) belongs to the formal expansion

Here, we used the expression of  from Proposition 24. It follows that
from Proposition 24. It follows that

Note that  for non-constant g. For constant g the theorem follows from the fact that the sum
for non-constant g. For constant g the theorem follows from the fact that the sum  is always non-negative. We conclude that
is always non-negative. We conclude that

□
We conclude that bit-based conventional division property is never worse than Carlet’s bound (Theorem 9). Furthermore, we will now show that already 1-dimensional (state-based) table-based division property propagation is never worse than Carlet’s bound and, in fact, is often better (at the cost of requiring more information about the graph indicator’s ANF and being computational).
Proposition 25.
Bounds by conventional state-level division property with table-based propagation (i.e., based on DF) are never worse than bounds from Theorem 9.
Proof
Let G1,…,Gr,g be defined as in Theorem 9, f = g ∘ Gr ∘… ∘ G1. Theorem 9 states that

We will prove that there doesn’t exist a weak division trail (under the weight projection wt1 = wt)
where wi ∈ [0,mi] for all i. This will prove that the division property implies the bound \(\deg _{f} \le d\).
The proof is by contradiction. Assume that such a weight trail exists. Note that it does not imply existence of the full binary trail, only separate trails for each of its steps:
where \(u \in {\mathbb {F}_{2}^{n}}, v_{i} \in \mathbb {F}_{2}^{m_{i}}\) for all i. By Theorem 3, each such transition implies a particular monomial (multiple) in the respective graph indicator’s ANF, implying a degree bound:

Summing the bounds leads to

By substituting the definition of d, it must be

which implies that g is constant. However, for constant g the only weak transition to 1 is \(0 \overset {g}{\rightharpoondown } 1\), and the only weak transitions to 0 are \(0 \overset {G_{i}}{\rightharpoondown } 0\), implying d + 1 = w1 = … = wr = 0, which is not possible due to d ≥ 0 (defining the degree of the constant zero function to be \(-\infty \) causes contradiction as well). We obtain a contradiction with existence of such a weight trail. □
5.4 Exposition of compositional bounds through bounds on monomials of the graph indicator
In this section, we will show that Carlet’s graph indicator method allows illustrative comparison of classic compositional bounds and 1-dimensional conventional division property. A key idea is to derive bounds on degrees of monomials in the graph indicator directly from a given classic bound. The motivation comes from the fact that possible degrees of monomials in the graph indicator’s ANF define 1-dimensional division property propagation. This allows comparison of bounds in the same setting.
The obtained bounds can then be illustrated graphically on an example function, exhibiting visually the impossible degree pairs that are or are not removed by each of the bounds. We will focus on the classic bounds for compositions of two functions.
Let \(F: {\mathbb {F}_{2}^{n}} \to {\mathbb {F}_{2}^{m}}\). Let xuyv be a maximal monomial in  Define
Define
Note that \(\deg {g} = m - \text {wt}(v)\). Recall that

Observe that the monomial \(x^{u}y^{v}y^{\lnot v}=x^{u}y^{\underline {1}}\) belongs to the polynomial 
 as it occurs exactly once in the formal expansion (due to the maximality of xuyv). It follows that xu belongs to g(F(x)) or is constant (if \(u=\underline {0}\)). Hence, \(\text {wt}(u) \le \deg {g{\circ} F}\). We can now apply classic bounds to the composition g ∘ F and obtain bounds on degrees of the monomial xuyv from the graph indicator of F.
as it occurs exactly once in the formal expansion (due to the maximality of xuyv). It follows that xu belongs to g(F(x)) or is constant (if \(u=\underline {0}\)). Hence, \(\text {wt}(u) \le \deg {g{\circ} F}\). We can now apply classic bounds to the composition g ∘ F and obtain bounds on degrees of the monomial xuyv from the graph indicator of F.
-
1.
By the naive bound (Proposition 22), we have
$$ \text{wt}(u) ~\le~ \deg{g{\circ} F} ~\le~ \deg{g} \cdot \deg{F} ~=~ (m-\text{wt}(v)) \cdot \deg{F}. $$Therefore,
$$ \text{wt}(u) + \text{wt}(v) \cdot \deg{F} \le m \cdot \deg{F}. $$(8) -
2.
By the Boura-Canteaut bound (Theorem 8), we have
$$ \text{wt}(u) ~\le~ \deg{g{\circ} F} ~\le~ m - \frac{m-\deg{g}}{\deg{F^{-1}}} ~=~ m - \frac{\text{wt}(v)}{\deg{F^{-1}}}. $$Therefore,
$$ \text{wt}(u)\cdot \deg{F^{-1}} + \text{wt}(v) \le m \cdot \deg{F^{-1}}. $$(9) -
3.
By the Carlet bound (Theorem 9), we have

Therefore,
 (10)
(10)
Remark 16.
The third bound is trivial by definition. What is important here is that it is equivalent to the Carlet’s bound. Similarly, the second bound can be obtained from the first one applied directly to the inverse of F. However, it is insightful to derive it directly from the Boura-Canteaut bound.
Note that by the monotonicity of bounds and by the fact that xuyv was chosen as a maximal monomial in the graph indicator’s ANF, these bounds ((8), (9), (10)) hold for all monomials  in general.
in general.
Example 9.
We will now illustrate these bounds on a simple example. Let \(F : \mathbb {F}_{2}^{14} \to \mathbb {F}_{2}^{14}\) be defined as
so that 
The three bounds together with the actual maximal degree pairs are displayed graphically on Fig. 3. The black dots correspond to the set of pairs

i.e., to pairs of degrees on x and y of monomials having a monomial multiple present in the ANF of the graph indicator of F. The black crosses correspond to pairs of degrees outside of this set. The red dashed line corresponds to the bound (8) derived from the naive degree bound. The blue dotted line corresponds to the bound (9) derived from the Boura-Canteaut degree bound. The purple dash-dot line corresponds to the bound (10) derived from the Carlet’s degree bound. The shaded areas above the lines (exclusive of the respective lines) cover points not satisfying the bounds.
Comparison of bounds on degrees on x and y of monomials f(x, y) = xuyv of the graph indicator  where \(F : \mathbb {F}_{2}^{14} \to \mathbb {F}_{2}^{14}\) is defined as \(F : (\mathbb {F}_{2^{7}})^{2} \to (\mathbb {F}_{2^{7}})^{2} : (x_{1},x_{2}) \mapsto (x_{1}^ 3, x_{2}^{1/3})\), so that
where \(F : \mathbb {F}_{2}^{14} \to \mathbb {F}_{2}^{14}\) is defined as \(F : (\mathbb {F}_{2^{7}})^{2} \to (\mathbb {F}_{2^{7}})^{2} : (x_{1},x_{2}) \mapsto (x_{1}^ 3, x_{2}^{1/3})\), so that  Shaded areas highlight the points not satisfying the respective bounds (exclusive of the respective lines themselves)
Shaded areas highlight the points not satisfying the respective bounds (exclusive of the respective lines themselves)
Note that the plot is symmetric along the \(\deg _{y} f=\deg _{x} f\) line, due to the construction of F implying \(\deg {F}=\deg {F^{-1}}\). This makes the naive and the Boura-Canteaut bounds fully symmetric (but not equivalent), which is not the case in general.
The figure shows that each bound is tight, i.e., that they all reach equality at some points, and that none of them are redundant. Furthermore, even all three bounds jointly do not precisely model the right set of degree pairs: the points with coordinates (7,12) and (12,7) do not belong to the set \(\downarrow \text {wt}_{14,14}(\mathcal {A}({\Gamma }_{F}))\), but are not rejected by any of the three bounds.
In Section 5.2 it was stated that degree-based bounds for 1-dimensional (state-based) conventional division property are not always precise. The points (7,12) and (12,7) mentioned above prove this statement. Indeed, the point (7,12) implies DF(7) = 14 − (12 − 1) = 3. At the same time, the bounds from Proposition 23 and Corollary 4 state respectively that \(D_{F}(7) \ge \left \lceil {\frac {7}{\deg {F}}}\right \rceil = 2\) and \(D_{F}(7) \ge n - (n-7)\deg {F^{-1}} = -14\).
Finally, we note that even 1-dimensional (state-based) conventional division property propagation (using DF rather than degree-based bounds) utilizes full knowledge of the degrees of the maximal monomials in the graph indicator’s ANF (by Theorem 3). Hence, it is illustrated as a precise boundary (black solid line) on the figure.
6 Security arguments
The perfect division property can be used to provide security arguments for ciphers against attacks. One important attack vector is higher-order differential cryptanalysis [35], which exploits a low algebraic degree of a cipher or, more generally, a missing monomial in the ANF. While the standard definition of the algebraic degree of a vectorial Boolean function considers the maximum degree over all its coordinates, the security of a cipher depends on the minimum degree over all possible (nonzero) linear combinations of the coordinates. Indeed, an adversary can choose any linear combination of output bits they want to attack.
Definition 14 (Degree of a Block Cipher 36).
Let \(E \colon {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\) be a block cipher, where the ANF can be written as \(E_{k}(x) = {\sum }_{u \in {\mathbb {F}_{2}^{n}}} p_{u}(k) x^{u}\). We define the algebraic degree of E by
Furthermore, we define the minimum degree of E by
Let \(E \colon { _{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\) be a block cipher. We can write the ANF of Ek as
where \(p_{u} \colon \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\) for all \(u \in {\mathbb {F}_{2}^{n}}\) and
When the input division property (u, v) propagates to ei for E, ı.e.,
this means that \(\lambda _{u, v}^{(i)} = 1\) and pu(k)≠ 0. We refer to u as the input monomial and v as the key pattern. The propagation above implies that the monomial xu occurs in the ANF of \(E_{k}^{(i)}\) for at least one key k.
To show that E has an algebraic degree of at least d, it is sufficient to find a \(u \in {\mathbb {F}_{2}^{n}}\) where wt(u) ≥ d, a key pattern \(v \in \mathbb {F}_{2}^{\ell }\) and an output bit i ∈{1,…,n}, so that
In the case of the minimum degree, we have to find n pairs of input monomials and key patterns (u1,v1),…,(un,vn) and compute the corresponding entries in the ANF for all output bits. When the matrix
has rank n, the minimum degree of E is at least \(\min \limits _{i \in \{1, \ldots , n \} } \text {wt}(u_{i})\).
The integral attacks can be seen as a generalization of higher-order differentials. While for the latter one, an adversary sums over
where the weight of u is larger then the algebraic degree of E, the adversary sums over an arbitrary set \(S \subset {\mathbb {F}_{2}^{n}}\):
This can be considered as a linear combination of coefficients of the ANF of \(\langle \beta , E_{k}(x) \rangle = {\sum }_{u \in {\mathbb {F}_{2}^{n}}} \lambda _{u} x^{u}\):
When this sum is always key-dependent, i.e., there does not exists an integral attack on a certain block cipher, we say that the cipher fulfills the integral-resistance property.
Definition 15 (Integral-Resistance Property 36).
Let \(E\colon {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\) be a block cipher. We say that E fulfills the integral-resistance property when for every proper non-empty subset \(M \subset { _{2}^{n}}\) and every non-zero output mask \(\beta \in {\mathbb {F}_{2}^{n}}\) the sum
is key-dependent.
Definition 16 (Integral-Resistance Matrix 36).
Let \(E\colon {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\) be a block cipher with the corresponding ANF
Further, let \(v_{1}, {\ldots } v_{s} \in \mathbb {F}_{2}^{\ell }\) be key patterns. We call the following matrix over \(\mathbb {F}_{2}^{n^{2} \times s}\)
an integral-resistance matrix. A column i corresponds to a key pattern vi and each row corresponds to a combination of an output bit and a monomial of weight n − 1.
Now, the integral-resistance matrix is sufficient to prove the integral-resistance property for a block cipher, assuming an independent whitening key added at the input (see also Proposition 18).
Proposition 26.
[36] Let \(E\colon {\mathbb {F}_{2}^{n}} \times \mathbb {F}_{2}^{\ell } \to {\mathbb {F}_{2}^{n}}\) be a block cipher and \(\mathcal {I}(E)\) be a corresponding integral-resistance matrix. If \(\mathcal {I}(E)\) has rank n2 and k0 is an independent whitening key, Ek(x + k0) fulfills the integral-resistance property.
7 Conclusions
In this survey, we explained the state-of-the-art variants of the division property, explained the connection with the ANF and how the division property can be used to find both attacks and security arguments for symmetric cryptographic primitives. Our focus was on the underlying theory and on a clear and precise notation. We hope that in particular readers with a background in Boolean functions find our survey helpful.
We also like to note that there are several important topics that we did not cover. Those topics are mainly concerned with an efficient computation of the division property using either dedicated algorithms [4, 7, 30, 37] or general tools, in particular mixed integer linear programming tools [8, 10, 17, 38,39,40,41,42,43], SAT/SMT solvers [16, 27, 44,45,46,47,48]. It is actually this practical computational aspect that is of great importance for all variants of the division property. As described, the security of symmetric primitives is the concrete security against concrete attacks. The division property is a powerful set of techniques to compute concrete properties of those ciphers.
Notes
This, and the picture of the Feistel cipher are taken from [19].
References
Knudsen, L.R.: Truncated and higher order differentials. In: Preneel, B. (ed.) FSE’94. LNCS, vol. 1008, pp. 196–211. Springer. https://doi.org/10.1007/3-540-60590-8_16 (1995)
Knudsen, L.R., Wagner, D.: Integral cryptanalysis. In: Daemen, J., Rijmen, V. (eds.) FSE 2002. LNCS , vol. 2365, pp. 112–127. Springer. https://doi.org/10.1007/3-540-45661-9_9 (2002)
Dinur, I., Shamir, A.: Cube attacks on tweakable black box polynomials. In: Joux, A. (ed.) EUROCRYPT 2009. LNCS, vol. 5479, pp. 278–299. Springer. https://doi.org/10.1007/978-3-642-01001-9_16 (2009)
Todo, Y.: Structural evaluation by generalized integral property. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015, Part I. LNCS, vol. 9056, pp. 287–314. Springer. https://doi.org/10.1007/978-3-662-46800-5_12 (2015)
Todo, Y.: Integral cryptanalysis on full MISTY1. In: Gennaro, R., Robshaw, M.J.B. (eds.) CRYPTO 2015, Part I. LNCS , vol. 9215, pp. 413–432. Springer. https://doi.org/10.1007/978-3-662-47989-6_20 (2015)
Todo, Y.: Integral cryptanalysis on full MISTY1. J. Cryptol. 30(3), 920–959 (2017). https://doi.org/10.1007/s00145-016-9240-x
Todo, Y., Morii, M.: Bit-based division property and application to simon family. In: Peyrin, T. (ed.) FSE 2016. LNCS, vol. 9783, pp. 357–377. Springer. https://doi.org/10.1007/978-3-662-52993-5_18 (2016)
Hao, Y., Leander, G., Meier, W., Todo, Y., Wang, Q.: Modeling for three-subset division property without unknown subset - improved cube attacks against Trivium and Grain-128AEAD. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020, Part I. LNCS, vol. 12105, pp. 466–495. Springer. https://doi.org/10.1007/978-3-030-45721-1_17 (2020)
Hao, Y., Leander, G., Meier, W., Todo, Y., Wang, Q.: Modeling for three-subset division property without unknown subset. J. Cryptol. 34(3), 22 (2021). https://doi.org/10.1007/s00145-021-09383-2
Xiang, Z., Zhang, W., Bao, Z., Lin, D.: Applying MILP method to searching integral distinguishers based on division property for 6 lightweight block ciphers. In: Cheon, J.H. , Takagi, T. (eds.) ASIACRYPT 2016, Part I. LNCS, vol. 10031, pp. 648–678. Springer. https://doi.org/10.1007/978-3-662-53887-6_24 (2016)
Boura, C., Canteaut, A.: Another view of the division property. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016, Part I. LNCS, vol. 9814, pp. 654–682. Springer. https://doi.org/10.1007/978-3-662-53018-4_24 (2016)
Boura, C., Canteaut, A.: On the influence of the algebraic degree of f− 1 on the algebraic degree of G ∘ F. IEEE Trans. Inf. Theory 59(1), 691–702 (2013)
Biryukov, A., Khovratovich, D., Perrin, L.: Multiset-algebraic cryptanalysis of reduced Kuznyechik, Khazad, and secret SPNs. IACR Trans. Symm. Cryptol. 2016(2), 226–247 (2016). https://doi.org/10.13154/tosc.v2016.i2.226-247. https://tosc.iacr.org/index.php/ToSC/article/view/572
Carlet, C.: Graph indicators of vectorial functions and bounds on the algebraic degree of composite functions. IEEE Transactions on Information Theory, 1–1. https://doi.org/10.1109/TIT.2020.3017494 (2020)
Chen, S., Xiang, Z., Zeng, X., Zhang, S.: On the relationships between different methods for degree evaluation. IACR Trans. Symm. Cryptol. 2021(1), 411–442 (2021). https://doi.org/10.46586/tosc.v2021.i1.411-442
Udovenko, A.: Convexity of division property transitions: Theory, algorithms and compact models. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021, Part I. LNCS, vol. 13090, pp. 332–361. Springer. https://doi.org/10.1007/978-3-030-92062-3_12 (2021)
Hu, K., Sun, S., Wang, M., Wang, Q.: An algebraic formulation of the division property: Revisiting degree evaluations, cube attacks, and key-independent sums. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020, Part I. LNCS, vol. 12491, pp. 446–476. Springer. https://doi.org/10.1007/978-3-030-64837-4_15 (2020)
Carlet, C.: Boolean functions for cryptography and coding theory, Cambridge University Press. https://doi.org/10.1017/9781108606806 (2021)
Jean, J.: TikZ for Cryptographers. https://www.iacr.org/authors/tikz/
Shannon, C.: A mathematical theory of cryptography (1945)
Ferguson, N., Kelsey, J., Lucks, S., Schneier, B., Stay, M., Wagner, D., Whiting, D.: Improved cryptanalysis of Rijndael. In: Schneier, B. (ed.) FSE 2000. LNCS , vol. 1978, pp. 213–230. Springer. https://doi.org/10.1007/3-540-44706-7_15 (2001)
Todo, Y., Aoki, K.: Fast fourier transform key recovery for integral attacks. IEICE Trans. Fundam. Electron. Commun. Comput. Sci. 98-A (9), 1944–1952 (2015)
Ye, C.-D., Tian, T.: Revisit division property based cube attacks: key-recovery or distinguishing attacks?. IACR Trans. Symm. Cryptol. 2019(3), 81–102 (2019). https://doi.org/10.13154/tosc.v2019.i3.81-102
Hebborn, P., Lambin, B., Leander, G., Todo, Y.: Lower bounds on the degree of block ciphers. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020, Part I. LNCS, vol. 12491, pp. 537–566. Springer. https://doi.org/10.1007/978-3-030-64837-4_18 (2020)
Hebborn, P.: Security assessment and design of symmetric ciphers for emerging applications. doctoralthesis, Ruhr-Universität Bochum, Universitätsbibliothek. https://doi.org/10.13154/294-8588 (2022)
Zhang, W., Rijmen, V.: Division cryptanalysis of block ciphers with a binary diffusion layer. IET Inf. Secur. 13(2), 87–95 (2018)
Hu, K., Wang, Q., Wang, M.: IACR transactions class documentation. IACR Trans. Symm. Cryptol. 2020(1), 396–424 (2020). https://doi.org/10.13154/tosc.v2020.i1.396-424
Göloğlu, F., Rijmen, V., Wang, Q.: On the division property of S-boxes. Cryptology ePrint Archive, Report 2016/188.(2016) https://eprint.iacr.org/2016/188
Lambin, B., Derbez, P., Fouque, P. -A.: Linearly equivalent S-boxes and the division property. Des. Codes Crypt. 88(10), 2207–2231 (2020)
Derbez, P., Fouque, P.-A.: Increasing precision of division property . IACR Trans. Symm. Cryptol. 2020(4), 173–194 (2020). https://doi.org/10.46586/tosc.v2020.i4.173-194
Canteaut, A., Videau, M.: Degree of composition of highly nonlinear functions and applications to higher order differential cryptanalysis. In: Knudsen, L.R. (ed.) EUROCRYPT 2002. LNCS, vol. 2332, pp. 518–533. Springer. https://doi.org/10.1007/3-540-46035-7_34 (2002)
Boura, C., Canteaut, A.: De Cannière, C.: Higher-order differential properties of Keccak and Luffa. In: Joux, A. (ed.) FSE 2011. LNCS, vol. 6733, pp. 252–269. Springer. https://doi.org/10.1007/978-3-642-21702-9_15 (2011)
Perrin, L., Udovenko, A.: Algebraic insights into the secret Feistel network. In: Peyrin, T. (ed.) FSE 2016. LNCS, vol. 9783, pp. 378–398. Springer. https://doi.org/10.1007/978-3-662-52993-5_19 (2016)
Carlet, C.: Handling vectorial functions by means of their graph indicators. IEEE Trans. Inf. Theory 66(10), 6324–6339 (2020). https://doi.org/10.1109/TIT.2020.2981524
Lai, X.: Higher order derivatives and differential cryptanalysis. In: Communications and cryptography. the springer international series in engineering and computer science, Vol. 276, Pp. 227–233. Springer (1994)
Hebborn, P., Lambin, B., Leander, G., Todo, Y.: Strong and tight security guarantees against integral distinguishers. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021, Part I. LNCS, vol. 13090, pp. 362–391. Springer. https://doi.org/10.1007/978-3-030-92062-3_13 (2021)
Todo, Y., Morii, M.: Compact representation for division property. In: Foresti, S., Persiano, G. (eds.) CANS 16. LNCS, vol. 10052, pp. 19–35. Springer. https://doi.org/10.1007/978-3-319-48965-0_2 (2016)
Todo, Y., Isobe, T., Hao, Y., Meier, W.: Cube attacks on non-blackbox polynomials based on division property. In: Katz, J., Shacham, H. (eds.) CRYPTO 2017, Part III. LNCS, vol. 10403, pp. 250–279. Springer. https://doi.org/10.1007/978-3-319-63697-9_9 (2017)
Sasaki, Y., Todo, Y.: New algorithm for modeling S-box in MILP Based Differential and division trail search. In: SECITC. Lecture Notes in Computer Science, Vol. 10543, Pp. 150–165. Springer (2017)
Wang, S., Hu, B., Guan, J., Zhang, K., Shi, T.: MILP-aided method of searching division property using three subsets and applications. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019, Part III. LNCS, vol. 11923, pp. 398–427. Springer. https://doi.org/10.1007/978-3-030-34618-8_14 (2019)
Sun, L., Wang, W., Wang, M.: MILP-Aided bit-based division property for primitives with non-bit-permutation linear layers. IET. Inf. Secur. 14(1), 12–20 (2020)
Delaune, S., Derbez, P., Gontier, A., Prud’homme, C.: A simpler model for recovering superpoly on trivium. In: AlTawy, R., Hülsing, A. (eds.) SAC 2021. LNCS, vol. 13203, pp. 266–285. Springer. https://doi.org/10.1007/978-3-030-99277-4_13 (2022)
ElSheikh, M., Youssef, A.M.: On MILP-based automatic search for bit-based division property for ciphers with (large) linear layers. In: Baek, J., Ruj, S. (eds.) ACISP 21. LNCS, vol. 13083, pp. 111–131. Springer. https://doi.org/10.1007/978-3-030-90567-5_6 (2021)
Sun, L., Wang, W., Wang, M.: Automatic search of bit-based division property for ARX ciphers and word-based division property. In: Takagi, T., Peyrin, T. (eds.) ASIACRYPT 2017, Part I. LNCS, vol. 10624, pp. 128–157. Springer. https://doi.org/10.1007/978-3-319-70694-8_5 (2017)
Han, Y., Li, Y., Wang, M.: Automatical method for searching integrals of ARX block cipher with division property using three subsets. In: Naccache, D., Xu, S., Qing, S., Samarati, P., Blanc, G., Lu, R., Zhang, Z., Meddahi, A. (eds.) ICICS 18. LNCS, vol. 11149, pp. 647–663. Springer. https://doi.org/10.1007/978-3-030-01950-1_38 (2018)
Eskandari, Z., Kidmose, A. B., Kölbl, S., Tiessen, T.: Finding integral distinguishers with ease. In: Cid, C., Jacobson Jr:, M.J. (eds.) SAC 2018. LNCS, vol. 11349, pp. 115–138. Springer. https://doi.org/10.1007/978-3-030-10970-7_6 (2019)
Hu, K., Wang, M.: Automatic search for a variant of division property using three subsets. In: Matsui, M. (ed.) CT-RSA 2019. LNCS, vol. 11405, pp. 412–432. Springer. https://doi.org/10.1007/978-3-030-12612-4_21 (2019)
Ghosh, S., Dunkelman, O.: Automatic search for bit-based division property. In: LATINCRYPT. lecture notes in computer science, Vol. 12912, pp. 254–274. Springer (2021)
Acknowledgements
The authors thank Claude Carlet for proposing the idea of this survey and the anonymous reviewers for their valuable suggestions which helped to greatly improve this work. The work was supported by the Luxembourg National Research Fund’s (FNR) and the German Research Foundation’s (DFG) joint project APLICA (C19/IS/13641232).
Funding
The work was supported by the Luxembourg National Research Fund’s (FNR) and the German Research Foundation’s (DFG) joint project APLICA (C19/IS/13641232).
Author information
Authors and Affiliations
Contributions
Phil Hebborn wrote Section 6 and part of Section 3. Gregor Leander wrote Section 1, Section 7 and parts of Section 2 and Section 3. Aleksei Udovenko wrote Section 4, Section 5 and parts of Section 2 and Section 3. Gregor Leander and Aleksei Udovenko edited the final manuscript.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
This work raises no ethical concerns.
Consent for Publication
All authors give consent for publication of this work.
Competing interests
The authors have no relevant financial or non-financial interests to disclose.
Availability of supporting data
This work has no supporting data.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Hebborn, P., Leander, G. & Udovenko, A. Mathematical aspects of division property. Cryptogr. Commun. 15, 731–774 (2023). https://doi.org/10.1007/s12095-022-00622-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12095-022-00622-2



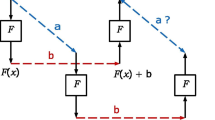


 (as a function), its ANF is empty and so must be the parity set (by Proposition 1).
(as a function), its ANF is empty and so must be the parity set (by Proposition 1).


