Abstract
Cognitive radio (CR) is a promising solution to cope with the inefficient usage of the frequency spectrum. CR lets its users leverage empty or idle parts of spectrum opportunistically. The medium access control (MAC) sub-layer in CR based networks is playing a crucial role in controlling user’s access to the shared medium and their interaction with Primary Users as well. Coordination and controlling users’ access to common control channel (CCC) at MAC sublayer can be a challenging issue in this type of networks. High availability of this channel is very important and crucial, so designing a mechanism which contributes to this, is of great importance. The CCC’s limited capacity alongside a large number of contending nodes for it causes channel saturation and consequently, leads to its unavailability. The paper introduces a useful method to compute supported saturation capacity of the CCC. It also introduces a new access mode for CCC called “Channelization”, to improve saturation capacity for it. The effect of “Channelization” scheme is also investigated on average packet delay, and according to it desirable parameters for channelization is calculated. Analytical analysis alongside simulation result shows that the channelization method can have a great impact on the increasing saturation capacity, and lower average packet transmission delay.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Today the spectrum allocation task is done by governmental agencies. They provide users with fixed frequency bands they are required, as well as required licensees. Most of the allocated frequency band is used occasionally, and rarely [1]. Although this method of spectrum allocation was a proper method in the past, nowadays increasing number of users and inappropriate usage of spectrum, implies developing new methods for spectrum allocation, which agitates researchers to use efficient ways of spectrum usage [2].
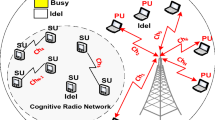
There are two user categories in cognitive radio (CR) networks: Primary Users (PUs) and Secondary Users (SUs) [1]. PUs are traditional users of licensed spectrum, but SUs are users who are trying to use idle spectrum by exploiting cognitive capabilities. CR networks are working based on spectrum sharing among PUs and SUs. An SU as soon as a PU appears must release and leave the channel or continue its activity aside PU as long as the interference level on the PU does not exceed the predefined threshold value [3]. MAC layer of these kinds of networks plays an important role. Alongside its usual task, it is responsible for determining the suitable channel using spectrum sensing results from the physical layer, further it might help network layer to find the best route by sending channels’ information to it. For coordination and negotiation purposes, it is essential for CR users to be able to exchange some messages. This task is carried out by MAC sublayer, and MAC uses common control channel to do so. The CCC facilitates processes of Sender/Receiver handshaking, adjacent node discovery, routeing information update, and updating topology change information, which is needed by users for working together correctly [3,4,5,6]. Therefore, designing a highly available CCC channel which is also reliable, could be very critical.
The CCC could be converted to network bottleneck if the number of users contending for it becomes very large. As a result of exceeding requests for channel acquisition, the channel will be saturated very soon. The CCC saturation issue causes inefficient usage of CR potentials since users should wait for a long time in channel allocation queue to get access to CCC, and negotiate over it, and then transmitted over a different agreed channel.
Few methods to cope with CCC saturation issue is proposed. In [7, 8] authors proposed a method in which they use a free available channel as the control channel. Their methods suffer from two main deficiencies. The first problem is that the control channel should be released if a primary user appeared, for this reason, selected channel should be a channel which is less used by PUs to ensure us that channel usage undergoes less interruption. Finding such a channel is not an easy task. Second, because of heterogeneous network channels, choosing an individual channel as a control channel for all the network is almost impossible. Other sources in literature like [9,10,11,12] assign a dedicated control channel to each network user. An available and network-wide CCC can be used for message broadcasting and peer to peer connectivity by CR users. In [13] three techniques for attacking saturation problem is introduced. (1) Limiting traffic load over the common control channel, (2) adjusting bandwidth rate considering data bands, and (3) control channel relocation taking into account traffic load. The first technique, as stated, depends on the traffic which is imposed by upper layers. For example, traffic load over the control channel in cooperative sensing depends on local sensing data quantization, and also the number of times these data are transmitted. The second one, adapting bandwidth rate is not always feasible, because typically, control channel’s bandwidth is assigned previously, and it is as much as a DATA channel bandwidth. Last technique is moving control channel to a better channel in the hope of getting a better quality and bandwidth efficiency, which is used in occasions that there is not a separate channel for a common control channel.
In [7, 14] to overcome control channel saturation issue, the CCC is eliminated. This means that the coordination is carried out by using adjacent channels’ seeking mechanisms. In [15] authors use a support-vector-machine (SVM)-based learning technique could build such a dependency from the CCC one very high performance. However, these protocols suffer from severe deficiencies at the time of message broadcasting.
2 The Proposed Method
In some random medium access methods, each user often waits for a random time and then commence its transmission. This waiting time before transmission lowers the collision rate and increases the performance. Our method by decreasing the amount of wasted time -waiting time for each user which is imposed by random access methods- leads to support more users in the network at the saturation point of CCC. In [16] we calculated a “saturation capacity” parameter for the CCC which is the number of negotiations that can be handled in a particular time using CCC. In this paper, we further developed it and used it to establish “Channelization” method. We use “saturation capacity” parameter to prove that our newly proposed scheme “Channelization”, increases the saturation capacity of the CCC, and it also can be helpful to decreases the overall delay of transmissions for each packet.
Channelization of common control channel can be done by dividing CCC’s frequency spectrum to a number of “sub-channels” with equal length. The users contending for CCC should also be divided into some groups with equal members. Members of each group are permitted to access their assigned sub-channel only. In other words, the amount of traffic which is transmitted over each subchannel should be as much as a value that enforces an equal number of contending users for each sub-channel. The number of sub-channels can be determined using a parameter called “Channelization Number” (Channelization number will be computed later in this paper). Moreover transmitting user for sake of choosing the correct frequency for data transmission, should be aware of the channel in which receiver is working.
The mentioned assumptions for dividing users equally, and also being aware of some details regarded to each sub-channel could be really challenging. But these tasks could be done readily by upper network layers. At this point, we should point out detecting saturation point, selecting a sub-channel, and informing other users about it is not something impossible. For example, we can allocate sub-channels statically, before reaching saturation point to enable users to use them after detecting the saturation point. Having a discussion about needed coordination for above situations is out of the scope of this work and we leave it here for future works. We assume an ideal condition in which our presumptions are factual.
Our intended CCC is a network wide dedicated channel, and it is always available. This channel is a licensed channel, thus its bandwidth is as much as a typical data channel which has a bandwidth of \(bw_{C}\) and carrier frequency of \(f_{C}\). If we divide common control channel to k sub-channels, we will have k sub-channels with a bandwidth of \(bw_{C} /k\) for each. The minimum amount of bandwidth for a given sub-channel is \(b_{0}\). \(b_{0}\) depends on practical constraints on subchannels bandwidth in action, and it is equal to least allowed bandwidth, in which radio can work correctly. Therefore k (number of sub-channels) must be less than or equal to \(bw_{C} /b_{0}\).
2.1 Assumptions a MAC Layer Architecture
The first assumption is that each node has a half-duplex receiver/transmitter. This means that it only can be either in the state of transmitting or receiving. This assumption is very common, and it is recommended for most of MAC protocols. In addition, radio is capable of working in different carrier frequencies or it can simply adapt its filters based on different frequency bands. This assumption demands dynamic cognitive switching which is typical for CR devices. Channel condition is presumed to be ideal, and a number of users contending for CCC are constant. Finally, each user always has a packet to be sent, in other words, the transmission queue will not be empty anytime. By the way, we are focused on a MAC protocol design in which each node can realise the presence of a PU confidently.
Two SUs must meet each other in the negotiation phase before the beginning of data exchange. The negotiation phase is carried out on the control channel by exchanging RTS/CTS packets. The sender puts some information like its accessible channels into an RTS packet and sends it to the receiver. On the other side receiver after successfully receiving an RTS chooses a suitable channel and puts its information into a CTS packet and sends back it to the sender.
As it is apparent from Fig. 1 users start exchanging DATA in Transmission Interval (TI) on agreed channel right after the negotiation phase. The duration of the Transmission Interval or TI should be such an amount that if during that time a PU related to that channel appeared, it could tolerate the possible interference error. As illustrated in Fig. 1 T neg stands for negotiation duration, and transmission interval is indicated by TI. RTS/CTS exchange is according to IEEE_802.11 DCF.
2.2 Calculating Common Control Channel Saturation Capacity
In this section, we are going to give a review on how to calculate saturation capacity for CCC based on our previous work [16].
T neg is the average negotiation time for SUs under the CCC. There are M primary channels. The maximum contending nodes that can acquire the CCC during TI is N. Therefore N = |TI/Tneg| is valid. It should be mentioned that a maximum of N SUs can opportunistically transmit over permitted channels simultaneously. As mentioned before, each user always has a packet to send, after each successful transmission, at every moment. Meanwhile the number of contending nodes for the CCC is constant, so negotiation time can be computed considering these assumptions, and finally, N could be derived.
Figure 2 shows a saturated CCC using an example. In this figure number of DATA channels is 7. A to K packets which are transmitted over the CCC are the negotiation packets that their transmission length is Tneg. After exchanging negotiation packets, an agreement on a channel should be made, and data exchange starts. For example, the successful transmission of packet A over the CCC is an indication of beginning data exchange phase (The first transmitted packet in Fig. 2.). In Fig. 2 we tried to utilise the maximum channel capacity (performance) based on priority, from lower to higher order, to have a better demonstration of ideal channels.
This visual demonstration is a proof for inefficient usage of network resources at saturation point.
What this figure tries to show is that if there are some idle channels, the transmission will happen on the channel with a lower number. Thus in the demonstration, after packet F’s transmission over CCC, channel 1 is selected again to carry packet transmission, since the idle channel with the lower number is the channel 1.
Meanwhile, during packet E’s transmission, channel 1 is not idle as users are negotiating over E, therefore it cannot be used after E’s transmission.
It is clear that if the length of the negotiation time is reduced, more DATA exchange can happen over channels, and thus channels’ utilisation will increase. Figure 2 is an interesting proof, which indicates how CCC can turn into network bottleneck and causes a poor performance by forcing us to use network resources inefficiently.
Now by comparing T neg and M (number of channels), we can realise whether CCC is saturated or not. In other words, if the number of available channels is greater than N this means that there are some channels which are not used, that would be interpreted as channel saturation point or network bottleneck.
-
Calculating the negotiation duration
In our method, the access method to the CCC is based on the IEEE_802.11 standard. For every pair of the sender/receiver in each transmission interval (TI), only two RTS/CTS packets are transmitted. If a user has no packet to send just listens to the channel, and upon reception of a packet destined to it, it will respond according to the request.
Negotiation interval duration is same as the time required to successfully transmit an RTS packet and successfully receiving a CTS packet for it. In [17] the needed time for transmitting a packet based on IEEE 802.11 standard is computed analytically. If we replace DATA/ACK with RTS/CTS respectively, then we can use formulas in [17] to calculate negotiation duration. For this reason, we alter the formula in [17] a little but keep the access mechanism intact.
According to the Fig. 3, a successful transmission time (\(T_{S}\)), and wasted time because of collision occurrence (\(T_{c}\)) are computed using below equations:
where Rc is channel bitrate, LRTC and LCTS are RTS and CTS packets length respectively, TSIFS and TDIFS are SIFS and DIFS time intervals. Now we can calculate the time duration that is spent on negotiation period using RTS/CTS mechanism leveraging below formula [17].
where σ is the duration of an empty slot time. Of course, the values Ts, Tc and σ must be expressed with the same unit. Ptr is the probability of having at least one transmission over the channel in a given timeslot which is equal to \(1 - (1 - \tau )^{n}\). Moreover, Ps is the probability of a successful transmission over the channel which is equal to \(n\tau (1 - \tau )^{n - 1} /1 - (1 - \tau )^{n}\) in which n is the number of contending nodes for winning CCC, and \(\tau\) is the probability of a user transmission in a random timeslot which is equal to:
In Eq. 4 number of backoff periods is shown by m, and W is the minimum window size.
-
DATA transmission interval
While an SU is transmitting it is possible that the PU associated with that channel comes back, but since SU is transmitting, it cannot sense the spectrum, therefore it cannot be aware of PU’s return, and thus continues its transmission. PUs can endure interference to some extent, so we can exploit this tolerance, and determine the length of transmission interval (TI).
We can assume two working modes for a channel: ON and OFF. The ON mode is analogous to channel busy state, and the OFF mode is analogous to channel idle state. PUs alternatively seize their corresponding channel and release it, so we can model their behaviour as a pattern which is depicted in Fig. 4. This figure illustrates random presence and absence of PUs in m channels.
PUs activities are considered as intervals with exponential distribution [18], so ON and OFF modes occurrences for each channel, have exponential distribution statistically. TOn,i, TOff,i respectively are average time, for being in either ON or OFF states for ith channel. Meanwhile the TOn,i, TOff,i are statistically independent.
Now considering PUs presence and absence periods, we can deliver a limit for TI, and we can use it to compute saturation capacity for CCC. As stated before TI is the transmission interval for a SU after negotiation phase. Considering the fact that radio is half-duplex, SU cannot sense the channel that is transmitting over it right now. The probability for a PU’s presence exactly t seconds after depletion of the associated channel, could be calculated using cumulative distribution function (CDF) for the exponential distribution which is given in (6-1). The mean for this distribution is \(1/T_{Off}\). In other words, the probability of collision between an SU and a PU during t is equal to \(1 - e^{{ - t/T_{Off} }}\) There is a predefined limit, for interference probability. This means that by knowing \(I_{th}\), we can calculate the transmission time over a channel using its statistical distribution, in a way that the interference probability for that channel does not exceed \(I_{th}\). Thus according to \(I_{th}\) we can calculate permitted TI for each channel which is TI = Toff ln [1/(1 − Ith)]. This Equation delivers the maximum permitted transmission interval, given that the probability of interference with PU will not exceed \(I_{th}\).
2.3 Improving Saturation Capacity Using Channelization Method
For proving performance improvement using Channelization method. First, we should review the CCC acquisition procedure. The negotiation phase can be looked at as a double phase procedure, a random back-off time and RTS/CTS exchange. These phases are repeated periodically. Negotiation duration can be calculated using. Using the Channelization method (with Channelization number k), the negotiation duration will be equal to \(T_{Back\_Off}^{k} + T_{RTS\_CTS}^{k}\). If we prove that the time needed to carry out k negotiations over a channel lasts more than carrying out k negotiations over k channels, then Channelization method’s superiority over traditional channel acquisition method will be proved.
So we should prove Eq. (5):
Considering the fact that the channel bitrate for the CCC is divided by k (using Channelization, with Channelization number, k), thus we can write \(T_{RTS\_CTS}^{k} = K \cdot T_{RTS\_CTS}^{1}\) with a good approximation. By changing Eq. (5) we can write the following equation:
Equation (7) can be easily extracted for Eq. (6); so, we should prove Eq. (7). It is clear that lowering the number of users leads to less contention over the channel and as a result lesser back-off time for each user which is also proved in [19]. So \(T_{Back\_Off}^{k} < T_{Back\_Off}^{1}\) has Eq. (7) inside it, therefore Eq. (5) is proved.
For example, consider Fig. 5. In this figure, the back-off time and the RTS/CTS transmission time is depicted for control channel without Channelization, and also with Channelization with 3 sub-channels. It is evident that using 3 sub-channels decreased the negotiation time for 3 users.
3 Proposed Method Evaluation and Results Discussion
We want to evaluate the system in CCC’s saturation state. We assume nodes always have a packet to be transmitted. To verify analytical results we use NS-2 network simulator. By default NS-2 does not support CR concepts, so we used helpful codes and information provided by [20, p. 2] to develop simulation environment.
To configure simulation environment we applied NOAH routeing method. Based on NOAH, MAC is involved in same connections which are defined in preliminary TCL configurations. The usage method is described in [21]; meanwhile, it is assumed that nodes are in each other’s range. Used MAC protocol is IEEE_802.11, and other configuration settings are illustrated in Table 1.
First, we evaluate the effectiveness of the proposed method. For this reason, we compare the saturation threshold of the CCC for different Channelization Numbers. So, Fig. 6 shows TI/Tneg according to the number of contending users. As it is clear from Fig. 6, in fact, the ratio of TI/Tneg indicates the number of coordination intervals during a transmission interval or TI. In other words, this ratio indicates the maximum number of users that have been negotiating with each other during TI intervals. As stated before the maximum number of contending users that can acquire channel during TI is N.
To clarify the subject, consider 30 contending nodes for the CCC -without any sub-channels and 2 Mbps bitrate. As can be seen in Fig. 6, the roundup of the saturation capacity is equal to 32. Now we increase the number of subchannels to 2, since we divided the CCC to 2 sub-channels, each sub-channel has a bit rate of 1 Mbps, and underlying users for each sub-channel is 15 users. Considering Fig. 6, during Transmission Interval (TI), 19 users have the coordination chance over 2 depicted parallel sub-channels. So comparing both methods of channel allocation, we will find that by using a single channel, saturation capacity will be 32, and by extending number of channels to 2 sub-channels, we will achieve an increment of 6 users in saturation capacity (19 * 2 = 38). We can simply see that for 3 sub-channels, the number of contending users will be (14 * 3) 42 users, and for 5 sub-channels they will be (9 * 5) 45 users.
The simulation results also approve mentioned numbers which are somehow near to what we obtain analytically. So, we present the results of the mentioned example for both simulation and analytical results in Table 2. These examples prove the effectiveness of the method clearly (Fig. 7).
Authors in [9,10,11,12] introduced MAC protocols using similar CCC access methods, including negotiation and transmission phases with minor differences. Our method also uses negotiation and transmission phases, but in our scheme users are contending for sub-channels of the CCC instead of the whole CCC, therefore if we reduce our sub-channels to one, then our method’s implementation and performance will be very similar to these proposals.
3.1 Average Transmission Delay for a packet, and Best Channelization Number
The Channelization method increases saturation capacity by incrementing channelization number, but is there any limitation for the number of sub-channels? and using channelization method, how much improvement can be achieved in term of packet transmission delay? By transmission delay we mean the time interval in which packet is ready to be transmitted from the MAC sub-layer queue, plus the time it takes to reach its destination. Figure 8 shows average transmission delay in different sub-channels considering the number of users.
Increasing channelization number has a two-fold effect. By reducing contention among users, their access time to the CCC decreases. On the other hand, transmission’s speed for each user decreases, because bitrate for each sub-channel is reduced as the number of sub-channels increases, and therefore users demand more time to transmit their data. Consequently, the possession time for each user will become longer. This implies that increasing number of sub-channels may not always increase the performance in term of packet delay, so we are encouraged to calculate a channelization number that guarantees minimum delay for each packet transmission.
Average transmission delay for a packet is calculated in [22]. This delay is composed of packet queuing delay at MAC sublayer and the time needed for a packet to reach its destination.
Equation (8) delivers expected packet transmission delay. Since in our method channel is divided to k sub-channels, we should change Eq. (8) in a way that it takes into account n/k users for each sub-channel as well as the bitrate of \(R_{C} /k\) for each sub-channel. For this reason, we should first change previously used formulas to recalculate τ, p, ptr, Ts, and Tc. By replacing these newly calculated values in Eq. (8), channelization method’s delay can be computed which will be indicated by E[Dk]. Now improvement ratio for packet delay related to different channelization numbers is computable using (E[D] − E[Dk])/E[D].
Figure 9 shows the improvement ratio of delay using proposed method regarded to different channelization numbers and different bitrates. Considering the above equation it is evident that as the mentioned ratio gets larger, packet transmission delay under that channelization scenario gets lower. According to the Fig. 9, using channelization method for a CCC with 200 and 400 Kbps bitrates worsen the packet transmission delay, and packet’s delay grows further. However, for higher channel bitrates improvement is significant.
The important issue is that how much channelization is optimum? The answer strictly depends on channel bit rate, and the number of subchannels, for example in Fig. 9 by having a 2 Mbps channel, at channelization number equal to 5 we have the maximum gain for depicted curve, and transmission delay is decreased by 4.73% for given scenario. In this scenario having more than 5 sub-channels does not help in improving packet transmission delay, therefore it can be said that there is no global optimum value for channelization number, however each scenario may have a local optimum value, wherein our settings it is 5.
4 Conclusion
In this paper, we investigated different challenges related to access mechanisms for a common control channel in cognitive radio networks. We showed that common control channel may be converted to network bottleneck if common control channel saturation happens. We calculated saturation capacity for the common control channel and then increased it by proposing channelization scheme. We showed by mean of analytical analysis and network simulation that our common control channel access method can lower packet transmission delay when applied to MAC sub-layer of cognitive radio networks.
References
Zhao, Q., & Swami, A. (2007) A survey of dynamic spectrum access: Signal processing and networking perspectives. In Acoustics, speech and signal processing, 2007. ICASSP 2007. IEEE international conference on (Vol. 4, pp. IV–1349).
Mitola, J., & Maguire, G. Q. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6(4), 13–18.
Akyildiz, I. F., Lee, W.-Y., Vuran, M. C., & Mohanty, S. (2006). NeXt generation/dynamic spectrum access/cognitive radio wireless networks: A survey. Computer Networks, 50(13), 2127–2159.
Akyildiz, I. F., Lee, W.-Y., & Chowdhury, K. R. (2009). CRAHNs: Cognitive radio ad hoc networks. Ad Hoc Networks, 7(5), 810–836.
Lo, B. F., Akyildiz, I. F., & Al-Dhelaan, A. M. (2010). Efficient recovery control channel design in cognitive radio ad hoc networks. IEEE Transactions on Vehicular Technology, 59(9), 4513–4526.
Akyildiz, I. F., Lo, B. F., & Balakrishnan, R. (2011). Cooperative spectrum sensing in cognitive radio networks: A survey. Physical Communications, 4(1), 40–62.
Kondareddy, Y. R., Agrawal, P., & Sivalingam, K. (2008). Cognitive radio network setup without a common control channel. In IEEE military communications conference, 2008. MILCOM 2008 (pp. 1–6).
Su, H., & Zhang, X. (2007). Cognitive radio based multi-channel MAC protocols for wireless ad hoc networks. In IEEE global telecommunications conference, 2007. GLOBECOM’07 (pp. 4857–4861).
Jia, J., Zhang, Q., & Shen, X. (2008). HC-MAC: A hardware-constrained cognitive MAC for efficient spectrum management. IEEE Journal on Selected Areas in Communications, 26(1), 106–117.
Cordeiro, C., & Challapali, K. (2007). C-MAC: A cognitive MAC protocol for multi-channel wireless networks. In 2nd IEEE international symposium on new frontiers in dynamic spectrum access networks, 2007. DySPAN 2007 (pp. 147–157).
Le, L., & Hossain, E. (2008). A MAC protocol for opportunistic spectrum access in cognitive radio networks. In IEEE wireless communications and networking conference, 2008. WCNC 2008 (pp. 1426–1430).
Zhang, X., & Su, H. (2011). CREAM-MAC: Cognitive radio-enabled multi-channel MAC protocol over dynamic spectrum access networks. IEEE Journal of Selected Topics in Signal Processing, 5(1), 110–123.
Ma, L., Han, X., & Shen, C.-C. (2005). Dynamic open spectrum sharing MAC protocol for wireless ad hoc networks. In 2005 first IEEE international symposium on new frontiers in dynamic spectrum access networks, 2005. DySPAN 2005 (pp. 203–213).
Kondareddy, Y. R., & Agrawal, P. (2008). Synchronized MAC protocol for multi-hop cognitive radio networks. In IEEE international conference on communications, 2008. ICC’08 (pp. 3198–3202).
Thilina, K. G. M., Hossain, E., & Kim, D. I. (2016). DCCC-MAC: A dynamic common-control-channel-based MAC protocol for cellular cognitive radio networks. IEEE Transactions on Vehicular Technology, 65(5), 3597–3613.
Nezhadal, S. M. M., Berangi, R., & Fathy, M. (2012). Common control channel saturation detection and enhancement in cognitive radio networks. International Journal of Distributed and Parallel Systems, 3(1), 15.
Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications, 18(3), 535–547.
Lee, W.-Y., & Akyildiz, I. F. (2008). Optimal spectrum sensing framework for cognitive radio networks. IEEE Transactions on Wireless Communications, 7(10), 3845–3857.
Tay, Y. C., & Chua, K. C. (2001). A capacity analysis for the IEEE 802.11 MAC protocol. Wireless Networks, 7(2), 159–171.
Calvo, R. A., & Campo, J. P. (2007). Adding multiple interface support in NS-2. University of Cantabria.
Borriello, D. (2005). [ns] Problem with protocol NOAH for static multihop. 09 Dec 2005.
Chatzimisios, P., Boucouvalas, A. C., & Vitsas, V. (2003). Packet delay analysis of IEEE 802.11 MAC protocol. Electronics Letters, 39(18), 1358.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
MirhoseiniNejad, S., Beragi, R. & Asadi, A. Improving Common Control Channel Capacity and Performance for Cognitive Radio Networks. Wireless Pers Commun 98, 2521–2534 (2018). https://doi.org/10.1007/s11277-017-4987-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4987-4