Abstract
Mobile ad hoc networks (MANETs) are dynamically configurable wireless networks that have no fixed infrastructures and do not require predefined configurations. In MANETs, the high mobility of the mobile nodes is a major reason for link failure. Based on ad hoc on-demand distance vector (AODV), we propose a fuzzy-based on-demand routing protocol (FBORP) for MANETs. The proposed scheme uses the fuzzy logic system to select a stable route to enhance system performance. The fuzzy logic system is based on the remained energies of the nodes on the routes, the bandwidth and the node mobility. This study also compares the performance of the FBORP protocol with the well-known AODV protocol. Simulation results show that the proposed FBORP outperforms AODV, especially in a high mobility environment.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The implementation of MANETs is steadily increasing. MANETs are especially popular in locations that lack a fixed communication infrastructure [1]. MANET is a self-organizing and self-configuring multi-hop wireless network. The nodes in MANET move randomly, resulting in rapid and unpredictable changes in network topology. Additionally, because of limited transmission range of mobile nodes in a MANET, some nodes cannot communicate directly with each other. Mobile nodes act not only as a host but also as a router to maintain routes to destination and forwards data packets for other nodes also in the network [2].
The performance of MANETs is related to efficiency of routing protocols and efficiency depends on several factors like convergence time after topology changes, bandwidth overhead to enable proper routing, power consumption [3]. Many routing protocols have been proposed in accordance with different network structures, mobility scenarios and types of applications. While developing a routing algorithm for MANETs, one of the most challenging peculiarities which developers must consider is the behavior of the proposed algorithm in the presence of node movement. Mobility has a potential to result in dynamic changes to network topology, making the task of routing algorithms more difficult [4]. The routing protocols in MANETs should cope well with dynamically changing topology and nodes should exchange information on the topology of the network in order to establish routes. Routing in ad hoc networks is challenging and several routing protocols have been proposed [5–7]. Hop count is the most commonly used metric when selecting a route from a source to a destination. However, the hop count metric may perform poorly in networks because a route with a minimum hop count may include slow or lossy links, leading to poor end-to-end throughput.
In general, MANET routing protocols can be divided into two classes: table-driven routing protocols and on-demand routing protocols. In table-driven routing protocols, every node continuously maintains the complete routing information of a network. When a node needs to forward a packet, a route is readily available. On-demand routing protocols are different in that they only look for routes when mobile nodes need to pass on information; thus, they reduce much of the load required when routes are sought [6]. On demand routing protocol provides a scalable and cost-effective solution for packet routing in wireless ad hoc networks. In order to facilitate communication within the network, a routing protocol is used to discover routes between nodes [8].
Several protocols that vary in performance and complexity have been developed for MANET. Dynamic source routing (DSR) is a well-known pure on-demand protocol. It is a simple protocol, but does not always select the optimal route to send a packet. The ad hoc on-demand distance vector (AODV), like DSR, is a well-known wireless ad hoc network protocol. It is based on the destination sequenced distance vector (DSDV) protocol. DSDV maintains a complete list of routes and announces every change concerning the network connectivity [7].
Concerning the routing, various protocols have been proposed for ad hoc networks. You et al. [9] proposed a hop count based heuristic routing protocol by utilizing the information carried by the peripatetic packets in the network. In those studies, heuristic function is defined to help in making the routing decision. Kanakaris et al. [10] evaluated four ad-hoc network protocols (AODV, DSDV, DSR and TORA) in different network scales taking into consideration the mobility factor. Vu et al. [11] proposed a mobility-assisted on-demand routing algorithm for mobile ad hoc networks in the presence of location errors. Their proposed mobility prediction is robust to the location errors. Sivakumar et al. [12] suggested a machine learning based hybrid power-aware approach for handling critical nodes via load balancing. Xia et al. [13] proposed on-demand trust-based unicast routing protocol for MANETs, to provide a flexible and feasible approach to choose the shortest route that meets the security requirement of data packets transmission. Moussaoui et al. proposed a new mechanism to establish stable and sustainable paths between all pairs of nodes in a mobile ad hoc network. They applied this mechanism on the OLSR protocol (optimized link state routing protocol) to elect stable and sustainable multipoint relays nodes and topology [14]. Kumar et al. [15] proposed energy management model and power consumption control flow chart is proposed to control power consumption by reducing data transmit time in mobile ad-hoc network. In paper [16] various energy accuracy scheme is introduce that works on reducing waste full energy consumption and increases data transmission and life of network.
As for the studies involving fuzzy logic, Sheng [17] proposed an adaptive routing algorithm in which the link cost was dynamically assigned using a fuzzy system. Their results show the traffic in the network is rerouted to have less congestion or spare capacity. Budyal et al. [18] proposed an adaptive neuro-fuzzy inference system based multiple QoS constrained any cast routing in MANETs by using a set of static and mobile agents. Yuanzhou et al. proposed an improved method of AODV routing protocol with fuzzy control theory and random early detection ideas. Their results show that the modified protocol reduces the average delay, routing load and packet loss rate while increasing the data forwarding capacity of nodes [19]. Goswami et al. proposed a novel fuzzy stochastic routing protocol for MANETs. In the proposed algorithm multiple metrics such as hop count, battery power, and signal strength are considered using fuzzy logic to give multiple optimal paths [20].
In this paper proposes a fuzzy-based on-demand routing protocol (FBORP) to enhance the stability of a network. The proposed scheme uses fuzzy logic system to select a stable route to enhance system performance.
Fuzzy logic was chosen due to the uncertainty associated with node mobility estimation and to the non-linearity and lack of mathematical models capable of estimating this mobility. A fuzzy sets definition (membership functions) and a set of rules (rule-base) have been proposed to design the new protocol. This paper describes work related to and the details of the proposed fuzzy-based on-demand routing protocol. A discussion of the simulation results and conclusions follow.
2 Related Work
AODV protocol [21] is an on-demand routing protocol that uses a broadcast route discovery mechanism and relies on dynamically established routing table entries at intermediate nodes. The functions performed by AODV include local connectivity management, route discovery, route table management and path maintenance. Local connectivity management may be summarized as follows: Nodes learn about their neighbors by either receiving or sending broadcast packets from or to their neighbors. Receiving the broadcast or HELLO from a new neighbor or failing to receive HELLO packets from a node that was previously in the neighborhood indicates that the local connectivity has changed. The source node initiates path discovery by broadcasting a route request packet (RREQ) to its neighbors. When a node receives an RREQ and has routing information, it sends a reply packet (RREP) back to the destination.
If it does not have routing information, it rebroadcasts the RREQ further to its neighbors. As the RREQ travels from source to destination, it automatically sets up the reverse path for all nodes back to the source. As the RREP travels back to the source, each node along the path sets up a forward pointer to the node from which the RREP came and updates its timeout information for route entries to the source and destination. For each destination of interest, a node maintains a single route table entry that contains the address of the destination, the next hop along the path to that destination, the number of hops to the destination, and other route related parameters. If a node is presented with two different routes to the destination, it chooses the fresher route. If both routes were discovered simultaneously, the route with fewer hops is preferred. Path maintenance is performed in several ways. When any node along an established path moves so that some of the nodes become unreachable, a special RREP is sent to the affected source nodes. Upon receiving notification indicating a broken link, the source node restarts the path discovery process, if it still needs that route.
3 Fuzzy-Based on-Demand Routing Protocol
In this section, the concept and rules for FBORP that will be used with AODV are introduced and the method to design its membership functions is presented. The goal is to improve the routing quality of MANETs using the information available and to increase the quality of path finding in the MANET networks using data accessible in the network. Choosing a stable path decreases the overhead and the number of hops in path finding and optimizes use of powerful and energetic paths.
3.1 Effect of Power of Battery on Link Stability
Power of battery is an evaluation criterion for link stability. We use the power remaining as the parameter to describe the power condition of an arbitrary node i. We denote the power remaining as \( P_{remi} \). The value of \( P_{remi} \) is evaluated with a very simple method as below:
where, \( P_{av} \) is the available energy of node, \( P_{rt} \) is the required transmit power of a data message of b-bits between two nodes by a transmission range of d meters.
The value of \( P_{rt} \) is evaluated with formula (2):
where, \( \varepsilon_{fs} = 10\,{\text{PJ}}/{\text{bit}}/{\text{m}}^{2} \) is the energy consumed in free space at the output transmitter antenna for transmitting one meter and \( {\text{P}}_{\text{elec}} = 50\,{\text{nJ}}/{\text{bits}} \) is the energy expended in the radio electronics [22].
The lifetime of the route has relationship with the minimum \( P_{remi} \) for all nodes in the path. That is, if the energy of any node in the path is exhausted, then the path would crashes. Thus, \( P_{remi} \) represents the power remaining of the node \( i \), therefore, the lifetime of the route is related to \( {\text{min }}P_{remi} \), that is:
If the power is low, the probability of the link broken will be high. Thus, the rules for the relationship between power and link stability should be as follows:
-
P1: If power is high then link stability must be high.
-
P2: If power is medium then link stability must be medium.
-
P3: If power is low then link stability must be low.
The power remaining value is expressed with dimensionless index within [0, 1].
3.2 Effect of Bandwidth on Link Stability
In addition, the bandwidth characteristic can also be considered as an evaluation criterion. We use the available bandwidth between two adjacent nodes, to describe the bandwidth condition. A simple method gives the available bandwidth based on transmission speed and can be used to measure the bandwidth for an (I, J) link. This link has an available bandwidth of:
where u is the link utilization (u = A(t)/t; A(t) is the total amount of time in which the link is used by nodes during an interval of time t. The link stability has relationship with the minimum Available bandwidth for all nodes in the path, when the route is congested, the shared bandwidth of channels would be reduced, so that the route became unstable due to the retransmission of the lost packets. That is, if the Available bandwidth of any node in the path is reduced, then the path would crashes, therefore, the lifetime of the route is related to min Available bandwidth, for all nodes in the path.
If the Available bandwidth is low, the probability of the link broken will be high. The rules for the relationship between Available bandwidth and link stability are
-
B1: If Available bandwidth is high then link stability must be high.
-
B2: If Available bandwidth is low then link stability must be low.
3.3 Effect of Node Mobility on Link Stability
MANETs experience dynamic changes in network topology because of the unrestricted mobility of the nodes in the network. If the end nodes experience much movement, then it is highly probable that their path will break. The node movement can be measured by the number of sent control packets between two sampling intervals. Sent control packet is any message of the following type: RREQ, RREP, RERR and RREP_ACK.
If the RREP packet records the number of sending control packet of the intermediate nodes is high, it represents the route is probably unstable. So, high number of these packets means high probability to loose some of its current links or packets [23]. In general, a rule can be defined: When sent control packet is high, the link stability must be low and vice versa. Consequently the following fuzzy rules are proposed:
-
S1: If sent control packet is high then link stability must be low.
-
S2: If sent control packet is medium then link stability must be medium.
-
S3: If sent control packet is low then link stability must be high.
The sent control packet value is expressed with dimensionless index within [0, 1].
In general, the link stability is an inverse ratio sent control packet.
Contrarily to the relationships between sent control packet and link stability, the link stability is a direct ratio to the power remaining and available bandwidth. The membership function for send control packet criterion should be considered as the dimensionless index [0, 1]. Based on this concept, the reverse sent control packet is defined as Rsent control packet = (1 _ sent control packet).
The membership functions for the rating values of sent control packet and Rsent control packet are respectively expressed by the two equations as below:
The converted sent control packet rating is combined with the former two rating criteria (Available bandwidth and power) to form a set of alternate route ratings. These three ratings are to be weighted to obtain the final rating.
In general, to prevent any extreme value after transformation, a practical value that is far below or far above its corresponding boundary value should be assigned as a very low rating or a very high rating.
The eight previous rules can be combined with one 3-dimensional rule-base for controlling the link stability adaptively as represented in Table 1. These ‘if–then’ rules statements were used to formulate the conditional statements that comprise fuzzy logic. The inputs to ‘if–then’ rules are the numerical values for the input variables (in this case, sent control packet, power remaining and available bandwidth) and the output is an entire fuzzy set (in this case, link stability). The inputs are then combined using the AND operator. This set will later be defuzzified, assigning one numerical value to the output. We design the knowledge based rules connecting the inputs and the output based on a thorough understanding of the system. The parameters and rules of our fuzzy logic system are initially set, induced from many analytical results of MANET routing.
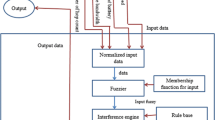
3.4 Membership Function for the Fuzzy Variables
Having defined the fuzzy linguistic rules, the membership functions corresponding to each element in the linguistic set (sent control packet, power remaining, available bandwidth and link stability) must be defined.
The criteria rating can be assessed by linguistic terms (dimensionless index) such as low (L), medium (M) and high (H).
The linguistic rating scale applied are illustrated in Figs. 1 and 2, and the membership functions of the three linguistic rating values is shown in Fig. 3.
3.5 Fuzzification, Inference and Defuzzificaiton
Fuzzification is a process where crisp input values are transformed into membership values of the fuzzy sets (as described in the previous section). After the process of fuzzification, the inference engine calculates the fuzzy output using fuzzy rules described in Table 1. The fuzzy inference system (FIS) is a mamdani type system with three inputs and one output. All inputs are normalized between 0 and 1 before applying them to FIS. The output of FIS which is link stability applied to the software simulation for evaluations. Design of FIS is the process of formulating the mapping from a given input to its output using fuzzy logic. Mamdani-type inference expects the output membership functions to be fuzzy sets. After the aggregation process, there is a fuzzy set for output variable as shown in Fig. 2. The fuzzy operator used for the AND method in if–then rules, such as, If A1 is a AND A2 is b, then A3 is c is multiplication.
Defuzzification is a mathematical process used to convert the fuzzy output to a crisp value. This crisp output is the link stability value. The fuzzy logic system has been simulated using Optimized Network Engineering Tool (OPNET) [24].
Formally, we can represent the rule-base (Table 1) of the fuzzy system in the following format:
where \( A_{i2} , A_{i3} ,B_{i} \) and are the linguistic labels low, medium and high and \( A_{i1} \) is the linguistic labels low and high of the \( i^{th} \) rule.
This rule-base is to be employed to build the fuzzy system as described below:
The link stability ratings of the different routes to the same destination under multiple criteria are evaluated. The membership function of rating values is assigned as F(i) for the \( route_{i} \). Here, we respectively correspond the membership function B(i), S(i), Rs(i) and P(i) to available bandwidth, sent control packet and power remaining. The membership functions S(i) and Rs(i) of the sent control packet rating value are expressed as follows:
The final rating is the fuzzy suitability index for each candidate \( route_{i} \) which can be calculated by the following equations:
where \( \alpha_{i} + \beta_{i} + \gamma_{i} = 1. \)
The reliability of a feasible path is based upon available bandwidth, sent control packet and power remaining. Based on the preceding discussions, an algorithm is proposed that effectively combines all three parameters with weighing factors \( \alpha_{i} \), \( \beta_{i} \) and \( \gamma_{i} \), the values of which can be chosen according to system requirements. For example, power remaining is very important in MANETs; thus, the weight of this factor can be increased. The flexibility to change factors helps the algorithm to select a routing path. Greater route power remaining and available bandwidth values represent higher reliability, as sent control packet.
F(i) is the approximated fuzzy number corresponding to the fuzzy index of the alternative \( route_{i} \). Further, we can list the final rating of the various routes to obtain the suitability index of the alternative \( route_{i} \).
The link stability is an inverse ratio corresponding to sent control packet via the previous processes and it is a direct ratio to the available bandwidth and power remaining. Consequently, the link stability rating value must be converted from the combined F(i).
The link stability of different routes under the different selection criteria are evaluated for each destination.
A fuzzy set of multiple criteria decision-making approaches is proposed to help us to obtain the two comparatively stable disjoint routes with the comparatively optimal link stability.
3.6 Route Discovery
FBORP is an on-demand routing protocol. Its route discovery process is similar to that of AODV. The route discovery process is initiated whenever a source node wants to communicate with another node for which it has no routing information in its table. The source node initiates route discovery by broadcasting a RREQ to its neighboring nodes. The RREQ format is shown in Fig. 4. Request ID is incremented each time the source node sends a new RREQ, so the pair (source address, request ID) identifies a RREQ uniquely. Upon receiving a RREQ, each node checks the source address and the request ID. If the node has already received a RREQ with the same pair of parameters, the new RREQ will be discarded. Otherwise, the RREQ will be either forwarded (broadcast) or replied to by (unicast) a RREP:
-
If the node has no route entry for the destination or has one that is no longer up-to-date, the RREQ will be rebroadcasted with an incremented HC.
-
If the node has a route with a sequence number greater than or equal to that of RREQ, a RREP will be generated and sent back to the source.
If a node is the destination, or has a valid route to the destination, it unicasts a RREP back to the source. The RREP format is shown in Fig. 5. By the time a broadcast packet arrives at a node that can supply a route to the destination node, a reverse path has been established to the source node of the route request. As the RREP travels back to the source node, each node along the path sets up a forward pointer to the node from which the route reply came, updates its timeout information for route entries to the source node and the destination node, and records the latest destination sequence number for the requested destination node.
The steps for the route discovery are described below. Path finding table structure FBORP is similar to the AODV protocol. When a source node wants to send data to an away node, the following steps must be followed:
-
1.
When source S receives a packet from the transport layer in the direction of destination D, it checks to see if a route exists to the destination. If it already has a route, it transmits the packet to the next hop node, otherwise, it transmits a RREQ to its own neighboring nodes and adds it’s ID, P, SC and BW of the RREQ to the packet entry.
-
2.
When a node X receives a RREQ request with source S, a destination D and a source-sequence-number sqn1.
-
If pair <S, D> exists in the routing table with a source-sequence-number of sqn2.
-
(sqn1 ≥ sqn2)
-
-
X updates the routing table.
-
If X # D
X records its own PB, SC and BW and broadcasts the RREQ to the neighboring node.
-
Otherwise:
-
1.
X waits for a certain amount of time to receive other RREQ packets.
-
2.
X analyzes and constructs the three basic evaluation criteria as available bandwidth, sent control packet and power remaining along each feasible path.
-
3.
Assigning membership functions B(i), S(i), Rs(i), P(i) The membership functions of the rating values available bandwidth, sent control packet and power remaining.
-
4.
Assuming \( \alpha_{\text{i}} = {\raise0.7ex\hbox{$1$} \!\mathord{\left/ {\vphantom {1 6}}\right.\kern-0pt} \!\lower0.7ex\hbox{$6$}} \), \( \beta_{\text{i}} = {\raise0.7ex\hbox{$1$} \!\mathord{\left/ {\vphantom {1 3}}\right.\kern-0pt} \!\lower0.7ex\hbox{$3$}} \), \( \gamma_{\text{i}} = {\raise0.7ex\hbox{$1$} \!\mathord{\left/ {\vphantom {1 {2 }}}\right.\kern-0pt} \!\lower0.7ex\hbox{${2 }$}} \) then, Computing the combined suitability indices, F(i). Using the combined rule-base to obtain the final fuzzy rating index represented as LS(i).
-
5.
X selects the two comparatively stable disjoint routes of the candidate routes. The selected optimal routes should be the higher LS.
-
6.
X adds it’s LS of the RREP to the packet entry and sends an RREP to source node S.
-
7.
S begins to send the data.
-
1.
-
Otherwise:
X records its own PB, SC and BW with the RREQ and broadcasts the RREQ to the neighboring node.
-
Otherwise:
X creates a new pair <S, D> with a source-sequence-number equal to sqn1.
3.7 Route Maintenance
Because of the high mobility of nodes in MANETs, links break easily. FBORP route maintenance is initiated when the route is active and data packets are transmitting. A link failure occurs when a mobile node moves out of another mobile node’s radio transmission range. The mobile nodes monitor their own neighborhood. When a node in an active route gets lost, a route error packet (RERR) is generated to notify the other nodes on both sides of the link of the loss of this link. Mobile nodes that receive the RERR will find this malefactor in their route cache and add one to their error count. On receiving a RERR, the source node initiates a new route of discovery or finds an alternative path for routing.
The proposed algorithm can be summarized as follows: Assume that source node S wants to find a path to destination node D and nodes I and J are chosen to be the transmitting node and that the link between node I and node J is broken. When a link is broken, node I receives a RERR.
-
If I detects the link failure to the next node:
-
1.
I sends the error packet.
-
2.
S receives the error packet.
-
3.
S stops sending the data.
-
4.
S restarts the route discovery process or finds an alternative path for routing.
-
1.
-
Otherwise:
Node I continues to send the data.
3.8 An Illustrative Example
In this section, a hypothetical problem is designed to demonstrate the computational process of the method. For example suppose source S wants to send data to destination D, the following steps must be followed:
-
1.
Initially, a source S floods the RREQ to its own neighboring nodes and adds it’s ID, power remaining, sent control packet and available bandwidth of the RREQ to the packet entry, the receivers re-flood non-duplicated RREQ and then the destinations D receives a RREQ request.
-
2.
Destination D waits for a certain amount of time to receive other RREQ packets. Assume that the returned multiple routes are R1, R2, R3, R4, R5, R6 from a S.
-
3.
D analyzes and constructs the three basic evaluation criteria as available bandwidth, sent control packet and power remaining from the different routes. The rule bases are listed in Table 2.
Table 2 The ratings of the alternative routes according to the three criteria described -
4.
Assigning membership functions B(i), S(i), Rs(i), P(i) The membership functions of the rating values available bandwidth, sent control packet and power remaining, B(i), S(i), Rs(i), P(i) respectively are assigned to each candidate \( {\text{route}}_{\text{i}} \) as shown in Table 3.
Table 3 The Fuzzy index ratings of the alternate routes -
5.
Computing the combined suitability indices, F(i). Using the combined rule-base to obtain the final fuzzy rating index represented as LS(i), the fuzzy suitability indices LS(i) of the six alternative routes can be obtained. The results are shown in Table 4.
Table 4 The ratings of the alternative routes
The source selects the two comparatively stable disjoint routes of the candidate routes. The selected optimal routes should be the higher link stability. From Table 4, the sequence of the priority of the routes to be selected is R5, R4, R2, R1, R6 and R3. The LS rating value is calculated from the combined F(i) value. Obviously, R5 (high available bandwidth, high power remaining, low sent control packet) is better than R4 (high available bandwidth, high power remaining, medium sent control packet). The second selected route is R2. Nevertheless, the destination finds the second disjoint route in rating order.
-
6.
D adds it’s LS of the RREP to the packet entry and sends an RREP to source node S.
-
7.
S begins to send the data from route 5.
4 Simulation Results
This section compares the performance of the proposed FBORP with the well-known AODV protocol. An Optimized Network Engineering Tool 10.5 (OPNET 10.5) was used to simulate the proposed algorithm, which is a synthetic simulation tool to simulate and analyze for network communication and distributed system, and it can provide three-tier model, where the top layer is the network layer that reflects the topology of the network, the middle layer is the node layer that is composed of the corresponding protocol models and reflects the characteristics of the equipment, and the bottom layer is the process model that is described by finite state machines. The three-tier model fully corresponds to the actual network, protocol and equipment, and it can reflect the relevant characteristics of the network.
Assumptions about the parameters of the system architecture were made in the simulations. The simulation modeled the network in a 1124 m × 1124 m area with 30 mobile nodes as shown in Fig. 6. The radio transmission range was assumed to be 250 m. The speed of each mobile node was assumed to be 0–9 m/s with a pause time fixed at 250 s. In each run, 20 CBR sessions were simulated with random source and destination pairs. Each CBR session generated 20 packets per second with data packets of 512 bytes. The simulation time was 600 s. We did our experiments with movement patterns for 7 difference pause times: 0, 100, 200, 300, 400, 500 and 600 s. The initial positions of the nodes were uniformly distributed throughout the network. Node mobility was simulated according to the random waypoint mobility model in which each node travels to a randomly selected location at a configured speed and then pauses for a configured pause time before choosing another random location and repeating the same steps.
This paper studies the simulation and analysis of FBORP and AODV protocols. The performance indexes tested are as follows:
-
1.
Network Throughput: it is the maximum rate that the network equipment can bear in the case of no data loss.
-
2.
Network Delay: it includes the routing discovery delay, waiting delay of packets in the interface queues, transmission delay and retransmission delay of the MAC layer.
-
3.
Routing Discovery Time: it is the time from launching the routing discovery of the source node to receiving the RREP packet and establishing the route.
-
4.
Average Number of Hops Per Route: it is defined as the average time of the total number of hops passed by the packet sent from the source node to the destination node, in the whole simulation process.
Figure 7 shows the average performance in terms of throughput for different pause times in a network of 30 nodes. The X-axis represents the pause times and the Y-axis represents the throughput. The simulations in Fig. 7 show that FBORP performed better than AODV. Most ad hoc routing protocols presuppose the presence of bidirectional links between the nodes in the network. In reality, the ad hoc network may consist of heterogeneous nodes with different power capabilities and different transmission ranges. When this is the case, a given node might be able to receive the transmission of another given node but might not be able to successfully transmit data to it. In FBORP protocol, using the fuzzy-based algorithm determined the suitability of the link and if the link was suitable, a given node was able to successfully transmit data to it. Thus, the throughput of the proposed algorithm was higher than the AODV algorithm.
Figure 8 shows the average delay for FBORP and AODV for different pause times. The X-axis represents the pause time and the Y-axis represents the delay. The AODV in Fig. 8 can be explained by the fact that the number of dropped packets was larger for AODV than for RBORP and that the dropped packets were not taken into account in the average delay calculation. When a packet was not dropped and was delivered with a large delay, the total average delay increased. However, if FBORP increased, the network reliability and average delay decreased.
Figure 9 shows the number of FREQs sent by both algorithms. The X-axis represents the pause time and the Y-axis the route discovery time. The figure shows that the FBORP algorithm greatly decreased the route discovery time. The improvements became more significant as the pause time increased.
Figure 10 shows the hope count of FBORP and AODV for different pause times. The X-axis represents the pause time and the Y-axis the HCs. Figure 10 shows that the hope count of FBORP was less than AODV.
5 Conclusion
This paper proposed a fuzzy based on-demand routing protocol (FBORP) with proper rules as defined with expert human. Using fuzzy logic approaches with capability robustness to uncertainty, especially for mobile ad hoc networks. FBORP selects a stable routing path by maximizing the link stability among the feasible paths. Three parameters are including the power of battery, the speed of mobile nodes, and the bandwidth used in FBORP to calculate the link stability of the feasible path. Route selection is based on the link stability value of each feasible path. Simulation results show that the proposed FBORP outperforms AODV method, especially in a high mobility environment.
References
Seno, S. A. H., Budiarto, R., & Wan, T. (2011). A routing layer-based hierarchical service advertisement and discovery for MANETs. Ad Hoc Networks, 9, 355–367.
Garg, N., Aswal, K., & Dobhal, D. C. (2012). A review of routing protocols in mobile ad hoc networks. International Journal of Information Technology, 5, 177–180.
Raich, A., & Vidhate, A. (2013). Best path finding using location aware AODV for MANET. International Journal of Advanced Computer Research, 3, 336–340.
Bilgin, Z., & Khan, B. (2010). A dynamic route optimization mechanism for AODV in MANETs. In IEEE ICC.
Misra, P. (2000). Routing protocols for ad hoc mobile wireless networks. http://www.cis.ohio-state.edu/~misra.
Wang, N.-C., Huang, Y.-F., & Chen, J.-C. (2007). A stable weight-based on-demand routing protocol for mobile ad hoc networks. Information Sciences: an International Journal, 177, 5522–5537.
EL-Afandi, H. (2006). An intelligent wireless ad hoc routing protocol. Milwaukee: University of Wisconsin–Milwaukee.
Jain, R., & Garg, S. (2014). Dynamic source routing protocol for ad hoc networks using the concept intelligent agent fuzzy logic. International Journal of Engineering and Management Research, 480–486.
You, L., Li, J., Wei, C., Dai, C., Xu, J., & Hu, L. (2014) A hop count based heuristic routing protocol for mobile delay tolerant networks. Scientific World Journal.
Kanakaris, V., Ndzi, D., & Azzi, D. (2010). Ad hoc networks energy consumption: A review of the ad-hoc routing protocols. Journal of Engineering Science and Technology Review.
Vu, T. K., & Kwon, S. (2014). Mobility-assisted on-demand routing algorithm for MANETs in the presence of location errors. The Scientific World Journal, 2014, 790103.
Sivakumar, B., Bhalaji, N., & Sivakumar, D. (2014). A survey on investigating the need for intelligent power-aware load balanced routing protocols for handling critical links in MANETs. The Scientific World Journal, 2014, 603547.
Xia, H., Jia, Z., Li, X., Ju, L., & Sha, E. H. M. (2013). Trust prediction and trust-based source routing in mobile ad hoc networks. Science Direct Ad Hoc Networks, 11, 2096–2114.
Moussaoui, A., Semchedine, F., & Boukerram, A. (2014). A link-state QoS routing protocol based on link stability for mobile ad hoc networks. Journal of Network and Computer Applications, 39, 117–125.
Kumar, K., & Singh, V. P. (2014). Power consumption based simulation model for mobile ad-hoc network. Wireless Personal Communications, 77, 1437–1448.
Kumar Jain, Y., & Kumar Verma, R. (2012). Energy level accuracy and life time increased in mobile ad-hoc networks using OLSR. International Journal of Advanced Research in Computer Science and Software Engineering, 2, 97–103.
Sheng, H., Wang, J., Huang, H., & Yen, D. (2006). Fuzzy measure on vehicle routing problem of hospital materials. Expert Systems with Applications, 30, 367–377.
Budyal, V. R., & Manvi, S. S. (2014). ANFIS and agent based bandwidth and delay aware anycast routing in mobile ad hoc networks. Journal of Network and Computer Applications, 39, 140–151.
Yuanzhou, L., & Weihua, H. (2010). Optimization strategy for mobile ad hoc network based on AODV routing protocol. In 6th international conference on wireless communications networking and mobile computing (WiCOM).
Goswami, M. M., Rughwani, V., & Anjikar, A. (2013). A novel fuzzy stochastic routing protocol for mobile adhoc network. International Journal of Computer Science and Mobile Computing, 2, 98–106.
Stojmenovic, I. (2002). Position-based routing in ad hoc networks. IEEE Communications Magazine, 40, 128–134.
Naruephiphat, W., & Usaha, W. (2008). Balanced energy-efficient routing in MANETs using reinforcement learning. Nakhon Ratchasima: School of Telecommunication Engineering, Suranaree University of Technology.
Su, B., Wang, M., & Huang, Y. (2007). Fuzzy logic weighted multi-criteria of dynamic route lifetime for reliable multicast routing in ad hoc networks. Journal of Expert Systems with Applications, 35, 476–484.
Hasan, M. S., Hongnian, Yu., Griffiths, A., & Yang, T. (2007). Simulation of distributed wireless networked control systems over MANET using OPNET. In Proc ICNSC (pp. 699–704).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Tabatabaei, S., Teshnehlab, M. & Mirabedini, S.J. Fuzzy-Based Routing Protocol to Increase Throughput in Mobile Ad Hoc Networks. Wireless Pers Commun 84, 2307–2325 (2015). https://doi.org/10.1007/s11277-015-2706-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2706-6