Abstract
In this study, resource allocation problems in uplink transmissions of long term evolution (LTE) networks involving single-carrier frequency division multiple access were addressed and a two-stage process for obtaining solutions was proposed. In the first stage, a buffer-aware (BA) scheme that allocates resources according to users’ buffer statuses is used to simultaneously reduce wastage of system resources and improve the throughput of each user. In the second stage, a BA-scheme-based enhanced algorithm is used for considering the delay-sensitive (DS) characteristics of packets. Simulations were conducted to compare the performance of the proposed BA and DS resource allocation algorithm with that of other approaches. The results show that the proposed algorithm can effectively improve the aggregate throughput and reduce both the packet loss rate and average packet delay in comparison with other schemes, thus enhancing the overall uplink efficiency of LTE networks.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The demand for broadband wireless access (BWA) networks is increasing with the growth of wireless applications such as social network services, real-time gaming, video streaming services, and Web TV. Since the characteristics of applications determine the quality-of-service (QoS) parameters such as sustained transmission rates and tolerable packet delays, the effective management and allocation of scarce wireless resources for supporting a variety of QoS requirements have become a critical research topic.
The long term evolution (LTE) access technologies developed by the Third-Generation Partnership Project (3GPP) group are promising BWA solutions for providing high-data-rate transmissions, coverage of an extensive area, and high-speed mobility for various wireless applications [1, 2]. LTE technologies involve using orthogonal frequency division multiple access (OFDMA) technology for downlink radio access since this technology offers high resistance to multipath fading and facilitates highly efficient spectrum utilization. However, a major problem is encountered during OFDMA use: the peak-to-average power ratio (PAPR) is high, possibly reducing the transmission power efficiency appreciably. Therefore, in the uplink of an LTE system, single-carrier frequency-division multiple access (SC-FDMA) is used because of the power constraints of handheld devices. Because of its single-carrier properties, SC-FDMA can reduce the PAPR to a greater extent compared with OFDMA. Nevertheless, there is a restriction associated with the single-carrier properties of SC-FDMA: the resource blocks (RBs) assigned to a single user must be adjacent to each other. This constraint can limit the system performance parameters such as the channel utilization efficiency and aggregate throughput. Thus, the resource allocation scheme used for SC-FDMA in the uplink of an LTE system must be appropriately designed to optimize the system performance under the channel contiguity constraint.
The resource allocation problems in the uplink of an LTE system have been investigated by previous studies [3–13]. While the authors of [3] proposed an uplink scheduling algorithm involving game theory for LTE systems, they did not consider the adjacent RB restriction for SC-FDMA. In [4], resource scheduling was designed by considering the end-to-end delay constraint in addition to the channel contiguity constraint. The studies in [5–7] proposed different schemes for uplink resource allocation in LTE systems. Nevertheless, these studies assumed saturated traffic conditions (i.e., every user always has a packet to send) along with an unlimited buffer length and did not consider different traffic load scenarios. In the resource scheduling scheme in [8], various users’ requirements for channel resources and different buffer statuses were considered and the focus was on the effect of the delay report interval. Extra RBs were pruned and allocated to other users. However, this scheme does not analyze its performance according to other QoS metrics such as the throughput and packet loss rate.
In this study, the resource allocation problems in the LTE uplink SC-FDMA system were addressed and a two-stage process for obtaining solutions was proposed. In the first stage, a buffer-aware (BA) scheme that allocates resources according to users’ buffer statuses to simultaneously reduce the wastage of system resources and improve the throughput of each user is used. The key concept of the proposed BA approach is based on the observation that most recent studies have not considered the buffer status and assumed saturated buffer conditions (i.e., users always have a packet to send in their buffer) [5–7], implying that the number of RBs assigned to a single user directly reflects the throughput of the user. This assumption is impractical because most traffic loads are dynamic, depending on the corresponding service types. This was the motivation for investigating a resource allocation algorithm that considers users’ buffer statuses in the present study. On the basis of the BA resource allocation scheme, an enhanced algorithm that considers the delay-sensitive (DS) characteristics of packets is used in the second stage. Using this resource allocation algorithm (BA + DS scheme) can improve the QoS for real-time applications by dynamically adjusting the priorities during channel allocation among users according to the number of time-sensitive packets accumulated in the buffer. Simulations were conducted to compare the performance of the proposed resource allocation algorithm (BA and BA + DS schemes) with that of other approaches. The results demonstrate that the proposed approach can effectively improve the aggregate throughput and reduce both the packet loss rate and average packet delay in comparison with the other approaches, thus enhancing the overall LTE uplink efficiency. The rest of this paper is organized as follows. Section 2 presents the SC-FDMA system model. Section 3 describes the proposed resource allocation algorithms. Sect. 4 explains the simulation setup and results. Finally, the conclusion is presented in Sect. 5.
2 System Model of SC-FDMA
The specific characteristic of SC-FDMA for the uplink resource allocation in LTE systems is the adjacent assignment of RBs for users to transmit their data. This implies that the allocation of RBs in the SC-FDMA system cannot be as flexible as that in the OFDMA system. According to [4], the constraint of RB selections for U users can be expressed as:
where R is the set of RBs and U is that of users; ɛ i,j is a binary parameter. The ith RB will be assigned to user j when ɛ i,j = 1, or not if ɛ i,j = 0. Equations (1) and (2) simply illustrate that each RB can only be assigned to one user in a given scheduling cycle. To meet the requirement of adjacent RB assignments, the following constraints are added:
where \( \sigma_{i,j}^{ + } \) and \( \sigma_{i,j}^{ - } \) are both binary parameters. \( \sigma_{i,j}^{ + } \) and \( \sigma_{i,j}^{ - } \) express the adjacent RB allocation of the ith and i + 1th RB associated with user j: if RB i is not assigned to user j but RB i + 1 is assigned to user j, \( \sigma_{i,j}^{ + } \) would be set to 1. On the contrary, if RB i is assigned to user j, but RB i + 1 is not assigned to user j, \( \sigma_{i,j}^{ - } \) would be set to 1. According to Eqs. (4) and (5), we can see that to a given user, one kind of RB-allocation status alteration (i.e., either from assignment to non-assignment or from non-assignment to assignment) can only occur once in each scheduling cycle. Thus, Eqs. (3), (4) and (5) can make sure that the allocation of RBs in each scheduling cycle will comply with the constraint of adjacent assignment requirement. Furthermore, as Eq. (6) shows, the situation of next RB allocation of the i + 1th RB to user j, ɛ i+1,j , can be derived from the condition of the present RB allocation, ɛ i,j , with the values of \( \sigma_{i,j}^{ + } \) and \( \sigma_{i,j}^{ - } \).
3 Proposed Resource Allocation Algorithm
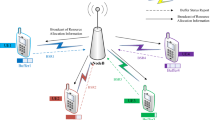
Consider the transmission scenario shown in Fig. 1. Various numbers of packets are waiting for transmission in the buffers of different users. The distances from the base station to Users A, B, and C are d A , d B , and d C , respectively, and d C < d B < d A . Generally, the channel quality is higher for a user closer to the base station (e.g., User C), and the user is expected to receive more resources than other users when the base station allocates resources according to users’ channel conditions. However, Fig. 1 shows that User C has fewer packets waiting for transmission compared with Users A and B. Hence, if users’ buffer statuses are considered in addition to their channel conditions for resource allocation, User C should not be allocated the largest amount of resources for data transmission. In fact, User B should be allocated more resources than the other two users because it has the largest number of packets waiting for transmission.
3.1 Algorithm 1: The Buffer-Aware (BA) Resource Allocation Algorithm
The preceding discussion implies that the users’ buffer statuses can be a key attribute in the design of resource allocation schemes, especially when the number of users is high and the available resources are limited [14–16]. Therefore, in this study, a BA resource allocation scheme in which both the buffer status and channel conditions of users are considered was proposed. To maximize the transmission throughput by considering buffer statuses in addition to channel conditions, the RB allocation problem can be formulated as a constrained optimization problem:
where λ i,j is the channel quality indicator (CQI) value of RB i for user j, and b j is the number of packets (in the unit of RB) accumulated in the buffer of user j. As (7) shows, the transmission throughput is maximized by selecting the user with the highest CQI value under the constraint of cumulated packet numbers in the buffer. Thus, when the constrained optimization problem in (7) is solved on the basis of (1)–(6), which specify the requirements for assigning adjacent RBs for SC-FDMA, the proposed BA resource allocation scheme can simultaneously meet the actual demand of users and reduce wastage of system resources.
Indeed, the constrained optimization problem in (7) under the block contiguity constraints (1)–(6) is a difficult mathematical problem. With the contiguity constraint, we may need to allocate users with some suboptimal RBs so as to optimize the objective in (7). Such the problem is NP-hard and thus it is difficult to find an optimization solution for real-time scheduling and resource allocation. In this study, we present heuristics algorithms to provide a suboptimal solution for real-time scheduling and resource allocation under the block contiguity constraints in SC-FDMA. The pseudocode of the proposed BA algorithm is presented in Fig. 2.
3.2 Algorithm 2: The Buffer-Aware (BA) and Delay-Sensitive (DS) Allocation Algorithm
Consider the transmission scenario shown in Fig. 1 again. Two types of packets are considered in the buffer: one without delay constraints (labeled cross) for non-real-time applications such as HTML and e-mails, and DS packets (labeled dotted) for real-time applications such as voice, video streaming, and real-time gaming. As shown in Fig. 1, among Users A, B, and C, User A has the highest number of real-time packets waiting for transmission. Hence, if the DS characteristics of packets are considered in addition to users’ buffer statuses for allocating resources, then the priority of resource allocation for User A should be higher than those for Users B and C.
This motivated consideration of the delay constraint in the proposed BA resource allocation scheme and the proposal of the BA and DS (BA + DS) algorithm. In the BA + DS algorithm, a nonlinear μ-law operation as that shown in (8) is performed. The so called μ-law operation is formerly a nonuniform pulse code modulation (PCM) adopted as a telecommunication standard in the US and Canada [17]. In this study, we apply the logarithmic function to control the priority of resource allocation according to the number of DS packets [17]. That is,
where B max represents the highest number of delay-constrained packets among all users, which can be time-varying in every scheduling cycle; d j is the number of DS packets of user j. The parameter w j is the weighting factor and controls the priority of channel allocation for user j (a higher value of w j indicates a higher priority for channel allocation) and is adopted in (9). The parameter μ determines the nonlinear characteristics between d j and w j . The variation of w j with the ratio d j /B max is shown in Fig. 3, where the value of 1 is adopted for μ; the curve is based on (8). The value of w j increases exponentially with an increase in d j . Thus, the approach used in the BA + DS algorithm can effectively improve the QoS performance of real-time applications by dynamically adjusting the priorities of channel allocation for users according to the number of time-sensitive packets in the users’ buffers.
After the value of w j for each user is calculated using (8), it is used to adjust the CQI value λ i,j to \( \lambda_{i,j}^{\prime } \) as follows:
The updated CQI value \( \lambda_{i,j}^{\prime } \) is then substituted for λ i,j in (7). Thus, the BA + DS algorithm can determine the resource allocation for users according to the channel conditions, buffer statuses, and numbers of DS packets.
The following example explains the operation of the proposed BA + DS algorithm. Assume that the channel quality of Users A, B, and C is as shown in Fig. 4 and that User A has a high number of DS packets waiting for transmission in comparison with Users B and C. Case 1 considers only the channel quality for resource assignment under the adjacent RB constraint in the SC-FDMA structure. User A is allocated the lowest amount of resources since the user’s channel conditions are poor. The BA + DS resource allocation scheme also considers the buffer status and DS packets, and the results obtained for this scheme correspond to the Case 2 results. The CQI value of User A is increased (marked as the red dotted line A′), leading to a channel being assigned to User A for a longer duration; the higher CQI value results from the higher w j , which increases with the number of DS packets. This example demonstrates that the proposed BA + DS algorithm has the potential to improve the QoS performance of real-time applications for users on the basis of the actual demand for channel resources. The pseudocode of the proposed BA + DS algorithm is shown in Fig. 5.
4 Performance Evaluation and Discussion
4.1 Simulation Setup
In this section, simulation scenarios of uplink transmission by using SC-FDMA in a FDD LTE cellular network are presented to demonstrate the effectiveness of the proposed resource allocation algorithms, the BA and BA + DS algorithms. The simulation was performed using C++ programming and by following the LTE standard closely [18–20]. The simulation setup assumes a single eNodeB with available power of 46 dBm and cell radius of 1 km. The wireless channel of simulations is based on the path loss model without fading described as L = 128.1 + 37.6 log10 R [21]. Adaptive modulation and coding (AMC) schemes are considered for variable PHY data rates according to the current channel conditions of wireless links. The modulation types supported in the LTE standards include binary phase-shift keying (BPSK), quadrature phase-shift keying (QPSK), 16-quadrature amplitude modulation (16-QAM) and 64-QAM. With the convolutional turbo code (CTC) and different code rates, various modulation and coding schemes (MCSs) are provided in the LTE system. For the simplicity of illustration, we assume the proportion of used MCSs is, QPSK with 3/4 CTC: 25 %, 16-QAM with 1/2 CTC: 25 %, and 64-QAM with 5/6 CTC: 50 %. We assume that the base station has a perfect knowledge of the channel quality information of all users across all RBs. The SC-FDMA PHY parameters and their values are listed in Table 1.
The simulation setup considered a mixture of real-time (RT) and non-real-time (NRT) traffic flows in uplink transmission. The types of RT traffic flows included conversational voice and conversational video, and for the NRT traffic flows, a Transmission Control Protocol (TCP)-based Web-browsing application was considered. The distributions of the three types of traffic flows were assumed to be uniform. The conversational voice was transmitted in fixed-size packets generated at periodic intervals, that is, a constant bit rate. The conversational video was transmitted in variable-size packets generated at periodic intervals, that is, a variable bit rate. The TCP-based Web-browsing application involved variable-size packets generated randomly. The simulation parameters for the three types of traffic models are provided in [22, 23]. The delay constraints corresponding to the three types of traffic services are listed in Table 2. The packets were assumed to be dropped when the time waiting for transmission exceeded the predefined tolerable delay time.
The performance of the proposed BA and BA + DS algorithms was compared with that of the round-robin (RR) and greedy algorithms [6]. For the proposed BA + DS algorithm, the value of μ in (8) was 1. The performance metrics were indexed as the packet loss rate, aggregated throughput, and packet delay time. The simulation results provided are the average values over 20 simulations.
4.2 Simulation Results and Discussions
Figure 6 shows the packet loss rates for different resource allocation schemes. When the number of users was lower than or equal to five, the packet loss rate was almost zero irrespective of the scheme chosen since the system resources were sufficient for all users to transmit data packets. When the number of users exceeded five and packets were increasingly accumulated in the users’ buffers, the packet loss rate increased because of the delay constraints for QoS requirements. When the number of users exceeded five, the proposed BA and BA + DS algorithms outperformed the other two algorithms, with the BA + DS algorithm showing the highest performance. In addition, the superiority of the proposed algorithm over the other two algorithms slightly decreased when the number of users increased. The main reason for this was that as the system load increased considerably, the difficulty in meeting the delay constraints increased, thereby causing more packets to be dropped. On average, the proposed BA scheme reduced the drop rate by 14.68 and 23.91 % in comparison with the greedy and RR algorithms, respectively, while the proposed BA + DS scheme further enhanced the performance by as much as 23.45 and 31.73 % over the greedy and RR algorithms, respectively. Compared with the BA scheme, the BA + DS algorithm improved the packet loss rate by 10.28 % since it considers the delay constraints of packets.
Figure 7 shows the aggregate throughput for different resource allocation schemes, indicating that the proposed algorithms are superior to the other two algorithms especially when the number of users is large, and that the BA + DS algorithm showed the highest performance according to the aggregate throughput. It is noted that even if the packet loss rates with different schemes (shown in Fig. 6) get close when the number of users becomes large, the aggregate throughput can rather differ to each other because the proposed buffer-aware schemes can allocate resources to users according to their demands and thus increasing the throughput efficiency. On average, the proposed BA scheme increased the aggregate throughput by 7.48 and 11.44 % in comparison with the greedy and RR schemes, respectively, while the proposed BA + DS scheme further enhanced the performance by as much as 12.81 and 16.97 % over the greedy and RR schemes, respectively. In comparison with the BA scheme, the BA + DS scheme increased the aggregate throughput by 4.97 % since it considers the delay constraints of packets. The simulation results shown in Figs. 6 and 7 demonstrate that the proposed resource allocation schemes, in which the buffer status and the DS packets are considered, can effectively improve the user-perceived QoS by reducing the packet loss rate and increasing the overall transmission efficiency.
To obtain insight into the performance difference between the proposed resource allocation schemes and other aforementioned schemes, users’ demand for RBs and the number of allocated RBs were analyzed using the greedy algorithm. Figure 8 shows a comparison between the users’ demand for RBs and the number of allocated RBs for the greedy algorithm. The greedy algorithm, which considers only the users’ channel conditions and not their buffer status and the delay constraint of packets, clearly cannot allocate resources appropriately. For example, in Fig. 8a, the allocated resources for both Users 1 and 4 exceeded their demand, whereas those for Users 2, 3, and 5 were insufficient. The severity of such situations can increase when the number of users increases, as shown in Fig. 8b. On the basis of the results shown in Fig. 8, Fig. 9 shows the total number of RBs allocated to users but remaining unused, and the total number of packets (in the unit of RB) that were waiting to be sent but were not assigned RBs for transmission. Certain parts of channel resources were apparently wasted, and some users could not acquire adequate RBs for transmitting their data packets. The discussion of Figs. 8 and 9 clearly shows that a resource allocation approach in which only the users’ channel conditions are considered cannot allocate resources appropriately; resource allocation schemes should exploit the knowledge of users’ buffer statuses and the delay constraint of packets, as the proposed BA and BA + DS algorithms do, to simultaneously reduce wastage of system resources and improve the overall transmission efficiency.
Finally, the average packet delay was considered (Fig. 10). When the number of users was lower than seven, the performance of all four schemes was similar since the network resources were sufficient for users to transmit their data packets. When the number of users increased and the system load increased, the proposed algorithms were apparently superior to the other two algorithms according to the average packet delay. The proposed BA scheme reduced the average packet delay by 3.16 and 4.50 % in comparison with the greedy and RR schemes, respectively. The BA + DS algorithm showed the highest performance among the four algorithms. It decreased the delay by 6.54 and 7.83 % in comparison with the greedy and RR schemes, respectively. When the number of users exceeded 15, the BA + DS algorithm showed performance similar to that of the BA algorithm because of the high system load and limited channel resources, and therefore, more packets were transmitted at times close to the delay bound even as different priorities were considered for DS packets. Overall, the BA + DS algorithm exhibited a 3.48 % improvement over the BA algorithm according to the packet delay time. The simulation results shown in Figs. 6, 7, 8, 9 and 10 demonstrate that the proposed resource allocation schemes in which users’ buffer statuses and DS characteristics of packets are considered can effectively improve the aggregate throughput and reduce both the packet loss rate and average packet delay in comparison with other schemes, thus improving the user-perceived QoS and the overall transmission efficiency in the LTE uplink SC-FDMA system.
5 Conclusion
This study addressed the resource allocation problems in the uplink SC-FDMA of LTE networks. A two-stage process for obtaining solutions was proposed. In the first stage, a BA scheme in which resources are allocated according to users’ buffer statuses for simultaneously reducing wastage of system resources and improving the throughput of each user is used. In the second stage, a BA-scheme-based enhanced algorithm is used to consider the DS characteristics of packets. The BA + DS algorithm can improve the QoS of real-time applications by dynamically adjusting the priority of channel allocation for different users according to the number of time-sensitive packets accumulated in the buffer. Simulations were conducted to compare the performance of the proposed resource allocation algorithm with that of other algorithms. The comparison results showed that the proposed approach can effectively improve the aggregate throughput and reduce both the packet loss rate and average packet delay in comparison with other approaches, thus enhancing the overall LTE uplink efficiency.
References
3GPP. http://www.3gpp.org.
Ghosh, A., Ratasuk, R., Mondal, B., Mangalvedhe, N., & Thomas, T. (2010). LTE-advanced: Next-generation wireless broadband technology. IEEE Wireless Communications, 17(3), 10–22.
Yaacoub, E., & Dawy, Z. (2009). A game theoretical formulation for proportional fairness in LTE uplink scheduling. In Proceedings of IEEE WCNC 2009.
Delgado, O., & Jaumard, B. (2010). Scheduling and resource allocation in LTE uplink with a delay requirement. In Proceedings of IEEE eighth annual communication networks and services research conference (CNSR) (pp. 268–275).
Lee, S.-B., Pefkianakis, I., Meyerson, A., Xu, S., & Lu, S. (2009). Proportional fair frequency-domain packet scheduling for 3GPP LTE uplink. In Proceedings of IEEE INFOCOM 2009 (pp. 2611–2615).
Wong, I., Oteri, O., & Mccoy, W. (2009). Optimal resource allocation in uplink SC-FDMA systems. IEEE Transactions on Wireless Communications, 8(5), 2161–2165.
Nwamadi, O., Zhu, X., & Nandi, A. K. (2011). Dynamic physical resource block allocation algorithms for uplink long term evolution. IET Communications, 5(7), 1020–1027.
Al-Rawi, M., Jantti, R., Torsner, J., & Sagfors, M. (2008). On the performance of heuristic opportunistic scheduling in the uplink of 3G LTE networks. In Proceedings of IEEE PIMRC 2008.
Wang, C., & Li, X. (2013). A buffer-aware resource allocation scheme for 4G LTE systems. In Proceedings of IEEE 17th international symposium on consumer electronics (ISCE) 2013 (pp. 157–158).
Saad, W., Dawy, Z., & Sharafeddine, S. (2012). A utility-based algorithm for joint uplink/downlink scheduling in wireless cellular networks. Journal of Network and Computer Applications, 35(1), 348–356.
Dechene, D. J., & Shami, A. (2011). Energy efficient resource allocation in SC-FDMA uplink with synchronous HARQ constraints. In Proceedings of IEEE ICC 2011.
Aijaz, A., Chu, X., & Aghvami, A. H. (2014). Energy efficient design of SC-FDMA based uplink under QoS constraints. IEEE Wireless Communications Letters, 3(2), 149–152.
Bodas, S., & Sadiq, B. (2013). Polynomial-complexity, low-delay scheduling for SCFDMA-based wireless uplink networks. In Proceedings of IEEE INFOCOM 2013 (pp. 575–579).
Tassiulas, L., & Ephremides, A. (1992). Stability properties of constrained queueing systems and scheduling policies for maximum throughput in multihop radio networks. IEEE Transactions on Automatic Control, 37(12), 1936–1948.
Neely, M. J. (2010). Stochastic network optimization with application to communication and queueing systems. San Rafael, CA: Morgan and Claypool.
Le, L. B., Modiano, E., & Shroff, N. B. (2012). Optimal control of wireless networks with finite buffers. IEEE/ACM Transactions on Networking, 20(4), 1316–1329.
Proakis, J. G., & Salehi, M. (2005). Essentials of communication systems engineering. London: Pearson.
3GPP. (2011). TS 36.213: 3rd generation partnership project; Technical specification group radio access network; Evolved universal terrestrial radio access (E-UTRA); Physical layer procedures, V10.4.0.
3GPP. (2011). TS 22.105, Universal mobile telecommunications system (UMTS); LTE; Services and service capabilities (Release 10), V10.0.0.
Sesia, S., Toufik, I., & Baker, M. (2009). LTE—The UMTS long term evolution, from theory to practice. London: Wiley.
Vaghefi, R. M., & Buehrer, R. M. (2014). Improving positioning in LTE through collaboration. In Proceedings of IEEE WPNC 2014.
Sadiq, B., Madan, R., & Sampath, A. (2009). Downlink scheduling for multiclass traffic in LTE. EURASIP Journal on Wireless Communications and Networking, 2009, 1–18.
Estepa, A. J., Vozmediano, J. M., López, J., & Estepa, R. M. (2011). Impact of VoIP codes on the energy consumption of portable devices. In Proceedings of the 6th ACM workshop on performance monitoring and measurement of heterogeneous wireless and wired networks (pp. 123–130).
Ali, S., & Zeeshan, M. (2011). A delay-scheduler coupled game theoretic resource allocation scheme for LTE networks. In Proceedings of IEEE 9th international conference on frontiers of information technology (FIT) (pp. 14–19).
Acknowledgments
This work was supported in part by Taiwan National Science Council under Grants 102-2221-E-003-002 and MOST 103-2221-E-003-007.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wang, C., Huang, JJ. & Su, CY. Buffer-Aware and Delay-Sensitive Resource Allocation in the Uplink of 3GPP LTE Networks. Wireless Pers Commun 84, 1877–1890 (2015). https://doi.org/10.1007/s11277-015-2490-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2490-3