Abstract
Internet of things (IoT) has been a noteworthy zone of research for empowering interconnection and joining the physical world through the Internet. At the beginning, it was used for single things but later advancements in different computing devices resulted in a new terminology called the internet of computing (IoC). In this paper, we review the latest progresses on IoT with IoC from a class review of published articles from 2009 to 2017. The review is classified alongside with (1) identification of users who are already in existence, (2) devices connected via various communication modes, (3) deterministic communication in IoT. The reviewed approaches are named as empirical, computing, innovative application and implementation approaches. The review shows that data stored in the cloud need to be mapped with geographic information system in order to fit with IoT and IoC. For IoT versus traditional communication approaches, it is found that reliable connection is one of the most emerging issues nowadays. It has been concluded that for the social consensus, IoC and IoT cooperating together are truly beneficial for upcoming years rather than just devices equipped with many sensor technologies. We hope to draw attention to this new topic with trends in the forthcoming era.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
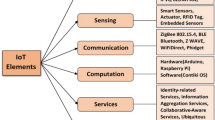
From last few years, the uses of remote devices have exponentially grown up. They were used as interconnectors in a specific network and services delivered via the Internet, which has been named as internet of things (IoT) [13]. Kevin Ashton firstly presented IoT in 1998 targeted to social community and industries [63]. It has become a noble approach, which is significantly progressing remote sensing data, automated systems for quick delivery of decisions through different communication channels. IoT uses radio frequency identification system (RFID) to help various devices (computers, machines, and sensors) in identifying objects, extracting and storing data from them [35]. Tags are used through which users can identify the “things” and keep tracking them as desired. Comparing the peer network to a complete wireless network [48], the world of IoT has become wise and broad nowadays. A wide range of IoT applications is illustrated in Fig. 1.
At the beginning, IoT was used for single “things” such as a network of heterogeneous sensors for monitoring environment [88]. Soon, by motivation from practical applications, researchers aimed to set up a connected network of different computing devices with each performing its own functionality; thus, resulting in a new terminology called the internet of computing (IoC) [86]. IoC uses various concepts, protocols, and technologies together [4]. While the wide array of IoC elements was designed to create numerous benefits in the areas of productivity and automation, at the same time it introduced new challenges such as scaling of vast numbers of devices and measures of information [84].
When IoC was introduced, several issues regarding the smartness of devices were raised [84]. The reason behind is that they are not intelligent enough or lag behind the proper use of sensors available [6, 8]. Besides, this technology is simple, insecure and unreliable. IoC connections were poor with its communicating channels being faced a lot of unwanted transmission impairments including noises [17]. After the introduction of the unified communications as a service (UCaaS), many companies with strong hardware aimed at cheaper, faster and more convenient approaches to integrate their system rather than building their own [2]. They continued to develop smarter devices to satisfy their customers. This resulted in people who could interact with different well-managed smart devices and sensors at every moment in their life [16]. A new era of IoT with IoC was started.
Looking at what IoT and IoC is nowadays, we have many applications such as smart cities, smart kitchen with millions of connected devices, etc. [62]. For example, a fog-supported smart city network architecture called fog computing architecture network has been given in [57]. It is a multi-level architecture in which applications work on things with each other through smart city conditions. It aims to diminish idleness and enhance energy provisioning and productivity of administrations among things with various capacities. Thus, it is necessary to draw a summary or review of the recent trends regarding this theme [36, 37, 47, 50].
The main objective of this paper is to analyze the latest progresses on IoT with IoC from a class review through published articles in 2009–2017. The review is classified alongside with (1) Identification of users who are already in existence, (2) devices connected via various communication modes, (3) deterministic communication in IoT. Here, integration refers to the focus on building all of those connectors in such a way that the key model is designed, developed and deployed. The building model would make things go faster and our lives more efficient. We hope to draw attention to this new topic with trends in the forthcoming era.
The rest of the paper is organized as follows. Section 2 introduces fundamental concepts of IoT. Then, the class review regarding IoT with IoC accompanied with summaries of advantages and disadvantages are described in Sects. 3 and 4, respectively. Lastly, Sect. 5 we end up the paper by conclusions and further works.
2 Internet of things
2.1 Genesis of IoT
The age of IoT is often said to start between the years of 2008 and 2009 (Table 1). During this period, a number of devices connected to the Internet eclipsed the world’s population. With more “things” connected to the Internet than people in the world, a new era of IoT was born. The person credited with the creation of the term “Internet of Things” is Kevin Ashton [63]. While working for Procter and Gamble in 1999, Kevin used this phrase to explain a new idea related to linking the company’s supply chain to the Internet. He has subsequently explained that IoT involves the addition of senses to computers. He was quoted as saying: “In the twentieth century, computers were brains without senses; they only knew what we told them” [19]. Computers depend on humans to input data and knowledge through typing, bar codes, and so on [31]. IoT changes this paradigm in which computers sense things for themselves [22]. Until now, various applications of IoT have been deployed (see Table 1).
Table 1 depicts various phases of the Internet. The first phase started with connectivity which was termed as an era of digital access. The information sharing was mostly done via emails, websites, and search engines like Google and Yahoo. In the second phase, electronic commerce was realized, and the digital access was enhanced with intensive business phase. Various portals tied up to boom economy through electronic media. For example, the payment gateway got into tied up with some websites, search engines like search engine optimization (SEO) in order to achieve the best E-commerce transactions. Soon, the need of interactive was felt and realized. This was more preferred than email texting. Multimedia applications like video and audio were spread through websites, and afterwards these websites were terms as portals that carry many features for flexible information sharing.
The third phase was defined as immerse experience and named as digital interaction. The above phases enhanced in such a way that computer networks were revolutionized. The need of using sensor devices and their integration was felt. Connectivity between objects, and sensors to devices was indeed necessary. This was yet another revolutionizing concept to get responsive connectivity to services. The fourth phase was termed as internet of things (IoT). The specialty of IoT is the connection without connected.
Table 2 summarizes different IoT applications and their capabilities. The first characteristic of IoT applications is local sensing and sharing which have the capability to access locations of IoT terminals. The end nodes provide services based on collected location information. This location information is determined through GPRS, cell ID, RFID and also contains the relative and absolute positions between locations. Location sensing and sharing also include the following terms, e.g. mobile tracking, traffic information management, and feet management.
The environmental IoT sensor collects all physical and chemical parameters by locally and widely deployed terminals in the environment. In most cases, the environmental sensor includes information that is related to temperature, humidity, pollution, etc. It also includes environment detection and medical monitoring. The third characteristic of IoT applications—remote controlling manages the IoT terminals and executes functions based on the information collected from end nodes and user requirements. It also includes disaster recovery and appliance control.
Ad-hoc networking defines the capability of IoT for self-organization of network with IoT sensor nodes being designed according to user requirements, e.g. a vehicle network. Lastly, IoT provides secure communication between platforms and IoT-end terminals based on service demands. IoT applications consist of different types of capability based service demands.
2.2 IoT and digitization
Digitalization is a fairly broad term, for example scanning a document to create a digital PDF file is considered as digitalization. Moving to a process where invoices are processed online could be considered digitalization. IoT is a product of digitalization which refers to devices and physical objects with digital components (e.g. smart watches, digital assistants like Alexa and Google Home, virtual receptionists in buildings). IoT and digitization are terms used interchangeably. In most contexts, this duality is fine, but there are main differences between them. At a high level, IoT focuses on connecting “things” such as objects and machines to a computer network. IoT is a well-understood term used across the industry. On the other hand, digitization can mean different things to different people but generally encompasses the connection of “things” with the data it generates and the business insights that result [46]. Similar digital identities with physical devices can be hard to configure.
In the coming years, IoT and digitization will witness real solutions that are dramatically changing the way we are living. There is no doubt that it will influence in any means. In one hand, IoT becomes the connection of cities, companies, and countries in a smart way whereas digitization is the most transformative means to ignite sustainable growth to improve society to drive innovation, growth and jobs of the future. With smart initiatives, we can percept a smart city ambition through IoT and digitization together. Sensors embedded throughout cities will connect everything from utilities to urban transportation, from entertainment to energy, and from policing to politics though digitization. Ultimately, the lives of human beings shall be exponentially improved. IoT and digitization will soon be a new phase of the Internet that brings many opportunities to revolutionize the world.
2.3 IoT impact
Around 14 billion “things” are connected to the Internet today [81]. Cisco system predicted that by 2020, this number will reach 50 billion [81]. UK government reported that this number could be even higher, in the range of 100 billion objects connected [81]. Cisco further estimated that these new connections will lead to $19 trillion in profits and cost savings [81]. The following demonstrates the impact of IoT through some real typical applications.
2.3.1 Connected roadway
People think about automated-driving cars for years. While this is now becoming a reality with well-known projects like Google’s self-driving cars, IoT is also necessary for implementing a fully connected transportation infrastructure [3]. Self-driving vehicles were allowed to better interact with transportation system around them through bidirectional data exchange [3]. They need always-on, reliable communication and data from other transportation-related sensors to reach their full potential. Connected roadways are fully integrated with surrounding transportation infrastructure [59, 93].
2.3.2 Smart connected buildings
In the past several decades, buildings became increasingly complex with systems overlaid one upon another, resulting in complex intersections of structural, mechanical, electrical, and IT components [62]. Over time, operational networks that support the building environment have matured into sophisticated systems [26]. However, for the most part, they were deployed and managed as separate systems that have little interaction with each other [25, 69].
2.3.3 Convergence of IT and OT
Information technology (IT) and operational technology (OT) are used for most parts lived in separate worlds [51]. IT supports connections to the Internet along with related data and systems whilst OT monitors and controls devices and processes on physical operational systems [7]. These systems include assembly lines, utility distribution networks, production facilities, roadway systems, and many more. Typically, IT did not get involved with the production and logistics of OT environments [97]. IT organization is responsible for information systems, and OT is responsible for devices and processes acting on industrial equipment. Traditionally, OT uses dedicated networks with specialized communications protocols to connect the devices. These networks have run separately from the IT networks [96].
To sum up, IoT is responsible for devices and processes acting on industrial equipment such as factory machines, meters, actuators, electrical distribution automation devices, and supervisory control and data acquisition systems. Over time, these operational networks have matured into sophisticated systems [69]. However, for most parts, they were deployed and managed as separated systems that have negligible interaction with each other [96]. The need of IoT with IoC has become compulsory for support systems.
2.4 IoT challenges
Many parts of IoT have become reality, but certain obstacles need to be overcome [49, 74, 76].
-
(a)
Simplified IoT architecture Each approach in IoT allows development of technologies and standards independently at each level or domain (Fig. 2). The commonality between those frameworks is that they recognize the interconnection of IoT endpoint devices to a network that transports the data used by applications, whether at the data center, in the cloud, or at various management points throughout the stack [11, 61].
-
(b)
Core IoT functional stack IoT networks are built around the concept of smart objects performing functions and delivering new connected services. These objects are smart because they use a combination of contextual information and configured goals to perform actions [80].
-
Things layer At this layer, physical devices need to fit constraints of environment in which they are deployed while still being able to provide information [11].
-
Communications network layer When smart objects are not self-contained, they need to communicate with an external system. In many cases, this communication uses a wireless technology. This layer has some sub layers as follows [87]:
-
Access network sub-layer The last mile of the IoT network is the access network, which is made up of wireless technologies such as 802.11ah, 802.15.4g and LoRa. The sensors connected to the access network may also be wired [15].
-
Gateways and Backhaul network sub-layer A common communication system organizes multiple smart objects in a given area around a gateway. The role of the gateway is to forward information through a longer-range medium (called the backhaul) to a head end central station where the information is processed [95].
-
Network transport sub-layer For success communication, network and transport layer protocols such as IP and UDP must be implemented to support the variety of devices to connect [45].
-
IoT network management sub-layer Additional protocols must be in places to allow head-end applications to exchange data with sensors. Examples include CoAP and machine to machine telemetry transport (MQTT) [53].
-
Application and analytics layer At the upper layer, an application needs to process collected data. It not only controls smart objects when necessary, but also makes intelligent decision based on information collected. In turn, it instructs things or other systems to adapt and change their behaviors appropriately [33].
-
-
(c)
Edge computing sometimes called the “mist” computing which aims to extend fog to furthest point possible, right into the IoT endpoint device itself. Fog computing solutions are being adopted by many industries. However, in recent years, the concept of IoT computing has been pushed even further to the edge, and in some cases resided directly in sensors and IoT devices [2, 85].
-
(d)
Security in IoT This includes disintegration of system design, unavoidable inheritance frameworks, shaky operational conventions, gadget uncertainty, reliance on outside sellers, and security information [14, 16].
From all the content presented in this section, it has been realized that IoT and IoC are correlated in several networks through various factors. Some challenges including lengthy battery power, sensor’s reliability, fetching accurate data from sensors, bandwidth, range of sensors, and interconnection reliability have been discussed. The similarity between frameworks has been analyzed. The interconnection of IoT endpoint devices to a network was recognized so that data used by such applications are stored and preserved either in data center or in the cloud. Besides, networks and transport protocols need to support them for reliable communication. The advancements of IoT and IoC show that vendors successful satisfied consumers in terms of products like cell phones, cars, TVs, smart home, smart kitchens, smart cars, etc. Thus, measuring reliability and availability of data fetched from IoT devices are necessary. Moreover, things connected in the IoT need to be validated efficiently.
2.5 Correlation of IoC and IoT
IoC and IoT have significant correlation in terms of bandwidth, range, and battery power. Table 3 describes the correlation based on these variables. The convergence of IoT and IoC brings significant bandwidth for WAN and Ethernet. It extends communication range from short range in IoT to wide range in IoC. However, this has negative effects on the cost of battery power, which is lengthy in IoT because of size and computing complexity of communication protocols. However, IoC is less efficient in terms of energy conservation.
In Table 3, bandwidth, range and battery are dependent variables used in Unification Engine. Battery power is not applicable in Ethernet and is merged with WAN. IoT devices can be analyzed with user’s identities uniformly though various communication channels to enable autonomous communication between connected things to accomplish smart services efficiently. The correlation can be distinguished through an example of accessing several integrated communication networks. Figure 3 shows the deployment of IoT to real applications through the platform of IoC from an evolutionary standpoint. In fact, there cannot be a genuine IoT without IoC since gadgets are not sufficiently brilliant to give enough recommendation to clients.
2.6 Availability and reliability of IoT devices
IoT has become a broad area where objects from consumer products are connected to build up a modern smart society. Despite of millions of users having all these services nowadays, challenges are still lying on the ground i.e. defining and computing of reliability and availability measures of these devices. When these devices are under use, a lot of untoward incidents occur these days. For example, if a smart system is suddenly crashed or burnt, interconnected devices may catch fire. Measuring the reliability and availability of data fetched from IoT devices are indeed necessary. Moreover, things connected in the IoT need to be validated efficiently. Undoubtedly, despite of these several issues, IoT has been exponentially used by consumers, and reshaped our day-to-day issues from healthcare to manufacturing.
IoT availability involves reliability and recoverability. IoT availability is driven by the increased demand around cloud computing and many other services, e.g. in software as a service (SaaS). Computers, storage devices are systematically managed. Many devices operate remotely without any human interaction. There is indeed urgent requirement of IoT enabled services with high degree of reliability. A highly capable IoT environment is needed to avoid fault tolerance, aero tolerances, sensor failures, absurd data that may arise from interconnected IoT devices.
2.7 Pros and cons of IoT
At the establishment level, IoT settles a portion of issues, for instance, information extraction conceivable from several canny gadgets examined with numerous online apparatuses. Bugs were settled online without illuminating clients. Data are again gathered and used to determine different procedures and choices. For example, an IoT-empowered lighting framework can change itself naturally in view of encompassing lighting levels, climate conditions, current inhabitance stack, and expected work process designs. Since more information is assembled, the framework can learn about inhabitants’ propensities and lighting needs, and alter appropriately. The processing and accessing of any resources take much time and money. This is an important factor to demonstrate benefits and reasons why IoTs are useful for future perspective [45, 52, 56].
The advantages of IoT are summed up as follows: (a) we produce billions of data in our daily life which can be in raw forms. Thus, IoT helps us to connect those data automatically without any further actions; (b) the accessing and processing time for the data are less. People will save money and efforts; (c) IoTs are also useful for monitoring devices that are connected with environments. For example, if you are out of station and want to monitor your smart farm house, this can be easily done by a smart phone.
However, there are still some disadvantages of IoT: (a) because the number of devices increases rapidly, it is required that they must have IP addresses to connect with the center, and most importantly all need compatibility for tagging and monitoring devices; (b) Large numbers of devices connected through the network increase the complexity of the network. If any failure occurs in the main system, then the entire network goes down; (c) the largest drawback of IoT is privacy, security, and trust. If any system is designed for a large network, there is possibility of hacking for them.
As clearly mentioned, IoT have some disadvantages in the early stage of developments. However, the advantages overcome those issues by saving more time and money.
3 Class review of IOT with IOC
3.1 Taxonomy
Figure 4 depicts new handshaking model with all techniques that have been confined for each layer in this review. The essential part of framework is the Perception layer. It assembles data using sensors, which are the most basic drivers of IoT. The accompanying compositional section that we ought to look at is IoC. Particular substances pass on the framework using different actions of IoT and IoC. Middleware enhances interoperability of IoT and makes it easy to offer different sorts of organizations (IoC). The classification delineates progressions in IoT regarding IoC and is assembled in view of four approaches as follows.
IoT introduces an ecosystem of content (e.g. offline and online). The best example for the online is weather forecasting from smart devices. From IoT to IoC, we see that there is an emergence of “Things” as Content Platforms, which are an extension of “mobile” platform proliferation across smartphones, tablets, wearables, etc. In fact, content will increasingly define even how consumers interface with their products.
3.1.1 The working methodology of the standalone IoT
Previously, networking standards used in IoT were based on three basic network topologies: P2P, hybrid, and mesh [45]. However, the current IoT technologies have varieties of wireless technologies. Figure 5 depicts the mechanisms of IoT in which IoT is dependent on requirements of a particular application [64, 66]. Parameters of these applications may be range, power consumption, data usage, and scalability. Considering connection technologies, both wireless and wired technologies are involved in IoT communications. Practically, every communications technology could be implemented in IoT [36].
Gateway plays a vital role in IoT and communication networks as it maps between IoT server and sensor data. It also enables interoperability with many IoT peripheral devices. Further, the IoT server distributes tasks over different devices in the network; thus enabling interconnection between various technologies. However, there are several issues while considering IoT only such as,
-
1.
Achieving quality of service (QoS): QoS is highly affected by delay in IoT network and delay due to multi-hop.
-
2.
Channel access delay: Collisions are likely to be created due to which additional exponential delays in the network may occur.
3.1.2 The working methodology of the standalone IoC
From Fig. 6, it has been found that IoC has some advantages such as universal access to any user with simplified and unified perspectives of information because of streamlined IoT and IoC organization and reception of self-benefit applications.
3.1.3 The difference and novelty of the handshaking model against the standalones
Figure 7 points out the differences of the handshaking model against the standalones:
-
1.
Decisions are smarter as the handshaking model describes contextual analysis and harvesting of the knowledge.
-
2.
The handshaking model can handle multidisciplinary domains with various incompatible data; thus yielding out unified intelligent solutions.
-
3.
The handshaking model gives managed services despite of a huge number of sensors deployed and communication channels. This is due to secured remote management in IoC and reliable quality of services in IoT.
-
4.
The functional approaches by using both IoT and IoC lead to primitive solutions i.e. if one of the solutions fails, the working model initializes an alternative solution so that end users become unaware of fault occurred.
-
5.
The handshaking model is independent on any domains.
-
6.
The handshaking model is completely independent on any application.
-
7.
The simplicity to build the handshaking model is one of the novelties.
-
8.
The handshaking model has low power consumption at IoT server.
-
9.
Interconnection of end-to-end devices in the handshaking model is highly efficient.
-
10.
In the handshaking model, the gateway is required to provide protocol translation and functional mapping between server and sensor data as shown in Fig. 7.
-
11.
The handshaking model enables interoperability with IoT peripheral devices and control stations. Therefore, it is not necessary to concentrate all of them in a single gateway.
-
12.
The handshaking model achieves high quality of service (QoS).
For more details of discussion, please refer to [64, 70, 76, 81,82,83, 86, 89,90,91, 93, 94, 96].
3.2 Empirical approach
The empirical approach includes researches with verification by observation or experience rather than theory or pure logic. In what follows, we summarize the main objectives and techniques of the researches in this group followed by their common drawbacks at the end.
Dohr et al. [21] proposed ambient assisted living approach that incorporates a specialized framework to help elderly individuals in their everyday routine. However, the work was completely relied on observations. Likewise, Atzori et al. [7] studied the most imperative parts of IoT. Another work published by Weber [84] discussed concept privilege to data arrangements that makes utilization of instruments of IoT, management on IT-security enactment, arrangement of components of IoT.
Atzori et al. [6] presented a novel worldview, social internet of things (SIoT), in view of social connections among objects. Through the SIoT, the ability of people and gadgets to find, select, and utilize objects with their administrations is augmented. Bandyopadhyay and Sen [10] introduced key specialized drivers, potential applications, issues and future research territories. Zhou and Chao [97] planned a proficient media-mindful security structure for encouraging different interactive media in IoT. Suo et al. [77] audited security in IoT, and dissected security qualities and prerequisites from four layers including perceptual layer, organize layer, bolster layer and application layer. The examination status from encryption component, correspondence security, ensuring sensor information, and encryption were examined. Miranda et al. [55] utilized smartphones to enhance joining with the IoT, which opened a new approach for IoT towards Internet of People. Hasan and Curry [32] proposed an approach which stresses a specialist’s point of view for building software that handles heterogeneity of IoT. Ma and Liu [52] presented foundation and related innovations of IoT and examined destinations. At that point, difficulties and key logical issues required in IoT development were shown.
In short, all the above papers either have either observations or theoretical discussion. We did not find any relevant logic through which the papers can be realized.
3.3 Computing approach
This approach emphasizes the existing computing models with respect to some attributes of IoT and distributed computing.
Sun et al. [76] proposed a pre-caution framework in light of IoT and distributed computing refined with capacities of constant observing of immersed line, seized water level and dam deformational. Likewise, Bonomi et al. [12] contended the same attributes as those of Sun, Zhang and Li [76] such as low inertness and attentiveness for various basic IoT administrations and applications such as Connected Vehicle, Smart Grid and Smart Cities. Similar researches can be found in Khan et al. [42] in which current improvement distorts, on-exclusive design of IoT, and conceivable future applications were addressed. However, the authors only conjectured key difficulties related with the advancement of IoT.
Zhang et al. [93] proposed an approach for a weighted topology of remote sensor systems in light of neighborhood world hypothesis for IoT. Stankovic [74] gave a premise about open research issues in IoT, and visualized a dream for how IoT could change the world in inaccessible future with eight key research themes. Wan et al. [82] proposed a plan of actions based on platform production services (PPS) and then applied it to vehicle maintenance services. Both IoT detecting structure between clouds computing are the vital factors in actualizing PPS plan of actions. Clohessy et al. [18] portrayed the idea of a smart city and investigated the capability of cloud computing to empower advancement for smart cities. They explored cutting edge related to choice of clouds by global governments, and presented a future research guide for cloud encouraged smart city improvement. Yau and Buduru [91] introduced a compelling way to deal with smart arrangements for mobile IoT applications. Yao et al. [90] introduced an IoT framework which flawlessly incorporates virtual and physical universes to proficiently oversee things of interest (TOIs), where services and assets offered by things can be observed and amassed for esteem included services by clients. Sicari et al. [70] introduced a study of innovations, applications and research challenges for IoT.
However, those researches in this group are still lag behind realization. They would have been much better if the authors proposed their models with at least virtual realization.
3.4 Innovative application approach
There have been some innovative advancement applications of IoT with IoC since 2014. By this time, many gadgets, sensor-based devices and interconnected devices are available for end users. Based on the working methodology of these gadgets, sensor based devices and their interconnectivity; many works have tremendously upgraded innovative applications of IoT with IoC as below.
Guo et al. [26] introduced entrepreneurial IoT, which is shaped in light of Ad-hoc, sharp systems administration of gadgets (e.g. cell phones and brilliant vehicles) utilizing short-run radio methods (e.g., Bluetooth and Wi-Fi). Gubbi et al. [25] exhibited a cloud driven vision for overall usage of IoT. The key empowering innovations and application spaces were given. A cloud usage utilizing Aneka, which depends on communication of private and open cloud, was exhibited. Baccelli et al. [9] explored prerequisites for an operating system (OS) in IoT. They presented RIOT OS, an OS that expressly considers gadgets with insignificant assets. RIOT OS gives multithreading and ongoing abilities.
Sheng et al. [69] gave a short diagram of the IETF convention suite. Bekara [11] explored security issues and difficulties of IoT-based Smart Grid, and characterized significant benefits when managing Smart Grid security. Perera et al. [61] investigated and assessed research endeavors to check difficulty in handling in desktop, web, versatile, sensor systems, and unavoidable registering paradigms. Perera et al. [62] showed the idea of IoT detection and demonstrated how it fits with IoT. Aazam et al. [1] examined the growing IoT and their incorporation with distributed computing for provisioning effective usage of assets. Tao, Cheng, Da Xu, Zhang and Li [80] addressed issue of how to understand changes from generation situated assembling to benefit arranged assembling.
Unlike others, Chen et al. [15] discussed challenges on innovations, applications, and institutionalization, and furthermore proposed an open and general IoT design comprising of three stages to address difficulty. Zhang et al. [95] started with general data security foundation of IoT and proceeded data security. At last, they additionally brought up inquiry about headings that could be future works for security challenges of IoT. Kovatsch et al. [43] introduced a framework for adaptable IoT cloud administrations in light of CoAP propelled by demonstrated designs for Web servers.
Guo et al. [27] demonstrated the present status and advancement capability of smart tourism in China, and offered proposals for applications in China. Hiremath et al. [34] recalled an initiative to conceptualize IoT. Savazzi et al. [67] endeavored to give industry-standard strategies and systems supporting plant creator amid wireless coverage prediction, virtual network deployment and post-layout verification. Whitmore et al. [87] gave a flow condition of research on the IoT by looking at flow patterns and portraying challenges. They undermined IoT dispersion, showed open research inquiries and future bearings, and ordered an exhaustive reference rundown.
Desai et al. [20] proposed a passage and Semantic Web empowered IoT engineering to give interoperability between frameworks, which uses built up correspondence and information standards. Xu et al. [89] proposed a unique IoT design structure and executed the node from the current standards and IoT. Ray et al. [64] gave an instruction to elements of IoT and their difficulties and tradeoffs associated. Kamilaris and Pitsillides [38] reviewed the most critical works performed in the region of cell phone computing joined with the Internet/web of things. Saha et al. [66] displayed a concise diagram on various patterns of the IoT and additionally talked about the IoT impacts to our everyday life.
Pan and McElhannon [58] examined the key reason and research points. Zaidan et al. [92] gave a broad look for managing smart homes, IoT and related applications. Lyu et al. [50] proposed a lightweight demand and affirmation structure to determine the adaptability issue. Wang et al. [83] examined a safe cloud IoT to keep information secrecy when gathering, putting away and accessing IoT information.
In short, most of the above researches have tried to map smart grid to IoT, or introduced engineering framework so that it gets adapted with IoT. However, they lag behind absolute result orientation. They tried to correlate these devices via various networks and other interconnecting protocols, but failed to demonstrate the validity of results. Thus, transmission impairments, failure in various attacks on the network, and data corruption were neglected. The issues such as multiple intrusions in the cloud, realizing data with customer satisfaction were not handled effectively.
3.5 Implementation approach
Apart from the framework design, this approach shows the trends that researchers tried to implement their models with keeping view of faults and possible errors that may occur during implementation as well as deployment.
Lee and Lee [45] presented five IoT advancements that are basic in effective IoT based items. Three IoT classes were examined for big business applications to improve client values. Madakam et al. [53] gave a diagram of IoT, designs, fundamental advances. Hassanalieragh et al. [33] highlighted open doors and difficulties of IoT in understanding human services. Pandey et al. [60] proposed life-cycle tracking system of LED bulbs that provides a platform for users to track lifetime of a LED bulb. The benefit of using this model is that, if it is applied to all connected devices then it can also be integrated with big data.
Zhang and Liu [94] abridged enhancements for intelligent transport systems getting lessening air contamination and mishap. Internet of vehicles (IoVs) enable portable vehicles to foresee coming mischance and caution drivers in time or proactively take prudent activities to keep away from mishap. Likewise, creators have investigated arrange coding applications for expanding substance of transmission and enhancing communicate reliability. Singh and Singh [71] indicated associated vehicle designs for hazards free and quick driving in both individual and open vehicles. Web of vehicle’s dashboard camera was utilized to control and mishap anticipation as it can catch and offer continuous film into sound, content and video structures to related experts.
Laghari and Niazi [44] attempted to investigate utilization of agent-based modeling as a major aspect of the cognitive agent-based computing (CABC) system to display a Complex correspondence network issue. Adat and Gupta [2] assessed innovative advances on issues of security and individual protection in IoV including security and necessities, hurt sorts, and applicable arrangements. In the view of dynamic topological structures, colossal system measure, non-uniform appropriation of hubs, and versatile impediment, IoV frameworks confront different sorts of assaults that cause a few testing prerequisites in security and level of protection. Gardašević et al. [24] introduced the IoT architectural frames under regular standardization efforts, design issues in conditions of IoT software and hardware components as well as IoT applications. Rossi et al. [65] have shown the architectures involved digital processing platforms and summarized ultra-low-power microcontrollers and problems faced with ultra-low-power.
Kant and Pal [39] examined difficulties and potential methodologies that could be enhance. Gao et al. [23] proposed an approach that expands the security of IoT gadgets by concealing data for IP watermarking, digital fingerprinting, and lightweight encryption fragments operands and relating fundamental number-crunching tasks that can be completed for all applications. Sethi and Sarangi [68] proposed a categorization for IoT advancements and profiled a few applications that can possibly have a striking effect in human life. Ansari and Sun [5] proposed a Mobile Edge IoT by utilizing the fiber-wireless access methodology, the cloudlet idea and the software characterized networking system. Kaur et al. [41] proposed a SDN-based edge-cloud transaction to handle gushing enormous information wherein SDN gives an effective middleware support.
4 Discussion
If devices are not modeled by using both IoT and IoC, soon we will face with circumstances where smart devices are ready to show alerts but cannot send notification in time. For example, when we are out of home, our PCs at home may get data of our body temperature but cannot warn us about appropriate prescriptions. IoT labels our everyday items. Sensors (IoT) might be a couple with these labels to gather more data about regular items and those present around them (IoC). The same applies to different organizations wherein PCs would monitor the stock accessible (IoT) and keep up them to ideal levels (IoC). This requires a strict coherence between IoT and IoC. It is now essential to experience the interest and weaknesses found from the reviewed literature in Sect. 3.
4.1 Favorable circumstances using handshaking of IoT and IoC
-
Information The more the data, the simpler they will give correct choices.
-
Following PCs keep track both on quality and suitability of things at home. Knowing lapse date of items before one devours will enhance security and personal satisfaction. Likewise, it will never come up short on anything when required.
-
Time The measurement of time spared in observing and quantity of excursions would be huge.
-
Cash The budgetary angle is the best-preferred standpoint. This innovation could supplant people who are accountable for observing and looking after provisions.
4.2 Hindrances of using handshaking of IoT and IoC
-
Similarity Currently, there is no standard for labeling and observing with sensors. A uniform medium is required.
-
Unpredictability There are few open doors for disappointment with complex frameworks. For instance, two people may get messages that drain is finished, and it is possible that both of them may wind up purchasing the same. That abandons with twofold the amount required.
-
Protection/security Privacy is a major issue with IoT and IoC. For example, information about budgetary status must be encoded.
-
Wellbeing It is likely that product can be hacked and abused. The conceivable outcomes are inestimable. Medicine can be changed or record subtle elements can be hacked. Henceforth, all those dangers turn into the shopper’s obligation.
In spite of the fact that IoT has many drawbacks, its focal points of IoT with IoC cannot be disregarded. The time is not far when the IoT will be usually observed in family units and organizations. Endeavors should be made to discover approaches to battle its impediments.
4.3 Lessons learnt from the literature
-
Motivation It was indicated that IoT and IoC are motivated from remote sensing systems. The four approaches in this review showed that they did not only emphasize on remote sensing but also the communication through cloud.
-
Proficiency detection Efficient heterogeneous data detection in IoT and IoC is necessary. The related researches have suggested organization movement, information stockpiling, and vitality usage. Imperatively, IoT and IoC both settled and portable detected foundation and irregular testing. The handshaking model generalizes each aspect using IoT with IoC where data detection can be done. The handshaking model also predicts different applications with innovative devices.
-
Security and privacy Security has been discussed as a noteworthy concern. There are numerous ways that the framework could be assaulted such as handicapping the system accessibility, pushing wrong information into the system, getting to individual data. The three physical parts of IoT namely RFID, WSN and cloud are helpless against such assaults. Security is basic to any system and the primary line of barrier against information defilement. We have presented delicate uses of IoT and IoC to address sophisticated and highly integrated sensor devices. Indeed, more devices get interconnected more vulnerability is likely to occur. IoT technology alone cannot help in resolving security and privacy issues. It has been shown that IoT along with IoC absolutely fit for many purposes including security and privacy.
-
Quality of service QoS is required activity composes inside the system as well as the capacity of a solitary system to help applications without QoS trade off. This review introduced data captured by IoT devices. Cloud issues were also projected which has not been raised in the previous works.
-
IoT versus traditional communication approaches Energy efficient MAC protocol and routing protocols have been proposed for various TDMA, CSMA and FDMA domains. Here, we realized the handshaking model is applicable to all kind of existing networks. We found that reliable connection is one of the most emerging issues nowadays. The framework of IoT and IoC provides an efficient way to get through with the communication issues.
-
GIS based visualization The development from CRT to Plasma, LCD, LED, and AMOLED offered ascend to profoundly proficient information portrayal. New perception plans for portrayal of heterogeneous sensors in 3D scene that differs transiently must be produced. We found that data stored in cloud needs to be mapped with geographic information system (GIS) in order to fit with IoT so that a new structured remotely sensed data can be transmitted.
-
Cloud computing We realized that coordination of IoT and Cloud empowers the formation of keen conditions, for example, Smart Cities should have the capacity to (a) consolidate administrations and (b) help countless in a solid and decentralized way. The cooperation can automate and accelerate administrations as well as scaling up the use of sensors, devices in a smart and decentralized way. It is not only to wired and remote system conditions but also to all conditions imperatively.
4.4 Visualization for the trends of IoT and IoC
IoT and IoC are forecasted to be used extensively for solving complex logistics, manufacturing, services, and supply chain problems. Due to this, the development of IoT devices connecting with IoC grows exponentially. Figure 8 depicts the growth of IoT devices on the basis of services that they are likely to deliver in the coming years. IoT market grows from 15.4 billion devices (2015) to 30.7 billion devices (2020) and 75.4 billion devices (2025) with data source in [75]. Mckinsey [54] forecasts that IoT market size will be $900 million (2015), growing to $3.7 billion (2020) and $6.2 trillion (2025). Obviously, the needs of IoT with IoC is an obvious trend.
5 Conclusion and future works
In this paper, we have clearly indicated that the handshaking model of IoT and IoC guarantees a smart life in the future. Soon, clients’ concern will yield out to explain who needs to endure with converters and workarounds, which can make life pointlessly convoluted. For example, after a fast shopping list endorsement from an occupant, related things will be arranged on the web and automaton will fly in the coveted merchandise in the nick of time for supper. Another usage of IoT and IoC is in washing robots. As the robot is working, it is required to purge the clothes washer when it is done and put fitting garments into the dryer. Savvy refuse canister just converses with a robot and reveal to it such that it is full and the junk should be taken out. The robot at that point opens the entryway and puts things in the cooler. The robot thusly arranges the automaton to fly it to the landfill. All of these examples show the advantages and benefits of a handshaking between IoT and IoC.
To summarize the main findings, the major issues with IoT are secured provisioning, connecting devices, and safe and automated IoT. None of the recent papers have been able to solve them without IoT and IoC as devices will be simply not smart enough to provide enough value to their users. Hence, the handshaking model for IoT and IoC is helpful in this regard. For motivation, four approaches in this review showed that they did not only emphasize on remote sensing but also the communication through cloud. For proficiency detection, efficient heterogeneous data detection in IoT and IoC are necessary. For security and privacy, we have shown that IoT technology alone cannot help in resolving security and privacy issues. IoT along with IoC absolutely fits for many purposes including security and privacy. For quality of service, this review introduced data captured by IoT devices. For IoT versus traditional communication approaches, we found that reliable connection is one of the most emerging issues nowadays.
The framework of IoT and IoC provides an efficient way to get through with the communication issues. For visualization, we found that data stored in cloud need to be mapped with GIS in order to fit with IoT so that new structured remotely sensed data can be transmitted. Lastly, for Cloud Computing, we realized that coordination of IoT and cloud can automate and accelerate administrations as well as scaling up the use of sensors, devices in a smart and decentralized way. It is not only to wired and remote system conditions but also to all conditions imperatively. The following further directions should be investigated as follows:
-
1.
Reliable connection: is one of the most emerging issues nowadays. As an example, a modern office space includes a vast array of IoT-enabled devices. But without a reliable connection to the network, these intelligent devices are simply machines and they cannot monitor surrounding environment and make instinctive adjustments. They even cannot provide data to give the better decisions. Without IoT, network connectivity will be undependable, business processes will suffer. Thus, IoT with IoC must work in a handshaking mean.
-
2.
Data captured by IoT devices: data fetched by IoT devices sent to the cloud are used for many purposes, e.g. weather, stock values forecast. It is likely that one of these interconnected devices may be failed or broken down. In these kinds of scenarios, data captured and stored becomes dumb. Therefore, it is necessary for IoT and IoC to be mapped together in data capture.
-
3.
All these issues should be covered within specific applications of IoT.
-
4.
Sensor based development for specific IoT and IoC applications with energy reduction is another target [28,29,30, 40, 72, 73, 78, 79].
References
Aazam, M., Khan, I., Alsaffar, A. A., & Huh, E. N. (2014). Cloud of things: Integrating internet of things and cloud computing and the issues involved. In 11th international Bhurban conference on applied sciences and technology (pp. 414–419).
Adat, V., & Gupta, B. B. (2017). Security in internet of things: Issues, challenges, taxonomy, and architecture. Telecommunication Systems, 67, 1–19.
Al-Dweik, A., Muresan, R., Mayhew, M., & Lieberman, M. (2017). IoT-based multifunctional scalable real-time enhanced road side unit for intelligent transportation systems. In 2017 IEEE 30th Canadian conference on electrical and computer engineering (CCECE) (pp. 1–6).
Angelakis, V., Avgouleas, L., Pappas, N., Fitzgerald, P., & Yuan, D. (2016). Allocation of heterogeneous resources of an IoT device to flexible services. IEEE Infocom, 3, 1–10.
Ansari, N., & Sun, X. (2018). Mobile edge computing empowers internet of things. IEICE Transactions on Communications, 101(3), 604–619.
Atzori, L., Iera, A., & Morabito, G. (2010). The internet of things: A survey. Computer Networks, 54(15), 2787–2805.
Atzori, L., Iera, A., & Morabito, G. (2011). Siot: Giving a social structure to the internet of things. IEEE Communications Letters, 15(11), 1193–1195.
Atzori, L., Iera, A., & Morabito, G. (2017). Understanding the internet of things: Ddefinition, potentials, and societal role of a fast evolving paradigm. Ad Hoc Networks, 56, 122–140.
Baccelli, E., Hahm, O., Gunes, M., Wahlisch, M., & Schmidt, T. C. (2013). RIOT OS: Towards an OS for the internet of things. In 2013 IEEE conference on computer communications workshops (pp. 79–80).
Bandyopadhyay, D., & Sen, J. (2011). Internet of things: Applications and challenges in technology and standardization. Wireless Personal Communications, 58(1), 49–69.
Bekara, C. (2014). Security issues and challenges for the IoT-based smart grid. Procedia Computer Science, 34, 532–537.
Bonomi, F., Milito, R., Zhu, J., & Addepalli, S. (2012). Fog computing and its role in the internet of things. IN Proceedings of the first edition of the MCC workshop on mobile cloud computing ACM (pp. 13–16).
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing and internet of things: A survey. Future Generation Computer Systems, 56, 684–700.
Catarinucci, L., De Donno, D., Mainetti, L., Palano, L., Patrono, L., Stefanizzi, M. L., et al. (2015). An IoT-aware architecture for smart healthcare systems. IEEE Internet of Things Journal, 2(6), 15–526.
Chen, S., Xu, H., Liu, D., Hu, B., & Wang, H. (2014). A vision of IoT: Applications, challenges, and opportunities with china perspective. IEEE Internet of Things Journal, 1(4), 349–359.
Chen, Y., Zhou, J., & Guo, M. (2016). A context-aware search system for internet of things based on hierarchical context model. Telecommunication Systems, 62(1), 77–91.
Christoforou, E., Anta, A. F., Georgiou, C., & Mosteiro, M. A. (2014). Algorithmic mechanisms for reliable master–worker internet-based computing. IEEE Transactions on Computers, 63(1), 179–195.
Clohessy, T., Acton, T., & Morgan, L. (2014). Smart city as a service (SCaaS): A future roadmap for e-government smart city cloud computing initiatives. In Proceedings of the 2014 IEEE/ACM 7th international conference on utility and cloud computing (pp. 836–841). IEEE Computer Society.
Cresci, S., et al. (2017). Nowcasting of earthquake consequence using big social data. IEEE Internet of Computing, 14, 1–9.
Desai, P., Sheth, A., & Anantharam, P. (2015). Semantic gateway as a service architecture for IoT interoperability. In 2015 IEEE international conference on mobile services (MS) (pp. 313–319). IEEE.
Dohr, A., Modre-Opsrian, R., Drobics, M., Hayn, D., & Schreier, G. (2010). The internet of things for ambient assisted living. In 7th international conference on new generations in information technology (pp. 804–809).
Gabbai, A. (2015). Kevin Ashton describes ‘the Internet of Things’: The innovator weighs in on what human life will be like a century from now. Smithsonian Magazine, 8–15.
Gao, M., Wang, Q., Arafin, M. T., Lyu, Y., & Qu, G. (2017). Approximate computing for low power and security in the internet of things. Computer, 50(6), 27–34.
Gardašević, G., Veletić, M., Maletić, N., Vasiljević, D., Radusinović, I., Tomović, S., et al. (2017). The IoT architectural framework, design issues and application domains. Wireless Personal Communications, 92(1), 127–148.
Gubbi, J., Buyya, R., Marusic, S., & Palaniswami, M. (2013). Internet of things (IoT): A vision, architectural elements, and future directions. Future Generation Computer Systems, 29(7), 1645–1660.
Guo, B., Zhang, D., Wang, Z., Yu, Z., & Zhou, X. (2013). Opportunistic IoT: Exploring the harmonious interaction between human and the internet of things. Journal of Network and Computer Applications, 36(6), 1531–1539.
Guo, Y., Liu, H., & Chai, Y. (2014). The embedding convergence of smart cities and tourism internet of things in China: An advance perspective. Advances in Hospitality and Tourism Research (AHTR), 2(1), 54–69.
Hai, D. T., Son, L. H., & Le Vinh, T. (2017). Novel fuzzy clustering scheme for 3D wireless sensor networks. Applied Soft Computing, 54, 141–149.
Hai, D. T., Tam, N. T., Son, L. H., & Vinh, L. T. (2016). A novel energy-balanced unequal fuzzy clustering algorithm for 3D wireless sensor networks. In Proceedings of the 7th symposium on information and communication technology (pp. 180–186). ACM.
Hai, D. T., Tam, N. T., Son, L. H., & Vinh, L. T. (2016). Experimental analyses of Terrain factors to performance of sensor placement optimization in 3D environments. International Journal of Engineering and Technology, 8(6), 394–400.
Hammoudi, S., Aliouat, Z., & Harous, S. (2017). Challenges and research directions for internet of things. Telecommunication Systems, 67, 1–19.
Hasan, S., & Curry, E. (2015). Thingsonomy: Tackling variety in internet of things events. IEEE Internet Computing, 19(2), 10–18.
Hassanalieragh, M., Page, A., Soyata, T., Sharma, G., Aktas, M., Mateos, G., & Andreescu, S. (2015). Health monitoring and management using internet-of-things (IoT) sensing with cloud-based processing: Opportunities and challenges. In 2015 IEEE international conference on services computing (SCC) (pp. 285–292).
Hiremath, S., Yang, G., & Mankodiya, K. (2014). Wearable internet of things: Concept, architectural components and promises for person-centered healthcare. In 2014 EAI 4th international conference on wireless mobile communication and healthcare (Mobihealth) (pp. 304–307). IEEE.
Hu, L., Ong, D. M., Zhu, X., Liu, Q., & Song, E. (2015). Enabling RFID technology for healthcare: Application, architecture, and challenges. Telecommunication Systems, 58(3), 259–271.
Hu, P., Ning, H., Qiu, T., Xu, Y., Luo, X., & Sangaiah, A. K. (2018). A unified face identification and resolution scheme using cloud computing in internet of things. Future Generation Computer Systems, 81, 582–592.
Hu, P., Ning, H., Qiu, T., Zhang, Y., & Luo, X. (2017). Fog computing based face identification and resolution scheme in internet of things. IEEE Transactions on Industrial Informatics, 13(4), 1910–1920.
Kamilaris, A., & Pitsillides, A. (2016). Mobile phone computing and the internet of things: A survey. IEEE Internet of Things Journal, 3(6), 885–898.
Kant, K., & Pal, A. (2017). Internet of perishable logistics. IEEE Internet Computing, 21(1), 22–31.
Kapoor, R., Gupta, R., Kumar, R., Son, L. H. & Jha, S. (2018). New scheme for underwater acoustically wireless transmission using direct sequence code division multiple access in MIMO systems. Wireless Networks. https://doi.org/10.1007/s11276-018-1750-z.
Kaur, K., Garg, S., Aujla, G. S., Kumar, N., Rodrigues, J. J., & Guizani, M. (2018). Edge computing in the industrial internet of things environment: Software-defined-networks-based edge-cloud interplay. IEEE Communications Magazine, 56(2), 44–51.
Khan, R., Khan, S. U., Zaheer, R., & Khan, S. (2012). Future internet: The internet of things architecture, possible applications and key challenges. In 10th international conference on frontiers of information technology (pp. 257–260).
Kovatsch, M., Lanter, M., & Shelby, Z. (2014). Californium: Scalable cloud services for the internet of things with COAP. In 2014 IEEE international conference on the internet of things (IOT) (pp. 1–6).
Laghari, S., & Niazi, M. A. (2016). Modeling the internet of things, self-organizing and other complex adaptive communication networks: A cognitive agent-based computing approach. PLoS ONE, 11(1), e0146760.
Lee, I., & Lee, K. (2015). The internet of things (IoT): Applications, investments, and challenges for enterprises. Business Horizons, 58(4), 431–440.
Li, F., Zheng, Z., & Jin, C. (2016). Secure and efficient data transmission in the internet of things. Telecommunication Systems, 62(1), 111–122.
Li, X., Li, D., Wan, J., Liu, C., & Imran, M. (2018). Adaptive transmission optimization in SDN-based industrial internet of things with edge computing. IEEE Internet of Things Journal,. https://doi.org/10.1109/JIOT.2018.2797187.
Li, X., Li, D., Wan, J., Vasilakos, A. V., Lai, C. F., & Wang, S. (2017). A review of industrial wireless networks in the context of industry 4.0. Wireless Networks, 23(1), 23–41.
Liew, C. S., Ang, J. M., Goh, Y. T., Koh, W. K., Tan, S. Y., & Teh, R. Y. (2017). Factors influencing consumer acceptance of internet of things technology. In The internet of things: Breakthroughs in research and practice (pp. 71–86). IGI Global.
Lyu, X., Tian, H., Jiang, L., Vinel, A., Maharjan, S., Gjessing, S., et al. (2018). Selective offloading in mobile edge computing for the green internet of things. IEEE Network, 32(1), 54–60.
Ma, H. D. (2011). Internet of things: Objectives and scientific challenges. Journal of Computer Science and Technology, 26(6), 919–924.
Ma, H., & Liu, W. (2017). Progressive search paradigm for internet of things. IEEE MultiMedia,. https://doi.org/10.1109/MMUL.2017.265091429.
Madakam, S., Ramaswamy, R., & Tripathi, S. (2015). Internet of things (IoT): A literature review. Journal of Computer and Communications, 3(5), 164–175.
Mckinsey. (2017). IoT markets. https://www.forbes.com/sites/louiscolumbus/2016/11/27/roundup-of-internet-of-things-forecasts-and-market-estimates-2016.
Miranda, J., Mäkitalo, N., Garcia-Alonso, J., Berrocal, J., Mikkonen, T., Canal, C., et al. (2015). From the internet of things to the internet of people. IEEE Internet Computing, 19(2), 40–47.
Mollah, M. B., Azad, M. A. K., & Vasilakos, A. (2017). Secure data sharing and searching at the edge of cloud-assisted internet of things. IEEE Cloud Computing, 4(1), 34–42.
Naranjo, P. G. V., Pooranian, Z., Shojafar, M., Conti, M., & Buyya, R. (2017). FOCAN: A fog-supported smart city network architecture for management of applications in the internet of everything environments. Preprint arXiv:1710.01801.
Pan, J., & McElhannon, J. (2018). Future edge cloud and edge computing for internet of things applications. IEEE Internet of Things, 5(1), 439–449.
Pan, J., Jain, R., Paul, S., Vu, T., Saifullah, A., & Sha, M. (2015). An internet of things framework for smart energy in buildings: Designs, prototype, and experiments. IEEE Internet of Things, 2(6), 527–537.
Pandey, S., Paul, A., & Chanu, L. J. (2015). Life-cycle tracking system of home automation devices (LED Bulbs). In 2015 International conference on green computing and internet of things (pp. 1582–1585).
Perera, C., Zaslavsky, A., Christen, P., & Georgakopoulos, D. (2014). Sensing as a service model for smart cities supported by internet of things. IEEE Transactions on Emerging Telecommunications Technologies, 25(1), 81–93.
Perera, C., Zaslavsky, A., Christen, P., & Georgakopoulos, D. (2014). Context aware computing for the internet of things: A survey. IEEE Communications Surveys and Tutorials, 16(1), 414–454.
Qin, Y., Sheng, Q. Z., Falkner, N. J., Dustdar, S., Wang, H., & Vasilakos, A. V. (2016). When things matter: A survey on data-centric internet of things. Journal of Network and Computer Applications, 64, 137–153.
Ray, S., Jin, Y., & Raychowdhury, A. (2016). The changing computing paradigm with internet of things: A tutorial introduction. IEEE Design and Test, 33(2), 76–96.
Rossi, D., Loi, I., Pullini, A., & Benini, L. (2017). Ultra-low-power digital architectures for the internet of things. In M. Alioto (Ed.), Enabling the internet of things (pp. 69–93). Berlin: Springer.
Saha, H. N., Mandal, A., & Sinha, A. (2017). Recent trends in the internet of things. In 2017 IEEE 7th annual computing and communication workshop and conference (CCWC) (pp. 1–4). IEEE.
Savazzi, S., Rampa, V., & Spagnolini, U. (2014). Wireless cloud networks for the factory of things: Connectivity modeling and layout design. IEEE Internet of Things Journal, 1(2), 180–195.
Sethi, P., & Sarangi, S. R. (2017). Internet of things: Architectures, protocols, and applications. Journal of Electrical and Computer Engineering, 14(2), 35–41.
Sheng, Z., Yang, S., Yu, Y., Vasilakos, A., Mccann, J., & Leung, K. (2013). A survey on the IETF protocol suite for the internet of things: Standards, challenges, and opportunities. IEEE Wireless Communications, 20(6), 91–98.
Sicari, S., Rizzardi, A., Cappiello, C., Miorandi, D., & Coen-Porisini, A. (2017). Toward data governance in the internet of things. In R. R. Yager & J. Pascual Espada (Eds.), New advances in the internet of things (pp. 59–74). Cham: Springer.
Singh, D., & Singh, M. (2015). Internet of vehicles for smart and safe driving. In 2015 IEEE international conference on connected vehicles and expo (pp. 328–329).
Singh, K., Singh, K., Son, L. H., & Aziz, A. (2018). Congestion control in wireless sensor networks by hybrid multi-objective optimization algorithm. Computer Networks, 138, 90–107.
Son, L. H., & Thong, P. H. (2017). Soft computing methods for WiMax network planning on 3D geographical information systems. Journal of Computer and System Sciences, 83(1), 159–179.
Stankovic, J. A. (2014). Research directions for the internet of things. IEEE Internet of Things Journal, 1(1), 3–9.
Statista. (2018). Internet of things (IoT) connected devices. Available at: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/.
Sun, E., Zhang, X., & Li, Z. (2012). The internet of things (IOT) and cloud computing (CC) based tailings dam monitoring and pre-alarm system in mines. Safety Science, 50(4), 811–815.
Suo, H., Wan, J., Zou, C., & Liu, J. (2012). Security in the internet of things: a review. In 2012 international conference on computer science and electronics engineering (Vol. 3, pp. 648–651).
Tam, N. T., Hai, D. T., Son, L. H., & Vinh, L. T. (2018). Improving lifetime and network connections of 3D wireless sensor networks based on fuzzy clustering and particle swarm optimization. Wireless Networks,. https://doi.org/10.1007/s11276-016-1412-y.
Tam, N. T., Thanh, H. D., Son, L. H. & Le, V. T. (2015). Optimization for the sensor placement problem in 3D environments. In 2015 IEEE 12th international conference on networking, sensing and control (ICNSC) (pp. 327–333). IEEE.
Tao, F., Cheng, Y., Da Xu, L., Zhang, L., & Li, B. H. (2014). CCIoT-CMfg: Cloud computing and internet of things-based cloud manufacturing service system. IEEE Transactions on Industrial Informatics, 10(2), 1435–1442.
Walport, M. (2015). The internet of things: Making the most of the second digital revolution. UK Government Chief Scientific Adviser (pp. 9–16).
Wan, J., Zou, C., Zhou, K., Lu, R., & Li, D. (2014). IoT sensing framework with inter-cloud computing capability in vehicular networking. Electronic Commerce Research, 14(3), 389–416.
Wang, W., Xu, P., & Yang, L. T. (2018). Secure data collection, storage and access in cloud-assisted IoT. IEEE Cloud Computing. https://doi.org/10.1109/MCC.2018.111122026.
Weber, R. H. (2010). Internet of things-new security and privacy challenges. Computer Law and Security Review, 26(1), 23–30.
Weinberg, B. D., Milne, G. R., Andonova, Y. G., & Hajjat, F. M. (2015). Internet of things: Convenience vs. privacy and secrecy. Business Horizons, 58(6), 615–624.
Wen, Y., & Li, Z. (2013). A service-integrated sensor network middleware applied to industrial solutions of IoT related. Telecommunication Systems, 53(1), 61–68.
Whitmore, A., Agarwal, A., & Da Xu, L. (2015). The internet of things—A survey of topics and trends. Information Systems Frontiers, 17(2), 261–274.
Wu, M., Tan, L., & Xiong, N. (2016). Data prediction, compression, and recovery in clustered wireless sensor networks for environmental monitoring applications. Information Sciences, 329, 800–818.
Xu, Y., Mahendran, V., & Radhakrishnan, S. (2016). Internet of hybrid opportunistic things: A novel framework for interconnecting IoTs and DTNs. In 2016 IEEE conference on computer communications workshops (INFOCOM WKSHPS) (pp. 1067–1068). IEEE.
Yao, L., Sheng, Q. Z., & Dustdar, S. (2015). Web-based management of the internet of things. IEEE Internet Computing, 19(4), 60–67.
Yau, S. S., & Buduru, A. B. (2014). Intelligent planning for developing mobile IoT applications using cloud systems. In 2014 IEEE international conference on mobile services (MS) (pp. 55–62). IEEE.
Zaidan, A. A., Zaidan, B. B., Qahtan, M. Y., Albahri, O. S., Albahri, A. S., Alaa, M., et al. (2018). A survey on communication components for IoT-based technologies in smart homes. Telecommunication Systems. https://doi.org/10.1007/s11235-018-0430-8.
Zhang, D. G., Zhu, Y. N., Zhao, C. P., & Dai, W. B. (2012). A new constructing approach for a weighted topology of wireless sensor networks based on local-world theory for the internet of things (IOT). Computers and Mathematics with Applications, 64(5), 1044–1055.
Zhang, S., & Liu, E. (2015). Improving reliability of message broadcast over internet of vehicles (IoVs). In 2015 IEEE international conference on computer and information technology: Ubiquitous computing and communications: dependable, autonomic and secure computing: pervasive intelligence and computing (pp. 2321–2328).
Zhang, Z. K., Cho, M. C. Y., Wang, C. W., Hsu, C. W., Chen, C. K., & Shieh, S. (2014). IoT security: Ongoing challenges and research opportunities. IN 2014 IEEE 7th international conference on service-oriented computing and applications (SOCA) (pp. 230–234).
Zhou, L. (2013). Green service over internet of things: A theoretical analysis paradigm. Telecommunication Systems, 52, 1–12.
Zhou, L., & Chao, H. C. (2011). Multimedia traffic security architecture for the internet of things. IEEE Network, 25(3), 74–85.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Son, L.H., Jha, S., Kumar, R. et al. Collaborative handshaking approaches between internet of computing and internet of things towards a smart world: a review from 2009–2017. Telecommun Syst 70, 617–634 (2019). https://doi.org/10.1007/s11235-018-0481-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-018-0481-x