Abstract
The wireless sensor networks (WSNs) based on the IEEE 802.15.4 beacon enabled mode provide a deterministic resource allocation offered by the guaranteed time slot (GTS) mechanism which is ideal for real-time traffic applications that requires high quality of service (QoS). In the beacon enabled mode the active and optional inactive period is governed by superframe order (SO) and beacon order (BO). Adapting the duty cycle using the SO and BO is desirable to accommodate the changing context of the WSNs traffic for network optimisation. However, existing approaches assumed a fixed SO and BO and segregate the evaluation of the contention access period and the contention free period that forms the active segment. To improve the performance of the IEEE 802.15.4 protocol in respect of the trade-off between power consumption and end-to-end delay, within a required QoS, a combination of dynamic priorities for traffic differentiation and dynamic duty cycle adaptation in the GTS allocation process are introduced. This work demonstrates that the proposed solution provides significantly better performance than the standard allocation method by simultaneously satisfying QoS and service differentiation demands with considerable power savings which is essential for WSNs. The specific novel use of this solution is in an application scenario where the deployed network is situated in an assisted living environment with a rich suite of heterogeneous wireless based communications in place.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The wireless sensor networks (WSNs) based on the IEEE 802.15.4 standard provide a deterministic resource allocation offered by the guaranteed time slot (GTS) mechanism in the beacon enabled mode which is ideal for real-time traffic applications. In the beacon enabled mode, the nodes can transmit in the active period and return to sleep in the inactive period which facilitates low power consumption which is essential for WSNs. However, such a mechanism can cause long packet delay which makes it difficult to adhere to strict delay bounds to support the successful transmission of real-time data. Real-time applications require high quality of service (QoS) sensitivity such as bounded end-to-end delay and low Bit Error Rate (BER).
WSNs are wireless networks constructed from small, energy-efficient devices, with low processing power and traditionally applications had low QoS requirements. However with the growing number of sensor applications, higher QoS is required for example healthcare applications which requires a deterministic service offering [1]. Wireless sensor applications range from environmental surveillance, health monitoring using (body sensor networks (BSNs)) and home automation [2].
1.1 Proposed application scenario requiring dedicated resources
Each of these wireless sensor applications have their own unique QoS requirements. For example, consider a scenario of independent living for the elderly whereby sensor nodes are used to assist residents by providing real-time emergency communication and real-time monitoring and surveillance. Under normal circumstances the sensor nodes operate to monitor a patient’s condition (temperature, pulse, etc.) and patient’s location scheduled on a less frequent reporting interval. However when an emergency is detected for instance an abnormal reading (above a predetermined threshold) or irregular location or position, sensor information is forwarded more frequently to assess the situation and the wireless network must be able to adapt to operate accordingly. The emergency event suggests a requirement for a low-latency service that presents real-time traffic requirements such as bounded end-to-end delay and high QoS sensitivity. In such demanding operations, the wireless nodes are still expected to minimise the power consumption for an extended network lifespan in line with WSN characteristics.
However problems which are well documented in the literature still exist in providing this low-latency service as suggested in [3]: “One of the main challenges in Distributed Sensor Network research is to design efficient deterministic and quasi-deterministic sensor nodes”. The main factor which determines the extent to which the WSN can deliver this low-latency service is the access method and policies set for managing the bandwidth constrained communication medium.
1.2 Motivation
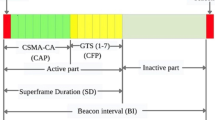
The IEEE 802.15.4 standard attempts to support this low latency service by providing a GTS facility for resource reservation for those applications that have deterministic bandwidth requirements and low delay constraints. Figure 1 shows the superframe structure employing the GTS.
The beacon interval is composed of an active and inactive period. The Contention Access Period (CAP) is based on slotted carrier sense multiple access with collision avoidance (CSMA/CA) and the contention free period (CFP) using GTS mechanism forms the active period. Although GTSs have been introduced in the IEEE 802.15.4 standard to allow applications to have service guarantees, the allocation mechanism described in the standard presents three main limitations in terms of flexibility and deployment in WSNs. Firstly, for each superframe (composed of sixteen equally sized time slots) only a maximum of seven GTSs can be allocated, forming the contention free period (CFP) also one GTS may utilize more than one time slot. Consequently once all seven GTSs have been allocated other devices requiring guaranteed service are not taken into consideration. This method of allocating resources is very restrictive. Secondly, each of the GTSs is assigned by a central controller called the PAN coordinator (PANC) in a first-come-first-served (FCFS) basis. Once all the seven time slots are occupied, any arriving high priority flow will be rejected.
Finally, in the GTS beacon enabled mode, it is possible to control the duty cycle by adjusting the superframe duration (SD) and the beacon interval (BI) that governs the active and the inactive period. Low duty cycle can be achieved by increasing the inactive period as power consumption in this region is very low. However, the inactive period can cause extended packet delay since a frame cannot be transmitted or received in this period. If the frame of a real-time application cannot satisfy latency requirements due to excessive packet delays, the frame will be dropped. Considering that WSN power resources are scarce, the GTSs time slots are limited, and do not support any kind of QoS or traffic differentiation. Therefore, introducing a GTS traffic differentiation and duty cycle adaptation for IEEE 802.15.4 WSN is necessary.
The motivation for the research outlined in our research paper is clearly defined by Noda et al. as follows in [4] “Wireless Sensor Networks (WSN) are seen as a viable alternative for monitoring, control and automation applications, provided they are made appropriately reliable and delays are bounded.
This paper has the following contributions:
-
It is the first paper to combine GTS traffic differentiation and duty cycle adaptation applicable to a healthcare application such as independent living
-
Secondly it proposes a realistic strategy on delivering real time traffic within a stipulated delay boundary
1.3 Scenario description
Figure 2 shows a scenario based on healthcare, namely independent living for the elderly which is the application considered in this paper. Suppose that in emergency situations, the emergency initiator node sends an emergency message to the PANC. Upon receiving this information, the PANC shall send a request only to the pre-determined node/s that require delay bound applications to change its critical tag from 0 (normal) to 1 (critical) and activate the delay threshold to run the required real-time applications. The detail on this procedure is not covered in the scope of this work. It is assumed that the device accepts this request and changes its critical tag and applications accordingly. It is envisaged that this procedure is to be developed at the application layer.
The sensor nodes with critical tag = 1 behaviour is now set for real-time applications. A real-time application means that the device has stringent timing requirements and bounded end to end delay. During emergency situations, the intended nodes are usually configured to a reduced interarrival time to provide a more robust communication process.
Based on these sensing applications shown in Fig. 2, it is clear that a traffic differentiation mechanism is required. Devices with critical tag = 0 continues to transmit in the CAP using slotted CSMA/CA as their traffic has no delay constraints while devices with critical tag = 1 will be slotted in the CFP utilising the GTS mechanism.
1.4 Related work
The performance of IEEE 802.15.4 beacon enabled mode with GTS allocation has been extensively investigated and among the earliest effort to investigate the GTS allocation defined in the IEEE 802.15.4 standard is by Koubaa et al. [5]. In the proposed scheme, called i-GAME, the objective is to enhance the bandwidth utilisation by allowing several devices to share the same set of GTSs in a round robin scheduling. This proposal improves the bandwidth utilisation and removes the limit of only seven devices that can have channel access within the CFP. However a mechanism for quantifying the flow characteristics and how the PANC enforces the admission control to use the shared GTS remains unanswered. These two challenges impose implementation difficulties for applications. In [6], the authors proposed a practical service differentiation mechanism in the CAP utilising the slotted CSMA/CA scheme for critical delay bound events. This paper proves that using differentiation strategies results in an improved performance for high priority frames and that priority queuing techniques reduces the average transaction delays. However this service differentiation strategy requires add-ons to the IEEE 802.15.4 MAC protocol.
In Tennina et al. [7] a cluster scheduling solution is proposed which allows network scalability whilst maintaining the ability to meet the QoS requirements. The work attempts to address synchronization for time sensitive WSNs. Multiple cluster networks are common and currently synchronization is available only in WSN star networks by the generation of periodic beacon frames. A synchronization mechanism based on time division clustering (TDCS) to build cluster-tree WSNs is proposed. The solution however requires add-ons to the existing Zigbee protocol.
Research by Mishra et al. [8] provides a scheduling model that attempts to meet the delay constraints of time-sensitive transactions. Time constraints meet ratio (TMR) was introduced and the on-line scheduling algorithm using a mathematical model proves to work with aperiodic and periodic messages even in overload conditions. However the drawback of the algorithm is that it may waste GTS timeslots towards the end of the CFP if the time required to slot a GTS is inadequate since it always allocates the GTSs from the first slot of the CFP.
A dynamic service differentiation scheme was proposed in [9] called D-SeDGAM, based on the static and transient aspects of QoS provisioning in WSN. The dynamic priority algorithm takes into account the delay, buffer and bandwidth metrics to prioritise nodes and construct the GTS scheduler. The admission control consists of a continuous process of monitoring capacity and allocating time slots to the node. The differentiation of service is effective with high priority applications being able to deliver more packets and having fewer rejected connections.
Admission control and service differentiation of packets in IEEE 802.15.4 MAC for controlling WSN with real-time applications appears promising. Nevertheless, three problems have not been addressed in employing IEEE 802.15.4 beacon enabled mode for WSN applications. First, all the work outlined above except for [9] segregate the evaluation of CAP and CFP for real-time applications rather than resolving it as a complete superframe utililising both CAP and CFP. Secondly, adapting the duty cycle using the superframe structure (SO and BO) is desirable to accommodate the changing context of the WSN traffic; however, it is always assumed fixed in existing approaches after the network starts. Thirdly, the optional inactive period was never considered in those methods. Manipulating the duty cycle can greatly improve power consumption since no transmission occurs in the inactive period and thus conserves node energy which is imperative for WSN.
We propose dynamic priorities (DP) as the traffic differentiation technique based on delay, packet loss and interarrival time metrics for the GTS allocation. The GTS dynamic duty cycle (DDC) is then triggered taking into account the most efficient duty cycle for power savings. The goal of these two techniques is to provide service differentiation and admission control while simultaneously satisfying the real-time application QoS requirement.
Our example real-time application used in this paper is interactive voice. This is supported by the specific scenario for in home support of the disabled and elderly. A number of projects use Voice over WSN (VoWSN) [10] for use with the disabled and elderly people. The main aim is to enable them to benefit from these new technologies. For example in an emergency situation the voice signals recorded in an environment will be transmitted to the network end-point in order to assist people needing urgent help.
The remainder of this paper is organised as follows; Sect. 2 gives an overview of the IEEE 802.15.4 MAC layer that administers the GTS beacon enabled mode. Section 3 describes the proposed dynamic priority for service differentiation and the dynamic duty cycle adaptation. The performance evaluation of the technique is discussed in Sects. 4 and 5 provides the conclusion and future work.
2 IEEE 802.15.4 overview
The IEEE 802.15.4 standard [11] defines physical (PHY) layer and medium access control (MAC) layer specifications for supporting low data rate and low power consumption in a wireless personal area network (WPAN).
2.1 Network architecture
The star and peer-to-peer (P2P) network topologies (Fig. 3) are supported in the IEEE 802.15.4 standard and the selection of which one to use depends on the application requirements. The IEEE 802.15.4 standard distinguishes two types of nodes; a full function device (FFD) which can operate in three different roles: it can be a PAN coordinator (PANC), a simple coordinator or an end device and the second type of node is a reduced function device (RFD) which can operate only as an end device. Therefore an FFD can communicate with either type of device, whereas an RFD can only interact with an FFD.
2.2 MAC layer
The MAC layer of the IEEE 802.15.4 supports two mechanisms for accessing the transmission channel; non-beacon enabled mode and beacon enabled mode. The non-beacon enabled mode does not support a power saving mechanism and it is using the simpler, unslotted CSMA/CA technique. Nodes in the unslotted CSMA/CA network compete to gain access to the transmission medium and do not provide any guarantee to deliver data frames within a certain deadline. This is not suitable for time-critical applications. However the advantage with regards to WSN application requirements is that unslotted CSMA/CA seamlessly allows scalability and self-organisation.
Alternatively the IEEE 802.15.4 standard offers an optional method for a deterministic service with the beacon-enabled mode. In this mode, a superframe structure is used which is bounded by network beacons sent by a PANC. The beacons are used to synchronise the devices in the WSN, to identify the WSN and to describe the superframe structure (Fig. 1). The length of these periods is specified by two system parameters i.e the superframe order (SO) and the beacon order (BO).
During the inactive period a node is allowed to power down and conserve energy (power saving mode). A slotted CSMA/CA mechanism is employed for channel access in the CAP. The time slots in the CFP are allocated on demand for exclusive channel access. Data frames transmitted in the CFP have a better chance for successful transmission due to the dedicated time slot. This deterministic service is called GTS. All contention based transactions are completed before the CFP begins. Also each device transmitting in a GTS ensures that its transaction is complete before the time of the next GTS or the end of the CFP. GTSs are continuously allocated by the PANC, either upon request from an RFD/ FFD or gateway specific resource request. The GTS transmissions are well suited for regular periodic sensor data with latency sensitive applications. As such, GTS traffic is considered independent of CSMA traffic in the IEEE 802.15.4 standard.
The beacon interval (BI) and the superframe duration (SD) are defined by Eqs. (1) and (2) through the two parameters; SO and BO as follows and simultaneously must satisfy Eq. (3).
3 Proposed methodology
The slotting of GTS is exclusively given to the nodes with critical tag = 1, hence to assess which of these nodes has higher priority among them and procure the GTS time slot (which is limited), a dynamic priority (DP) assessment is formulated. Then amongst the nodes listed in the priority list, a dynamic duty cycle (DDC) algorithm is initiated for admission control based on QoS requirement and duty cycle for efficient power consumption.
3.1 Traffic differentiation strategy
Service Differentiation in conventional wireless networks usually distinguishes between those applications that have delay constraints (i.e. real time—VoIP) and those applications that do not have delay constraints (i.e. non real-time—FTP). However, in WSN scheduling requirements differ from the traditional networks in many ways. Provision of a delay bounded service ensures a timely data delivery which is critical; because outdated data packets may not accurately reflect the state of the sensed scenario. For example, if an emergency has been reported that a patient has fallen down (from the tilt sensor) other activated sensors i.e. pulse, blood pressure and ECG must send the information with high priority. Secondly in relation to wireless transmission and protocols, packet loss occurs due to collisions, back-off period, retransmission failure as well as congested buffers, hence packet loss must be taken into account.
Thirdly, in a critical situation, the information obtained from the nodes must be regularly renewed to effectively assess the situation. Taken in the context of the scenario where a patient becomes incapacitated the tilt sensor becomes a critical device and may dynamically change its transmission strategy, for example by decreasing its traffic interarrival time to facilitate a more timely reporting mechanism.
This is perceived in the context that critical nodes will decrease the interarrival time during emergency situations. However among the nodes that is requesting for the GTS time slots, the strategy is to give high priority to the nodes using a larger interarrival time as their ability to report is less frequent.
Figure 4 illustrates this strategy. When a packet is dropped or lost during transmission, the lower interarrival time denoted by stream x will deliver the next packet in 2t (t + t) while the higher interarrival time (stream y) requires longer period; 4t (2t + 2t), hence it is to be given a higher priority.
3.1.1 Delay cost
Total packets received (TPR) signifies the total number of successful packets received for a particular node during the beacon interval (BI). Successful punctual packets (SPP) represents the packets that arrive before the threshold level. The late packet arrival ratio (LPAR) can be calculated as:
N is the number of nodes, \({\textit{LPAR}}_i\) is the late packet arrival ratio of node i, \({\textit{TPR}}_i\) is the total packet received of node i, and \({\textit{SPP}}_i\) is the successful punctual packets of node i
Finally the delay cost of node \(i (D_c^i)\) can be obtained as:
From Eq. (5), the product is a comparative value of each node’s state in relation to other nodes connected to the PANC. Higher priority is given to the node with the highest value which suggests that the node received less on time packets.
3.1.2 Packet loss cost
The packet loss cost is calculated in the same manner as delay cost but with different parameters. The Packet Loss Ratio (PLR) is calculated based on total packet received against total packet sent from each node:
\({\textit{PLR}}_i\) is the packet loss ratio of node i and \({\textit{TPS}}_i \) is the total packet sent of node i.
Then, the packet loss cost \((PL_c^i)\) can be expressed as:
A node with higher packet loss cost denotes higher priority.
3.1.3 Interarrival cost
Given the perception that in an emergency situation nodes reduce interarrival time to send more packets. The interarrival cost \((IAT_c^i)\) is then formulated:
3.1.4 Dynamic priority list
Conclusively, from all the cost metrics the dynamic priority (DP) list of all nodes used for scheduling can be formulated as:
\({\textit{DP}}^{i}\) is the dynamic priority of the ith node, \(D_c^i\) is the delay cost of node i, \({\textit{PL}}_c^i\) is the packet lost cost of node i, and \({\textit{IAT}}_c^i\) is the interarrival cost of node i
From Eq. (9), higher value of \({\textit{DP}}^{i}\) (nodes with poor QoS) receives a higher probability to be slotted into the GTS.
3.2 Dynamic duty cycle strategies
The duty cycle (DC) is defined as the fraction of time in which the sensor node is in the active period (SD) within a beacon interval (BI). The smaller the DC the lower is the energy consumption. The DC is formulated as follows:
The graph in Fig. 5 plots the DC time ratio against the possible combination of SOs and BOs. The graph illustrates that the DC ratio decreased significantly for the combination of a small SO against larger value of BO. The prohibited region is defined as the region that violates Eq. (3).
However fixing the network to a small DC can cause packet loss because of buffer overflows or delays because of the long inactive period which is not desirable in the case of real-time traffic. Consequently, the DC can be adapted instead for optimal energy efficiency in the beacon enabled mode.
The dynamic duty cycle procedure is used to find the optimal DC. The procedure for dynamic priority and dynamic duty cycle (DP & DDC) is explained in the flow chart shown in Fig. 6. First the PANC checks the number of nodes listed in the DP list. If it is more than seven nodes, then the seven uppermost nodes will be considered for the GTS time slots. The remainder from the list will be directed to transmit in the CAP using the slotted CSMA/CA mechanism. Step 1–3 is explained and elaborated in Sects. 3.2.1 and 3.2.2.
3.2.1 Beacon order (BO) determinants
In the IEEE 802.15.4 for 2.4 GHz spectrum and data link rate (C) of 250 Kbps, abaseSuperframeDuration (abSD) is represented with 960 symbols and each symbol comprise of 4 bits. Thus, abSD period \((\hbox {abSD}_{\mathrm{T}})\) can be expressed as:
Apparently BI coincides with the selection of BO and must be within the delay threshold \((\hbox {D}_{\mathrm{T}})\) which is application defined. The BO can then be expressed as:
Substitute Eq. (12) into Eq. (1) yield;
The algorithm for the selection of BO is carried out by PANC.
3.2.2 Superframe order (SO) determinants
The determination of an effective SO depends on the packet size, the occupied time slot per GTS and the total GTS bits that filled the CFP within a SD. The SO is determined for the seven nodes listed on the DP list based on 3 main steps:
Step 1 Ensuring that the generated packet size is suitable for one GTS time slot. At the initial stage SO is set at 0 and the time slot per GTS is equal to 1.
The packet size (PS) is defined as:
\({\textit{Pd}}^{i}\) is the data payload of node i, \({\textit{MAC}}_h^i\) is the MAC header of node i, \({\textit{PHY}}_h^i\) is the PHY header of node i, and \({\textit{IFS}}^{i}\) is the interframe spacing (long or short) of node i
A superframe duration (Eq.(2)) is subdivided into 16 equal size time slots with aBaseSuperframeDuration (abSD) is represented with 960 symbols (4 bits per symbol) [11]. The GTS time slot size (TTS) is calculated as:
The number of packets per GTS (NPGTS) time slot is then obtained as:
If NPGTS is equal to 0, then the SO needs to be upgraded to the next level because the GTS size cannot accommodate the PS, also the selected SO must comply to Eq. (3).
Step 2 To ensure that the arrival rate (total generated packets per second) can be served by the number of SD per second. If this is not satisfied the queue within the buffer will grow indefinitely. The total number of beacon interval (TBIPS) which the SD reside in one second is calculated as:
Substituting Eq. (1), in Eq. (17):
Finally, the number of packet that the ith node GTS \((GTSAc_{i})\) can accommodate per second can be formulated as:
\(IAT^{i}\) is the interarrival time of node i
If the GTSAc is less than the generated packets then the number of time slots per GTS need to be increased or the buffer will overflow over time.
The standard mandate that 440 symbols is the minimum number of symbols forming the CAP (aMinCAPLength). This is to ensure that the MAC commands can still be transferred to devices when GTSs are being used. Figure 7 illustrates this condition.
Step 3 To check that the total GTSAc is within the minimum CAP requirement.
Therefore, from Eq. (20) the GTS slot compliance can be obtained as:
If GTSSC is more than aMinCAPLength then all the packets are ready to transmit, else the maximum GTS slot node (\(\hbox {GTS}_{i}\) max) will reduce one time slot to satisfy the GTSSC condition.
The dynamic priority and dynamic duty cycle algorithm is carried out by PANC at the beginning of each beacon interval and the allocation is included into the next beacon. Even though the algorithm is performed at the cost of PANC power usage, it can typically be accommodated because the PANC is commonly powered locally but of course this depends on the types of applications being used.
4 Performance evaluation
In this section the performance of the proposed work compared to the standard IEEE 802.15.4 beacon enabled mode GTS allocation mechanism based on FCFS was evaluated. The performance measures the ability to prioritise nodes and satisfy the time constraints and its ability to select effective DC to achieve maximum power savings.
4.1 The simulation setting
Table 1 shows the IEEE 802.15.4 parameters defined in the evaluation. In IEEE 802.15.4 WSN, the Interframe Spacing (IFS) is equal to a Short IFS (SIFS) of 48 bits, for frame lengths smaller than aMaxSIFSFrameSize (144 bits). Otherwise, the IFS is equal to Long IFS (LIFS) of 160 bits, for a frame length greater than aMaxSIFSFrameSize bits and smaller than aMaxPHYPacketSize (1016 bits).
Three types of data payload size is used and listed in Table 2. The selection of the low payload size of 40 bits is to evoke the SIFS. For medium payload size of 384 bits was chosen, this was based on Allen [12] and Na [13] in their thesis that uses constant bit rates (CBR) for the data flows with constant payload size of 384 bits and 352 bits respectively to represent real-time application traffic. The 912 bits was chosen to represent high payload so as not to exceed the aMaxPHYPacketSize. These payloads are realistic based on the Xmesh sensing applications (with 5 different sensors sampled) developed by crossbow [14] with packet size between 232 bits (29 bytes) and 384 bits (48 bytes).
In voice communication, interactive voice requires an end-to-end latency of 250 ms or less, beyond which users notice a drop in interaction quality [15]. Other literature recommends that latency in WSN for real-time traffic should not exceed 100 ms [9, 16]. For this case we use 250 ms for the emergency delay threshold. Although a single access scenario is considered here previous work by one of the authors [17] in fixed networks takes the probability distribution of delay for a single node and shows that by using a convolution process the end-to-end delay distribution can be predicted. The same technique could be applied in a WSN scenario to obtain the full distribution of the end-to-end delay.
The network is a star topology with ten end point nodes and one PANC (Fig. 8) in a 20m radius. One of the end nodes (node_0_CAP) is used to generate background traffic in the CAP (Slotted CSMA/CA). It is assumed that the background traffic generated data frames have a constant size, hence the packet size is fixed at 300 bits (constant) and the interarrival time is set with exponential distribution. The interarrival time is then tailored to suit different offered load as explained later in Sect. 4.3. Note that exponential distribution is typically adopted by most simulation and analytical studies on CSMA/CA [9, 18, 19].
The other nine nodes are setup according to Table 3. These nodes are setup to transmit in the CAP using Slotted CSMA/CA during normal condition (critical tag = 0) and request for GTS during emergency situation. The payload and the interarrival time are configured to produce constant bit rate (CBR) traffic.
The simulation duration is set to 50 s and run with 3 different seed values were selected. We have verified that the results presented are equivalent to those obtained with higher simulation durations and the distribution of the results do not vary over time.
OPNET\(^{\mathrm{TM}}\) modeler [20] was used in developing the IEEE 802.15.4 simulation model. The OPNET\(^{\mathrm{TM}}\) modeler is based on a graphical user interaface (GUI) for discrete-event network modelling and simulation environment. OPNET was chosen because of its precision and its advanced GUI (OPNET supports the use of modeling different sensor-specific hardware, such as physical-link transceivers and antennas) [21]. Other simulators such as ns-2 have been used to evaluate WSN, however since the MAC protocols, packet formats and energy models were originally built for IP-based networks and later extended for wireless ad-hoc networks the results can be less accurate [22, 23].
The OPNET modeler native zigbee models implements the slotted and the unslotted CSMA/CA MAC protocols, however it does not support the GTS mechanism. To evaluate the GTS mechanism, the IEEE 802.15.4/Zigbee OPNET simulation model developed by the research group based in the research centre in real-time computing systems (CISTER) at the Polytechnic Institute of Porto (IPP), Portugal [24] is used.
4.2 Performance metrics
The average offered load \((\hbox {L}_{mac})\) at the MAC sublayer is introduced to represent the global load generated by all node’s depending on the inter-arrival time. Network Throughput (T) is defined as the fraction of traffic correctly received by the network analyser. The \(\hbox {T}(\hbox {L}_{mac})\) like mechanisms was first introduced in [25].
The performance metrics analysed in this study are the following:
-
Success Probability \(({P}_s)\) This metric is defined as (T) divided by \(\hbox {L}_{mac}\). It reflects the degree of reliability achieved by the network for successful transmissions. It is denoted by \(\hbox {P}_{\mathrm{s}}(\hbox {L}_{mac})\) the success probability as a function of the offered load \(\hbox {L}_{mac}\).
-
Delay (D) Is the average delay experienced by a data frame from the start of its generation at the application layer to the end of its reception by the PANC.
-
Power Consumption (E) This metric essentially gives the amount of energy used to transmit 1 bit successfully. It is computed as the average energy \((E_{avg})\) acquired from the battery power consumed in Joules (J) measured by the nodes divided by the successful transmitted bits abstracted from the success probability (250 Kbps). The battery model is based on the MicaZ power usage [26]. The Power Consumption is defined as:
$$\begin{aligned} Power\; Consumption= \frac{E_{avg}}{P_s (L_{mac}) \cdot C} \end{aligned}$$(22)
Lower power consumption per bit translates to a better power efficiency.
4.3 Results
Three transmission types are compared in this study; the transmission based on CAP (slotted CSMA/CA), the transmission based on the proposed dynamic priority and dynamic duty cycle (DP & DDC) and the standard IEEE 802.15.4 beacon enabled mode.
4.3.1 Success probability
Setting the SO and BO is one of the important tasks of the PANC. In this section the Success Probability is evaluated as the function of the offered load \((\hbox {L}_{mac})\) for different SO and BO values. Each curve corresponds to four different network loads (25, 50, 75 and 100 %) by adjusting the interarrival time of the background traffic node (node_0_CAP). Since the delay threshold is set at 250 ms, the BO is configured equal to 4 based on Eq. (12) and BI duration is then computed to be equal to 245.76 ms from Eq. (13). Figure 9a–e present the success probability \(\hbox {Ps}(\hbox {L}_{mac})\) based on the various initial inputs of SO and BO generally set during the pre-deployment stage by the network administrator.
It is observed that for the proposed DP & DCC algorithm, the SO and BO values change from the initial value based on the process flow (Fig. 6), in contrast to the SO and BO for the Slotted CSMA/CA and standard IEEE 802.15.4 GTS mechanism which is fixed. From the observation, \(\hbox {P}_{\mathrm{s}}(\hbox {L}_{mac})\) for all combination of SO and BO shows a similar trend that the lower offered load produced higher success probability. This is basically due to the fact that lower offered load creates less contention to the network, hence increasing the Success Probability. The increase of the initial SO from 0 to 4 has significant impact on the success probability. This is centered on two factors; one, as the SO increases the Superframe Duration increases accordingly allowing higher packet size to be transmitted; secondly, the increase in SO means more packets per GTS time slots can be achieved. However a unique situation occurs when SO and BO = 4, the slotted CSMA/CA and standard IEEE 802.15.4 transmission produce better results compared to the proposed DP & DCC. The explanation behind this phenomenon is that the SO for the DP & DCC has been dynamically changed from 4 initially to 3 which produced a lower duty cycle. This lower duty cycle has a substantial impact on the power consumption which will be shown in Sect. 4.3.3 later. Moreover, even though the success probability is higher compared to the DP & DCC for SO and BO = 4, the average packet delay for these two transmissions is far off the required QoS for lower value of SO when the average delay is factored in. This is explicitly depicted in Sect. 4.3.2. (Fig. 10a–d)
4.3.2 Average delay
Figure 10a–d shows the average GTS delay (primary y axis) and the number of GTS allocated (secondary y axis) as a function of the various SO and offered load. BO is fixed at 4 to comply with the delay threshold. CMSA/CA scheme is omitted in the evaluation as it does not cater for GTS.
The average GTS delay significantly decreases for higher SO in the standard IEEE 802.15.4 beacon enabled mode compared to the DP & DDC algorithm. It is also observed that for the standard IEEE 802.15.4, higher delays are experience with higher offered load. The is due to the fact that data transmission is less than the packet arrival rate because of the limited GTS time slot window, hence the buffer keeps on accumulating packets that contributes to the delay.
The DP & DDC algorithm delay measurement performs better and within the QoS requirement throughout various initial network settings for SOs and offered load. This is because of the dynamic nature of the proposed algorithm; first, the GTS time slot in DP & DDC algorithm can be expanded within the total GTS length limit (aMinCAPLength) to cater for more packet transmission per GTS, thus clearing up the buffer and reduces the queuing delay. Secondly, the DCC algorithm adjusts the SO so that all nodes listed in the DP successfully obtain a GTS time slot. This compares with the standard IEEE 802.15.4 that drops the packets if the packet size is bigger than the GTS time slot. The severity of the packet drop is noticed for lower SOs of the standard IEEE 802.15.4 simultaneously reflects on the success probability of the network.
4.3.3 Power consumption
Figure 11 shows the power consumption as the node consumed energy per number of correctly received bits for a WSN with different offered load and SO and BO combinations. For all offered loads and combinations of SOs and BOs, the proposed DP & DCC algorithm outperforms the slotted CSMA/CA and standard IEEE 802.15.4 beacon enabled mode with lower J/bits.
The slotted CSMA/CA requires higher J/bits among all three transmission type due to the contention and collision which requires retransmissions and higher power usage. It is also clear that higher offered load proportionally increases the power consumption for all transmission types which is intuitive because heavy load translates to higher transmission and power consumption. From Fig. 11, it is clear that the proposed DP & DCC scheme improves power efficiency.
5 Conclusion and future work
This paper presented a GTS time slot allocation techniques using dynamic priority for traffic differentiation and an adaptive dynamic duty cycle for admission control over the standard IEEE 802.15.4 beacon enabled mode. WSN resources are assigned dynamically to the devices depending on their QoS requirements and prioritized data (critical tag). Results shows that the DP & DDC approach is effective in the proposed scenario with high priority devices being able to deliver higher success probability especially for low Superframe Order and within the required delay requirement at a better power consumption compared to the existing GTS mechanism specified in IEEE 802.15.4 beacon enabled mode. For future work, the proposed algorithm is to be extended to consider buffer size dimensioning in the IEEE 802.15.4 beacon enabled network.
References
Ko, J., Lu, C., Srivastava, M. B., Stankovic, J. A., Terzis, A., & Welsh, M. (2010). Wireless sensor networks for healthcare. Proceedings of the IEEE, 98, 1947–1960.
Akyildiz, I. F., & Can Vuran, M. (2010). Wireless sensor networks: Advanced text in communications and networking. Hoboken: Wiley.
Sitharama Iyengar, S., Parameshwaran, N., Phoha, V. V., Balakrishnan, N., & Okoye, C. D. (2010). Fundamentals of sensor network programming: Applications and technology. Oxford: Wiley-IEEE Press.
Noda, C., Prabh, S., Alves, M., Boano, C., & Voight, T. (2011). Quantifying the channel quality for interference-aware wireless sensor networks 2011. In Proceedings of 10th international conference on information processing in sensor networks (IPSN) (pp. 167–168), ISBN 978-1-61284-854-9.
Koubaa, A., Alves, M., & Tovar, E. (2006). i-GAME: An implicit GTS allocation mechanism in IEEE 802.15.4 for time-sensitive wireless sensor networks. In 18th Euromicro conference on real-time systems (ECRTS ’06), Dresden (pp. 182–192).
Koubaa, A., Alves, M., Nefzi, B., & Song, Y.-Q. (2006). Improving the IEEE 802.15.4 slotted CSMA/CA MAC for time-critical events in wireless sensor networks. In 18th Euromicro conference on real-time systems (ECRTS ’06), Dresden.
Tennia, S., Koubaa, A., Daidone, R., Alves, M., Jurcik, P., Severino, R., Tiloca, M., Hauer, J., Pereira, N., Dini, G., Bouroche, M., & Tovar, E. IEEE 802.15.4 and zigbee as enabling technologies for low-power wireless systems with quality-of-service constraints, Springer Briefs in Electrical and Computer Engineering, Cooperating Objects, Springer, ISBN 978-3-642-37368-8.
Mishra, A., Na, C., & Rosenburgh, D. (2007, October). On scheduling guaranteed time slots for time sensitive transactions in the IEEE 802.15.4 Networks. In IEEE military communications conference (MILCOM ’07), Orlando, FL (pp. 1–7).
Villaverde, B. C., Rea, S., & Pesch, D. (2010, April). D-SeDGAM: A dynamic service differentiation based GTS allocation mechanism for IEEE 802.15.4 WSN. In 7th international conference on information technology: New generations (ITNG ’10), Las Vegas, NV (pp. 852–857).
Palafox, L. E., & Antonio, J. (2009). Garcia-Macias CICESE: Wireless sensor networks for voice capture in ubiquitous home environments, wireless pervasive computing 2009 IEEE Xplore. doi:10.1109/ISWPC.2009.4800614.
IEEE. (2006). IEEE 802.15.4 Ext Standard. Part 15.4: Wireless medium access control (MAC) and physical layer (PHY) specifications for low-rate wireless personal area networks (LR-WPANs). Piscataway, NJ: IEEE Press.
Allen, J. (2011). Development and evaluation of techniques for monitoring capacity and performance in wireless mesh networks. M.Sc., Software Engineering, Athlone Institute of Technology.
Na, C. W. (2011). IEEE 802.15.4 wireless sensor networks: GTS scheduling and service differentiation, PhD Thesis, Electrical and Computer Engineering, Virginia Polytechnic Institute and State University.
\(\text{ Crossbow }\_\text{ Technology }\). (2007, April). XMesh user’s manual. http://www.xbow.com/support/wUserManuals.aspx
Mangharam, R., Rowe, A., Rajkumar, R., & Suzuki, R. (2006). Voice over sensor networks, presented at the real-time systems symposium, Rio de Janeiro.
Lim, J.-H., & Jang, B. T. (2008). Dynamic duty cycle adaptation to real-time data in IEEE 802.15.4 based WSN. In 5th IEEE consumer communications and networking conference (CCNC ’08), Las Vegas, NV (pp. 353–357).
Stewart, R. (2002). End-to-end delay analysis for small/medium scale IP networks, Ph.D. Thesis, Queen Mary University of London.
Park, T. R., Kim, T. H., Choi, J. Y., Choi, S., & Kwon, W. H. (2005). Throughput and energy consumption analysis of IEEE 802.15.4 slotted CSMA/CA. IET Electronics Letters, 41, 1017– 1019.
Misic, J., Shafi, S., & Misic, V. B. (2005). The impact of MAC parameters on the performance of 802.15.4 PAN. Elsevier Ad Hoc Networks Journal, 3, 509–528.
OPNET official website. http://www.opnet.com.
Pratap Singh, C., Vyas, O. P., & Tiwari, M. K. (2008). A survey of simulation in sensor networks. In International conference on computational intelligence for modelling, control and automation, Vienna.
Huang, Y.-K., Pang, A.-C., & Hung, H.-N. (2008). An adaptive GTS allocation scheme for IEEE 802.15.4. IEEE Transaction in Parallel Distributed System, 19, 641–651.
Song, J., Ryoo, J.-D., Kim, S., Kim, J., Kim, H., & Mah, P. (2007, May). A dynamic GTS allocation algorithm in IEEE 802.15.4 for QoS guaranteed real-time applications. In IEEE international symposium on consumer electronics (ISCE ’07), Minneapolis, MN (pp. 1–6).
\(\text{ Research }\_\text{ Centre }\_\text{ in }\_\text{ Real-Time }\_\text{ Computing }\_\text{ Systems }\). CISTER. http://www.cister.isep.ipp.pt/.
Kleinrock, L., & Toubagi, F. A. (1975). Packet switching in radio channels: Part I—Carrier sense multiple access modes and their throughput-delay characteristics. IEEE Transactions on Communications, 23, 1400–1416.
Crossbow. (2004). MicaZ Datasheet - MPR2400CA. http://www.xbow.com/Products/Product_pdf_files/Wireless_pdf/MICAz_Datasheet.pdf.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Hassan, M.N., Murphy, L. & Stewart, R. Traffic differentiation and dynamic duty cycle adaptation in IEEE 802.15.4 beacon enabled WSN for real-time applications. Telecommun Syst 62, 303–317 (2016). https://doi.org/10.1007/s11235-015-0074-x
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-015-0074-x