Abstract
E-healthcare requires communication of patient report to a specialized doctor in a real time scenario. Therefore, any harm to patient medical data can lead to a faulty diagnosis that can be lethal for the patient. To ensure safe and secure communication in E-healthcare framework, an efficient reversible data hiding algorithm in encrypted domain has been proposed in this paper. The proposed algorithm gives a higher embedding rate by embedding a single bit of patient data in \(base_2\) numeral framework at every pixel of the cover image without any occurrence of underflow and overflow problem. The proposed method has been evaluated for content authentication by subjecting it to various image processing attacks. The experimental study reveals that for test images, proposed method has higher embedding rate than the compared methods, precisely recover patient information with an average value of Peak Signal Noise Ratio value of 48.13 dB between the cover image and stego image respectively. A comparison of the observed results with that of some state-of-art methods shows that proposed method performs better and as such is an ideal candidate for content authentication of Electronic patient information in a typical E-healthcare framework.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
E-healthcare systems are currently being integrated with conventional health care systems to acquire benefits of current-day technological advancements. The current E-healthcare system is doing telediagnosis of a patient, for this purpose, it requires medical reports of the patient including all image and text-based reports to share among its remote centers. Though E-healthcare systems bring the best medical facilities at your doorsteps, but during the implementation process experiences some challenges also. One of the fundamental concerns to be addressed for the implementation of E-healthcare system is security, authentication and copyright protection of the patient data respectively. Data hiding is the most robust tool that can address the above-mentioned issues. Various data hiding techniques are applied to protect data integrity and through these techniques, one can ensure data reliability. Sometimes, during the data hiding process, receiver is not able to reconstructed cover image successfully while in few applications, for example, medical, military, and law crime scene investigation, loss of cover image is not permitted. In these cases, an extraordinary sort of data hiding strategy called reversible or lossless data hiding is utilized. Reversible data hiding is meant to embed the secret message in cover image in such a way that at receiver end, secret message as well as original cover image is recovered successfully. Encryption is the most promising solution to maintain confidentiality and privacy of data. The integration of encryption and reversible data hiding technologies plays an important role in privacy protection. As a result, reversible data hiding (RDH) in encrypted image (RDH-EI) has attracted great attention from the research community. A detailed review of the stated work ([14, 17,18,19,20]) reveals that for medical images, reporting methods have low embedding capacity and they do not even support content authentication for patient data also. Keeping this in view, an enhanced reversible data hiding algorithm in encrypted domain to embed electronic patient information in cover image has been presented in this paper. In addition to embedding EPI, it also adds a fragile watermark for authentication of EPI at receiver end. Any type of attack during transmission process results in non-recovery of embedded watermark at receiver end that conveys that the EPI has been transformed during transmission process. The key features of the proposed algorithm are summarized as follows:
-
Paillier cryptosystem is used for encryption instead of conventional ones to avoid underflow and overflow problems during data embedding in cover image.
-
Binary EPI is embedded at every pixel of cover image to improve the embedding capacity.
-
A fragile watermark is used for content authentication at the receiver end.
The layout of paper is given as follows. Section 2 shows a compact written work outline about reversible data hiding methods. Section 3 described proposed algorithm in detail. Further, discussions are conducted in Section 4 for comparison of embedding performance and reversibility nature of proposed algorithm with the compared algorithms. Finally, paper is concluded in Section Section 5.
2 Literature Review
There is a lot of research done in reversible data hiding domain; some are illustrated as follows- Firstly, the idea of hiding information from attackers was presented by Shi [1]. Afterward, difference expansion based reversible data hiding technique was proposed by Tian[2], where a single bit was embedded between two close-by pixels through difference computation. Ni et al. [3] had given a scheme where a secret message is embedded at the histogram’s peak point of cover image. Afterward, Bo et al.[4] had given a method where cover image is segmented into equal-sized blocks and each block’s histogram embedded secret message in it. M. Celik et al.[5] depicted a steganographic methodology for compressed cover image pixels. Qian et al.[6] exhibited a separable reversible data hiding algorithm where cover image is encrypted through block cipher algorithm.
Zhang[7], firstly segmented cover image into equal-sized blocks, and after that, each block is further subdivided into two sub-blocks where one bit of secret message is embedded in it. The secret message is extracted through the computation of fluctuation function corresponding to each block. But during the computation of fluctuation function, boundary pixels are to be excluded which results in high bit error rate value. Wu and Sun[8] exhibited a method where blocks are further segmented into two sub-blocks. Embeddable pixel’s neighbors are not selected for data embedding which results in high peak-signal-to-noise-ratio(PSNR) value and low bit error rate respectively. Hong et al.[9] included boundary pixels during computation of fluctuation function which results in the same PSNR value and low bit error rate value as compare to Zhang[7]. Young et al.[10] segmented cover image into equal-sized blocks and after that, each block is further subdivided into two sub-blocks where one bit of secret message is embedded in it using the concept of lattice. Embeddable pixel’s four-connectivity neighbors are not selected for data embedding which results in high PSNR value and low bit error rate value. Ma et al.[11] proposed a reversible data hiding method before encryption of cover image. Liao and Changwen[12] improved computation of fluctuation function through calculating mean difference of neighboring pixels. Paillier cryptosystem[13] is utilized for encryption of cover image in Chen et al.[14] where one bit of secret message is embedded per pixel pair. Wu et al.[15] presented a reversible data hiding algorithm for signals which are encrypted through Paillier cryptosystem[13] and embedded one bit of binary secret message at a single pixel successfully. Bhardwaj and Aggarwal[16] introduced a reversible data hiding algorithm in encrypted domain where n secret bits are embedded per block by segmenting them into n sub-blocks. The drawback of this method is that for small block size, secret message is not extracted correctly which result in a high bit error rate.
Lu et al.[17] had given a method where dual stego images are generated by folded secret message centrally. Yao et al.[18] described a dual-image method based on pixel co-ordinate system which results in minimum distortion of pixel’s coordinate value. Lee and Huang[19] presented a method where dual stego images are generated through orientation combination of pixel coordinates. Here, binary secret message by changed over it into \(base_{5}\) numeral framework is embedded which results in improved embedding rate. Chi et al.[20] presented a dynamic encoding scheme where frequent occurrence of secret digits is encoded as the minimum absolute digit. The favored stance denotes that for the same embedding rate, the proposed method gave a higher PSNR than existing methods. Lu et al.[21] proposed a frequency encoding method to eliminate the disadvantage of Lu et al.[17] strategy.
Shiu et al.[22] employed a reversible scheme for preservation of patient information in ECG signals through error correcting-coding method where \((n-m)\) bits of secret message are embedded into n number of signals with the help of (n, m) hamming code successfully. Parah et al.[23] presented a reversible data hiding scheme for embedding patient information in medical images where cover image is interpolated through Pixel to Block (PTB) conversion method to guarantee reversibility of medical images. A high capacity reversible data hiding method which is capable of tamper detection of patient information at receiver end has been presented in this paper [24]. Bhalero et al.[25] embedded patient data in ECG signals using a prediction error expansion scheme where prediction of the sample values is performed through deep neural network respectively. Mansour et al.[26] proposed a highly robust reversible data hiding method in encrypted domain where patient data is hidden in medical images with the help of Discrete Ripplet Transformation technique successfully. The most significant commitment of proposed work is to employ adaptive genetic algorithm for optimal pixel adjustment process that enhances embedding capacity as well as imperceptibility features also.
3 Proposed Algorithm
The current E-healthcare system is doing telediagnosis of a patient, for this purpose, it requires medical reports of the patient including all image and text-based reports to share among its remote centers. Though E-healthcare systems bring the best medical facilities at your doorsteps, but during implementation process experiences some challenges also. Primary concern to be addressed for the implementation of E-healthcare system is security, authentication and copyright protection of the patient data respectively. Encryption is the most promising solution to maintain confidentiality and privacy of data. The integration of encryption and reversible data hiding technologies plays an important role in privacy protection. Keeping this in view, an enhanced reversible data hiding algorithm in the encrypted domain to embed electronic patient information(EPI) in cover image has been represented in this paper. In proposed method (Fig.1), Paillier cryptosystem is used for encryption instead of conventional ones to avoid underflow and overflow problems during data embedding in cover image.
Pailler cryptosystem[13] is discussed briefly in subsection 3.1 respectively.Data embedding algorithm is discussed in detail in subsection 3.2 while as data extraction and image recovery algorithm is discussed briefly in subsection 3.3.
3.1 Paillier Cryptosystem
This is public key cryptosystem based on the composite residuosity class problem. It comprised three procedures: key generation, data encryption and data decryption as described as follows-
-
Let p and q be two large prime numbers that are independent of each other.
-
Compute \(N=pq\) and \(\lambda =LCM(p-1,q-1)\)
-
Select generator g such that \(g \;\in \; Z_{N^2}^{*}\) and \(gcd(S(g^{\lambda } mod \; N^{2}),N)=1\) where
$$ S(x)=\frac{x-1}{N} $$(1) -
Consider a message \(m \in Z_N^*\) and randomly chosen \(r\in Z_N^*\). Compute the cipher text of m as
$$ c={g}^m{r}^N\mathit{\operatorname{mod}}\ {N}^2 $$(2) -
Public key is composed of (N, g) and private key is composed of \((p,q,\lambda )\).
-
Decryption of ciphertext c is given by
$$ m=\frac{S\left({c}^{\lambda}\mathit{\operatorname{mod}}\ {N}^2\right)}{S\left({g}^{\lambda}\mathit{\operatorname{mod}}\ {N}^2\right)}\mathit{\operatorname{mod}}\ N $$(3) -
Given two plaintexts \(m_1\) and \( m_2 \), corresponding ciphertexts are given by \(Enc [m_1]\) and \(Encr[m_2]\). The additive homomorphic property, \(Encr[m_1]\times Encr[m_2] =Encr[m_1+m_2]\) holds because of
The multiplicative homomorphic property,
3.2 Data Embedding Phase


3.3 Data extraction and image recovery phase
In our method, firstly stego image is decrypted through Paillier cryptosystem[13] at receiver end, then it is conceivable to extract the secret message and recuperate original cover image with no error.


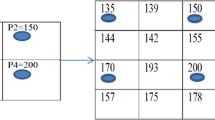
Example: Working of proposed algorithm on sample pixel values 0, 64, 127 and 255 is shown in Table2.
4 Experimental Study
The experimental study has been carried out using MATLAB R2017a platform for different \({512 \times 512}\) test images obtained from database of The Cancer Imaging Archive (TCIA) as shown in Fig.2 respectively. The exhibition of the proposed method has been assessed as far as metrics like Peak Signal to Noise Ratio (PSNR), Mean Square Error (MSE), Structural Similarity Index Matrix (SSIM), Normalized Cross-correlation (NCC), Bit Error Rate (BER) and Embedding Rate (bpp) respectively. PSNR, SSIM, NCC are used to evaluate the quality of stego images while BER is used to evaluate the error between embedded and extracted watermark. Let f(x, y) denote the value of pixel (x, y) in the cover image of size \(M \times N\) and sm and \(sm^{'}\) is embedded and extracted watermark,where \(A \times B\) is the size of the watermark. These metrics are defined as follows -
where
where \(\mu _x\) is average of x, \(\mu _y\) is average of y, \(\sigma _x^2\) is variance of x, \(\sigma _y^2\) is variance of y, \(\sigma _{xy}\) is covariance of x and y, \(c_1=(k_1L)^2, c_2=(k2L)^2, L=(2^8-1), k_1=0.01\) and \(k_2=0.03\) respectively.
4.1 Result Analysis
Here, we examined the performance of the proposed method and compared it with the existing state-of-the-art algorithms of Lu et al.\((k=2)\)[17], Yao et al.\((k=1,k=2)\)[18], Lee & Huang[19] and Chi et al.\((k=2)\)[20] respectively. Table 3 demonstrates the examination of the proposed method with all other compared methods with reference to embedding rate and the PSNR value attained on test images as shown in Fig.2 respectively. From Table 3, it can be observed that the proposed method achieved maximum embedding rate for all test images (approx.) and similarity of cover and stego image with one another in a degree to yield an average PSNR value of 48.13 dB. The same can also be observed from Fig.3 which graphically represents the comparison of the different payloads achieved by the proposed and compared methods. The embedding rate of proposed scheme is most prominent than other compared methods with an average visual quality of the stego images. Indeed, even as far as bits per pixel value, in most of the cases, embedding rate produced by the proposed method is at par with all the compared methods (Fig.4). After data embedding phase, proposed method successfully recovered original pixel values from stego image to facilitate reversibility. The unrivaled performance of the proposed method on all test images is attributed to its ability to manage the low-intensity pixels, which can cause the underflow issue during the procedure of data embedding. In the compared methods, they fundamentally neglect these low-intensity pixels, or by the day’s end mark them as non-embeddable cases. Since, in medical images, the count of such type of pixels is high as compared to natural images. The comparable can be seen from the outcomes introduced in Fig.4 too. The explanation behind this immense improvement in the embedding performance of the proposed method lies in its ability to hide information properly without any occurrence of underflow problem respectively. In this manner, all the compared methods were capable to give great embedding rate on natural images in contrast with medical images. Table 4 demonstrates the examination of the proposed algorithm with state-of-the-art algorithms with reference to image quality metrics like SSIM, NAE, NCC and Embedding Rate attained on medical images respectively. It is obvious from the obtained average values of quality metrics, high SSIM value coupled with NCC value of approximate unity specify that proposed algorithm is capable of providing high-quality images for a payload of one bpp respectively. It is also examined from Table 4 that the proposed algorithm gives a high embedding rate in encrypted domain with content authentication at receiver end while all other compared methods did not. In this manner it very well may be inferred that proposed method altogether beated all the compared methods in its ability to embed secret information and precisely recover it with maintaining the visual nature of stego images too. The purpose behind this enormous improvement in the embedding performance of the proposed methods lies in its capacity to embed data properly at low intensity pixels without any occurrence of underflow problem. Since, larger part of the pixels are black in medical images, so the proposed method performed extraordinarily well as compared to other methods for medical images.
4.2 Authentication Analysis
To evaluate performance of proposed scheme for its hidden message security at receiver end, we embedded a watermark inside the cover image. At the receiver end, extracted watermark is compared with the original one, if both watermarks are not matched with each other, it is accepted that the stego image and the hidden message is not legitimate. To assess performance of proposed scheme for its embedded message authentication, we subject stego image to well known image processing attacks on \({Med_4}(512 \times 512)\) cover image with embedding of watermark (cameraman) of size \((256 \times 256)\) Fig 5 respectively. From the outcomes for different attacks which are referenced in Fig 5, it is obvious that our strategy is profoundly fragile to every one of the attacks completed on different stego images and is approved by the way that the recovered watermark in the majority of the cases is not recognizable, thus demonstrative that the stego image has been attacked during transmission. High bit error rate value of the order of about (18-60)% for test images, approve the way that the proposed scheme is profoundly fragile, irrespective of the type of cover image.
4.3 Reversibility Analysis
At the receiver end, after extraction of the secret message, cover image is also reconstructed through stego image successfully. Theorem 1:-The proposed method is reversible in nature so that after extraction of the secret message, it reconstructs the original cover image at the receiver end successfully. Proof:-Consider any pixel value \((P_{u,v}= 2^{k}, k\le 7)\) in cover image(CI) which is divided into three units \(x_{u,v}\), \(y_{u,v}\) and \(z_{u,v}\) as follows-
Assumed secret message (\(w_{u,v}>0\)), after embedding \([w_{u,v}]\) into \([x_{u,v}]\), \([y_{u,v}]\) and \([z_{u,v}]\), they will be changed into \([x^{*}_{u,v}]\), \([y^{*}_{u,v}]\) and \( [z^{*}_{u,v}]\) as follows-
At receiver end, firstly \([x_{u,v}^{*}],[y_{u,v}^{*}],[z_{u,v}^{*}]\) are decrypted through Paillier cryptosystem[13] and extract the secret message \(w_{u,v}\) and reconstruct cover image(CI) as follows:-
Similarly, all pixel values of the cover image are retrieved and finally, the extraction of secret message and reconstruction of the original cover image is done successfully at the receiver end. So, it is to be concluded that proposed method is reversible in nature.
5 Conclusion
Data hiding applications in the E-healthcare framework have an extreme indulgence with reversibility, high payload and content authentication. To recover the original medical image at the receiver end for diagnosis and transfer of high payload, an enhanced reversible data hiding technique in an encrypted domain has been proposed in this paper. The proposed algorithm gives higher embedding rate by embedding a single bit of patient data in \(base_2\) numeral framework at every pixel of the cover image without any occurrence of underflow and overflow problem. As the proposed method does not incur underflow and overflow problem now it has been commissioned to embed and recover patient information precisely from low-intensity pixels too. This superlative quality makes the proposed method appropriate for utilization on medical images. An evaluation of the proposed algorithm with some state-of-the-art algorithms shows that the proposed method has higher embedding capacity and as such as far suitable for content authentication of EPI in a typical E-healthcare system. The proposed algorithm has been tested out in the spatial domain so that the embedded EPI is not robust to various types of noise attacks. In the future, we need to improve the robustness of the proposed method.
References
Yun Q Shi. Reversible data hiding. In Int. workshop on digital watermarking, pages 1–12. Springer, 2004
Tian Jun (2003) Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 13:890–6
Ni Zhicheng, Shi Yun-Qing, Ansari Nirwan, Wei Su (2006) Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 16:354–8
B Xiao, Lizhi Ying, and Yongfeng Huang. Reversible data hiding using histogram shifting in small blocks. In Communications (ICC), 2010 IEEE Int. Conf on, pages 1–6. IEEE, 2010
Mehmet Utku Celik, Gaurav Sharma, A Murat Tekalp, and Eli Saber. Lossless generalized-lsb data embedding. IEEE Trans. Image Process., 14:253–13, 2005
Qian Zhenxing, Zhang Xinpeng, Ren Yanli, Feng Guorui (2016) Block cipher based separable reversible data hiding in encrypted images. Multimed Tools Appl 75:13749–17
Zhang Xinpeng (2011) Reversible data hiding in encrypted image. IEEE Signal Process Lett. 18:255–3
Xiaotian Wu, Sun Wei (2014) High-capacity reversible data hiding in encrypted images by prediction error. Signal Process. 104:387–13
Hong Wien, Chen Tung-Shou, Han-Yan Wu (2012) An improved reversible data hiding in encrypted images using side match. IEEE Signal Process Lett. 19:199–3
Kim Young-Sik, Kang Kyungjun, Lim Dae-Woon (2015) New reversible data hiding scheme for encrypted images using lattices. Appl Math Inform Sci 9:2627
Ma Kede, Zhang Weiming, Zhao Xianfeng, Nenghai Yu, Li Fenghua (2013) Reversible data hiding in encrypted images by reserving room before encryption. IEEE Trans. Inf. Forensics Secur. 8:553–9
Liao Xin, Shu Changwen (2015) Reversible data hiding in encrypted images based on absolute mean difference of multiple neighboring pixels. J. Visual Commun. Image Represent. 28:21–6
Pascal Paillier. Public-key cryptosystems based on composite degree residuosity classes. In International Conference on the Theory and Applications of Cryptographic Techniques, pages 223–15. Springer, 1999
Chen Yu-Chi, Shiu Chih-Wei, Horng Gwoboa (2014) Encrypted signal-based reversible data hiding with public key cryptosystem. J. Visual Commun. Image Represent. 25:1164–6
Xiaotian Wu, Chen Bing, Weng Jian (2016) Reversible data hiding for encrypted signals by homomorphic encryption and signal energy transfer. Journal of Visual Communication and Image Representation 41:58–64
Bhardwaj Rupali, Aggarwal Ashutosh (2018) An improved block based joint reversible data hiding in encrypted images by symmetric cryptosystem. Pattern Recognit. Lett
Tzu-Chuen Lu, Jhih-Huei Wu, Huang Chun-Chih (2015) Dual-image-based reversible data hiding method using center folding strategy. Signal Process. 115:195–18
Yao Heng, Qin Chuan, Tang Zhenjun, Tian Ying (2017) Improved dual-image reversible data hiding method using the selection strategy of shiftable pixels’ coordinates with minimum distortion. Signal Process. 135:26–9
Lee Chin-Feng, Huang Yu-Lin (2013) Reversible data hiding scheme based on dual stegano-images using orientation combinations. Telecommun Syst 52:2237–10
Chi Li-Pin, Chang-Han Wu, Chang Hsung-Pin (2018) Reversible data hiding in dual stegano-image using an improved center folding strategy. Multimed Tools Appl 77:8785–18
Tzu-Chuen Lu, Chi Li-Pin, Chang-Han Wu, Chang Hsung-Pin (2017) Reversible data hiding in dual stego-images using frequency-based encoding strategy. Multimed Tools Appl 76:23903–26
Shiu Hung-Jr, Lin Bor-Sing, Huang Chien-Hung, Chiang Pei-Ying, Lei Chin-Laung (2017) Preserving privacy of online digital physiological signals using blind and reversible steganography. Computer methods and programs in biomedicine 151:159–170
Shabir A Parah, Farhana Ahad, Javaid A Sheikh, and Ghulam Mohiuddin Bhat. Hiding clinical information in medical images: a new high capacity and reversible data hiding technique. Journal of biomedical informatics, 66:214–230, 2017
Shabir A Parah, Farhana Ahad, Javaid A Sheikh, Nazir A Loan, and Ghulam Mohiuddin Bhat. A new reversible and high capacity data hiding technique for e-healthcare applications. Multimedia Tools and Applications, 76(3):3943–3975, 2017
Siddharth Bhalerao, Irshad Ahmad Ansari, Anil Kumar, and Deepak Kumar Jain. A reversible and multipurpose ecg data hiding technique for telemedicine applications. Pattern Recognition Letters, 125:463–473, 2019
Romany F Mansour and Elsaid M Abdelrahim. An evolutionary computing enriched rs attack resilient medical image steganography model for telemedicine applications. Multidimensional Systems and Signal Processing, 30(2):791–814, 2019
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Bhardwaj, R., Singh, A. An efficient reversible and secure patient data hiding algorithm for E-healthcare. Multimed Tools Appl 80, 31687–31703 (2021). https://doi.org/10.1007/s11042-021-10892-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10892-2