Abstract
In this paper, a reversible data hiding scheme is proposed based on histogram shifting of n-bit planes (nBPs). This scheme extracts nBPs from an 8-bit plane for each pixel to generate the bit plane truncation image (BPTI), and then block division is used in the BPTI. These operations can make the peak point of the block histogram more concentrated and improve the probability of the zero point in the block histogram. The histogram shifting method was used to embed secret bits into the peak point in each block. Note that this block was not utilized to embed secret bits if the zero point of a certain block did not exist, thus, there was no overflow or underflow in our scheme when the histogram was shifted. Our proposed scheme achieved higher hiding capacity than previous histogram-based schemes, and its visual quality was very satisfactory. The experimental results validated the expected merits of the proposed scheme.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
With the rapid development of network and multimedia technology, digital media data can be transmitted conveniently on communication networks. This brings more convenience for people, but it is accompanied by a number of problems concerning the security of senstive information. Data hiding [2, 17] is an important technology for securely transmitting secret messages in networks, and it is concerned mainly with the issue of embedding secret data into public host media, e.g., texts, audios, images, and videos, so that these secret data can be transmitted securely on public channels. Steganography [4], as the main embranchment of data hiding, hides the secret data into a host image by modifying the pixels of the host image, and the modifications of the pixel values should be undetectable to the observers. This ensures that any third party (i.e., aside from the comunication parties) cannot be aware of the existence of the secret data. Usually, this host image is called the cover-image, and the image in which the secret data have been embedded is called the stego-image. However, modification of pixels may damage the original cover-image permanently. In some special application areas, such as military remote-sensing images, medical images, and legal evidence images, any tiny change of an image may affect the credibility of the original image, which could lead to serious consequences. In this case, the cover-image cannot be distorted, even to a small extent, after the secret data have been extracted. Reversible data hiding technology is proposed to solve this problem because it can extract the secret data completely from the stego-image and restore the original cover-image without any distortion.
The first reversible data hiding scheme was proposed by Honsinger et al. [6] in 2001. The hash value of the original image as the authentication information was hidden into the original image by using modulo-256. Goljan et al. [3] proposed a revesible data hiding algorithm based on block status code. Their algorithm divided the cover-image into non-overlapping blocks, and embedded the secret data into the status of the image blocks. Since then, many reversible data hiding schemes based on difference technique have been reported in the literatrue [7, 12, 13, 15, 18, 19, 21]. Among them, difference expansion [21] is an effective, high-capacity, lossless watermarking algorithm for data hiding. In this algorithm, the secret data are embedded into the least significant bits (LSBs) of the expanded differences between the adjacent pixels. But it has high computational complexity and produces an image with poor visual quality. Alattar [1] extended the difference expansion method by using the vector instead of the pair to improve embedding capacity, and as a result, (k + 1) bits can be hidden into a set of k adjacent pixels. In 2010, an adaptive prediction-based reversible data hinding scheme [13], which was presented by Lee et al., provided higher embedding capacity by taking full advantage of the large quantities of smaller difference values.
Histogram modification, which was developed by Ni et al. [18], is another effictive scheme for hiding secret data. This scheme utilized the peak and zero points of the cover-image histogram and slightly modified the pixel grayscale values to allow secret data to be embedded. It provided better quality images than most of the other reversible hiding schemes. However, the hiding capacity was limited by the number of the peak point. Later, several related research efforts [5, 8–11, 14, 16, 20, 22] based on Ni et al.’s scheme were developed. Hwang et al. [9] proposed the idea of slightly adjusting the pixel values located at both sides of the peak point to embed data. But a location map still must be stored in order to achieve reversible recovery, and this has an adverse effect on the hiding capacity. Kuo et al. [11] used lock division to increase the hiding capacity of Hwang et al.’s scheme [9], and the experimental results also confirmed that this scheme was more effective in increasing the hiding capacity than in improving the visual quality of the image. In 2009, Kim et al. [10] proposed a novel reversible hiding scheme based on histogram shifting. Their idea was to divide the cover-image into several sub-images, and then calculate the differences between the sub-images. Finally, the difference histogram was modified to embed the data. Different from Kim et al.’s scheme, Luo et al. [16] exploited the high correlation among block pixels to produce a difference histogram, and the secret data were embedded by referring to the median value of each block.
In this paper, in order to achieve higher hiding capacity and better visual quality, we proposed a new and simple reversible data hiding scheme, which shifts and modifies the histogram of n -bit planes (nBPs) for embedding data. First, we extracted nBPs from the 8-bit plane for each pixel to generate a new image, called the bit plane truncation image (BPTI). Second, in order to improve the hiding capacity, we divided BPTI into non-overlapping blocks. In this way, the peak point of the histogram in each block can be more concentrated, and its zero point can have a higher probability of appearing. Finally, we utilized the peak point and the nearest zero point of the block histogram and slightly modified the pixel values of BPTI to embed the secret data. Our proposed scheme achieved higher hiding capacity than the previous histogram-based schemes, and it provided satisfactory visual quality. Our experimental results proved the expected merits of the proposed scheme.
2 Related work
2.1 Ni et al.’s scheme
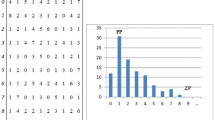
Ni et al. [18] introduced a reversible data hiding scheme by shifting and modifying the histogram of the pixels to hide data. A histogram of the cover-image was generated, and then the peak point and the zero point were identified. We used the “Lena” image and its histogram as an example, and the results are shown in Fig. 1. First, assume that P is the value of the peak point and that Z is the value of the zero point. Also, one is added to each pixel value in the range of [P + 1, Z-1], leaving the pixel value (P + 1) empty. Next, we embed the secret bits when the peak point P is encountered. The entire image is scanned from top to bottom and from left to right. Once the peak point P is encountered, we check the to-be-embedded secret bit. If this secret bit is 1, the pixel value of P is increased by 1. Otherwise, there is no modification. The data extraction process of this scheme is very easy. However, we can see that the number of the hidden bits is limited by the number of the peak point. If there is no zero point, the minimum point can be used instead of the zero point. But the number of extra bits will be increased dramatically, resulting in a decrease in the hiding capacity.
2.2 Kuo et al.’s scheme
Kuo et al.’s scheme [11] utilized block division to cooperate with the histogram modification to improve the embedding capacity effectively. The steps of the data embedding process are described as follows:
-
Step 1.
Divide the cover-image into several non-overlapping blocks, and then take the histogram of each block, as shown in Fig. 2.
-
Step 2.
Determine the maximum point and the two minimum points in each block histogram.
-
Step 3.
Shift both sides of the maximum point to the right and the left one point to generate the embedding space.
-
Step 4.
Record the related information, i.e., maximum point, left minimum point, and right minimum point in each block, into a location map.
-
Step 5.
Embed the secret data into the embedding space by using Ni et al.’s method.
Although this scheme improves the embedding capacity by using block division, improvement of the performance is not obvious. In addition, a location map must be stored.
2.3 Kim et al.’s scheme
Kim et al.’s scheme [10] used the high spatial correlation in adjacent pixels to achieve high capacity and imperceptible embedding. The main idea of the data embedding algorithm is described as follows.
Input. The cover-image C sized m × n,
Output. The stego-image C′
Step.
-
Step 1.
Sub-sample the cover-image C into several equal-sized sub-images \( {c}_1,{c}_2,\dots {c}_{\varDelta^2} \) by using Eq. (1):
$$ {c}_k\left(i,j\right)=C\left(i\cdot \varDelta +\left\lfloor \frac{k-1}{\varDelta}\right\rfloor, j\cdot \varDelta +\left(\left(k-1\right) \mod \varDelta \right)\right) $$(1)where (i, j) denotes the i th row and j th column pixel in the sub-images with i = 1, 2, …, m/Δ, j = 1, 2, …, n/Δ. Δ is the subsampling intervals.
-
Step 2.
Choose a subsampled image c r as the reference image, and compute the difference d k (i, j)(k ≠ r) according to Eq. (2):
$$ {d}_k\left(i,j\right)={c}_k\left(i,j\right)-{c}_r\left(i,j\right)\kern0.5em \left(k=1,2,\dots, {\varDelta}^2\ and\ k\ne r\right) $$(2) -
Step 3.
Shift the difference histogram according to Eq. (3):
$$ {d}_k^{\prime}\left(i,j\right)=\left\{\begin{array}{l}{d}_k\left(i,j\right)+L+1,\kern0.5em if\ {d}_k\left(i,j\right)\ge L+1\hfill \\ {}{d}_k\left(i,j\right)-L-1,\kern0.5em if\ {d}_k\left(i,j\right)\le -L-1\hfill \\ {}{d}_k\left(i,j\right),\kern2.25em otherwise\hfill \end{array}\right. $$(3)where L is the embedding level.
-
Step 4.
Embed the secret bits s by modifying the shifted histogram.
$$ {d}_k^{{\prime\prime}}\left(i,j\right)=\left\{\begin{array}{l}{d}_k^{\prime}\left(i,j\right)+L+s,\kern0.5em if\ {d}_k^{\prime}\left(i,j\right)=L\ne 0\hfill \\ {}{d}_k^{\prime}\left(i,j\right)-L-s,\kern1.9em if\ {d}_k^{\prime}\left(i,j\right)=-L\ne 0\hfill \\ {}{d}_k^{\prime}\left(i,j\right)+s,\kern2.4em if\ {d}_k^{\prime}\left(i,j\right)=L=0\hfill \end{array}\right. $$(4) -
Step 5
Compute the marked subimages \( {c}_1^{\prime },{c}_2^{\prime },\dots {c}_{\varDelta^2}^{\prime } \) according to Eq. (5), and reconstruct the stego-image C′.
$$ {c}_k^{\prime}\left(i,j\right)={c}_r\left(i,j\right)+{d}_k^{{\prime\prime}}\left(i,j\right) $$(5)
The data extracting algorithm is the inverse process of data embedding. Note that the reference sub-image cannot be used for embedding the secret data in this scheme.
3 Proposed scheme
In Ni et al.’s scheme, if the minimum point is used to substitute for the zero point, the extra bits will be increased dramatically because the location and value of each minimum point must be recoded. This will consume a significant amount of hiding capacity to achieve the purpose of lossless recovery. In this paper, we take two steps to overcome the shortcomings of Ni et al.’s scheme and improve the hiding capacity and the visual quality. In the first step, we extract n -bit planes (nBPs) from the 8-bit plane of each pixel in the cover-image to generate a new image, called the bit plane truncation image (BPTI). This operation can make the peak point of the histogram more concentrated. In the second step, we divide BPTI into non-overlapping blocks in order to increase the probablity of a zero point in each block. Then, we utilize the peak point and the zero point of the block histogram and slightly modify the pixel values of BPTI to embed the secret data. Fig. 3a–h show the histograms of several blocks of the “Lena” image. These figures show that most of the block histograms have the peak point and the zero point (as shown in Fig. 3a, b, d–h), and the number of the zero points is usually greater than one. In this case, we choose the zero point that is nearest to the peak point. In addition, a few block histograms may not have a zero point (as shown in Fig. 3c), so these blocks are not used to embed secret data.
3.1 Data embedding algorithm
In order to distinguish the embeddable and non-embeddable blocks, a variable, which is called the location map (LM), is defined to recode whether a certain block can embed secret bits. That is, each block would take up to 1-bit of the LM. If the LM is set to 1, it means that the current block can be used to hide secret bits; otherwise, the current block cannot be used for this purpose. Note that the value of the peak point and the value of the zero point in each embeddable block must be recoded. Figure 4 shows our definition of the structure of extra bits.
In Fig. 4, PP and ZP are optional, i.e., the values of PP and ZP are recoded when LM is 1; otherwise, we skip this block and do not recode their values.
The steps of the data embedding algorithm are described as follows:
Input. The cover-image I sized 512 × 512, the secret bits S generated randomly
Output. The stego-image I′
Steps.
-
Step 1.
Divide the cover-image I into region A and region B for embedding the secret bits and extra bits respectively, as shown in Fig. 5. For example, given a 512 × 512 cover-image, the pixels in the last eight rows and columns, i.e., region B, are used for hiding the extra bits. Usually, the division of region B should be enough to hide extra bits and high efficiency lossless compression techniques also are used to compress the extra bits.
-
Step 2.
In region A of the cover-image, we extract nBPs from the 8-bit plane of each pixel to generate BPTI and divide it into non-overlapping blocks of size B × B. Note that the sizes of the blocks should be determined by the actual situation. Extra bits will increase if the block size is smaller; on the contrary, hiding capacity will decrease if the block size is larger.
-
Step 3.
Generate the histogram H of the current block and search the peak point p and the zero piont z. If z exists, LM is set to 1, and the peak point p and the nearest zero point z are recoded; otherwise, LM is set to 0, and there’s nothing to do.
-
Step 4.
When LM is equal to 1, the secret bit embedding algorithm in the current block is implemented according to the code in Fig. 6. For example, assuming that the matrix of the embeddable image block is shown in Fig. 7a, the peak point p = 25 and the zero point that is nearest to the peak point is z = 27. Obviously, p < z, so all of the values of 26 should be increased by 1, and they are marked in red in Fig. 7b. Then, the whole block is scanned from top to bottom and from left to right. Once the peak point p = 25 is encountered, we check the to-be-embedded secret bit. If this secret bit is 1, the pixel value is increased by 1. Otherwise, there is no modification. This process is marked with blue color in Fig.7c.
-
Step 5.
Repeat Steps 3 and 4 until all of the blocks have been scanned.
-
Step 6.
Use the renewed BPTI to substitute the n-bit plane in the original cover-image.
-
Step 7.
Embed the extra bits into the pixels’ LSBs in region B.
Example for histogram modification according to the code in Fig. 6
Now, the stego-image I′ has been generated. Note that, in order to achieve reversible data hiding, these pixels’ LSBs are extracted in advance and attached to secret bits S to form S′, which is embedded into the cover-image.
3.2 Data extraction algorithm
The goal of data extraction is to extract the secret bits from the stego-image accurately while ensuring that the cover-image is not distored. In our scheme, the data extraction algorithm is a simple inverse process of data embedding. Its steps are described as follows:
-
Step 1.
Extract the nBPs from the 8-bit plane of each pixel of the stego-image in region A and extract extra bits from the pixels’ LSBs in region B.
-
Step 2.
Divide the BPTI into non-overlapping blocks of size B × B.
-
Step 3.
Scan each block and its corresponding extra bits in the same sequential order that was used in the embedding process, and, as shown in Fig. 8, perform the following steps.
For instance, first, we extract the values of p = 25 and z = 27 from the extra bits when LM = 1, and judge whether p < z, as shown in Fig. 9a. Next, the whole block is scanned from top to bottom and from left to right. If the peak point p = 25 is encountered, secret bit 0 will be extracted. If p + 1 = 26 is encountered, secret bit 1 will be extracted. And, meanwhile, the original pixel value is recovered decreasing by 1. This process is marked in Fig. 9b and c. Finally, the original image block can be reconstructed by moving the value of z = 27 to left by 1, as shown in Fig. 9d.
-
Step 4.
Repeat Steps 3 until all of the blocks have been recovered.
-
Step 5.
Use the restored BPTI to substitute the n-bits plane in the stego-image and to restore the pixels’ LSBs in region B. In this way, the original image can be recovered without any distortion.
4 Experimental results
We chose five grayscale images, each with 512 × 512 pixels, as cover-images for testing, i.e., “Lena,” “Airplane,” “Baboon,” “Boat,” and “Tiffany,” as shown in Fig. 10. The performance of the proposed scheme was evaluated by hiding capacity and the peak-signal-to-noise ratio (PSNR) of the stego-image. The hiding capacity, i.e., the total number of secret bits embedded, is represented by C (bits). The secret bits are created by using a pseudo-random number generator. The size of embeddable region A was 504 × 504, and the rest of the cover-image was used to embed extra bits.
Two vital factors that can affect the performance of our scheme directly must be considered. One is the selection of the n -bit planes, and the other is the size of the block division. In our scheme, there are different sizes of block divisions to choose from, i.e., 2 × 2, 3 × 3, 4 × 4, 6 × 6, 8 × 8, 9 × 9, 14 × 14, 18 × 18, and 21 × 21. Although the small block sizes can obtain higher hiding capacities, the extra bits will increase simultaneously. Table 1 gives a comparison of hiding capacity and extra bits in different sizes of block division of the image “Lena.” We can see that the number of the extra bits is five times the number of the hiding capacity when the block size is 2 × 2. Obviously, the enormous number of extra bits cannot be fully hidden into region B. As the size of the block increases, the hiding capacity decreases, and the number of extra bits will decrease sharply. When the block size is 18 × 18, the number of extra bits is only 20 % of the hiding capacity.
Tables 2, 3 and 4 compare the performances with an 18 × 18 block division when selecting the different bit planes to generate BPTI. From the tables, we can see that: (1) The number of extra bits increases as the number of bit planes increases. For example, the number of extra bits when six bit planes are selected is greater than the number when five bit planes are selected. (2) Choosing a higher bit planes can reduce the quality of the stego-image. Table 3 shows that the image quality when the bit planes are selected from the third bit to the seventh bit is better than that when the bit planes are selected from the second bit to the sixth bit. (3) Choosing the higher bit planes can improve the hiding capacity. In Table 4, the hiding capacity was the highest when the bit planes from the second bit to the fifth bit are selected, but the image quality is the worst.
Based on the above analysis, we selected the BPTI generated by bit planes from the third bit to the seventh bit and the 18 × 18 block division to conduct the following experiments. Figure 10 compares the visual quality of the cover-images and stego-images. Visually, it is impossible to distinguish between them. The higher PSNR means that the quality of the stego-image is similar to that of the original image. Table 5 compares our scheme with other related schemes, i.e., Ni et al.’s scheme [18], Kim et al.’s scheme [10], and Luo et al.’s scheme [16], in terms of hiding capacity and PSNR. Ni et al.’s scheme [18] first used the peak point and the zero point of the histogram of the image to hide secret bits, so the hiding capacity is limited by the number of the peak point. Kim et al.’s scheme [10] fully utilized the high spatial correlation inherent in neighboring pixels to obtain higher hiding capacity than that of Ni et al.’s scheme [18]. Based on Kim et al.’s scheme, Luo et al. [16] exploited the high correlation among block pixels to produce a difference histogram, and the secret data are embedded by referring to the median value of each block. This process of block division can increase the number of the peak point, thereby improving the hiding capacity further. Therefore, the hiding capacity in Luo et al.’s scheme obtains significant improvement compared with Ni et al.’ scheme and Kim et al.’ scheme. In addition to block division, our scheme also used the method of truncating the bit planes to increase the number of the peak point and the probablity of the zero point in each block. The experimental results shown in Table 5 demonstrate that our scheme produces better results both in hiding capacity and in PSNR. Note that, in Kim et al.’s scheme and Luo et al.’s scheme, the 3 × 3 block division is chosen and EL is set 0.
In order to further demonstrate the superiority of our scheme, we did a series of experiments using multi-embedding. Multi-embedding means that the generated stego-image can be used as the new cover-image to embed the secret data repeatedly by using the same embedding algorithm. Because our scheme can recover the cover-image reversibly, the multi-embedding method did not affect the extraction of secret data and the recovery of the original cover-image. Figure 11 shows the comparison of our multi-embedding results with those of other schemes, including Kim et al.’s scheme [10] and Luo et al.’s scheme [16]. It is apparent that the performance of our scheme is better than those of Kim et al.’s scheme [10] and Luo et al.’s scheme [16].
5 Conclusions
In this paper, a reversible data hiding scheme was proposed based on histogram shifting of n -bit planes. In the proposed scheme, nBPs were extracted to generate BPTI, and it used the concept of block division to improve the hiding capacity and the image quality. Our experimental results proved that our scheme has higher hiding capacity than the previous histogram-based schemes, and it also has a very satisfactory PSNR.
References
Alattar AM (2004) Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans Image Process 13(8):1147–1156
Chan CK, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37(3):469–474
Goljan M, Fridrich JJ, Du R (2001) Distortion-free data embedding for images. Information Hiding. Springer Berlin Heidelberg, 27–41
Hamid N, Yahya A, Ahmad RB et al (2012) Image steganography techniques: an overview. Int J Comput Sci Secur (IJCSS) 6(3):168–187
Hong W, Chen TS, Shiu CW (2009) Reversible data hiding for high quality images using modification of prediction errors. J Syst Softw 82(11):1833–1842
Honsinger CW, Jones PW, Rabbani M et al. (2001) Lossless recovery of an original image containing embedded data. U.S. Patent No.6278791
Huang HC, Chang FC (2013) Hierarchy-based reversible data hiding. Expert Syst Appl 40(1):34–43
Huang HC, Fang WC (2011) Authenticity preservation with histogram-based reversible data hiding and quadtree concepts. Sensors 11(10):9717–9731
Hwang JH, Kim JW, Choi JU (2006) A reversible watermarking based on histogram shifting. Digital Watermarking. Springer Berlin Heidelberg, 348–361
Kim KS, Lee MJ, Lee HY et al (2009) Reversible data hiding exploiting spatial correlation between sub-sampled images. Pattern Recogn 42(11):3083–3096
Kuo WC, Jiang DJ, Huang YC (2008) A reversible data hiding scheme based on block division. CISP’08 Congr IEEE Image Signal Process 1:365–369
Lee CF, Chang CC, Pai PY et al. (2015) An adjustable and reversible data hiding method based on multiple-base notational system without location map. J Digit Imaging
Lee CF, Chen HL, Tso HK (2010) Embedding capacity raising in reversible data hiding based on prediction of difference expansion. J Syst Softw 83(10):1864–1872
Li X, Li B, Yang B et al (2013) General framework to histogram-shifting-based reversible data hiding. IEEE Trans Image Process Publ IEEE Signal Process Soc 22(6):2181–2191
Lin CC, Liu XL, Tai WL et al. (2013) A novel reversible data hiding scheme based on AMBTC compression technique. Multimedia Tools Appl 1–20
Luo H, Yu FX, Chen H et al (2011) Reversible data hiding based on block median preservation. Inf Sci 181(2):308–328
Mali SN, Patil PM, Jalnekar RM (2012) Robust and secured image-adaptive data hiding. Digit Signal Process 22(2):314–323
Ni Z, Shi YQ, Ansari N et al (2006) Reversible data hiding. IEEE Trans Circ Syst Video Technol 16(3):354–362
Qin C, Chang CC, Chen YC (2013) Efficient reversible data hiding for VQ-compressed images based on index mapping mechanism. Signal Process 93(9):2687–2695
Tai WL, Yeh CM, Chang CC (2009) Reversible data hiding based on histogram modification of pixel differences. IEEE Trans Circ Syst Video Technol 19(6):906–910
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circ Syst Video Technol 13(8):890–896
Zhao P, Li S, Zhou L, Li L, Guo X (2015) Detecting affine-distorted duplicated regions in images by color histograms. J Inf Hiding Multimed Signal Process 1(6):163–174
Acknowledgments
This work was supported in part by NNFSC (No.61272262), Shanxi NSF (No.2012011014-3), YSTRF of TYUST (No.20123004).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, L., Chang, CC. & Wang, A. Reversible data hiding scheme based on histogram shifting of n-bit planes. Multimed Tools Appl 75, 11311–11326 (2016). https://doi.org/10.1007/s11042-015-2855-3
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-015-2855-3