Abstract
In a resource-constrained wireless sensor network, energy efficiency is a principle issue for monitoring the movement of continuous objects, such as wild fire and hazardous chemical material. In this paper, a continuous object tracking scheme with two-layer grid model (TGM-COT) is proposed. To address the problem of boundary distortion caused by uneven node distribution, we put forward a novel mechanism for boundary nodes identification. Furthermore, a streamlining mechanism is designed to reduce the amount of uploaded data. Simulation results demonstrate that, without sacrificing additional energy consumption, TGM-COT is able to achieve high tracking accuracy and significantly reduce the communication overhead.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Rapid improvements of microsensor machining technology and wireless communication technology have enabled the development of miniaturizing, highly integrated and multi-functional nodes. With low cost for large-scale deployment, these nodes can form a self-organized network which spontaneously sense, collect and process data in an area of interest [1–3]. Nowadays, wireless sensor networks (WSNs) have been widely applied in various applications, ranging from habitat monitoring to military surveillance [4]. One of the most important services provided by WSNs is object tracking. Traditionally, the implementation of object tracking entails two stages, namely, monitoring and reporting. Monitoring phase aims to identify the nodes surrounding the object boundary. Once a target intrudes upon the monitoring area, a subset of nodes are able to detect it using sensing module. Through information exchange, nodes located around the boundary can be determined to describe the object’s moving trajectory. Reporting phase aims to select report nodes and then transmit information of boundary nodes to a sink in time [5–7].
Normally, objects intended to be monitored and tracked can be divided into two categories: continuous objects and individual objects. An individual object might be an enemy soldier, a tank or a single wild animal which has fixed size and occupies limited area. Different with individual object, a continuous object, such as toxic gas, wild fire and migrating sheep, is continuously distributed in a large-scale area. A continuous object is pretty flexible and dynamic due to its sensitiveness to surrounding natural effects. Even though there are many researches on individual object tracking [8–15], they cannot be directly applied to continuous object tracking. Due to the fact that continuous objects always cover large area with unfixed shape and size, tracking such targets in real time entails large quantity of exchanged messages. Much communication overhead occurs in this process. Also, without considering energy supplement, the most challenge in WSNs is energy constraint, thus it is essential to propose an efficient tracking algorithm which minimizes the communication overhead as much as possible.
In this paper, we propose an energy-efficient algorithm named TGM-COT for continuous object tracking. A two-layer grid-based network model is specially designed for TGM-COT. In TGM-COT, coarse-grained grids are proactively established over the sensing area. And then, fine-grained grids are established within coarse-grained grid cells around the continuous object. A cluster-based network is established based on the two-layer grid structure. By assigning numerous calculation tasks to cluster heads, less communication occurs to non-cluster head nodes. Furthermore, considering uneven node distribution, the algorithm introduces a streamlining mechanism to eliminate redundant nodes in high node density areas and an avoidance mechanism to prevent boundary distortion in low node density area, respectively. The main contributions of TGM-COM are that:
-
(a)
In TGM-COT, data flow is unidirectional. The amount of data transmission can be reduced by one-half.
-
(b)
Owing to the two-layer grid-based model, cluster heads can remove redundant boundary nodes without decreasing tracking accuracy.
-
(c)
An avoidance mechanism is proposed to address the problem of boundary distortion caused by uneven node distribution.
The remainder of this paper is organized as follows: in Sect. 2, we discuss the previous work and make an analysis. In Sect. 3, we give the preliminaries and introduce the two-layer grid-based network model. Section 4 presents the partition of the two-layer grid network. Boundary node identification mechanism and streamlining mechanism are described in Sect. 5. In Sect. 6, performance of TGM-COT is evaluated through simulations. Finally, we draw the conclusion.
2 Related work
In this section, we briefly review some of the prominent continuous object tracking algorithms.
In [16], Chang et al. proposed a continuous object detection and tracking algorithm (CODA). CODA is based on a hybrid static/dynamic clustering technique which enables each node to detect and track the moving boundaries of objects in the sensing field. To estimate the boundary profile within each cluster, CODA employs cluster heads in static clusters. Each dynamic cluster head fuses all the boundary information within its own cluster and then relays it to the sink in a compressed data format. CODA incurs lower communication costs and achieves better boundary estimation precision irrespective of the size of the continuous object and the sensor network density. However, if the boundary profile is a concave polygon, it may acquire incorrect boundary information from original diffusing object.
In [17], Kim et al. proposed an energy-efficient algorithm named DEMOCO for boundary detection and monitoring of continuously moving phenomena. Using representative nodes chosen from boundary nodes to upload data, the traffic load between boundary nodes and the sink can be relieved. Furthermore, a representative node only sends one neighbor node’s ID, which is possibly the closest node among its neighbors that have different current reading. It means the report message size can be smaller, especially when the density of the deployed nodes is high. However, in the process of boundary node identification, DEMOCO introduces much messages exchange between neighboring nodes. Also, when the target boundary is shrinking, DEMOCO chooses the nodes within the area occupied by the object as boundary nodes. It is unreasonable in certain practical scenarios. Figure 1 illustrates the tracking of poisonous gas. \(U_1\) consisting of nodes 1, 2, …, and 7 (Fig. 1a) is the set of inner boundary nodes. \(U_2\) consisting of nodes A, B, …, and N (Fig. 1b) is the set of outer boundary nodes. Clearly, there is a blank area between \(U_1\) and \(U_2\), where toxic gas exists. Inner boundary nodes determined by DEMOCO overlook the existence of the blank area so that frontline staff might be misguided into the contamination area.
In [18], Park et al. proposed a novel continuous object tracking scheme which takes into account a grid-based structure. To fulfill the requirement of flexibility, the scheme firstly constructs a coarse-grained grid structure. Once a continuous object appears, fine-grained grids are established within coarse-grained grid cells around the continuous object. Based on the consideration of reliability, minute grid cells of the fine-grained grid structure are able to provide detailed shape of the continuous object boundary. To quickly deal with diffusion of the continuous object, the scheme executes the fine-grained grid division within the next coarse-grained grid cells toward diffusion direction of the continuous object. However, the scheme does not take into account the uneven node distribution. Therefore, if no nodes exist in a grid, the grid is unable to be selected as a boundary grid even though a target travels across it. The grid-based model is also adopted by researchers in [19–21], in our study, we modify the model and design a two-layer grid model.
3 Network model
In this section, we make general assumptions about sensor nodes and the framework of sensor networks. As shown in Fig. 2a, the sensing field is defined as a square area which can be partitioned into several mesh divisions. The mesh divisions represent first layer grids. A predefined system parameter \(\alpha\) determines the size of mesh divisions (\(\alpha\) is 4 in Fig. 2a). As shown in Fig. 2b, within first layer grids, a second layer division is constructed. A predefined system parameter \(\beta\) (\(\beta\) is 3 in Fig. 2b) determines the size of the grids. Values of \(\alpha\) and \(\beta\) are set at initial phase of the network. A quartering-partition division within each second layer grid is illustrated in Fig. 2c. In addition, we assume that the sensor network has the following properties.
-
1.
Nodes are randomly deployed in the sensing area.
-
2.
Each node, as well as the sink, is quasi-stationary.
-
3.
Each sensor can automatically adjust its sensing range [22].
-
4.
Each node is location-aware through GPS [23] or other positioning techniques [24].
-
5.
Possible data lost or congestion is not considered.
-
6.
Time synchronization is available to each node.
4 Two-layer grid structure
4.1 First layer grid formation
In Fig. 2a, a hexagram locates in the coordinate points \(({x_0},{y_0})\). The hexagram represents a reference point. Based on the reference point, first layer grids can be constructed and their corresponding coordinates denoted by \({C_{\mathrm{first\_grid}}}(a,b)\) can be also obtained. Each node can calculate the coordinates of the gird it belongs to by the formula: \(a = \left\lfloor {\left( {x - {x_0}} \right) /\left( {{X_{{\rm m}}}{/}\alpha } \right) } \right\rfloor ,\,b = \left\lfloor {\left( {y - {y_0}} \right) /\left( {{Y_{{\rm m}}}/\alpha } \right) } \right\rfloor,\) where (x, y) is the sensor node coordinates. \({{X_{{\rm m}}}}\) and \({{Y_{{\rm m}}}}\) are the length and width of the monitoring region, respectively. For simplicity and without loss of generality, we assume that the coordinates of \({C_{\mathrm{first\_grid}}}(a,b)\) are positive integer.
Sensor nodes deployed in the same grid form a cluster. In the cluster, a node with larger residual energy while closer to the center of first layer grid is more likely to be selected as a first layer cluster head. The cluster head acts as an intermediary between second layer cluster heads and the sink node. To compete for becoming a cluster head, each node is assigned with a back-off time \({T_{{\mathrm{{backoff\_big}}}}}\), which is derived via formula (1).
where \(E_{\mathrm{residual}\_1}\) denotes the residual energy, R denotes the distance between the sensor node and the center of the first layer grid. The mathematical expression of R is given in formula (2):
After \(T_{{\mathrm{{backoff\_big}}}}\) expires, the node will broadcast an advertisement packet within the first layer grid to which it belongs and announce that it becomes a cluster head. If a node receives an advertisement packets from other nodes, it will extract the location information of the first layer cluster head in the packet.
4.2 Second layer grid formation
As shown in Fig. 2b, second layer grids are constructed based on first layer grids. A node can calculate the coordinates of the second layer grid it belongs to, denoted by \({C_{{\mathrm{{second}\_grid}}}}({{{c}}},d)\) as follows:
where a and b are the coordinate parameters of the first layer grid to which the node belongs.
All the nodes within the same second layer grid form a cluster. In the cluster, a second layer cluster head is chosen as an intermediary between non-cluster nodes and first layer cluster heads. Since the scale of the second layer grid is small, residual energy is considered as the only metric in cluster head election. Similarly, we define a back-off time for each node to compete for becoming a cluster head:
After back-off time expires, each node tries to win the election as a cluster head by broadcasting an advertisement packet which includes its ID, coordinates of both first layer grids and second layer grids. If a node receives the advertisement from other nodes within the same first layer and second layer grids, it will retract its advertisement and extract the location information of the second layer cluster head in the received packet.
To conserve energy, each node is able to work under different transmission power. The communication radii of normal nodes and second layer cluster heads are denoted by \(R_{{\mathrm{{trans\_node}}}}\) and \(R_{{\mathrm{{trans\_level\_2}}}}\), respectively. To maintain the connectivity between normal nodes and second layer cluster heads, and the connectivity between first layer cluster heads and second layer cluster heads, relationship between \(\alpha ,\,\beta\) and communication radius should satisfy the following constraints given by formulas (6) and (7):
By solving formulas (6) and (7), values of \(\alpha ,\,\beta\) can be obtained:
4.3 Quartering-partition design
To avoid the distortion of object boundary caused by uneven node distribution, we propose a quartering-partition approach. The approach makes TGM-COT more practical in terms of toxic gas monitoring. As shown in Fig. 2c, quartering partition is constructed within the second layer grid. Each second layer grid is divided into four subregions, namely, region I, region II, region III, and region IV.
5 Continuous object tracking and boundary detection
5.1 Definition
Definition 1
(Values of nodes—VON) The default value of a node is set to be 0. If a node can detect an event, the value of the node (VON) is changed to be 1.
Definition 2
(Nodes of changed value—NCV) Compared with previous time (i.e., at time slot \(t-1\)), a node which has a different value at current stage (i.e., at time slot t) is defined as a NCV.
Definition 3
(Candidate boundary nodes—CBNs) A candidate boundary node is the node surrounding the boundary of the object. There is at least one node with a different value within CBN’s communication range.
Definition 4
(\({V_{\mathrm{{ratio}}}}\)) \(V_{\mathrm{{ratio}}}\) is the percentage of nodes whose value is 1 among the total number of nodes in the corresponding quartering-partition grid.
5.2 Proposed algorithm
TGM-COT consists of a streamlining mechanism designed for candidate boundary nodes and a mechanism of data uploading.
Step 1
Node U periodically activates to carry out local detection.
Step 2
When node U becomes a NCV, it will send a notifying message (NM) to its second layer cluster head. The second layer cluster head updates the information of non-cluster nodes to count the number of NCV.
Step 3
Boundary nodes identification
According to \(V_{{\mathrm{{ratio}}}}\), the identification of boundary nodes in a quartering-partition region can be divided into three cases.
Case 1
\(0\,<\,{V_{\mathrm{ratio}}}\,<\,1\)
In this case, both nodes with value 0 and 1 are in the quartering partition simultaneously. Nodes with value 0 are selected as CBNs. As shown in Fig. 3a, nodes a–f are CBNs.
Case 2
\({V_{\mathrm{ratio}}} = 1\) or \({V_{\mathrm{ratio}}} = 0\)
In this case, all the nodes’ values are 1 or all their values are 0 in the corresponding quartering partition. When the object boundary expands, a subset of nodes’ values change into 1. Oppositely, when the object boundary shrinks, the nodes’ values change into 0. Fig. 3b shows an example of the situation. In Fig. 3b, a continuous object moves from left to right. In the left cluster, all the nodes can detect the target so that they are assigned with value 1. In the right cluster, none of the nodes can detect the object so that they are assigned with value 0. Because nodes in quartering partition cannot satisfy the case that \(0< {V_{\mathrm{ratio}}} < 1\), the boundary nodes cannot be identified using the identification rule in case 1. In this regard, the phenomenon of boundary distortion comes up. To avoid the phenomenon of boundary distortion, each second layer cluster head sends a warning message (WM), including the sender’s first layer coordinates, second layer coordinates and the corresponding quartering-partition number, to its neighboring second layer cluster heads. As shown in Fig. 3b, when the object expands, nodes which cannot detect the object in \({P_{{{t - 1}}}}\) while can detect the object in current time \(P_{{{t}}}\) will send NMs to their second layer cluster heads, and the cluster heads can make statistical analysis to calculate \(V_{\mathrm{ratio}}\). The NMs are transmitted from the left quartering partition to the right quartering partition, and the second layer cluster heads on the right side make the judgment based on the statistical analysis. If \(V_{{\mathrm{ratio}}} = 0\), the left cluster heads will send a reply message to the right cluster heads to notify that all the nodes’ value in their cluster are 0, so as to ensure that all the CBNs identified are outer type. Then the right cluster heads can identify the corresponding CBNs within their related quartering-partition region. Based on the rules for boundary identification mechanism proposed above, it can be acknowledged that whether the object expands or shrinks, nodes a–f are always outer-type CBNs.
Case 3
A special case
In Fig. 3c, the dark stripe region is a blank area without any nodes. Second layer cluster head A marks the region as a blank area at the initial stage. If an object moves into the region, the second layer cluster head A will send a WM to its neighboring second layer cluster heads B and C. Once the second layer cluster heads B and C receive the WMs, they will make a local judgment about which case it fits (case 1 or case 2). Based on the analysis above, node a–f are identified as CBNs in the corresponding region. In this regard, this prevention mechanism can effectively avoid boundary distortion phenomenon.
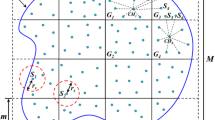
Figure 4 illustrates the above-mentioned three cases of boundary nodes identification. In Fig. 4a, the scenario in region C is an example of Case 1. Nodes e–h can be identified as CBNs according to the judgment criterion: \(0< {V_{\mathrm{ratio}}} < 1\). Analogously, nodes i and j in region G are also CBNs. According to the judgment criterion of Case 2, nodes a–d in region B are recognized as CBNs. So are the nodes q–v in region F. There is a blank area in region G. When a target move into region G, a cluster head in region E will send a WM to its neighboring cluster heads in region G and F. Then, the second layer cluster heads in G and F run the local boundary nodes identification mechanism, nodes k–p are identified as CBNs.
Step 4
Streamlining mechanism
Based on the analysis mentioned above, CBNs can be effectively identified. However, since nodes are usually densely deployed, many redundant nodes can be recognized as CBNs. To address this problem, we introduce two concepts of distance: the relative distance \(d_{\mathrm{rel}}\) and the absolute distance \(d_{\mathrm{abs}}\). \(d_{\mathrm{abs}}\) is the Euclidean distance. \(d_{\mathrm{rel}}\) is the distance between two CBNs projected onto the grid line. Only \(d_{\mathrm{abs}} > \sigma\) and \({d_{\mathrm{rel}}} > \varepsilon\) (\(\varepsilon\) and \(\sigma\) are system parameters), the node can be regarded as a final boundary node.
In Fig. 5, CBNs are \(a, b,\ldots ,j\) and k. Although the \(d_{\mathrm{abs}}\) between nodes h and i meets the constraint: \({d_{\mathrm{abs}}} > \sigma\), the relative distance \(d_{\mathrm{rel}}\) cannot satisfy the requirement: \({d_{\mathrm{rel}}} > \varepsilon\). Finally, nodes a–k are selected as final BNs.
Step 5
Data upload
It is unwise to involve all the BNs in data upload. Since the information of normal nodes are stored in second layer cluster heads, the second layer cluster heads only need to extract and compress the information, and then send to the corresponding first layer cluster heads. Each first layer cluster head brings together the information received from second layer cluster heads and forward them to the sink node. Figure 2a, b show the direction of data flows. Unidirectional data are uploaded from normal nodes to the second layer cluster head. And then, from second layer cluster heads to the first layer cluster head. Finally, from first layer cluster heads to the sink node.
6 Performance evaluation
In this section, performance of TGM-COT is evaluated by a series of simulations using Matlab. TGM-COT is compared with continuous object tracking algorithm DEMOCO and TG-COD.
6.1 Simulation setting
In simulation, nodes are randomly deployed over a 100 m \(\times\) 100 m square. The shape of the continuous object is simulated as a quarter circle. At the lower left corner of the network, the object initiated with the radius of 0 m and diffuses at a rate of one meter per second. Tracking period is set to be 1 time slot and experimental results are recorded every 20 time slots. Power consumption rates in active modes and sleep modes are 3 mW and 15 μW. Transmitting and receiving power consumption rates are 35 and 38 mW [25]. We take the average of 200 simulation runs as the final results to reduce accidental errors. A node’s ID, first layer grid coordinates and second layer grid coordinates are all assumed to be 1 byte. The value of \(\alpha\) and \(\beta\) is 3 and 4, respectively.
We compare TGM-COT with DEMOCO [17] and TG-COD [18] in terms of the number of boundary and represent nodes, the number of exchanged packet, energy consumption and tracking accuracy. We analyze the impacts of communication range R and the number of nodes N on the performance of the tracking algorithms.
-
1.
Number of boundary and represent nodes Redundant boundary nodes and report nodes bring more message exchange. Under the premise that the tracking accuracy is ensured, less nodes are preferred to be involved in the object tracking.
-
2.
Number of exchanged packet Exchanged packet falls into two categories: the control messages and the report messages. The former are exchanged in the process of boundary identification, while the latter are transferred to the sink node.
-
3.
Energy consumption We record the energy consumed from beginning to the current time span, and the energy consumption in per time slot, respectively.
-
4.
Tracking accuracy We define a parameter \(e\left( i \right)\) in formula (10) to quantify the tracking accuracy:
$$\begin{aligned} e\left( i \right) = \frac{{\sum \nolimits _{j = 1}^m {\sqrt{{{\left( {r\left( j \right) - r} \right) }^2}} } }}{m} \end{aligned}$$(10)where \(r\left( j \right) = \sqrt{{x_j}^2 + {y_j}^2}\); m denotes the number of boundary nodes; \(\sqrt{{{\left( {r\left( j \right) - r} \right) }^2}}\) means the absolute distance between the boundary node with the coordinates of \(\left( {{x_j},{y_j}} \right)\) and the real boundary of the object. The value of \(e\left( i \right)\) closer to 0 indicates a better tracking accuracy the algorithm can achieve.
6.2 Simulation results
6.2.1 Snapshots of tracking contours
Figure 6 illustrates the tracking snapshot of a shrinking object at 200 time slot. Blue nodes denote the normal nodes and red nodes denote the current boundary nodes. The comparison shows that, boundary nodes are always distributed along the outer boundary in Fig. 6a, while in Fig. 6b, the boundary nodes are all in the internal boundary of the object. Understandably, in DEMOCO [17], while the object is shrinking, the Changed Value Nodes (CVNs) which send the CompareOneZero message (COZ) are located outside the object. Therefore, nodes neighboring CVNs meanwhile staying inside the object would be the boundary nodes. Oppositely, while the object is expanding, the boundary nodes stay out of the object boundary. However, TGM-COT is robust to the expanding or shrinking of the object. In the lower right-hand corner of Fig. 6b, phenomenon of boundary distortion exists because DEMOCO does not have any precautionary measures to deal with uneven node distribution. Based on the analysis, we can draw a conclusion that TGM-COT is more practical and applicable for tracking continuous objects than DEMOCO.
6.2.2 Number of boundary nodes and report nodes
The number of BNs and report nodes reflects the tracking efficiency of an algorithm. On the premise that the tracking accuracy can be ensured, less boundary nodes and report nodes helps to improve energy efficiency. Figure 7 shows the number of boundary nodes the three algorithms identified. Three curves have the same trend which is determined by the diffusion of the object. The diffusion rule follows a circulative process. With the movement of the target, the area covered by the target gradually expands and reaches to a maximum value. Then, the target shrinks. It should be pointed out that DEMOCO generates more BNs than TGM-COT in any time slot. It is because DEMOCO cannot eliminate redundant nodes which serve no benefit to the tracking accuracy.
TGM-COT produces more BNs than TG-COD, owing to different identification mechanisms. TG-COD uses a grid as the BNs to achieve energy saving. However, tracking accuracy decreases by using grids to describe the object boundary.
In Fig. 8, we compare the number of report nodes generated by the algorithms. Three curves also have the same trend determined by the diffusion of the object. Report nodes in DEMOCO are nodes which could cover neighboring BNs within their communication range. The number of report nodes is related to the communication R. While report nodes in TGM-COT are just first layer cluster heads. Therefore, the number of report nodes in DEMOCO is larger than that of TGM-COT. However, it should be pointed out that TGM-COT generated a little more report nodes than TG-COD, because TG-COD uses a certain ratio of boundary nodes to achieve a dynamic equilibrium process between expansion and shrink of the object.
6.2.3 Number of exchanged message
In this section, we compare the communication overhead during the process of target tracking. Traffic load is caused by transmitting two kinds of message, namely, control message and report message. The former denotes the message generated in the process of boundary node identification. The latter denotes the messages sent to the sink node by report nodes. Less message exchange suggests the characteristic of energy efficiency and timeliness.
Figure 9 compares the variation of control messages broadcast by TGM-COT, TG-COD and DEMOCO over time. The number of control messages increases with the increasing radius of the object and then declines as the radius of the object decreases.
In DEMOCO, the BNs are determined by COZ messages sent by CVNs. However, first layer cluster heads which function as report nodes are selected at network initialization stage in TGM-COT and TG-COD. It means in TGM-COT and TG-COD, control messages used for report nodes selection can be omitted.
Figure 10 compares the number of report messages generated by the three algorithms. For any given time slot, it can be observed that the number of report nodes changes with the object radius. Furthermore, TGM-COT consistently outperforms DEMOCO in terms of the number of report nodes. Due to the similar network structure, TGM-COT and TG-COD have similar performance in terms of the number of report nodes. Figure 11 shows the number of total messages, which include the control messages and the report messages in the process of target tracking. Based on the above-mentioned analysis, it is understandable that the variation of exchanged messages in each time slot follows the change of the area covered by the object.
6.2.4 Energy consumption
Figure 12 illustrates the energy consumption in each time slot. At network initialization stage, due to the additional energy consumption caused by the construction of two-layer grid structure in TGM-COT and TG-COD, DEMOCO outperforms than TGM-COT and TG-COD. It can be observed that DEMOCO consistently consumes more energy than TGM-COT and TG-COD after 20 time slot. During the first 100 time slot, the object expands so that nodes involved to track it increase. Since the energy consumed in each time slot is determined by the number of exchanged message, the energy consumption increases with the increasing message. In the following 40 time slot, the object begins to shrink, and the nodes involved to track it decrease. Therefore, the energy consumption decreases during this stage.
Figure 13 shows the total energy consumption in the 200 time slots. Since in TG-COD, energy is consumed for data exchanging, and the boundary information is proactively gathered and sent to the sink node, TG-COD slightly outperforms the TGM-COT in terms of total energy consumption.
6.2.5 Tracking accuracy
Figure 14 depicts the relationship between the number of node and the tracking accuracy achieved by each algorithm. It can be observed that the impact of node density on tracking accuracy is small. While the communication range has large influence on tracking accuracy. It is because, although the node density determines the number of BNs, as denoted in the formula (12), with the expanding of the object, subsection \(\sum \nolimits _{j = 1}^m {\sqrt{{{\left( {r\left( j \right) - r} \right) }^2}}}\) of \(e\left( i \right)\) increases as well. Then the \(e\left( i \right)\) keeps a dynamic equilibrium. On the other hand, as the communication range R changes from 5 to 8 m, more sensor nodes will become neighbors of those CVNs. Among these neighbors, there are boundary nodes which locate far away from real boundary of the object. Such supplement increases the subsection \(\sum \nolimits _{j = 1}^m {\sqrt{{{\left( {r\left( j \right) - r} \right) }^2}} }\) of \(e\left( i \right)\). For TGM-COT and TG-COD, it seems that node density has larger effect than communication range on tracking accuracy because fine-grained grids determines the object boundary. If the density of node can be maintained, the tracking accuracy will keep stable with the change of the communication range. However, with the increasing of the node density, less error is incurred in determining the \({B_{\mathrm{ratio}}}\), which is designed for boundary grid identification. Nevertheless, with a similar two-layer grid structure and a boundary nodes identification mechanism, TGM-COT is robust to the number of nodes. Additionally, owing to the advantage of streamlining mechanism which eliminates redundant nodes, TGM-COT outperforms the other two algorithms.
7 Conclusion
In this paper, an energy-efficient continuous object tracking scheme with two-layer grid model is proposed for WSNs. The proposed scheme divides the monitored region into both coarse-grained and fine-grained grids. A novel mechanism for boundary nodes identification is designed and the problem of boundary distortion caused by uneven node distribution is also addressed. Furthermore, we put forward a streamlining mechanism for candidate boundary nodes selection, which is beneficial to reduce the number of boundary nodes and significantly increase the tracking accuracy. Simulation results demonstrate that TGM-COT outperforms TG-COD and DEMOCO in terms of energy efficiency and tracking accuracy.
References
Han G, Jiang J, Shu L, Xu Y, Wang F (2012) Localization algorithms of underwater wireless sensor networks: a survey. In: Sensors (Basel, Switzerland), pp 2026–2061
Baadache A, Adouane R (2015) Minimizing the energy consumption in wireless sensor networks. J Ad Hoc Sens Wirel Netw 27:223–237
Zhang D, Zhou J, Guo M, Cao J (2011) TASA: tag-free activity sensing using RFID tag arrays. IEEE Trans Parallel Distrib Syst 22:225–270
Zhao J, Mo L, Wu X, Wang G, Liu E, Dai D (2014) Error estimation of iterative maximum likelihood localization in wireless sensor networks. J Ad Hoc Sens Wirel Netw 23:277–295
Yingqi X, Winter J, Lee W-C (2004) Prediction-based strategies for energy saving in object tracking sensor networks. In: IEEE international conference on mobile data management, pp 346–357
Yingqi X, Winter J, Lee W-C (2004) Dual prediction-based reporting for object tracking sensor networks. In: Annual international conference on mobile and ubiquitous systems, pp 154-163
Chen WP, Hou JC, Sha L (2004) Dynamic clustering for acoustic target tracking in wireless sensor networks. IEEE Trans Mobile Comput 3:258–271
Liu BH, Ke WC, Tsai CH, Tsai MJ (2008) Constructing a message-pruning tree with minimum cost for tracking moving objects in wireless sensor networks is NP complete and an enhanced data aggregation structure. IEEE Trans Comput 57:849–863
Lazos L, Poovendran R, Ritcey JA (2007) Detection and tracking: probabilistic detection of mobile targets in heterogeneous sensor networks. In: International conference on information processing in sensor networks, pp 519–528
Song L, Hatzinakos D (2007) A cross-layer architecture of wireless sensor networks for target tracking. IEEE/ACM Trans Netw 15:145–158
Shrivastava N, Mudumbai R, Madhow U, Suri S (2006) Target tracking with binary proximity sensors: fundamental limits, minimal descriptions, and algorithms. In: International conference on embedded networked sensor systems, pp 251–264
Yueqin Z, Xiaopeng D (2010) Based on cluster cover algorithm in coal mine gas forecast application. In: 2010 International conference on intelligent computation technology and automation (ICICTA 2010), pp 854–857
Hajiaghajani F, Naderan M, Pedram H (2012) HCMTT: hybrid clustering for multitarget tracking in wireless sensor networks. In: Processing of 2012 IEEE international conference on pervasive computing and communications workshops, pp 889–894
Schurgers C, Tsiatsis V, Ganeriwal S, Srivastava M (2002) Topology management for sensor networks: exploiting latency and density. In: Processing of the third ACM international symposium on mobile ad hoc networking and computing (MobiHoc), pp 135–145
Liao PK, Chang MK, Kuo CJ (2004) Distributed edge detection with composite hypothesis test in wireless sensor networks. In: Processing of IEEE communication society Globecom, pp 129–133
Chang WR, Lin HT, Cheng ZZ (2008) CODA: a continuous object detection and tracking algorithm for wireless ad hoc sensor networks. In: Processing of the 5th IEEE consumer communications and networking conference (CCNC 2008), pp 168–174
Kim JH, Kim KB, Chauhdary SH, Yang W, Park MS (2008) DEMOCO: energy-efficient detection and monitoring for continuous objects in wireless sensor networks. IEICE Trans Commun E91-B:3648–3656
Park B, Park S, Lee E (2010) Large-scale phenomena monitoring scheme in wireless sensor networks. In: Processing of VTC 2010—Spring, pp 1–5
Hong SW, Noh SK, Lee E, Park S, Kim SH (2010) Energy-efficient predictive tracking for continuous objects in wireless sensor networks. In: Processing of PIMRC 2010, pp 1725–1730
Lee W, Yim Y, Park S (2012) Selective wakeup discipline for continuous object tracking in grid-based wireless sensor networks. In: IEEE Conference—WCNC wireless communication and networking, pp 2179–2184
Kim WS, Park HS, Lee JC (2012) Efficient continuous object tracking with virtual grid in wireless sensor networks. In: Processing of VTC 2012 Spring, pp 1–5
Jin DX, Chauhdary SH, Ji X (2009) Energy-efficiency continuous object tracking via automatically adjusting sensing range in wireless sensor network. In: Processing of the fourth IEEE international conference on computer sciences and convergence information technology, pp 122–127
US Naval Observatory (USNO) GPS Operations. http://tycho.usno.navy.mil/gps.html
Han G, Zhang C, Shu L, Rodrigues JJPC, Lloret J (2014) A mobile anchor assisted localization algorithm based on regular hexagon in wireless sensor networks. In: Processing of the Scientific World Journal
Hong H, Oh S, Lee J, Kim S (2013) A chaining selective wakeup strategy for a robust continuous object tracking in practical wireless sensor networks. In: Processing of 2013 IEEE 27th international conference on advanced information networking and applications (AINA), pp 333–339
Acknowledgments
The work is supported by “Qing Lan Project”, “National Science Foundation of China, Nos. 61572172 and 61401107”, “2013 Special Fund of Guangdong Higher School Talent Recruitment, Educational Commission of Guangdong Province, China Project No. 2013KJCX0131” and “Guangdong High-Tech Development Fund No. 2013B010401035”.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Han, G., Shen, J., Liu, L. et al. TGM-COT: energy-efficient continuous object tracking scheme with two-layer grid model in wireless sensor networks. Pers Ubiquit Comput 20, 349–359 (2016). https://doi.org/10.1007/s00779-016-0927-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00779-016-0927-7