Abstract
We demonstrate that a vectorial beam with a random polarization state can be used as the illumination source in a joint transform correlator configuration to encrypt and compress images. Illumination light featuring both space-variant phase and a space-variant polarization distribution can be generated using a common-path interferometric arrangement. A hybrid joint power spectrum is registered using an array of linear micro-polarizers that is closely attached to a charge-coupled device in the recording plane. Introduction of the vectorial beam into a security application enables simultaneous manipulation of multiple light wave parameters, which will significantly enlarge the key dimensions and key space of the cryptosystem. This vectorial optical cryptosystem may also provoke interest in probing optical vector encryption methods.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
As a salient feature and part of the intrinsic nature of light, polarization plays an important role in interactions between light and matter. Vectorial optical fields with spatially variant states of polarization (SoPs) have attracted wide interest because of their remarkable properties and potential applications in various areas [1]. For example, a more sharply focused spot beyond the diffraction limit has been observed when a cylindrical vector beam was focused using a high-numerical-aperture lens [2]. Other significant applications include particle guidance [3], acceleration and trapping [4, 5]. Motivated by both known and potential applications, various methods for the effective generation of arbitrary vector beams have been proposed. For example, an interferometric approach allows both the SoPs and the phase of the vector beam to be tailored independently [6]. In addition to the cylindrical symmetrical vector beams, vector fields with elliptic symmetry and bipolar symmetry have also been generated and analyzed [7, 8]. These new types of vectorial beam provide additional degrees of freedom that assist in the engineering of the field distribution at the focus, and may lead to specific applications such as lithography and material processing.
In addition to vectorial beams with symmetrical SoPs distributions, structured optical fields with random polarization patterns have shown fascinating potential for data security applications because they provide additional degrees of freedom for encryption that can fully exploit the multi-dimensional processing capabilities of optical methods. One approach for the generation of arbitrary three-dimensional polarization orientations using a single optically configured vectorial beam was applied to gold nanorods to achieve orientation-unlimited polarization encryption with ultra-security [9]. Geometrical phase encryption obtained using space-variant subwavelength gratings has also been proposed [10]. A dual encryption scheme has been developed based on a matrix of linear polarizers using Mueller matrix calculus [11], and the robustness of this algorithm against various attacks has also been investigated [12]. Other methods based on polarization encryption include double-random polarization image encoding [13] and image encryption based on polarized light interference [14].
In this paper, we explore the application of a vectorial beam with random SoPs and random phase patterns to image encryption. The principle of the proposed method is double-random phase encoding (DRPE) with a joint transform correlator (JTC) configuration [15–18]. The illuminating vectorial beam can be engineered to have random phase and random SoPs distributions, which both serve as keys in a common-path interferometric vector generator. In the recording plane, an array of micro-polarizers (AMP) with transmission axes that are oriented randomly in the horizontal or vertical directions is combined with a charge-coupled device (CCD) camera to register a hybrid joint power spectrum (JPS) as the ciphertext. An effective compression method is then proposed that is especially suitable for this encryption scheme. The proposed cryptosystem can make full use of the multi-dimensional abilities of optical methods for secure data transmission.
2 Principles
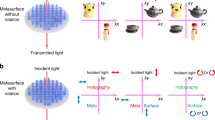
The encryption and decryption setups of the proposed cryptosystem are illustrated schematically in Fig. 1a, b, respectively. The encryption architecture is composed of three main components, comprising a specific vector wave generator, an aperture with two windows and the JTC encryption configuration. In the following, these three components are described.
The vector wave generator used here is based on a common-path interferometric arrangement. By loading a calculated holographic grating (HG) on a spatial light modulator (SLM) in the input plane of the 4-f system and filtering the diffracted terms in the spatial frequency plane using two quarter-wave plates (QWPs), this configuration enables the generation of vectorial beams with space-variant distributions of both the SoPs and the phase. A detailed description of the principle of this generator can be found in [6], and it will therefore not be described here.
Other than the generation of radial or azimuthal vector beams [6], in this paper, we describe the generation of vectorial beams with both random SoPs and random phase distributions for illumination applications. The amplitude transmission function of the SLM with a HG written onto it can be expressed as,
In Eq. (1), δ 1(x, y) and δ 2(x, y) are additional phases that are uniformly and randomly distributed between 0 and 2π and are imposed on the vertical and horizontal HGs, respectively. Also, f 0 and γ are the spatial frequency and the modulation depth of the HG, and x and y are the coordinates in the spatial domain, as shown in Fig. 1. When a linearly polarized plane wave is incident on the HG, the output vector beam can be given as a superposition of the left-hand and right-hand circular polarization components [6],
in which \(\alpha = (\delta_{1} - \delta_{2} )/2\) and \(\beta = (\delta_{1} + \delta_{2} )/2\). Equation (2) shows a vectorial beam with phase and locally linear SoPs distributions that are used as the illumination beam for the proposed cryptosystem.
The aperture between the vector wave generator and the input SLM of the JTC scheme is both essential and important. It should be noted here that the Ronchi grating, the aperture and the input SLM should be sufficiently close together to avoid any unwanted diffraction caused by wave propagation within the Fresnel diffraction distance.
Several functions are assigned to this aperture. First, the sizes and positions of the two windows that are opened within this aperture should be designed and adjusted to match the diameter of the output vectorial beam to the distance between the centers of the object image and the reference image, i.e., the two windows should be able to select parts of the vector beam profiles in the cross section to fully cover the joint images that are displayed on the input SLM. The second meaningful function is the ability to simply and rapidly update the illumination beam, which is achieved by moving the aperture that is bonded with the input SLM to within the diameter of the vectorial beam. In this sense, the aperture position can be regarded as a key for the proposed system. From another perspective, the translation of the aperture together with the input SLM may lead to a lateral translation multiplexing-based optical encryption method.
In the JTC encryption section, a parallel-aligned liquid crystal device (PAL-LCD) is located on the input plane of the JTC scheme. The PAL-LCD offers the advantage that its orthogonal polarization state is unaffected by the device. As a benefit of this property, transformation of the SoPs can be achieved using the PAL-LCD. Therefore, the JTC part of our proposal can be called the polarization joint transform correlator (PJTC). The Jones matrix of an object at coordinate x = a on the PAL-LCD with fast axes orientated at 0° with respect to the y-axis is,
where fn(x, y) is the normalized \(f(x,y) \times n(x,y)\) product, in which f(x, y) is plaintext, and n(x, y) is a random number matrix that is uniformly distributed in the interval of [0–1]. Note that the one-dimensional expression is used for simplicity here.
When the generated vectorial beam is incident on the input SLM, the spatial SoPs distributions of the object window and the reference window are, respectively,
In Eq. (5), h(x, y) denotes the normalized random phase mask in the reference window. Here, we must recall the third function of the aperture sandwiched between the Ronchi grating and the input SLM. For a PAL-LCD working in a polarization modulation mode, the Jones matrix of the birefringent molecules becomes an identity matrix when a zero voltage is applied. In this situation, the SoPs of the incident vectorial beam would remain unchanged after passing through the PAL-LCD. To perform the PJTC function, this case must be avoided. Therefore, an aperture with only two separate windows that allow the transmission of part of the vectorial beam is essential.
A Fourier lens and a CCD camera attached to an AMP are arranged to perform the PJTC function and record the hybrid JPS. For fully polarized and fully coherent illumination, the Jones matrix treatment for an optical Fourier processor with structured SoPs can be applied to calculate the vectorial diffraction [19]. Thus, the hybrid JPS, which is used as the ciphertext, can be expressed as,
In Eq. (6), FT{·} denotes the Fourier transform operator. The subscript “hy” represents a hybrid of the horizontal and vertical JPS, where the horizontal or vertical JPS can be obtained when either a horizontal or vertical polarizer is placed in front of the CCD camera, respectively. An AMP placed just in front of a photodetector array is used as a polarization imaging camera (PIC) [20]. Each single micro-polarizer on each pixel has a different light transmission axis that is randomly and uniformly oriented in either the horizontal or vertical direction, depending on the spatial position coordinates, as shown in Fig. 1a. This kind of device can be fabricated using photonic crystals provided, for example, by Photonic Lattice, Inc. This nonlinear recording operation can also further enhance the security level of the system.
The decryption configuration is a 4-f system, as shown in Fig. 1b. Authorized users can simply block the object window within the aperture and lay the hybrid JPS in the spatial frequency plane. Here, the hybrid JPS, which has a pure intensity distribution, should be physically placed in the rear focal plane of the first Fourier lens. This can be implemented by loading the transmittance function of the hybrid JPS on a SLM working in amplitude modulation mode. The decryption AMP attached to the hybrid JPS should be reproduced while only the horizontal or vertical components of the micro-polarizer are “turned on,” i.e., when the horizontal components of the hybrid JPS are chosen to retrieve the plaintext, the decryption AMP should be part of the encryption AMP with all the vertical micro-polarizers being shut out to cut off the illumination light. It should be noted that the elements of the AMP must be matched with the hybrid JPS in terms of both position and size. For example, when using the PI-110 polarization imaging camera with a typical micro-polarizer on the 5-µm scale in front of the CCD camera during recording, the pixel sizes of the CCD and the SLM must be ≤5 µm. Of course, any necessary rescaling of the hybrid JPS may be conducted during the experimental process to meet this requirement.
From a holographic point of view, the JPS can be regarded as a piece of a digital hologram; therefore, decryption using the AMP is equivalent to sampling of a partial horizontal JPS or vertical JPS for holographic reconstruction. In this case, the decrypted image must suffer some loss of resolution and noise, which can be observed in the following simulation results. The decryption process using a sampled JPS can be denoted by,
in which IFT{·} denotes the inverse Fourier transform operator and x s is the sampled spatial coordinate. The subscript H represents the horizontal component of the vectorial beam or the hybrid JPS. From Eq. (7), we can determine that when coordinate x = a, the object function can be observed. The complete recovery of the plaintext f(x, y) can be achieved by eliminating all additional terms of the vectorial beam and extracting the phase in Eq. (4). This vectorial illuminated PJTC (VI-PJTC) security system has five keys, including the SoPs and the phase keys of the vectorial beam, the reference window phase key, the position of the aperture and the AMP orientation key.
3 Simulations and discussions
We perform a proof-of-concept study using simulations based on the MATLAB 7.01 platform to verify the feasibility of this proposal. It was noted that the proposed scheme shows good practicability when the original information is represented by a quick response (QR) code. Here, the message “Mechanical Engineering College” (Fig. 2a) is coded into the 256 × 256 pixel QR code shown in Fig. 2b. The version type is set as 2, and the error correction capability is chosen as L (7 %). All QR codes are generated using the software Psytec QR code editor. Following these protocols, the JPSs in the horizontal and vertical directions are shown in Fig. 2c, d. The hybrid JPS is shown in Fig. 2e. During the reconstruction process, the decrypted QR code emerges from the noise, as shown in Fig. 2f, h, after an adjacent pixel interpolation post-processing step when using either the horizontal JPS (HJPS) or the vertical JPS (VJPS), respectively. The extracted and magnified images are shown in Fig. 2g, i. Thanks to the error correction property of the QR code, a noise-free plaintext can be produced using a QR code scanning app on a smartphone, and the results can be observed in Fig. 2j, k for the images of Fig. 2g, i, respectively. When the hybrid JPS is used for decryption, no message can be revealed, as shown in Fig. 2l.
a Original message; b QR code of message on (a); c horizontal JPS; d vertical JPS; e hybrid JPS; f decrypted image from partial horizontal JPS; g locally magnified QR code from (f); h decrypted image from partial vertical JPS; i locally magnified QR code from (h); j, k scan results for (g) and (i), respectively; l decrypted image from hybrid JPS
We then evaluate the sensitivity and the fault tolerance of the different keys during decryption. Note that the proposed system necessitates the use of the horizontal or vertical components of the hybrid JPS for successful recovery of a QR code. During the numerical simulation process, we generate a decryption AMP key with a MATLAB uniform random function, in which the distribution of the horizontal micro-polarizers and the vertical micro-polarizers is completely disordered in positional terms when compared with the encryption AMP. Under these conditions, the decrypted QR codes are as shown in Fig. 3a, b when using the HJPS and the VJPS, respectively. Note that the wrongly decrypted QR codes are all noise. However, we can see that the proposed scheme is more sensitive to the vertical AMP key when using the vertical JPS for decryption. This result is not difficult to understand because the mismatch between the JPS with the corresponding decryption wave will inevitably induce noise, which will then be superposed onto the correct decrypted part. Then, when the reference window random phase key is in error, in the same manner as the generation of the wrong AMP key, the decrypted QR code is shown in Fig. 3c, d when using HJPS and VJPS decryption, respectively. Some blurred silhouettes can be seen, but no information can be read out, even after binarization. Also, when the selected beam profile of the illuminating vectorial beam is wrong in one pixel (which is quite common, because the position of the vector wave generator may vary because of vibration), the decrypted QR codes are as shown in Fig. 3e, f. Obviously, nothing but noise is presented. This tells us that the relative positioning of the aperture and the vector wave generator is important for correct decryption. Therefore, in practical use, the two components should be bonded together or made adjustable using precision mechanical structures. The information in the QR codes cannot be retrieved from Fig. 3a–f, even after blocking, processing and binarization.
Wrongly decrypted images. a, b AMP keys are wrong for HJPS and VJPS decryption; c, d reference window random phase key is wrong for HJPS and VJPS decryption; e, f vector wave generator translated only one pixel for HJPS and VJPS decryption; g, h only the phase component of the vectorial beam is used to decrypt for HJPS and VJPS decryption; i, j only the SoPs component of the vectorial beam is used to decrypt for HJPS and VJPS decryption
Then, to verify the importance of the structures of the vectorial beam to decryption, we perform an analysis based on the proviso that only the phase or SoPs components of the illuminating wave are used for decryption. The phase-only decryption case is tested by simply generating a scalar wave with only the phase profile of the original encryption vectorial beam. At the same time, the SoPs-only decryption is performed by waiving the phase term β(x, y) in the vectorial beam, which leaves only the SoPs component correct. The results are shown in Fig. 3g, h for phase-only decryption and in Fig. 3i, j for SoPs-only decryption when using HJPS or VJPS, respectively. The results reveal that when HJPS is used for decryption, the phase component of the vectorial beam is more important, while the SoPs component of the vectorial beam is more important than the phase component when using VJPS for decryption. This property can be recognized as a unique feature of this cryptosystem that may confuse an attacker who does not have pre-knowledge of the composition of the ciphertext.
Finally, we evaluate decryption using either partial HJPS or VJPS. It is essential that the QR code is retrieved using partial JPS, because the AMP leads to a nonlinear cut of the full JPS. Therefore, the percentage of HJPS or VJPS required for successful recovery of the QR code should be made clear. The relationship between the correlation coefficient (CC) of a retrieved QR code and the original QR code and the percentage of the JPS is shown in Fig. 4. For successful reading of the QR code, about 45 % of the HJPS or VJPS should be used for decryption, which means that 45 % of the decryption AMP keys should be correct to obtain satisfactory decrypted image quality. Of course, this proportion will vary with the error correction capability of the individual QR code. It should also be noted here that the theoretical limit for the CC function versus the fragment percentage is much smaller than 1; this can be explained using the sampling theorem for holographic reconstruction. From Eq. (7), we see that the spatial coordinate denotes the sampled coordinate, which indicates that the recovery must suffer some kind of loss of resolution or noise. The noise that accompanies the decrypted image thus cannot be eliminated theoretically. This noise originated from the nonlinear cut on the JPS with the AMP. However, the QR code has intrinsic advantages against pollution and noise; also, the accompanying noise is always high-frequency noise, which will not affect the identification of the QR code, and the original information coded within the QR code can still be read out as shown in Fig. 2j, k. In view of this, while the AMP key reduced the decrypted image quality, the accompanying security enhancement should be praised.
Based on the error analysis above, we see that the proposed scheme shows relatively good performance for different key dimensions. However, the development of modern communication systems is accompanied by an urgent demand for the reduction of the transmitted data. To alleviate or solve this problem, a compression method should be integrated into optical cryptosystems, as it is in traditional security systems. Fortunately, the proposed system is suitable for the addition of a compression algorithm. A special compression process is also proposed hereinafter.
From both the theoretical deductions and the numerical analysis, we can see that only a part of the pixels within the hybrid JPS are essential for correct decryption. The only contributions of the other pixels may be to confuse attackers. Therefore, these data seem to be redundant. However, they are still all transmitted as part of the ciphertext. Obviously, this mechanism is not efficient enough. We therefore propose to multiplex the encrypted JPSs of several plaintexts to generate a single ciphertext for transmission. This process can be simply performed as a post-processing operation after the encryption procedure for each plaintext. Note that the encryption keys for each plaintext should remain unchanged. The following three steps should then be executed.
-
1.
Encrypt each plaintext with all the same encryption keys and generate several provisional ciphertexts.
-
2.
Select partial pixels of the HJPS or VJPS within each ciphertext (the regions or pixels of the selected data for each ciphertext should not be superposed on each other) with a specific fragment percentage.
-
3.
Assemble all selected partial JPSs without overlapping and fill the remaining pixels with pre-generated random noise to form the final and compressed ciphertext. Note that the added noise can prevent decryption of the last plaintext without the corresponding AMP selection key.
A flowchart that briefly illustrates the three steps above is shown in Fig. 5. After the three operations are conducted, we obtain the final ciphertext. Apparently, this compressed ciphertext reduces the number of data bits required for transmission while leading to a simultaneously encrypted and compressed optical cryptosystem. Also, the selection regions (pixels) of the partial JPS used for each plaintext can be used as the demultiplexing AMP keys when decrypting the corresponding plaintext.
The simulation results for this compression procedure are shown in Fig. 6. A basic dual image encryption and compression process is presented. Figure 6a shows the second plaintext together with the first plaintext, which is also shown in Fig. 2a. The partial JPSs after step two is performed are shown in Fig. 6c, d for the first and second plaintexts, respectively. After recombination (step three), the compressed ciphertext is shown in Fig. 6e. In this example, about 45 % of the HJPS for the first plaintext and 30 % of the VJPS for the second plaintext are used (Q level with error correction capability of 25 %), together with about 25 % random noise. During decryption, an authorized user who knows the exact selected pixels or regions for each plaintext during compression can easily recover the original message, with results as shown in Fig. 6f, g for the first plaintext and Fig. 6h, i for the second plaintext. Note that because relatively fewer pixels were selected for the second QR code, post-processing should be performed in Fig. 6h. However, the error correction ability of the Q level can lead to successful reading of the original information.
a Second original message; b the QR code of (a); c the selected hybrid JPS for the first QR code; d the selected VJPS for the second QR code; e the compressed hybrid JPS using (c), (d) and pre-generated noise; f the decrypted first QR code; g scan result of (f); h the decrypted second QR code; i scan result of (h) after post-processing
While the proposed compression method is especially suitable for our cryptosystem, existing compression methods may also be useful. The proposed compression method is actually quite similar to the discrete cosine transform (DCT)-based method, which can multiplex several spectra of different images to form a ciphertext [21]. The spectrum phase information can also be quantized based on the root-mean-square (RMS) duration principle to compress the data that must be transmitted [22, 23].
Above all, the proposed cryptosystem not only makes full use of the multiple parameters of light waves to encrypt images but can also compress the essential data bits required for the transmission and reconstruction of information. In future work, we intend to further integrate other existing compression algorithms and analyze the attack resistibility of the proposed scheme.
4 Conclusions
In summary, we have extended the vectorial beam using random SoPs and phase distributions to achieve data encryption and compression based on a VI-PJTC architecture. The feasibility and the performance of the proposed cryptosystem are verified by several simulation results. In addition, introduction of the vectorial beam into security and compression applications enables simultaneous manipulation of multiple parameters of light waves, which will significantly enlarge the key dimensions and key space of the cryptosystem. This VI-PJTC security system may also lead to other types of vectorial optical cryptosystems, which we expect will open up new research perspectives.
References
Q. Zhan, Cylindrical vector beams: from mathematical concepts to applications. Adv. Opt. Photonics 1, 1–57 (2009)
R. Dorn, S. Quabis, G. Leuchs, Sharper focus for a radially polarized light beam. Phys. Rev. Lett. 91, 233901 (2003)
C. Varin, M. Piché, Acceleration of ultra-relativistic electrons using high-intensity TM01 laser beams. Appl. Phys. B. 74, S83 (2002)
T. Kuga, Y. Torii, N. Shiokawa, T. Hirano, Y. Shimizu, H. Sasada, Novel optical trap of atoms with a doughnut beam. Phys. Rev. Lett. 78, 4713 (1997)
Q. Zhan, Trapping metallic Rayleigh particles with radial polarization. Opt. Express 12, 3377 (2004)
H. Chen, J. Hao, B. Zhang, J. Xu, J. Ding, H. Wang, Generation of vector beam with space-variant distribution of both polarization and phase. Opt. Lett. 36, 3179 (2011)
Y. Pan, Y. Li, S. Li, Z. Ren, L. Kong, C. Tu, H. Wang, Elliptic-symmetry vector optical fields. Opt. Express 22, 19302 (2014)
Y. Pan, Y. Li, S. Li, Z. Ren, Y. Si, C. Tu, H. Wang, Vector optical fields with bipolar symmetry of linear polarization. Opt. Lett. 38, 3700 (2013)
X. Li, T.-H. Lan, C.-H. Tien, M. Gu, Three-dimensional orientation-unlimited polarization encryption by a single optically configured vectorial beam. Nat. Commun. 3, 998 (2012)
G. Biener, A. Niv, V. Kleiner, E. Hasman, Geometrical phase image encryption obtained with space-variant subwavelength gratings. Opt. Lett. 30, 1096 (2005)
A. Alfalou, C. Brosseau, Dual encryption scheme of images using polarized light. Opt. Lett. 35, 2185 (2010)
M. Dubreuil, A. Alfalou, C. Brosseau, Robustness against attacks of dual polarization encryption using the Stokes–Mueller formalism. J. Opt. 14, 094004 (2012)
O. Matoba, B. Javidi, Secure holographic memory by double-random polarization encryption. Appl. Opt. 43, 2915 (2004)
N. Zhu, Y. Wang, J. Liu, J. Xie, H. Zhang, Optical image encryption based on interference of polarized light. Opt. Express 17, 13418 (2009)
P. Refregier, B. Javidi, Optical image encryption based on input plane and Fourier plane random encoding. Opt. Lett. 20, 767 (1995)
W. Chen, B. Javidi, X. Chen, Advances in optical security systems. Adv. Opt. Photonics 6, 120 (2014)
T. Nomura, B. Javidi, Optical encryption using a joint transform correlator architecture. Opt. Eng. 39, 2031 (2000)
E. Rueda, M. Tebaldi, R. Torroba, N. Bolognini, Three-dimensional key in a modified joint transform correlator encryption scheme. Opt. Commun. 284, 4321 (2011)
I. Moreno, C. Iemmi, J. Campos, M.J. Yzuel, Jones matrix treatment for optical Fourier processors with structured polarization. Opt. Express 19, 4583 (2011)
T. Kiire, S. Nakadate, M. Shibuya, T. Yatagai, Three-dimensional displacement measurement for diffuse object using phase-shifting digital holography with polarization imaging camera. Appl. Opt. 50, H189 (2011)
A. Alfalou, M. Elbouz, M. Loussert, A new simultaneous compression & encryption method for images suitable to recognize form by optical correlation. Proc. SPIE. 7486, 74860J–74861J (2009)
A. Alfalou, M. Elbouz, A. Mansour, G. Keryer, New spectral image compression method based on an optimal phase coding and the RMS duration principle. J. Opt. 12, 115403 (2010)
A. Alfalou, A. Mansour, Simultaneous multiplexing & encoding of multiple images based on a double random phase encryption system. Proc. SPIE. 7486, 74860L–74861L (2009)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lin, C., Shen, X. & Hu, W. Information encryption and compression based on random polarization modulation in a joint transform correlator scheme under vector beam illumination. Appl. Phys. B 120, 89–95 (2015). https://doi.org/10.1007/s00340-015-6104-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00340-015-6104-2