Abstract
Aiming at the problem of the security of secret information in various potential applications, we introduce a robust information hiding algorithm based on lossless encryption, non-subsampled contourlet transform (NSCT), Hessen-berg decomposition (HD) and singular value decomposition (SVD). Firstly, the carrier and secret mark information is transformed by NSCT-HD-SVD. Secondly, the singular score of secret media information is concealed in the carrier image. Thirdly, the text document is further concealed in the carrier marked image via pseudo magic cubes to achieve the final carrier marked image. Finally, the lossless encryption scheme is utilized to encrypt the final marked image. The simulation results of the proposed algorithm indicate good invisibility and robustness effect compared to existing schemes with high security and hiding efficiency. It indicates a considerable improvement in robustness of up to 96.36% over other schemes. Overall, the proposed algorithm for various images, achieved peak signal-to-noise ratio (PSNR), normalized correlation (NC), structural similarity index (SSIM), number of changing pixel rate (NPCR) and unified averaged changed intensity (UACI) of up to 67.36 dB, 0.9996, 1.0000, 0.9964 and 0.4005, respectively, indicating its effectiveness for secure media applications.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
With the advancement of internet technologies, an increasing amount of media data is easily distributed, stored and shared on different social media and other plateforms such as Linkedin, Facebook, Twitter and Flickr [1]. Using digital images is a most common way to share such data over these popular platforms. Sharing of such images might bring issues of privacy leakage, copyright protection, identity theft and the data tampered by any intruder [2, 3]. Therefore, protection of such images has attracted considerable attention for different research community. To overcome such issues, data hiding scheme is widely adopted in the past few years to protect the media content by invisibly concealing secret mark (s) into host media for copy-protection purpose [4]. Watermarking and steganography are the main branch of data hiding scheme. Among the schemes, digital watermarking is widely and actively used method [5]. The research of watermarking scheme is mainly to improve performances in context to the invisibility, embedding capacity and robustness, which is difficult to balance the tradeoff among these performances [2]. According to the operations domains, the watermarking approaches include two significant domains, i.e., spatial and transform [6]. Compared with the spatial-domain scheme, the transform domain-based watermarking schemes are more robust in nature [7].
Considering the advantages and limitations of a single type of domain-based method, this paper introduces a hybrid of spatial and transform-based dual watermarking algorithm. The contributions of this work are as follows:
-
Invisible and robust hiding scheme with high hiding efficiency: The proposed scheme uses fusion of NSCT-HD-SVD [8, 9], which is improving the robustness. The proposed scheme is further improving the embedding capacity by means of pseudo magic cubes [10], so as to avoid the increase in distortion caused by large-capacity embedding.
-
Enhanced security via dual marking and encryption: Dual marks are concealed into the cover media to ensure the copy-protection and content security at the same time. Further, fusion of DNA computing, chaotic and hash function-based encryption scheme [11] provides the additional security of our scheme.
-
Enhanced robustness: The simulation results of the proposed algorithm indicate good robustness effect compared to existing schemes with high security and hiding efficiency.
The remaining chapter is ordered as follows: Sect. 2 gives the relevant works. Section 3 gives the detailed design of the proposed scheme, followed by result analysis in Sect. 4. The work summary along with future directions is presented in Sect. 5.
2 Literature survey
Some related works are briefly described in this section.
Kazemi et.al developed a watermarking algorithm utilized neural network model in the NSCT-domain [12]. Firstly, cover image is transformed using NSCT, and appropriate coefficients are chosen by means of Kurtosis. The method uses genetic algorithm to get the optimum embedding strength, and perceptron neural network is performed at extraction procedure to obtain recovered logo image. Although the method is robust, it required more time to perform training data sets. Thakur et al. [13] designed an improved algorithm, which can invisibly embed dual marks in NSCT-RDWT-SVD domain. Further, chaotic encryption is applied on marked image to ensure confidentiality of the media data.
Ali et.al [14] introduced a PSO-based scheme in NSCT- SWT-SVD domain. In this approach, NSCT decomposed host image into lower frequency and directional coefficient. However, SWT and SVD performed on NSCT coefficient of host image. The embedding factor of this scheme is optimized through PSO scheme optimized by neural networks. In the blind watermarking scheme proposed by Li and Zhang [15], scrambled mark is embedded into carrier image using NSCT and Schur. Although method is invisible and robust, it doesn’t provide better performance against few attacks such as scaling and low pass filtering. Su et.al [16] designed a blind watermarking using NSCT and HD and included a hash algorithm to randomly select the block for embedding binary mark purpose. A watermarking algorithm is introduced for offering the authenticity of digital data in [17]. In embedding part, multiple marks are embedded into cover image through NSCT, RDWT and SVD. After that, marked image is encrypted and compressed to increase the security and reduce bandwidth utilization, respectively. In Ref [18], author discussed a watermarking algorithm using transformed schemes and included wavelet-based compression to reduce the bandwidth utilization. This method increased the security by using dual watermarking and scrambled the signature mark. A robust watermarking scheme has been developed for 3D images in ref [19]. In preprocessing part, cover image is transformed into YUV channel, and sub-block division is performed on Y-component. After that, 3rd level of NSCT is utilized on designated sub-block of cover image. The scrambled mark is placed in the appropriate NSCT cover. Vaidya et.al [20], have introduced a multi-decomposition-based watermarking approach is proposed for copy-protection of color media. Initially, DWT adopted on ‘Y’ part of host media. After that ‘LL’ band is transformed using CT, Schur and SVD. Thereafter, encrypted mark image is concealed in the transformed coefficient of host. To provide the solution of false positive problem, authors have introduced a multi-scale watermarking scheme through IWT and SVD [21]. Objective Evaluation Function (OEF) is applied to provide solution of false positive problem. An optimal factor is obtained by using optimal mapping scheme to balance the tradeoff among watermarking performances. The various NSCT-based watermarking schemes and their limitations are depicted in Table 1.
3 Proposed method
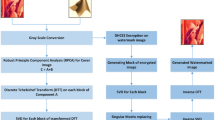
This section provides the detailed description of the proposed algorithm (See Fig. 1). It is divided into different procedures: (a) the mark embedding, (b) marked encryption and (c) recovery. Initially, sub-sampling process is employed to obtain sub-component of cover image. Further, the multiple decomposition (NSCT-HD-SVD) is performed on maximum entropy component of cover image. Similarly, mark image is also transformed. After that, mark image is concealed into singular vector of cover image with the help of appropriate embedding factor to obtain marked image. However, text mark and hash value of cover image are also embedded into the marked image using pseudo magic cubes to obtain final marked image. The fusion of DNA computing, chaotic and hash function-based encryption scheme on marked data provides the additional security of our scheme. Finally, the inverse steps of embedding process are performed to obtain extracted mark image. The process of lossless encryption procedure of the marked data can be seen in Fig. 2. The detail description of embedding procedure, encryption scheme and recovery procedure are presented below in Algorithm 1–3, respectively. Notation and its description used in Algorithm 1 to 3 are depicted below in Table 2.
Flowchart diagram of encryption scheme [11]



4 Experimental results
The experimental analysis of our implemented algorithm has been simulated on MATLAB 2019a. In the experiment, sixteen gray-images (See Fig. 3) of dimensions 512 \({\text{~}} \times 512\) \(\times 8\) are used for testing [22]. The size of mark image is chosen as 256 \({\text{~}} \times 256 \times 8\) for embedding purpose. The text document of the size 564 characters (500 characters of text information and hash value of cover image of 64 characters) is also chosen for embedding purpose into marked image. In our experiments, PSNR and SSIM [23] between original cover and marked image are used to measure invisibility, NC [23] between original mark and recovered mark are adopted to determine robustness. Further, NPCR and UACI [23] are used to examine the performance of lossless encryption scheme. The performance analysis of our scheme is evaluated at a different gain are depicted in Table 3. It is noticed that the best PSNR and SSIM scores are obtained as 85.41 dB and 1.000, respectively, at gain = 0.015. The best NC score = 0.9996 at gain = 0.1. In order to improve the mark capacity, magic cube-based algorithm is used to embed text data up to 80,000 characters. From Fig. 4, it indicates that the distortion increases at high payload. The NPCR and UACI scores as obtained for encryption scheme are depicted in Fig. 5. In this figure, it is observed that best NPCR and UACI score is found as 0.9964 and 0.4005, respectively.
Table 4 provides the comparative investigation in terms of invisibility of the proposed model with the existing techniques [15, 16, 18, 19]. As shown in Table 4, PSNR and SSIM score of our algorithm is superior than existing related techniques. The embedding capacity of our method is (256 \({\text{~}} \times 256{\text{*}}8\))/ (512 \({\text{~}} \times 512 \times 8\)) = 0.25. We also embed text document of the size 564 characters in marked image to improve mark capacity of our algorithm. Table 5 provides the comparative investigation in terms of capacity of the proposed model with the existing techniques [13, 16,17,18, 23]. As the result indicated, the capacity of our algorithm is superior than existing related techniques [16, 17] except [13] and [18]. However, the capacity of our algorithm is similar to related techniques [23].
The histogram of plain, encrypted and decrypted image of our proposed scheme is illustrated in Fig. 6. According to Fig. 6, we can notice that encrypted image is similar to noise like image, and it could not be extract original information about plain image. Histogram of encrypted image indicates that it shows in uniform manner which makes very difficult to extract information.
Figure 7 shows the invisibility and robustness performance of our proposed algorithm for fifteen images. It can be seen that when gain = 0.05, the best PSNR, SSIM and NC scores are obtained as 67.36 dB, 1.000 and 0.9996, respectively. The performance our proposed scheme is evaluated in terms of robustness under various image processing attacks are shown in Fig. 8. According to Fig. 8, robustness is evaluated against JPEG attacks with different quality factor. If quality factor of JPEG is improved, then NC score of proposed scheme is also increased. The NC value is obtained more than 0.9875 against average filtering. In median filtering, NC value is obtained more than 0.9948. In Fig. 8, NC score is evaluated as 0.9832 against Histogram Equalization. In salt and pepper noise, NC score is obtained more than 0.9362. In Speckle and Gaussian noise, NCs value obtained more than 0.9360 and 0.9368, respectively. In rotation attack, NC value obtained as 0.9962. The NC score obtained as 0.9969 against scaling attack. In sharpening attack, NC value is evaluated as 0.9968. According to this table, we have observed that NC value of our scheme is more than 0.9360 against mention attacks.
Table 6 provides the comparative robustness investigation of the proposed model with the existing techniques [23,24,25] under well-known attacks. From this table, we have noticed that robustness of the model is higher than that of other traditional algorithms except salt & pepper and speckle noise. It indicates a considerable improvement in robustness of up to 96.36% against histogram equalization attack over other schemes.
5 Conclusions
This paper has described an interesting information hiding algorithm that utilizes NSCT-HD-SVD for concealing of mark data. Further, the algorithm uses magic cube algorithm for higher payload and lossless encryption for additional authentication. The results show that compared with the traditional schemes, robustness of our algorithm is significantly improved. The proposed algorithm not only provides the additional level of information security, but also offers the good hiding efficiency. Further, performance of this scheme can be further improved by selecting optimal embedding factor using metaheuristic approaches.
References
Mahato, S., Yadav, D., Khan, D.: A novel information hiding scheme based on social networking site viewers’ public comments. J. Inf. Secur. Appl. 47, 275–283 (2019)
Singh, A.K., Kumar, B., Singh, G., Mohan, A.: Digital Image Watermarking: Concepts and Applications. In: Singh, A., Kumar, B., Singh, G., Mohan, A. (eds) Medical Image Watermarking. Multimedia Systems and Applications. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-57699-2_1
Xia, Z., Wang, X., Zhang, L., Qin, Z., Sun, X., Ren, K.: A Privacy-preserving and copy-deterrence content-based image retrieval scheme in cloud computing. IEEE Trans. Inf. Forensics Secur. 11(11), 2594–2608 (2016)
Singh, A.K.: Data Hiding: Current Trends, Innovation and Potential Challenges. ACM Trans. Multimed. Comput. Commun. Appl. 16(3s), 1–16 (2021)
Singh, O.P., Singh, A. K., Srivastava, G., Kumar, N.: Image watermarking using soft computing techniques: A comprehensive survey. Multimed. Tools Appl., pp. 1–32, 2020.
Mohanty, S., Sengupta, A., Guturu, P., Kougianos, E.: Everything you want to know about watermarking: from paper marks to hardware protection: from paper marks to hardware protection. IEEE Consum. Electr. Mag. 6(3), 83–91 (2017)
Yuan, Z., Su, Q., Liu, D., Zhang, X.: A blind image watermarking scheme combining spatial domain and frequency domain. Vis. Comput. 37, 1867–1881 (2021)
Nam, S., Mun, S., Ahn, W., Kim, D., In, Yu., Kim, W., Lee, H.: NSCT-based robust and perceptual watermarking for DIBR 3D images. IEEE Access 8, 93760–93781 (2020)
Liu, J., Huang, J., Luo, Y., Cao, L., Yang, S., Wei, D., Zhou, R.: An optimized image watermarking method based on HD and SVD in DWT domain. IEEE Access 7, 80849–80860 (2019)
Ranjani, J., Zaid, F.: Pseudo magic cubes: a multidimensional data hiding scheme exploiting modification directions for large payloads. Comput. Electr. Eng. 89, 1–10 (2021)
Zefreh, E.: An image encryption scheme based on a hybrid model of DNA computing, chaotic systems and hash functions. Multimed. Tools Appl. 79(33–34), 24993–25022 (2020)
M. Kazemi, M. Pourmina and A. Mazinan, "Novel Neural Network Based CT-NSCT Watermarking Framework Based upon Kurtosis Coefficients", Sensing and Imaging, vol. 21, no. 1, 2019.
Thakur, S., Singh, A., Ghrera, S., Mohan, A.: Chaotic based secure watermarking approach for medical images. Multimed. Tools Appl. 79(7–8), 4263–4276 (2018)
A. Amiri and S. Mirzakuchaki, "A digital watermarking method based on NSCT transform and hybrid evolutionary algorithms with neural networks", SN Applied Sciences, vol. 2, no. 10, 2020.
Li, J., Zhang, C.: Blind watermarking scheme based on Schur decomposition and non-subsampled contourlet transform. Multimed. Tools Appl. 79(39–40), 30007–30021 (2020)
Su, Q., Wang, G., Lv, G., Zhang, X., Deng, G., Chen, B.: A novel blind color image watermarking based on Contourlet transform and Hessenberg decomposition. Multimed. Tools Appl. 76(6), 8781–8801 (2016)
Singh, A.K., Thakur, S., Jolfaei, A., Srivastava, G., Elhoseny, M., Mohan, A.: Joint encryption and compression-based watermarking technique for security of digital documents. ACM Trans. Internet Technol. 21(1), 1–20 (2021)
Kumar, C., Singh, A.K., Kumar, P., Singh, R., Singh, S.: SPIHT - based multiple image watermarking in NSCT domain. Concurrency and Computation: Practice and Experience 32(1) (2018)
Nam, S., Mun, S., Kim, D., Ahn, W., Yu, I., Kim, W., Lee, H., et al.: NSCT-based robust and perceptual watermarking for DIBR 3D images. IEEE Access 8, 93760–93781 (2020)
P. S. and C. P. V. S. S. R., "A robust semi-blind watermarking for color images based on multiple decompositions", Multimedia Tools and Applications, vol. 76, no. 24, pp. 25623–25656, 2017.
Luo, Y., Li, L., Liu, J., Tang, S., Zhang, S., Qiu, S., Cao, Y.: A multi-scale image watermarking based on integer wavelet transform and singular value decomposition. Expert Systems with Applications 168, 114272 (2021)
Anand, A., Singh, A. K.: An improved DWT-SVD domain watermarking for medical information security. Comput. Commun. 152, 72–80 (2020)
Anand, A., Singh, A.K., Lv, Z., Bhatnagar, G.: Compression-then-encryption-based secure watermarking technique for smart healthcare system. IEEE Multimed. 27(4), 133–143 (2020)
Thakur, S., Singh, A. K., Kumar, B., Ghrera, S.P.: Improved DWTSVD-Based Medical Image Watermarking Through Hamming Code and Chaotic Encryption. Lecture Notes in Electrical Engineering, pp. 897–905 (2019)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Singh, O.P., Singh, A.K. A robust information hiding algorithm based on lossless encryption and NSCT-HD-SVD. Machine Vision and Applications 32, 101 (2021). https://doi.org/10.1007/s00138-021-01227-0
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s00138-021-01227-0