Abstract
Human trafficking represents the second most profitable criminal activity in the world. Here, based on the snowball sampling method, we obtained a novel dataset of a human trafficking network on the southern border of Mexico. This dataset was used to construct an unweighted and undirected graph that represents the interactions of the trafficking network. Our analysis reveals a moderate level of centralization at 44.32% and a medium density of 0.401, indicative of a structural balance that facilitates the coordination of criminal activities without a single actor’s dominance. Addressing the challenge posed by the network’s minimal cohesiveness, which hampers the sharing of resources among members, we assess four dismantling strategies: random removal, targeting hubs and brokers, a human capital-focused approach, and Generalized Network Dismantling (GND). Our findings underscore the efficacy of targeting moderately connected actors, a strategy that disrupts the network’s resilience and operational capacity by severing important but inconspicuous connections, thereby destabilizing the network’s efficiency subtly and avoiding immediate alert to the dismantling activities. This work is a significant contribution to the field of criminal network modeling and analysis.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Human trafficking is a ruthless crime that seeks to exploit people for different purposes. The International Labor Organization estimates that there are 40.3 million people who are victims of this crime, which represents the second most profitable criminal activity in the world after weapon trafficking (Forced labor, modern slavery, and human trafficking 2014). Human trafficking has persisted over the years because there is a market for exploiting individuals for affordable prices. As long as the social demand continues to exist, it will continue to be addressed, perpetuating this heinous crime (Casillas 2011).
Mexico has one of the highest rates of human trafficking in the world (United States Department of State 2021). This can be attributed to institutional instability, discrimination, corruption, and other causes. There have been very few efforts taken to combat human trafficking in the country. The violence unleashed in Mexico in the twenty-first century to combat drug trafficking has demonstrated that tear-down techniques based on the elimination of random individuals were ineffective (Dell 2015). Human trafficking, as any other form of criminal activity, is a complex problem that requires a multidisciplinary approach for its effective prevention and combat. The numbers of human trafficking victims are notoriously inaccurate, and estimates may range from a high to 10 times that of the minimum (Aronowitz 2009).
Social networks and the respective collection of data within criminology have received considerable interest in the scientific community to abstract illicit networks (Bindu et al. 2017; Granados and Nicolás-Carlock 2021). The study ‘Disrupting resilient criminal networks through data analysis: The case of Sicilian Mafia’ offers valuable insights into strategies employed in different contexts, specifically focusing on the Sicilian Mafia. It highlights the challenges and methodologies pertinent to disrupting highly resilient criminal networks using data analysis (Cavallaro et al. 2020). The actors in a criminal network, which are the nodes in a network, are most often people but occasionally organizations. Criminals are connected as family, friends, or rivalries; these connections are represented by the edges in a network (Faust and Tita 2019). Studying how elements of a network are connected can help uncover salient patterns in the criminal network. The connections between data elements are often assumed to be observed, at least partially. However, in many real-world applications, the configuration interpretation is not given a priori and needs to be inferred from the available data.
Strategies for the disintegration of criminal networks have been largely proposed in the literature, for example, by deleting nodes randomly, Keegan et al. (2010), or simply removing nodes with essential connections, Duijn et al. (2014). More complex techniques like social network analysis (SNA) can help find weak points in the criminal network, supporting a more thorough investigation and more efficient network application decision-making (Duijn and Klerks 2014). Different stages of women trafficking and the structure of criminal networks in the Netherlands are studied in Diviak et al. (2021). The authors found that actors were likely to form ties with each other in the stages of recruitment, accommodation, and exploitation, but not in the stages of transport and finance.
Another example is in terrorist networks. It was found that removing nodes with a lot of connections and subsequently removing nodes with privileged roles were equally beneficial in diminishing the network (Xu and Chen 2003). Contrastingly, with the criminal organization ‘Cosa Nostra’, network analysis was employed to devise the most effective assault strategies. It was determined that actors affiliated with this mafia syndicate were crucial in the network’s operation, thereby focusing on these individuals was key to disrupting the network (Musciotto and Miccichè 2022). The criminal intelligence network discovered that by removing just 2% of the nodes, the network could be dismantled (da Cunha and Gonçalves 2018). Crime disruption strategies strongly depend on both network topology and network resilience (Duijn et al. 2014). In Dimas et al. (2022), the authors provide a systematic literature review related to the anti-human trafficking domain; they identify current trends in methodologies, theoretical approaches, data sources, trafficking contexts, target regions, and victim–survivor demographics.
In this paper, we are focused on Chiapas, which is one of Mexico’s poorest states. Located in the southeast of the country, it has a border with Guatemala that stretches for 658 km (Secretaría de Seguridad y Protección Ciudadana del Estado de Chiapas 2020). There are three very common ways to attract a person for human trafficking in Chiapas. One example is foreigners from Central and South America, as well as a few Asians, Caribbeans, and Africans, who seek to go to Mexico to enter the USA. They arrive in Chiapas and search for jobs in the area while they figure out how to keep moving forward. Very commonly, they turn to illicit nightlife companies because of their immigration status, where they end up being exploited for labor. Another case occurs when Central Americans are promised a decent job in Chiapas so that they can get out of poverty. They ask for little money to help them cross the border and promise them a stable life, yet these people are being recruited to exploit them. The last case occurs when someone in a vulnerable situation is approached by a person in a park, a nightclub, or a shopping center offering them work or a love relationship and ends up being exploited (Casillas 2011). A discussion of this diversity of scenarios has been addressed by Campana and Varese (2016), Campana (2020), the authors offer empirical evidence of the key building blocks of smuggling, and how smuggling can turn into trafficking.
To abstract the social interaction between the criminals in a human trafficking network in Chiapas, we developed a social network analysis. By collecting real data with the snowball sampling methodology from a border state in the southern part of Mexico, with the human traffic network, we performed a network analysis to further characterize and then understand the criminal organization in Tapachula, Chiapas. Consequently, we evaluate the potential dismantling strategies and their respective limitations.
2 Methodology
In this section, we present the fundamental concepts to provide the necessary tools to abstract real-world situations into a mathematical framework allowing the application of various algorithms and analytical techniques to understand and manipulate networks effectively.
2.1 Graphs
Graph theory studies the properties of graphs, which are mathematical structures modeling pairwise relationships between objects. A graph G is defined as a pair \(\left( V(G), E(G) \right)\), with V(G) being a non-empty set of vertices or nodes, and E(G) being a set of unordered pairs of vertices, known as edges. These edges may be directed, indicating a one-way relationship, or undirected, implying a bidirectional relationship. This distinction is crucial in representing various phenomena, such as the flow of information, money, or goods (West 1996; De Nooy et al. 2018).
To represent the structure of graphs, the adjacency matrix, denoted by A, is widely used. This square matrix captures the connections between vertices: \(A_{i,j} = 1\) if there is an edge from vertex i to vertex j, and \(A_{i,j} = 0\) otherwise. In a simple graph, this matrix is symmetric (\(A_{i,j} = A_{j,i}\)) and has zeros along its diagonal (\(A_{i,j} = 0\) for \(i = j\)), reflecting the absence of loops. The adjacency matrix is crucial for executing graph computations and compactly storing the graph for algorithmic processing (West 1996).
The concept of an eigenvector \(\vec {x}\) of a matrix A is fundamental. It is defined as a nonzero vector that, when multiplied by A, produces a scalar multiple of itself, \(A\vec {x} = \lambda \vec {x}\), with \(\lambda\) being the corresponding eigenvalue. This concept is pivotal in analyzing graphs’ properties, including network connectivity, stability, and centrality measures, by revealing inherent structural characteristics (Strang 2016).
The Laplacian matrix, denoted by L, is another critical construct, formulated as \(L=D-A\). Here, D is the degree matrix, a diagonal matrix listing the degree of each vertex, and A is the adjacency matrix. The Laplacian matrix is symmetric and positive semidefinite, ensuring that for any vector \(\vec {z}\) in \({R}^n\), the quadratic form \(\vec {z}^\textsf{T}L\vec {z}\) is non-negative. The eigenvalues of the Laplacian are always non-negative, and its eigenvectors are orthogonal to each other, reflecting the structural properties of the graph. These characteristics make the Laplacian matrix an invaluable tool in analyzing a graph’s structure, connectivity, and the network’s potential resilience and response to changes.
2.2 Graph metrics
In network analysis, key graph metrics, such as density, diameter, and mean degree, serve as vital indicators of structural characteristics. The density \(\rho\) of a graph is the ratio of the number of edges m to the maximum possible number of edges, yielding \(\rho = \frac{2m}{n(n-1)}\), which measures the network’s overall connectivity. The diameter of a graph represents the maximum geodesic distance between any two vertices, signifying the network’s maximum breadth. The mean degree c, calculated as \(c = \frac{2\,m}{n}\), indicates the average connectivity and is integral to understanding the network’s redundancy and robustness against node failures. Collectively, these metrics offer insights into the network’s complexity, cohesiveness, and resilience, critical for devising effective strategies for network manipulation and intervention (Newman 2010).
2.2.1 Centrality measures
Centrality is a principal concept in network analysis, signifying the importance of vertices within the graph structure. Degree centrality for a vertex v is denoted as \(C_D(v) = k_v\), where \(k_v\) is the number of edges incident to v. This measure serves as an indicator of the node’s immediate influence within the network. In directed networks, degree centrality is bifurcated into in-degree \(k_v^{in}\) and out-degree \(k_v^{out}\) centrality. Eigenvector centrality \(C_E(v)\) assigns relative scores to all nodes in the network based on the principle that connections to high-scoring nodes contribute more to the score of the node in question. Mathematically, it is given by the equation \(x_v = \frac{1}{\lambda } \sum _{t \in M(v)} x_t\), where \(x_v\) is the eigenvector centrality of vertex v, M(v) is the set of neighbors of v, and \(\lambda\) is a constant. Betweenness centrality \(C_B(v)\) captures a node’s intermediacy in connecting pairs of nodes, quantified as \(C_B(v) = \sum _{s\ne v \ne t} \frac{\sigma _{st}(v)}{\sigma _{st}}\), where \(\sigma _{st}\) is the total number of shortest paths from node s to node t, and \(\sigma _{st}(v)\) is the number of those paths that pass through v. Closeness centrality \(C_C(v)\) inversely relates to the average length of the shortest paths to reach all other nodes from a given node v, represented as \(C_C(v) = \frac{1}{\sum _{t \ne v} d(v, t)}\), where d(v, t) is the shortest-path distance between v and t. Collectively, these measures elucidate various facets of nodal prominence within network dynamics (Newman 2010).
2.2.2 Network components and connectivity
A network’s structure can be dissected into distinct groups, known as components, which are segments where each vertex is reachable from any other within the same segment via at least one path. These are self-contained in the sense that no additional connections exist to vertices outside the group while maintaining this reachability. The concept of a connected network is one where a single, all-encompassing component exists, encompassing all vertices. Conversely, in networks composed of multiple disjointed segments, each segment stands as an independent component. When represented mathematically, the connectivity of a network with multiple disjoint segments is depicted in an adjacency matrix partitioned into isolated blocks along the matrix’s diagonal, indicating isolated interaction within components with zero connectivity between them. This block diagonal structure is emblematic of the network’s segmented connectivity, Newman (2010).
2.2.3 Clustering and community detection
In the realm of network analysis, the concept of partitioning a network is crucial and commonly addressed through the clustering coefficient. This coefficient, symbolized as \(C_i\), quantifies how close a node’s neighbors are to form a complete subgraph, essentially a clique. This measure is particularly insightful for uncovering tight-knit groups or communities within a network. Mathematically, the clustering coefficient for a node i is defined as \(C_i = \frac{2t_i}{k_i(k_i - 1)}\), where \(t_i\) represents the number of triangles involving the node i, and \(k_i\) is the degree of the node, indicating the total number of links connected to i. A \(C_i\) value of 0 signifies no connectivity among a node’s neighbors, whereas a value of 1 denotes a complete interconnection. The average clustering coefficient across the network provides an aggregate measure of the propensity for cluster formation. Community detection techniques leverage this and other metrics to delineate the network’s subdivision into communities, aiding in the understanding of the network structure and function, Saramäki et al. (2007).
2.3 Roles in networks
Within the framework of network theory, certain nodes emerge as highly influential due to their structural positions. Hubs are recognized as nodes with an extensive number of connections, positioning them as influential components in the network topology. These hubs serve as critical points for the dissemination and aggregation of information or resources throughout the network. On the other hand, brokers play a pivotal role as intermediaries within the network’s communication pathways. A broker’s influence is measured by their level of betweenness centrality, which quantifies the number of times a node acts as a bridge along the shortest path between two other nodes. Brokers facilitate interactions between otherwise disconnected nodes and can control the flow of information, thereby holding strategic positions within the network (Newman 2010). Together, hubs and brokers are vital for maintaining network cohesion and efficiency, influencing the dynamics and resilience of the network structure.
2.4 Fragmentation and network resilience
A more precise measure of network fragmentation calculates the number of disconnected node pairs. Given the adjacency matrix B, where \(b_{A,i,j}\) represents the connection status between nodes i and j, the fragmentation F can be defined as \(F = 1 - \frac{2 \sum _{i} \sum _{j < i} b_{A,i,j}}{n(n - 1)}\). Here, \(F = 1\) if no node is connected to another, and \(F = 0\) if all nodes are interconnected, indicating a complete graph (Borgatti 2002).
3 Data
The snowball sampling method addresses the challenges inherent in studying covert networks, such as those involved in illicit activities. This approach, first conceptualized by Leo A. Goodman in 1961, is a technique to uncover network members through successive recruitment. Starting with a random sample, each participant is asked to identify further individuals within the network; thus, the sample grows progressively larger like a rolling snowball. This methodology has been employed to maximize the identification of individuals within a network, particularly useful in scenarios where members are not openly known (Goodman 1961; Campana and Varese 2022; Robins 2015).
We employed this method to study the trafficking network in Tapachula, using basic interviews to identify and understand the network members (Goodman 1961). Interviews were conducted online with various stakeholders, including victims, traffickers, and ex-convicts, within the Soconusco region. We ensured that ethical considerations were at the forefront of our methodology, especially given the sensitive nature of the information and the potential ongoing involvement of some individuals in trafficking networks. The data gathering phase occurred during June, July, and August of 2020. To preserve the anonymity and safety of all involved, including authors, victims, interviewees, and the interviewer, we used coded identifiers for all participants. The primary source of contact and information came from an individual well-versed in conducting and publishing interviews within this domain. This individual’s insights were instrumental in connecting with people impacted by trafficking, either as victims or participants.
Table 1 delineates the various roles identified within human trafficking network in Tapachula, based on the findings from our interviews and corroborated by the literature (Casillas 2011).
Our initial contact with members of the criminal network was facilitated through collaboration with non-governmental organizations (NGOs) focused on victim assistance and reintegration, as well as working with reformed ex-convicts to gain deeper insights into the trafficking industry. These NGOs, operating across different states in Mexico, provided invaluable contacts and narratives, contributing to a richer understanding of the traffickers’ behaviors and relationships.
During our investigation, we managed to conduct interviews with five survivors of human trafficking and three ex-convicts. Their testimonies shed light on the organizational structure and operations of the trafficking network but offered limited insight into personal connections among the criminals. Subsequent interviews with individuals still actively involved in trafficking revealed the roles and dynamics within the network, although some chose to remain vague about their exact involvement.
In reconstructing the network, we focused on gathering detailed information about the participants, their roles, and the activities within the network. The compilation of questions was designed to elicit comprehensive responses, contributing to the accuracy of the network’s portrayal. This methodical approach led to interviews with a total of five survivors, six ex-convicts, and eleven individuals still active in trafficking at the time of the study. The validation of relationships was meticulously confirmed by cross-referencing between interviewees, ensuring only substantiated connections were included. Individuals solely victimized and not involved in the network’s operations were excluded from the data.
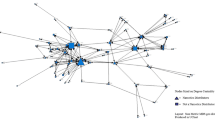
The resulting network consists of 34 nodes, representing the actors, and 225 undirected edges, symbolizing the reciprocal relationships, see Figure 1. While acknowledging the simplicity and constraints of using undirected graphs, the richness and asymmetry of directed relationships in the future models could provide more nuanced insights into the hierarchical and influence dynamics within the network. The limitations inherent in criminal network analysis, especially concerning incomplete data, are well-documented and acknowledged in our study, informing our interpretation and analysis of the network (Granados and Nicolás-Carlock 2021; Ficara et al. 2021).
We further delve into the intricacies of the network by examining the value chain of criminal activities. This approach, aligned with the work of Ficara et al. (2022), views the network as a series of interconnected activities enhancing the value of information, goods, and human capital at each stage. The Tapachula trafficking network operates as a sequential value chain, beginning with recruitment and culminating in exploitation. Each participant, from recruiters to financial managers, contributes specific resources and skills, emphasizing the importance of understanding each link in the chain for effective intervention strategies. This comprehensive view of the value chain aids in identifying key intervention points and understanding the full scope of the human trafficking operation in Tapachula, Chiapas.
Social interactions of the human trafficking network of Chiapas, Mexico. The actors of the network (gray circles) are labeled as follows: Caretaker (\(C_i\)), Company (\(Co_i\)), Body Guard (\(B_i\)), Estafeta (\(Es_i\)), Exploiter (\(Ex_i\)), Public Servant (\(Ps_i\)), Guide (\(G_i\)), Participant (\(P_i\)), Raitero (\(Ra_i\)), Recruiter (\(Re_i\)), and Recruiter/Victim (\(Rv_i\)). The subindex i indicates the number of the actor in case exist more than one in that position. Blue lines represent the connections with the respective
4 Network dismantling strategies
Network dismantling is a crucial process based on the spectral properties of the Laplacian matrix, which reflects the connectivity of the graph it represents, providing a crucial analysis for understanding network resilience and developing systematic dismantling strategies (Fig. 1). In the study of networks, especially those of illicit or covert operations, dismantling strategies are crucial for understanding how to disrupt the network effectively. In our analysis, we have considered the following methods:
-
Random Node Removal: This baseline strategy involves the arbitrary selection and elimination of nodes from the network. It serves as a control scenario to gauge the effectiveness of more strategic interventions.
-
Removal of Hubs and Brokers: This strategy targets the most connected nodes (hubs) and nodes that act as critical connectors or bridges between different parts of the network (brokers). By removing these nodes, the network’s efficiency in information transfer and resource distribution is significantly reduced.
-
Removal Based on Human Capital: In networks involving individuals, such as criminal networks, nodes are evaluated based on their ‘human capital,’ which can include factors such as influence, knowledge, or other attributes that make the individual node critical to the network’s operation. Removing nodes with high human capital can dismantle the network’s operational capabilities (Ficara et al. 2023).
-
GND Algorithm Removal: The Generalized Network Dismantling (GND) algorithm is a computational approach that identifies the minimum set of nodes, whose removal leads to the fragmentation of the network into isolated subcomponents of non-extensive size. This method is systematic and often computationally intensive but can yield near-optimal dismantling sets and will be explained in detail in Sect. 4.1.
Each of these strategies has different implications for the network’s structure and function post-dismantlement. Their efficacy can vary based on the network’s topology, the resilience of the remaining nodes, and the network’s redundancy in connections.
The cost of removing an actor is set to the degree of the node that represents all the strategies since this reflects the actor’s value in the network in terms of its connections. Because of the intricacy of the measurement, each node does not have a monetary cost assigned to it, but the aim of indicating which node is more costly is served by establishing that the more connections there are, the greater the isolation cost.
4.1 Generalized network dismantling method
The Generalized Network Dismantling (GND) method is an advanced strategy in the realm of network dismantling, categorized within spectral methods due to its reliance on the spectral properties of graphs. This method identifies a set of nodes, whose removal optimally diminishes the network’s connectivity, thereby minimizing the overall dismantling costs while adhering to certain constraints. A pivotal element in GND is the Fielder vector, which is the eigenvector corresponding to the second-smallest eigenvalue of the graph’s Laplacian matrix. In spectral graph theory, the Fielder vector is instrumental for tasks such as graph bipartitioning and envelope reduction, as it captures the essential structural information about the graph’s connectivity (Ren et al. 2019).
The GND algorithm implements a nuanced, two-step dismantling approach. Initially, it considers the adjacency matrices of the complete network G and a particular subnetwork \(G^*\). For each node i within \(G^*\), the algorithm computes \(k_i\), the node’s degree in the subnetwork, and contrasts it with \(h_i\), its degree in the entire network G. Nodes are then prioritized for removal based on a calculated ratio \(\frac{k_i}{h_i}\), identifying those with disproportionately high connectivity within the subnetwork \(G^*\). This methodical selection is integral to incorporating the Weighted Vertex Cover (WVC) algorithm, which efficiently selects a subset of nodes for removal, emphasizing those with significant connectivity within \(G^*\). The aim is to disrupt the network’s structure strategically and cost-effectively by targeting these pivotal nodes. The algorithm iterates this process, progressively dismantling \(G^*\) until its edge set \(E^*\) is depleted. Detailed steps and operational flow of this algorithm are outlined in the provided pseudocode, illustrating the systematic approach embedded in the WVC algorithm, as delineated in Algorithm 1.
Weighted Vertex Cover, for further details see Bar-Yehuda and Even (1981).
Subsequently, the GND algorithm advances to generate a weighted adjacency matrix B by combining the original adjacency matrix A with a removal cost matrix W. A diagonal matrix \(D_B\) is then constructed from B, representing the weighted degrees of the nodes. Using \(D_B\), the weighted Laplacian matrix L is formed, which is pivotal for calculating the Fiedler vector \(\vec {v_2}\). This vector informs the bisection of the network into two subnetworks M and \(\bar{M}\). It is at this juncture that the WVC technique is again employed, this time to determine the nodes for removal from the bisected subnetworks. This targeted removal of nodes significantly enhances the dismantlement strategy’s efficiency and effectiveness. The comprehensive methodology followed by the GND algorithm, along with the integrated WVC, is detailed in the pseudocode presented in Algorithm 2.
Generalized Network Dismantling (Ren et al. 2019).
5 Results
5.1 Network metrics results
The architectural nuances of the human trafficking network in Chiapas are quantitatively unraveled through our analysis presented in Fig. 2. The eigenvector centrality, showcased in Fig. 2a, identifies key players based on their influential connectivity. The actors \(Ex_1\), \(P_1\), and \(Rv_1\) stand out with prominent eigenvector centrality scores, indicating their crucial positions in the network’s structure.
The degree rank plot, Fig. 2b, provides further insight by ordering nodes according to their connectivity. The precipitous initial decline points to the presence of ‘hubs’-nodes with disproportionately high connections. These hubs are strategic targets for disrupting the network, as their removal can significantly affect the network’s structural integrity.
In Fig. 2c, the degree histogram portrays the connectivity distribution across the network, suggesting a power-law pattern typical of social networks. This pattern indicates that the network contains a few highly connected nodes, in contrast with many nodes with fewer links. Such a distribution implies that random removals are less likely to disrupt the network than targeted actions against these hubs.
These analyses converge to illustrate the network’s varied connectivity and the potential efficacy of strategic dismantlement approaches. Targeting the nodes highlighted in Fig. 2b and considering the connectivity distribution depicted in Fig. 2c could enable authorities to dismantle the network’s backbone.
The interaction profile of the 34 actors within the network, along with an average degree centrality of 13.235, suggests a network that is interlinked but not densely connected. With a moderate centralization of 44.32% and medium density of 0.401, detailed in Table 2, the network’s cohesiveness appears vulnerable to deliberate targeting. Isolating the most interconnected actors—about the top 10%—could markedly disrupt the network’s operations, drawing on insights from the network’s degree distribution and diameter.
However, this network may not exhibit strong cohesiveness, which could be a result of incomplete data or intentional obfuscation tactics by traffickers. Furthermore, the network’s diameter of three indicates that isolating these influential nodes could lead to significant disruption, although this strategy depends on the available data and the inherent complexity of criminal networks.
Table 2 synthesizes the network’s core metrics, including betweenness centrality, which at 2%, provides a relative measure of a node’s centrality and its role in mediating interactions within the network. The other metrics, such as the average clustering coefficient, density, and diameter, offer additional layers of understanding about the network’s resilience and potential pressure points for tactical interventions.
The strategic importance of the exploiters within the criminal network is further corroborated in Fig. 3. \(Ex_1\) is depicted as the linchpin in the network, bridging the operational divide between \(Ex_2\) and \(Ex_3\). The data indicate \(Ex_1\) predominantly manages sexual exploitation, while \(Ex_2\) is entrenched in labor exploitation. This bifurcation of responsibilities underscores the network’s compartmentalized yet synergistic modus operandi.
As evident from Table 3, the isolation of hubs and subsequent removal of human capital significantly alter the network’s structure. Betweenness centrality’s initial increase (from 2% to 11.44%) and subsequent decrease (to 1.7%) highlight the shifting importance of nodes. The average clustering coefficient and density variations indicate changes in local and overall connectivity, with a notable decrease in network compactness as seen by the increased diameter when hubs are removed. Fragmentation and average degree changes further confirm the network’s structural evolution, becoming more fragmented with isolated hubs and then partially reintegrating. These metrics collectively underscore the network’s sensitivity to the removal of strategic nodes and the complex interplay of network dynamics in maintaining connectivity and efficiency.
5.2 Network dismantling strategies results
5.2.1 Random removal
This approach simulates the effects of non-targeted interventions, where nodes are removed indiscriminately, potentially mimicking the loss of actors due to chance events or non-strategic actions.
In the context of our study, random removal serves as a baseline for evaluating the effectiveness of more strategic dismantling methods. Figure 4a illustrates the impact of random removal on the largest connected component size of the human trafficking network. As nodes are randomly withdrawn, we observe a gradual decline in the size of the largest connected component, indicative of the network’s resilience to such non-specific interventions.
Contrasting this with the other strategies shown in Fig. 4, the random removal curve delineates a slower reduction in connectivity, underscoring the limited efficacy of this method in dismantling a structured network. The largest connected component remains relatively large even after significant dismantling costs, suggesting that random node removal is less likely to disrupt the network’s core structure compared to targeted strategies.
5.2.2 Hubs and brokers removal
Targeted dismantlement strategies are crucial in the disruption of criminal networks, aiming to destabilize the structural and functional integrity of these illicit organizations (Everton 2012). Our study employs such a strategy by isolating key nodes that serve dual roles as hubs and brokers within a human trafficking network. The removal of these nodes, identified as the exploiter (\(Ex_1\)) and the participant (\(P_1\)), is crucial for understanding the network’s resilience and susceptibility to intentional fragmentation.
Figure 4 illustrates the effect of hub and broker removal on the network’s cohesion. Panel (a) demonstrates how the largest connected component size diminishes with the dismantling cost, highlighting the network’s potential fragility to the loss of key actors. Panel (b) shows the change in network density, which can indicate the network’s operational capacity after the removal of these nodes. Panel (c) reflects the betweenness centrality changes, providing insight into the remaining nodes’ ability to maintain the network’s flow of information and resources.
The strategic extraction of hubs and brokers can lead to an increase in network fragmentation, implying less interconnectivity among the remaining actors. This decrease in cohesion directly impacts the network’s capability to efficiently manage the circulation of individuals and resources. While the immediate goal of such removals is to dismantle the network’s core operations, the long-term consequences can be multifaceted and complex. For instance, the sudden absence of these central nodes could inadvertently strengthen latent sub-networks or prompt the emergence of new leaders, particularly if these nodes have established connections with authoritative figures.
Furthermore, the network’s rapid reorganization into more covert and elusive structures could present significant challenges for ongoing detection and intervention efforts. Law enforcement agencies must, therefore, prepare for and adapt to these potential adaptive responses, which could include increased corruption or retaliatory actions by the network, to maintain its integrity and operations.
The approach of removing hubs and brokers, as visualized in the dismantling performance metrics of Fig. 4, emphasizes their critical roles and the impact of their removal. This strategic focus on the most influential nodes within the network presents a proactive method to counter the adaptability and resilience of criminal networks, offering a path toward more effective law enforcement interventions.
5.2.3 Human capital removal
In the current analysis, we have chosen to isolate nodes with the specific roles of ‘caretaker’, ‘recruiter’, and ‘victim/recruiter’. These roles are considered to have significant human capital weight within the network, meaning that the individuals in these positions contribute essential functions that may not be easily replaceable. For instance, caretakers are integral in maintaining the day-to-day operations, recruiters are pivotal in network growth and sustainability, and victim/recruiters are critical as they embody both the roles of sustaining the network and potentially expanding it.
As illustrated in Fig. 4 dismantling, the human capital removal strategy yields fewer data points in the dismantling cost graph compared to other strategies such as random removal or targeting based on node degree (hubs). This is because the approach is selective, focusing only on a subset of actors whose removal is hypothesized to cause a disproportionate impact on the network’s structure and efficiency. The limited data points reflect this precision targeting, as opposed to the broader sweeps of other dismantling strategies.
The figure also demonstrates that despite targeting fewer nodes, the human capital removal strategy significantly affects the largest connected component size and the network’s density, which suggests a high level of efficacy. In addition, the betweenness centrality graph further supports the effectiveness of this method; the rapid decline indicates that removing these key actors drastically reduces the number of shortest paths passing through them, potentially fragmenting the network and impeding its operations. This empirical evidence underpins the premise that dismantling based on human capital can be an efficient way to disrupt and destabilize a network by carefully selecting and removing its most pivotal members.
5.2.4 GND removal
The Generalized Network Dismantling (GND) algorithm is a sophisticated method that initially targets nodes with a degree close to the network’s average before progressing to the most connected nodes. This strategic approach begins by removing nodes that, while not the most connected, play a critical role in maintaining the network’s communication channels. The first node identified by the GND algorithm for removal is participant 3 (\(P_3\)), which boasts 15 connections. This actor is integral to the network, with its removal significantly impacting the cost, which aligns closely with the original network’s average degree.
The GND algorithm’s nuanced strategy contrasts with direct hub attacks; it systematically weakens the network by targeting intermediate nodes before addressing the hubs. The second node to be removed is raitero 4 (\(Ra_4\)), a node linked to eleven other nodes, further demonstrating the algorithm’s methodical dismantling approach.
Figure 4 encapsulates the efficacy of the three dismantling strategies. In Panel (a), the GND algorithm exhibits superior performance, reducing the network’s largest connected component size at a lower cost compared to other strategies. Panel (b) reveals that only the GND strategy successfully eliminates network density. Panel (c) shows that betweenness centrality remains lower with the GND algorithm than with the others, suggesting that it effectively disrupts the network’s communication pathways.
The GND algorithm’s success is further highlighted in the reduction of network density and betweenness centrality, indicating a more fragmented network with diminished communication efficiency. This strategy’s ability to maintain low betweenness centrality post-dismantling suggests a lasting impact on the network’s operational capabilities, making it an optimal approach for network disruption.
In summary, the GND algorithm stands out as a resource-efficient dismantling strategy, achieving substantial network disruption with lower relative costs. Its effectiveness lies in its systematic approach to dismantling, which ensures that the network’s structural integrity is progressively weakened, thereby impeding its illicit operations.
Table 4 presents a quantitative comparison of the costs associated with network dismantling strategies at three different dismantling thresholds: 20%, 50%, and 80%. The strategies include Random Isolation, Isolation by Hubs, and Isolation based on GND. The costs, likely representing resources, time, or effort needed for dismantling, increase across all methods as the dismantling threshold rises. Random Isolation involves removing nodes at random, Isolation by Hubs prioritizes the removal of highly connected nodes, and Isolation based on GND likely refers to a strategy grounded in a specific network characteristic or algorithm. The table encapsulates the varying efficiencies and resource intensiveness of each method across different levels of network dismantling.
5.3 Limitations of the study
While the framework developed in this study provided significant insights into the structure and dynamics of a human trafficking network, it is important to note that the underlying data was collected in 2020. Human trafficking networks, like many criminal networks, are highly dynamic and can change rapidly in response to external pressures and internal decisions. As such, while the results presented here were accurate at the time of the study, they may not fully represent the network’s current state. This limitation is inherent in the study of covert networks, where the data can quickly become outdated, underscoring the need for ongoing surveillance and analysis. Future research should focus on developing adaptive methods that can be updated regularly to reflect the current or future dynamics of these networks.
6 Conclusions
In this study, we explored the complex issue of human trafficking through social network analysis (SNA), focusing on a network in Chiapas, Mexico. While the research centers on a small segment of a larger criminal operation, dismantling even one such unit could mean the freedom of many lives. The creation of the novel dataset depicting this network is a substantial contribution to the field, given the scarcity of empirical data.
In our study, we discovered that the most effective strategy for disrupting human trafficking networks is neither targeting the most connected nor the most peripheral individuals but focusing on those with moderate connections. Using the General Network Dismantling (GND) algorithm, we identified that this approach fragments the network efficiently with minimal cost. This tactic undermines the network’s resilience and operational capacity by removing moderately connected actors who facilitate crucial, yet not overtly visible, connections, thus subtly eroding the network’s efficiency. Our findings challenge the conventional wisdom of targeting highly connected nodes, revealing that such methods often yield only temporary disruptions due to the high replacement dynamics and significant costs associated with removing network leaders, rendering these tactics less effective in the long term.
The methodology employed successfully identified pivotal nodes, such as an exploiter crucial in connecting victims and criminals. Future research could refine this by assigning weights to roles, and aligning isolation costs more closely with reality. This study not only sheds light on the topology of human trafficking networks but also sets a foundation for further investigation into their structures.
However, dismantling networks alone is not a panacea. Sustainable solutions require reducing demand for trafficked persons, increasing awareness, creating better opportunities for vulnerable populations, and enhancing institutional functions. The costs of network dismantlement, although significant, pale in comparison with the lifelong consequences for the victims.
This research enhances our understanding of human trafficking networks and offers a strategic framework for more effective countermeasures, blending academic insight with practical applications for law enforcement and policymakers.
7 Supporting information
GitHub repository: https://github.com/sofiadelamora/HumanTMexicoNetwork
Data availability
Data are provided within the manuscript. https://github.com/sofiadelamora/HumanTMexicoNetwork
References
Aronowitz A (2009) Human trafficking, human misery: the global trade in human beings. Praeger, Westport. Conn. https://doi.org/10.1007/s12117-012-9168-y
Bar-Yehuda R, Even S (1981) A linear-time approximation algorithm for the weighted vertex cover problem. J Algorithms 2(2):198–203. https://doi.org/10.1016/0196-6774(81)90020-1
Bindu PV, Thilagam PS, Ahuja D (2017) Discovering suspicious behavior in multilayer social networks. Comput Hum Behav 73:568–582. https://doi.org/10.1016/j.chb.2017.04.001
Borgatti S (2002) The key player problem. SSRN Electron J. https://doi.org/10.2139/ssrn.1149843
Campana P (2020) Human smuggling: structure and mechanisms. Crime Justice 49(1):471–519. https://doi.org/10.1086/708663
Campana P, Varese F (2016) Exploitation in human trafficking and smuggling. Eur J Crime Policy Res 22(1):89–105. https://doi.org/10.1007/s10610-015-9286-6
Campana P, Varese F (2022) Studying organized crime networks: data sources, boundaries and the limits of structural measures. Soc Netw 69:149–159. https://doi.org/10.1016/j.socnet.2020.03.002
Casillas R (2011) Redes visibles e invisibles en el tráfico y la trata de personas en chiapas. Migración y Seguridad: nuevo desafío en México 5:53–72. https://hdl.handle.net/20.500.11986/COLMEX/10006314
Cavallaro L, Ficara A, De Meo P, Fiumara G, Catanese S, Bagdasar O (2020) Disrupting resilient criminal networks through data analysis: the case of Sicilian mafia. PLoS ONE 15(7):e0236476. https://doi.org/10.1371/journal.pone.0236476
da Cunha BR, Gonçalves S (2018) Topology, robustness, and structural controllability of the Brazilian federal police criminal intelligence network. Appl Netw Sci 3(1):1–20. https://doi.org/10.1007/s41109-018-0092-1
De Nooy W, Mrvar A, Batagelj V (2018) Exploratory social network analysis with Pajek: revised and expanded edition for updated software, vol 46. Cambridge University Press
Dell M (2015) Trafficking networks and the Mexican drug war. Am Econ Rev 105(6):1738–1779. https://doi.org/10.1257/aer.20121637
Dimas GL, Konrad RA, Lee Maass K, Trapp AC (2022) Operations research and analytics to combat human trafficking: a systematic review of academic literature. PLoS ONE 17(8):1–24. https://doi.org/10.1371/journal.pone.0273708
Diviak T, Dijkstra JK, van der Wijk F, Oosting I, Wolters G (2021) Women trafficking networks: structure and stages of women trafficking in five Dutch small-scale networks. Eur J Criminol 20:1–24. https://doi.org/10.1177/14773708211053135
Duijn PAC, Klerks PPHM (2014) Social network analysis applied to criminal networks: recent developments in Dutch law enforcement. In: Masys AJ (ed) Networks and network analysis for defence and security. Springer, Cham, pp 121–159. https://doi.org/10.1007/978-3-319-04147-6_6
Duijn PAC, Kashirin V, Sloot PMA (2014) The relative ineffectiveness of criminal network disruption. Sci Rep 4(1):1–15. https://doi.org/10.1038/srep04238
Everton SF (2012) Disrupting dark networks. Cambridge University Press, Cambridge. https://doi.org/10.1017/cbo9781139136877
Faust K, Tita GE (2019) Social networks and crime: Pitfalls and promises for advancing the field. Ann Rev Criminol 2:99–122. https://doi.org/10.1146/annurev-criminol-011518-024701
Ficara A, Cavallaro L, Curreri F, Fiumara G, De Meo P, Bagdasar O, Song W, Liotta A (2021) Criminal networks analysis in missing data scenarios through graph distances. PLoS ONE 16(8):e0255067. https://doi.org/10.1371/journal.pone.0255067
Ficara A, Curreri F, Fiumara G, De Meo P, Liotta A (2022) Covert network construction, disruption, and resilience: a survey. Mathematics. https://doi.org/10.3390/math10162929
Ficara A, Curreri F, Fiumara G, Meo PD (2023) Human and social capital strategies for mafia network disruption. IEEE Trans Inf Forensics Secur 18:1926–1936. https://doi.org/10.1109/TIFS.2023.3256706
Forced labour, modern slavery and human trafficking. Accessed (2014). https://www.ilo.org/global/topics/forced-labour/lang--en/index.htm
Goodman LA (1961) Snowball sampling. Ann Math Stat 32(1):148–170
Granados OM, Nicolás-Carlock JR (2021) Corruption networks: concepts and applications. Springer, Cham. https://doi.org/10.1007/978-3-030-81484-7
Keegan B, Ahmed MA, Williams D, Srivastava J, Contractor N (2010) Dark gold: statistical properties of clandestine networks in massively multiplayer online games. In: Proceedings of the 2nd IEEE international conference on social computing, PASSAT 2010. pp 201–208. https://doi.org/10.1109/SocialCom.2010.36
Musciotto F, Miccichè S (2022) Effective strategies for targeted attacks to the network of Cosa nostra affiliates. EPJ Data Sci 11(1):1–14. https://doi.org/10.1140/epjds/s13688-022-00323-z
Newman M (2010) Networks: an introduction. OUP, Oxford
Ren XL, Gleinig N, Helbing D, Antulov-Fantulin N (2019) Generalized network dismantling. Proc Natl Acad Sci USA 116(14):6554–6559. https://doi.org/10.1073/pnas.1806108116
Robins G (2015) Doing social network research: network-based research design for social scientists. Sage, Thousand Oaks. https://doi.org/10.4135/9781473916753
Saramäki J, Kivelä M, Onnela J-P, Kaski K, Kertész J (2007) Generalizations of the clustering coefficient to weighted complex networks. Phys Rev E 75(2):027105
Secretaría de Seguridad y Protección Ciudadana del Estado de Chiapas, Policía Estatal Fronteriza (2020). https://www.sspc.chiapas.gob.mx/policia_estatal_fronteriza
Strang G (2016) Linear algebra and its applications, 5th edn. Cengage Learning
United States Department of State, (2021) trafficking in persons report: Mexico. Accessed (2021). https://www.state.gov/reports/2021-trafficking-in-persons-report/mexico/
West DB (1996) Introduction to graph theory, vol 2. Prentice Hall, Upper Saddle River, NJ
Xu J, Chen H (2003) Untangling criminal networks: a case study. Lecture notes in computer science (including subseries Lecture notes in artificial intelligence and lecture notes in bioinformatics), vol 2665, pp 232–248. https://doi.org/10.1007/3-540-44853-5_18
Acknowledgements
MNL acknowledges the financial support from the Asociación Mexicana de Cultura, A.C.
Author information
Authors and Affiliations
Contributions
MNL and EAHV designed research. SMT obtained data. SMT, MNL, and EAHV performed research and analyzed data. SMT, MNL, and EAHV wrote the paper.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
De la Mora Tostado, S., Hernández-Vargas, E.A. & Núñez-López, M. Modeling human trafficking and the limits of dismantling strategies. Soc. Netw. Anal. Min. 14, 84 (2024). https://doi.org/10.1007/s13278-024-01208-x
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s13278-024-01208-x