Abstract
Wireless Sensor Network (WSN) consists of several Sensor Nodes (SN) for monitoring various applications and sensing the environmental data. The WSN gathers and compiles the detected data before sending it to the Base Station (BS). The nodes have limited battery power, so efficient data transmission techniques and data collection methods are required to enhance the sensor network lifetime. In this paper, the Particle Swarm Optimization (PSO) method is utilized to form the cluster, and a Fuzzy based Energy Efficient Routing Protocol (E-FEERP) is proposed using average distance of SN from BS, node density, energy and communication quality to transmit data from cluster head to the BS in an optimal manner. The proposed protocol used parallel fitness function computing to quickly converge to the best possible solution with fewer iterations. The protocol used PSO-based clustering algorithm that recognize how birds act when they are in a flock. It is an optimization strategy that uses parallel fitness function computing to get to an optimal solution quickly and with a small number of iterations. Fuzzy is combined with PSO to increase coverage with reduced computational overhead. The proposed E-FEERP improves network performance in terms of packet delivery ratio, Residual Energy (RE), throughput, energy consumption, load balancing ratio, and network lifetime.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In recent years, WSNs have attracted researchers in different studies primarily because of various applications in different sectors. The WSN utilized in health monitoring, environmental monitoring, military tracking, animal detection and monitoring and other network tracking applications [1, 2]. WSN is a group of SNs that are scattered and are responsible for recording an environment's physical conditions. Temperature, soil moisture Pressure and other physical factors are data collection parameters. The data are organized at a central point known as BS over wireless links [3]. The sensors in a WSN are attached to a radio transceiver, a microprocessor, an electronic gadgets for communicating with other devices and an energy supply, typically battery-powered [4]. Energy management is critical in WSNs, as the energy source cannot be recharged or replaced [5]. The transfer of sensed information to the BS can be accomplished by various approaches, including single-hop, multi-hop, tree-based, chain-based, and cluster-based transmission [6]. Low Energy LEACH is the first hierarchical routing protocol based on clusters. Each cluster node gets the opportunity to become a CH in this protocol [7]. For effective data collection and transmission tasks, various clustering and routing protocols are available nowadays [8]. Due to the elimination of data redundancies, the clustering approach based on data aggregation and transmission results in a longer life span [3]. Clustering approaches partitioned the SNs into different clusters; where each and every cluster has a CH. Each SN in their respective cluster communicates the detected data to its associated CH for further transmission to the base station. After cluster generation, there may be some leftover nodes in the monitoring area, known as individual nodes [6]. These SN consume more energy to transmit the data directly to the sink node. However, these nodes must send several control messages to decide the next optimal hop toward the base station. The Optimized-Energy Efficient Routing Protocol (OEERP) enhances the lifetime of network. During the clustering with OEERP, few nodes remain in the sensor network that does not belong to any cluster. Each cluster formation follows precisely the same procedure. The proposed work uses the PSO method for cluster creation and CH election, which eliminates the creation of leftover nodes [7]. There are various variants of LEACH protocols, like Modified LEACH (MODLEACH) [9], which is an improved version of the LEACH. It changes CH in each round using a threshold. If the current CH energy is higher than the threshold, it becomes the next CH. MODLEACH is enhanced by adding two new variants, MODLEACHHT [9] and MODLEACHST [9]. They reply faster than MOD-LEACH, although they have certain flaws. In a large-scale area, they also use a single-hop data transmission. The data is sent from the node to the sink via multi hops techniques in Multi-Hop LEACH (MH-LEACH) [10]. The following are the operational modes of MH-LEACH. The nodes send CH detected data to CH and then pass it on to the next CH. This procedure is continued till the data packet is delivered to the sink node. The delivery of data packets over several hops uses more energy and time; thus, MH-LEACH addresses the single-hop problem in MODLEACH. To enhance the RE of SN, the Average Clustering Ratio (ACR) is determined in the paper. Another significant aspect affecting the network lifespan is the routing path development. The proposed system uses the Fuzzy-based Search Algorithm [8] (FSA) technique to choose the next optimum hop in the network. The node position, velocity, and energy among the CHs are considered while determining the next optimum hop. The highest energy clusters are chosen to transmit the data to BS. In [11] the authors used a PSO technique in the protocol in order to minimize intra-cluster gaps and improve network performance. In [12], the authors proposed a fuzzy-based enhanced flower pollination technique. With the help of the heuristic algorithm, the threshold-sensitive and clustering protocol for energy efficiency is proposed to improve the CH methodology selection. When choosing the CH, node centrality, RE, and distance to the BS are considered. The authors proposed in recent years, several other methods have been presented to ensure a longer multi-level clustering. These methods include the centralized energy [13], the hybrid unequal clustering [14], and sleep–awake energy-efficient method [15]. In [16], the authors designed a centralized routing method base-station controlled dynamic clustering protocol (BCDCP) to increase network lifespan and energy efficiency. The effectiveness of BCDCP is then contrasted with clustering-based techniques such as LEACH, LEACH-C, and PEGASIS. According to simulation results, BCDCP extends network lifetime and lowers overall energy usage. In [17], the authors proposed a protocol named TelMED, a dynamic user clustering method based on heterogeneous nodes. In order to dynamically group users and classify them. Thus, the approach outperforms dynamic MIMO user grouping by 92.3%. In [18], the authors presented an improved energy-efficient LEACH (IEE-LEACH) protocol. IEE-LEACH incorporates residual node energy and network average energy. To reduce sensor energy usage, IEE-LEACH accounts for the ideal CHs and restricts closer nodes from joining the cluster. Simulation findings show that the proposed protocol decreases WSN energy usage compared to existing methods.
1.1 Motivation and Contributions
The paper presents a PSO-based clustering protocol which utilized the fuzzy logic-based routing approach to transmit the data effectively to BS. The motivation behind this work is as:
-
a.
PSO is considered as a multi-criteria optimization approach, in which multiple particles in a swarm can work towards optimizing a fitness function and hence the convergence of the protocol is faster.
-
b.
Most of the existing clustering approaches have been proposed to improve the network lifetime by reducing the energy of SN The method aims to minimize the RE of SN; as a result, the energy consumption is minimized, and improved system performance.
-
c.
A Fuzzy logic-based routing strategy is proposed, which considers multiple parameters and can provide better network performance.
In [19], the authors discussed the addition, subtraction, multiplication, and division operations' distribution characteristics are simulated using the recently created metaheuristic search approach known as the Arithmetic Optimization Algorithm (AOA), which solve the issues.
In [20], the authors discussed Dwarf mongoose optimization method (DMO) is a novel metaheuristic algorithm proposed in this research for solving the classical problems. The DMO can be seen foraging like a dwarf mongoose.
In [21], the authors discussed that a modified binary grey wolf optimizer with a support vector machine is used to improve an IDS (GWOSVM-IDS). In [22], the suggested approach for detecting intrusions combines Particle Swarm Optimization (PSO) with Grey Wolf Optimization (GWO) to tackle feature selection issues and utilizes the optimal value to update each grey wolf position's data. This method avoids the GWO algorithm entering a local optimum by maintaining the individual's location information.
The proposed PSO-based clustering algorithm that makes use of a bird's flocking behavior. It is an optimization strategy that uses parallel fitness function computing in order to converge quickly and deliver an optimal solution with comparatively few iterations. A fuzzy method is coupled with PSO to increase coverage regions while reducing computation overhead. The proposed approach outperforms existing systems in energy consumption, load balancing ratio, and network longevity.
The categorization of paper as follows: a literature review is presented in Sect. 2, a PSO-based clustering method is proposed in Sect. 3, results and discussion are shown in Sect. 4, and a conclusion and discussion on future work are presented in Sect. 5.
2 Related Work
The research in the field of WSN has focused on effective techniques for cluster formation, data collection, data aggregation and routing. In this section, we have discussed some of those techniques:
2.1 Low Energy Adaptive Clustering Hierarchy (LEACH)
LEACH is a clustering technique with self-healing capabilities. The process in LEACH contains a random selection of CH. The CH is elected using the SN that has energy maximum and is the most accessible in the network [23]. The CH is elected, and a data fusion operation is performed for data compression in the network. The compressed information/data is transferred only to the sink; hence the network lifetime is enhanced. The LEACH protocol is divided into three stages:
-
(1)
Advertising stage A random sequence number between 0 and 1 is chosen by each SN. If the selected value is lower threshold \(T(n\)), the respective SN is marked as CH for that round. The threshold is using Eq. (1).
$$T\left( n \right) = \left\{ {\begin{array}{*{20}l} {p/\left\{ {1 - p(rmod\left( {1/p} \right)} \right\}} \hfill & {{\text{if }}\quad {\text{n}} \in G} \hfill \\ 0 \hfill & {{\text{else}}} \hfill \\ \end{array} } \right.$$(1)here, n indicates the nodes, p indicates the required node percentage considered as CH, r indicates the SN in the existing round elected as CH in the previous 1/p rounds, and G is the candidate CH nodes [24].
-
(2)
Cluster formation stage In this state, the SN notifies the corresponding CH to choose to join the cluster as a cluster member (CM) during the cluster formation phase. The Medium Access Control protocol based on Carrier Sense Multiple Access is used.
-
(3)
Steady state-stage For each of its CM, the CH build a TDMA for the transmission of data in the network. The cluster SN are forced to transfer the sensed information within the allotted time frame. After receiving data from cluster nodes, CH aggregated it and transmits it to BS. Each node’s energy ingesting is reduced by turning off the equipped transmitter until the data transmission time slot arrives.
2.2 Data Routing for In-Network Aggregation (DRINA)
DRINA is a technique for constructing routing trees and determines the optimal path between all SN in a network [25]. The role of the entities used to construct the routing tree in the protocol is as follows:
Collaborator The collaborator node detects and collects data in response to an event. The information gathered sent to coordinator SN [26].
Coordinator The collaborator node. At the end of the election, this node is called the coordinator node. It handles the data collection and aggregation and transmitted data to BS.
Relay nodes These nodes lay between the sink and the coordinator node. These nodes are called relay nodes because they send information to BS [27].
The steps follows:
-
Routing tree construction
-
Election of the Coordinator (Cluster head)
-
Data is sent to the base station after it is sensed.
2.3 Base-Station Controlled Dynamic Clustering Protocol (BCDCP)
The BCDCP represents a centrally controlled routing technique with BS as an important component and has a huge computational capability. It divides the area into two sub-networks called sub-clusters and again into smaller clusters till the desired number of clusters is achieved. To provide complete coverage across the field, CHs are positioned at a maximum distance [28]. This technique employs a CH-to-CH multiple hop data transmission policy to determine the most energy-efficient transmission path. A threshold value is set after calculating the average energy. The SN with adequate energy chosen as CHs for round. The minimum spanning tree approach is used to choose routing paths. To avoid radio disruption caused by neighboring clusters, this protocol employs the Code Division Multiple Access (CDMA) mechanism. Cluster formation occurs regularly, and information is communicated to the BS.
2.4 NEEC
The Energy Efficient Cluster (NEEC) represents a recently introduced clustering technique [29]. The base station starts the cluster formation. Cluster heads are chosen by recognizing the nodes that receive the maximum response from the nodes for the initiated request messages. Furthermore, CHs are elected based on overall energy dissipation and lifetime. The cluster formation operation begins after the BS receives all the node’s details, their position and RE level. The highest node level is the cluster head. To route the sensed data, a route request message is provided. The shortest path is identified using the response message and the sequence (Table 1).
This paper proposes a PSO-based clustering mechanism using the flocking nature of a bird. It is an optimization technique which involves parallel computation of fitness function, so it can converge fast and provide an optimal solution in relatively less iteration. In order to achieve more coverage regions with less computation overhead, a Fuzzy technique is integrated with PSO.
3 Proposed Protocol
The proposed aims to determine the optimal cluster using the PSO-based optimization method and select the optimal path for forwarding data to route it toward the BS. The steps of the proposed protocol are shown in Fig. 1.
-
(i)
Determine the CHs using the PSO optimization technique.
-
(ii)
Cluster formation
-
(iii)
Sensing the environmental parameters
-
(iv)
Using the Fuzzy Inference approach, the data transmission path to the BS is chosen
The details of each step are discussed in the subsequent sections.
3.1 Proposed PSO-Based Clustering
PSO starts with a random collection of particles and iterates over generations to find the best solution, as shown in Fig. 2. The peak value is updated for every particle in several iterations. The initial highest values, known as p_best, can be considered as fitness. The particle swarm optimizer can track the second “optimal” value, which is the optimal value identified in the entire swarm inhabitants and is represented as the global best (g_best). Similarly, when a particle adopts topological neighbours in a swarm inhabitant, it is known as local best (l_best).
3.2 Cluster Prediction in the Network
Consider the sensing region of the dimensions (X, Y) and the coverage of a sensor node to be r. Figure 3 illustrates a representative cluster formation in the WSN. It is subdivided into smaller segments known as clusters with a radius of r.
Consider a cluster with coordinates in a particular sensing zone as (x, y). The clusters generated (NC) is determined using entire area and the network cluster size.
where X, and Y represent the network region and x, and y denotes the cluster area.
Let x = y = t, then Eq. (3) can be written as,
Figure 3 shows a right-angled triangle. The radius r value can easily be computed as,
Hence, the number of clusters is computed as,
The count for the upper bound clusters can be computed as,
If X = Y, t = r2, & x, y = t, then Eq. (6) can be re-written as,
Using the lower and upper bound values, we can estimate the average amount of formed clusters in a network with the help of Eqs. (5) and (6), respectively, as,
3.3 Cluster Formation
The clustering process begins after the deployment of SN in the monitoring region. The BS transmit an information collection message to all SN in the WSN [30]. In turn, SN transmits to BS an information collection reply message that includes:
-
a.
The energy level of the node is represented by E.
-
b.
The respective velocity (V) of the node V = (v1, v2), where v1 and v2 represent the average and current velocity of the node, respectively.
-
c.
Location or Position of the node (x, y).
The nodes’ location, energy, and velocity values are stored and updated at BS. The BS then configures the SN for clustering using PSO. All the nodes in a WSN are presumed to be a particle in this case. The clustering effectively prevents the establishment of individual nodes. This is accomplished by enabling each node to discover its nearest neighbours inside its radio transmission range and form clusters. Similarly, all nodes in a WSN are permitted to create clusters. As a result, all SN become members of one of the clusters. The same procedure is continued until all nodes in the network become members of any cluster. Each particle’s average RE is calculated.
Consider a space containing sensors (particles). The sample space has N sensors (particles) = {1, 2, 3… m}. The two parameters used to generate particles are,
-
1.
Position (x, y)
-
2.
Velocity (v1, v2)
The following three key factors determine the respective fitness value used to choose a cluster particle:
-
1.
The SN energye/particle (EN).
-
2.
Particles/SN within radio range of a specific particle’s energy (p)
-
3.
The distance between a particle and all other particles within the radio range (p)
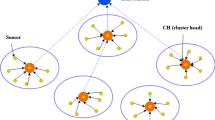
Cluster formation considers all particles’ fitness. A cluster particle is associated with each cluster as shown in Fig. 4. Cluster particles are chosen from AN that are accessible to the maximum SN number. The nodes having a greater number of nodes within their sensing range are considered as cluster particles [31].
The fitness value (FV) [32, 33] of each particle is computed using Eq. (9) as,
where α1 and α2 are random constant values between 0 & 1.
where dNr represents Nth node, N = 1, 2, 3,…,m,dN − dP is distance between sensor(particle) and Nth node, and Cn is number of clusters accessible from particle p.
where n denotes the total amount of SN a specific particle can reach. Equation 13 represents the updated velocity [31] of every particle and is computed using Eq. 13:
where, ω is weight is associated with the node velocity, ω1 and ω2 represent respective weights of the node location, pt−1 = preceding position of the SN, vt−1 = preceding velocity of the SN and pt = present position of the SN.
The particle’s position may be changed using the information of the particle's prior position, and current velocity, as shown in Eq. (14).
Each iteration’s fitness function is determined [31]. The l_best refers to the maximum FV associated with each rotation, while g_best denotes the maximum fitness in overall iterations. If the g_best value is attained in the ith rotation, the FV of every particle in that lth rotation is used when clustering occurs. The node with the highest FV is used as a reference; cluster formation is done by adding nodes within its communication range, referred to as CMs. The g_best value is broadcast to each CH to inform each CH about the g_best node. The information is delivered with respect to the node id. The fitness value that corresponds to each SN in a network is shown in Table 2 during global iteration.
It is clearly seen in Fig. 5 that the SN with the highest FV is 10. The initial cluster is constructed by adding neighbouring nodes as the CMs.
In a more extensive network, such as one consisting of 100 nodes, requires more amount of memory to store the database. To escape it, the fitness threshold \({\mathrm{f}}_{\mathrm{T}}\) is calculated as:
As a result, it is mandatory to keep the database table updated, having FV equal to or larger than the associated threshold.
Figure 5 illustrates a sensor network with nodes and the FV derived with the algorithm in Eq. (9). In this example, three groups of clusters are produced based on the maximum FV. It is shown that the node that is reachable to the sensing range of the majority of the nodes in an area has the highest FV. The method is repeatedly continued for the construction of the cluster. The second largest number is 9, forming a second cluster. As shown in Table 2, the third greatest fitness value is 7; however, as shown in Fig. 5, the node having an FV value = 7 is already a CM of the 2nd cluster. Thus, to create the 3rd cluster, FV = 6 is used, and so on. In this process, a Cluster Assistant (CA) node is chosen adjacent to the cluster particle or cluster head for each cluster with the highest fitness score. The CA for the very first cluster has an FV of 5, which is adjacent to the cluster particle shown in Fig. 5. The cluster assistant aims to function as a support node for the CH. If a CA dies, it may revert to a CH. The different RE level of the nodes in the process is shown in Fig. 6.
3.4 E-FEERP-Based Path Selection Algorithm
In the E-FEERP, a fuzzy-based path selection technique is utilized to get the optimal route for sending the data from CH to BS. The source node is the one that contains the data to send. This node determines the next hop for transmitted the detected datato destination or BS [34]. The route request message (Rq) is transmitted to all neighbours to determine the next optimal hop. This message includes information: (i) node’s position, (ii) velocity, (iii) node degree and (iv) energy pertaining to the neighbour’s node [35].
The Neighbor nodes transfer requests to neighbours by modifying their values for the receiving position, energy, and velocity. The procedure is repeatedly continued until the request reaches the BS. The FSA technique is used to get the optimal next hop in the proposed protocol. Figure 7 shows the model representing the proposed E-FEERP protocol. In the proposed E-FEERP model, CH selection depends upon four input membership functions: Battery Energy, Node Density, Communication Quality and Average distance of SN from BS.The triangular membership function represents the Fuzzy membership graph to represent input range values.
3.4.1 Development of a FIS System
The various steps involved in firing the fuzzy rules using the Fuzzy Inference System are as follows:
Step 1 Take the input variables as Battery Power, Node Density, Communication Quality and Average Distance and the output variable as the likelihood.
Step 2 Take Membership Functions (MFs) for Battery Power as Low, medium, high, and very high, MFs for Node Density as Low, medium, high, and very high, MFs for Communication Quality as poor, medium, good, and very good and MFs for Average Distance as reasonable, good, and extensive.
Step 3 If then rule is applied for CH selection.
Step 4 Fuzzy value is obtained for likelihood.
Step 5 De-fuzzification.
3.4.2 Fuzzy Rule Set
Let Battery power is represented as: \({\mathrm{B}}_{\mathrm{p}}\), Node density:\({\mathrm{N}}_{\mathrm{d}}\), Average distance from BS:\({\mathrm{D}}_{\mathrm{Avg}}\), Communication quality:\({\mathrm{C}}_{\mathrm{q}}\), the fuzzy rules are created as follows:
Rule [1] If (\({\mathrm{B}}_{\mathrm{p}}\) is Very High) and (\({\mathrm{N}}_{\mathrm{d}}\) is Very High) and (\({\mathrm{D}}_{\mathrm{Avg}}\) is Very High) and (\({\mathrm{C}}_{\mathrm{q}}\) is Very Good) then (Likelihood is Very High).
Rule [2] If (\({\mathrm{B}}_{\mathrm{p}}\) is High) and (\({\mathrm{N}}_{\mathrm{d}}\) is High) and (\({\mathrm{D}}_{\mathrm{Avg}}\) is High) and (\({\mathrm{C}}_{\mathrm{q}}\) is Good) then (Likelihood is High).
Rule [3] If (\({\mathrm{B}}_{\mathrm{p}}\) is Medium) and (\({\mathrm{N}}_{\mathrm{d}}\) is Medium) and (\({\mathrm{D}}_{\mathrm{Avg}}\) is Medium) and (\({\mathrm{C}}_{\mathrm{q}}\) is Medium) then (Likelihood is Medium).
Rule [27] If (\({\mathrm{B}}_{\mathrm{p}}\) is Low) and (\({\mathrm{N}}_{\mathrm{d}}\) is Low) and (\({\mathrm{D}}_{\mathrm{Avg}}\) is Low) and (\({\mathrm{C}}_{\mathrm{q}}\) is Poor) then (Likelihood is Low).
3.4.3 Representation of Fuzzy Membership Function (MF)
The proposed E-FEERP protocol chooses the best path for data transmission from cluster nodes to the BS using the defined fuzzy rules. Figure 8, 9, 10 and 11 shows the membership function and the respective input range values of the input parameters. The first Input Membership (IM) is the battery power of nodes. Low, Medium, High, and Very High are the four membership functions (MFs) available, as shown in Fig. 8. Equation 16 shows the mathematical representation of the respective fuzzy membership values.
where, TH1 and TH2 are upper and lower thresholds.
Average node density is the next IM in the proposed fuzzy model. The network density determines the creation of CH; high-density areas require significant data aggregation; therefore, CH formation is necessary. The Trapezoidal MFs represent average node density in the defined input range value with wider range values.
Low, Medium, High, and Very High are the four membership functions (MFs) available, as shown in Fig. 9. CH can improve data transfer in areas with a weak connection. The third IMF in the given fuzzy model is communication quality. Low, Medium, High, and Very High are the four membership functions (MFs) available, as shown in Fig. 10.
The energy dissipated in data transmission is determined by the distance between SN and BS. CH reduces energy consumption during data transmission and increases network lifespan. The fourth IMF in the given fuzzy model is the Average distance. Low, Reasonable, good, and extensive are the three MFs available, as shown in Fig. 11. The likelihood function is selected based on the Fuzzy rules embedded in the FIS of E-FEERP. The likelihood for the output to choose a node for data transmission from SN to the BS is calculated by fuzzy output membership. The various MF values associated with the likelihood of the output are (i) low, (ii) medium, (iii) high, and (iv) very high, as shown in Fig. 12.
The principles for mapping IF—then output variables based on the defined Fuzzy rules are shown in Table 3. Here 4 input parameters are used, and each variable can be assigned one of 4 MF values, then, the total possible rules are computed as 4 × 4 × 4 × 4 = 256.
Once the cluster is created and the CH is elected using the PSO technique, all the SN in the cluster begin the operation of sensing and transmitting data to CH respective. This causes the CHs to initiate the procedure of aggregating input signals to reduce data redundancy.Thus, prior to transmitting the detected data to the BS, each CH needs to anticipate the shortest, most reliable route for transmitting the aggregated data. As a result, each cluster head begins by determining the optimal next hop.
4 Result and Discussion
The proposed E-FEERP protocol developed with the integration of PSO with Fuzzy is simulated using the Matlab simulator. Matlab is suitable software for analyzing and evaluating the outcomes of work performed on WSNs.
4.1 Network Deployment
The amount of RE nodes for each step of cluster formation is estimated and compared for both proposed and existing techniques. The proposed E-FEERP utilizes a revolutionary approach to cluster formation called PSO. The formation of a cluster occurs relies on the fitness values of the nodes. Table 4 lists the basic parameters taken into account during network configuration.
Equations (9) and (10) are used to get the fitness value in the proposed work. In the deployment phase, 100 nodes are deployed in a 200 × 200 m2 region in the proposed protocol, as depicted in Fig. 13.
In the proposed protocol’s cluster formation stage, clusters are formed using the PSO techniques. The E-FEERP sends CH data to BS, as shown in Fig. 14.
4.2 Performance Comparison
The efficiency of E-FEERP is contrasted with the prevailing approaches on various performance parameters as follows:
4.2.1 Residual Energy
In the proposal, FV-based clusters are constructed. In each iteration, the priority index is assigned to each node, and each node is assumed as the CH. There may be fewer or zero nodes available in the deployed WSN. When there are zero residual nodes or a very small number of residual nodes, this is called a global iteration, and at this stage, the formation of the clustering process stops. At the end of the iteration, residual nodes are still left the network depicted in Fig. 15. When the proposed E-FEERP is used, fewer residual nodes are formed than in the existing protocol. The average network lifetime is improved when all of the nodes join at least one of the clusters. The results demonstrate that the number of residual energy is 6 for E-FEERP, which is significantly less than the existing approaches. The residual energy is 6, 35, 42, 17 and 19 for the approaches E-FERP, LEACH, BCDCP and NEEC, respectively.
Figure 15 shows the details of the first parameters that were thought about during network setup. E-FEERP is proposed. Both the proposed and existing approache’ residual nodes for each cluster formation step are compared. Cluster formation occurs based on the nodes’ fitness value. The network’s remaining nodes are fewer as a result. Reducing leftover nodes reduces energy usage and improves network longevity.
4.2.2 Load Balancing Ratio
The term ‘load balancing’ refers to the parameter that determines the average amount of nodes with a similar energy level in an individual cluster in the WSN. The same is illustrated in Fig. 16 for a variety of protocols. The results show that the LBR is 1.2 for the E-FEERP, which is significantly higher than the existing approaches. The load balancing ratio is 1.0, 1.0, 1.1 and 0.1 for the approaches OEERP, LEACH, BCDCP and NEEC, respectively.
4.2.3 Energy Consumption
The majority of the energy usage of an individual node is the combination of sensing, computation, and communication. The Node energy consumption can be calculated as
The total amount of energy dissipation of the nodes at various time slots is calculated for the existing and proposed approach, as seen in Fig. 17. The results show that energy consumption is least for the E-FEERP and it increases with the increase in the simulation time.
The total number of SN directly relates to the energy usage. In other words, as the number of SN increases, so does the overall energy usage. Each protocol has a progressive increase in the amount of energy consumed over a different time period. According to Fig. 17, the proposed E-FEERP energy consumption is less than that of other existing protocols. It has reduced energy usage resulting in an increased network lifespan. The energy consumption of E-FEERP, OEERP, LEACH, DRINA, and BCDCP protocol for 50 ms are 8 J, 10 J, 20 J, 7 J and 15 J, respectively. Similarly, for 100 ms are 4 J, 10 J, 16 J, 18 J and 42 J, respectively. Similarly, for 150 ms are 18 J, 19 J, 42 J, 17 J and 19 J, respectively. Similarly, for 200 ms are 20 J, 35 J, 70 J, 19 J and 19 J, respectively. Similarly, for 250 ms are 25 J, 37 J, 85 J, 43 J and 24 J, respectively.
4.2.4 Throughput
The term “throughput” refers to the efficiency of transmitting data to the targeted receiver or the BS and is measured in bits/s. The proposed E-FEERP and existing protocols’ throughputs are compared in Fig. 18. The bar graph demonstrates the proposed approach has a higher throughput than existing protocols. The throughput of E-FEERP, OEERP, LEACH, DRINA, and BCDCP protocol for 50 ms are 78,000 packets, 51,000 packets, 52,000 packets, 72,000 packets and 19,000 packets, respectively. Similarly, for 100 ms are 80,000 packets, 52,000 packets, 51,000 packets, 79,000 packets and 24,000 packets, respectively. Similarly for 150 ms are 81,000 packets, 61,000 packets, 60,000 packets, 79,000 packets and 25,000 packets respectively. Similarly, 200 ms are 81,000 packets, 61,000 packets, 60,000, 71,000 packets, and 39,000 packets, respectively. Similarly, for 250 ms are 81,000 packets, 61,000 packets, 60,000 packets, 62,000 packets and 30,000 packets, respectively.
4.2.5 Packet Delivery Ratio
The improvement in packet delivery ratio (PDR) shows the effectiveness of the E-FEERP protocol when compared to other existing protocols, as shown in Fig. 19. The packet delivery ratio of E-FEERP, OEERP, LEACH, DRINA, BCDCP protocol for 50 ms are 96 packets, 60 packets, 62 packets, 83 packets and 20 packets, respectively. Similarly, for 100 ms are 97 packets, 62 packets, 63 packets, 96 packets and 38 packets, respectively. Similarly, for 150 ms are 97 packets, 60 packets, 62 packets, 96 packets and 38 packets, respectively. Similarly, 200 ms are 83 packets, 60 packets, 62, 82 packets, and 38 packets, respectively. Similarly, for 250 ms are 82 packets, 60 packets, 61 packets, 72 packets and 30 packets, respectively. Similarly, 200 ms are 83 packets, 60 packets, 62, 82 packets, and 38 packets, respectively. Similarly, for 300 ms are 77 packets, 58 packets, 61 packets, 62 packets and 39 packets, respectively.
4.2.6 Network Lifetime
The lifetime of network is determined by the sensor node's effectiveness. The sensing regions of the sensor nodes are utilized to perform sensing, computation, and transmission. The lifetime can be enhanced by preventing the SN from transmitting duplicate data. The same can be attained by using these mechanisms:
-
Aggregation of sensed data to avoid data redundancy
-
Removing the overhead control messages from the network and
-
Avoiding the use of long-distance communication.
The network’s overall lifetime can be increased if the elements listed above are considered when designing the network. These considerations are incorporated into the proposed strategy, which enhances network lifetime. Figure 20 shows the total lifetime of E-FEERP is greater than the lifetime of other protocols.
The proposed E-FEERP protocol optimally utilizes energy consumption inside the network and significantly extends the lifetime of WSN when compared to previous protocols. The proposed work has a longer lifetime.
The packet delivery ratio of E-FEERP, OEERP, LEACH, DRINA, and BCDCP protocol for 50 ms are 9000 rounds, 7000 rounds, 2900 rounds, 8700 rounds and 4900 rounds, respectively. Similarly, for 100 ms are 7700 rounds, 3000 rounds, 1700 rounds, 6700 rounds and 3000 rounds, respectively. Similarly, for 150 ms are 5100 rounds, 2000 rounds, 1000 rounds, 3200 rounds and 2100 rounds, respectively. Similarly, 200 ms are 1900 rounds, 1800 rounds, 1500 rounds, 1700 rounds, and 1800 rounds respectively. Similarly, for 250 ms are 1700 rounds, 1600 rounds, 1500 rounds, 1550 rounds and 1650 rounds, respectively. Similarly, for 300 ms are 1500 rounds, 1400 rounds, 1200 rounds, 1150 rounds and 1650 rounds, respectively.
4.2.7 End to End Delay
The End to End delay of E-FEERP, OEERP, LEACH, DRINA, and BCDCP protocol for 25 nodes are 95 ms, 97 ms, 99 ms, 103 ms and 104 ms, respectively. Similarly, for 50 nodes are 96 ms, 100 ms, 102 ms, 104 ms and 106 ms, respectively. Similarly, for 75 nodes are 105 ms, 108 ms, 110 ms, 113 ms and 116 ms, respectively. Similarly, 100 nodes are are 110 ms, 115 ms, 118 ms, 125 ms, and 132 ms, respectively as shown in Fig. 21.
5 Conclusion and Future Work
The paper presented a PSO-based clustering and fuzzy-based routing approach to enhance the performance of the WSN. The PSO-based clustering improved the cluster formation in E-FEERP protocol by reducing the number of residual nodes. The network efficiency is increased in the proposed protocol because of the fuzzy rule-based optimum route selection and data transmission phase. The increase in the number of nodes increases the total consumption of energy, thus, the proposed protocol makes use of an optimal number of sensor nodes to decrease the consumption of energy in the network. The simulation results demonstrate the improvement in lifetime of the network in terms of packet delivery ratio, throughput and energy consumption when compared to various existing protocols. The research can be extended to a huge network area using a multi-tier network architecture with heterogeneous nodes.
Data Availability
There are no data required for this work.
Code Availability
There is no code available for this manuscript.
Abbreviations
- WSN:
-
Wireless Sensor Network
- CH:
-
Cluster head
- BS:
-
Base station
- CM:
-
Cluster Member
- SN:
-
Sensor Node
- RE:
-
Residual Energy
- OEERP:
-
Optimized Energy Efficient Routing Protocol
- LEACH:
-
Low Energy Adaptive Clustering Hierarchy
- PSO:
-
Particle Swarm Optimization
- ACR:
-
Average Clustering Ratio
- FSA:
-
Fuzzy Based Search Algorithm
- TDMA:
-
Time Division Multiple Access
- DRINA:
-
Data Routing for In-Network Aggregation
- BCDCP:
-
Base Station Controlled Dynamic Clustering Protocol
- RE:
-
Residual Energy
- CDMA:
-
Code Division Multiple Access
- E:
-
Energy level
- V:
-
Velocity
- FV:
-
Fitness Value
- CA:
-
Cluster Assistant
- EFEERP:
-
Enhanced Fuzzy Based Energy Efficient Routing Protocol
- FIS:
-
Fuzzy Inference System
- MF:
-
Membership Function
- IMF:
-
Input Membership Function
- LBR:
-
Load Balancing Ratio
References
Chaturvedi, P., & Daniel, A. K. (2015). An energy efficient node scheduling protocol for target coverage in wireless sensor networks. In 2015 Fifth International Conference on Communication Systems and Network Technologies (pp. 138–142). IEEE. doi: https://doi.org/10.1109/CSNT.2015.10.
Narayan, V. & Daniel, A. K. (2020). Multi-Tier Cluster Based Smart Farming Using Wireless Sensor Network. In 2020 5th International Conference on Computing, Communication and Security (ICCCS), pp. 1–5.
Narayan, V. & Daniel, A.K. (2021). RBCHS: Region-Based Cluster Head Selection Protocol in Wireless Sensor Network. In Proceedings of Integrated Intelligence Enable Networks and Computing, Springer, pp. 863–869.
Ari, A. A. A., Yenke, B. O., Labraoui, N., Damakoa, I., & Gueroui, A. (2016). A power efficient cluster-based routing algorithm for wireless sensor networks: Honeybees swarm intelligence based approach. Journal of Network and Computer Applications, 69, 77–97.
Famila, S., & Jawahar, A. (2020). Improved artificial bee Colony optimization-based clustering technique for WSNs. Wireless Personal Communications, 110(4), 2195–2212.
Narayan, V., & Daniel, A. K. (2021). A novel approach for cluster head selection using trust function in wsn. Scalable Computing: Practice and Experience, 22(1), 1–13. https://doi.org/10.12694/scpe.v22i1.1808
Narayan, V., Daniel, A. K., & Rai, A. K. (2020). Energy efficient two tier cluster based protocol for wireless sensor network. In 2020 International Conference on Electrical and Electronics Engineering (ICE3) (pp. 574–579). IEEE. doi: https://doi.org/10.1109/ICE348803.2020.9122951.
Faiz, M. & Daniel, A. K. (2021). Multi-criteria based cloud service selection model using fuzzy logic for QoS. In International Conference on Advanced Network Technologies and Intelligent Computing, pp. 153–167.
Mahmood, D., Javaid, N., Mahmood, S., Qureshi, S., Memon, A. M., & Zaman, T. (2013). MODLEACH: a variant of LEACH for WSNs. In 2013 Eighth international conference on broadband and wireless computing, communication and applications, pp. 158–163.
Neto, J. H. B., Rego, A., Cardoso, A. R., & Celestino, J. (2014). MH-LEACH: A distributed algorithm for multi-hop communication in wireless sensor networks. ICN, 2014, 55–61.
Thiagarajan, R. (2020). Energy consumption and network connectivity based on Novel-LEACH-POS protocol networks. Computer Communications, 149, 90–98.
Mittal, N., Singh, U., Salgotra, R., & Bansal, M. (2020). An energy-efficient stable clustering approach using fuzzy-enhanced flower pollination algorithm for WSNs. Neural Computing and Applications, 32(11), 7399–7419.
Aslam, M., Shah, T., Javaid, N., Rahim, A., Rahman, Z., & Khan, Z. A. (2012). CEEC: Centralized energy efficient clustering a new routing protocol for WSNs. In 2012 9th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON), pp. 103–105.
Malathi, L., Gnanamurthy, R. K., & Chandrasekaran, K. (2015). Energy efficient data collection through hybrid unequal clustering for wireless sensor networks. Computers & Electrical Engineering, 48, 358–370.
Ahmed, G., Zou, J., Fareed, M. M. S., & Zeeshan, M. (2016). Sleep-awake energy efficient distributed clustering algorithm for wireless sensor networks. Computers & Electrical Engineering, 56, 385–398.
Muruganathan, S. D., Ma, D. C. F., Bhasin, R. I., & Fapojuwo, A. O. (2005). A centralized energy-efficient routing protocol for wireless sensor networks. IEEE Communications Magazine, 43(3), S8-13.
Ahmed, S. T., Sandhya, M., & Sankar, S. (2020). TelMED: Dynamic user clustering resource allocation technique for MooM datasets under optimizing telemedicine network. Wireless Personal Communications, 112(2), 1061–1077.
Liu, Y., Wu, Q., Zhao, T., Tie, Y., Bai, F., & Jin, M. (2019). An improved energy-efficient routing protocol for wireless sensor networks. Sensors, 19(20), 4579.
Kaveh, A., & Hamedani, K. B. (2022). Improved arithmetic optimization algorithm and its application to discrete structural optimization. Structures, 35, 748–764.
Agushaka, J. O., Ezugwu, A. E., & Abualigah, L. (2022). Dwarf mongoose optimization algorithm. Computer Methods in Applied Mechanics and Engineering, 391, 114570.
Safaldin, M., Otair, M., & Abualigah, L. (2021). Improved binary gray wolf optimizer and SVM for intrusion detection system in wireless sensor networks. Journal of Ambient Intelligence and Humanized Computing, 12(2), 1559–1576.
Otair, M., Ibrahim, O. T., Abualigah, L., Altalhi, M., & Sumari, P. (2022). An enhanced grey wolf optimizer based particle swarm optimizer for intrusion detection system in wireless sensor networks. Wireless Networks, 28(2), 721–744.
Fu, C., Jiang, Z., Wei, W. E. I., & Wei, A. (2013). An energy balanced algorithm of LEACH protocol in WSN. International Journal of Computer Science Issues, 10(1), 354.
Sharma, R., Vashisht, V., & Singh, U. (2019). EEFCM-DE: Energy-efficient clustering based on fuzzy C means and differential evolution algorithm in WSNs. IET Communications, 13(8), 996–1007.
Villas, L. A., Boukerche, A., Ramos, H. S., De Oliveira, H. A. B. F., de Araujo, R. B., & Loureiro, A. A. F. (2012). DRINA: A lightweight and reliable routing approach for in-network aggregation in wireless sensor networks. IEEE Transactions on Computers, 62(4), 676–689.
Daniel, A. K., Faiz, M. (2022). Wireless Sensor Network Based Distribution and Prediction of Water Consumption in Residential Houses Using ANN. In Internet of Things and Connected Technologies. ICIoTCT 2021. Lecture Notes in Networks and Systems, vol. 32, pp. 107–116, doi: https://doi.org/10.1007/978-3-030-94507-7_11.
Narayan, V., Daniel, A. K. (2022). CHHP: Coverage optimization and hole healing protocol using sleep and wake-up concept for wireless sensor network. International Journal of System Assurance Engineering and Management, pp. 1–11.
Mehta, S., Vhatkar, S., & Atique, M. (2015). Comparative study of BCDCP protocols in wireless sensor network. International Journal of Computers and Applications, 975, 8887.
Xie, D., Zhou, Q., You, X., Li, B., & Yuan, X. (2013). A novel energy-efficient cluster formation strategy: From the perspective of cluster members. IEEE Communications Letters, 17(11), 2044–2047.
Narayan, V. & Daniel, A. K. (2021). IOT Based Sensor Monitoring System for Smart Complex and Shopping Malls. In International Conference on Mobile Networks and Management, 2021, pp. 344–354.
Kulkarni, R. V., & Venayagamoorthy, G. K. (2010). Particle swarm optimization in wireless-sensor networks: A brief survey. IEEE Transactions on Systems, Man, and Cybernetics, Part C (Applications and Reviews), 41(2), 262–267.
Yang, J., Zhang, H., Ling, Y., Pan, C., & Sun, W. (2013). Task allocation for wireless sensor network using modified binary particle swarm optimization. IEEE Sensors Journal, 14(3), 882–892.
Kim, Y. G., & Lee, M. J. (2014). Scheduling multi-channel and multi-timeslot in time constrained wireless sensor networks via simulated annealing and particle swarm optimization. IEEE Communications Magazine, 52(1), 122–129.
Chaturvedi, P., & Daniel, A. K. (2021). A hybrid protocol using fuzzy logic and rough set theory for target coverage. Recent Advances in Computer Science and Communications (Formerly: Recent Patents on Computer Science), 14(2), 467–476.
Rafsanjani, M. K., & Dowlatshahi, M. B. (2012). Using gravitational search algorithm for finding near-optimal base station location in two-tiered WSNs. International Journal of Machine Learning and Computing, 2(4), 377.
Funding
There was no funding availed for carrying out this research.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that there is no conflict of interest with this publication.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Narayan, V., Daniel, A.K. & Chaturvedi, P. E-FEERP: Enhanced Fuzzy Based Energy Efficient Routing Protocol for Wireless Sensor Network. Wireless Pers Commun 131, 371–398 (2023). https://doi.org/10.1007/s11277-023-10434-z
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-023-10434-z