Abstract
Cooperative communication has emerged to reap the benefits of spatial diversity. To fully exploit cooperative diversity, we propose a medium access control and routing enabled cross-layer cooperative transmission (MACR-CCT) protocol for improving the performance in multi-hop wireless ad hoc networks (MWAN). Different from previous cooperative protocols that determine a receiver in one hop according to a non-cooperative routing protocol first and then select a cooperative relay, MACR-CCT selects the cooperative relay together with the receiver in one hop to exploit fully cooperative diversity, so that the receiver is selected for higher cooperative gain and closer distance to destination, and the relay is selected to achieve the better throughput performance while considering transmission error. Furthermore, considering that there are multiple source–destination pairs in MWAN, MACR-CCT takes interference mitigation into account to further improve network throughput when selecting the cooperative relay. Besides, we propose a theoretical model to analyze the throughput performance. Finally, we take advantage of simulation results to validate the effectiveness of our analytical model and show that our proposed MACR-CCT protocol can significantly outperform existing packet transmission mechanisms in terms of throughput and delay under the multi-hop multi-flow network scenario.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
In this paper, we investigate the design problem of the cross-layer protocol that spans physical, medium access control (MAC) and routing layers for exploiting cooperative diversity in multi-hop wireless ad hoc networks (MWAN). In cooperative communication system, two stages are always needed to obtain cooperative diversity. Data packets are broadcasted by the transmitter in the first stage, which can be overheard by the receiver and cooperative relays simultaneously. Then, data packets are forwarded to the receiver by the relays in the second stage. By this kind of cooperative, network performance can be significantly improved as comparison to the traditional non-cooperative schemes when the direct link quality is poor.
Up to now, much research has been conducted on cooperative MAC and routing protocols (see Sect. 2), respectively. However, these cooperative MAC and routing protocols are designed separately, and do not adopt the cross-layer approach that incorporates the MAC and routing layers to improve the performance in multi-hop wireless networks. More specifically, (1) when designing the cooperative MAC protocol, it is assumed that the receiver in transmission path has been pre-determined by a certain routing protocol (such as DSR or AODV), and (2) when designing the cooperative routing protocol, it is assumed that there is a certain MAC protocol to select the cooperative relay and coordinate among the transmitter, relay and receiver.
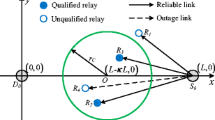
Although there is limited research on cross-layer design (see Sect. 2) in MWAN, it does not solve the problem that the cooperative relay and receiver in one hop should be jointly considered for exploiting fully cooperative diversity, instead of determining the receiver first. As shown in Fig. 1, when sender S transmits a data packet to destination D, there may have three cooperative links CL i (S, H i , R i ) (1 ≤ i ≤ 3) or even more for S to complete the transmission, where H i and R i (1 ≤ i ≤ 3) denote the cooperative relay and receiver, respectively. If we would determine R1 as the receiver according to a non-cooperative routing protocol, the cooperative link CL 1 (S, H 1, R 1) (the cooperative relay H 1 can be replaced according to a relay selection method) will be used to transmit data packets. However, it is very possible that CL 1 (S, H 1, R 1) is not the best one to reap the performance benefits (such as throughput and delay, etc.) among three cooperative links. The reason is that the receiver R 1 is determined first, without considering R 2 and R 3 as the potential receiver. Therefore, for exploiting fully cooperative diversity in MWAN, the cooperative relay and receiver in one hop should be jointly considered to obtain the performance benefits. That is our starting point in this paper.
In this paper, we propose a medium access control and routing enabled cross-layer cooperative transmission protocol (MACR-CCT) to improve the performance in multi-hop wireless networks. In MACR-CCT protocol, the cooperative relay and receiver in one hop are jointly considered to exploit fully cooperative diversity, which means that multiple potential receivers in one hop and the corresponding relays are considered to construct multiple potential cooperative links. As a consequence, the best cooperative link will be selected so that the receiver is determined for higher cooperative gain and closer distance to the destination, and the cooperative relay is determined to achieve the better performance of throughput with considering transmission error. Interference has an important impact on system performance in wireless networks [1–3]. Therefore, considering that there are multiple source–destination pairs in MWAN, MACR-CCT takes interference mitigation into account to further improve network throughput when selecting the cooperative relay. In addition, we derive saturation throughput based on an analytical model and conduct simulation to validate the effectiveness of our analytical model. Finally, we carry out extensive simulations to investigate the performance of MACR-CCT protocol with comparisons to the existing cross-layer protocol and two packet transmission mechanisms: non-cooperative IEEE 802.11 MAC with AODV routing protocol and cooperative MAC with AODV routing protocol. Simulation results show that MACR-CCT significantly outperforms existing packet transmission mechanisms in terms of throughput and delay under the multi-hop multi-source network scenario.
The remainder of this paper is organized as follows. The related work is described in Sect. 2. In Sect. 3, we elaborate the proposed MACR-CCT protocol. Section 4 presents an analytical model for performance evaluation. In Sect. 5, simulation results are given to validate the analytical model and to evaluate the cooperative performance of MACR-CCT in comparison with existing packet transmission mechanisms under the multi-hop multi-source network scenario. Finally, conclusions are given in Sect. 6.
2 Related work
To convert the cooperative gain at physical layer into the performance benefits at high layer, plenty of cooperative MAC and routing protocols were proposed [4–27]. As for a cooperative MAC protocol, the key problem is to select the best relay which the transmitter is going to cooperate with. In [4–15], with different relay selection metrics, various cooperative MAC protocols were proposed to coordinate the operations among the transmitter, receiver and relays for completing one data transmission. As for a cooperative routing protocol, the key problem is to select one optimal path from source to destination. These cooperation-based routing algorithms in [16–21] established a non-cooperative shortest path first and then build the cooperative route. Indeed, these routing strategies can not fully exploit cooperative diversity because the optimal cooperative path may completely different from the non-cooperative shortest path. To overcome this deficiency, the work in [22–26] proposed different routing algorithms based on cooperative shortest path. Different from all the above mentioned routing protocols that focus on unicast routing, In [27], Li et al. proposed a reliable multicast protocol called CodePipe using opportunistic routing and random linear network coding. However, these routing algorithms do not consider cooperative MAC layer support.
Clearly, all the aforementioned cooperative protocols do not consider fully the characteristic of multi-hop networks, i.e., in a routing path, it is mutually dependent to choose the cooperative relay and receiver in one hop, because the transmission quality is determined by three links of transmitter to receiver, transmitter to relay and relay to receiver in cooperative communications. Therefore, we need to design a cross-layer protocol that incorporates the MAC and routing layers. There is a little work [28–32] on cooperative protocols using cross-layer approach for multi-hop networks. In [28], Jakllari et al. presented a novel multilayer approach for exploiting cooperative diversity in ad hoc networks, but the approach does not consider the interdependence between choosing the receiver and corresponding relay in one hop, and also does not design a cross-layer protocol. In [29], Babaee et al. proposed a physical-network cross-layer routing algorithm with the goal of minimization of the end-to-end outage probability. But, [29] does not consider MAC layer cooperation. In [30], Aguilar et al. proposed a cross-layer protocol, CoopGeo, which involves two levels of joint design, i.e., a MAC-network cross-layer design for forwarder selection and a MAC-PHY for relay selection. Indeed, CoopGeo still determines the receiver in one hop first. He et al. [31] proposed a cooperative routing algorithm, where a cross-layer routing metric is used to select a path from source to destination. In [31], routing metric is computed on each cooperative link (including transmitter to receiver, transmitter to relay and relay to receiver), which will result in larger overhead, especially in high density networks. In [32], Gokturk et al. proposed a cross-layer protocol called routing enabled cooperative medium access control (RECOMAC) that spans physical, MAC and routing layers to improve the performance of multi-hop communication. In RECOMAC, using randomized distributed space–time codes (RDSTC) at physical layer, data packets are transmitted from the source to one cooperative set, or from one cooperative set to another cooperative set until reaching the destination. Compared with RECOMAC protocol, our proposed protocol carries out the cooperative transmission by selecting the best relay not all relays in a cooperative set, and we design a selection metric that includes three key elements of the packet error, throughput and interference with other data flows, which are not considered in RECOMAC protocol. On the other hand, when only the best relay participates in cooperation, the same cooperative diversity gain can be obtained [33], and other relays can be exempted from information transmission so that the expenditure of network resource is reduced. Furthermore, according to [34], the interference-sensitive region can also be shrunk with only one relay taking part in cooperation.
3 MACR-CCT protocol
In this section, we provide detailed description of the proposed MACR-CCT protocol. First, we make the following assumptions adopted in this paper:
-
1.
All nodes equip with one omni-directional antenna.
-
2.
Channels between any two nodes are assumed to be reciprocal and suffer from independent Rayleigh fading with additive white Gaussian noise (AWGN), and the fading coefficients remain the same during one frame exchange duration [32].
-
3.
In the second stage of cooperation, each relay may simply amplify and forward it (corresponding to AF protocol), or decode the received information and forward it (corresponding to the DF protocol). In this paper, since the relay node has to decode the overheard signal for accepting or discarding it before retransmission, the DF protocol is adopted.
-
4.
For achieving the maximum likelihood performance, maximal ratio combiner (MRC) technique is adopted by each receiver to combine the signals directly from the sender in the first stage and that from the relay in the second stage, and perfect synchronization is assumed at the receiver [6].
-
5.
Each node has capability to obtain its own up-to-date location information using some location services, such as Global Positioning System (GPS) [35], and similar to [36, 37], source is aware of the location information of destination. HELLO packets are exchanged periodically to make sure that each node has the location information of its neighbors.
3.1 Protocol description
The proposed MACR-CCT spans and combines the functions of MAC and routing layers to realize end-to-end data delivery while fully exploiting cooperative gain at physical layer. To realize the MACR-CCT protocol, it is required to introduce five kinds of control frames, i.e., cross-layer request-to-send (CL-RTS), cross-layer clear-to-send (CL-CTS), cross-layer relay-to-help (CL-RTH), cross-layer announce-to-receiver (CL-ATR) and cross-layer acknowledgement (CL-ACK). The format of these frames is extended to IEEE 802.11 RTS/CTS/ACK control frames [38] and the modified frame format is shown in Fig. 2. In the following, we generalize the protocol by describing the operations of sender (including source node), receiver (including destination node) and relay in one hop.
3.1.1 The operation of sender
Whenever sender has a data packet from source to destination in its buffer, and it is not destination of the data packet, it starts the data transmission by broadcasting the CL-RTS frame after sensing the channel to be idle. Since the sender does not know the transmission rate of data packet at the time of CL-RTS transmission, it should set duration field of CL-RTS to be D RTS , which is given by
where T CTS , T RTH and T ATR are the transmission time of CL-RTS, CL-CTS, CL-RTH and CL-ART packets, respectively. T SIFS is the time duration of one short inter-frame spacing (SIFS) in IEEE 802.11 and α is the number of potential receivers piggybacked in CL-RTS. \(T_{{CON_{1} }}\) is the average contention time for transmitting the CL-CTS frames by all potential receivers in a distributed way. \(T_{{CON_{2} }}\) is the average contention time for selecting the best cooperative relay in a distributed way according to a performance metric (we will introduce \(T_{{CON_{1} }}\) and \(T_{{CON_{2} }}\) in Sect. 4). Note here, that D RTS does not include the transmission time of data packet, and is aim at reserving the channel time for the exchange of the control packets in a conservative way.
Besides, at the moment of CL-RTS transmission, the sender should set up a timer \(T_{{O_{1} }}\) to wait for the arrival of CL-CTS frame, which can be written as
If no CL-CTS frame is received before the timer \(T_{{O_{1} }}\) expires, the sender will give up the current transmission to perform regular random backoff procedure for the next retransmission. Implicitly, due to the collision from the CL-CTS frames, the sender may not receive all of the CL-CTS frames from α potential receivers, but at least one.
During the period of D RTS − T ATR − 2T SIFS , if the sender receives the CL-RTH frame, it knows that the best relay is ready to construct a cooperative link. After the T ATR + 2T SIFS , the sender should carry out the first stage of cooperative transmission, i.e., it broadcasts the data packet toward the best relay and corresponding receiver. If the sender does not successfully receive the CL-RTH frame, which means CL-RTH frame collision happens, it should employ direct transmission and select the receiver with the maximum performance to send data packet. It is noted that MACR-CCT employs two transmission types, i.e., cooperative transmission (CT) and direct transmission (DT). When the DT is activated, the CL-RTH frame is broadcasted by the sender firstly to inform the other relay and the receiver. Since CL-RTH frame includes transmission rate and type, the duration field of data packet set by the sender can be expressed as follows:
where T CT DATA,2 denotes the transmission time of data packet for the second stage in CT and T ACK is the transmission time of CL-ACK. Besides, the sender should start a timer \(T_{{O_{2} }}\) to wait for the arrival of CL-ACK frame, which can be given by
where T CT DATA,1 denotes the transmission time of data packet for the first stage in CT and T DT DATA denotes the transmission time of data packet in DT.
During the \(T_{{O_{2} }}\) period, if the sender receives the CL-ACK, it deduces that the data packet is successfully delivered toward the destination in one hop and returns to execute the next packet transmission. If the sender does not receive the CL-ACK, it will start the retransmission of the data packet with updated backoff counter.
3.1.2 The operation of receiver
When a neighbor i of the sender receives the CL-RTS frame, it deduces that it may be a potential receiver in current hop. According to the sender and destination location piggybacked in CL-RTS, neighbor i will set up a timer T i to contend for the channel for transmitting the CL-CTS frame, which can be given by
where d s,dest and d i,dest denote the distance from sender to destination and from neighbor i to destination, respectively. T max is the maximal selection time and r radio is the transmission range. Since neighbor i is in the transmission range, then T i ∊ [0, T max ]. As shown in Fig. 3, neighbor j with d s,dest < d j,dest should not become a potential receiver in current hop, so, for reducing the network overhead, we can stipulate that these neighbors like j do not set up a timer for transmitting the CL-CTS frame. Formula (5) means that one neighbor providing the larger advance towards destination (defined in [39]) will has the smaller timer. Therefore, when one neighbor has the largest advance, it will terminate the timer and transmit the CL-CTS frame firstly.
To construct multiple cooperative links from which we can select the best one, it is necessary to let α potential receivers with superior advance transmit the CL-CTS frames. Therefore, let neighbor i start up a counter C i and initiate C i = α simultaneously with setting up the timer T i . Afterwards, whenever neighbor i receives one CL-CTS frame correctly and finds that its timer does not expire, it will set C i = C i − 1. If T i = 0 and C i ≠ 0 at a certain moment, which means that neighbor i is one of α potential receivers, neighbor i will transmit the CL-CTS frame and insert the current value of C i into the counter field of CL-CTS frame. Otherwise, if T i = 0 (or T i ≠ 0) and C i ≠ 0, which means that neighbor i is not one of α potential receivers, neighbor i will cancel the T i and does not transmit the CL-CTS frame.
Need to say, for successfully receiving the CL-CTS frame, it is necessary to address two issues:
-
1.
Collision detection and avoidance. Assume that there are three potential receiver nodes: p, q and w. Let T p = T q < T w and C p , C q , C w > 1. Therefore, nodes p and q will transmit the CL-CTS frames simultaneously prior to node w and collision is incurred at a certain moment. Due to the collision, node w can not receive the CL-CTS frame correctly, so it does not update the value of C w . Afterwards, the timer T w expires and node w transmits the CL-CTS frame. When nodes p and q receive the CL-CTS frames correctly, if they find that the value of counter field is not less than their own, they can deduce that the CL-CTS frames transmitted by them are collided (note that, the CL-CTS frame is short and not easy to cause error with basic transmission rate). If it does, they each randomly select backoff time-slot and retransmit the CL-CTS frame in their self-appointed slots. For reducing the overhead, we demand that each potential receiver can retransmit the CL-CTS frame at most once. Note here that, when nodes p and q transmit the CL-CTS frames, if C p = C q = 1, which means that nodes p and q are the last potential receives, nodes p and q can not detect the collision. In this case, nodes p and q are the potential receivers with the minimum advance, thus for reducing network overhead, we do not adopt other methods to let them retransmit the CL-CTS frames.
-
2.
Coverage radius improvement. In order to let all potential receivers successfully receive the CL-CTS frames from each other, we require that each CL-CTS frame is sent with a higher power to cover all potential receivers. Obviously, the key issue is to set up the value of transmission power. Here, we propose two methods to determine the value of power as follows:
Because all potential receivers are in the transmission range of the sender, each potential receiver can simply set up the value of power for covering the two times transmission range. Furthermore, considering that neighbor j with d s,dest < d j,dest should not become a potential receiver, each potential receiver can set up the value of power to let coverage radius be equal to r max , which is the maximum one of coverage radius to cover all potential receivers. As shown in Fig. 4, r max is the longest separated distance between two possible potential receivers p and q, which can be given by Formula (6). Clearly, in this method, the same value of power is set up to cover all potential receivers.
Since node location can affect its coverage radius, we can let each potential receiver compute its own coverage radius to set up the value of power, according to the sender, destination and its own location. As shown in Fig. 4, one potential receiver k can compute its own coverage radius r cov , which can be written as
where
where d k,s denotes the distance from node k to the sender. Note that, using the trigonometric function, r cov in Formula (7) can be converted to the function of d s,dest , d k,dest , d k,s and r radio . Evidently, in this method, each potential receiver can adjust its own value of power according to its own location. Since there is r cov < r max , this method can save power consumption compared with the previous method.
Assume that one potential receiver k is in the m-th transmission order, because it does not know the transmission type and rate of data packet, it makes a conservative reservation and sets the duration field of CL-CTS frame to be D CTS with the transmission rate of direct link, which can be expressed as
where δ = α − C k + 1 and \(T_{{CON_{1,\delta } }}\) is the contention time to transmit the CL-CTS frame for the remaining α − δ potential receivers. Since the CL-CTS frame is transmitted with a higher power, which can also improve interference range, we require that a node, which does not receive the CL-RTS frame but receives the CL-CTS frame not from its neighbors, does not set its network allocation vector (NAV) (defined in IEEE 802.11 standard) according to D CTS . Also, potential receiver k needs to initiate a timer \(T_{{O_{3} }}\) to wait for the arrival of CL-RTH frame, which can be given by
If one potential receiver receives the CL-RTH frame during the \(T_{{O_{3} }}\) period and discerns that the receiver ID piggybacked in CL-RTH is consistent with its own, it concludes that it is just the receiver of current hop. The receiver should broadcast a CL-ATR frame to keep the other node silent during the period of its packet reception. Therefore, according to the transmission type included in CL-RTH, it sets the duration field of CL-ATR frame to be D ATR , which can be written as
If the receiver receives successfully the data packet, it should send the ACK packet to the sender following a SIFS after the packet reception. Note that, for CT, the successful packet reception means that the receiver need apply MRC technique to combine the data packets transmitted by sender and relay. When the receiver receives the packet not destined to itself, it will act as the sender in the next hop.
3.1.3 The operation of relay
If a neighbor of the sender receives the CL-RTS and CL-CTS frames, it judges itself to a potential relay. Since there are multiple potential receivers (≤α), one potential relay h will receive multiple CL-CTS frames and construct multiple potential cooperative links. As for each cooperative link, h calculates its achievable performance according to the given metric. At the last, h selects one cooperative link, which has the maximum achievable performance among all potential cooperative links, to contend for the channel with the other potential relays. If h accesses the channel successfully, it becomes the best relay that can obtain the maximum achievable performance among all potential relays.
The best relay should broadcast a CL-RTH frame to declare that it is ready for the CT. As mentioned previously, the sender can also send a CL-RTH frame for the DT. Therefore, according to the transmission type, the duration field of CL-RTH frame can be set up as
Besides, for CT, the best relay should set a timer \(T_{{O_{4} }}\) to wait for the arrival of data packet transmitted by the sender in the first stage, which can be written as
When the best relay receives data packet, it inspects whether or not the relay address included in data packet header is consistent with its own. If it does, after a SIFS, the best relay forwards the received data packet to the receiver.
In the end, we can find out that the MACR-CCT protocol forms the procedure of CL-RTS/CL-CTS/CL-RTH/CL-ATR/DATA/CL-ACK packet exchanges at sender, relay and receiver nodes, and the other nodes set NAV accordingly, which is depicted in Fig. 5. Besides, for vividly describing the above mentioned operations, we depict them by flow charts in Fig. 6.
3.2 Relay selection
3.2.1 Performance metric
In MACR-CCT protocol, a key issue is to determine whether to use cooperative communication and which node is selected as the relay. The answer to both questions needs to investigate the performance gain brought by cooperative communication when a different relay is selected. For this purpose, we need to derive a metric, by which a relay can compute its throughput performance under the condition of transmission error. Since the transmission collision probability is the same in both cases of cooperative and direct transmissions, we assume that transmission failure is only caused by transmission error. Furthermore, according to [40], cooperative communication can result in enlarged interference area, which can decrease the cooperation gain. Therefore, considering there are multiple source–destination pairs in MWAN, MACR-CCT protocol should take interference mitigation into account to improve network throughput when selecting a relay node. To this end, the metrics for cooperative and direct transmissions, which are denoted by M CT and M DT , respectively, are given by
where L DATA denotes the payload length of data packet, T CT and T DT denote the total transmission time (including packet exchanges overhead in term of time) of a data packet for cooperative and direct transmissions, respectively, p c err and p d err are the frame error probability for cooperative and direct transmissions, respectively, and p r int is the transmission interference probability at relay node (including the interferences from and to other nodes) in CT. To compute M CT and M DT , we should compute the following parameters in (13) and (14):
-
1.
T CT and T DT . According to the packet exchanges in MACR-CCT protocol, we can derive
$$\begin{aligned} T_{CT} & = T_{RTS} + \alpha T_{CTS} + T_{RTH} + T_{ATR} + T_{DATA,1}^{CT} \\ +\, T_{DATA,2}^{CT} + T_{ACK} + (\alpha + 6)T_{SIFS} + T_{{CON_{1} }} + T_{{CON_{2} }} . \\ \end{aligned}$$(15)In (15), T CT DATA,1 = T PHDR + T MHDR + L DATA /R 1 and T CT DATA,2 = T PHDR + T MHDR + L DATA /R 2, where T PHDR and T MHDR denote the transmission durations for the PHY header and MAC header, respectively, R 1 and R 2 are the transmission rates for the first and second stages in CT, respectively. \(T_{{CON_{1} }}\) and \(T_{{CON_{2} }}\) will be introduced latter in Sect. 4. Similarly, we can derive the T DT as follow
$$\begin{aligned} T_{DT} & = T_{RTS} + \alpha T_{CTS} + T_{RTH} + T_{ATR} + T_{DATA}^{DT} \\ \quad +\, T_{ACK} + (\alpha + 6)T_{SIFS} + T_{{CON_{1} }} + T_{{CON_{2} }} , \\ \end{aligned}$$(16)where T DT DATA = T PHDR + T MHDR + L DATA /R 1.
-
2.
p c err and p d err . Suppose that the wireless channel is a Rayleigh fading channel with Gaussian noise, and bit errors are independent identically distributed over the whole frame. For simplicity, we also assume that the modulation BPSK is adopted. Since the error probability of the control packets can be ignored because of short length and low basic transmission rate, the transmission error probability can be approximated to be the error probability of the data packet. Let p e,sr denote the error probability of the received data packet at relay sent from sender, p e,sd denote the error probability of the received data packet at receiver sent from sender, and p e,ct denote the error probability of the received data packets combined at receiver in CT. We can derive
$$p_{err}^{c} = p_{e,sr} p_{e,sd} + (1 - p_{e,sr} )p_{e,ct} ,$$(17)where
$$\left\{ \begin{aligned} p_{e,sr} = 1 - (1 - p_{b,sr} )^{{L_{DATA} }} , \\ p_{e,sd} = 1 - (1 - p_{b,sd} )^{{L_{DATA} }} , \\ p_{e,ct} = 1 - (1 - p_{b,ct} )^{{L_{DATA} }} , \\ p_{b,sr} = Q(\sqrt {2\gamma_{sr} } ), \\ p_{b,sd} = Q(\sqrt {2\gamma_{sd} } ), \\ p_{b,ct} = Q(\sqrt {2\gamma_{ct} } ), \\ \end{aligned} \right.$$where p b,sr , p b,sd and p b,ct are the corresponding bit error probability (BER) of p e,sr , p e,sd and p e,ct , respectively, γ sr is the signal to noise ratio (SNR) of received signal at relay sent from sender, γ sd is the SNR of received signal at receiver sent from sender, andγ ct = γ sd + γ rd is the SNR of combined signal at receiver sent from sender and relay, in which γ rd is the SNR of received signal at receiver sent from relay. According to [41], \(Q(x) = \frac{1}{{\sqrt {2\pi } }}\int_{x}^{\infty } e xp( - \frac{{t^{2} }}{2})dt\) is gauss error function. In the same manner, we can also derive
$$p_{err}^{d} = 1 - (1 - p_{b,sd} )^{{L_{DATA} }} .$$(18) -
3.
p r int . In MACR-CCT, it is required that the sender must monitor the radio channel for signs of activity before transmitting a packet. If any activity is detected, transmission is deferred. This is known as carrier sensing mechanism adopted in IEEE 802.11 protocol. If the two senders are within the carrier sense range of each other, then only one of them will transmit at a time. Otherwise, their transmissions are interfered with each other. For a node, let T P denote the measurement period, T b denote the channel busy period sensed by the node, and T t denote the transmission period of its own, then, T b /T p represents the probability of interference from the other transmission in carrier sense range, and T t /T p represents the probability of interference to the other transmission in carrier sense range. Therefore, we have
$$p_{int}^{r} = \frac{{T_{b} + T_{t} }}{{T_{p} }}.$$(19)Using (19), a relay node can estimate the interferences from and to other nodes and derive p r int .
3.2.2 Channel access to relay
Since there are multiple relays, we should select the best one, which has the maximum achievable performance, to access the channel for sending the CL-RTH frame. Here, inspired by the idea of black-burst contention [42], we propose an efficient mechanism to provide deterministically selection for the best relay. Specifically, for a contention relay, after waiting for the channel to be idle for a SIFS, instead of further waiting for the channel to be idle for a duration of backoff time, the relay will send a busy tone, and the length of the busy tone (in the unit of slot time) is equal to
where M i CT (i = 1, 2, … α) denotes the value M CT of ith cooperative link for one relay, M i DT denotes the value M DT of ith direct link for the sender, S ref is the referenced throughput used to convert M CT or M DT into an integral number of busy tone, and \(\left\lfloor x \right\rfloor\) is the floor of x, i.e., the largest integer not larger than x. When one relay completes its own busy tone, the relay monitors the channel for the duration of a SIFS. If the channel is still busy (which means that at least one other relay is sending busy tone), the relay will quit the current contention and wait for the channel to be idle again. Otherwise, the relay, which sends the longest busy tone and achieves the maximal performance gain, will send its CL-RTH frame. Note that if only one relay (i.e., the best relay) sends the CL-RTH frame, the relay will receive the CL-ATR frame transmitted by the receiver after the duration of T RTH + T SIFS . Otherwise, if two or more relays happen to send the same longest busy tone, a collision occurs and these relays can not receive the CL-ATR frame. For the next contention, these relays choose a backoff timer randomly from their contention windows.
4 Analysis model
In this section, we give analysis for the throughput of MACR-CCT protocol on an err-prone wireless channel. IEEE 802.11 is widely used in ad hoc networks, and most existing cooperative MAC mechanisms [4–8] are designed based on IEEE 802.11. Therefore, for simplicity and performance comparison, we take IEEE 802.11b physical layer specifications as the basis of the analytical model. In addition, we consider a multi-rate network scenario with N flows and M potential relays, in which there are four different transmission rates, i.e., 1, 2, 5.5 and 11 Mbps, and each rate has the corresponding minimum required SNR.
Considering the Rayleigh fading channel, the received SNR γ at distance d has the following distribution:
where θ g (d) is the expectation of the received SNR at distance d. Let θ 2, θ 5.5 and θ 11 denote the minimum required SNR to support transmission rate 2, 5.5 and 11 Mbps, respectively. Let r denote the transmission rate determined by each sender or relay. According to (21), we have
For simplicity, we analyze the saturation throughput based on Bianchi’s model [43] by assuming each source node always has data to transmit. Let τ denote the transmission probability of each sender in an expected slot, we have
where CW min is the minimum contention window, m is the maximum backoff stage, and p u is the transmission failure probability given by
where p err is the average frame error probability, p col is the frame collision probability. MACR-CCT protocol does not require that the sender receives all of α CL-CTS frames after the CL-RTS frame transmission, this means that frame collision does not happen when the sender receives a CL-CTS frame from one potential receiver. Therefore, we can write p col as
By solving the set of nonlinear Eqs. (23)–(25), we can obtain τ and p col . Let p tr be the probability that there is at least one transmission in the considered slot time:
Let P s be the probability that a successful transmission occurs conditioned on the fact that at least one station transmits, we have
To this end, the normalized saturation throughput S can be expressed as
where σ, T s and T c denote the duration of an idle slot, the average duration of a successful transmission and the average duration of a frame collision, respectively.
To compute S, we should obtain T c , T s and p err as follows:
Since there are four rate available: 1, 2, 5.5 and 11 Mbps in which the basic rate 1 Mbps is used for control frames, PLCP header and MAC sub-header, we can derive the average transmission time T avg for a packet as follow:
where T oh = T PHDR + T MHDR , r d is the transmission rate of direct link. For a relay node, there are α potential cooperative links to choose, therefore, in (30), P x,y = αP(r 1 = xMbps, r 2 = yMbps) in which r 1 and r 2 are the transmission rates for the first and second stages in CT, respectively. According to [6], we also have P x,y = αP(r 1 = xMbps)P(r 2 = yMbps) (x = 11, 5.5 and y = 11, 5.5).
Therefore, according to the packet exchanges in MACR-CCT protocol, T s can be expressed as
where T CON2 can be expressed as
In (32), MB = max{L BT } and W is the constant contention window. On the right hand of (32), the first term represents the duration used for busy tone if only one relay or the sender chooses the maximum length i of busy tone, and others choose the value less than i. The second term represents the duration used for busy tone and backoff if at least two nodes (including relays and sender) choose the maximum length i of busy tone, and others choose the value less than i. In this case, collision can happen and these relays choose a backoff timer randomly from its constant contention window (for simplicity, we consider collision happens only once). Here, T s is mainly determined by T avg , and we can easily derive (T avg |α > 1 − T avg |α = 1) < 0. Therefore, it means that the relay select scheme in MACR-CCT protocol can achieve the better performance gain.
In (31), \(T_{{CON_{1} }} = max\{ T_{i} \} + \frac{W}{2}\sigma\) (i = 1, 2, … α and as above, we consider collision happens at most once). Being conservative, we can set \(T_{{CON_{1} }} = T_{max} + \frac{W}{2}\sigma\). Also, if we suppose that neighbors of the sender are uniformly distributed in coverage range of the sender, which means that E(T i ) = T max /2, we can set \(T_{{CON_{1} }} = 0.5\beta T_{max} + \frac{W}{2}\sigma\) (1 ≤ β < 2).
Because the frame error probability and transmission rate are dependent on the SNR, we can derive p eer as the weighted sum of the corresponding frame error probabilities in the four transmission rates as follow:
where p c err (x, y) (x = 11, 5.5 and y = 11, 5.5) is p c err in (17) with the cooperative transmission rates xMbps and yMbps for the first and second stages, respectively, and p d err (x) is p d err in (18) with direct transmission rate xMbps.
Since the received SNR is dependent on the distance from sender, it is difficult to obtain the exact values of γ sd , γ sr and γ rd in (32) and (33) for solving (28). Therefore, we will analyze the throughput performance under the given various values of γ sd , γ sr and γ rd .
Equation (28) indicates throughput expression in single hop instance. Under multi-hop instance, the same condition will be considered more than once. So the average end-to-end throughput S sys under multi-hop instance will be:
where h (≥ 2) denotes the hop counts from source to destination, τ i denotes the transmission probability of the ith hop that can be derived from Eq. (23). Therefore, given various values of γ sd , γ sr and γ rd , we can derive the average end-to-end throughput under different hop counts. In addition, according to S sys , we can also derive the average end-to-end delay D sys = L DATA /S sys .
5 Simulation results and analysis
In this section, we validate our analysis and evaluate the performance of MACR-CCT using NS-2 simulator [44]. The parameters used in our simulation are listed in Table 1. First, we use link throughput as the performance metrics to validate the analytical model compared with simulation results. After that, we use end-to-end throughput and end-to-end delay to validate the analytical model under multi-hop instance. At the last, we use system throughput, hop counts and end-to-end delay as performance metrics to evaluate MACR-CCT protocol compared with the existing protocols. As for the existing protocols, we consider the following three cases:
-
1.
Non-cooperative path and non-cooperative MAC. In this case, we adopt IEEE 802.11b DCF protocol at the MAC layer and AODV protocol at the routing layer. This case is set to observe whether MACR-CCT protocol can obtain performance gain compared with the traditional non-cooperative transmission.
-
2.
Non-cooperative path and cooperative MAC. In this case, we adopt the well-known CoopMAC protocol at the MAC layer and AODV protocol at the routing layer. This case is set to observe whether MACR-CCT protocol can obtain performance gain by taking advantage of cooperative diversity both at MAC and routing layers. Note here, that we do not consider the mentioned cooperative routing protocols in Sect. 2 as comparison target, because most of the existing cooperative protocols take account into energy-efficient as design objective, so that it is not easy to give accurate comparison. Although TOCR protocol [19] is designed to optimize throughput, it does not consider multiple rates network scenario.
-
3.
Cooperative diversity both at MAC and routing layers. In this case, we consider RECOMAC protocol [32] as comparison target. This case is set to observe whether MACR-CCT protocol can obtain the same performance gain with RECOMAC protocol only by selecting the best relay not all relays in a cooperative set.
5.1 Model validation
To demonstrate the effectiveness of MACR-CCT and compare with the well-known CoopMAC protocol, in the following simulations, we set R sr = R rd = 2 Mb/s and R sd = 1 Mb/s, where R sr , R rd denote the transmission rates between sender and relay, relay and receiver, and R sd denotes the direct transmission rate. In the first simulation, we investigate the performance improvement of our proposed MACR-CCT protocol under various channel conditions. Assume there are 10 contending nodes and 5 potential relays, γ sd is fixed to 7 dB, the data frame length is set to 1000 B and α is set to 1. We let γ sr = γ rd and vary γ sr (γ rd ) from 7 to 16 dB. In Fig. 7(a), we can see that the analytical results and simulation results match very well. When γ sr (γ rd ) is higher than 7.8 dB, the throughput of MACR-CCT is improved obviously. In contrast, the throughput of CoopMAC is independent of γ sr (γ rd ). The reason is that MACR-CCT considers the overhead caused by transmission error while deciding to adopt cooperative transmission or not, but CoopMAC does not consider. For example, we assume that transmission error probability is 0.25 in direct transmission mode and 0.1 in cooperative transmission mode. Then, the throughput in direct transmission mode is R sd * (1 − 0.25) = 0.75 Mb/s, but the throughput in cooperative transmission mode is (1/R sr + 1/R rd ) * (1 - 0.1) = 0.9 Mb/s. Obviously, in this case, cooperative transmission will be selected. However, when we ignore the transmission error, the direct transmission will be adopted because cooperative transmission can not compensate the additional overhead caused by cooperation. From Fig. 7(a), we can also see that when γ sr (γ rd ) is lower than 7.8 dB, MACR-CCT and CoopMAC have very closer performance. The reason is that in this situation both protocols use direct transmission mode. Next, we change γ sd from 7 to 16 dB and fix γ sr (γ rd ) to 15 dB. It is shown in Fig. 7(b) that MACR-CCT outperforms CoopMAC in throughput when γ sd is lower than 10 dB. The main reason is that due to the remarkable transmission error of direct link in this situation, MACR-CCT can choose cooperative transmission, but CoopMAC does not. However, when γ sd is lower than 10 dB, the throughput of CoopMAC is improved significantly. The reason is that when the channel condition of direct link is improved, transmission error is decreased significantly. In Fig. 7(b), when γ sd is higher than 10 dB, both MACR-CCT and CoopMAC protocols adopt direct transmission and have similar performance.
In the second simulation, we investigate the performance improvement of our proposed MACR-CCT protocol for various number of contending nodes. We consider γ sr = γ rd = 15 dB, γ sd = 7 dB, the data frame length is set to 1000 B and α is set to 1. We vary the number of contending nodes from 2 to 32. We can see from Fig. 8 that the throughput of both protocols decreases with the number of contending nodes. The reason is that the more number of nodes contend for transmission, the higher collision probability occurs.
In the third simulation, we investigate the performance improvement of our proposed MACR-CCT protocol for various number of potential relay nodes. Let the data frame length be set to 1000 B and α be set to 1. Besides, we set γ sd = 7 dB and fix R sd = 1 Mb/s. We randomly place some potential relay nodes (from 2 to 10) in the transmission range of sender and receiver. So, in this situation, the transmission rates of potential relay nodes are not fixed and decided by their channel conditions. Figure 9 shows the average throughput of MACR-CCT, CoopMAC and direct transmission protocol (such as IEEE 802.11). Because MACR-CCT takes into account the transmission channel error, more cooperation opportunities are caught. In contrast, CoopMAC misses some cooperation opportunities.
In the fourth simulation, we investigate the performance improvement of our proposed MACR-CCT protocol for various data frame length. Let γ sr = γ rd = 15 dB, γ sd = 7 dB, α = 1 and vary the data frame length from 500B to 5000B. In Fig. 10(a), we can see that the throughput of our proposed MACR-CCT protocol increases with the data frame length. For the main reason, there is almost no transmission error due to the good relay channel provided by cooperation, and thus, the longer the data frame length, the better the performance. Furthermore, with the longer data frame length, the proportion of cooperation overhead in total transmission time becomes lower, and thus, the impact of cooperation overhead on the performance is decreased so that the performance is improved. In contrast, owing to missing some cooperation opportunities and not good direct channel condition, the performance of CoopMAC is decreased when the data length is longer than 1200 B. The reason is that the transmission error probability of CoopMAC increases with the data frame length.
In order to investigate the relationship between optimal data frame length and γ sd , we set γ sr = γ rd = 15 dB and vary γ sd from 7 to 16. In Fig. 10(b), we can see that when γ sd < 11 dB, the optimal data frame length of CoopMAC increases with γ sd , but it keeps the fixed maximum value in MACR-CCT. The reason is that when γ sd < 11 dB, CoopMAC chooses direct transmission mode, but MACR-CCT chooses cooperative transmission mode. When γ sd ≥ 11 dB, the direct channel condition is good enough, and thus, both of the two cooperative protocols adopt direct transmission mode and choose the same value as the optimal data frame length.
In the fifth simulation, we investigate the performance improvement of our proposed MACR-CCT protocol for various α. We set γ sr = γ rd = 15 dB and γ sd = 4, 6, 8 dB. It is shown in Fig. 11 that there exists an optimal α to maximize the throughput under different γ sd , and the optimal α is decreased with γ sd . For example, when γ sd = 4 dB, the optimal α is equal to 4, but when γ sd = 8 dB, the optimal α is equal to 1. It means that when direct channel condition becomes better, MACR-CCT adopts direct transmission mode and does not need more potential cooperation links for reducing cooperation overhead. We can also see from Fig. 11 that the throughput of MACR-CCT decreases with α. The reason is that the larger the value of α, the more cooperation overhead, and then, the throughput is decreased.
In the sixth simulation, we investigate the performance of MACR-CCT protocol and validate the analytical model under multi-hop instance. We let L DATA = 1000B, γ sd = 7 dB and α = 1. From Fig. 12, we can see that the analytical results and simulation results match very well. As the hop count increases, the average end-to-end throughput decreases and the average end-to-end delay increases. This is because that a longer route from the source node to the destination node results in more packets dropped and retransmission.
5.2 Performance evaluation
In this section, we use throughput, end-to-end delay and hop counts as performance metrics to evaluate MACR-CCT protocol in comparison to RECOMAC protocol and layered architecture employing AODV protocol at routing layer and IEEE 802.11 (denoted as AODV + 802.11), CoopMAC protocols at the MAC (denoted as AODV + CoopMAC), respectively. We consider that all nodes are uniformly distributed in a square area of 600 m × 600 m, and a source–destination pair is randomly selected. In simulations, source node always transmits data packets to the destination node. The results are averaged over 500 simulation runs. Besides, the data frame length is set to 1000 B.
In Fig. 13(a), we investigate the system throughput of MACR-CCT, RECOMAC, AODV + 802.11 and AODV + CoopMAC under the scenario of five flows coexisting. It is observed that the throughput of AODV + 802.11 improves with node density, which is owing to the fact that higher node density leads to higher likelihood of establishing a better path between source and destination. Besides, we can also see from Fig. 13(a) that the throughput of MACR-CCT and AODV + CoopMAC also improves with node density and is much better than that of AODV + 802.11, which can be attributed to the benefits of cooperation. In comparison to AODV + CoopMAC, MACR-CCT improves the throughput performance more significantly, which is due to the fact that MACR-CCT considers transmission channel error and interference mitigation while choosing cooperative transmission mode. From Fig. 13(a), we can also find that MACR-CCT and RECOMAC protocols have the similar throughput performance. Because RECOMAC protocol adopts cooperative flooding strategies to select relay nodes, when the network size is a little smaller, i.e., the number of nodes is smaller than 100, RECOMAC protocol can find more relay nodes, and thus, the throughput performance of RECOMAC is better than MACR-CCT. However, RECOMAC protocol requires all relays in a cooperative set to execute cooperative transmission, instead of selecting the best relay, which results in larger transmission interference range. Indeed, as the network size increases, which means that MACR-CCT protocol can find more potential relays and select the best one, the throughput performance of RECOMAC is worse than MACR-CCT, owing to the larger interference range of RECOMAC protocol.
Furthermore, in Fig. 13(b), we depict the system throughput for various number of data flows with 100 nodes. We can see that because the inter-flow interference increases with number of data flows, the system throughput decreases after the number of flows reaches one certain value. As comparison, MACR-CCT can keep a better throughput performance, which is owing to the fact that it takes interference mitigation into consideration.
In Fig. 14, we investigate the average number of total hops between source and destination. It is observed that AODV + 802.11 and AODV + CoopMAC have the almost same number of total hops, which is due to the fact that they use thesame routing protocol to find a better path from source to destination. However, MACR-CCT can provide the smaller number of total hops. The primary reason is that MACR-CCT can choose a receiver of one hop closer to the destination. MACR-CCT and RECOMAC protocols have the similar number of total hops. In addition, because of cooperative flooding strategies, RECOMAC has the smallest number of total hops when the network size is small.
In Fig. 15, we investigate the average end-to-end delay per delivered packet. It can be seen that MACR-CCT improves the delay performance significantly, because it takes smaller number of hops to reach the destination, and reduces number of retransmission caused by channel error and multi-flow interference. As the network size increases, RECOMAC undergoes larger delay than MACR-CCT, which is ascribed to the extended interference range. Compared with AODV + 802.11, AODV + CoopMAC obtains the better delay performance, which is due to the benefits of cooperation at MAC layer.
6 Conclusions
In this paper, a novel cross-layer cooperative transmission (MACR-CCT) protocol combining the MAC and routing layers for multi-hop wireless ad hoc networks is proposed.
Different from existing protocols, MACR-CCT can determine cooperative relay and receiver in one hop jointly to exploit fully cooperative diversity. Through careful protocol design, our proposed MACR-CCT can choose the most suitable relay and receiver in one hop, and thus alleviating the transmission error and the impact of inter-flow interference. In addition, the saturation throughput of MACR-CCT based on an analytical model is also derived. Finally, extensive simulation results show that our proposed analytical model is effectiveness and MACR-CCT significantly improves the performance of throughput and delay under the multi-hop multi-source network scenario, as compared to layered architecture employing AODV protocol at routing layer and IEEE 802.11 (or CoopMAC) at MAC layer.
References
Meng, T., Wu, F., Yang, Z., Chen, G., & Vasilakos, A. V. (2015). Spatial reusability-aware routing in multi-hop wireless networks. IEEE Transactions on Computers, 65(1), 244–255.
Zhang, X., Zhang, Y., Yan, F., & Vasilakos, A. V. (2015). Interference-based topology control algorithm for delay-constrained mobile ad hoc networks. IEEE Transactions on Mobile Computing, 14(4), 742–754.
Duarte, P. B. F., Fadlullah, Z. M., Vasilakos, A. V., & Kato, N. (2012). On the partially overlapped channel assignment on wireless mesh network backbone: a game theoretic approach. IEEE Journal on Selected Areas in Communications, 30(1), 119–127.
Liu, P., Tao, Z., Narayanan, S., et al. (2007). CoopMAC: A cooperative MAC for wireless LANs. IEEE Journal on Select Areas Communication, 25(2), 340–354.
Zhu, H., & Cao, G. (2006). rDCF: A relay-enabled medium access control protocol for wireless ad hoc networks. IEEE Transactions on Mobile Computer, 5(9), 1201–1214.
Guo, T., & Carrasco, R. (2009). CRBAR: cooperative relay-based auto rate MAC for multirate wireless networks. IEEE Transactions on Wireless Communications, 8(12), 5938–5947.
Shan, H., Cheng, H. T., & Zhuang, W. (2011). Cross-layer cooperative MAC protocol in distributed wireless networks. IEEE Transactions on Wireless Communications, 10(8), 2603–2615.
Cao, B., Feng, G., Li, Y., et al. (2014). Cooperative media access control with optimal relay selection in error-prone wireless networks. IEEE Transactions on Vehicular Technology, 63(1), 252–265.
Moh, S., & Yu, C. (2011). A cooperative diversity-based robust MAC protocol in wireless ad hoc networks. IEEE Transactions on Parallel and Distributed Systems, 22(3), 353–363.
He, X., & Li, F. Y. (2011). Cooperative MAC design in multi-hop wireless networks: Part I: When source and destination are within the transmission range of each other. Wireless Personal Communications, 57(3), 339–350.
Ahmed, M. H. U., Razzaque, M. A., & Hong, C. S. (2013). DEC-MAC: delay- and energy-aware cooperative medium access control protocol for wireless sensor networks. Annals of Telecommunications, 68(9), 485–501.
Wang, X., & Li, J. (2015). Improving the network lifetime of MANETs through cooperative MAC protocol design. IEEE Transactions on Parallel and Distributed Systems, 26(4), 1010–1020.
Zhang, X., Guo, L., Wei, X., et al. (2013). An energy-balanced cooperative MAC protocol based on opportunistic relaying in MANETs. Computers & Electrical Engineering, 39(6), 1894–1904.
Zhou, Y., Liu, J., & Zheng, L. (2011). Link-utility based cooperative MAC protocol for wireless multi-hop networks. IEEE Transactions on Wireless Communications, 10(3), 995–1005.
Liu, K., Chang, X., Liu, F., et al. (2015). A cooperative MAC protocol with rapid relay selection for wireless ad hoc networks. Computer Networks, 91, 262–282.
Khandani, A. E., Abounadi, J., Modiano, E., & Zhendg, L. (2003). Cooperative routing in wireless networks. In 41th Allerton confcrencc on communications, control and computing, pp. 1270–1279.
Khandani, A. E., Abounadi, J., Modiano, E., et al. (2007). Cooperative routing in static wireless networks. IEEE Transactions on Communications, 55(11), 2185–2192.
Ibrahim, A., Zhu, H., & Liu, K. J. R. (2008). Distributed energy-efficient cooperative routing in wireless networks. IEEE Transaction on Wireless Communications, 7(10), 3930–3941.
Wang, L., & Liu, K. (2009). An throughput-optimized cooperative routing protocol in ad hoc network. In Proceedings of the 3rd IEEE international symposium on Microwave, Antenna, Propagation/EMC technology wireless communication, pp. 1255–1258.
Chen, S., Huang, M., & Li, Y., Zhu, Y., & Wang, Y. (2012). Energy-balanced cooperative routing in multihop wireless ad hoc networks. In IEEE international conference on communications (ICC’12), pp. 307–311.
Lakshmanan, S., & Sivakumar, R. (2013). Proteus: Multi-flow diversity routing for wireless networks with cooperative transmissions. IEEE Transactions on Mobile Computing, 12(6), 1146–1159.
Li, F., Wu, K., & Lippman, A. (2006). Energy-efficient cooperative routing in multi-hop wireless ad hoc Networks. In IPCCC, 2006, 215–222.
Sheng, Z., Ding, Z., & Leung, K. K. (2009). Distributed and power efficient routing in wireless cooperative networks. In IEEE international conference on communications (ICC’09), pp. 1–5.
Guan, Y., Xiao, Y., Shen, C. C., & Cimini, L. (2011). CSR: Cooperative source routing using virtual MISO in wireless ad hoc networks. In IEEE wireless communications and networking conference (WCNC), pp. 1119–1124.
Zhang, J., & Zhang, Q. (2008). Cooperative routing in multi-source multi-destination multi-hop wireless networks. In 27th IEEE conference on computer communications (INFOCOM’08), pp. 2369–2377.
Sharma, S., Shi, Y., Hou, Y. T., et al. (2012). Joint flow routing and relay node assignment in cooperative multi-hop networks. IEEE Journal on Selected Areas in Communications, 30(2), 254–262.
Li, P., Guo, S., Yu, S., & Vasilakos, A. V. (2014). Reliable multicast with pipelined network coding using opportunistic feeding and routing. IEEE Transactions on Parallel and Distributed Systems, 25(12), 3264–3273.
Jakllari, G., Krishnamurthy, S. V., & Faloutsos, M. (2007). A cross-layer framework for exploiting virtual MISO links in mobile ad hoc networks. IEEE Transactions on Mobile Computing, 6, 579–594.
Babaee, R., & Beaulieu, N. C. (2010). Cross-layer design for multihop wireless relaying networks. IEEE Transaction on Wireless Communications, 9(11), 3522–3531.
Aguilar, T., Syue, S. J., & Gauthier, V. (2011). CoopGeo: A beaconless geographic cross-layer protocol for cooperative wireless ad hoc networks. IEEE Transaction on Wireless Communications, 10(8), 2554–2565.
He, X., & Li, F. Y. (2012). Metric-based cooperative routing in multihop ad hoc networks. Journal of Computer Networks and Communications, 2012, 1–12. doi:10.1155/2012/893867.
Gokturk, M. S., Gurbuz, O., & Erkip, E. (2013). A cross-layer multi-hop cooperative network architecture for wireless ad hoc networks. Computer Networks, 57(18), 4010–4029.
Bletsas, A., Khisti, A., Reed, D. P., et al. (2006). A simple cooperative diversity method based on network path selection. IEEE Journal on Selected Areas in Communications, 24(3), 659–672.
Zhu, Y., & Zheng, H. (2008). Understanding the impact of interference on collaborative relays. IEEE Transactions on Mobile Computing, 7(6), 724–736.
Mauve, M., Widmer, J., & Hartenstein, H. (2001). A survey on position based routing in mobile ad-hoc networks. IEEE Network Magazine, 15(6), 30–39.
Karp, B., & Kung, H. (2000). Gpsr: Greedy perimeter stateless routing for wireless networks. In ACM MOBICOM’00, pp. 243–254.
Zeng, K., Yang, Z., & Lou, W. (2008). Location-aided opportunistic forwarding in multirate and multihop wireless networks. IEEE Transactions on Vehicular Technology, 58(6), 3032–3040.
IEEE Std. 802.11. (1999). IEEE standard for wireless LAN medium access control (MAC) and physical layer (PHY) specifications.
Melodia, T., Pompili, D., & Akyildiz, I. F. (2004). Optimal local topology knowledge for energy efficient geographical routing in sensor networks. In 23th IEEE conference on computer communications (INFOCOM’04), pp. 1705–1716.
Zhou, Y., & Zhuang, W. (2013). Beneficial cooperation ratio in multi-hop wireless ad hoc networks. In IEEE INFOCOM 2013, pp. 250–254
Li, Y., Zhu, X., Liao, C., & Daneshmand, M. (2013). Relay selection considering MAC overhead and collision in wireless networks. In IEEE wireless communications and networking conference, pp. 1592–1596.
Sobrinho, J. L., & Krishnakumar, A. S. (1999). Quality of service in ad hoc carrier sense multiple access wireless networks. IEEE Journal on Selected Areas Communications, 17(8), 1353–1368.
Bianchi, G. (2000). Performance analysis of the IEEE 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications, 18(3), 535–547.
Fall, K., & Varadhan, K. (2011). The NS manual. http://www.isi.edu/nsnam/ns/doc/index.html.
Song, Y., Zhu, X., Fang, Y., & Zhang, H. (2010). Threshold optimization for rate adaptation algorithms in IEEE 802.11 WLANs. IEEE Transaction on Wireless Communications, 9(1), 318–327.
Acknowledgments
This work is funded by China Postdoctoral Science Foundation (Grant No. 2014M561627), Natural Science Foundation of Anhui Province (Grant Nos. 1308085MF101 and 1408085MF130), and Natural Science Foundation of Anhui Higher Education Institutions (Grant Nos. KJ2014A172 and KJ2013A229)
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Wu, Q., Zhou, X. & Ge, F. A cross-layer protocol for exploiting cooperative diversity in multi-hop wireless ad hoc networks. Wireless Netw 23, 1591–1610 (2017). https://doi.org/10.1007/s11276-016-1238-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-016-1238-7