Abstract
Although the researchers have proposed many arbitrator quantum signature (AQS) for various applications in practice, the security proof of most AQSs was not strictly presented. Many results have shown that the AQS schemes without strict security proof may be broken by various measurement and forgery attacks. Therefore, a secure AQS should strictly put its security on the quantum theorems and principles. Based on the non-orthogonal entangled-triple sequence, an AQS with provable security is proposed. First, the theoretical security proof of our AQS is presented. Second, we prove the non-cloning theorem for the entangled-triple sequence. Third, by using the non-cloning property of the entangled-triple particle, we prove the new AQS signature cannot be forged. At last, the non-repudiation of the proposed AQS is analyzed. We showed that if an adversary can break the signature, his/her actions will violate some quantum principles. The security proof of the proposed signature scheme also shows the idea of provable security for a quantum signature. On the other hand, in the proposed scheme, the partners need not perform the probabilistic quantum state comparison test. It has better qubit efficiency. Therefore, compared with the other similar schemes, ours has the better merits in security and efficiency.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Now, the world is a digital word. Every day, many digital messages are exchanged by the internet. And most often, the transmitted messages have to be authenticated by the message receivers. That is, the receivers need to check where the messages come from, and whether they have been eavesdropped or disturbed by an adversary before receiving them. To address the need of authenticating digital messages, Diffie et al. [1] proposed the idea of digital signature. Generally, in a digital signature system, the signatory creates his/her signature by encrypting the message with some secret key, and the signature receiver can verifies its validity with the public key of the signer. By the digital signature technologies, one can efficiently authenticate the received digital messages.
Since the introduction of the digital signature, the researchers proposed many different classical signature schemes for the applications in different environments [2,3,4,5,6]. However, the security of all these classical digital signatures is heavily dependent on the mathematic computation problems [7, 8], which may be efficiently solved with the help of the modern quantum computer [9,10,11,12].
To make the digital signature be secure against the quantum computer, Gottesman and Chuang [13] introduced the concept of quantum digital signature, whose security was found on some physical theorems and quantum properties of the particles instead of the unproved mathematical assumptions. Therefore, the quantum signature has the good merit of physical security. Based on the work in [13], many novel quantum signature schemes were proposed [14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47]. In the schemes [13, 40,41,42], the signers’ signing keys and public keys can only be used one time. To make the quantum signature more secure and practical, Zeng and Christoph developed the AQS [14], in which the signing key can be reused. In the AQS, an arbitrator, which is a party trusted by all participants, is introduced. The arbitrator takes part in the key generation phase so that the participants can share some private keys, which are used to sign and verify a message. During the signature verification phase, the arbitrator can securely help the signature verifier verify the quantum signature. What is more, the arbitrator is very helpful in solving the disputations between the signer and the verifier. Therefore, compared with the quantum signature in [13, 40,41,42], Zeng and Christoph’s AQS was more efficient and practicable. Based on the Zeng et al.’s idea, many AQSs schemes [15,16,17,18,19,20,21, 23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39, 43,44,45,46,47,48,49,50,51] were proposed. For example, Yang et al. presented the weak arbitrator-based AQSs [15, 16, 44, 45] so as to improve the security of the AQS scheme. Jiang’s AQS [17] was based on the product states with local indistinguishability so that the AQS could be more practicable. Although there were lots of AQSs, their security was not strictly proved. That is, there was not strictly proof to support the security of the proposed AQS schemes. In fact, many AQS schemes have been proven to be insecure against various attacks duo to two main reasons as follows.
First, according to Kerckhofs’s principle, the security of the modern cryptography systems should depend on the secrecy of the users’ private keys rather than the cryptography algorithm. Especially, in a signing system, if the signer’s private key is broken, anyone can produce the forgery of the quantum signature by using the broken key. Generally, in an AQS scheme, the signer’s private key is created by performing the unconditionally secure quantum key distribution protocol (e.g., BB84 Protocol [52]) such that the private key cannot be broken during the key generation phase of the scheme. However, it should be noted that in a quantum signature scheme, the signature is generated by performing the quantum encryption with the signer’s private key. Therefore, the quantum signature also includes the information of the private key. To guarantee the security of the private key, the quantum signature ciphertext should be information-theoretically secure [53,54,55]. That is, the quantum signature should be theoretically indistinguishable such that the adversary cannot derive any useful information about the private key from the quantum signature. However, the information-theoretical security of most existing quantum signature schemes cannot be strictly proved. This means that for these schemes, the adversaries may get some information about the private keys by performing some measurement attacks or other unknown attacks to the quantum signatures. For example, in 2019, Chen et al. [56] proved the private keys of the quantum signature systems based on quantum one-time pad (QOTP) [57] could be broken by performing the controlled SWAP attack. This means the adversary can get some information about the private keys of the signers in the QOTP-based quantum signature systems (e.g., [14, 25,26,27,28, 36, 39, 43]) by the controlled SWAP attack. Therefore, the quantum signature ciphertext should be theoretically indistinguishable and the quantum signature scheme should be information-theoretically secure.
Second, can a quantum signature with unconditionally secure signing key (private key) be secure against forgery? The answer is no due to much strong proof. For example, under the man-in-the-middle attack, Luo’s AQS [16] can be forged [22]. Although Jiang presented some security analysis in [17], his AQS can still be forged by a quantum adversary [23]. In [29], Zhou et al. showed that the quantum signature in [30] could be forged by adaptively performing some Hadamard gates on the signed message without knowing the private key of the signer. Similarly, Ding et al. [31] demonstrated that the quantum signature in [32] was not secure, because the signature receiver could generate a forgery by adaptively performing NOT gate to the received signature without knowing the signer’s private key as well. He et al. [33] proved that in [34], the adversary could create a forgery by performing the NOT and Hadamard operators on the received signature, because he/she knew the structure of the original message. Gao et al.’s research results showed that some AQS schemes using Pauli operators were insecure against the participant’s forgery [24]. Some other results [35,36,37,38] also showed various forgery attacks to the quantum signatures [36, 48,49,50,51] without knowing the signers’ private keys. Why many quantum signatures can be forged? In fact, in these quantum signature schemes, there are two common features. First, in these schemes, the authors analyzed that their quantum signatures were secure against forgery because the forger could not master the private keys. Then, this kind of security analysis is not comprehensive, because many quantum signatures with unconditionally secure private keys can still be forged. On the other hand, their security against forgery cannot be proved with strict formal mathematical proof. No formal proof can sufficiently support that the unforgeability of these quantum signatures strictly depends on the basic principles of the quantum mechanics such as the non-cloning theorem and the theoretical indistinguishability of the quantum states. How can we guarantee the security of a quantum signature such that its unforgeability is strictly dependent on the basic principles of the quantum mechanics? A general idea is that the unforgeability of the quantum signature should be proved with the strict proof based on the principles of the quantum mechanics. That is, we should mathematically prove that if an adversary can generate a forgery for the quantum signature, his/her actions will violate some quantum principles. This is the idea of provable security for a quantum signature.
In this paper, the main contribution is that we propose the first provably secure AQS with strictly security proof. Different from most of the AQSs, the proposed scheme can be proved to be information-theoretically secure, and its security against forgery can be proved under the basic principle of quantum mechanics as well. In this ASQ, the signature is produced with the controlled particles such that the signed particles have the same states, which can be used to prove the theoretical indistinguishability of the proposed AQS. Thus, the secrecy of the signatory’s private key can be proved. On the other hand, we prove that the unforgeability of the proposed AQS with the non-cloning principle. That is, for the proposed scheme, if an adversary can produce a forgery of the signature, his/her actions will violate the non-cloning principle. This means it is impossible for the adversary to generate a forgery for our signature under the basic principle of quantum mechanics. On the other hand, compared with the similar schemes, our AQS has the better merits in security and efficiency as well.
The following contents of our paper include: AQS scheme in Sect. 2, AQS security proof, security and efficiency comparisons in Sect. 3, and paper conclusion in Sect. 4. On the other hand, in appendix A and appendix B, a simple simulation of our scheme is presented.
2 The proposed AQS
In the proposed AQS scheme, the operators \(H = \left( {\left| 0 \right\rangle \left\langle 0 \right| + \left| 1 \right\rangle \left\langle 0 \right| + \left| 0 \right\rangle \left\langle 1 \right| - \left| 1 \right\rangle \left\langle 1 \right|} \right)/\sqrt 2\) and \(X = \left| 0 \right\rangle \left\langle 1 \right|{ + }\left| 1 \right\rangle \left\langle 0 \right|\) are used. We define the operator H0 = X0 = I, in which I is the identity map. Assume that \(f:\{ 0, \, 1\}^{*} \to \{ 0, \, 1\}^{n} \, \) is a public one-way hash function, which has the uniform output. On the other hand, we assume Alice is the message signatory. Bob acts as the receiver. On the other hand, Trent is employed as the arbitrator, who is trusted by all of the other parties.
Our AQS includes the following three phases: initialization, signature generation phase and message verification phase.
2.1 Initializing phase
In this phase, the partners share the private key and entangled particle sequence. The following are the initializing steps.
IS-1: By performing Bennett and Brassard’s quantum key distribution protocol (BB84 Protocol) [52], Trent and Alice share a random n-bit private key \(k=(k_{1},k_{2},...,k_{n})\).
IS-2: In this step, the private key k is used. Trent prepares n entangled-triple particles \(\phi_{1}\), \(\phi_{2}\),…, \(\phi_{n}\). The state of each particle \(\phi_{i}\) is \(\left| {\phi_{i} } \right\rangle = \frac{1}{\sqrt 2 }\left( {\left| {0_{i}^{(T1)} 0_{i}^{(T2)} 0_{i}^{A} } \right\rangle \, + \left| {1_{i}^{(T1)} 1_{i}^{(T2)} 1_{i}^{A} } \right\rangle } \right)\), where \(i = 1,2, \ldots ,n\). According to the private key k = (k1, k2,…, kn), for each \(\phi_{i}\), if ki = 0, Trent performs the operator \(I \otimes I \otimes I\) on the particle \(\phi_{i}\), or he performs the operator \(H \otimes H \otimes H\) on the particle \(\phi_{i}\). Thus, the state of each entangled \(\phi_{i} \left( {i = 1,2, \ldots ,n} \right)\) is changed into.
where \(\left| + \right\rangle = \left( {\left| 0 \right\rangle + \left| 1 \right\rangle } \right)/\sqrt 2\) and \(\left| - \right\rangle = \left( {\left| 0 \right\rangle - \left| 1 \right\rangle } \right)/\sqrt 2\). According to the entangled particles \(\phi_{1} ,\phi_{2} , \ldots ,\phi_{n}\), Trent composes three particle sequences \(G_{T1} = \{ t_{1}^{(T1)} , \, t_{2}^{(T1)} , \ldots , \, t_{n}^{(T1)} \}\), \(G_{T2} = \{ t_{1}^{(T2)} , \, t_{2}^{(T2)} , \ldots , \, t_{n}^{(T2)} \}\) and GA = {a1, a2,…, an}, in which \(t_{i}^{(T1)}\),\(t_{i}^{(T2)}\), and \(a_{i} \, (i = 1, \, 2, \ldots , \, n)\) represent the first, the second and the third particle of \(\phi_{i}\), respectively.
IS-3: Trent randomly produces sufficient decoy particles whose states come from the non-orthogonal set \(\left\{ {\left| 0 \right\rangle ,\left| 1 \right\rangle ,\left| + \right\rangle ,\left| - \right\rangle } \right\}\). Then, Trent mixes them with GA at random and gets the new non-orthogonal sequence \(G_{A}^{\prime }\). After that, Trent transmits the sequence \(G_{A}^{\prime }\) to Alice.
IS-4: After Alice receives \(G_{A}^{\prime }\), Trent publishes the information of the decoy particles including their positions and correct states. Then, Alice measures all the decoy particles in \(G_{A}^{\prime }\) and checks whether the measurement results are the same as those published by Trent. Once the error rate is above the established standards set by the system, the partners restart the protocol. Or Alice gets GA from the sequence \(G_{A}^{\prime }\) by deleting the decoy particles. GA is kept by Alice as her private sequence.
2.2 Signing phase
Suppose that Alice will sign a classical message c ∈ {0, 1}*. Alice generates the signature by the steps as follows.
SS-1: Alice computes the message digest f(k||c) = m = (m1, m2,…, mn) with her key k and the hash function f, where the symbol “||” denotes the connection of the bit strings. After that, Alice prepares a particle sequence S = {s1, s2,…, sn}, and the state of the i-th particle si of the sequence S is \(\left| {s_{i} } \right\rangle = \left| {m_{i} } \right\rangle\).
SS-2: According to the private key k, the private sequence GA = {a1, a2,…, an} and the sequence S = {s1, s2,…, sn}, Alice performs n controlled unitary operations as follows.
For the ith operation \((i = 1, \, 2, \ldots , \, n)\), if ki = 0, Alice executes the controlled NOT operator on ai and si, where ai is operated as the controlled particle, while si as the target particle. Thus, the particles \(t_{i}^{(T1)}\), \(t_{i}^{(T2)}\), ai and si are entangled together with the state
For the ith operation \((i = 1, \, 2, \ldots , \, n)\), if ki = 1, Alice executes the operator H on ai. Then, she performs the controlled NOT operation on ai and si, where ai is operated as the controlled particle, while si the target particle. Next, Alice performs the H operations on the particles ai and si, respectively. Thus, the entangled state of \(t_{i}^{(T1)}\), \(t_{i}^{(T2)}\), ai and si is changed into
After that, Alice sends c and S to Bob. Bob keeps the particle sequence S as the quantum signature on c.
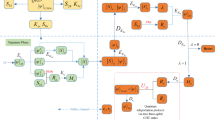
The simple schematic diagram of the signing process is shown in Fig. 1.
2.3 Verifying phase
In our scheme, Alice is the signer. In this phase, the quantum signature S signed by Alice is verified. This phase includes three verification steps:
VS-1: Bob publishes c. Then, by the decoy particles and the methods in steps IS-3 and IS-4, Bob sends Trent the sequence S.
VS-2: According to k, the private sequence \(G_{T1} = \{ t_{1}^{(T1)} , \, t_{2}^{(T1)} , \ldots , \, t_{n}^{(T1)} \}\) and the sequence S = {s1, s2,…, sn}, Trent performs n controlled unitary operations as follows.
For the ith operation \((i = 1, \, 2, \ldots , \, n)\), if ki = 0, Trent executes the controlled NOT operator on the controlled \(t_{i}^{(T1)}\) and the target particle si. Then, the entangled state of \(t_{i}^{(T1)}\), \(t_{i}^{(T2)}\), ai and si evolves into
For the ith operation (i = 1, 2,…, n), if ki = 1, Trent performs the H operations on the particles \(t_{i}^{(T1)}\) and si, respectively. Then, he performs the controlled NOT operator on \(t_{i}^{(T1)}\) and si so that \(t_{i}^{(T1)}\) is operated as the controlled particle, while si the target particle. At last, he applies operator H to \(t_{i}^{(T1)}\). Then, the entangled state of \(t_{i}^{(T1)}\), \(t_{i}^{(T2)}\), ai and si evolves into
VS-3: Trent measures each particle si (i = 1, 2,…, n) with z-basis \(\left\{ {\left| 0 \right\rangle ,\left| 1 \right\rangle } \right\}\). By the measurement result of si, Trent sets
Thus, Trent gets \(m^{\prime } = \left( {m_{1}^{\prime } ,m_{2}^{\prime } , \ldots ,m_{n}^{\prime } } \right)\). Then, by the shared k and the message c published by Bob, Trent computes the message digest m = f(k||c). Next, he checks whether \(m = m^{\prime }\). If \(m = m^{\prime }\)(\(m \ne m^{\prime }\)), Trent publishes “Yes” (“No”), and Bob accepts (denies) the validity of the quantum signature. If the signature is valid, Trent also keeps (c, m, Bob) as the “proof” of the quantum signature so as to solve the disputation that may occur between Alice and Bob in the future.
3 Analysis of the security
The correctness of the AQS can be easily verified. This section first showed the theoretical security proof for the proposed AQS. Then, the unforgeability of the quantum signature is proved. At last, the no-repudiation of the signature is analyzed.
3.1 Information-theoretical security
In this section, first, by analyzing the density operator of the quantum signature, it is found that all the quantum signatures have the same state. What is more, any unitary operator attack to the quantum signature cannot change its density operator. This means that the adversary cannot get useful information about the private key by performing the unitary operator attack. Second, we analyze information-theoretical security of the proposed scheme. In [55], Yang et al. proved that for a quantum signature scheme, its information-theoretical security relies on the trace distance of the different quantum signatures. Then, by analyzing the trace distance of different quantum signatures, we prove that the trace distance of different quantum signatures is zero. Then, the proposed AQS can be proved to be information-theoretically secure.
Theorem 1.
The quantum signatures on all the messages have the same density operator.
Proof.
Note that any c and its signature S satisfies Eqs. (2) and (3). Hence, the density operator of si is.
Therefore, for any message c, the corresponding density operator of signature S is always \(\rho_{s} = \frac{{ \otimes_{i = 1}^{n} I}}{{2^{n} }}\). Therefore, the quantum signatures on all the messages have the same density operator. □
Suppose that an adversary Eve attempts to get some information on the signer’s secret k by performing some unitary operator \(U = \otimes_{i = 1}^{n} U_{i}\) on the signature S. However, we can prove that the operation U cannot change the density operator of the state of the signatures S.
Theorem 2.
If an adversary Eve performs some unitary operator \(U = \otimes_{i = 1}^{n} U_{i}\) on the signature S, the density operator of the signature will not have any change. That is, for each message-signature pair (c, S), after the unitary operator attack \(U = \otimes_{i = 1}^{n} U_{i}\) on S, the density operator of the state of the disturbed quantum signature S is always \(\rho_{s} = \frac{{ \otimes_{i = 1}^{n} I}}{{2^{n} }}\).
Proof.
Note the signature S and the message c satisfy Eqs. (2) and (3). If an adversary Eve applies some unitary operator \(U = \otimes_{i = 1}^{n} U_{i}\) to S, the density operator of si can be computed as follows.
Therefore, if an adversary Eve applies some unitary operator \(U = \otimes_{i = 1}^{n} U_{i}\) to S, the density operator of the state of the disturbed quantum signatures S is \(\rho_{s} = \frac{{ \otimes_{i = 1}^{n} I}}{{2^{n} }}\). Therefore, for any unitary operator attack, the signature density operator will not have any change. □
The following theorem shows that the AQS’s information-theoretical security can also be proved. This means that the adversary can get no information about the secret key of the signatory from the published quantum signature by the unitary operation attack.
Theorem 3.
For any message c and unitary operator attack \(U = \otimes_{i = 1}^{n} U_{i}\) on the signature S, the mutual information between private key space K and the probabilistic polynomial-time quantum adversary Eve is zero. That is,
Proof.
Note that the mutual information.
Because \(H(K\left| {c, \, S, \, U} \right.) \le H(K)\), we can get
Because the private k is randomly generated by performing the unconditional secure quantum protocol on key sharing [52], the private key space K has a uniform distribution. Therefore, the entropy of K is
Now, we consider the probability of Eve’s successfully guessing the private key k under the unitary operator attack with the public message c and the quantum signature S. By Theorem 2 and Eq. (8), we can get that for any c, k and unitary operator attack U, the signature S has the same density operator. Therefore, According to Theorem 2 and Eq. (8), Eve can guess the private key k from c, S and the unitary operation attack U with a probability
Hence, the conditional entropy
Therefore, by Eqs. (11, 12, 14), we can get \(I\left( {K;{\text{Eve}}\left| {c, \, S, \, U} \right.} \right) = 0\). □
Theorem 3 shows that if an adversary Eve tries to perform some unitary operator attack, he will get nothing about the signatory’s secret key from the published information.
Now, for the proposed scheme, we prove that there exists no polynomial algorithm Cn such that the signatures on different messages can be efficiently distinguished.
It should be noted that the quantum signature is generated by encrypting the message c. Then, our scheme can be viewed as one quantum encryption scheme. In [53,54,55], for the quantum signature, its information-theoretical security is defined as follows.
Definition 1.
We call a quantum signature is information-theoretically secure, if there exists no polynomial distinguishing algorithm Dn such that it can distinguish the quantum signatures S and S* with a non-negligible probability, where S and S* are the quantum signatures on any two different messages c and c* in the message space {0, 1}n, respectively. That is, for any positive polynomial p(·) and sufficient large n, a quantum signature scheme with information-theoretical security should satisfy
The results in [55] show that for a quantum signature scheme, its information-theoretical security relies on the trace distance of the different quantum signatures.
Theorem 4
[55]. A quantum signature has information-theoretical security only if, for each polynomial p and different messages c and c*, the trace distance.
where \(\rho_{c}\)(\(\rho_{{c^{*} }}\)) denotes the density operator of the signature S (S*) on c(c*).
Theorem 5.
Our new AQS has the information-theoretical security.
Proof.
Let c and c* be any two different messages. Let S and S* be the quantum signatures on the messages c and c*, respectively. We use \(\rho_{c}\) and \(\rho_{{c^{*} }}\) which denote the density operators of the states of the quantum signatures S and S*, respectively. According to Theorem 1, it follows that
According to Eq. (17), we can get
It is clear that Eq. (18) satisfies the result of Theorem 4. Therefore, our scheme can be of information-theoretical security. □
The result of Theorem 5 means that no distinguishing algorithm Dn can distinguish the signatures S and S* efficiently. This means that for our quantum signature scheme, no efficient distinguishing algorithm Dn can break the signer’s key. Otherwise, given any two quantum signatures S and S* on different messages c and c*, respectively, the quantum adversary can use the private key to accurately generate the corresponding quantum signatures on c and c* such that S and S* can be distinguished by performing the quantum swap test algorithm [58], which contradicts the theoretical security of our AQS that proved in Theorem 5. Therefore, there is no efficient distinguishing algorithm that can break the signatory’s private key. The proposed AQS can guarantee the secrecy of signatory’s private key.
3.2 Unforgeability
In this section, we prove that it is infeasible to generate a forgery for the proposed quantum signature without knowing the private of the signer. First, based on the non-orthogonality of \(\left\{ {\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right),\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)} \right\}\), the non-cloning theorem for the non-orthogonal entangled-triple sequence \(\Pi = \left\{ {\pi_{1} ,\pi_{2} , \ldots ,\pi_{k} } \right\}\) is proved, in which each \(\pi_{i} \in \left\{ {\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right),\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)} \right\}\). Then, we prove that if an adversary can forge the quantum signature, his forgery action will violate the non-cloning theorem for the non-orthogonal entangled-triple sequence \(\Pi\). This means it is infeasible for the adversary to forge the quantum signature of the signer.
Theorem 6.
Given an entangled-triple sequence \(\Pi = \left\{ {\pi_{1} ,\pi_{2} , \ldots ,\pi_{k} } \right\}\), in which each entangled \(\pi_{i}\) (1 ≤ i ≤ k) is randomly selected in the set \(\left\{ {\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right),\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)} \right\}\), there is not any unitary operator W so that the sub-system of each \(\pi_{i}\) can be cloned. That is, there is not any unitary operator W so that.
and
where \(\varepsilon\) is an auxiliary particle.
Proof.
Let \(\Pi = \left\{ {\pi_{1} ,\pi_{2} , \ldots ,\pi_{k} } \right\}\) be an entangled-triple sequence, in which each entangled \(\pi_{i}\) (1 ≤ i ≤ k) is randomly selected in the set \(\left\{ {\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right),\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)} \right\}\). Note that the states \(\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right)\) and \(\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)\) are non-orthogonal. Therefore, the entangled-triple sequence \(\Pi\) is a non-orthogonal sequence, which cannot be accurately distinguished. Suppose there is some unitary operator W so that Eqs. (19, 20) hold. From Eqs. (19, 20), we can get.
from which we can get a conflict equation \( 1= \sqrt 2\). Therefore, there is not any unitary operator W so that the sub-system of each \(\pi_{i}\) can be cloned.
Theorem 7.
Without the knowledge of the signer’s private key, it is not feasible for the adversary Eve to produce a forged quantum signature.
Proof.
Suppose Eve is a quantum adversary, who plays the role of the forger. Note that Sect. 3.1 has proved the information-theoretical security for the proposed AQS, which can ensure the secrecy of signatory’s key. For our scheme, to forge the quantum signature, Eve has to query the oracle f for its output. Suppose that Eve can successfully forge a signature S on some message c without knowing the signatory’s key k. And the answer for the output of the query on the oracle f about the message c is m = (m1, m2,…, mn) ∈ {0, 1}n. Note that the quantum signature S satisfies Eqs. (2, 3). This means that the state sequence of entangled particle sequence including the forged quantum signature S is.
in which each
According to m = (m1, m2,…, mn) and the forged quantum signature S, Eve composes a new particle sequence \(S|_{{m_{{i_{j} }} = 0}}\). That is, for each particle si (1 ≤ i ≤ n) of the particle sequence S, if mi = 0, Eve puts the particle si into the set \(S|_{{m_{{i_{j} }} = 0}}\). Assume that
where i1, i2,…,il ∈ {1, 2,…, n} and the corresponding \(m_{{i_{1} }} = m_{{i_{2} }} = \cdots = m_{{i_{l} }} = 0\). According to Eq. (1), it follows that
which is corresponding to Eq. (24). After the successful forgery, Eve queries about the private particles indexed by i1, i2,…,il, the signing system outputs the particle sequence \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) for Eve. Because \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) is a non-orthogonal particle sequence, the particles in \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) cannot be accurately distinguished from each other. Therefore, for Eve, \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) is an unknown quantum sequence.
On the other hand, according to Eq. (22) and i1, i2,…,il, the signing system outputs a sequence
Now, we compare the form of each particle of the particle sequence \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) with that of the particle sequence \(\chi_{T1,T2,A,S} |_{{m_{{i_{j} }} = 0}}\). According to Eqs. (2, 3, 24–26), it follows that if \(k_{{i_{j} }} = 0\) (j = 1, 2,…, l)
If \(k_{{i_{j} }} = 1\) (j = 1, 2,…, l)
According to Eqs. (24, 25, 27, 28), we can get that if Eve can produce a valid forged signature S, he can clone a particle sequence \(S|_{{m_{{i_{j} }} = 0}} = \left\{ {s_{{i_{1} }} ,s_{{i_{2} }} , \ldots ,s_{{i_{l} }} } \right\}\) from the unknown entangled-triple sequence \(\Phi {|}_{{m_{{i_{j} }} = 0}} = \left\{ {\phi_{{i_{1} }} ,\phi_{{i_{2} }} , \ldots ,\phi_{{i_{l} }} } \right\}\), which is conflict to the non-cloning theorem (proved in Theorem 6) for the sub-system of each entangled \(\phi_{{i_{j} }}\). Therefore, it will be infeasible for Eve to forge the quantum signature of the signer.
3.3 Non-repudiation
In Sect. 3.2, for the proposed AQS, we have proved its unforgeability. Therefore, once the verification shows the validity of the signature, both the signer and the signature receiver cannot refuse its validity due to the unforgeability of the quantum signature.
For the signature, when the partners finish checking its validity, either the signatory or the signature receiver will lose the state of signature, because it has been changed after the signature verification. The signatory may deny her signature generation for the signature receiver. And the signature receiver may refuse his participation of the signature verification. In this case, Trent can solve the disputation between the signer and the signature receiver. Note that in the proposed scheme, the message digest of c is computed by m = f(k||c). That is, to compute the digest m, the private key k has to be used as the input of the one-way function f. Therefore, without k, it is not feasible for the adversary to compute the digest m. At the same time, without the input k of f, the adversary can guess the message digest m by the negligible probability \(\frac{1}{{2^{n} }}\) because of the uniform distribution of f. This means that only the signatory can generate m by her key k. Note that in the new AQS, when verifying a signature, Trent keeps the triple (c, m, Bob) as the “proof” of the quantum signature. If the signatory denies her signature generation for the signature receiver, Trent can recover the proof (c, m, Bob) to prove that signer has ever produced the valid signature S, because only the signer can produce the message digest m = f(k||c) with the private key k. On the other hand, it is infeasible for Bob to deny the truth of the signature verification due to the verification proof (c, m, Bob), in which c was announced by Bob.
According to the analysis above, it follows that both the signature receiver and the signer cannot refuse a valid signature. At the same time, the signer cannot deny her signature generation for the signature receiver, and the signature receiver cannot refuse his participation of the signature verification. Therefore, we can get the non-repudiation of the proposed AQS.
3.4 Security and efficiency comparisons
In this section, the security and efficiency of the similar schemes are compared. Here, we ignore the AQSs which have been proved to be insecure against forgery attacks and disavowal attacks.
First, although the private keys of most quantum signature systems were created with the unconditionally secure quantum key distribution protocol (e.g., BB84 Protocol), they still could be broken by some novel attacks or some unknown unitary operator attacks to the quantum signatures, which include the information of the private keys. For example, Chen et al. [56] found that the private keys of the QOTP [57]-based quantum signature schemes could be broken by performing the controlled SWAP attacks to the quantum signatures. This means the QOTP-based signatures in [14, 25,26,27,28, 36, 39, 43] is not immune to the controlled SWAP attacks. Therefore, to guarantee the security of private keys of the quantum signing systems, the quantum signature ciphertexts should be information-theoretically secure such that there is not any unitary operator attack or polynomial distinguishing algorithm which can distinguish the quantum signature ciphertexts with a non-negligible probability. In Sect. 3.1, we have proved the information-theoretical security of the proposed AQS scheme. However, in the similar schemes, the information-theoretical security of the quantum signatures was not proved.
Second, to our knowledge, in most of the quantum signature schemes including the schemes in [18, 23, 36, 44,45,46,47], the unforgeability of the signature was analyzed by emphasizing the secrecy of the private keys of the signers. However, according to the review of the quantum signature in Sect. 1, we know that many quantum signatures can be forged by various forgery attacks without knowing the private keys of the signers. No sufficient formal proof can mathematically prove that the unforgeability of these schemes relies on the basic the quantum theories. In this paper, we prove that the unforgeability of the proposed scheme depends on the non-cloning theorem. That is, if the adversary can forge the signature, his/her actions will violate the non-cloning theorem. This means that it is infeasible for the adversary to forge the quantum signature. However, in the similar schemes, no sufficient formal security proof can mathematically prove that the unforgeability of these schemes is strictly dependent on the basic principles of the quantum mechanics.
Third, we compare the qubit efficiency of the similar AQSs. In [59], the qubit efficiency is defined as \(\eta { = }\delta_{1} /\delta_{2}\), where \(\delta_{1} (\delta_{2} )\) denotes the number of transmitted bits (qubits) in the quantum protocol. In our AQS, 2n qubits are transmitted during the signature generation and verification phases, while n bits classical message bits are authenticated. Therefore, the qubit efficiency of the proposed AQS is about 50%(the decoy particles which are used to check the quantum channel are ignored). In Table 1, the qubit efficiency of the other similar schemes is computed as well.
Fourth, in the schemes of [18, 43, 45,46,47], the arbitrators or the signature receivers had to perform the quantum state comparison algorithm [58] so as to verify the signature. Note that the quantum state comparison test may fail with probability \(\left( {1 + \theta^{2} } \right)/2\), where \(\theta = \left| {\left\langle {\alpha } \mathrel{\left | {\vphantom {\alpha \beta }} \right. \kern-\nulldelimiterspace} {\beta } \right\rangle } \right| \in \left( {0,1} \right)\) dependents on the compared states. Then, the signature can be successfully verified by the quantum state comparison algorithm with probability \(p = 1 - \left( {\frac{{1 + \theta^{2} }}{2}} \right)^{t}\), where t denotes the count of performing the quantum state comparison. Therefore, in [18, 43, 45,46,47], to make the comparison result be reliable, the verifiers should perform the state comparison many times so that \(p = 1 - \left( {\frac{{1 + \theta^{2} }}{2}} \right)^{t} \to 1(t \to + \infty )\). What is more, the signers should produce many copies of the quantum signature and transmit them to the receivers for the use of quantum state comparison. All of these will greatly decrease the computation efficiency and the qubit efficiency of the AQSs. In our AQS, the quantum signature is verified without performing any quantum state comparison algorithm. Therefore, compared with the similar AQSs [18, 43, 45,46,47], our scheme has the better computation efficiency.
4 Conclusions
First, in most of the existing AQSs, the signers’ private keys were created with the unconditionally secure quantum key distribution protocol so that the private keys cannot be broken during the key generation phase. However, the adversary may break the private keys by performing some novel attacks (e.g., the controlled SWAP attacks) or some unknown attacks to the quantum signatures, which include the information of the private keys. Therefore, the quantum signature ciphertext should be theoretically indistinguishable and the quantum signature scheme should be information-theoretically secure such that the adversary can get no useful information about the private key of the signer from the quantum signatures.
Second, in most of the quantum signature schemes, the unforgeability of the signatures was analyzed by emphasizing the secrecy of the private keys of the signers. This kind of security analysis is not comprehensive. According to the review of the quantum signature schemes, we found many quantum signatures could still be forged, even if the private keys of the signers were unconditionally secure. Therefore, the unforgeablity of an AQS should be provably secure. The unforgeability of the quantum signature should be proved with the strict proof based on the principles of the quantum mechanics. We can prove that if an adversary can generate a forgery for the quantum signature, his/her actions will violate some quantum principles.
Third, we proposed such an AQS with provable security. The proposed AQS was different from the other existing AQS schemes. Its security can be supported by the information-theoretical indistinguishability of the non-orthogonal quantum states and the non-cloning theorem. In the proposed scheme, we proved the non-cloning theorem for the sub-system of the entangled-triple particles with non-orthogonal states. The unforgeability of the proposed scheme was proved as well. Theorem 7 shows that the unforgeability of the proposed AQS was put on the quantum mechanics. That is, the adversary forgery will lead to some conflict actions on the quantum principles. The security proof of our AQS also showed the idea of provable security for a quantum signature.
On the other hand, in the proposed AQS, the participants need not perform the probabilistic quantum state comparison test. The proposed scheme has better qubit efficiency.
Therefore, compared with the other similar schemes, ours has the better security and efficiency.
Data availability
My manuscript has no associated data.
References
Diffie, W., Hellman, M.E.: New direction in cryptography. IEEE Trans. Inf. Theory 22(6), 644–654 (1976)
Mambo, M., Usuda, K., Okamoto, E.: Proxy signature: delegation of the power to sign messages. IEICE Trans. Fundam. E79-A(5), 1338–1354 (1996)
Chaum, D.: Blind signatures for untraceable payments. In: Chaum, D., Rivest, R.L., Sherman, A.T. (eds.) Advance in Cryptology-CRYPTO’82, pp. 199–203. Springer, Boston (1983)
Chaum, D., Heyst, E.: Group signatures. In: Davies, D.W. (ed.) Advance in cryptology- EUROCRYPT’91, pp. 257–265. Springer, Berlin (1991)
Rastegari, P., Berenjkoub, M., Dakhilalian, M., et al.: Universal designated verifier signature scheme with non-delegatability in the standard model. Inform. Sci. 479, 321–334 (2019)
Rastegari, P., Susilo, W., Dakhilalian, M.: Certificateless designated verifier signature revisited: achieving a concrete scheme in the standard model. Int. J. Inf. Secur. 18(5), 619–665 (2019)
Rivest, R.L., Shamir, A., Adelman, L.: A method for obtain digital signatures and public-key cryptosystem. Commun. ACM 21(2), 120–126 (1978)
Cha, C.J., Cheon, J.H.: An identity-based signature from gap Diffie-Hellman groups. In: PKC 2003, Springer, Berlin, pp. 18–30 (2003)
Shor, P. W.: Algorithms for quantum computation: discrete logarithm and factoring. In: Proceedings of the 35th Annual Symposium on the Foundations of Computer Science, IEEE Computer Society Press, pp. 124–134 (1994)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26(5), 1484–1509 (1997)
Grover, L.K.: Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 79(2), 325–328 (1997)
Huang, Y., Su, Z., Zhang, F., Ding, Y.: Quantum algorithm for solving hyperelliptic curve discrete logarithm problem. Quantum Inf. Process. 19(62), 1–17 (2020)
Gottesman, D., Chuang, I.: Quantum digital signatures. arXiv: quant-ph/0105032 (2001)
Zeng, G.H., Keitel, C.H.: Arbitrated quantum-signature scheme. Phys. Rev. A 65(4), 042312 (2002)
Yang, Y.G., Zhou, Z., Teng, Y.W., Wen, Q.Y.: Arbitrated quantum signature with an untrusted arbitrator. Eur. Phys. J. D 61, 773–778 (2011)
Luo, M.X., Chen, X.B., Yun, D., Yang, Y.X.: Quantum signature scheme with weak arbitrator. Int. J. Theor. Phys. 51(7), 2135–2142 (2012)
Jiang, D.H., Xu, Y.L., Xu, G.B.: Arbitrary quantum signature based on local indistinguishability of orthogonal product states. Int. J. Theor. Phys. 58(3), 1036–1045 (2019)
Wang, M.Q., Wang, X., Zhan, T.: An efficient quantum digital signature for classical messages. Quantum Inf. Process. 17(10), 275 (2018)
Liang, X.Q., Wu, Y.L., Zhang, Y.H., Wang, S.S., Xu, G.B.: Quantum multi-proxy blind signature scheme based on four-qubit cluster states. Int. J. Theor. Phys. 58(1), 31–39 (2019)
Qin, H., Tang, W.K.S., Tso, R.: Efficient quantum multi-proxy signature. Quantum Inf. Process. 18(2), 53 (2019)
Xin, X., Wang, Z., Yang, Q., Li, F.: Quantum designated verifier signature based on Bell states. Quantum Inf. Process. 19(79), 53 (2020)
Su, Q., Li, W.M.: Improved quantum signature scheme with weak arbitrator. Int. J. Theor. Phys. 52(9), 3343–3352 (2013)
Xin, X., He, Q., Wang, Z., Yang, Q., Li, F.: Security analysis and improvement of an arbitrated quantum signature scheme. Optik 189, 23–31 (2019)
Gao, F., Qin, S.J., Guo, F.Z., et al.: Cryptanalysis of the arbitrated quantum signature protocol. Phys. Rev. A 84, 022344 (2011)
Li, Q., Chan, W.H., Log, D.Y.: Arbitrated quantum signature scheme using Bell states. Phys. Rev. A 79(5), 054307 (2009)
Zou, X.F., Qiu, D.W.: Security analysis and improvements of arbitrated quantum signature schemes. Phys. Rev. A 82(4), 23504–23516 (2010)
Li, W., Shi, R., Huang, D., et al.: Quantum blind dual-signature scheme without arbitrator. Phys. Scr. 91, 035101 (2016)
Xia, C., Li, H., Hu, J.: A semi-quantum blind signature protocol based on five-particle GHZ state. Eur. Phys. J. Plus 136, 633 (2021)
Zhou, B.M., Lin, L.D., Wang, W., et al.: Security analysis of particular quantum proxy blind signature against the forgery attack. Int. J. Theor. Phys. 59, 465–473 (2020)
Liu, G., Ma, W.P., Cao, H., et al.: A novel quantum group proxy blind signature scheme based on five-qubit entangled state. Int. J. Theor. Phys. 58, 1999–2008 (2019)
Ding, L., Xin, X., Yang, Q., et al.: Security analysis and improvements of XOR arbitrated quantum signature-based GHZ state. Mod. Phys. Lett. A 37(2), 2250008 (2022)
Zheng, X.Y., Kuang, C.: Arbitration quantum signature protocol based on XOR encryption. Int. J. Quantum Inf. 18, 2050025 (2020)
He, Q., Xin, X., Yang, Q.: Security analysis and improvement of a quantum multi-signature protocol. Quantum Inf. Process. 20, 26 (2021)
Jiang, D.H., Hu, Q.Z., Liang, X.Q., et al.: A novel quantum multi-signature protocol based on locally indistinguishable orthogonal product states. Quantum Inf. Process. 18(9), 268 (2019)
Zhang, L., Sun, H.W., Zhang, K.J., et al.: The security problems in some novel arbitrated quantum signature protocols. Int. J. Theor. Phys. 56, 2433–2444 (2017)
Wang, C., Liu, J.W., Shang, T.: Enhanced arbitrated quantum signature scheme using Bell states. Chin. Phys. B 23(6), 060309 (2014)
Xu, G., Zou, X.: Security analysis of an arbitrated quantum signature scheme with Bell states. Int. J. Theor. Phys. 55, 4142–4156 (2016)
Liu, F., Zhang, K., Cao, T.: Security weaknesses in arbitrated quantum signature protocols. Int. J. Theor. Phys. 53, 277–288 (2014)
Wang, J., Zhang, Q., Tang, C.J.: Efficient quantum signature protocol of classical messages. J. Commun. 28(1), 64–68 (2003)
Dunjko, V., Wallden, P., Andersson, E.: Quantum digital signatures without quantum memory. Phys. Rev. Lett. 112(4), 040502 (2014)
Wallden, P., Dunjko, V., Kent, A., et al.: Quantum digital signatures with quantum key distribution components. Phys. Rev. A 91(4), 042304 (2014)
Amiri, R., Wallden, P., Kent, A., et al.: Secure quantum signatures using insecure quantum channels. Phys. Rev. A 93(3), 032325 (2016)
Lu, D., Li, Z., Yu, J., et al.: A verifiable arbitrated quantum signature scheme based on controlled quantum teleportation. Entropy (Basel) 24(1), 111 (2022)
Zou, X.F., Qiu, D.W., Mateus, P.: Security Analyses and improvement of arbitrated quantum signature with an untrusted arbitrator. Int. J. Theor. Phys. 52(9), 3295–3305 (2013)
Zhang, M.L., Liu, Y.H., Nie, M., et al.: Arbitrated quantum signature of quantum messages with a semi-honest arbitrator. Int. J. Theor. Phys. 57, 1310–1318 (2018)
Zhang, K.J., Zhang, W.W., Li, D.: Improving the security of arbitrated quantum signature against the forgery attack. Quantum Inf. Process. 12(8), 2655–2669 (2013)
Zhang, L., Sun, H.W., Zhang, K.J., et al.: An improved arbitrated quantum signature protocol based on the key-controlled chained CNOT encryption. Quantum Inf. Process. 16(3), 70 (2017)
Wang, Y., Xu, K., Guo, Y.: A chaos-based arbitrated quantum signature scheme in quantum crypotosystem. Int. J. Theor. Phys. 53(1), 28–38 (2014)
Liu, F., Qin, S.J., Huang, W.: An arbitrated quantum signature with Bell states. Int. J. Theor. Phys 53(5), 1569–1579 (2014)
Li, Q., Li, C.Q., Long, D.Y., et al.: Efficient arbitrated quantum signature and its proof of security. Quantum Inf. Process. 12(7), 2427 (2013)
Li, Q., Du, R.G., Long, D.Y., et al.: Entanglement enhances the security of arbitrated quantum signature. Int. J. Quantum Inf. 7(5), 913 (2009)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. Theor. Comput. Sci. 560, 7–11 (2014)
Menezes, A.J., Oorschot, P.V., Vanstone, S.A.: Handbook of Applied Cryptography. CRC Press, Boca Raton (1996)
Yang, L., Yang, B., Pan J.: Quantum public-key encryption with information theoretic security. In: Proceedings of SPIE, vol. 8440, p. 84400E-17 (2010)
Yang, L., Xiang, C., Li, B.: Quantum probabilistic encryption scheme based on conjugate coding. China Commun. 10(2), 19–26 (2013)
Chen, F.L., Zhang, L.H., Zhang, H.: Controlled SWAP attack and improved quantum encryption of arbitrated quantum signature schemes. Quantum Inf. Process. 18, 140 (2019)
Boykin, P.O., Roychowdhury, V.: Optimal encryption of quantum bits. Phys. Rev. A 67(4), 645–648 (2003)
Buhrman, H., Cleve, R., Watrous, J., de Wolf, R.: Quantum fingerprinting. Phys. Rev. Lett. 87(16), 167902 (2001)
Hwang, T., Lee, K.C.: EPR quantum key distribution protocols with 100% qubit efficiency. IET Inf. Secur. 1(1), 43–45 (2007)
Acknowledgements
This work is supported by the Key Scientific Research Project of Colleges and Universities in Henan Province (CN) (No.22A413010).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendices
Appendix A: A simple simulation of the proposed scheme
To simplify the example, we suppose the parameter n = 4. Assume that \(f:\{ 0, \, 1\}^{*} \to \{ 0, \, 1\}^{4} \, \) is a public one-way hash function, and it has the uniform output.
1.1 Appendix A.1: Initializing phase
IS-1: By performing Bennett and Brassard’s BB84 Protocol, Trent and Alice share a random private key k. Assume k = (1001). Thus, k1 = k4 = 1, k2 = k3 = 0.
IS-2: Trent prepares four entangled-triple particles \(\phi_{1}\), \(\phi_{2}\), \(\phi_{3}\) and \(\phi_{4}\). The state of each particle \(\phi_{i}\) (i = 1, 2, 3, 4) is \(\left| {\phi_{i} } \right\rangle = \frac{1}{\sqrt 2 }\left( {\left| {0_{i}^{(T1)} 0_{i}^{(T2)} 0_{i}^{A} } \right\rangle \, + \left| {1_{i}^{(T1)} 1_{i}^{(T2)} 1_{i}^{A} } \right\rangle } \right)\). According to k, for each \(\phi_{i}\)(i = 1, 2, 3, 4), if ki = 0, Trent performs the operator \(I \otimes I \otimes I\) on \(\phi_{i}\), or he performs the operator \(H \otimes H \otimes H\) on \(\phi_{i}\). Thus, the states of \(\phi_{1}\), \(\phi_{2}\), \(\phi_{3}\) and \(\phi_{4}\) are changed into
where \(\left| + \right\rangle = \left( {\left| 0 \right\rangle + \left| 1 \right\rangle } \right)/\sqrt 2\) and \(\left| - \right\rangle = \left( {\left| 0 \right\rangle - \left| 1 \right\rangle } \right)/\sqrt 2\). According to \(\phi_{1}\), \(\phi_{2}\), \(\phi_{3}\) and \(\phi_{4}\), Trent composes three particle sequences \(G_{T1} = \{ t_{1}^{(T1)} , \, t_{2}^{(T1)} ,t_{3}^{(T1)} , \, t_{4}^{(T1)} \}\), \(G_{T2} = \{ t_{1}^{(T2)} , \, t_{2}^{(T2)} ,t_{3}^{(T2)} , \, t_{4}^{(T2)} \}\) and GA = {a1, a2, a3, a4}, in which \(t_{i}^{(T1)}\),\(t_{i}^{(T2)}\), and ai represent the 1st, the 2nd and the 3rd particle of \(\phi_{i}\), respectively, where i = 1, 2, 3, 4.
IS-3: Trent randomly produces sufficient decoy particles whose states come from the non-orthogonal set \(\left\{ {\left| 0 \right\rangle ,\left| 1 \right\rangle ,\left| + \right\rangle ,\left| - \right\rangle } \right\}\). Then, Trent mixes them with GA at random and gets the new non-orthogonal sequence \(G^{\prime}_{A}\). After that, Trent transmits the sequence \(G^{\prime}_{A}\) to Alice.
IS-4: After Alice receives \(G^{\prime}_{A}\), Trent publishes the information of the decoy particles including their positions and correct states. Then, Alice measures all the decoy particles in \(G^{\prime}_{A}\) and checks whether the measurement results are the same as those published by Trent. Once the error rate is above the established standards set by the system, the partners restart the protocol. Or Alice gets GA from the sequence \(G^{\prime}_{A}\) by deleting the decoy particles. GA is kept by Alice as her private sequence.
1.2 Appendix A.2: Signing phase
Suppose that Alice will sign a classical message c = (0100101).
SS-1: Alice computes the message digest f(k||c) = m with her key k and the hash function f. Suppose \(m=(1100)\). Then \(m_{1}=m_{2}=1\) and \(m_{3}=m_{4}=0\). After that, Alice prepares a particle sequence where the symbol “||” denotes the connection of the bit strings. After that, Alice prepares a particle sequence S = {s1, s2, s3, s4}, and the state of the i-th particle si of the sequence S is \(\left| {s_{i} } \right\rangle = \left| {m_{i} } \right\rangle\). That is,
SS-2: For the ith(i = 1, 2, 3, 4) operation, if ki = 0, Alice executes the controlled NOT operator on ai and si, where ai is operated as the controlled particle, while si as the target particle.
For the ith(i = 1, 2, 3, 4) operation, if ki = 1, Alice executes the operator H on ai. Then, she performs the controlled NOT operation on ai and si, where ai is operated as the controlled particle, while si the target particle. Next, Alice performs the H operations on the particles ai and si, respectively.
After that, the particles \(t_{i}^{(T1)}\), \(t_{i}^{(T2)}\), ai and si are entangled together with the state as follows:
After that, Alice sends c and the particle sequence S to Bob. Bob keeps the particle sequence S as the quantum signature on c.
1.3 Appendix A.3: Verifying phase
VS-1: Bob publishes c = (0100101). Then, by the decoy particles and the methods in steps IS-3 and IS-4, Bob sends Trent the sequence S.
VS-2: According to the shared key k = (k1, k2, k3, k4) = (1001), the particle sequences \(G_{T1} = \{ t_{1}^{(T1)} , \, t_{2}^{(T1)} ,t_{3}^{(T1)} , \, t_{4}^{(T1)} \}\) and S = {s1, s2, s3, s4}, Trent performs four controlled unitary operations as follows.
For the ith(i = 1, 2, 3, 4) operation, if ki = 0, Trent executes the controlled NOT operator on the controlled \(t_{i}^{(T1)}\) and the target particle si.
For the ith (i = 1, 2, 3, 4) operation, if ki = 1, Trent performs the H operations on the particles \(t_{i}^{(T1)}\) and si, respectively. Then, he performs the controlled NOT operator on \(t_{i}^{(T1)}\) and si so that \(t_{i}^{(T1)}\) is operated as the controlled particle while si the target particle. At last, he applies operator H to \(t_{i}^{(T1)}\).
After that, the entangled state of \(t_{i}^{(T1)}\), \(t_{i}^{(T2)}\), ai and si (i = 1, 2, 3, 4) evolves into
VS-3: Trent measures each particle si (i = 1, 2, 3, 4) with z-basis \(\left\{ {\left| 0 \right\rangle ,\left| 1 \right\rangle } \right\}\). By the measurement result of si, Trent sets \(m^{\prime} = \left( {m^{\prime}_{1} ,m^{\prime}_{2} ,m^{\prime}_{3} ,m^{\prime}_{4} } \right)\), where.
According to Eq. (A3), it is clear that \(\left| {s_{1} } \right\rangle = \left| {s_{2} } \right\rangle = \left| 1 \right\rangle\) and \(\left| {s_{3} } \right\rangle = \left| {s_{4} } \right\rangle = \left| 0 \right\rangle\). Therefore, Trent gets \(m^{\prime } = \left( {1,1,0,0} \right)\). Then, by the shared k and the message c published by Bob, Trent can compute the message digest f(k||c) = m = (1100). Next, he checks whether \(m = m^{\prime }\). If \(m = m^{\prime }\) (\(m \ne m^{\prime }\)) Trent publishes “Yes”(“No”), and Bob accepts (denies) the validity of the quantum signature. If the signature is valid, Trent also keeps (c, m, Bob) as the “proof” of the quantum signature so as to solve the disputation that may occur between Alice and Bob in the future.
For this example, it is obvious that \(m = m^{\prime }\). Then, the signature is valid. Thus, Trent keeps (c, m, Bob) as the “proof” of the quantum signature so as to solve the disputation that may occur between Alice and Bob in the future.
Appendix B: Analysis of the security
In this section, the example in Appendix A is used.
2.1 Appendix B.1: Information-theoretical security
Theorem 1.
The quantum signatures on all the messages have the same density operator.
According to the proposed scheme in Appendix A, we know that the quantum signature S on message c satisfies Eq. (A2). By Eq. (A2), we can get
Therefore, for the message c, the corresponding density operator of the signature S is \(\rho_{s} = \frac{{ \otimes_{i = 1}^{4} I}}{{2^{4} }}\). Similarly, for any signature S on the message c, we can compute the same density operator \(\rho_{s} = \frac{{ \otimes_{i = 1}^{4} I}}{{2^{4} }}\). Then, the correctness of Theorem 1 can be verified.
Theorem 2.
If an adversary Eve performs some unitary operator \(U = \otimes_{i = 1}^{n} U_{i}\) on the signature S, the density operator of the signature will have not any change. That is, for each message–signature pair (c, S), after the unitary operator attack \(U = \otimes_{i = 1}^{n} U_{i}\) on S, the density operator of the state of the disturbed quantum signature S is always \(\rho_{s} = \frac{{ \otimes_{i = 1}^{n} I}}{{2^{n} }}\).
For the example, the signature S and the message c satisfy Eq. (A2). If an adversary Eve applies some unitary operator \(U = \otimes_{i = 1}^{4} U_{i}\) to S, the density operator of si can be computed as follow.
Therefore, if an adversary Eve applies some unitary operator \(U = \otimes_{i = 1}^{4} U_{i}\) to S, the density operator of the state of the disturbed quantum signatures S keeps as \(\rho_{s} = \frac{{ \otimes_{i = 1}^{4} I}}{{2^{4} }}\). Therefore, for any unitary operator attack, the signature density operator will not have any change. Then, the correctness of Theorem 2 can be verified.
Theorem 3.
For any message c and unitary operator attack \(U = \otimes_{i = 1}^{n} U_{i}\) on the signature S, the mutual information between private key space K and the probabilistic polynomial-time quantum adversary Eve is zero. That is,
Theorem 3 depends on the result of Theorem 2, Eq. (8) and the distribution of the key space for the key generated by the unconditional secure BB84 protocol. For the proof of Theorem 3, please refer to Sect. 3.1
Theorem 4
[55]. A quantum signature has information-theoretical security only if, for each polynomial p and different messages c and c*, the trace distance.
where \(\rho_{c}\)(\(\rho_{{c^{*} }}\)) denotes the density operator of the signature S (S*) on c(c*).
Theorem 5.
Our new AQS has the information-theoretical security.
Let c and c* be any two different messages. Let S and S* be the quantum signatures on the messages c and c*, respectively. We use \(\rho_{c}\) and \(\rho_{{c^{*} }}\) denote the density operators of the states of the quantum signatures S and S*, respectively. According to Theorem 1, it follows that \(\rho_{c} = \rho_{{c^{*} }} = \frac{{ \otimes_{i = 1}^{4} I}}{{2^{4} }}\). Therefore,
It is clear that Eq. (A8) satisfies the result of Theorem 4. Therefore, our scheme can be of information-theoretical security.
2.2 Appendix B.2: Unforgeability
Theorem 6.
Given an entangled-triple sequence \(\Pi = \left\{ {\pi_{1} ,\pi_{2} , \ldots ,\pi_{k} } \right\}\), in which each entangled \(\pi_{i}\) (1 ≤ i ≤ k) is randomly selected in the set \(\left\{ {\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right),\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)} \right\}\), there is not any unitary operator W so that the sub-system of each \(\pi_{i}\) can be cloned. That is, there is not any unitary operator W so that.
and
where \(\varepsilon\) is an auxiliary particle.
The proof the Theorem 3 depends on the non-orthogonality of the states \(\frac{1}{\sqrt 2 }\left( {\left| {000} \right\rangle + \left| {111} \right\rangle } \right)\) and \(\frac{1}{\sqrt 2 }\left( {\left| { + + + } \right\rangle + \left| { - - - } \right\rangle } \right)\). For more detail proof of Theorem 3, please refer to Sect. 3.2.
Theorem 7.
Without the knowledge of the signer’s private key, it is not feasible for adversary Eve to produce a forged quantum signature.
For this example, the parameter n = 4 and the signer’s private key k = (k1, k2, k3 k4) = (1001). Thus, k1 = k4 = 1, k2 = k3 = 0. Suppose Eve is a quantum adversary, who plays the role of the forger. Note that Sect. 3.1has proved the information-theoretical security for the proposed AQS, which can ensure the secrecy of signatory’s key. For our scheme, to forge the quantum signature, Eve has to query the oracle f for its output. Suppose that Eve can successfully forge a signature S on some message c = (0101100) without knowing the signatory’s key k. And the answer for the output of the query on the oracle f about the message c is m = (0101). Note that if S is a valid forgery. Then, the forgery S must satisfy Eq. (A9) as follows:
According to m = (0, 1, 0, 1) and the forged quantum signature S, Eve composes a new particle sequence \(S|_{{m_{{i_{j} }} = 0}}\). That is, for each particle si (1 ≤ i ≤ 4) of the particle sequence S, if mi = 0, Eve puts the particle si into the set \(S|_{{m_{{i_{j} }} = 0}}\). Then,
According to Eq. (A1), it follows that
After the successful forgery, Eve queries about the private particles indexed by 1 and 3, the signing system outputs the particle sequence \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) for Eve.
On the other hand, according to Eq. (A10) and the indexes 1 and 3, the signing system outputs a sequence
Now, we compare the form of each particle of the particle sequence \(\Phi {|}_{{m_{{i_{j} }} = 0}}\) with that of the particle sequence \(\chi_{T1,T2,A,S} |_{{m_{{i_{j} }} = 0}}\). According to Eqs. (A9–A12), it follows that
According to Eqs. (A10, A11, A13, A14), we can get that if Eve can produce a valid forged signature S, he can clone a particle sequence \(S|_{{m_{{i_{j} }} = 0}} = \left\{ {s_{1} ,s_{3} } \right\}\) from the entangled-triple sequence \(\left\{ {\phi_{1} ,\phi_{3} } \right\}\), which is conflict to the non-cloning theorem (proved in Theorem 6) for the sub-system of each entangled \(\phi_{{i_{j} }}\) of \(\left\{ {\phi_{1} ,\phi_{3} } \right\}\). Therefore, it will be not feasible for Eve to forge the quantum signature of the signer.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Xin, X., Ding, L., Zhang, T. et al. Provably secure arbitrated-quantum signature. Quantum Inf Process 21, 390 (2022). https://doi.org/10.1007/s11128-022-03730-3
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-022-03730-3