Abstract
The design of cryptographic algorithms using the chaos theory has become a hotspot in the field of information security. However, existing chaotic systems are prone to chaotic degradation, and generally do not exhibit multi-stability. In view of these issues, we first propose a non-degenerate multi-stable discrete chaotic system (NMDCS). After a rigorous theoretical analysis, it is proved that the NMDCS has an infinite number of unstable fixed points, and the number of positive Lyapunov exponents (LE) is equal to the system dimensions, indicating that the system has an infinite number of coexisting attractors and is not susceptible to chaotic degradation. In addition, Simulation experiments demonstrate that the NMDCS displays significant chaotic behavior and high efficiency. Finally, to satisfy the confidentiality protection demands for sensitive images, an efficient image encryption algorithm is designed by combining the NMDCS with an adaptive zigzag transformation method. Simulation experiments demonstrate that our image encryption algorithm has high efficiency in both encryption and decryption processes. Moreover, it demonstrates excellent security properties.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Communication over the globe is becoming a basic need of populaces [1]. However, the inherent openness, dynamism, and complexity of the Internet frequently result in information leakage incidents, which makes it imperative to enhance the security level of sensitive information. The most direct method for the protection of information confidentiality is encryption, and various classic encryption algorithms, such as data encryption standard (DES) and advanced encryption standard (AES), have been proposed successively. Although these algorithms are easily available, extensively tested, and widely accepted for text data encryption, their application in image encryption is constrained due to the large amount of data, strong correlation between adjacent pixels, and high redundancy of image data.
Chaos is a central research topic of nonlinear theories. It exhibits distinctive properties, including initial state sensitivity, topological transitivity, and periodic orbit density [2]. These properties establish a natural connection between chaos and traditional cryptography, resulting in wide application in various fields such as S-box design [3, 4] and information hiding [5, 6]. At present, more than 32% of image encryption algorithms are designed based on chaos theory. Chaotic image encryption algorithms offer confidentiality protection for sensitive images in a variety of fields, such as e-medicine, military reconnaissance, remote sensing mapping, etc., thus avoiding the security risks associated with leaks of private information and misuse of data.
The fundamental prerequisite for the design of chaotic image encryption algorithms is the establishment of chaotic systems with excellent dynamic behavior. Chaotic systems are classified into two types: continuous chaotic systems and discrete chaotic systems. Currently, researchers mainly focus on continuous chaotic systems. For example, Yang et al. [7] designed a fractional-order hyperchaotic system based on the Lorenz system and analyzed the dynamical behavior of this system in detail using the Adomian decomposition method. Ma et al. [8] presented a multi-stable chaotic system with coexisting attractors by tuning the offset operation. However, continuous chaotic systems are inefficient due to the necessity of using time-consuming numerical analysis methods, like the Runge–Kutta method or the Adomian decomposition method, to generate chaotic sequences [9]. Discrete chaotic systems have proven to be more efficient than continuous chaotic systems, and a variety of classical chaotic maps, such as the Logistic map and the Tent map, have been successively introduced. However, Hua et al. [10] pointed out that the structure of these chaotic maps is relatively simple. In general, high-dimensional discrete chaotic systems are more likely to produce hyperchaotic attractors, which implies better chaotic properties. Choi et al. [11] constructed generalized high-dimensional Arnold systems using the Laplace theorem. Hua et al. [12] constructed high-dimensional discrete chaotic systems by composing classical low-dimensional discrete chaotic systems. Through rigorous theoretical analysis, Liu et al. [13] demonstrated that the third-order nonlinear filter can exhibit strong chaotic behavior if its system parameters are chosen appropriately. Unfortunately, the limited number of positive LE in the mentioned discrete chaotic systems is significantly lower than their dimensions, making them susceptible to chaotic degradation during digitization. To tackle this issue, Hua et al. [14] first discussed the internal relationship between the number of positive LE and the Arnold parameter matrix. Then, they presented a high-dimensional discrete chaotic system with an arbitrary number of positive LE. Wang et al. [15] and Zang et al. [16] designed non-degenerate discrete chaotic systems by using the chaotic inverse control method and the strict diagonal occupation matrix respectively. Liu et al. [17] also proposed a non-degenerate discrete chaotic system with uniform trajectories using nonlinear filters and the feed-forward and feed-back structure. Since the above discrete chaotic systems have a much greater number of positive LE compared to general chaotic systems, they are capable of displaying complex chaotic behavior. However, these systems do not exhibit multi-stability, which means that they are unable to switch freely between various steady states to meet diverse demands. Qin [18] pointed out that chaotic systems with more equilibrium points may contain more attractors, resulting in different coexisting attractors. Due to the inherent nonlinearity and periodicity of trigonometric functions, researchers have recently begun to investigate the design of multi-stable chaotic systems using them [19]. For example, Ali et al. [20] constructed a novel chaotic map using two sine functions with irrational frequency ratios but comparable amplitude and phase, and found coexisting attractors. Huang et al. [21] proposed a three-dimensional (3D) multi-stable hyperchaotic map with a concise symmetric structure. Furthermore, memristors are employed to enhance the dynamic behavior of multi-stable chaotic systems due to their distinctive nonlinear characteristics [22]. Ma et al. [23] designed a memristive chaotic system that has infinite equilibrium points and can exhibit seven different types of attractors. Liu et al. [24] and Marco et al. [25] proposed a class of discrete multi-stable chaotic systems using discrete memristors, respectively. However, these chaotic systems do not meet the non-degeneracy requirement and remain susceptible to chaotic degradation.
Chaos theory offers a plethora of beneficial insights for the design of image encryption algorithms. In 1989, Matthews et al. put forward the first chaotic image encryption algorithm using the Logistic map. Subsequently, Li et al. [26] constructed a key stream generator using the Tent map and applied it to the design of a stream cipher algorithm that is suitable for image confidentiality protection. Sang et al. [27] generated cipher images with excellent statistical features by scrambling plain images using the Logistic map and incorporating uniform distribution constraints to the training of deep auto-encoder. However, the above image encryption algorithms suffer from potential security risks due to the simple structure of the chaotic maps they use. In response to the above problem, Lai et al. [28] designed a novel neuron model with significant chaotic properties and applied it to the design of image encryption algorithms. Wang et al. [29] first designed a hyperchaotic system with complex chaotic behavior based on the Lorenz system and then proposed a color image encryption algorithm by combining the chaotic system and deoxyribonucleic acid (DNA) coding. Hua et al. [30] put forward an image encryption algorithm using a novel Logistic-Sine-coupling chaotic system. Javeed et al. [31] put forward an image encryption algorithm using the Rabinovich-Fabricant chaotic system. The above research has contributed to the research progress in the field of chaotic image encryption. However, none of the above chaotic systems are non-degeneracy, which may lead to security risks in image encryption algorithms due to chaotic degradation. To overcome this drawback, Wen et al. [32] and Wang et al. [33] proposed plaintext-related chaotic image encryption algorithms using non-degenerate discrete chaotic systems and the hash values of plain images, respectively. However, the derived key in the above algorithm is strongly linked to the hash values of plain images, making even a slight alteration in the hash value during transmission could result in decryption failure. Thus, how to securely transmit the hash value of a plain image limits the application of such image encryption algorithms.
Although chaotic cryptography has achieved several important research results after years of development, the existing chaotic systems are susceptible to chaotic degradation and generally do not exhibit multi-stability, and the current chaotic image encryption algorithms suffer from low efficiency in encryption and decryption and inadequate security measures. As such, existing research faces challenges in meeting the criteria for safeguarding the confidentiality of sensitive images In conclusion, there is still considerable research value in investigating non-degenerate multi-stable discrete chaotic systems and applying them to the design of effective image encryption algorithms.
The remainder of this paper is structured as follows. Section 2 presents a non-degenerate multi-stable discrete chaotic system that is analyzed through theoretical analysis and simulation experiments. In Sect. 3, we propose an image encryption algorithm based on non-degenerate multi-stable discrete chaos, and its performance is evaluated. Section 4 concludes this paper.
2 Non-degenerate multi-stable discrete chaotic system
In this section, we design a discrete chaotic system called NMDCS. Rigorous theoretical analyses and simulation experiments demonstrate that the NMDCS exhibits multi-stability and is not prone to chaotic degradation.
2.1 Mathematical expression of our discrete chaotic system
The mathematical model of N-dimensional NMDCS is described by Eq. (1), whose block diagram is shown in Fig. 1.
where \(a = \frac{b}{{2 \cdot c}}\) is the system parameter, \(b,c \in \mathbb {Z} \backslash \left\{ 0 \right\} \) are coprime, \(\left| b \right| > 6 \cdot \left| c \right| \), \(\left\{ {{x_{1,t}},{x_{2,t}}, \cdots ,{x_{N-1,t}}} \right\} \in {I}\) and \({x_{N,t}} \in {I^*}\) are the chaotic state variables at moment t, \(I = \left[ { - 1,1} \right] \) and \({I^*} = \left[ { - 1 {+} k \cdot b {+} {\varepsilon _1},1 {+} k \cdot b {+} {\varepsilon _2}} \right] \) are the chaotic intervals, \(k \in \mathbb {Z}\), and the absolute values of \({\varepsilon _1}\) and \({\varepsilon _2}\) are far less than 1.
2.2 Theoretical analysis of our discrete chaotic system
In this section, we prove that the NMDCS system has unstable fixed points, and is not susceptible to chaotic degradation.
2.2.1 Fixed points analysis
According to Eq. (1), the fixed point equation of our NMDCS system can be derived as Eq. (2).
Obviously, Eq. (2) has an infinite number of solutions. Therefore, the fixed points of the NMDCS system can be expressed as \(X = \left\{ {0,0, \cdots ,0,k \cdot b} \right\} \).
The Jacobian matrix of Eq. (2) at X is described by Eq. (3).
The characteristic polynomial of Eq. (3) is defined by Eq. (4).
According to Eq. (4), we can derive the eigenvalues as Eq. (5).
where \({i^2} = - 1\).
It is clear that there must be eigenvalues with zero or positive real parts, which means that the fixed point X may be critically stable or unstable.
2.2.2 Non-degenerate analysis
In this section, we analyze the trajectories of our NMDCS system using the following lemmas. Afterwards, we prove that the NMDCS system is a non-degenerate chaotic system using the above lemmas.
Lemma 1
If \({x_{n,0}}\) follows the uniform distribution in the interval I, the probability density function of \({x_{n,1}} = f\left( {{x_{n,0}}} \right) = \sin \left( {\pi \cdot {x_{n,0}}} \right) \) can be derived as \(p\left( {{x_{n,1}}} \right) = \left\{ {\begin{array}{*{20}{l}} {\frac{1}{{\pi \sqrt{1 - x_{n,1}^2} }},\mathrm{{ }}if\mathrm{{ }}{x_{n,1}} \in I}\\ {0,\mathrm{{ }}others} \end{array}} \right. \), where \(n \in \left\{ {1,2, \ldots ,N} \right\} \).
Proof
Since \({x_{n,0}}\) follows the uniform distribution in the interval I, its probability density function is \(p\left( {{x_{n,0}}} \right) = \left\{ {\begin{array}{*{20}{c}} {\frac{1}{2},\mathrm{{ }}if \mathrm{{ }}{x_{n,0}} \in I}\\ {0,\mathrm{{ }}others} \end{array}} \right. \). Divide the interval I into a series of subintervals \({I_l} = \left[ {\frac{{l - 1}}{2},\frac{l}{2}} \right) \), where \(l \in \left\{ { - 1,0,1,2} \right\} \). Let \(h\left( {{x_{n,1}}} \right) \) be the inverse function of \(f\left( {{x_{n,0}}} \right) \), whose expression is shown in Eq. (6).
According to Eq. (6), the probability density function of \({x_{n,1}} = f\left( {{x_{n,0}}} \right) \) can be derived as Eq. (7).
Lemma 1 is thus proved. \(\square \)
Lemma 2
If \({x_{n,0}}\) follows the uniform distribution in the interval I, the probability density function of \({x_{n,2}} = {f}\left( {{f}\left( {{x_{n,0}}} \right) } \right) = \sin \left( {\pi \cdot \sin \left( {\pi \cdot {x_{n,0}}} \right) } \right) \) can be derived as \(p\left( {{x_{n,2}}} \right) = \left\{ \begin{array}{*{20}{lll}} \frac{1}{{\pi \sqrt{1 - x_{n,2}^2} }} \cdot \sum \nolimits _{i = 0, 1}\\ {\frac{1}{{\sqrt{{\pi ^2} - {{\left( {\arcsin \left| {{x_{n,2}}} \right| - i \cdot \pi } \right) }^2}} }}} ,\mathrm{{ }}if\mathrm{{ }}{x_{n,2}} \in I\\ {0,\mathrm{{ }}others} \end{array} \right. \), where \(n \in \left\{ {1,2, \ldots ,N} \right\} \).
Proof
Divide the interval I into a series of subintervals \({I_l} = \left[ {\frac{{l - 1}}{2},\frac{l}{2}} \right) \), where \(l \in \left\{ { - 1,0,1,2} \right\} \). Let \(h\left( {{x_{n,2}}} \right) \) be the inverse function of \(f\left( {{x_{n,1}}} \right) \), whose expression is listed in Eq. (8).
From Eq. (8), the probability density function of \({x_{n,2}} = f\left( {{x_{n,1}}} \right) \) can be derived as Eq. (9).
Lemma 2 is thus proved. \(\square \)
Theorem 1
The NMDCS system is a non-degenerate discrete chaotic system.
Proof
From Eq. (1), the Jacobian matrix of the NMDCS system at moment t is shown in Eq. (10).
Where \(f^\prime \left( {{x_{n,t}}} \right) = \pi \cdot \cos \left( {\pi \cdot {x_{n,t}}} \right) \) and \(n \in \left\{ {1,2, \ldots ,N} \right\} \). The characteristic polynomial of (10) can be derived as (11).
As is shown in Sect. 2.1, it is clear that \(\left| a \right| > 3\). Thus, we can derive Eq. (12) from Eq. (11).
According to Eq. (12), we can derive the eigenvalues as Eq. (13).
From Eq. (13) and Lemma 2, we can derive the LE of our NMDCS system as \(\left\{ {L{E_1}, \cdots ,L{E_n}, \cdots ,L{E_N}} \right\} \), where \(L{E_n}\) is calculated by Eq. (14).
In conclusion, the LE of the NMDCS system are all 0.6672, indicating that our NMDCS system is a non-degenerate discrete chaotic system. \(\square \)
2.3 Simulation experiments of our discrete chaotic system
This section demonstrates that our NMDCS system shows excellent chaotic behavior from the aspects of LE, coexisting attractors, Poincaré section, sensitive dependence on initial conditions, and iterative efficiency. Our experiments were conducted on a Windows machine running on an Intel Core i5-6300HQ and 12 GB RAM.
2.3.1 Lyapunov exponent spectrum
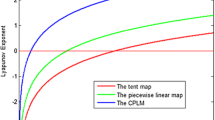
LE is always used to measure the rate of convergence or divergence of adjacent trajectories of a dynamical system. A positive LE means that the system stays in a chaotic state. If there are more than two positive LEs, the chaotic map becomes hyper-chaos and exhibits complex chaotic behavior in multiple dimensions. This section conducts simulation experiments to estimate the LE of the NMDCS, and the experimental results are shown in Fig. 2.
As is shown in Fig. 2, the number of positive LE of our NMDCS system is equal to its dimension, regardless of the selection of the system parameter a. Additionally, the LE values are all very close to the theoretical value of 0.6672 derived from Theorem 1. Therefore, the NMDCS system is a non-degenerate discrete chaotic system with stronger chaotic behavior than most of the existing chaotic systems, and is not prone to chaotic degradation during digitization.
2.3.2 Coexisting attractor analysis
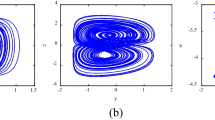
Due to the periodic properties of trigonometric functions, the position of the attractor of the NMDCS system depends on the initial state \({x_{N,0}}\), which means that our NMDCS system has coexisting attractors. This behavior is very interesting, and next we will draw the phase diagrams of the NMDCS system by selecting different \({x_{N,0}}\) to understand this phenomenon more intuitively. The simulation results are listed in Fig. 3.
From Fig. 3, it is obvious that the coexisting attractors of the NMDCS system are all square or cube, regardless of the initial state, which means that these coexisting attractors are all homogeneous. This is because although the initial states between different coexisting attractors are completely different, 2a and 4a are the period of the nonlinear term \(\sin \left( {\frac{{\pi \cdot {x_{N,t}}}}{a}} \right) \) in Eq. (1) respectively, so there will be no significant difference in the shape of the coexisting attractors.
2.3.3 Efficiency analysis
Efficiency is a crucial factor in assessing the practicality of chaotic systems. This section examines the effectiveness of chaotic systems through the symbol transfer rate. During the analysis, each chaotic system generated 320 Mbit of chaotic sequences. Table 1 shows the results of the efficiency analysis.
As demonstrated in Table 1, the efficiency of our NMDCS exceeds that of the chaotic systems in [18, 34, 35]. This is because chaotic systems in [18, 34, 35] necessitate the utilization of time-consuming numerical analysis techniques, such as the Runge–Kutta method, throughout the iterative process. Although the efficiency of the NMDCS may not be on par with the chaotic systems described in [16, 24] due to the use of slightly time-consuming trigonometric function operations, it still achieves a symbol transmission rate of 53.2595 Mbps. Therefore, we can conclude that our NMDCS exhibits a commendable level of efficiency.
2.3.4 Poincaré section analysis
The Poincaré section is always used to analyze the dynamical behavior of multivariate autonomous systems. If there are only a few points on the Poincaré section, the motion is periodic. Otherwise, if there is a closed curve on the Poincaré section, the motion is determined to be quasi-periodic. When there are patches of dense points on the Poincaré section, the motion is assumed to be chaotic. This section sets various system parameters, and the Poincare section of our NMDCS system is shown in Fig. 4.
As is shown in Fig. 4, it can be seen that although the system parameters of the NMDCS are different, there are patches of dense points distributed on each Poincaré section. The above results further indicate that our NMDCS is chaotic.
2.3.5 Sensitivity to initial conditions
Initial condition sensitivity is the most essential property of chaotic systems, reflecting the inherent randomness of chaotic systems. Initial condition sensitivity refers to the fact that tiny differences between the initial states of a chaotic system will result in completely different trajectories, indicating that the long-term motion state of a chaotic system is unpredictable. In this section, different system parameters are selected to test the initial condition sensitivity of our NMDCS system, and the results are shown in Fig. 5.
As is shown in Fig. 5, it is obvious that slight changes between the initial values will cause our chaotic system to exhibit completely different trajectories. Therefore, our NMDCS system is highly sensitive to initial conditions and is particularly suitable for the design of cryptographic algorithms.
3 Image encryption algorithm based on non-degenerate multi-stable discrete chaos
Since our NMDCS system is not susceptible to chaotic degradation and has an infinite number of coexisting attractors, the chaotic system is used to design an efficient and secure image encryption algorithm.
3.1 Overall flow of the algorithm
Our image encryption algorithm based on non-degenerate multi-stable discrete chaos (IEA-NMDCS) mainly involves four steps of key derivation, pixel confusion, adaptive zigzag transformation, and cross-plane permutation, and its block diagram is shown in Fig. 6.
3.1.1 Key derivation
Our key derivation algorithm takes the 144-bit master key \(MK = M{K_1}||\) \(M{K_2}||M{K_3}\) as input to generate the derived keys \(S{K_1},S{K_2}\) for subsequent encryption and decryption operations, where the lengths of \(M{K_1},M{K_2},M{K_3}\) are all 48-bit, and || represents the link symbol. The procedure of the algorithm is shown in Algorithm 1.
-
(1)
It calculates the chaotic initial state \(IV = {\left\{ {I{V_i}} \right\} _{i \in \left\{ {1,2,3} \right\} }}\), where \(I{V_i} = \frac{{M{K_i}}}{{{2^{47}}}} - 1\).
-
(2)
It generates a chaotic sequence Q of size \(R \times C \times 3\) by iterating NMDCS according to IV.
-
(3)
It quantifies the chaotic sequence Q using Eq. (15).
$$\begin{aligned} DQ = \mathrm{{floor}}\left( {Q \times {{10}^{15}}} \right) \end{aligned}$$(15) -
(4)
It computes the confusion key \(S{K_1} = \left\{ {S{K_1}\left( {r,c,d} \right) } \right\} _{r \in \left\{ {1, \cdots ,R} \right\} ,c \in \left\{ {1, \cdots ,C} \right\} ,d \in \left\{ {1,2,3} \right\} }\), where \(S{K_1}\left( {r,c,d} \right) \) is computed using Eq. (16).
$$\begin{aligned} S{K_1}\left( {r,c,d} \right) = \bmod \left( {DQ\left( {r,c,d} \right) ,256} \right) \end{aligned}$$(16) -
(5)
It computes the cross-plane key \(S{K_2} = {\left\{ {S{K_2}\left( {r,c,d} \right) } \right\} _{r \in \left\{ {1, \cdots ,R} \right\} ,c \in \left\{ {1, \cdots ,C} \right\} ,d \in \left\{ {1,2} \right\} }}\), where \(S{K_2}\left( {r,c,d} \right) \) is computed using Eq. (17).
$$\begin{aligned} S{K_2}\left( {r,c,d} \right) = \bmod \left( {DQ\left( {r,c,d} \right) ,D - d + 1} \right) + 1\nonumber \\ \end{aligned}$$(17)
3.1.2 Pixel confusion
Confusion is a nonlinear transformation that intricately disrupts the correlation between plain images and cipher images as well as between key and cipher images by changing pixels. In this section, the S-Box in [9] is used as the nonlinear confusion component to enhance the probabilistic statistical analysis resistance of our IEA-NMDCS algorithm, and the specific process is shown in Algorithm 2.
3.1.3 Adaptive zigzag transformation
The correlation between neighboring pixels of a plain image can be effectively eliminated using the zigzag transformation. However, the initial position of the traditional zigzag transformation remains unaffected by the plain images, so minor alterations in a plain image will not transmit to the whole cipher image, resulting in its limited diffusion capability. To address the above problem, this section uses the mean value of the pixels and our NMDCS system to design a novel adaptive zigzag transformation that can improve the diffusion capability of our IEA-NMDCS algorithm while eliminating the correlation of neighboring pixels. The details are shown in Fig. 7.
-
(1)
It calculates the average value of the pixels in each plane of the cipher image and records them as \({\left\{ {{e_d}} \right\} _{d \in \left\{ {1,2,3} \right\} }}\).
-
(2)
It calculates the chaotic initial state \({\varvec{x}^0} = {\left\{ {x_d^0} \right\} _{d \in \left\{ {1,2,3} \right\} }}\) by Eq. (18).
$$\begin{aligned} x_d^0 = \frac{{{e_d}}}{{128}} - 1 \end{aligned}$$(18) -
(3)
It generates a chaotic sequence of length \(T + 2\) using the NMDCS system, and records the last two chaotic states as \({\varvec{x}^{T + 1}} = {\left\{ {x_d^{T + 1}} \right\} _{d \in \left\{ {1,2,3} \right\} }}\), and \({\varvec{x}^{T + 2}} = {\left\{ {x_d^{T + 2}} \right\} _{d \in \left\{ {1,2,3} \right\} }}\).
-
(4)
It calculates the initial coordinates of the rows and columns using Eqs. (19) and (20), and records them as \({\varvec{r}^0} = {\left\{ {r_d^0} \right\} _{d \in \left\{ {1,2,3} \right\} }}\) and \({\varvec{c}^0} = {\left\{ {c_d^0} \right\} _{d \in \left\{ {1,2,3} \right\} }}\) respectively.
$$\begin{aligned} r_d^0 = mod\left( {floor\left( {x_d^{T + 1} \times {{10}^{15}}} \right) ,R} \right) + 1 \end{aligned}$$(19)$$\begin{aligned} c_d^0 = mod\left( {floor\left( {x_d^{T + 2} \times {{10}^{15}}} \right) ,C} \right) + 1 \end{aligned}$$(20) -
(5)
It performs a zigzag transformation on the cipher image starting at \({\varvec{r}^0} = {\left\{ {r_d^0} \right\} _{d \in \left\{ {1,2,3} \right\} }}\) and \({\varvec{c}^0} = {\left\{ {c_d^0} \right\} _{d \in \left\{ {1,2,3} \right\} }}\) respectively.
3.1.4 Cross-plane permutation
Due to color images consisting of three planes of red, green, and blue, the cross-plane permutation algorithm must be developed to remove the correlation of pixels across different planes. Our IEA-NMDCS algorithm uses the cross-plane permutation key and the shuffling algorithm to blur the pixels between different planes of the image. The specific process is shown in Fig. 8 and Algorithm 3.
3.2 Security and efficiency analysis
This section evaluates the performance of our IEA-NMDCS algorithm from the following aspects. The test images are all taken from the USC-SIPI database and the CVG-UGR database.
3.2.1 Key space analysis
Key space is an important indicator reflecting the resistance of encryption algorithms to brute force attacks. The larger the key space, the more difficult it is to obtain the correct key through brute forces. Typically, a key space of at least \(2 ^{100}\) possible secret keys is expected [36]. Since our IEA-NMDCS algorithm uses a 144-bit master key to generate derived subkeys, its key space is much larger than \(2^{100}\). The above results show that our IEA-NMDCS algorithm is sufficient to withstand brute force attacks.
3.2.2 NIST randomness test
The National Institute of Standards and Technology (NIST) provides a series of guidelines for statistical tests known as the NIST Test Suite 800-22. In this section, the randomness of the cipher images obtained using the IEA-NMDCS algorithm has been evaluated through the application of this test suite. The test results are shown in Table 2.
It can be clearly seen from Table 2 that the P-value and proportions are all greater than 0.01 and 0.96 respectively. Therefore, the cipher images obtained using the IEA-NMDCS algorithm exhibit excellent randomness.
3.2.3 Histogram analysis
The histogram of an image can intuitively reflect the distribution of image pixels. In general, the histogram of a plaint image does not follow the uniform distribution, so it is susceptible to probabilistic statistical analysis. For an optimal encryption algorithm, the cipher images encrypted using the algorithm ought to conform to the uniform distribution. Figure 9 displays the histogram test results for the plain images and their cipher images encrypted with the IEA-NMDCS algorithm.
As can be seen from Fig. 9, the histogram of the plaint image exhibits an uneven distribution, whereas the histogram of its cipher image is uniformly distributed, indicating that the cipher image does not leak any statistical information from the plain image.
To further demonstrate that the IEA-NMDCS algorithm can effectively withstand statistical analysis, we employ the chi-square test and the variance analysis to verify the uniformity of the histogram of the cipher images. The calculation methods for the chi-square test and the variance analysis are shown in Eq. (21) and [37], respectively.
where \({\eta _i}\) and \(\mu \) represent the number of observations and the expected number of each pixel in the image, respectively. We set a significance level \(\alpha = 0.05\), and determine the following hypotheses using the chi-square test and the variance analysis. The analysis results are listed in Table 3.
\(H_0\): The cipher images encrypted using the IEA-NMDCS algorithm are uniformly distributed.
\(H_1\): The cipher images encrypted using the IEA-NMDCS algorithm are not uniformly distributed.
From Table 3, the Chi-square test values for the cipher images encrypted with the IEA-NMDCS algorithm are all less than \(\chi _{0.05}^2\left( {255} \right) = 293.2478\). In addition, the histogram variance values of the \(512 \times 512 \times 3\) and \(256 \times 256 \times 3\) cipher images are approximately 3000 and 800, respectively. The above results indicate that the \(H_0\) assumption is correct. In conclusion, the cipher images generated by the IEA-NMDCS algorithm are uniformly distributed, so they can effectively resist statistical analysis.
3.2.4 Key sensitivity analysis
Key sensitivity refers to the fact that even minor alterations in the master key will produce an entirely different encryption or decryption result. A secure encryption algorithm must be sensitive to the master key. To test the key sensitivity of the IEA-NMDCS algorithm, we first randomly chose a master key \({K_1} = \mathrm{{c1e}}\underline{{\textbf {1}}} \mathrm{{bda054ebc9f6accfd2f7c5ca9783618}}\underline{{\textbf {2}}}\) of size 144-bit, and obtain the keys \({K_2} = \mathrm{{c1e1bda054ebc9f6a}} \mathrm{{ccfd2f7c5ca9783618}}\underline{{\textbf {0}}}\) and \({K_3} = \mathrm{{c1e}}\underline{{\textbf {0}}} \mathrm{{bda054ebc9f6acc}}\mathrm{{fd2f7c5ca97836182}}\) by randomly changing 1-bit of \(K_1\). Then,we encrypted and decrypted the images using \(K_1\), \(K_2\), and \(K_3\) respectively. The specific results are shown in Figs. 10 and 11.
Figure 10 demonstrates that although the plain images have specific statistical features, the cipher images encrypted with the IEA-NMDCS algorithm are similar to the random noise, and they are completely different when using different keys. Therefore, our IEA-NMDCS algorithm is sensitive to the master key during the encryption process.
Figure 11 clearly illustrates that only decrypting the cipher image with the correct key will obtain the corresponding plain image, while the images decrypted by incorrect keys are similar to random noises. Furthermore, the images decrypted by different wrong keys are completely different. Therefore, our IEA-NMDCS algorithm is responsive to the master key utilized in the decryption procedure.
3.2.5 Sensitivity analysis for plain images
Plaintext sensitivity refers to the capability of algorithms to withstand chosen plaintext attacks and differential attacks. Researchers commonly use the pixel change rate (NPCR) and normalized average change intensity (UACI) to assess the intensity of plaintext sensitivity. The calculation methods for these assessments are thoroughly described in [12]. The NPCR and UACI are anticipated to be 99.6094% and 33.4635% respectively. In addition, Wu et al. [38] have highlighted the necessity for NPCR values to surpass a defined threshold \({N_\alpha }\) and for UACI values to fall within the interval \(\left( {U_\alpha ^ -,U_\alpha ^ + } \right) \), where \({N_\alpha } = 99.5693\% \) and \(\left( {U_\alpha ^ -,U_\alpha ^ + } \right) = \left( {33.2824\%,33.6447\% } \right) \) for an image of size \(256 \times 256\), and \({N_\alpha } = 99.5893\% \) and \(\left( {U_\alpha ^ -,U_\alpha ^ + } \right) = \left( {33.3730\%,33.5541\% } \right) \) for an image of size \(512 \times 512\). The NPCR and UACI scores for the cipher images encrypted using the IEA-NMDCS algorithm are displayed in Tables 4 and 5 respectively.
As is evidenced by Tables 4 and 5, the NPCR and UACI scores for the cipher images encrypted using the IEA-NMDCS algorithm are all within the acceptable intervals, with values very close to 99.6094% and 33.4636% respectively. To further demonstrate the excellent plaintext sensitivity of our IEA-NMDCS algorithm, we use the ‘Lena’ as the plain image, and encrypt it using different image encryption algorithms. The NPCR and UACI comparison results can be found in Tables 6 and 7 respectively.
From Tables 6 and 7, the NPCR and UACI scores for the cipher images encrypted by different image algorithms are all within acceptable intervals, and the difference between them is very small, so they all achieve excellent plaintext sensitivity. However, the derived keys of the image encryption algorithms in [40, 41] associated with plain images, and how to securely transmit the information has become a critical security bottleneck that constrains the application of such image encryption algorithms. Therefore, it can be deduced that our IEA-NMDCS algorithm is capable of withstanding chosen plaintext attacks and differential attacks.
3.2.6 Relevance analysis
Generally, the adjacent pixels in a plain image are highly correlated with each other. An excellent image encryption algorithm should eliminate the correlation between adjacent pixels through substitution and permutation to enhance the pseudo-randomness of the cipher images. Consequently, the correlation between adjacent pixels becomes an essential indicator in the assessment of an algorithm’s security. The correlation coefficient R is calculated by Eq. (22).
where X denotes the set consisting of image pixels, Y denotes the set consisting of adjacent pixels of pixels in X, and n is the number of pixels. The lower the correlation coefficient, the lower the correlation between adjacent pixels. In this section, we randomly select 12,000 pairs of adjacent pixels to calculate the correlation coefficients in the horizontal, vertical, and diagonal directions. The details are displayed in Fig. 12 and Table 8.
As can be seen from Fig. 12 and Table 8, it is clear that the adjacent pixels of the plain images exhibit a high level of correlation, whereas the adjacent pixels of their cipher images display very low correlation. In addition, the correlation between the adjacent pixels of the cipher images encrypted using the IEA-NMDCS algorithm is very close to the ideal value of 0. To further prove that our algorithm can withstand statistical attacks, we performed correlation coefficient comparison tests for different image encryption algorithms. The comparison results are shown in Table 9.
As illustrated in Table 9, the correlation coefficients of the cipher image encrypted with our IEA-NMDCS algorithm are closer to 0 than those of existing image encryption algorithms. The aforementioned results demonstrate that our image encryption algorithm is capable of effectively reducing the correlation among the adjacent pixels of images.
3.2.7 Information entropy
In this section, we evaluate the pseudo-randomness of the cipher images using information entropy. Each pixel of an image contains 8 bits of information, so the theoretical maximum value of its information entropy is 8. Table 10 displays the information entropy values of the plain images and their cipher images encrypted using the IEA-NMDCS algorithm.
From Table 10, it can be seen that although the information entropy of the plain images is far less than the ideal value of 8, the information entropy of the cipher images encrypted with the IEA-NMDCS algorithm is very close to 8, indicating that the cipher images are uniformly distributed and have excellent pseudo-randomness. To further evaluate the encryption effect of the IEA-NMDCS algorithm, we encrypted the Lena image using the existing image encryption algorithms as well as our algorithm, and the information entropy values of the cipher images are listed in Table 11.
From Table 11, the information entropy values of the cipher image encrypted with our IEA-NMDCS algorithm are 7.9993, 7.9994, and 7.9994 respectively, which are better than those of existing image encryption algorithms except [12, 41]. Thus, it can be concluded that our IEA-NMDCS algorithm can generate the cipher images with a uniform distribution that is highly resistant to probabilistic statistical analysis.
3.2.8 Efficiency analysis
Efficiency is a crucial factor in evaluating the practicality of image encryption algorithms. Because decryption is the reverse process of encryption, it has the same algorithmic efficiency as encryption, this section only lists the comparison results of the encryption efficiency between the IEA-NMDCS algorithm and existing image encryption algorithms in Table 12.
From Table 12, it can be seen that the IEA-NMDCS algorithm is more efficient in encryption than the existing image encryption algorithms. This is mainly because our IEA-NMDCS algorithm does not require time-consuming numerical analysis methods to generate pseudo-chaotic sequences. Furthermore, it possesses efficient substitution and permutation operations.
4 Conclusion
This paper first designs a non-degenerate multi-stable discrete chaotic system that can be demonstrated to exhibit the properties of multi-stability and non-degeneracy through rigorous theoretical analysis. Simulation experiments demonstrate that our discrete chaotic system exhibits strong chaotic behavior and high efficiency in terms of Lyapunov exponents, coexisting attractors, Poincaré sections, sensitivity to initial conditions, and iterative efficiency. Then, an efficient image encryption algorithm is proposed by combining the aforementioned discrete chaotic system and an adaptive zigzag transformation method. Simulation experiments show that our image encryption algorithm offers superior performance in terms of encryption and decryption efficiency, as well as impressive security properties, including histogram, key sensitivity, plaintext sensitivity, correlation between adjacent pixels, and information entropy. The proposed image encryption algorithm provides a robust foundation for the confidentiality protection of sensitive images in key industries, including government agencies, healthcare systems and financial institutions. In the future, we will design chaotic image compression and encryption algorithms based on the compressed perception theory, which can reduce the storage and transmission costs of sensitive images as well as ensure their confidentiality.
Data availibility
The data that support the findings of this study are available from the corresponding author upon reasonable request.
References
Hussain, S., Shah, T., Javeed, A.: Modified advanced encryption standard (MAES) based on non-associative inverse property loop. Multimed. Tools Appl. 82(11), 16237–16256 (2023)
Liu, X., Tong, X., Wang, Z., Zhang, M., Fan, Y.: A novel devaney chaotic map with uniform trajectory for color image encryption. Appl. Math. Model. 120, 153–174 (2023)
Liu, H., Kadir, A., Xu, C.: Cryptanalysis and constructing s-box based on chaotic map and backtracking. Appl. Math. Comput. 376(1), 125153 (2020)
Jamal, S.S., Hazzazi, M.M., Khan, M.F., Bassfar, Z., Aljaedi, A., ul Islam, Z.: Region of interest-based medical image encryption technique based on chaotic s-boxes. Expert Syst. Appl. 238, 122030 (2024)
Wang, X., Liu, C., Jiang, D.: A novel visually meaningful image encryption algorithm based on parallel compressive sensing and adaptive embedding. Expert Syst. Appl. 209, 118426 (2022)
Ye, G., Du, S., Huang, X.: Image compression-hiding algorithm based on compressive sensing and integer wavelet transformation. Appl. Math. Model. 124, 576–596 (2023)
Yang, F., Mou, J., Liu, J., Ma, C., Yan, H.: Characteristic analysis of the fractional-order hyperchaotic complex system and its image encryption application. Signal Process. 169, 107373 (2020)
Ma, C., Mou, J., Xiong, L., Banerjee, S., Liu, T., Han, X.: Dynamical analysis of a new chaotic system: asymmetric multistability, offset boosting control and circuit realization. Nonlinear Dyn. 103, 2867–2880 (2021)
Liu, X., Tong, X., Wang, Z., Zhang, M.: Uniform non-degeneracy discrete chaotic system and its application in image encryption. Nonlinear Dyn. 108(1), 653–682 (2022)
Hua, Z., Zhou, B., Zhou, Y.: Sine-transform-based chaotic system with FPGA implementation. IEEE Trans. Industr. Electron. 65(3), 2557–2566 (2017)
Choi, U.S., Cho, S.J., Kim, J.G., Kang, S.W., Kim, H.D.: Color image encryption based on programmable complemented maximum length cellular automata and generalized 3-D chaotic cat map. Multimed. Tools Appl. 79, 22825–22842 (2020)
Hua, Z., Zhu, Z., Yi, S., Zhang, Z., Huang, H.: Cross-plane colour image encryption using a two-dimensional logistic tent modular map. Info. Sci. 546, 1063–1083 (2021)
Liu, X., Tong, X., Wang, Z., Zhang, M.: Efficient high nonlinearity s-box generating algorithm based on third-order nonlinear digital filter. Chaos, Solitons & Fractals 150, 111109 (2021)
Hua, Z., Yi, S., Zhou, Y., Li, C., Wu, Y.: Designing hyperchaotic cat maps with any desired number of positive lyapunov exponents. IEEE Trans. Cybern. 48(2), 463–473 (2017)
Wang, C., Fan, C., Ding, Q.: Constructing discrete chaotic systems with positive lyapunov exponents. Int. J. Bifurc. Chaos 28(07), 1850084 (2018)
Zang, H., Liu, J., Li, J.: Construction of a class of high-dimensional discrete chaotic systems. Mathematics 9(4), 365 (2021)
Liu, X., Tong, X., Zhang, M., Wang, Z., Fan, Y.: Image compression and encryption algorithm based on uniform non-degeneracy chaotic system and fractal coding. Nonlinear Dyn. 111(9), 8771–8798 (2023)
Qin, M.: Yet new extreme multistable chaotic system. IEEE Trans. Circuits Syst. II: Expr. Br. 70(8), 3124–3128 (2023)
Sriram, G., Ali, A.M.A., Natiq, H., Ahmadi, A., Rajagopal, K., Jafari, S.: Dynamics of a novel chaotic map. J. Comput. Appl. Math. 436, 115453 (2024)
Ali, A.M.A., Sriram, S., Natiq, H., Ahmadi, A., Rajagopal, K., Jafari, S.: A novel multi-stable sinusoidal chaotic map with spectacular behaviors. Commun. Theor. Phys. 75(11), 115001 (2023)
Huang, L., Li, C., Liu, J., Zhong, Y., Zhang, H.: A novel 3D non-degenerate hyperchaotic map with ultra-wide parameter range and coexisting attractors periodic switching. Nonlinear Dyn. 112(3), 2289–2304 (2024)
Yang, L., Lai, Q.: Construction and implementation of discrete memristive hyperchaotic map with hidden attractors and self-excited attractors. Integration 94, 102091 (2024)
Ma, X., Mou, J., Xiong, L., Banerjee, S., Cao, Y., Wang, J.: A novel chaotic circuit with coexistence of multiple attractors and state transition based on two memristors. Chaos, Solitons & Fractals 152, 111363 (2021)
Liu, X., Sun, K., Wang, H., He, S.: A class of novel discrete memristive chaotic map. Chaos, Solitons & Fractals 174, 113791 (2023)
Di Marco, M., Forti, M., Pancioni, L., Tesi, A.: New class of discrete-time memristor circuits: First integrals, coexisting attractors and bifurcations without parameters. Int. J. Bifurc. Chaos 34(01), 2450001 (2024)
Li, C., Luo, G., Qin, K., Li, C.: An image encryption scheme based on chaotic tent map. Nonlinear Dyn. 87, 127–133 (2017)
Sang, Y., Sang, J., Alam, M.S.: Image encryption based on logistic chaotic systems and deep autoencoder. Pattern Recognit. Lett. 153, 59–66 (2022)
Lai, Q., Lai, C., Zhang, H., Li, C.: Hidden coexisting hyperchaos of new memristive neuron model and its application in image encryption. Chaos, Solitons & Fractals 158, 112017 (2022)
Wang, S., Peng, Q., Du, B.: Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Optics Laser Technol. 148, 107753 (2022)
Hua, Z., Jin, F., Xu, B., Huang, H.: 2D logistic-sine-coupling map for image encryption. Signal Process. 149, 148–161 (2018)
Javeed, A., Shah, T., Ullah, A.: A color image privacy scheme established on nonlinear system of coupled differential equations. Multimed. Tools Appl. 79(43), 32487–32501 (2020)
Wen, H., Liu, Z., Lai, H., Zhang, C., Liu, L., Yang, J., Lin, Y., Li, Y., Liao, Y., Ma, L., et al.: Secure DNA-coding image optical communication using non-degenerate hyperchaos and dynamic secret-key. Mathematics 10(17), 3180 (2022)
Wang, M., Liu, H., Zhao, M.: Construction of a non-degeneracy 3D chaotic map and application to image encryption with keyed s-box. Multimed. Tools Appl. 82(22), 34541–34563 (2023)
Ye, X., Wang, X.: Hidden oscillation and chaotic sea in a novel 3D chaotic system with exponential function. Nonlinear Dyn. 111(16), 15477–15486 (2023)
Yang, Y., Huang, L., Kuznetsov, N.V., Lai, Q.: Design and implementation of grid-wing hidden chaotic attractors with only stable equilibria. IEEE Trans. Circuits Syst. I: Regul. Pap. 70(12), 5408–5420 (2023)
Wu, Y., Zhang, L., Berretti, S., Wan, S.: Medical image encryption by content-aware DNA computing for secure healthcare. IEEE Trans. Industr. Info. 19(2), 2089–2098 (2022)
Javeed, A., Shah, T., et al.: Lightweight secure image encryption scheme based on chaotic differential equation. Chin. J. Phys. 66, 645–659 (2020)
Wu, Y., Noonan, J.P., Agaian, S., et al.: NPCR and UACI randomness tests for image encryption. Cyber J.: Multidiscipl. J. Sci. Technol. J. Selected Areas Telecommun. (JSAT) 1(2), 31–38 (2011)
Wang, X., Gao, S.: Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a boolean network. Info. Sci. 539, 195–214 (2020)
Gao, X., Sun, B., Cao, Y., Banerjee, S., Mou, J.: A color image encryption algorithm based on hyperchaotic map and DNA mutation. Chin. Phys. B 32(3), 030501 (2023)
Hosny, K.M., Kamal, S.T., Darwish, M.M.: A novel color image encryption based on fractional shifted gegenbauer moments and 2D logistic-sine map. Vis. Comput. 39(3), 1027–1044 (2023)
Alawida, M., Samsudin, A., Teh, J.S., Alkhawaldeh, R.S.: A new hybrid digital chaotic system with applications in image encryption. Signal Process. 160, 45–58 (2019)
Zhou, Y., Hua, Z., Pun, C.M., Chen, C.P.: Cascade chaotic system with applications. IEEE Trans. Cybern. 45(9), 2001–2012 (2014)
Hua, Z., Zhou, Y.: Design of image cipher using block-based scrambling and image filtering. Info. Sci. 396, 97–113 (2017)
Funding
This work was supported by the following projects and foundations: Project ZR2019MF054 supported by Shandong Provincial Natural Science Foundation, National Natural Science Foundation of China (Grant No.61902091).
Author information
Authors and Affiliations
Contributions
Xiaojun Tong: Supervision, Writing review & editing, Funding Acquisition. Xudong Liu: Conceptualization, Methodology, Software, Writing original draft. Miao Zhang: Investigation. Zhu Wang: Validation. Yunhua Fan: Data curation.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no Conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Tong, X., Liu, X., Zhang, M. et al. Non-degenerate multi-stable discrete chaotic system for image encryption. Nonlinear Dyn 112, 20437–20459 (2024). https://doi.org/10.1007/s11071-024-10083-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11071-024-10083-2