Abstract
This paper presents a dual watermarking technique using discrete wavelet transform (DWT), singular value decomposition (SVD) and set partitioning in hierarchical tree (SPIHT). The method uses second level DWT to transform the host image in to different frequency components. Next, we further transform the selected wavelet component via SVD. Before embedding, the logo watermark is secured via Arnold transform and signature watermark are encoded by hamming code. Finally, we embed both encoded watermarks into the transformed host image via an embedding approach. The watermarked image is further compress by SPIHT scheme along with the location key. With our scheme, maximum PSNR, NC and SSIM are obtained as 36.97 dB, 0.9965 and 0.9974, respectively. However best obtained BER is zero. Experimental results on various images demonstrate the importance of our scheme and superior to competing methods.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Nowadays massive amount of digital data is generated, copied, shared and transmitted as a result of growth in information and communication technology (ICT) [4, 17]. Secure transmission of digital data is still one of the major issues related with it. So, some scheme is needed to secure the digital data transmission/storage/sharing via open networks. One of the popular schemes to provide security of the contents from illegal users is digital watermarking [4, 7, 17, 20, 22]. The technique used to embed secret data imperceptibly into multimedia cover for the purpose of content authentications, annotation, ownership and copyright protection. However, it has also been applied to many other applications [4, 5, 17, 20]. Digital watermarking is used for last several years and it is an emerging area of research [4]. Various remarkable watermarking schemes have been introduced for prevention of identity theft and copyright protection. However, recent researches try to optimize the balance between contradictory factors of watermarking that motivate the necessary and continuous research in this area [1, 5, 17, 20].
Further, single watermarking techniques are able to achieve limited goals such as protection of single owner. However, to achieve better security some applications require copyright protection of several owners in multiple levels. So, dual watermarking is proved to be beneficial for protection and validate the integrity of contents [17]. There are three methods for securing images using dual watermarking. In first scheme, dual-watermark (one watermark embedded into another watermark) is embedded into cover image. In second method, primary and secondary watermarked images are generated by embedding watermark one after another respectively. In third technique, multiple watermarks are embedded simultaneous into cover image. Dual watermarking is helpful in various potential applications [3, 11, 21].
In the direction described above, we propose a DWT-SVD based robust and imperceptible dual watermarking for digital image. An encoded signature and scrambled logo watermark is simultaneously placed inside the cover for copyright protection and image validation, respectively. After embedding, the watermarked image is compressed by SPIHT scheme for efficient transmission and reduces storage need. Major contributions of our work as follows:
Fusion of DWT-SVD: Due to extraordinary properties of DWT [15], it is the best choice for any researchers in watermarking domain. Further, excellent energy compaction properties and good stability make the SVD more popular for watermarking applications. It is established that DWT-SVD based watermarking schemes achieved better robustness as compared to applied separately [2, 9]. Therefore, the proposed method uses fusion of DWT-SVD to improve the robustness against attacks and preserves imperceptibility.
Compress image via SPIHT: Our method uses fast and efficient SPIHT compression scheme to compress the watermarked image for efficient transmission and reduce storage requirement [12]. Further, this scheme added the flexibility to improve the performance (see Table 2) by setting an appropriate bit rate.
Imperceptibly embeds encoded dual watermarks: To improve the security and reduce the bandwidth need, the method imperceptibly hides multi-watermarks inside the cover image. Further, our scheme is directly embedding the image watermark (instead of singular value of the watermark) in to the cover for better visual quality of the images. In addition, before embedding, the image and signature (text) watermark is encoded using Arnold transform and Hamming code, respectively. Therefore, the scheme provides additional security and robustness.
Data management: Based on the robustness requirements [15], our scheme embeds more important data at high level DWT coefficients.
2 Related works
Some remarkable watermarking techniques are discussed below.
In [4], author described a secure watermarking scheme in transform domain. The method uses multi-objective evolutionary optimizer (MEO) to balance the major conflicting factors of watermarking system. Further, the method used Fibonacci-Lucas transformation for better security than Arnold transform. In [22], author uses different technique to produce a robust and imperceptible watermarking system for the authentication of medical images. Further, watermarked image is secured by using 2-D logistic map based chaotic encryption. Simulation results clearly confirmed that the method is robust, imperceptible and secure against various watermarking attacks. In similar way, Kumar et al. [7] also combined different techniques to provide a robust watermarking system. The method used SPIHT and Arnold transform for better robustness and security of the digital contents. Experimental study on different images proved that the scheme is robust and secure against various attacks. Author [13] developed imperceptibly embedding of multi-watermarks in the cover image. Before embedding, the method uses an encryption scheme to encrypt the text watermark. It is noticed that this encryption method minimize the encryption-decryption time while preserves security. The results studies indicate that technique is robust against considered attacks.
In [9], Author uses DWT-SPIHT-Arnold transform to develop a robust watermarking for medical data. The scrambled data, as a watermark image, is placed inside the appropriate wavelet coefficients of the cover. Before embedding, SPIHT scheme uses to determine the suitable coefficients of the cover image. In [6], Kumar et al. also introduced the embedding of scrambled version of watermark is placed inside the transformed coefficients of the cover images. The method uses the SPIHT scheme to compress watermarked image for efficient transmission on the network. Result study indicates the usefulness of the scheme in terms of objective and subjective evaluations. In [10], to improve the security of the medical data, a secure watermarking scheme is proposed, where encrypted version of the medical watermark is placed inside the cover image. Through experiments, the method is imperceptible and achieves good robustness against various kinds of attacks. In [18], Singh et al. developed the embedding of multi-watermark in the DWT-DCT-SVD coefficients of the cover image. Before embedding, text watermark is encoded via error correction code. Further, the selective encryption method is used to encrypt the watermarked image. In addition, the robustness of the scheme is further improved via neural networks. The robustness and imperceptibility of the scheme investigated through objective and subjective metrics. Various simulations confirm that the scheme provide a good trade-off between major parameters of the watermark systems. In similar way, Author of [23] introduced a BPNN based watermarking in DWT-DCT-SVD domain. The method imperceptibly embeds three encoded watermarks in the cover image. Lossless compression scheme and hamming code is used to compress and encode the symptom and signature text watermark, respectively. The test resultsfor considered image showed the usefulness of the scheme. In [19], author introduced embedding of logo and QR code in selected DWT coefficient of the cover image. Results demonstrations indicate that, the method is robust for popular image processing attacks.
In [8], Liu et al. developed a dual watermarking scheme in wavelet domain. The method uses DWT to transform the ‘Y’ channel of the ‘YCbCr’ cover image and the robust logo watermark placed inside the resulting cover image. Further, fragile watermark is embedded in the RGB model of the watermarked image through spatial domain scheme. Test analysis on eight different color images indicates that the method is highly imperceptible and robust and suitable for copyright protection and authentication of image. In [14], a dual watermarking scheme is also proposed by Singh et al., in which different type of watermark is placed inside the DWT-SVD cover image. Before embedding, the method uses error correction code to encode the text watermark. Further, author investigated the performance of three well know code. Detail analysis of the work indicates the importance of the method in medical applications. In [16], a robust dual watermarking scheme in LWT-DCT domain is proposed. The method uses color image as cover and two encoded watermarks are imperceptibly embedded for authentication purpose. According to the result’s study, the method not only improved the robustness, but also computationally low.
3 Proposed method
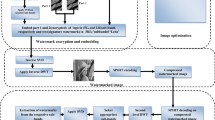
Embedding and extraction procedure of our scheme is clearly presented in Fig. 1. The process is divided into three phases: 1) imperceptibly embedding of dual watermarks, 2) compress the watermarked image via SPIHT scheme, and 3) robustly extract both watermarks. After the second level DWT decomposition of the cover, apply the SVD on selected sub-band to obtain the singular vector for watermarking. Next, security of logo watermarkis enhanced by Arnold encryption. Encrypted logo watermark is divided into two sub-images (both having equal size). Sub-image 1 and sub-image2 are embedded into ‘LH’ and ‘HL’ sub-band of 1st level DWT of cover image, respectively. However, text watermark is encoded by hamming code and placed inside the ‘HH’ sub-bands of second level DWT. Further inverse SVD and DWT are applied on watermarked image. Finally, the watermarked image is compressed via SPIHT scheme. In extraction process, all presented steps are implemented in reverse order to extract both watermarks from respective bands. Further, encrypted parts of watermark is combined together to recover the watermark image. At last, inverse Arnold is applied to decrypt original watermark image and hamming decoder is implemented to recover signature watermark.
3.1 Algorithm for watermarks embedding


3.2 Extraction algorithm for watermark

4 Experimental results
Our experiments are performed via MATLAB version 2013b. In this, ten different types of cover image (dimensions: 512 × 512), two watermarks as ‘logo’ (dimensions: 256 × 256), ‘signature’ watermark (96 bits) and ten important attacks are used for evaluation purpose. We used Peak signal to noise ratio (PSNR), normalized correlation (NC), Bit error rate (BER) and structured similarity index (SSIM) as standard performance metric to evaluate the performance of proposed scheme. These performance metrics are well defined in [17]. The Lena (cover image), watermarks (logo & signature) and watermarked images are shown in Fig. 2. Figure 3 shows extracted logo and signature watermarks. Extracted watermarks and watermarked (attacked) images are depicted in Fig. 4. We analyzed the performance of our proposed scheme in Tables 1, 2, 3, 4, 5, 6 and 7.
Table 1 summarizes the performance in terms of PSNR, NC, BER and SSIM of our proposed method at different gain and bit rate. In Table 1, the best value of PSNR, NC and SSIM are 36.97 dB (at gain = 0.01 and bit rate = 3), 0.9965 (at gain = 0.1 and bit rate = 2), and 0.9969 (at gain = 0.01 and bit rate = 3), respectively. However, BER is zero in all considered cases.
The performance of our method at different bit rates and gain = 0.05 are shown in Table 2. In this Table, the best value of PSNR, NC and SSIM are 33.15 dB (at gain = 0.05 and bit rate = 1), 0.9950 (at gain = 0.05 and bit rate = 3), 0.9929 (at gain = 0.05 and bit rate = 1), respectively. However, BER is zero in all considered gain and bit rate values. From Table 2, it is observed that the best performance is obtained at bit rate = 3 and gain = 0.05. Hence, these values are selected for further investigation. Table 3 lists the PSNR, NC, BER and SSIM values of our method for different cover images under bit rates =3 and gain = 0.05. From this table, best value of PSNR, NC and SSIM is 33.20 dB (for ‘Moon’ image),0.9962(for ‘Tire’ image) and 0.9974 (for ‘Moon’ image), respectively.
Table 4 lists the NC, BER and SSIM values with gain = 0.05 & bit rate = 3 under various attacks. From Table 4, best value of NC is 0.9999 for average filtering attack, BER is zero for most of the considered attacks, and SSIM is 0.9966 under median filter [33]. However, maximum BER = 4.76 under cropping attack. Table 5 shows the NC, BER and SSIM for varying size of text watermark at bit rate = 3. By considering this Table, we noticed that greater size of watermark affect the performance of our approach.
Tables 6 and 7 lists the NC value’s comparison with other approaches under popular attacks. From these tables, our scheme achieves a better robustness in compare to the competing methods [6, 12, 16]. As shown in these tables, it is established that the proposed scheme presented up to 77.40% enhancement in NC value over competing methods at low BER value.
Therefore, with the above discussion, the proposed scheme offers the optimal performance and superiority. Consequently, our scheme offers a better trade-off between conflicting factors of watermarking.
5 Conclusions
In this work, a robust technique for multiple watermarking techniques based on DWT, SVD, SPIHT and Arnold transform is proposed. We have embedded multi-watermarks inside cover image for purpose of authentication and integrity. Arnold transform provides extra level of security. Due to spatio-frequency localization properties of DWT, watermark location can be easily detected. However, visual-perception of cover image remains unchanged if there is slight change in singular values due to mathematical property of SVD. Further, presence of SPIHT provides bandwidth efficient transmission of data. Experimental results reveal that the scheme is secure and robust for different attacks and found superior to competing approaches. In future, proposed scheme can be further improved and expanded to other multimedia watermarking schemes such as audio and video.
References
Bhatnagar G, Raman B (2009) A new robust reference watermarking scheme based on DWT-SVD. Computer Standards & Interfaces 31(5):1002–1013
Chang CC, Tsai P, Lin CC (2005) SVD-based digital image watermarking scheme. Pattern Recogn Lett 26(10):1577–1586
Elhoseny M, Ramírez-González G, Abu-Elnasr OM, Shawkat SA, Arunkumar N, Farouk A (2018) Secure medical data transmission model for IoT-based healthcare systems. IEEE Access 6:20596–20608. https://doi.org/10.1109/ACCESS.2018.2817615
Gunjal BL, Mali SN (2015) MEO based secured, robust, high capacity and perceptual quality image watermarking in DWT-SVD domain. 4(1), pp. 126
Kumar C, Singh AK, Kumar P (2018) A recent survey on image watermarking techniques and its application in e-governance. Multimed Tools Appl 77(3):3597–3622
Kumar C, Singh AK, Kumar P (2018) Improved wavelet-based image watermarking through SPIHT. Multimed Tools Appl:1–14. https://doi.org/10.1007/s11042-018-6177-0
Kumar C., Singh A. K., Kumar P., Singh R. and Singh S.(2018) SPIHT based multiple image watermarking in NSCT domain, Concurrency and Computation: Practice and Experience, https://doi.org/10.1002/cpe.4912
Liu XL, Lin CC, Yuan SM (2018) Blind dual watermarking for color images’ authentication and copyright protection. IEEE Transactions on Circuits and Systems for Video Technology 28(5):1047–1055
Meenpal T (2018) DWT-based blind and robust watermarking using SPIHT algorithm with applications in tele-medicine. Sādhanā 43(1):4
Sharma A, Singh AK, Ghrera SP (2017) Robust and secure multiple watermarking for medical images. Wirel Pers Commun 92(4):1611–1624
Shehab A, Elhoseny M, Muhammad K, Sangaiah AK, Yang P, Huang H, Hou G (2018) Secure and robust fragile watermarking scheme for medical images. IEEE Access 6:10269–10278. https://doi.org/10.1109/ACCESS.2018.2799240
Shivani J. L.andSenapati R. K. (2017) Robust Image Embedded Watermarking Using DCT and Listless SPIHT. Future Internet 9(3):1–16
Singh AK (2017) Improved hybrid algorithm for robust and imperceptible multiple watermarking using digital images. Multimed Tools Appl 76(6):8881–8900
Singh AK (2019) Robust and distortion control dual watermarking in LWT domain using DCT and error correction code for color medical image. Multimed Tools Appl:1–11. https://doi.org/10.1007/s11042-018-7115-x
Singh AK, Dave M, Mohan A (2014) Wavelet based image watermarking: futuristic concepts in information security. Proceedings of the National Academy of Sciences, India Section A: Physical Sciences 84(3):345–359
Singh AK, Kumar B, Dave M, Mohan A (2015) Robust and imperceptible dual watermarking for telemedicine applications. Wirel Pers Commun 80(4):1415–1433
Singh AK, Kumar B, Singh G, Mohan A (2017) Medical Image Watermarking: Techniques and Applications, book series on Multimedia Systems and Applications, Springer, USA, ISBN: 978–3319576985
Singh, A.K., Kumar, B., Singh, G. and Mohan, A.(2017). Secure Multiple Watermarking Technique Using Neural Networks. In: Singh et al. (eds.) Medical Image Watermarking: Techniques and Applications (pp. 175–194). Springer, Cham.
Singh RK, Shaw DK, Jha SK, Kumar M (2017) A DWT-SVD based multiple watermarking scheme for image based data security. J Inf Optim Sci 39(1):67–81. https://doi.org/10.1080/02522667.2017.1372153
Singh L, Singh AK, Singh PK (2018) Secure data hiding techniques: A survey. Multimed Tools Appl:1–21. https://doi.org/10.1007/s11042-018-6407-5
Thakur S, Singh AK, Ghrera SP, Elhoseny M (2018) Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed Tools Appl. https://doi.org/10.1007/s11042-018-6263-3
Thakur S, Singh AK, Ghrera SP, Mohan A (2018) Chaotic based secure watermarking approach for medical images. Multimed Tools Appl:1–14. https://doi.org/10.1007/s11042-018-6691-0
Zear A., Singh A.K. and Kumar P.(2016). A proposed secures multiple watermarking techniques based on DWT, DCT and SVD for application in medicine. Multimedia Tools and Applications, pp. 1–20.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Kumar, C., Singh, A.K. & Kumar, P. Dual watermarking: An approach for securing digital documents. Multimed Tools Appl 79, 7339–7354 (2020). https://doi.org/10.1007/s11042-019-08314-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-019-08314-5