Abstract
The ownership verification of digital images is possible by the help of image watermarking. Watermarking make the image secure towards unlawful use; but at the same time, it causes some information loss too. Medical and defense are few fields, where even a small change in data can be very problematic. So there is need of reliable and lossless watermarking schemes. The present study is focused on the development of lossless watermarking method that can fulfill five basic requirements (robustness, reversibility, invisibility, security and capacity) of ideal lossless watermarking scheme maximally. Arnold transformed watermark is embedded into the host to restrict any unauthorized access of watermark even after extraction. Slantlet transformed coefficients are known to be quite robust towards image processing attacks; so block wise Slantlet transform is employed to resist the maximum attacks and to ensure a decent capacity. Mean values of transformed coefficients are used for embedding to increase the robustness and imperceptibility. The spatial domain overflow/underflow (due to embedding) is taken care by a post processing to satisfy the reversibility requirements. The embedding strength of watermarking is controlled with the help of artificial bee colony (ABC) in order to get an optimal tradeoff between invisibility and robustness. The proposed scheme is applied to a range of images to show its applicability to different domains.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
The development of internet, multimedia and related tools make the sharing of images very easy and fast but this also makes the security of these images quite vulnerable. Today many powerful image processing tools are available, which can change the images in such a way that it’s become almost impossible to verify the authenticity of modified images with naked eyes [19, 31]. Doing so, attacker can claim the false ownership of copyrighted images. Attacker can also manipulate some important portion in the image that can lead to money lose/ in worst cases human life (medical and defense) too [19, 31]. So there is need of technique, which can protect digital images from intentional/unintentional attacks as well as preserve the ownership information. Image watermarking is one of the most powerful tools, which is currently being used to solve this issue. In Image watermarking, digital information (watermark) is inserted into the host image, which is used to check the authenticity and ownership of host image after intentional/unintentional attacks [25]. The watermark insertion can be visible/ invisible in the host image; but invisible watermark gets more preference as it is difficult to remove from to host. Though, in some cases, both types of watermark are inserted in host for better security. Watermarking can also be classified on the basis of embedding domain as spatial domain embedding and transferred domain embedding. Spatial domain provides higher capacity but such watermarks generally show fragile nature [19, 31]. Though, fragile watermark are also useful in many cases (tampering localization [33]/tampered area recovery [8]) but it doesn’t provide an effective solution for ownership checking. On the other hand, transformed domain provides much more robust watermarking but with lesser capacity. Transformed domain watermarking provides higher resistance towards signal processing as well as geometrical attacks [1, 2, 7, 10, 23, 27, 30]. There is also a class know as semi fragile watermarking [41], which can resist more attacks than spatial domain but lesser than transformed domain [19, 31]. Transformed domain watermarking uses any/combination of DFT (Discrete Fourier transform [30]), DCT (Discrete cosine transform [2]), DWT (Discrete wavelet transform [1]), SVD (Singular value decomposition [7]) etc. for the transformation of host image. DWT and its variants [23, 27] are one of the most preferred transforms for robust watermarking as they show better performance than other transforms.
In addition to robust watermarking, the aim of robust-reversible watermarking is not only the protection and recovery of watermark after the attacks but also the lossless recovery of host image itself [24]. This makes the design of robust-reversible watermarking schemes even more challenging. Many real life applications (Medical, defense and remote sensing etc.) required protection along with lossless retrieval of host images because even a small change in the data can produce a critical change in the decisions based on them. In order to satisfy this need, reversible data hiding techniques are developed by researchers.
The next section is providing a review of work done in the field of robust-reversible watermarking along with the suggested improvements. After that, some preliminary theories are discussed in section three that are used in this study. The proposed watermarking is discussed in section four. Section five provides results of proposed scheme along with a detailed discussion. At last, the study is concluded in section six.
2 Related work
The Recovery of original host image after extraction of the watermark is desirable in many real life applications and it can be realized by using robust-reversible watermarking [20, 26]. Such type of watermarking must have the ability to deal with unintentional attacks (channel noise, JPEF compression etc.). Even, it will be better if it could sustain intentional attacks (histogram equalization, gamma correction etc.).
In 2000, Macq [26] proposed one of the first lossless watermarking schemes by utilizing modulo addition 256 and patchwork algorithm. Honsinger et al. [20] also proposed a scheme based on modulo addition 256. But both the schemes [20, 26] suffer with low imperceptibility and are not able to sustain salt and pepper noise attack. Fridrich et al. [15] proposed a reversible watermarking scheme by modifying the LSB (least significant bit) but it limit the capacity of scheme and show fragile nature. To improve the capacity, Fridrich et al. [16] proposed an improved scheme in 2002. De Vleeschouwer et al. [12, 13] suggested the embedding of watermark in the host image based on the rotation of histogram. This make the scheme robust towards JPEG compression but this scheme was also unable to pass from salt and pepper noise. In these schemes [12, 13], the very first time watermarked medical image’s ability is tested to resist lossy compression along with the ability to regenerate the host image. Afterwards, many other schemes have been proposed by different researchers to deal with unintentional attacks [3–6, 17, 28, 29, 40, 41] and the noise attack of the channel [3–6, 40, 41]. The aim of these schemes was to provide a robust reversible watermarking. Robust reversible schemes can be classified into two domains i.e. spatial domain [4–6, 12, 13, 17, 28, 29] and transformed domain [3, 40, 41].
To overcome the problem of salt and pepper attack, Ni et al. [28, 29] suggested dividing of host image into non overlap blocks and then these blocks are further divided into equal halves. The embedding of watermark is done by changing the average value of these two halves. Overflow/underflow is controlled by using four different strategies for watermark embedding after dividing them into four groups. The scheme show robustness toward lossy attacks but fail to provide complete reversibility. Gao et al. [17] proposed an improvement to solve the issue of imperfect reversibility by incorporating block skipping methodology into the scheme. This helps to choose such blocks for embedding, which can produce complete reversible host image and skips the inappropriate blocks. Due to this, the issue of imperfect reversibility was resolved but it reduces the capacity of scheme.
A transform domain approach for robust reversible watermarking is presented by Zou et al. [40, 41] by making use of the properties of IWT (integer wavelet transform). The scheme used the high frequencies (sub-band) coefficients of the transformed host image for insertion of watermark. It divides the sub-band in small blocks and shifts the mean value for each block for embedding. This shifting causes overflow/underflow problem in some blocks. In order to solve this issue, spatial domain block classification is been utilized but this changes the watermark bit in some cases, which is further been resolved by incorporating error correction methods. This scheme show robust nature towards lossy attacks (JPEG compression, Gaussian noise etc.) but it was unable to provide complete reversibility and also suffers with low data hiding. An et al. [3] proposed a scheme based on the transform coefficients of IWT. It utilizes one of the high frequencies sub-bands of IWT for embedding of watermark. The overflow/underflow is avoided by using a preprocessing on pixels. In this preprocessing, the histograms of pixels are shifted by a maximum shift (opposite direction) that can be happen to them during the embedding of watermark. This method required some side information to be saved, which is needed during the extraction of watermark in order to ensure the complete reversibility of scheme. This scheme shows a complete reversible nature and it was robust towards many lossy attacks. However, the scheme capacity and imperceptibility was low.
Rasha et al. [37] suggested a new scheme using the Slantlet transform; to improve the imperceptibility of watermarked image without compromising any other parameter. This scheme divided the host image into non-overlapped blocks and then transforms these blocks to SLT (Slantlet transform) matrix. Then after, it divides the matrix into four blocks. The watermark insertion is done by shifting the mean value of any one band. It also incorporates the pre-processing proposed by An et al. [3] to avoid overflow/underflow. Thabit et al. [38] again improved their method [37] by utilizing the same transformed but changing the watermark insertion methodology and pre-processing to post-processing to deal with overflow/underflow.
The earlier developed reversible watermarking scheme was mostly focused on the gray scale domain [3–6, 12, 13, 17, 28, 29, 40, 41] and a very less emphasis was given on color image [17, 29, 38]. Thabit et al. [38] applied the reversible data hiding technique to medical color images by looking at the future need to do so. In recent times, diverse color information based medical imaging aspects have been introduced (e.g., wound photography, microscopy, skin scanning, and gastrointestinal endoscopy) [11]. The gray scale schemes are not applicable directly to the color domain [11], so new research need to be done in this field as the use of color medical image is increasing and so the need of relevant security schemes.
Watermark embedding strength is the parameter that controls the robustness and imperceptibility of watermarking scheme. Thabit et al. [38] used different embedding strength to provide a variation of imperceptibility and robustness. In the present work, it is shown that imperceptibility and robustness are inversely proportional parameters. The increase of embedding strength increases the robustness but decrease the imperceptibility, whereas opposite happen on decreasing the embedding strength. To tackle this problem, a new watermarking scheme ABCORRW (ABC Optimized robust reversible watermarking) is presented in this work. In this work, we are presenting a way to obtain the tradeoff between robustness and imperceptibility by controlling the embedding strength using artificial bee colony [21]. The proposed scheme is applied to images of different domains in order to show its usefulness.
3 Preliminary
The section is providing a preliminary knowledge of different theories that are utilized in proposed work.
3.1 Arnold transform
The pixels of the watermark image are randomized in order to make it secure even after successful extraction from the host image. For the said purpose, Arnold transform is utilized because of its secured nature. Arnold transform matrices can only be reversed back to original form by the unique key/code. This transform provides an iterative movement to the image pixels of the array [39]; to which it is been applied. The mathematical representation of a 2D Arnold transform is shown in equation 1.
In equation 1, ‘m’ and ‘n’ are fixed positive integer numbers, which help in deciding the period of the transform. Arnold transform is applicable to square matrices only. With the consideration of square matrix, ‘h’ is the height of image. Pixel values are represented by x and y and transformed pixel values are represented by x i and y i after ‘i’ number of iterations. As already mentioned that Arnold transform show periodic nature i.e. if we kept on transforming complete image then each pixel (x and y) will came back to their initial position after a certain number of transforms (T), which is also known as period of Arnold Transform. The period value value depends on the values of m, n and h.
Suppose that ‘i’ transforms are performed on the original image during the randomization process. So, in order to get the original image back, further (T-i) transforms needs to be performed on this pre-randomized image.
3.2 Slantlet transform
DWT has been applied to many domains of image processing and it has been proven to be very useful because of its excellent capability of spatio-frequency representation. The DWT is used to obtain the time localization as well as the smoothness parameters at any instant. The unique representation of both parameters is not possible at one point, due to limitation of uncertainty principal. So a good tradeoff needs to be obtained between these two parameters. Ivan W. Selesnick [34, 35] proposed a DWT equivalent representation, called Slantlet transform (SLT). Slantlet transform provides a better time localization and smoothness by supervising the length of discrete-time basis functions as well as their moments. SLT provides an equivalent representation of DWT filter banks in order to obtain the filter coefficients. The equivalent SLT filter banks representation is shown in Fig. 1.
On the contrary of filter multiplication of DWT, SLT filter banks are making use of parallel structure as shown in the Fig. 1. So, the lengths of SLT filters are shorter than the equivalent DWT filters. A detail implementation can be seen in [34, 35] along with the proof of orthogonality of slantlet transform. The host image is first divided into non-overlapping blocks and then SLT is implemented on these blocks.
3.3 Artificial bee colony (ABC)
Karaboga [21] introduce a simple and robust population based optimization algorithm in the year 2005 and named it artificial bee colony (ABC). It is based on the smart foraging actions of a honey bee swarm. Experimental result showed that ABC performs quite alike other metaheuristics techniques but provides an additive advantage of using less control parameters [22]. The ease of implementation and effectiveness make researches to use ABC in solving many problems [9, 14, 18, 32, 36]. Artificial Bee colony is already been implemented into different imaging optimization problems like image segmentation [18], compression [32] and enhancement [14]. The use of ABC provided an improved result in all these domains. ABC is known to tackle the multidimensional search quite effectively and the same is utilized in this work also.
The possible solutions of given problem are represented by the food source in ABC algorithm and fitness of any solution is represented by nectar amount of a food source. There are three types of bees exist in ABC: employed bees, onlooker bees and scout bees. Employed bees represent the number of solutions in the given population size. ABC starts with an initial population of solutions of size N (food source locations) with each having a dimension D i.e. initial solution can be represented as X i = {x (i, 1), x (i, 2) … x (D,i)}; where i = 1, 2 … N
After the initial distribution, search becomes a repetitive process of choosing best solution till the stopping criteria is reached. The onlooker bees choose the best food sources based on the fitness function value and information supplied by employed bees, whereas the scout bees leaves their current food source in order to search better food sources. In ABC algorithm, employed bees and onlookers and are responsible for exploitation process, whereas scouts bees take care of proper exploration. The ABC algorithm contain following steps:
-
1)
N numbers of food sources are allotted randomly between the permissible lower X min = (x (min,1), … x (min, D)) and upper limit X max = (x (max,1), … x (max, D)) of allocation with each having dimension D using equation 2.
-
2)
Each employed bee generates a new solution on the basis of local information available to it and compares the fitness of generated solution with the parent solution. The better solution among these two is used for next iteration. The new solution Y i = (y (i,1), y (i,2) … y (i,j)) from current solution X i = (x (i,1), x (i,2) … x (i,j)) is generated by using equation 3.
Here, indices k ∈ (1, 2 … N) and j ∈ (1, 2 … D) are randomly chosen in such a way that k are i remain different. Ф (i,j) is a random number between zero and one.
-
3)
The employed bee shared the fitness information with the Onlooker bee. The Onlooker bee generates a probability (P i ) of nectar (fitness) amount using equation 4 and 5.
Here f(X i ) represents the value of objective function at the food location X i . The objective function used in current study is defined by equation 16.
-
4)
A random number is generated for each onlooker bee between zero and one; if P i of food location have a greater value than the random number then step 2 is followed by that onlooker bee too.
-
5)
If predetermined number of iterations is not able to change the food locations then such location are assumed to be abandoned. The value of predetermined number of iterations is important parameter and known as limit. In such situations, scout bee determines the new positions randomly in order to replace the abandoned positions.
Steps (1)–(5) kept on repeating till the predetermined stopping criteria (maximum iteration, minimum change) met.
4 Watermarking scheme
Proposed scheme is making use of SLT domain by dividing it into four bands (LL, LH, HL and HH) such that
4.1 Watermarking embedding
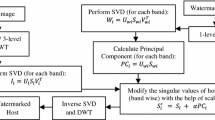
The block diagram of embedding process is shown in the Fig. 3 and it contains the following steps:
-
1)
The transformed host image (H × W) is divided into smaller non-overlapping blocks (NB) of size L × L such that it satisfy equation 6.
-
2)
Each block in spatial domain (A i ) gets transformed into SLT domain (B i ) using equation 7 in such a way that it can be reconstructed using equation 8.
-
3)
All the transformed blocks gets converted into four bands as shown in Fig. 2.
-
4)
The mean value of the coefficients in HL and LH bands i.e. Mean HL and Mean LH are calculated.
-
5)
Arnold transform is applied on the watermark image with a secret key to protect it even after successful extraction.
-
6)
Insertion of one watermark bit is done in each block using the modification factors (MF 1, MF 2) as shown in equation 9 and 10 and explains below.
If watermark bit = 1 and Mean HL − Mean LH ≥ T then there will be no change
If watermark bit = 1 and Mean HL − Mean LH < T then Mean new HL = Mean HL + MF 1 and Mean new LH = Mean LH − MF 1 If watermark bit = 0 and Mean LH − Mean HL ≥ T then there will be no change
If watermark bit = 0 and Mean LH − Mean HL < T then Mean new LH = Mean LH + MF 2 and Mean new HL = Mean HL − MF 2
-
7)
After the embedding, mean values of LH and HL in all the block follow the pattern such that: If watermark bit is 1, Mean HL − Mean LH ≥ T and if watermark bit is 0, Mean HL − Mean LH < T .
-
8)
The changes in mean values (block wise) are saved as side information for host image reversibility.
-
9)
Conversion of the image from SLT domain to spatial domain is done. Rounding off of pixels is performed. The change in SLT coefficients values may cause an overflow (pixel value > 255)/underflow (pixel value < 0). So, these pixels values are change as per equation 11. Locations and original pixel values have been saved as side information.
4.2 Watermarking extraction and host regeneration
It is assumed that the watermarked image goes through certain attacks and so it is represented by A′ * w instead of A ′ w . Extraction of watermark and host regeneration is shown in Fig. 4. It contains the following steps:
-
1)
With the help of side information of overflow/underflow, retrieved back approximated version of spatial domain watermarked image A * w .
-
2)
Apply the block wise slantlet transform on A * w and extract the approximated watermark bits using equation 12.
-
3)
Inverse Arnold transform is performed as per the key to obtain the watermarked image.
-
4)
With the help of side information related to changes in Mean coefficients, Host image is regenerated.
4.3 Optimization of scaling factors using ABC
From the embedding and extraction process, it is quite visible that the quality of formed watermarked image and extracted watermark are totally depends on the embedding strength T. A low value embedding strength degrades the robustness of watermark where as a high value minimizes the imperceptibility so there is a need to choose an optimal value embedding strength for each embedding, which provides a balance between imperceptibility and robustness. Imperceptibility is the measure of similarity between the host image and watermarked image. Suppose the size of host (X) and watermarked image (X*) is n × n and they can attain a maximum pixel value as X max . Then, imperceptibility can be define in term of PSNR (peak signal to noise ratio) as:
Robustness is defined as scheme’s ability to deal with the attacks. The difference of extracted watermark and original watermark can be used to show the robustness of scheme in terms of BER (Bit error rate) as:
Suppose that the scheme considered N type of attacks during the embedding strength optimization. Then, the average robustness can be written as:
The objective of the ABC optimization is to maximize both imperceptibility and robustness, so following objective function (Equation 16) is formulated for minimization:
The solution of error function is a multi-dimensional search of embedding strengths [T], which can’t be visualize graphically and needs special tool like ABC to search the optimal values.
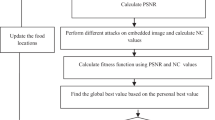
A bounded initialization of population size of 20 is done in the range of 1 to 10. 200 generations are used in the ABC optimization. The other controlling parameters are shown in Table 1. The block diagram of optimization process is shown in Fig. 5 and the algorithm of optimization process is shown in Fig. 6.
5 Results and discussions
In this study, a variety of images are used as host image to show the applicability of proposed scheme in different domain. Figure 7 is showing few host images and watermarks used in this study. All the host images are of size 512 × 512 and gray in nature. Both the watermarks are of size 128 × 128 and binary of nature. The scaled version of ‘watermark-1’ In order to show the importance of proposed approach, the results (imperceptibility and robustness) are first computed with fixed embedding parameter and then with ABC optimized parameters. The proposed scheme is evaluated in terms of capacity, imperceptibility, robustness and reversibility.
5.1 Capacity
The capacity is directly dependent on the block size used for host image division. One bit is inserted in each block so capacity can be simply calculated by equation 17. Table 2 is showing the capacity of scheme in terms of block size.
In order to increase the capacity of scheme, a smaller block size can be utilized but this results into reduction of the imperceptibility and robustness of the scheme. The change in imperceptibility with different block sizes is shown in Fig. 8. It is quite clear from the Fig. 8 that a higher imperceptibility can be achieved with a larger block size.
The same pattern (imperceptibility vs. block size) is also followed by the other host images; as shown in the Table 3.
5.2 Imperceptibility
The imperceptibility of the watermarked image is dependent on the embedding strength and block size. With the assumption that the block size is 16 × 16, Table 4 is showing the variation in PSNR of watermarked image with different embedding strength.
It can be clearly seen from the Table 4 that as the embedding strength increases, the PSNR of watermarked image gets decreased. This proofs that use of higher embedding strength decreases the imperceptibility of the scheme. Figure 9 is showing the watermarked image with block size 16 × 16 and embedding strength of 3.
5.3 Robustness
Robustness is defined as the ability to deal with the attacks. Fifteen different attacks are considered in this study as shown in Table 5. Table 5 is showing the variation in the robustness of scheme (in terms of BER) with different embedding strengths. ‘Lena’ is used as host image and watermark-1 is used as watermark for the calculation of Table 5. The average BER (using all the attacks) is calculated for all the host images of different domain and the same is shown in Table 6 with different embedding strengths. It is quite evident from the Tables 5 and 6 that a higher embedding strength provides a better robustness (Low BER).
5.4 Optimization of embedding strength
From the sections 5.2 and 5.3, it is quite clear that a higher value of embedding strength provides a better robustness but poor imperceptibility and lower value of embedding strength provides opposite of that. Though, a good watermarking scheme needs to have a high value of both parameters, i.e. imperceptibility and robustness. Both parameters cannot be maximized simultaneously, so there is a need to choose an optimal value of embedding strength that provides a good tradeoff between imperceptibility and robustness.
In order to obtain an optimal value, an error function is defined in equation 15. The objective is to minimize the error function by changing the embedding strength. Figure 10 is showing the variation of error function with respect to the embedding strength for different hosts and Table 7 is showing the values of error function with different hosts and watermarks.
The corresponding embedding strengths for the highlighted values of error function (Table 7) are providing the best tradeoff with respective host and watermark. In Fig. 10 and Table 7, a single value of embedding strength is used for all the blocks. The use of different values of embedding strength for different blocks; can help in minimizing this error function further. The use of multiple embedding strength, makes this minimization a multi-dimensional search and so a specialized tool; artificial bee colony is used to solve this complex search problem. The detail of ABC implementation is shown in section 4.3. Figure 11 is showing the error function minimization with respect to the ABC generations. Tables 8, 9 and 10 are showing the comparison of imperceptibility and robustness of ABC optimized embedding strengths with the single optimal value of embedding strength. From the Tables 8, 9 and 10, it is quite evident that the proposed scheme outperforms the existing scheme.
5.5 Reversibility
The proposed scheme is tested for reversibility after embedding strength optimization with ABC and it shows complete reversibility during all the tests. The IER (image error rate) is used to evaluate the reversibility of proposed scheme as defined by [3]. 100 test images of each group (General, Medical and SAR) are used to check the reversibility of proposed scheme. Table 11 is showing the comparison of proposed scheme with previous methods in terms of IER.
5.6 Applicability of proposed scheme to color images
The proposed scheme is applied to color images (General and Medical) to verify its usefulness in producing reversible color watermarked images. Ten general (G1 to G10) and ten medical (M1 to M10) color hosts are used in this study in order to shown the applicability of proposed scheme. Figure 12 is showing the color host images used in this study. Color image (RGB) is made up of three channels i.e. red, green and blue. During embedding, each channel is separated and embedding is done in any one of channel (R/G/B) same like the watermarking done in gray channel (section 4.1) and then original channel is replaced by the watermarked channel. After single channel embedding for all the three channels, the embedding is also done for all the three channels at once i.e. same watermark is embedded in all the three channels in one experiment. A block division of size 16 × 16 (8 × 8 in SLT) is utilized for embedding and ABC based embedding strength optimization is performed on all the host images. Table 12 is showing the imperceptibility (PSNR) of watermarked color hosts, when the watermark is inserted in the red channel (R), green channel (G), blue channel (B) and all the three channels (RGB). In case of single channel embedding, the PSNR is calculated for that particular channel only and in case of multi channel embedding, the average of all the channel’s PSNR is calculated to obtain the overall PSNR.
The extraction and reversibility process for all color images are performed. All hosts are recovered back completely using the proposed scheme and the extracted watermark show a zero BER (bit error rate) without any attack.
6 Conclusion
This paper proposed a robust-reversible watermarking scheme based on Slanlet transform and Artificial Bee Colony. It utilized the mean value coefficients of HL and LH bands for the watermark embedding and this provided a very good imperceptibility and robustness to scheme. The study further suggested that there is a need to find an optimal value of embedding strength to obtain a tradeoff between the imperceptibility and robustness. So it utilized artificial bee colony optimization to find the optimal values of embedding strength. The proposed scheme is completely reversible and it was checked over various types of images (medical, thermal etc.) for applicability. In future, more variants of ABC along with other metaheuristic techniques will be applied to improve the performance (generation used, PSNR, BER etc.) of watermarking process. Also, new insertion methodologies need to be developed in order to sustain major and deep geometrical attacks.
References
Ali M, Ahn CW (2014) An optimized watermarking technique based on self-adaptive DE in DWT–SVD transform domain. Signal Process 94:545–556
Ali M, Ahn CW, Pant M (2014) A robust image watermarking technique using SVD and differential evolution in DCT domain. Optik-Int J Light Electron Optics 125(1):428–434
An L, Gao X, Li X, Tao D, Deng C, Li J (2012) Robust reversible watermarking via clustering and enhanced pixel-wise masking. IEEE Trans Image Process 21(8):3598–3611
An L, Gao X, Yuan Y, Tao D, Deng C, Ji F (2012) Content-adaptive robust lossless data embedding. Neurocomputing 79:1–11
An L, Gao X, Yuan Y, Tao D (2012) Robust lossless data hiding using clustering and statistical quantity histogram. Neurocomputing 77(1):1–11
An L, Gao X, Deng C (2010) Reliable embedding for robust reversible watermarking. Proc Sec Int Conf Internet Multimed Comput Service, Harbin, China 57–60
Ansari IA, Pant M (2015) SVD watermarking: particle swarm optimization of scaling factors to increase the quality of watermark. Proc Fourth Int Conf Soft Comput Problem Solv 205–214
Ansari IA, Pant M, Ahn CW (2015) SVD based fragile watermarking scheme for tamper localization and self-recovery. Int J Mach Learn Cybern. doi:10.1007/s13042-015-0455-1
Ansari IA, Pant A, Ahn CW (2016) Robust and false positive free watermarking in IWT domain using SVD and ABC. Eng Appl Artif Intell 49:114–125
Ansari IA, Pant M, Neri F (2014) Analysis of gray scale watermark in RGB host using SVD and PSO. IEEE Symp CIMSIVP 1–7
Celebi ME, Schaefer G (2013) Color medical image analysis. Lect Notes Comput Vision Biomech 6
De Vleeschouwer C, Delaigle J, Macq B (2001) Circular interpretation of histogram for reversible watermarking. Proc IEEE Fourth Workshop Multimed Sign Process 345–350
De Vleeschouwer C, Delaigle J, Macq B (2003) Circular interpretation of bijective transformations in lossless watermarking for media asset management. IEEE Trans Multimed 5(1):97–105
Draa A, Bouaziz A (2014) An artificial bee colony algorithm for image contrast enhancement. Swarm Evol Comput 16:69–84
J. Fridrich, M. Goljan, R. Du (2001) Invertible authentication. Proc SPIE Sec Watermark Multimed Content, San Jose, USA 197–208
Fridrich J, Goljan M, Du R (2002) Lossless data embedding — new paradigm in digital watermarking. EURASIP J Appl Sign Process 2:185–196
Gao X, An L, Li X, Tao D (2009) Reversibility improved lossless data hiding. Signal Process 89(10):2053–2065
Hanbay K, Talu MF (2014) Segmentation of SAR images using improved artificial bee colony algorithm and neutrosophic set. Appl Soft Comput 21:433–443
Haouzia A, Noumeir R (2008) Methods for image authentication: a survey. Multimed Tools Appl 39(1):1–46
Honsinger CW, Jones PW, Rabbani M, Stoffel JC (2001) Lossless recovery of an original image containing embedded data. US Patent no 6:278–791
Karaboga D (2005) An idea based on honey bee swarm for numerical optimization. Tech Rep TR06. Erciyes Univ Eng Fac Comput Eng Dep
Karaboga D, Akay B (2009) A comparative study of artificial bee colony algorithm. Appl Math Comput 214:108–132
Lagzian S, Soryani M, Fathy M (2011) A new robust watermarking scheme based on RDWT-SVD. Int J Intell Inform Process 2(1):22–29
Li YC, Yeh CM, Chang CC (2010) Data hiding based on the similarity between neighboring pixels with reversibility. Digit Sign Process 20(4):1116–1128
Lin W, Tao D, Kacprzyk J, Li Z, Izquierdo E, Wang H (2011) Multimedia analysis processing and communications 346
Macq (2000) Lossless multiresolution transform for image authenticating watermarking. Proc EUSIPCO 533–536
Makbol NM, Khoo BE (2014) A new robust and secure digital image watermarking scheme based on the integer wavelet transform and singular value decomposition. Digit Sign Process 33:134–147
Ni Z, Shi YQ, Ansari N, Su W, Sun Q, Lin X (2004) Robust lossless image data hiding. IEEE Int Conf Multimed Expo, Taipei, Taiwan 2199–2202
Ni Z, Shi YQ, Ansari N, Su W, Sun Q, Lin X (2008) Robust lossless image data hiding designed for semi-fragile image authentication. IEEE Trans Circ Syst Video Technol 18(4):497–509
Poljicak A, Mandic L, Agic D (2011) Discrete Fourier transform–based watermarking method with an optimal implementation radius. J Electron Imag 20(3):033008–033008
Potdar VM, Han S, Chang E (2005) A survey of digital image watermarking techniques. 3rd IEEE Int Conf Industr Inform INDIN’05 709–716
Ramanathan R, Kalaiarasi K, Prabha D (2013) Improved wavelet based compression with adaptive lifting scheme using artificial bee colony algorithm. Int J Adv Res Comput Eng Technol (IJARCET) 2(4):1549
Rawat S, Raman B (2011) A chaotic system based fragile watermarking scheme for image tamper detection. AEU Int J Electron Commun 65:840–847
Selesnick IW (1998) The slantlet transform. Proc IEEE-SP Int Symp Time-Freq Time-Scale Anal. Pittsburgh, PA 53–56
Selesnick IW (1999) The slantlet transform. IEEE Trans Signal Process 47(2):1304–1313
Sharma TK, Pant M, Ahn CW (2013) Improved food sources in artificial bee colony. IEEE Symp Swarm Intell (SIS) 95–102
Thabit R, Khoo BE (2014) Robust reversible watermarking scheme using Slantlet transform matrix. J Syst Softw 88:74–86
Thabit R, Khoo BE (2015) A new robust lossless data hiding scheme and its application to color medical images. Digital Sign Process 38:77–94
Wu L, Zhang J, Deng W, He D (2009) Arnold transformation algorithm and anti-Arnold transformation algorithm. 1st IEEE Int Conf Inform Sci Eng 1164–1167
Zou D, Shi Y, Ni Z, Su W (2006) A semi-fragile lossless digital watermarking scheme based on integer wavelet transform. IEEE Trans Circ Syst Video Technol 16(10):1294–1300
Zou D, Shi Y, Ni Z (2004) A semi-fragile lossless digital watermarking scheme based on integer wavelet transform. IEEE 6th Workshop Multimed Sign Process, Siena, Italy. 195–198
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Science, ICT & Future Planning (NRF-2015R1D1A1A02062017).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Ansari, I.A., Pant, M. & Ahn, C.W. Artificial bee colony optimized robust-reversible image watermarking. Multimed Tools Appl 76, 18001–18025 (2017). https://doi.org/10.1007/s11042-016-3680-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-016-3680-z