Abstract
Upgraded network technology presents an advanced technological platform for telecare medicine information systems (TMIS) for patients. However, TMIS generally suffers various attacks since the information being shared through the insecure channel. Recently, many authentication techniques have been proposed relying on the chaotic map. However, many of these designs are not secure against the known attacks. In spite of the fact that some of the constructions attain low computation overhead, they cannot establish an anonymous communication and many of them fail to ensure forward secrecy. In this work, our aim is to present authentication and key agreement protocol for TMIS utilizing a chaotic map to achieve both security and efficiency. The underlying security assumptions are chaotic theory assumptions. This scheme supports forward secrecy and a secure session is established with just two messages of exchange. Moreover, we present a comparative analysis of related authentication techniques.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
Introduction
The TMIS is applicable in various healthcare systems, such as remote user’s medical monitoring, consultation, and health-related flexible and convenient services. In the healthcare sector, these systems are essential for the current demand as these provide private health facilities to the patients at their home. Healthcare services are improved due to the technological development in the network. As a consequence, electronic devices can be used by patients to receive healthcare services. We know that the users use the public insecure channel to access the service. This leads to a security threat. Thus, the communication must be through an effective authenticated channel in order to achieve privacy and security. To fill this gap, Wu et al. [10] came up with a secure authentication scheme for the system. In the following, Wei et al. [9] noticed that the work of Wu et al. [9] is vulnerable to two-factor authentication. Therefore, a new scheme is proposed based on a smart card for TMIS to validate two-factor authentication. In 2012, Zhu [12] found that in Wei et al.’s technique password guessing is possible. He proposed an advanced scheme, but that was without anonymous communication. Later, Chen et al. [5] developed an anonymous authentication technique for TMIS. In the following, Lin et al. [7] showed that in Chen et al.’s scheme, the user’s identity can be disclosed with the help of the dictionary attack and guessing of the password is possible using smart card’s information. In order to prevent the existing attacks, Lin et al. [7] presented an anonymous authentication scheme. Cao and Zhai [4] illustrated that the design of Chen et al. is vulnerable to password guessing and identity guessing attacks due to smart card information. Thus, they designed an efficient protocol for TMIS. The protocols [4, 7, 12] are not secure against input verifying conditions since incorrect input cannot be efficiently distinguished by these protocols. Cryptosystems, based on the chaotic maps, have been developed in order to improve efficiency and security. Apart from security, privacy attributes have equal importance. Two key privacy attributes are anonymity and unlinkability,
which are missing in many authentication schemes for TMIS, such as [9, 10, 12, 31] protect user’s anonymity. In 2013, Guo et al. [14] constructed an AKA-CM (authenticated Key agreement based on the chaotic map) protocol. Later, Hao et al. [15] showed that the work [14] does not provide the user traceability due to the use of two secret keys. Hoa et al. then developed a new technique that performs better over the work of Guo et al. In 2014, the weaknesses in Hoa et al.’s scheme were noticed by Jiang et al. [16]. They observed that the scheme is not secure against the stolen smart card (SSC) attack. Li et al. [21], in 2016, proposed an AKA-CM for healthcare. However, Madhusudhan et al. noticed that the design is vulnerable to impersonation (IMP) and password guessing (PAG) attacks. Later, Jiang et al. [27] presented an improved AKA model for TMIS, which uses three messages of exchange for session key agreement. Moreover, this scheme is not much efficient as it uses six elliptic curve scalar multiplication as given in [27], which has the highest cost as given in [27]. At the same time, Wu et al. [28] presented RFID based AKA scheme, which uses the hash function. In the following, Radhakrishnan et al. [19] presented an authentication protocol (AUTP) for TMIS which is not secure against identity guessing (IDG), SSC information, and PAG attacks. Later, Zhang et al. [25] proposed an AUT (authentication technique) for TMIS. Unfortunately, this protocol is also insecure against PAG, IDG, and replay (RPL) attacks. In the following, a robust AUT was developed by Madhusudhan et al. [20] for telecare medical information system (TMIS). However, it can be observed that their scheme remains insecure against SSC, IMP, PAG, and IDG attacks. The brief analysis of security attributes is given in Tables 1 and 2. In [34], Li et al. presented a cloud-assisted mutual authentication and privacy preservation protocol for TIMS. In the following, a secure mutual authentication protocol for cloud-assisted TMIS based on elliptic curve cryptography was proposed by Kumar et al. [35]. Later on, Salem and Amin [36] developed an RFID authentication protocol relying on El-Gamal cryptosystem for secure telecare medical information systems. Nayak and Pippal [38] also discussed existing authentication protocols for TMIS and did their efficiency analysis. Recently, a chaotic hash function based lightweight client authentication scheme with anonymity for TMIS was proposed by Gaikwad et al. [37].
As we know Th ≈ 0.00032s is a very light weight operation as we compared with other’s such as tme ≈ 0.0192s, \(t_{fe} \approx t_{h_{b}}\approx t_{ecm} \approx 0.0171 s\) [32], tb ≈ 0.380s, tsym ≈ 0.0056s, tecm ≈ tc ≈ 0.0171s [2]. We compare the performance of related schemes in. Figure 1.
A comparative summary of the security attributes of authentication protocols (chaotic map-based) for TMIS is given in Table 2. We use the notations √ and × to denote that a scheme achieves the attribute and fails to attain the attribute respectively. It can be seen from Tables 1 and 2 that existing protocols for TMIS are weak from a security point of view. In other words, the protocols cannot resist all existing attacks as provided in Tables 2 and 1. Thus, it is required to have an AKA-MP for TMIS preserving the following attributes:
-
User friendly login and password update.
-
Unlinkability.
-
Mutual authenticated secure session-key based Communication.
-
Low computational overhead and high security.
-
Less communication overhead and anonymity.
Therefore, we proposed a secure and efficient AKA-MP for TMIS. The security analysis of our scheme is given in this work. Our construction is resistant to existing attacks and possesses a key agreement using two message exchange.
Roadmap
The paper is originated as follows: Basic assumptions, notations and model is discussed in “Preliminaries”. The proposed scheme is described in “Proposed Scheme”. The claim of security is proved in “Security Analysis”. The performance of the proposed scheme is discussed in “Computational Efficiency Analysis”. Lastly, conclusion is provided in “Conclusion”.
Preliminaries
The notations and basic definitions are presented in this section. Also Chaos theory’s definition with its properties are discussed. The description of the notations is given as in Table 3.
Chebyshev Chaotic Map (CCM)
The following definition of CCM are taken from [17, 18].
-
Definition 1 Chebyshev polynomial (CHP) of degree n (positive integer) is denoted by Tn(x) and defined as \(T_{n}(x) = cos(n (\arccos (x)))\) such that \(T_{n}(x):(-\infty ,+\infty )\rightarrow [-1,+1]\). It satisfies the relation Tn(x) = (2xTn− 1(x) − Tn− 2(x)) for \(x\in (-\infty ,+\infty )\), T0(x) = 1 and T1(x) = x
-
Definition 2 The DLP (discrete logarithm problem) is to compute an integer u satisfying the equality Tu(x) = y given y and x.
-
Definition 3 Computational Diffie-Hellman (CDH) problem is defined as follows: given the tuple \(\left (x,T_{u}(x),T_{v}(x)\right )\), it is hard to compute Tuv(x).
Threat model
We follow the notations as described in Table 3 and a threat model as depicted in Figure (1) under security assumptions [8] about the computational power of R in smart card security in password-based and chaotic map-based authentication schemes.
-
The pseudo-random password is chosen by the user from the dictionary. Sj has private key. Essential values are inserted by the server in the smart card during the registration.
-
The R, Ui and Sj communicate via oracle queries that enable R to break authentication scheme.
-
The R controls the communication channel by intercepting, modifying, resenting and diverting the message.
-
The R can steal the smart card and can get its stored information.
Proposed Scheme
We now present an AKA-CM to address the security and efficiency requirements.
Registration Phase
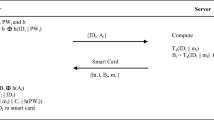
Ui adopts secure channel to complete his registration with Sj. The communication of messages and computation are described in Fig. 2.
-
Ui chooses Idi, Pwi,imprints biometric Hi = hb(biometric) and executes Ai = h(Idi||Pwi||Hi) and forwards {Idi,Ai} to Sj.
-
The Sj, after recovering {Idi,Ai}, checks the correctness of Ui’s identity Idi. If validation succeeds, then Sj uses its secret key x to derive Tx(Idi||ni) for user Ui, where \(n_{i} \in Z_{p}^{\ast }\) is randomly chosen. Sc then derives Bi = Tx(Idi||ni) ⊕ Ai.
-
Using secure channel, Sj issues Sc storing {h(.),Bi,ni} to Ui. Sj stores ni corresponding to Idi in secure database.
-
Ui then puts in Di in Sc along-with {h(.),Bi,Di,ni} after computing Tx(Idi||ni) = Bi ⊕ Ai,Di = h(Tx(Idi||ni)||Pwi||Idi||Hi).
Login Phase
Ui login to Sj by following steps. Description is provided via Fig. 3.
-
Ui inserts Sc, Idi and Pwi. Ui imprints his biometric on sensor and computes \(H_{i}^{\prime } =h_{b}(biometric)\) and \(A_{i}^{\prime } = h(Id_{i}||Pw_{i}||H_{i})\).
-
Utilizing \(A_{i}^{\prime }\), Sc receives \(T_{x}(Id_{i}||n_{i})' = A_{i}^{\prime } \oplus B_{i}\) and executes \(D_{i}^{\prime }= h(T_{x}(Id_{i}||n_{i})'||Pw_{i}||Id_{i}||H_{i})\) and verifies the equality \(D_{i}^{\prime } \overset {?}{=} D_{i}\). The verification holds if all input parameters Idi, Pwi and biometric are correct.
-
Sc chooses \( y \in Z_{p}^{\ast } \) randomly and derives Wi = TyTx (Idi||ni),Ci = Ty(Idi||ni), Gi = Idi ⊕ h(Ty(Idi||ni) ||Wi||T1) and Fi = h(Tx(Idi||ni)||Wi||T1). Finally, Ui transmits {Ci,Gi,Fi,T1} to Sj.
Authentication Phase
Description is provided via Fig. 4. On receiving {Ci,Fi,T1} from Ui, Sj performs the following steps:
-
Sj verifies correctness of T1, and then derives TxTy \((Id_{i}||n_{i}) = W_{i}^{\prime }\), \(Id_{i} = G_{i} \oplus h(T_{y}(Id_{i}||n_{i})||Sk_{i}^{\prime }||T_{1})\) and \(F_{i}^{\prime } = h(T_{x}(Id_{i}||n_{i})||Sk_{i}^{\prime }||T_{1})\), and verifies the equality \( F_{i}^{\prime } \overset {?}{=} F_{i}\) to check user validity.
-
Sj selects a random value z and computes Cj = Tz (Idi||ni), Wj = TzTy(Idi||ni), \(Sk_{j} = h(W_{i}^{\prime }||W_{j}||T_{1})\) and Fj = h(Skj||Wj||T2).
-
Sj transmits {Fj,Cj,T2}.
-
On receiving {Fj,Cj,T2}, Ui verifies the correctness of T2, then executes \(W_{j}^{\prime } = T_{z}T_{y}(Id_{i}||n_{i})\), \(Sk_{i} = h(W_{i}||W_{j}^{\prime }||T_{1})\) and \(F_{j}^{\prime } = h(Sk_{i}||W_{j}^{\prime }||T_{2})\) and verifies \(F_{j}^{\prime } \overset {?}{=} F_{j}\). If verification succeeds, Ui accepts \(Sk_{i} = h(W_{i}||W_{j}^{\prime }||T_{1})\).
Security Analysis
Our construction achieves mutual authentication and makes a secure communication between the Ui and the Sj.
Description of Existing Attacks
Our protocol is secure against insider attack, offline PAG attack, online PAG attack, server IMP attack and the user IMP attack, which are described below:
-
Three factor authentication: Ui with valid smart cart can execute the login session only after successfully delivering three factors {Idi,Pwi,Hi} as session executes after the verification of \(D_{i} \overset {?}{=} h(X_{i}||Pw_{i}||Id_{i}||H_{i})\), where Hi = hb(biometric) and Xi = h(Idi||Pwi||Hi) ⊕ Bi. In order to get Xi = Tx(Idi||ni)′, R requires three factors {Idi,Pwi,Hi} as Xi = Ai ⊕ Bi, where \(A_{i}^{\prime }= h(Id_{i}||Pw_{i}||H_{i})\). The two factors (pwi, biometric) are only with Ui. The Third factor (Idi) masked value (Gi) is transmitted, where Gi = Idi ⊕ h(Ty(Idi||ni)||Wi||T1). To extract, Idi from Gi, R has to calculate Wi = TyTx(Idi||ni), which is computationally infeasible.
-
Anonymity and unlinkability: Dynamic value (masked identity) Gi instead of Idi is involved in the message transmission, i.e. {Ci,Gi,Fi,T1}. Moreover, it is computationally infeasible to achieve Idi using Gi and Ty(Idi||ni) as Gi = Idi ⊕ h(Ty(Idi||ni)||Wi||T1), where Wi = TyTx(Idi||ni). It justifies that protocol ensures anonymity.
Furthermore, linking of any two sessions messages is not possible in proposed protocol as all the values of transmitted messages {Ci,Gi,Fi,T1} and {Fj,Cj,T2} calculated using randomly generated values or timestamp. In other words, since during communication Ty(Idi||ni), Tz(Idi||ni), T1 and T2 changes every time, the proposed protocol supports unlinkability. Hence anonymity and unlinkability is preserved.
-
Insider attack: It is a form of malicious attack performed on a computer or network by entity who is having authorized system access. In our scheme, it is impossible to get a Ui’s password by any destructive insider in the system. Ui submits the masked value of password as h(Idi|Pwi||Hi) instead of Pwi to Sj, where h(.) is considered secure one way function. Thus, due to this secure hash function, any insider is unable to retrieve the password Pwi of the user. Moreover, R cannot guess the password as to guess the password, R needs Hi = hb(biometric).
-
Stolen smart card attack: This attack fails as R is unable to extract the value Tx(Idi||ni), which is required to initiate login session. As Tx(Idi||ni) = Ai ⊕ Bi and Ai = h(Idi||Pwi||Hi), thus to get Tx(Idi||ni) R has to compute Ai = h(Idi||Pwi||Hi). The computation of Ai = h(Idi||Pwi||Hi) requires three factors {Idi,Pwi,Hi}, which are only with Ui. Moreover, neither Ai nor any factor {Idi,Pwi,Hi} are stored in Sc. To directly compute < Tx(Idi||ni) >, Sj secret key x and user’s Idi are required. However, both parameters (x, Idi) are not public.
-
Off-line password guessing attack: To verify the guessed password, R can use the condition \(D_{i} \overset {?}{=} h(X_{i}||Pw_{i}||Id_{i}||H_{i})\). However, the computation of Di requires the knowledge of the secret factors {Idi,Pwi,Hi,Xi}, where Hi = hb(biometric), Xi = Ai ⊕ Bi, \(A_{i}^{\prime }= h(Id_{i}||Pw_{i}||H_{i})\). To compute Xi from Bi, {Idi,Hi} are needed other then guessed Pwi. Since both the factors (Idi,Hi), are unknown to R, it cannot correctly guess Pwi.
-
Replay attack: This attack is a kind of network attack where transmission of valid data is maliciously delayed or repeated by an originator or by an advisory who intercepts the data and retransmits it. In our scheme, R can retrieves the old transmitted messages {Ci,Gi,Fi,T1} and {Fj,Cj,T2} as these messages transmits via public channel. However, Sj and Ui can easily verify the replay of old messages using timestamp.
-
User impersonation attack: R can retrieves the messages {Ci,Gi,Fi,T1} and {Fj,Cj,T2} as these messages transmits via public channel. However, to establish a valid session R has to compute the fresh login message as proposed scheme resist replay attack. R cannot modify the previously transmitted message {Ci,Gi,Fi,T1} to impersonate as R has to update Fi = h(Tx(Idi||ni)||Wi||T1), which is not possible as this is the output of hash function and to freshly compute Fi, Tx(Idi||ni) is needed. Moreover, R can also get the values {Bi,Di,ni} from the lost/ stolen card. However, this information is also not sufficient to impersonate a valid user, which is shown in stolen smart card attack.
-
Server impersonation attack: The R, with the knowledge of {h(.),Bi,Di,ni} and old transmitted messages {Ci,Gi,Fi,T1} and {Fj,Cj,T2}, cannot impersonate a server as follows:
-
(a)
Ui can easily detect old transmitted message {Fj, Cj,T2} using timestamp T2 and Fj = h(Skj|| Wj||T2), where Wj = TzTy(Idi||ni), Skj = h(Wi ||Wj||T1) and Wi = TyTx(Idi||ni).
-
(b)
R cannot generate fresh response by impersonating server as R has to compute Fj = h(Skj||Wj ||T2), which requires the information of Sj or Ui secret key.
-
(a)
-
Forward secrecy: With the knowledge of Sj’s secret key x, R cannot compute \(Sk_{i} = h(W_{i}||W_{j}^{\prime }||T_{1})\) as
-
(a)
Session key is defined as h(Wi||Wj||T1).
-
(b)
Computation of Ski requires, the computation of Wi and Wj, where Wi = TyTx(Idi||ni) and Wj = TzTy(Idi||ni).
-
(c)
Computation Wj = TzTy(Idi||ni) using Ty(Idi|| ni) and Tz(Idi||ni) is infeasible.
-
(d)
Without the knowledge of Wj, R cannot compute Ski.
-
(a)
Proof of Security
In this section, the security of our proposed scheme is explained against the general attacks. Here, we follow the symbols of [6].
-
(a) Existential-UNT-QSE (E-UNT-QSE): Here, the R is not successful to choose request format of the user by communicating with the server and the smart card. In addition to that, he would not be able to eavesdrop over the existing channel.
-
(b) Forward-UNT-QSER (F-UNT-QSER): Here, the R would not be able to trace past information on receiving the smart card which leaks stored information.
The following channels are to be used for oracles in our proof:
-
CHA1: Transmitting messages to the Sj from the Ui.
-
CHA2: Transmitting messages to the Ui from the Sj.
The following oracles will be used in our proof:
-
Query(\({\pi _{U}^{i}}, m_{1}, {\pi _{S}^{j}}\)) A request m1 is sent to the server by R via CHA1.
-
Send(\(\pi _{S_{j}}^{k}, m_{2}, {\pi _{U}^{i}}\)): On receiving the query in CHA2, m2 is sent to the server by R via CHA2 in order to obtain the Sj’s access.
-
Execute(\({\pi _{U}^{i}}, {\pi _{S}^{j}}\)):R uses an instance of the protocol P run between Sj and smart card, and retrieves the messages which are communicated via CHA1, CHA2.
-
Reveal (\({\pi _{U}^{i}}\)): R obtains the stored information in the smart card of the user. This may be utilized once so that Query (Q), Send (S), Execute (E) and Reveal (R) may not be applied further.
Theorem 1
The proposed key agreement protocol P is E-UNT-QSE.
Proof
Let us assume that R has taken \(\mathcal {Q}\)-Oracle so that \(\omega _{i}(U_{1})\in \{\mathit {Query}(\pi _{U_{1}}^{i}, *)\}\) and \(\omega _{i}(U_{2})\in \{\mathit {Query}(\pi _{U_{2}}^{i}, *)\}\). The output m1 ∈〈Ci,Fi,T1〉 of \(\mathcal {Q}\)-Oracle and simultaneously m2 ∈〈Cj,Ti〉,Fi of the Sj are unlinkable due to the dynamic parameter Fi = h(Tx(Idi||ni)||Wi||T1). To retrieve Idi, R has to find y from Ty(Idi||ni) which is chaotic based discrete logarithm problem. Since, DLP problem is computationally hard, R cannot get Idi from Fi and Ty(Idi||ni). Additionally, Fi = h(Tx(Idi||ni)||Wi||T1) is generated using random number y as Wi = TyTx(Idi||ni). For different sessions this changes Fi, which is essential. During communication also the time-stamp T1 changes. Therefore, it is impossible to link the communicated messages. The Sj sends Hi after inserting T2. Cj = Tz(Idi||ni) is clearly dynamic. Here, the value Idi is masked with the dynamic value so that in each session the output is changing. Hence, the proposed scheme offers anonymity along with unlinkability in the communication between Ui and Sj.
In CHA1, the Ui cannot be impersonated by R since he has no knowledge about Pwi, Idi and the private key x of Sj. In a similar manner, the Sj cannot be impersonated by R in CHA2 as he has no knowledge about Sj’s secret key x and the user’s Idi. Hence, our scheme stops unauthorized Ui and Sj to impersonate in CHA1 and CHA2. Thus, in the given \(\mathcal {Q}\)-Oracle, the R’s advantage is not important as he gets no useful information. Therefore, P is E-UNT-Q. Assume that R gets QS-Oracle’s access such that \(\omega _{i}(U_{1})\in \{Query(\pi _{U_{1}}^{i}, *), Send(*, \pi _{U_{1}}^{i})\}\) and \(\omega _{i}(U_{2})\in \{Query(\pi _{U_{2}}^{i}, *), Send(*, \pi _{U_{2}}^{i})\}\). The Sj will not be impersonated by R he has no knowledge of Idi, y and the Sj’s secrete key. Therefore, R has trivial advantage with the \(\mathcal {QS}\)-Oracle’s help. So, P is E-UNT-QS. Let us consider that the R has \(\mathcal {QSE}\)-Oracle’s access such that \(\omega _{i}(U_{1})\in \{Query(\pi _{U_{1}}^{i}, *), Send(*, \pi _{U_{1}}^{i}), Execute(\pi _{U_{1}}^{i}, {\pi _{S}^{j}})\}\) and ωi \((U_{2})\!\in \! \{Query(\pi _{U_{2}}^{i}, *), Send(*, \pi _{U_{2}}^{i}),\) \( Execute(\pi _{U_{2}}^{i}, {\pi _{S}^{j}} \}\). Due to the fresh use of y,T1,T2, the messages exchanged during P’s execution are unique. Moreover, the replay of an old is stopped by the timestamp. Any old message cannot be used further as the Sj verifies a masked message and the R has no knowledge of the server’s private key x and the random number y. Hence, P is E-UNT-QSE which is the necessary security feature. □
Theorem 2
Our key agreement protocol P is resistant to active-attacks.
Proof
Suppose R gets \(\mathcal {QSE}\)-Oracle’s access and in all the session, during communication he modifies the message. If the Sj or the Uj believe that a modified message is correct then the protocol is not secure against an active attack. In this case, our goal is to prove that the R has a trivial advantage. Suppose, the R uses the \(\mathcal {Q}\)-Oracle to change a message in the CHA1 and simultaneously in the CHA2. But, the modified message cannot be accepted in the Sj and Ui as the Sj verifies Ti, the Fi and the Idi in M1 during authentication phase. Moreover, Hi in M1 is verified by the user during the authentication phase.
If the R uses the \(\mathcal {Q}\)-Oracle to change a message {Ci,Fi,T1} of communication, the Sj verification becomes invalid in Fi = h(Tx(Idi||ni)||Wi||T1).
Due to the chaotic discrete logarithm problem and the hash function, the R cannot modify the message. Furthermore, he uses the \(\mathcal {QS}\)-Oracle to modify a message in the CHA2. Therefore, R will get a trivial advantage because the Ui checks the Cj,T2. Moreover, even if the R has \(\mathcal {QSE}\)-Oracle’s access, then also he would not be able to get success by performing the communication repeatedly. The verification of the modified message is not possible and in the concerned communication, the authorized entity terminates the session key. Hence, P is secure against active attacks. □
Analysis of Security using BAN Logic
BAN logic [26] is a set of rules for analyzing message exchange protocols. BAN logic assumes that the information exchange happens public monitoring.For verification following notations used:
-
1.
A|≡ Y: The principal A acts as Y holds.
-
2.
A ⊲ Y: An entity sent Y to A who can read and repeat Y.
-
3.
\(A |\sim Y\): A once said Y, implies A|≡ Y when A sent it.
-
4.
A|⇒ Y: A controls Y, A has an jurisdiction on Y .
-
5.
#Y: Message Y is fresh means Y never sent before.
-
6.
\(A |\equiv B \overset {{k}}\longleftrightarrow A\): A and B use K common shared key for communication.
-
7.
\(A \overset {K}{\rightleftharpoons } B:\) secret K is used by A and B.
-
8.
{Y }k: The Y is encrypted with k.
-
9.
< Y >X: The formula Y is blended with formula X.
-
10.
(Y )k: The Y formula is keyed hash with the k.
For description of BAN logic terms [26], the required rules are discussed below:
Rule (1)
Message means rule care of messages:
For shared private keys:
If A trusts that B knows k and looks X encrypted with k, A trusts that B once said X.
Rule (2)
The nonce verification rule confirms message is recent:
If A trusts that X is fresh and A trusts that B once said X, A trust that B believes X.
Rule (3)
The jurisdiction rule ensures that A trusts B has jurisdiction on X:
Rule (4)
The freshness rule ensures that message is true if one part of message is true:
According to the BAN logic, the presented scheme achieves: Goal 1. \( U_{i}|\equiv (U_{i}\overset {{Sk}}\longleftrightarrow S_{j})\); Goal 2. \(S_{j}|\equiv (U_{i}\overset {{Sk}}\longleftrightarrow S_{j})\); The protocol type:
Message 1. \(U_{i} \rightarrow S_{j}: C_{i} = T_{y}(Id_{i}||n_{i}), F_{i} = h(T_{x}(Id_{i}||n_{i})||W_{i}||T_{1}), T_{1}\).
Message 2. \(S_{j} \rightarrow U_{i}: C_{j}, T_{2}\) We assume the following about the initial condition of the protocol to analyze given protocol: A1: Ui|≡ #(T1); A2: Sj|≡ #(T2); A3: \(U_{i} |\equiv (U \overset {{X_{U}}}\longleftrightarrow S)\); A4: \(S_{j} |\equiv (U \overset {X_{U}}\longleftrightarrow S )\); A5: \(U_{i} |\equiv S |\equiv (U \overset {{X_{U})}}\longleftrightarrow S)\); A6: \(S_{j} |\equiv U |\equiv (U \overset {X_{U}}\longleftrightarrow S )\); We analyze proposed protocol based on the BAN logic and the proof of presented scheme is given as follows:With the message 1, we obtain goal (2):S1: \(S \lhd (ID_{U_{i}}, T_{u_{i}}(y),T_{1})_{x_{u}}, T_{u_{i}}(y).T_{1}\)According to A4, we apply the rule :S2: \(S |\equiv U|\sim T_{1}\)According to the A1, we apply the freshness rule to get:S3: \(S |\equiv \# (ID_{u_{i}}, T_{u_{i}}(x), T_{1})_{X_{u}}\)With the S2 and S3, apply the nonce verificationS4: \(S |\equiv U|\equiv (T_{u_{i}}(y), T_{1})_{X_{u}}\)According to the A4 and S4, we concern the jurisdiction to get:S5: S|≡ T1According to sk = h(TyTx(Idi||ni)||TzTy(Idi||ni)||T1), S5 and A2, we could obtainS6: \(S |\equiv (U \overset {{Sk}}\longleftrightarrow S)\) With the message 2, we could achieve goal (1):S7: \(U \lhd (ID_{u_{i}}, T_{1}, T_{2})_{X_{U}}, T_{2}\)With the assumption A3 and the message meaning rule we get:S8: \(U |\equiv S|\sim T_{2}\)With the A2, we apply the freshness rule and get:S9: \(U |\equiv \# (Id_{u_{i}}, T_{1}, T_{2})_{X_{U}}\)According to the S8 and S9, we apply nonce verification ruleS10: \(U |\equiv S|\equiv (Id_{u_{i}}, T_{1}, T_{2})_{X_{U}}\)With the A3 and S10 we concern the jurisdiction ruleS11: U|≡ T2According to Ski = h(TyTx(Idi||ni)||TzTy(Idi||ni)||T1), S11 and A1, we could obtainS12: \(U |\equiv (U \overset {{Sk}}\longleftrightarrow S)\)Hence,we achieved the goal-1 and goal-2 in the proposed scheme which proves security using BAN logic.
Computational Efficiency Analysis
We utilize the following notations th, \(t_{h_{b}}\), Tme, Tfe, tb, tsym, tc, Tecm describing as computation time of hash function, computation time of bio-hashing, computation time of modulo exponentiation, computation time of fuzzy extractor, computation time of bilinear pairing, computation time of symmetric encryption/ decryption, computation time of chaotic map operation, computation time of elliptic curve point multiplication, respectively.
Generally, telecare medicine services rely on devices with limited storage and low computation cost. This makes the necessity of efficient and secure authentication scheme. Although the existing schemes for TMIS guarantee to remove the security weaknesses, still from Tables 1 and 2 it can be seen that these schemes have weak security. In addition, computational overhead of proposed scheme is comparable with related schemes [15, 16, 20, 21, 24] (see Table 4).
Conclusion
In this paper, the security of recently presented chaotic map-based authentication scheme has been illustrated. We have observed the vulnerabilities of existing scheme against stolen smart card attack, identity guessing attack and impersonation attack. Moreover, many schemes provide limited support to unlikability. In order to ensure secure and authorized communication, we developed an authentication protocol relying on the chaotic map for TMIS to achieve desirable security and performance attributes. Note that the proposed protocol overcome the prevalent limitations in existing protocols. In particular, it allows session key verification and mutual authentication with only two messages exchange. Moreover, it ensures forward secrecy along with anonymity and unlinkability. Furthermore, a comparison of proposed construction with existing protocols in terms of computation cost is provided.
References
Wang Y.: Password protected smart card and memory stick authentication against off-line dictionary attacks. IFIP international information security conference. Springer 1 (1): 489–500, 2012
Wazid M., Das A.K., Kumar N., Conti M., Vasilakos A.V. (2017) A novel authentication and key agreement scheme for implantable medical devices deployment. IEEE Journal of Biomedical and Health Informatics, 22(4), 1299–1309
Wu D., Zhou C.: Fault-tolerant and scalable key management for smart grid. IEEE Transactions on Smart Grid 2 (2): 375–381, 2011
Cao T., Zhai J.: Improved dynamic id-based authentication scheme for telecare medical information systems. Journal of Medical Systems 37 (2): 1–7, 2013
Chen H.M., Lo J.W., Yeh C.K.: An efficient and secure dynamic id-based authentication scheme for telecare medical information systems. Journal of Medical Systems 36 (6): 3907–3915, 2012
Gildas A. (2005) Adversarial Model for Radio Frequency Identification. IACR Cryptology ePrint Archive, 7, 49–62
Lin H.Y.: On the security of a dynamic id-based authentication scheme for telecare medical information systems. Journal of Medical Systems 37 (2): 1–5, 2013
Dolev D., Andrew Y.: On the security of public key protocols. IEEE Transactions on Information Theory 29 (2): 198–208, 1983
Wei J., Hu X., Liu W.: An improved authentication scheme for telecare medicine information systems. Journal of Medical Systems 36 (6): 3597–3604, 2012
Wu Z.Y., Lee Y.C., Lai F., Lee H.C., Chung Y.: A secure authentication scheme for telecare medicine information systems. Journal of Medical Systems 36 (3): 1529–1535, 2012
Xie Q., Zhang J., Dong N.: Robust anonymous authentication scheme for telecare medical information systems. Journal of Medical Systems 37 (2): 1–8, 2013
Zhu Z.: An efficient authentication scheme for telecare medicine information systems. Journal of Medical Systems 36 (6): 3833–3838, 2012
Jiang Q., Ma J., Ma Z., Li G.: A privacy enhanced authentication scheme for telecare medical information systems. Journal of Medical Systems 37 (1): 1–8, 2013
Guo C., Chang C.C.: Chaotic maps-based password-authenticated key agreement using smart cards. Communications in Nonlinear Science and Numerical Simulation 18 (6): 1433–1440, 2013
Hao X., Wang J., Yang Q., Yan X., Li P.: A chaotic map-based authentication scheme for telecare medicine information systems. Journal of Medical Systems 37 (2): 1–7, 2013
Jiang Q., Ma J., Lu X., Tian Y.: Robust chaotic map-based authentication and key agreement scheme with strong anonymity for telecare medicine information systems. Journal of Medical Systems 38 (2): 1–8, 2014
Kohda T., Tsuneda A., Lawrance A.J.: Correlational properties of chebyshev chaotic sequences. Journal of Time Series Analysis 21 (2): 181–191, 2000
Kohda T., Tsuneda A.: Pseudonoise sequences by chaotic nonlinear maps and their correlation properties. IEICE Transactions on Communications 76 (8): 855–862, 1993
Niranchana R., Karuppiah M.: An efficient and secure remote user mutual authentication scheme using smart cards for Telecare. Medical Information Systems Informatics in Medicine Unlocked 16: 1–38, 2019
Madhusudhan R., Nayak C.S.: A robust authentication scheme for telecare medical information systems. Multimedia Tools and Applications 78: 15255–15273, 2019
Li C.-T., Lee C.-C., Weng C.-Y., Chen S.-j.: A secure dynamic identity and chaotic maps based user authentication and key agreement scheme for e-healthcare systems. Journal of Medical Systems 40: 11–233, 2016
Yu L., Kaiping X.: An improved secure and efficient password and chaos-based two-party key agreement protocol. Nonlinear Dynamics 84: 549–557, 2016
Li C.-T., Lee C.-C., Weng C.-Y.: A secure chaotic maps and smart cards based password authentication and key agreement scheme with user anonymity for telecare medicine information systems. Journal of Medical Systems 38: 9–86, 2014
Lee T.F.: An efficient chaotic maps-based authentication and key agreement scheme using smartcards for telecare medicine information systems. Journal of Medical Systems 37 (6): 1–9, 2013
Zhang L., Zhu S., Shanyu T.: Privacy protection for telecare medicine information systems using a chaotic map-based three-factor authenticated key agreement scheme. IEEE Journal of Biomedical and Health Informatics 21 (2): 465–475, 2017
Burrows M., Abadi M., Needham R.M.: A logic of authentication. Proceedings of the Royal Society of London. A. Mathematical and Physical Sciences 426 (1871): 233–271, 1989
Jiang Q., Chen Z., Li B., Shen J., Yang L., Jianfeng M.: Security analysis and improvement of bio-hashing based three-factor authentication scheme for telecare medical information systems. Journal of Ambient Intelligence and Humanized Computing 9: 1061–1073, 2018
Wu F., Xu L., Kumari S., Li X., Das A.K., Shen J.: A lightweight and anonymous RFID tag authentication protocol with cloud assistance for e-healthcare applications. Journal of Ambient Intelligence and Humanized Computing 9: 919–930, 2018
Xu X., Zhu P., Wen Q., Jin Z., Zhang H., He L.: A secure and efficient authentication and key agreement scheme based on ecc for telecare medicine information systems. Journal of Medical Systems 38 (1): 1–7, 2014
Wu F., Xu L.: Security analysis and improvement of a privacy authentication scheme for telecare medical information systems. Journal of Medical Systems 37 (4): 1–9, 2013
Lee T.F., Chang I.P., Lin T.H., Wang C.C.: A Secure and Efficient Password-Based User Authentication Scheme Using Smart Cards for the Integrated EPR Information System. Journal of Medical Systems 37 (3): 1–7, 2013
Jia X., He D., Kumar N., Choo K.R.: A Provably Secure and Efficient Identity-Based Anonymous Authentication Scheme for Mobile Edge Computing. IEEE Systems Journal 14 (1): 560–571, 2020
Mishra D., Obaidat M.S., Rana S., Dharminder D., Mishra A., Sadoun B.: Chaos-Based Content Distribution Framework for Digital Rights Management System. IEEE Systems Journal 15 (1): 570–576, 2021
Li C.-T., Shih D.-H., Wang C.-C.: Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Computer Methods and Programs in Biomedicine 157: 191–203, 2018
Kumar V., Ahmad M., Kumari A.: A secure elliptic curve cryptography based mutual authentication protocol for cloud-assisted TMIS. Telematics and Informatics 38: 100–117, 2019
Salem F.M., Amin R.: A privacy-preserving RFID authentication protocol based on El-Gamal cryptosystem for secure TMIS. Information Sciences 527: 382–393, 2020
Gaikwad V.P., Tembhurne J.V., Meshram C., Lee C.-C. (2021) Provably secure lightweight client authentication scheme with anonymity for TMIS using chaotic hash function. The Journal of Supercomputing, 1–24
Nayak P., Pippal R.S.: Cryptanalysis of Zhian Zhu’s Scheme and Evaluation of TMIS Smart Card Authentication Schemes. Journal of Scientific Research 13 (2): 407–413, 2021
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Research involving human participants and/or animals
This article does not contain any studies with human participants or animals performed by any of the authors.
Informed consent
All the authors have agreed to this submission.
Disclosure of potential conflicts of interest
All authors declare that they have no conflict of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection on Mobile & Wireless Health
Rights and permissions
About this article
Cite this article
Dharminder, D., Kundu, N. & Mishra, D. Construction of a Chaotic Map-Based Authentication Protocol for TMIS. J Med Syst 45, 77 (2021). https://doi.org/10.1007/s10916-021-01750-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10916-021-01750-7