Abstract
How to handle conflict in Dempster-Shafer evidence theory is an open issue. Many approaches have been proposed to solve this problem. The existing approaches can be divided into two kinds. The first is to improve the combination rule, and the second is to modify the data model. A typical method to improve combination rule is to assign the conflict to the total ignorance set \(\varTheta \). However, it does not make full use of conflict information. A novel combination rule is proposed in this paper, which assigns the conflicting mass to the power set (ACTP). Compared with modifying data model, the advantage of the proposed method is the sequential fusion, which greatly decrease computational complexity. To demonstrate the efficacy of the proposed method, some numerical examples are given. Due to the less information loss, the proposed method is better than other methods in terms of identifying the correct evidence, the speed of convergence and computational complexity.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Data fusion has always been a hot topic of research. Many theories proposed to address it, such as the Dempster-Shafer evidence theory (Xiao 2020; Fei and Wang 2022), information fusion in quantum theory (Xiao and Pedrycz 2022; Deng et al. 2023), entropy-based approaches (Pan and Gao 2023; Yang et al. 2022; Zhou et al. 2021), possibility theory (Solaiman and Bossé 2019; Zhou et al. 2022).
Among these methods, the Dempster-Shafer evidence theory has gotten a lot of attention. Compared to probability theory, it requires fewer conditions and can handle uncertain information such as fuzzy, missing, and contradictory information. Therefore it is widely used in decision-making (Xiao 2019; Song et al. 2019; Liao et al. 2020), risk analysis (Chen and Deng 2022; Liang et al. 2021), uncertainty measurements (Moral-García and Abellán 2021; Meng et al. 2020), classification system (Li et al. 2023a), pattern classification (Zhun-Ga Liu et al. 2019; Huang and Xiao 2023; Xiao et al. 2022a), information fusion (Xiao 2022; Xinyang et al. 2022; Xiao et al. 2022b), group decision making settings (Li et al. 2023b; Zhang and Li 2022). Dempster’s combination rule is a crucial method for multi-source combination. But when fusing the highly conflicting evidences, counter-intuitive conditions often occur.
Zadeh (1979) presented an example to illustrate the drawback of the combination rule, that has caused widespread concern. Dealing with contradictory evidence has been extensively researched. The solutions can be divided into two kinds: improving the combination rules and modifying the data model. Yager (1987), Dubois and Prade (1992), Smets (1990) and Lefevre et al. (2002) proposed other combination rules. In addition, Murphy (2000) presented an improved combination rule, which evenly distributes the basic probabilities of the collected evidence. Then, a weighted average in terms of the similarity of evidences was presented for conflict management (Zhang and Deng 2019). Furthermore, several recent works were reported in this area. Liu et al. proposed a new classifier fusion method (Liu et al. 2020). A geometric approach to the theory of evidence was proposed by Cuzzolin (2008). Abellan et al. presented a new hybrid rule and analyzed the mathematical properties Abellán et al. (2021). A method of dealing with high conflicts from the perspective of the network was proposed by Xiong et al. (2021). Deng et al. proposed a method can handle conflicting evidence and produce a fused result that reflects the degree of agreement among the source (Deng et al. 2021). In various fields, conflict management remains a widely discussed and relevant topic.
Yager (1987) pointed out that the normalization of the combination rule is the main reason for counter-intuitive results. To address this issue, the conflict is assigned to the total ignorance set \(\varTheta \) without the normalization step. Yager’s method partially mitigates the counter-intuitive situation of Dempster’s combination rule. However, there are two shortcomings. One is that the convergence rate is relatively slow, and the other is that the uncertainty degree is relatively high. The main reason is that almost all conflicts are not utilized. If all of the conflict is assigned to \(\varTheta \), it would result in the loss of some useful information. In fact, the conflict information contains certain information that could be utilized.
To overcome the problem discussed above, a novel conflict allocation method is proposed. The main contribution is to assign the conflicting mass to the power set (Song and Deng 2021), rather than the total ignorance set. The proposed method offers significant advantages, mainly due to its capability of integrating high-conflict evidence while minimizing the loss of information and accurately identifying the target. Compared to other methods, it shows superior convergence performance and reduces computational complexity. Furthermore, the proposed method supports sequential fusion, making it appropriate for high real-time update systems.
This paper is structured as follows. In Sect. 2, a brief overview of the concepts of Dempster-Shafer evidence theory and a discussion of Yager’s rule. In Sect. 3, a novel method that assigns the conflicting mass to the power set is proposed. The framework and pseudo code of the proposed method are also provided. In Sect. 4, some numerical examples are presented to compare it with other commonly methods. Concluded in Sect. 5.
2 Preliminaries
In this section, brief introductions to previous knowledge are presented.
2.1 Dempster-Shafer evidence theory
Dempster-Shafer evidence theory was first proposed by Dempster (2008) and then expanded by Shafer (1976). It has been researched ever since (Deng 2020; Song et al. 2018; Deng and Jiang 2020), and some applications are being studied in fault diagnosis (Gong et al. 2018) and human reliability analysis (Gao et al. 2021).
2.1.1 Frame of discernment
Let \(\varTheta \) be a fixed set of n exclusive and exhaustive elements, called the framework of discernment (FOD), defined as follows (Shafer 1976):
The power set of \(\varTheta \) is denoted as \(2^\varTheta \), and has \(2^n\) elements, \(2^\varTheta \) is indicated by:
It is different from power sets, as a new type of set called random permutation set have been proposed (Deng 2022). It has received a lot of attention (Zhou et al. 2023; Chen et al. 2023).
2.1.2 Mass function
For \(\varTheta \), the basic probability assignment (BPA), also known as the mass function, can be defined as follows (Shafer 1976):
constrained conditions as follows:
If \(A \in 2^{\varTheta }\) and \(A \ne {\emptyset }\), m(A) represents the degree of belief in the supporting evidence A. The larger m(A), the stronger the evidence that proves. There are some studies about mass function (Xiao 2021; Han et al. 2016; Chen et al. 2021), which has been used in many fields. Related references include (Deng and Jiang 2022; Chang et al. 2021).
2.1.3 Dempster’s combination rule
Given two BPAs \(m_1\) and \(m_2\), their combination \(m_1 \bigoplus m_2\) can be mathematically defined as follows (Shafer 1976):
where A, B, C \(\in 2^\varTheta \), k is a normalization factor,
The conflict coefficient k represents the degree of conflict between two BPAs. When \(k = 0\) indicates that \(m_1\) and \(m_2\) are consistent with each other, while \(k = 1\) means that \(m_1\) and \(m_2\) are completely contradictory. In other words, the two pieces of evidence strongly support different hypotheses that are incompatible with each other. However, it should be noted that when combining highly contradictory evidence using Dempster’s combination rule, the resulting conclusion may be counter-intuitive (Zadeh 1979).
2.2 Yager’s rule
Yager proposed a rule to overcome the counter-intuitive problem of the Dempster’s combination rule, which can be described as (Yager 1987):
where A, B, C \(\in 2^\varTheta \), k is conflicting mass,
Yager’s rule proposes to allocate conflicting mass k to the total ignorance set \(\varTheta \). However, it remains to be discussed whether this approach to managing conflicts is reasonable or not (Yang and Dong-Ling 2013).
2.3 Murphy’s rule
Suppose there are n BPAs \(m_1, m_2,..., m_n\) on \(\varTheta \), Murphy’s rule is expressed as (Murphy 2000),
Then use Eq. (5) and Eq. (6) combine \(m_{AM(A)}\) n - 1 times to get \(m_{M}(A)\). In Murphy’s rule, all BPAs are assigned to the equal weight without taking into account the difference or similarity among different BPAs.
3 The proposed method
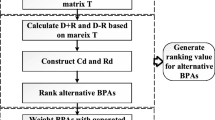
A reasonable method for conflict management named ACTP is proposed in this section. The corresponding framework is shown in Sect. 3.1. The proposed algorithm is illustrated in Sect. 3.2. A simple example is provided in Sect. 3.3.
3.1 Assign conflict to the power set (ACTP)
Example 1
Suppose \(\varTheta = \{A, B\}\), two BPAs as follows,
As shown in Example 1, it can be seen that \(m_1\) and \(m_2\) are completely opposite. If we apply Yager’s rule, \(m_Y(\{A\}) = m_Y(\{B\}) = 0\), \(m_Y(\{\varTheta \})\) = 1. Obviously, after the conflict is given to \(\varTheta \), the result is unreasonable.
Suppose there are two balls of different colors in an opaque box. If we take the ball or balls out of the box, then we can get three \((2^2-1=3)\) situations with the same possibility as shown in Fig. 1a. If there are three balls of different colors, then there are seven \((2^3-1=7)\) situations with the same possibility as shown in Fig. 1b. The main idea of the proposed method is assigning conflict to all situations with the same possibility, that is, all elements in the power set except empty set. By doing this, useful information will not be lost and will be distributed reasonably.
A novel combination rule for conflict management in data fusion which assigns conflict to the power set (ACTP) is proposed. The framework of ACTP is described as Fig. 2. In FOD \(\varTheta = \{\theta _1, \theta _2,..., \theta _n\}\), assume \(m_1,m_2...m_x\) are x pieces of evidence. The power set \(2^\varTheta \) contains \(2^n\) elements. Conflicting mass k is assigned to all elements in the power set except empty set. In this way, k is divided into \({2^n-1}\) parts. We can then utilize the proposed rule to combine the evidence and derive the final combined result.
3.2 The proposed algorithm
Let \(\varTheta \) be a fixed set, which has n mutually exclusive and exhaustive elements. The power set of \(\varTheta \) is \(2^\varTheta \), in which the number of elements is \(2^n\). The formula is given as:
where k is defined in Eq. (6) and n represents each subset of the power set \( 2^{\varTheta }\) except empty set. \(\textbf{k}_{AP}\) is used to redistribute the conflicting mass, which divides k into \(2^n-1\).
For example, given a FOD with 4 elements,
\(\displaystyle \textbf{k}_{AP} = \frac{k}{2^4-1}=\frac{k}{15}.\)
As shown in the example, conflict is divided into 15 on average.
Given two BPAs \(m_1\) and \(m_2\). For the combination of \(m_1\) \(\bigoplus \) \(m_2\), the resulting mass denoted \(m_{AP}\) is given as:
A denotes all subsets in \(\varTheta \) excluding the empty set \(\emptyset \), and \(m_{AP}(A)\) represents the belief value that support the proposition A.
3.3 A simple example
A simple example to show the calculation of ACTP.
Example 2
Suppose \(\varTheta = \{A, B, C\}\), two BPAs as follows,
As shown in Example 2, it can be seen that the value of \(m_1\) supports the object A and \(m_2\) support the object B, while \(m_1(\{A\}) = 0.6\) and \(m_2(\{B\}) = 0.7\). They also have multiple objects, while \(m_1(\{A, B\}) = 0.2\) and \(m_2(\{A, B, C\}) = 0.3\). The calculation processes are given as follows:
First calculate the conflicting mass k according to Eq. (6),
Then, get the \(\textbf{k}_{AP}\) according to Eq. (9),
Finally, using the combination rules based on Eq. (10).
It can be seen from the result that \({m}_{AP}({A})\) is the largest, so object A is the target.
4 Examples and discussions
In this part, some examples are given to demonstrate the benefits of the proposed method.
Example 3
Suppose \(\varTheta = \{A, B\}\), and the following are the two BPAs,
As shown in Example 3, \(m_1\) and \(m_2\) has the same value, while \(m_1(\{A\}) = 0.6\) and \(m_2(\{A\}) = 0.6\), \(m_1(\{B\}) = 0.4\) and \(m_2(\{B\}) = 0.4\). The results shown in Table 1.
As shown in Table 1, it can be observed that all methods correctly identify A. ACTP is found to be as effective as the other methods when dealing with non-conflicting evidence.
Example 4
Suppose \(\varTheta = \{A, B, C\}\), and the following are the two BPAs (Zadeh 1979),
As demonstrated in Example 4, two sources are in high conflict, where source 1 strongly supports A and source 2 supports C. The resulting combination is presented in Table 2.
Table 2 shows that when using Dempster’s rules, the result is \(m(\{B\}) = 1\). This is counter-intuitive. Using Yager’s rule, the result is \(m_Y(\{B\}) = 0.0001\) and \(m_Y(\varTheta ) = 0.9999\), indicating that B only has minimal support and most of the conflict is assigned to the total ignorance set. Hence, both Dempster’s and Yager’s rules are deemed unreasonable.
According to ACTP, \(m_{AP}({B})\) is not significantly greater than other mass functions, indicating that B does not have more support than others. This result is evidently more reasonable, as A, B, and C have approximate probabilities.
Example 5
Suppose \(\varTheta = \{A, B, C\}\), and there are five BPAs as shown in Table 3 (Guo and Li 2011),
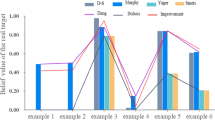
In Example 5, we presented the outcomes of the other five common methods of combining evidence and compared them with our proposed method. The experimental results are illustrated in Tables 4, 5 and Fig. 3. Some discussions are detailed as follows.
(1) Identify the correct evidence
As shown in Table 4, Dempster’s rule produces counterintuitive results. Although the following evidence supports A, the Dempster’s rule supports \(C ( C = 0.8578 )\), but completely against \(A ( A = 0 )\). No matter how much more evidence there is in support of A, Yager’s rule supports \(C ( C= 0.00129 )\) and is totally against \(A ( A = 0 )\). The value of the total ignorance set \(\varTheta \) is increasing, which means increasing uncertainty in the system. Other methods and ACTP can correctly identify A.
(2) The speed of convergence
According to Table 5, Murphy and Li et al. identify the correct target until the 4th evidence appears. In comparison, the convergence speed of the proposed method is better, since identifying correct target A only by two times combined.
(3) Computational complexity
In Fig. 3, Murphy’s method achieves a much higher value than other methods. If there are n evidences in the system, Murphy’s method efficiently combines conflicting evidence by simple averaging. Then use the Dempster’s method to combine n-1 times. The proposed method is a sequential fusion method. When one piece of evidence comes, integrate it immediately. In comparison, the proposed method has lower computational complexity. For example, given a system with 10000 evidence, Murphy’s method needs 9999 times Dempster’s combination process. While the proposed method just need 1 time combination process.
In conclusion, the proposed method is better than other methods in terms of identify the correct evidence, the speed of convergence and computational complexity.
5 Applicaiton
In this section, ACTP is applied in a real-time update system to illustrate its practicability and efficiency. The result is also discussed as well. The data in Li et al. (2020) is used for.
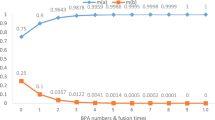
The problem is described as follows. Assuming a radar system is detecting targets from the air. \(\varTheta = \{F_1, F_2, F_3\}\), which means there are three targets. There is a group of five sources of information, \(m_1\) to \(m_5\), providing evidence of the target’s existence. The detection results are shown in Table 6, where each target corresponds to a BPA \(m_i\), \(i \in \{1,2,3,4,5\}\). For example, \(m_1({F_1})=0.5\) indicates that there is a 50% chance of the target object \(F_1\) existing within the scanning range of the radar. By using the rule of ACTP in Eq. (10), these BPAs can be combined to obtain the belief function of the existence of the target object, which provides support for further decision-making. The results are shown in Table 7. It can be seen that BPA of \(F_1\) is the highest one, which means \(F_1\) is the target.
To demonstrate the effectiveness ACTP, we also compared the data with other methods. The results are shown in Table 8 and Fig. 4. Obviously, facing conflicting sources of information \(m_2\), ACTP can effectively identify the target \(F_1\), which is consistent with Murphy’s method and sun et al.’s method. Additionally, Murphy’s method has the highest belief degree \(( F_1 = 0.7958 )\) which is higher than Sun et al.’s method \(( F_1 = 0.2110 )\) and ACTP \(( F_1 = 0.3923 )\).
In the real-time system, new information will always be updated. Assuming the radar system has detected two additional sources, as indicated in Table 9. The results of the fusion using different methods are presented in Table 10. Obviously, as shown in Table 10, in Murphy’s method, the result of sequential fusion is different from the result of simultaneous synthesis. The weighted average method is not suitable for real-time systems. On the contrary, our proposed methods ACTP is simple, fast and accurate. Therefore, this method is particularly suitable for real-time update systems that continuously generate new data.
Our method is not only applicable for target recognition, but it also holds an advantage in group decision-making settings (Dong et al. 2022; Yang et al. 2023). In the process of group decision-making, to achieve consensus, ACTP can be utilized to calculate the evidence trustworthiness among decision-makers and determine the final consensus. In software risk assessment (Chen and Deng 2023), ACTP can also be used to combine different risk assessment values and ultimately form a risk ranking.
6 Conclusion
In this paper, a novel conflict management based on assigning conflict to the power set has been proposed. In the case of high conflict, the performance of fusing evidence can be improved when using ACTP. The experimental results illustrate that the evidence combination rule we proposed is better than other methods. The following is a list of the advantages,
-
(1)
ACTP can identify the target correctly in different alternatives.
-
(2)
Compared with the existing combined method, ACTP has the best convergence performance.
-
(3)
The important point is that ACTP can achieve sequential fusion, which has lower computational complexity. Therefore, it is suitable for high real-time update systems.
In the future, based on ACTP, we can do more research.
(a) According to the main ideas of conflict handling proposed in this paper, more conflict management methods can be designed. (b) Besides target recognition, this new combination rule has the potential application in practical engineering base on sensor data fusion, such as fault diagnosis and risk analysis.
Availability of data and materials
All data and materials generated or analysed during this study are included in this article.
Code availability
The code of the current study is available from the corresponding author on reasonable request.
References
Abellán J, Moral-García S, Benítez MD (2021) Combination in the theory of evidence via a new measurement of the conflict between evidences. Expert Syst Appl 178:114987
Chang L, Zhang L, Chao F, Chen Y-W (2021) Transparent digital twin for output control using belief rule base. IEEE Trans Cybern 52(10):10364–10378
Chen X, Deng Y (2022) An evidential software risk evaluation model. Mathematics 10(13):2325
Chen X, Deng Y (2023) A new belief entropy and its application in software risk analysis. Int J Comput Commun Control 18(2):5299
Chen L, Deng Y, Cheong KH (2021) Probability transformation of mass function: a weighted network method based on the ordered visibility graph. Eng Appl Artif Intell 105:104438
Chen L, Deng Y, Cheong KH (2023) The distance of random permutation set. Inf Sci 628:226–239
Cuzzolin F (2008) A geometric approach to the theory of evidence. IEEE Trans Syst Man Cybern Part C 38(4):522–534
Dempster PA (2008) Upper and lower probabilities induced by a multivalued mapping. Classic works of the Dempster-Shafer theory of belief functions. Springer, Cham, pp 57–72
Deng Y (2020) Uncertainty measure in evidence theory. Sci China Inf Sci 63(11):210201
Deng Y (2022) Random permutation set. Int J Comput Commun Control. https://doi.org/10.15837/ijccc.2022.1.4542
Deng X, Jiang W (2020) On the negation of a Dempster-Shafer belief structure based on maximum uncertainty allocation. Inf Sci 516:346–352
Deng X, Jiang W (2022) A framework for the fusion of non-exclusive and incomplete information on the basis of d number theory. Appl Intell. https://doi.org/10.1007/s10489-022-03960-z
Deng J, Deng Y, Cheong KH (2021) Combining conflicting evidence based on Pearson correlation coefficient and weighted graph. Int J Intell Syst 36(12):7443–7460
Deng X, Xue S, Jiang W (2023) A novel quantum model of mass function for uncertain information fusion. Inf Fusion 89:619–631
Dong Q, Sheng Q, Martínez L, Zhang Z (2022) An adaptive group decision making framework: Individual and local world opinion based opinion dynamics. Inf Fusion 78:218–231
Dubois D, Prade H (1992) Combination of fuzzy information in the framework of possibility theory. Data Fusion Robot Mach Intell 12:481–505
Fei L, Wang Y (2022) An optimization model for rescuer assignments under an uncertain environment by using dempster-shafer theory. Knowl-Based Syst 255:109680
Fuyuan X (2022) Gejs: a generalized evidential divergence measure for multisource information fusion. IEEE Trans Syst Man Cybern. https://doi.org/10.1109/TSMC.2022.3211498
Gao X, Su X, Qian H, Pan X (2021) Dependence assessment in human reliability analysis under uncertain and dynamic situations. Nucl Eng Technol. https://doi.org/10.1016/j.anucene.2017.10.045
Gong Y, Xiaoyan S, Qian H, Yang N (2018) Research on fault diagnosis methods for the reactor coolant system of nuclear power plant based on ds evidence theory. Ann Nucl Energy 112:395–399
Guo K, Li W (2011) Combination rule of d-s evidence theory based on the strategy of cross merging between evidences. Expert Syst Appl 38(10):13360–13366
Han D, Liu W, Dezert J, Yang Y (2016) A novel approach to pre-extracting support vectors based on the theory of belief functions. Knowl-Based Syst 110:210–223
Huang Y, Xiao F (2023) Higher order belief divergence with its application in pattern classification. Inf Sci 635:1–24
Lefevre E, Colot O, Vannoorenberghe P (2002) Belief function combination and conflict management. Inf Fusion 3(2):149–162
Li B, Wang B, Wei J, Huang Y, Guo Z (2001) Efficient combination rule of evidence theory object detection, classification, and tracking technologies. Int Soc Opt Photon 4554:237–240
Li Y, Yang Y, Jiang B (2020) Prediction of coal and gas outbursts by a novel model based on multisource information fusion. Energy Explor Exploit 38(5):1320–1348
Li Y, Herrera-Viedma E, Pérez IJ, Barragán-Guzmán M, Morente-Molinera JA (2023a) Z-number-valued rule-based classification system. Appl Soft Comput 137:110168
Li Z, Zhang Z, Wenyu Yu (2023b) Consensus reaching for ordinal classification-based group decision making with heterogeneous preference information. J Oper Res Soc 0(0):1–22
Liang XR, Yao PY, Liang DL (2008) Improved combination rule of evidence theory and its application in fused target recognition. Electr Opt Control 12:010
Liang Y, Yanbing J, Qin J, Pedrycz W (2021) Multi-granular linguistic distribution evidential reasoning method for renewable energy project risk assessment. Inf Fusion 65:147–164
Liao H, Ren Z, Fang R (2020) A deng-entropy-based evidential reasoning approach for multi-expert multi-criterion decision-making with uncertainty. Int J Comput Intell Syst 13(1):1281–1294
Liu Z-G, Huang L-Q, Zhou K, Denoeux T (2020) Combination of transferable classification with multisource domain adaptation based on evidential reasoning. IEEE Trans Neural Netw Learn Syst 32(5):2015–2029
Meng D, Xie Tianwen W, Peng ZS-P, Zhengguo H, Yan L (2020) Uncertainty-based design and optimization using first order saddlepoint approximation method for multidisciplinary engineering systems. ASCE-ASME J Risk Uncertain Eng Syst Part A. https://doi.org/10.1061/AJRUA6.0001076
Moral-García S, Abellán J (2021) Required mathematical properties and behaviors of uncertainty measures on belief intervals. Int J Intell Syst. https://doi.org/10.1002/int.22432
Murphy CK (2000) Combining belief functions when evidence conflicts. Decis Support Syst 29(1):1–9
Pan L, Gao X (2023) Evidential Markov decision-making model based on belief entropy to predict interference effects. Inf Sci 633:10–26
Qianli Zhou, Ye Cui, Zhen Li, Yong Deng (2023) Marginalization in random permutation set theory: from the cooperative game perspective. Nonlinear Dyn. https://doi.org/10.1007/s11071-023-08506-7
Quan Sun X-Q, Ye W-KG (2000) A new combination rules of evidence theory. Acta Electron Sin 28(8):117–119
Shafer G (1976) A mathematical theory of evidence. Princeton University Press, Princeton
Smets P (1990) The combination of evidence in the transferable belief model. IEEE Trans Pattern Anal Mach Intell 12(5):447–458
Solaiman B, Bossé É (2019) Possibility theory for the design of information fusion systems. Springer, Cham
Song Y, Deng Y (2021) Entropic explanation of power set. Int J Comput Commun Control 16(4):4413
Song Y, Wang X, Zhu J, Lei L (2018) Sensor dynamic reliability evaluation based on evidence theory and intuitionistic fuzzy sets. Appl Intell 48(11):3950–3962
Song Y, Fu Q, Wang Y-F, Wang X (2019) Divergence-based cross entropy and uncertainty measures of Atanassovs intuitionistic fuzzy sets with their application in decision making. Appl Soft Comput. https://doi.org/10.1016/j.asoc.2019.105703
Xiao F (2019) Efmcdm: evidential fuzzy multicriteria decision making based on belief entropy. IEEE Trans Fuzzy Syst 28(7):1477–1491
Xiao F (2020) Generalization of dempster-shafer theory: a complex mass function. Appl Intell 50(10):3266–3275
Xiao F (2021) Ceqd: a complex mass function to predict interference effects. IEEE Trans Cybern. https://doi.org/10.1109/TCYB.2020.3040770
Xiao F, Pedrycz W (2022) Negation of the quantum mass function for multisource quantum information fusion with its application to pattern classification. IEEE Trans Pattern Anal Mach Intell 45(2):2054–2070
Xiao F, Junhao W, Witold P (2022a) Generalized divergence-based decision making method with an application to pattern classification. IEEE Trans Knowl Data Eng. https://doi.org/10.1109/TKDE.2022.3177896
Xiao F, Zehong C, Chin-Teng L (2022b) A complex weighted discounting multisource information fusion with its application in pattern classification. IEEE Trans Knowl Data Eng. https://doi.org/10.1109/TKDE.2022.3206871
Xinyang D, Yebi C, Jiang W (2022) An ecr-pcr rule for fusion of evidences defined on a non-exclusive framework of discernment. Chin J Aeronaut 35(8):179–192
Xiong L, Xiaoyan S, Qian H (2021) Conflicting evidence combination from the perspective of networks. Inf Sci 580:408–418
Yager RR (1987) On the dempster-shafer framework and new combination rules. Inf Sci 41(2):93–137
Yang J-B, Dong-Ling X (2013) Evidential reasoning rule for evidence combination. Artif Intell 205:1–29
Yang X, Xing H, Su X, Ji X (2022) Entropy-based thunderstorm imaging system with real-time prediction and early warning. IEEE Trans Instrum Meas. https://doi.org/10.1109/TIM.2022.3164167
Yang Y, Gai T, Cao M, Zhang Z, Zhang H, Jian W (2023) Application of group decision making in shipping industry 4.0: bibliometric analysis, trends, and future directions. Systems 11(2):69
Zadeh LA (1979) On the validity of Dempster’s rule of combination of evidence. EECS Department, University of California, Berkeley. http://www2.eecs.berkeley.edu/Pubs/TechRpts/1979/28427.html
Zhang W, Deng Y (2019) Combining conflicting evidence using the DEMATEL method. Soft Comput 23:8207–8216
Zhang Z, Li Z (2022) Consensus-based topsis-sort-b for multi-criteria sorting in the context of group decision-making. Ann Oper Res. https://doi.org/10.1007/s10479-022-04985-w
Zhou M, Zhu S-S, Chen Y-W, Jian W, Herrera-Viedma E (2021) A generalized belief entropy with nonspecificity and structural conflict. IEEE Trans Syst Man Cybern 52(9):5532–5545
Zhou Q, Huang Y, Deng Y (2022) Belief evolution network-based probability transformation and fusion. Comput Ind Eng 174:108750
Zhun-Ga Liu Yu, Liu JD, Cuzzolin F (2019) Evidence combination based on credal belief redistribution for pattern classification. IEEE Trans Fuzzy Syst 28(4):618–631
Acknowledgements
The work is partially supported by National Natural Science Foundation of China (Grant No. 61973332), JSPS Invitational Fellowships for Research in Japan (Short-term).
Funding
The work is partially supported by National Natural Science Foundation of China (Grant No. 61973332).
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. All authors performed material preparation, data collection and analysis. Xingyuan chen wrote the first draft of the paper. All authors contributed to the revisions of the paper. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Conflict of interest
Author Xingyuan Chen declares that she had no conflict of interest. Author Yong Deng declares that he has no conflict of interest.
Ethical statement
This article does not contain any studies with human participants or animals performed by any of the authors.
Consent to participate
Informed consent was obtained from all individual participants included in the study.
Consent for publication
The participant has consented to the submission of the case report to the journal.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Chen, X., Deng, Y. A novel combination rule for conflict management in data fusion. Soft Comput 27, 16483–16492 (2023). https://doi.org/10.1007/s00500-023-09112-w
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-023-09112-w