Abstract
According to the human requirement, such as mineral extraction, transportation, etc., tunnel construction is an evident need. Mining and tunneling activities are full of problems with uncertainty, which make these problems complex and difficult. Overbreak is one of these problems that we are encountering in the tunneling process, particularly in the drill and blast method. Overbreak causes to decreasing the safety and increasing the operational costs. Therefore, it must be minimized. Overbreak prediction is the first step to decreasing the damaging effects of this phenomenon. Overbreak influencing factors are classified into two groups of uncontrollable factors and controllable factors. In this study, 267 sets of causing factors and overbreak data were used to overbreak prediction model’s development using the multiple linear and nonlinear regression analysis, artificial neural network, fuzzy logic, adaptive neuro-fuzzy inference system, and support vector machine. The determination coefficient values of these models have been obtained as 0.84, 0.87, 0.93, 96, 0.97, and 0.87, respectively. The results illustrated that the fuzzy and adaptive neuro-fuzzy inference system models have done more appropriate prediction than other prediction models.
Similar content being viewed by others
Explore related subjects
Discover the latest articles, news and stories from top researchers in related subjects.Avoid common mistakes on your manuscript.
1 Introduction
Tunnels and underground spaces are required to be constructed for responding several human requirements, such as mineral extraction, power generation, underground storage, transportation, etc. Without regard to the purpose of tunnel excavation, all are involved in overbreak problems [1]. Overbreak is one of the unfortunate phenomena that we are encountering in the drilling and blasting method. Because of low investment cost and high flexibility against the ground condition variation, drilling and blasting method is the first choice for the tunnel and underground space excavation in comparing another method. However, negative effects of blasting operation in the form of overbreak are inevitable.
Two major groups of factors, geological and blasting parameters, are influenced on the occurrence of overbreak. Some special overbreak incident can be due to the certain factors, but it cannot be generalized without explanation of other influencing factors [2].
Overbreak puts at risk both workers and equipment and adds to dilution of the ore in mines. In addition, it has negative effects on mine and underground space management by producing undesirable works such as dilution and requirements for additional supports and their removal [2].
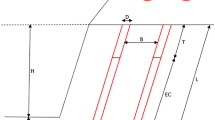
Approximately, 85% of the energy that produced in the blasting operation is not used in the process of rock fragmentation and pulling out of the rock from tunnel face. This energy leads to weakening and damages to the tunnel face surrounding rock mass. This damage is known as overbreak [3]. Therefore, overbreak can be defined as a surplus excavated area of rock further the designed contour in a tunnel [2]. Figure 1 illustrates the overbreak and underbreak in the tunnel blasting.
For minimizing undesirable effects of overbreak, this phenomenon must be controlled and prevented through the tunnel construction. For overbreak prevention, we need to predict it first. Establishment of a predictor model for prediction of overbreak is the primary requirement in the development of overbreak management procedure. However, prediction of the phenomenon like overbreak is not simple. The plural relationship between causing factors and overbreak is not very clear. In fact, there does not exist a crisp relation, which depicts the overbreak according to the causing factors. Therefore, in this study, overbreak prediction models are illustrated using of soft computing methods, which can overcome these difficulties and are capable of address uncertainty. The application of soft computing techniques in the tunneling and mining industry is extensive and covers a considerable number of applications [4].
The present paper is arranged as follows. In Sect. 2, our search of the literature has been described. Section 3 illustrates the factors influencing to overbreak. Section 4 explains the case studies. Section 5 explains the overbreak prediction models. Section 6 evaluates the performance of prediction models and the sensitivity analysis of overbreak causing factors. Finally, Sect. 7 concludes our findings.
2 Literature review
Numerous research papers have been provided to making clear the overbreak. There is summarized of some of the researchers’ attempts.
One of the first attempts in the field of overbreak has done by Longeforse and Lundborg. According to the Longeforse opinion, the delay time between the blast holes should be as small as possible for avoiding blasting damage that caused by the simultaneous blast. Actually, he was believed to the blasting with delays of a few milliseconds. However, Rustan emphasizes that the simultaneous blasting of contour holes has a less effect on the overbreak occurrence and the length of the radial crack emanating from blast holes than short delay blasting [5]. Chakraborty et al. considered the influence of rock quality and joint orientation on the quality of blasting operation in the tunnel. According to their investigation, from the overbreak point of view, in the case of gently dipping joint planes, the planes of weakness are parallel to the tunnel axis. The joint planes limited the transmission of the shock waves towards the roof, but not towards the tunnel axis and the sides of the tunnel. Thus, the overbreak zone towards the roof limited; however, overbreak zone increased towards the tunnel axis and the tunnel sides. In addition, in the case of steeply dipping joint planes, the planes of weakness are perpendicular to the tunnel axis. At this condition, the overbreak zone towards the roof and sides of the tunnel increased; however, overbreak zone limited towards the tunnel axis [6]. Ibarra et al. proposed a linear relationship between overbreak (underbreak) with the logarithm of Q-System value and perimeter specific charge (PCF). They concluded that the rock mass quality is more influential in causing overbreak [7]. Kim et al. applied the guideline to how to draw a contour line, to drill blasting holes, and to charge explosives for overbreak control in the Korean tunnels [8].
Murthy et al. proposed a formula using the peak particle velocity (PPV) threshold levels for overbreak prediction [1]. However, due to the facts that maximum charge per delay is one of the several influencing factors that require being considered and the PPV is a site-specific value, this formula is not credible for use in other cases. The reason is that the formula used only the [2]. Singh and Xavier investigated the causes and impacts of overbreak in underground excavations. Their work showed that suitable drilling and blasting pattern designing and high preciseness in drilling operation have an important role in reducing the amount of overbreak [9]. Schmitz et al. proposed a relationship between the lithology rock mass rating (RMR) value and overbreak. Based on their conclusion, overbreak was related to the RMR, discontinuity spacing, and the orientation of the discontinuities with respect to the tunnel [10]. Dey and Murthy using linear regression analysis introduced a mathematical relationship between the overbreak and rock mass, explosive and blast design parameters [11]. Shiwei et al. have a study on the effect of the lamella joints at the tunnel blasting. According to their paper, it is hard to have minor blasting damage when the lamella joints cross the designed contour line of the tunnel [12].
Implementation of soft computing methods in mining and tunneling field has increased in recent years. Some of the researches are mentioned in Table 1. According to Table 1, the most of researchers have been utilized the soft computing methods in the field of surface excavations; some of them have been used these methods for underground excavation issues. According to the topic of the present paper, three numbers of researches that are in the field of overbreak prediction have been compared in the following.
The first attempt for overbreak prediction using soft computing methods has been done by Jang and Topal for prediction of overbreak of Bigye tunnel in South Korea using the artificial neural network (ANN) and multiple regression. Jang and Topal for the construction of the predictor model used 49 data sets, and six input and one output variables. RMR value unconfined strength of rock (UCS), rock quality designation (RQD), spacing of joints, the state of joints, and ground water condition considered as input variables; in addition, overbreak data considered as an output variable. Based on the results of Jang and Topal study, the multiple layer perceptron ANN with feed forward back propagation (BP) learning algorithm showed a better performance for overbreak prediction than statistical models. The correlation coefficient (R) of ANN and linear and nonlinear multiple regression models have been obtained as 0.945, 0.694, and 0.704, respectively [2].
Jang and Topal in their research took a big step for overbreak prediction using ANN. However, in the presented models, the blasting parameters, which have a great influence on the overbreak occurrence, ignored. Blasting parameters, especially in the contour holes, are very influencing to overbreak.
The second attempt has been done by Sun et al. They introduced a predictor model for the overbreak at Hongfeng tunnel in China, which is constructed using wavelet neural network models. This network is a feed forward network based on the wavelet analysis construction [23]. In this network, the transfer function is a wavelet function and with training the network, in addition to adjusting the connection weight, the wavelet function parameter will be adjusted. Therefore, the model performance will be increased.
Input variables for Sun et al. predictor model consist of geometrical parameters that include the following characteristics: the orientation of the structural plane (dip and dip direction), the trace length of the structural plane, and the spacing of the structural plane. Based on the results of Sun et al. study, the wavelet neural network model could predict overbreak with 10~30% differences between the predicted and measured overbreaks [23].
Similar to the Jang and Topal research, Sun et al. also ignored the blasting parameters. They believe that the influence of blasting parameters will be resolved using advanced construction methods such as smooth blasting method [23]. In addition, only geometrical features of geological parameters have been regarded and parameters such as the strength of rock and state of joints ignored.
The third attempt has been done by Mohammadi et al. using fuzzy logic and linear multiple regression. They introduced overbreak prediction model for Alborz tunnel in Iran. Mohammadi et al., in their study, considered RMR values and joint orientation favorability percentage as geological parameters; powder factor, specific drilling, ratio of number of contour holes to the total number of holes, ratio of amount of charge in contour holes to the burden in contour, and ratio of length of holes to the stemming have been considered as blasting parameters. They used 202 data sets of blasting parameters, geological parameters, and overbreak values as input and output variables of predictor model. The determination coefficient (R 2) between measured and predicted overbreaks has been obtained as 0.96 and 0.55 for fuzzy and multiple linear regression models, respectively [3]. Their results showed that the fuzzy predictor model is a reliable model for overbreak prediction at the Alborz tunnel.
Contrary to the Jang and Topal and Sun et al.’s researches, Mohammadi et al. used both blasting and geological parameters in their research. It is obvious that their fuzzy models have more precise and capable for overbreak prediction. Therefore, for constructing a strong predictor model, it is important to consider most of the overbreak influencing factors.
3 Factors influencing to overbreak
At the prediction step, factors influencing to overbreak have been recognized and analyzed for overbreak prediction. Influencing factors of overbreak are classified into blasting and geological parameters [2]. Geological parameters are uncontrollable and constrained to the project by the ground condition. Blasting parameters are controllable which consist of the blasting design information and can be reconciliation by engineers through the tunnel construction. In addition, there are another causing factors that known as semi-controllable parameters, which consist of excavation shape and size. Figure 2 depicts the causes of overbreak.
Summary of the causes of overbreak [8]
Uncontrollable factors are fixed and most of them, such as the UCS of rock and discontinuity features, have the influential influence on the overbreak [2]. For example, the filling material within a discontinuity walls changes its wave transmission characteristics. Filling material with the small width and the impedance closer to the host rock impedance caused better transmission of strain energy through the discontinuity and reduced the occurrence of overbreak. The presence of clay materials in discontinuity caused weakening rock mass quality (due to the swelling potential), resulting in excessive overbreak [9].
Overbreak also may be the result of poor blast design, especially in contour holes. In addition, if a good blast design poorly implemented (inaccurate drilling and marking out of holes), we should expect overbreak occurrence. Much overbreak is caused by blast holes that diverge or converge and holes that fail to detonate on time and in sequence [7]. Obviously, the accuracy of drilling is more important than the footage per shift [9]. As blasting parameters can be adjusted, overbreak can be controlled by changing these parameters [2]. In addition, an excavation with complex profile results in higher overbreak. Also, the larger excavation span, the higher deformation of the strata and the more overbreak [37].
4 Case studies
In this study, overbreak prediction models have been provided using information of three case studies.
4.1 First case study
Alborz tunnel is the tunnel to be excavated along the Tehran–Shomal Freeway in Iran, which runs through Alborz Mountain Range. The rocks that have been blasted in this tunnel were Tuff and Anhydrite belonging to the Karaj formation. The UCS of the Tuffs ranges from 48 to 158 MPa and ranges from 37 to 68 MPa for Anhydrite. Emulsion cartridges were the explosives that used in the tunnel blasting and explosive cartridge diameter was 35 mm. The blasting area was approximately 65 m2 and the diameter of the holes was 57 mm [3].
4.2 Second case study
This case study is consisting of five tunneling sites from India. Site-1 was a horizontal tunnel of dimension 3.2 × 4.5 m2. The host rock was chlorite–serisite schist with UCS equal to 63 MPa. Holes’ length was 3.2 m. Site-2 was a horizontal tunnel. Tunnel blasting area was 3 × 4 m2. The host rock was chlorite schist with UCS equal to 104 MPa and holes length was 3.2 m. In both Site-1 and Site-2, the initial openings were created with 5 × 3.2 m2 face dimension to have an additional area to locate ventilation ducts, etc. These blasts were carried by 3.2 m holes. Site-3, Site-4, and Site-5 were the horizontal openings of a chromite mine and all tunnels’ blasting area is 2.5 × 2.5 m2. In Site-3, the host rock was serpentinite. In Site-4, the host rock was serpentinite. Site-5 was a tunnel through hard chromite formation. The UCS of the host rocks in Site-1, Site-2, and Site-3 is 67, 81, and 100 MPa, respectively, and their holes’ length was 1.5 m. The emulsion was the explosive that used in the tunnel blasting at each site [11].
4.3 Third case study
Tazare coalmine is one of the Eastern Alborz Coal Corporation mines. This mine is located in the northwest of Shahrood city in Iran through Alborz Mountain Range. The host rocks of the tunnel during this study were Siltstone and Grey Shale. The UCS of the host rocks ranges from 23 to 75 MPa. The explosive type was emulsion cartridges. The diameter of explosive cartridges was 27 mm. The tunnel blasting area was approximately 7.6 m2 and the diameter of drill holes was 35 mm.
5 Overbreak prediction
According to the past researches and collected data, the input parameters have been adopted in some way, which is covering most of the influencing parameters. Therefore, blasting area (excavation size) as a semi-controllable parameter, specific charge, specific drilling, ratio of the amount of charge in contour holes to the contour holes burden value as a blasting parameters, and rock mass rating value as geological parameters are used as input parameters. The specific charge covers explosives’ type and holes’ diameter. The specific drilling covers holes’ length and the ratio of the amount of charge in contour holes to the contour holes burden value covers the perimeter holes’ pattern. In addition, the reason for considering RMR value as an indicator of geological parameters is that the RMR consists of most of the geological parameters, which are influencing on overbreak. The range of input and output parameters are shown in Table 2 along with their symbols. 267 data sets were obtained from the three-mentioned case studies. 232 sets of the data sets were used in model’s construction and 35 sets were used for model’s performance testing (217 data sets were obtained from the Alborz Tunnel, 30 data sets were obtained from the second case study, and 20 data sets were collected from Tazare coal mine blasting operations).
It must be mentioned which geological investigation at the second case study was based on Q-System value, and therefore, using Eq. (1) [38], the Q values turned to the RMR values:
In this paper, soft computing methods, which used for development of overbreak prediction models, have been described in brief. Various literatures, which mentioned in Table 1, can be suitable for more information about soft computing methods.
5.1 Multiple regression models
In multiple regression methods, the relationship between the independent variable (input parameter) and the dependent variable (output parameter) determined in the form of a function. Using this technique, a linear or nonlinear relationship between input and output parameters can be achieved [39]. In this section, the results of overbreak prediction models based on multiple linear and nonlinear regression analysis have been described. To multiple regression analysis, the SPSS software was used.
5.1.1 Multiple linear regression (MLR) model
MLR analysis is employed to create a relationship that explains overbreak as a dependent variable against blasting and geological parameters as independent variables. The multiple linear regression models are obtained using the SPSS software and all the variables entering into the model. Based on the data sets, Eq. (2) was proposed for overbreak prediction. The value of determination coefficient (R 2) of testing the model calculated 0.85 using Eq. (3) [15]. In Eq. (3), OB im is the ith measured overbreak, OB ip is the ith predicted overbreak, \(\overline{\text{OB}}_{\text{p}}\) and \(\overline{\text{OB}}_{\text{m}}\) are the average of predicted and measured overbreak, respectively, and n is the number of data sets:
When MLR analysis is applied, the multicollinearity problem must be managed. This problem takes place when the correlation among the independent variables is robust [2]. Thus, for prevention of multicollinearity problem, instead of entering all the variables into the model, the stepwise method was used. In the stepwise method, all possible combinations of input variables were considered, and if any of these variables had multicollinearity problem, intended variable will be removed [2]. The new overbreak prediction model can be shown as follows:
The R 2 value of testing the new linear model calculated 0.84. Although this value is less than the R 2 value of Eq. (2), the multicollinearity problem is avoided. Figure 3 illustrates the predicted percentage of overbreak against the actual percentage of overbreak for a new MLR model.
5.1.2 Multiple nonlinear regression (MNLR) model
Most of the problems in engineering and specifically in mining and tunneling engineering are complex when many numbers of variables are present in the model. Thus, MLR is restricted in its ability to propose a suitable relationship [2]. Due to the fact that input and output variables in overbreak prediction problem have a nonlinear connection, then MNLR analysis was used to enhance the performance predictor model. Before employing MNLR analysis, the nonlinear model of each input variable versus output variable was determined. The results of this work are presented in Table 3. The final MNLR predictor model was created by the combination of all nonlinear models of input variables. The final model can be shown as follows:
Figure 4 illustrates the predicted percentage of overbreak against the actual percentage of overbreak for the nonlinear regression model. The R 2 value of the nonlinear model is 0.87, which is better than MLR model result. However, the performance of MNLR model is not good enough and it is not a reliable model for overbreak prediction.
The results of statistical methods showed that these methods have a weakness for introducing a proper relationship in complex problems like overbreak prediction. Therefore, soft computing methods can be used as a solution.
5.2 ANN model
An artificial neural network is a soft computing method that motivated by the human brain process. The network architecture, learning algorithm, and transfer function are three components of a typical ANN [29]. The suggested method in this study is the utilization of multi-layer perceptron (MLP) neural network.
The BP algorithm is a well-known algorithm for training MLP networks in a supervised way. In BP algorithm, the weights of the interneuron connections are adapted according to the difference between the predicted and actual network outputs [24, 25].
Forward pass and the backward pass through the network layers are two passes of the BP learning algorithm. Input vector logs into the network and its effect propagates layer by layer in the forward pass of the algorithm (during this pass, the network neuron weights are all fixed). Then, a set of outputs is produced as the output of the network. During the backward pass, according to the error signal (the difference between the network output value and the corresponding actual output value), the network neuron weights are all adapted [25].
To create networks with different architectures, the NeurophStudio software was used. The input data were normalized using Eq. (6), and to determine best network architecture, mean square error (MSE) [Eq. (7)] [22] and R 2 values were calculated for various models. As shown in Table 4, the best architecture of the predictor model was achieved at 5–6–3–1, which consists of 5 inputs, 6 and 3 neurons in the first and second hidden layers, and 1 in the output layer. The trained model attained MSE value of 4.64 at 44 984th iterations. Figure 5 illustrates the predicted values of overbreak against actual values of overbreak for ANN model:
where X 0 is the parameter value, X max is the maximum value of the parameter, and X n is the normalized value of the parameter:
where n is the number of data sets and OB ip and OB im are the ith predicted and measured elements, respectively.
5.3 Fuzzy logic model
Fuzzy logic introduced by Zadeh, which is a powerful tool to deal with linguistic variables and variables with approximate nature, and, therefore, can be used in the problems with uncertainties. In fuzzy logic, if–then rules are used to establish qualitative relationships between the input and output variables. Using this rule base, information can express in the form of language statements. This characteristic makes the models transparent to analysis [18]. In the fuzzy logic, the numerical calculation performed using membership functions (MF) that stipulated with linguistic labels. The degree of membership for each element is in the interval between 0 and 1 (contrary to a classical logic in which the elements degree of membership is 0 or 1) [19].
The first step in fuzzy modeling is fuzzification. In fuzzification step using MFs, numerical values converted to the fuzzy values. The second step is the fuzzy proposition. In this step of the fuzzy process, the relationship between input and output described using fuzzy conditional rules. The selection of fuzzy inference system (FIS) type is the next step. FIS used to aggregate if–then rules and achieving outputs from the given rules and input values. Defuzzification is the final step. In defuzzification, fuzzy values are transformed to crisp values [19]. Centroid of area (COA), mean of maximum (MOM), smallest of maximum (SOM), largest of maximum (LOM), and bisector are defuzzification methods that can be used for this purpose.
The fuzzy model that constructed for overbreak prediction is based on the Mamdani FIS and 232 if–then rules are utilized (using MATLAB Fuzzy toolbox). The triangular and trapezoidal MFs are used in this paper. The MFs of input and output parameters are shown in Fig. 6a–f. The MOM, COA, bisector, SOM, and LOM were applied as defuzzification methods, respectively. According to the result, MOM method has a better performance for defuzzification. Table 5 explains the result of defuzzification methods. Figure 7 shows the results of prediction by fuzzy model.
5.4 ANFIS model
ANFIS is an extension of the Sugeno fuzzy model. In general, ANFIS is much more complicated than FIS. The ANFIS allows the fuzzy systems to learn the parameters of a membership function using adaptive BP learning algorithm [40].
ANFIS has become an attractive method by the combination of learning laws of ANNs and the linguistic transparency of fuzzy logic within the framework of adaptive networks. In the fuzzy logic, model designers can see how the model attained its goal. It is because of that in the FIS, the MFs adapted by trial and error by designers (FIS model act like a white box). On the other side, ANNs can learn, but designers cannot see how the model attained its goal (ANNs act like a black box). Implementing the ANN to improve the parameters of a fuzzy model permits us to learn from a given set of training data. Simultaneously, the solution mapped out into the fuzzy model can be interpreted in linguistic terms as a collection of if–then rules [41].
The ANFIS architecture includes five layers, i.e., a fuzzification layer, a product layer, a normalized layer, a defuzzification layer, and an output layer [25].
In this study, grid partitioning (GP) was used to generate FIS structure. The data space by axis paralleled partitions separates into rectangular subspaces. This separation is based on a predefined number of MFs and their types. The limitation of GP is that the number of rules exponentially increases when the number of inputs increases (the number of input variable: n, the number of MFs for each input: m, the number of fuzzy rules: m n). These large numbers of rules require large memory. According to Jang, GP is only suitable for problems with a small number of input variables like model with less than six input variables [41]. In the present study, the proposed overbreak prediction model has five input variables. It is rational to implement the GP for FIS generation.
For ANFIS model training, the hybrid-learning algorithm was implemented. The hybrid-learning algorithm that proposed by Jang uses forward and backward passes with the combination of the steepest descent and least squares estimate (LSE) learning algorithm. In forward pass, the premise parameters (“if” part) are fixed and the consequent parameters (“then” part) are adapted using the LSE algorithm. In backward pass, the consequent parameters are fixed and the premise parameters are adapted using the gradient descent algorithm [25].
Using the Neuro-Fuzzy toolbox of the MATLAB software, various models with five inputs and one output were examined. MSE value was computed for each constructed model to find the best model. According to Table 6, the model with three numbers of triangle MF for input variable has the better results for overbreak prediction.
Information of the final ANFIS model are shown in Table 7. The predicted percentage of overbreak against the actual percentage of overbreak for ANFIS model is shown in Fig. 8.
5.5 SVM model
SVM is a tool for solving pattern recognition and regression problems. Recently, SVM has attracted a lot of researchers and it is a valuable method for applications in the various fields [42].
The SVM trying to minimize an upper bound of the generalization error rather than to minimize the empirical error is used in neural networks. This is due to the sum of the empirical error and a confidence interval term that bounded generalization error. Confidence interval term depends on the Vapnik–Chervonenkis (VC) dimension. Proper balance between the empirical error and the confidence interval leads to attaining an optimal model structure. SVM transforms an input space to a high-dimensional space. For the establishment of a relationship among inputs and outputs, SVM uses a nonlinear mapping based on a kernel function. SVM also can find proper solutions for problems with small training data [14].
For solving the problems that use SVM for regression, Smola and Schölkopf proposed an iterative algorithm, called sequential minimal optimization (SMO). This algorithm is an extension of the SMO algorithm that proposed by Platt. Calculative speed and easy applying are some of the remarkable characteristics of this algorithm [42].
For the training and testing of the predictor model, the Weka software was used. This software contains many of machine learning algorithms and the SMOreg learning algorithm (Shevada et al. introduced some improvements to Platt’s SMO algorithm and extended SMO algorithm for regression which known as SMOreg [42]) can be applied directly to the data set.
The training process of the SVM model contained the suitable setup of the capacity parameter (C), insensitive loss function (ε), and the kernel function parameter values. For determining the sample distribution in the mapping space, a kernel function should be selected. The radial basis function (RBF) is usually used in many researches as kernel function due to its good performance and few adjustable parameters [43]. Therefore, in this study, the RBF kernel was used as follows:
where x and x ′ are the independent variables and γ is a kernel parameter.
C is a regularization parameter that controls the trade-off between maximizing the margin and minimizing the training error. When the too small value sets up for C, inadequate stress will be placed on the training data fitting. Contrary, when the too large value sets up for C, this too large value may increase over fitting risk. However, Wang et al. indicated that prediction error is hardly affected by C value, and to have stable training process, a large value should be selected for C (e.g., C = 100) [20]. Therefore, in this study, 100 were set up for C parameter.
To find the optimum values of γ and ε and prevent the over fitting risk, the cross validation of the whole training data sets was performed [25]. The mean absolute error (MAE) was used to evaluate the quality of the model [Eq. (9)]. In addition, data sets were normalized by Eq. (6):
The number of support vectors has a close relation with the performance of the SVM and training time. Therefore, for having good performance and rational training time, the optimum value of γ must be determined. The large number of support vectors could cause over fitting and increases the training time. In addition, γ by managing the amplitude of the RBF function can manage the generalization ability of the SVM [43]. Comparing of γ values against MAE on the cross validation for the data set is shown in Fig. 9. As can be seen from Fig. 9, the optimal γ for data sets was 0.5.
Finally, the effect of ε value was tested. Type of noise that present in the data affects the ε value. This noise is usually unknown [20]. Comparing ε values against MAE on the cross validation for data sets is shown in Fig. 10. The optimal ε value for data sets was 0.04.
Therefore, for data sets, the best choices for γ, ε, and C were obtained 0.6, 0.04, and 100, respectively. Figure 11 illustrates the predicted percentage of overbreak against the actual percentage of overbreak using SVM model.
6 Results and discussion
6.1 Evaluation and comparing model’s performance
For comparing model’s performance, R 2 value and the root mean square error (RMSE) (Eq. (10), [15]) as performance indices were used. The model’s performance indices are summarized in Table 8:
The RMSE and R 2 values for ANFIS and fuzzy models against other models show the superiority of ANFIS and fuzzy model over MLR, MNLR, ANN, and SVM models. As can be seen, in this study, the results of ANN and SVM methods have not been satisfactory for overbreak prediction. Most important reason for the superiority of fuzzy and ANFIS models over other constructed models in the present study is considering the uncertainties which exist in the problem variables. Thus, in the problems like mining and tunneling engineering problems, which there are many uncertainties in the nature of the variables, fuzzy and ANFIS methods could introduce better results. Figure 12 illustrates the comparison of measured overbreak and predicted overbreak by ANN, fuzzy, and ANFIS models.
6.2 Sensitivity analysis
To determine the most effective parameters on the overbreak occurrence, the sensitivity analysis was performed. Cosine amplitude method (CAM) was the method, which used for this purpose. In CAM method, all the data pairs are defined as a specific point in m-dimensional space. In this way, each of the parameters is directly connected to the outputs. The strength of this relation r ij is calculated by [19, 22]:
where x i and x j are inputs and outputs, respectively; and m is the number of all data sets. The larger the r ij is, the higher the influence of relevant input is.
The r ij values are shown in Fig. 13. It can be inferred that the specific drilling, specific charge, and rock mass rating are the most influential input parameters on the overbreak phenomenon.
7 Conclusions
In this study, the overbreak prediction models based on MLR, MNLR, ANN, fuzzy, ANFIS, and SVM were developed for overbreak prediction in the tunneling. Models were developed based on the 267 data sets, which were obtained from blasting operations. Parameters such as blasting area, specific charge, and drilling, the ratio of the amount of charge in contour holes to the contour holes’ burden value, and RMR are used as input parameters. The performance of the proposed models was compared with each other. The comparison of R 2 and RMSE values of predictor models showed superiority of the ANFIS and fuzzy models over statistical, ANN, and SVM models in this specific study. R 2 values for ANFIS and fuzzy models were equal to 0.97 and 0.96, respectively. In addition, RMSE values for these models were equal to 1.38 and 1.49, respectively. Finally, using sensitivity analysis, specific drilling, specific charge, and RMR were determined as most effective factors on the overbreak. The overbreak prediction models can be used as a warning system for overbreak incidence before blasting in tunneling and mining projects. Therefore, blasting engineer can modify the controllable parameters and consequently minimize the overbreak amount. The ability and generality of proposed models can be improved by adopting with other tunnel data sets.
References
Murthy VMSR, Dey K, Raitani R (2003) Prediction of over break in underground tunnel blasting a case study. J Can Tunn 109–115
Jang H, Topal E (2013) Optimizing over break prediction based on geological parameters comparing multiple regression analysis and artificial neural network. Tunn Undergr Space Technol 38:161–169
Mohammadi M, Farouq MH, Mirzapour B, Hajiantilaki N (2015) Use of fuzzy logic for minimizing overbreak in underground blasting operations—a case study of Alborz Tunnel, Iran. Int J Min Sci Technol 25(3):439–445
Jang H, Topal E (2014) A review of soft computing technology applications in several mining problems. Appl Soft Comput 22:638–651
Rustan AP (1998) Micro-sequential contour blasting-how does it influence the surrounding rock mass? Eng Geol 49:303–313
Chakraborty AK, Jethwa JL, Palthankar AG (1994) Assessing the effects of joint orientation and rock mass quality on fragmentation and over break in tunnel blasting. Tunn Undergr Space Technol 9(4):471–482
Ibarra JA, Maerz NH, Franklin JA (1996) Over break and under break in underground openings Part2: causes and implications. Geotech Geol Eng 14:325–340
Kim Y, Moon H (2013) Application of the guideline for over break control in granitic rock mass in Korean tunnels. Tunn Undergr Space Technol 35:67–77
Singh SP, Xavier P (2005) Causes, impact and control of over break in underground excavation. Tunn Undergr Space Technol 20:63–71
Schmitz RM, Viroux S, Charlier R, Hick S (2006) The role of rock mechanics in analyzing over break: application to the soumagne tunnel. EURock 2006-Multiphysics coupling and long term behavior in rock mechanics. Taylor & Francis, London, pp 631–636. doi:10.1201/9781439833469.ch92
Dey K, Murthy VMSR (2012) Prediction of blast induced over break from uncontrolled burn-cut blasting in tunnel driven through medium rock class. Tunn Undergr Space Technol 28:49–56
Shiwei S, Lie N, Shulin D, Yan X (2013) Influence mechanism of lamella joints on tunnel blasting effect. Res J Appl Sci Eng Technol 5(20):4905–4908
Monjezi M, Dehghani H (2008) Evaluation of effect of blasting pattern parameters on back break using neural network. Int J Rock Mech Min Sci 45:1446–1453
Khandelwal M, Kankar PK, Harsha SP (2010) Evaluation and prediction of blast induced ground vibration using support vector machine. Int J Min Sci Technol 20:64–70
Monjezi M, Rezaei M, Yazdian A (2010) Prediction of backbreak in open-pit blasting using fuzzy logic. Expert Syst Appl 37:2637–2643
Monjezi M, Bahrami A, Varjani AY, Sayadi AK (2011) Prediction and controlling of fly rock in blasting operation using artificial neural network. Arab J Geosci 4:421–425
Monjezi M, Amini H, Yazdian A (2011) Optimization of open pit blast parameters using genetic algorithm. Int J Rock Mech Min Sci 48:864–869
Fişne A, Kuzu C, Hüdaverdi T (2011) Prediction of environmental impacts of quarry blasting operation using fuzzy logic. Environ Monit Assess 174:461–470
Rezaei M, Monjezi M, Yazdanian VA (2012) Development of fuzzy model to predict fly rock in surface mining. Saf Sci 49(298):305
Amini H, Gholami R, Monjezi M, Torabi SR, Zadhesh J (2012) Evaluation of fly rock phenomenon due to blasting operation by support vector machine. Neural Comput Appl 21:2077–2085
Khandelwal M, Monjezi M (2013) Prediction of backbreak in open-pit blasting operations using the machine learning method. Rock Mech Rock Eng 46:389–396
Sayadi A, Monjezi M, Talebi N, Khandelwal M (2013) A comparative study on the application of various artificial neural networks to simultaneous prediction of rock fragmentation and backbreak. J Rock Mech Geotech Eng 5:318–324
Sun S, Liu J, Wei J (2013) Prediction of overbreak blocks in tunnels based on the wavelet neural network method and the geological statistics theory. Math Probl Eng. doi:10.1155/2013/706491
Hajihassani M, Armaghani DJ, Sohaei H, Tonnizam EM, Marto A (2014) Prediction of airblast-overpressure induced by blasting using a hybrid artificial neural network and particle swarm optimization. Appl Acoust 80:57–67
Esmaeili M, Osanloo M, Rashidinejad F, Aghajani AB, Taji M (2014) Multiple regression, ANN and ANFIS models for prediction of backbreak in the open pit blasting. Eng Comput 30(4):549–558
Armaghani DJ, Hasanipanah M, Mohammad ET (2016) A combination of the ICA-ANN model to predict air-overpressure resulting from blasting. Eng Comput 32(1):155–171
Ghasemi E, Kalhori H, Bagherpour R (2016) A new hybrid ANFIS–PSO model for prediction of peak particle velocity due to bench blasting. Eng Comput 32(4):607–614
Ghasemi E, Amnieh HB, Bagherpour R (2016) Assessment of backbreak due to blasting operation in open pit mines: a case study. Environ Earth Sci 75:552–563
Ebrahimi E, Monjezi M, Khalesi MR, Armaghani DJ (2016) Prediction and optimization of backbreak and rock fragmentation using an artificial neural network and a bee colony algorithm. Bull Eng Geol Environ 75(1):27–36
Dehghani H, Shafaghi M (2017) Prediction of blast-induced flyrock using differential evolution algorithm. Eng Comput 33(1):149–158
Hasanipanah M, Naderi R, Kashir J, Noorani SA, Zeynali AAQ (2017) Prediction of blast-produced ground vibration using particle swarm optimization. Eng Comput. doi:10.1007/s00366-016-0462-1
Hasanipanah M, Shahnazari A, Amnieh HB, Armaghani DJ (2017) Prediction of air-overpressure caused by mine blasting using a new hybrid PSO-SVR model. Eng Comput. doi:10.1007/s00366-016-0453-2
Fouladgar N, Hasanipanah M, Amnieh HB (2017) Application of cuckoo search algorithm to estimate peak particle velocity in mine blasting. Eng Comput. doi:10.1007/s00366-016-0463-0
Hasanipanah M, Golzar SB, Larki IA, Maryaki MY, Ghahremanians T (2017) Estimation of blast-induced ground vibration through a soft computing framework. Eng Comput. doi:10.1007/s00366-017-0508-z
Faradonbeh RS, Monjezi M (2017) Prediction and minimization of blast-induced ground vibration using two robust meta-heuristic algorithm. Eng Comput. doi:10.1007/s00366-017-0501-6
Armaghani DJ, Mohamad ET, Narayanasamy MS, Narita N (2017) Development of hybrid intelligent models for predicting TBM penetration rate in hard rock condition. Tunn Undergr Space Technol 63:29–43
Mahtab MA, Rossier K, Kalamaras GS, Grasso P (1997) Assessment of geological over break for tunnel design and contractual claims. Int J Rock Mech Min Sci 34(3–4):185-e1–185-e13
Singh B, Goel RK (2011) Engineering rock mass classification: tunneling, foundations, and landslides. Elsevier Inc, UK
Armaghani DJ, Amin MFM, Yagiz S, Shirani R, Abdullah RA (2014) Prediction of the uniaxial compressive strength of sandstone using various modeling techniques. Int J Rock Mech Min Sci 85:174–186
Yurdakul M, Gopalakrishnan K, Akdas H (2014) Prediction of specific cutting energy in natural stone cutting processes using the neuro-fuzzy methodology. Int J Rock Mech Min Sci 67:127–135
Abdulshahed AM, Longstaff AP, Fletcher S (2015) The application of ANFIS prediction models for thermal error compensation on CNC machine tools. Appl Soft Comput 27:158–168
Shevade SK, Keerthi SS, Bhattacharyya C, Murthy KRA (2000) Improvements to the SMO algorithm for SVM regression. IEEE Trans Neural Netw 11(5):1188–1193
Zhao CY, Zhang HX, Zhabg XY, Liu MC, Hu ZD, Fan BT (2006) Application of support vector machine(SVM) for prediction toxic activity of different data sets. J Toxicol 217:105–119
Acknowledgements
We are grateful to Mohammad Farouq Hosseini, Mohammad Mohammadi, Kaushik Dey, and V.M.S.R. Murthy for the use of their researches information in this paper. In addition, we are grateful to the chief executive of Eastern Alborz Coal Corporation due to preparing the convenience condition for data gathering.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Mottahedi, A., Sereshki, F. & Ataei, M. Development of overbreak prediction models in drill and blast tunneling using soft computing methods. Engineering with Computers 34, 45–58 (2018). https://doi.org/10.1007/s00366-017-0520-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00366-017-0520-3