Abstract
Scheduling a scientific workflow in a cloud computing environment is a critical issue that is widely discussed in the literature, and since security is one of the most important user concerns, researchers were constantly looking for the most efficient techniques to solve the problem while taking into account the security and privacy of data and tasks. Thus we introduce in this paper, a literature review, taxonomy and comprehensive analysis of the research works that investigate the mentioned problem. Additionally, we highlight and discuss limitations, gaps and problem aspects that are not sufficiently investigated in the literature, as well as future research challenges.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
In a cloud computing environment, scheduling a scientific workflow is a crucial problem that is extensively covered in the literature. The issue attracted a lot of attention due to the powerful features provided by cloud environments, which encourage businesses to carry out their scientific workflows in such environments. Among these characteristics, we distinguish the ability of cloud service providers to offer a pool of resources such as computing power, storage, and bandwidth in the form of on-demand services that users can rent via the Internet. Additionally, the cloud computing platform provides rapid elasticity, extensive network access, and measured services [32].
The problem was designated as multi-objective and multi-constrained due to the varying user needs, e.g., some users need to optimize the workflow execution time, while others are concerned with cost optimization or other objectives such as resource utilization and reliability of the system. In addition, a user can express one or more constraints like deadline, budget, security, and others.
Since security is one of the most important user concerns, researchers were constantly looking for the most efficient techniques to prevent security-related issues, ensure privacy and data confidentiality when scheduling. Thus, in the present paper, we introduce a literature review, taxonomy, and comparative analysis of the different research works that investigate the mentioned problem.
The remainder of this paper is structured as follows. Related work is presented in Sect. 2. In Sect. 3, we provide details about our systematic review process. The main aspects surrounding the workflow scheduling problem are presented in Sect. 4. Additionally, the proposed taxonomy is illustrated in Sect. 5. Then, we summarize the existing secure cloud workflow scheduling approaches in Sect. 6, and we present a comprehensive analysis in Sect. 7 with a highlight of the open issues and challenges in Sect. 8. Finally, Sect. 9 brings the paper to a close.
2 Related Work
Scheduling a scientific workflow in a cloud computing environment is a critical issue that is widely discussed in the literature. In fact, some researchers have tended to provide various heuristic, meta-heuristic, and hybrid approaches to solve the problem while considering different objectives and QoS requirements. However, other researchers have tackled the problem by reviewing, classifying, and analyzing existing solutions.
In this field, certain systematic studies define and assess a wide range of workflow scheduling techniques, classifying them in accordance with various criteria [2, 9, 22, 23, 36]. For example, in [17, 51] The authors concentrated on some of the key workflow scheduling techniques and divided them into static and dynamic scheduling strategies, while in [44] the categorization was done in terms of scheduling criteria, schedule generation, and task-resource mapping. Furthermore, in [31] the authors divided the existing scheduling schemes into task scheduling, workflow scheduling, and task and workflow scheduling schemes. After concentrating on the workflow scheduling schemes, the authors divided them into heuristic and meta-heuristic techniques, and then further divided them based on the type of scheduling algorithms. The existing schemes were similarly categorized into heuristic, meta-heuristic, and hybrid methods by [25]. However, the authors’ focus in [21, 43] was solely on meta-heuristic-based methods for cloud task scheduling. While [4] limited their survey on the existing cost optimization scheduling approaches.
Since security is one of the most important user concerns, researchers were constantly looking for the most efficient techniques to solve the problem under security and privacy considerations. However, till now, no study in the literature summarizes and classifies all the existing secure scheduling schemes, which can make it easier for Cloud Service Provider (CSP) and users to choose the most adequate approach to their needs, it also allows researchers to know the gaps, the existing problems and thus provide more effective solutions. Except, [18] performed an investigation into secured workflow scheduling systems in the cloud setting. But, the work is limited in terms of the number of studied approaches, where they explored only 9 research works, as well as they didn’t provide a critical literature review, and they didn’t mention the limitations of each approach. Consequently, we introduce in the present paper a systematic literature review, taxonomy, and comprehensive analysis of almost all the research works that investigate the aforementioned problem over the last decade. Additionally, we highlight and discuss limitations, gaps, and problem aspects that are not sufficiently investigated in the literature, as well as future research challenges.
3 Systematic Review Process
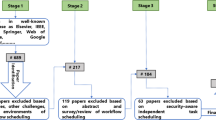
We outline the procedure we used to conduct this review in this section. Where we first gathered different research papers that are published in international journals and conferences during the period (2010–2022), we based on various well-known digital libraries such as Google Scholar,Footnote 1 Springer LNCS,Footnote 2 ScienceDirect—Elsevier,Footnote 3 and IEEE eXplore.Footnote 4 We used different search keywords, e.g., secure workflow scheduling in the cloud, secure optimization, QoS parameters, etc. Second, we examined the collected papers and then deleted the ones that don’t address our problem, or that are not published and indexed in well-known databases. Third, we studied and classified the selected papers, as well as we extracted the gaps of each reviewed paper as described in Sect. 6. Forth, we discussed and analyzed the reviewed approaches as illustrated in Sect. 7. Finally, we conducted the open issues and challenges surrounding the problem as mentioned in Sect. 8 (see Fig. 1).
4 Workflow Scheduling in Cloud
In this section, we describe the most important notions surrounding the cloud workflow scheduling problem.
Scientific Workflow: It is a group of computational tasks that reveal dependencies among them in order to address a scientific issue.
Cloud Environment: Cloud service providers can offer their services in public, private, community, or hybrid environments [32].
-
Public Cloud is a computing environment that allows the public to use resources freely. A corporation, academic institution, government agency, or a combination of them may own, manage, and operate the cloud infrastructure on the premises of the cloud service provider [32].
-
Private Cloud is a computing environment that allows one company to access resources privately. The business, a third party, or a combination of them may own, manage, and operate the cloud infrastructure, which is present on or off the cloud service provider’s premises [32].
-
Community Cloud is a computing environment that allows a community of organizations to access resources privately. The cloud infrastructure may be owned, managed, and maintained by one or more community groups, a third party, or a mix of them. It may exist on or off the cloud service provider’s premises [32].
-
Hybrid Cloud is a computing environment that combines two or more distinct cloud computing environments (public, private, or community) that are linked by standardized or proprietary technology that enables portability of data and applications [32].
Scheduling Strategy: Workflow scheduling strategies are categorized into three categories (static, dynamic, static and dynamic) depending on the workflow resources’ information that was available during the scheduling process [36, 51].
-
Static Scheduling: this type of schedule ends before the workflow execution begins. The advantage of this strategy is that it produces high-quality solutions as it has the possibility of comparing several feasible solutions to obtain the best fit. However, the disadvantage of this strategy is that it only makes estimates concerning missing information such as task execution time and communication time, which may be poor or not adaptable with the real system [36, 49, 51].
-
Dynamic Scheduling: this type of scheduling is done during the execution of the workflow. The advantage of this strategy is that it adapts to real systems as it takes into account unexpected actions that may occur during execution, and relies on exact information about the workflow and resources. However, the disadvantage of the dynamic schedule is that it cannot produce high-quality solutions, because it has not the possibility of trying several feasible solutions and choosing the best one [36, 49, 51].
-
Static and Dynamic: this category combines the two aforementioned scheduling strategies to achieve their advantages simultaneously, where a static mapping is performed before the start of execution based on approximate estimations. Then, during the execution, the assignment is adapted and redone if necessary [36, 51].
Figure 2 shows the scheduling strategies with their advantages and disadvantages.
Workflow Scheduling Objectives and constraints: Usually, the workflow scheduling process has some objectives to achieve and QoS constraints to meet, where these objectives and constraints express the user’s requirements. In the following, we explain these concepts.
4.1 Scheduling Objectives
In the literature, researchers have introduced various scheduling objectives, but the most studied are makespan and cost besides other objectives like resource utilization, energy consumption, load balancing, reliability of the system, throughput, etc.
-
Makespan is the time passed between the beginning of the first workflow task’s execution and the end of the last workflow task [10, 25].
-
Cost is the price that the user has to pay to run his workflow [11].
-
Resource Utilization refers to the optimal use of resources by minimizing time slots of resource inactivity [10].
-
Energy consumption refers to the consumed energy by the cloud servers including the use of electricity and the carbon emissions [2].
-
Load Balancing refers to the balanced distribution of workloads between different computing resources to avoid overloading one of the resources [5, 12].
-
Reliability is the system’s capacity to deliver service for a specific time frame without interruption or failure [39].
-
Throughput is the number of tasks completed in a predetermined period [33].
4.2 User’s Constraints
In the literature, researchers have introduced various scheduling QoS constraints, but the most expressed are deadline, budget, and security.
-
Deadline is the maximum time a user can wait to complete the execution of his workflow.
-
Budget is the maximum price a user can pay to run his workflow in a cloud environment
-
Security defines the user’s needs in terms of security services and scheduling policies to ensure high protection of his sensitive tasks and data.
Workflow Scheduling Algorithms: Generally, researchers have introduced heuristics, meta-heuristics, and hybrid algorithms to fix the cloud workflow scheduling issues.
-
Heuristics generally used to quickly find satisfactory solutions.
-
Meta-Heuristics generally used to find satisfactory solutions for large-scale problems [15].
-
Hybrid algorithms combine two or more heuristic or meta-heuristic algorithms to gain more advantages simultaneously.
5 Taxonomy of Secured Workflow Scheduling Approaches
In this paper, we have reviewed about 32 scientific papers dealing with secure workflow scheduling problem in cloud computing, these papers were selected from the period (2010–2022) using various well-known digital libraries such as Google Scholar,Footnote 5 Springer LNCS,Footnote 6 ScienceDirect—Elsevier,Footnote 7 and IEEE eXplore.Footnote 8 While reviewing the papers, we noticed that they can be classified according to the aspects mentioned in the previous Sect. 4, in addition to the other two parameters that we have extracted while reviewing, where the first relates to the policy of security they used and the second to the security level they targeted. Thus, Fig. 3 illustrates the taxonomy we have proposed for the secure workflow scheduling approaches in cloud environments.
5.1 Security Policy
The research works we have reviewed use different policies to meet the user requirements in terms of security, among them we distinguish two policies: task/data placement policy and security-enhanced scheduling policy.
Task/Data Placement Policy: This category includes the set of studies assuming that the CSP offers secure resources, e.g., the CSP provides some virtual machines that are pre-provisioned with a certain level of security services, even in the case of the hybrid cloud they assume that the private cloud is secure. Therefore, they propose data/task placement policies so that sensitive data/tasks will be mapped to secure resources.
Security-Enhanced Scheduling Policy: This category includes the set of studies assuming that the user has some security requirements, and the available cloud resources cannot meet these requirements, so they enhance the scheduling approach with some hash functions, encryption/decryption algorithms, and security services like authentication, confidentiality, and integrity services.
5.2 Security Level
The research works we have reviewed can be classified according to the level of security they target in three categories: task level, data level, and task and data level.
Task Level: In this category, the scheduler must preserve sensitive tasks, either by adding security services or by implementing placement strategies so that sensitive tasks will be protected.
Data Level: In this category, the scheduler must preserve sensitive data, either by adding security services or by implementing placement strategies so that sensitive data will be protected.
Task and Data Level: In this category, the scheduler must preserve both tasks and data simultaneously, it hybridizes the two aforementioned strategies.
6 Summary of Secured Workflow Scheduling Approaches
In this section, we list and summarize the existing secure workflow scheduling approaches. In addition, we classify them according to the taxonomy proposed in the previous section (Tables 1 and 2). Furthermore, we criticize the existing approaches and extract the disadvantages for each reviewed paper as shown in Table 3, in order to find the gaps and help researchers to improve and cover this research area and provide more effective solutions.
6.1 Task/Data Placement Policy
In the literature, various studies have proposed task/data placement strategies to secure workflow scheduling, so that sensitive tasks/data will be mapped to the most secure resources without affecting the temporal and monetary cost of the workflow scheduling, as described in Sect. 5.1. Table 1 summarizes and classifies the existing studies regarding the taxonomy proposed in the previous section.
-
Xiaoyong et al. [52] offered a Security Driven Scheduling (SDS) algorithm for heterogeneous distributed systems in order to meet tasks security requirements with minimum makespan, where the SDS algorithm measures the trust level of system nodes dynamically, then provides secure scheduling list that considers security overhead and risk probability.
-
Liu et al. [28] presented a Variable Neighborhood Particle Swarm Optimization (PSO) (VNPSO) to solve the scheduling issues for workflow applications in data-intensive distributed computing environments, where the goal of the schedule was to reduce the makespan while maintaining security requirements. To evaluate the proposed VNPSO, they compared it with Multi-Start Genetic Algorithm (GA) (MSGA) and Multi-Start PSO (MSPSO) and they found that VNPSO is the most feasible and efficient.
-
Marcon et al. [30] proposed a scheduling approach in order to reduce the tenant cost while preserving the security and time requirements in a hybrid cloud.
-
Jianfang et al. [24] They utilized a cloud model to assess the security level of tasks and resources as well as the user’s degree of security satisfaction. They developed a Cloud Workflow Discrete PSO (CWDPSO) algorithm to overcome the security issues while scheduling workflows in the cloud. The scheduling goals were to accelerate the execution, reduce the monetary cost and preserve security requirements.
-
Liu et al. [29] proposed a security-aware placement strategy based on the ACO algorithm, which uses dynamic selection to choose the best data centers for intermediate data while taking data transmission time into account.
-
Zeng et al. [54] introduced the concept of an immovable dataset, which limits the transfer of some information for economic and security reasons. In order to offer higher security services and a quicker response time, they also recommended a security and budget-constrained workflow scheduling approach (SABA).
-
Chen et al. [13] presented a Genetic Algorithm (GA)-based technique to reduce the processing cost and preserve data privacy while scheduling data-intensive workflow applications in the cloud, where they considered that the private data can only be placed and scheduled in a specified data center, it cannot be transmitted to or duplicated from other datacenters during scheduling process.
-
Sharif et al. [37] presented the MPHC algorithm with three policies (MPHC-P1/P2/P3) to address task/data privacy and time requirements while reducing workflow execution costs. Regarding privacy protection, they applied and studied two different policies Multi-terminal Cut and Bell-LaPadula.
-
Li et al. [27] introduced a PSO-based security and cost-aware scheduling (SCAS) algorithm, where the scheduling objective was to reduce monetary cost and met the user’s deadline and risk rate constraints.
-
Prince et al. [35] proposed a hybrid workflow scheduling algorithm that combines the HEFT and SABA algorithms, in order to reduce the workflow execution time under deadline, budget, and security limitations.
-
Shishido et al. [41] studied the impact of three meta-heuristic algorithms Practicle Swarm Optimisation (PSO), GA, and Multi Population GA (MPGA) on the cloud workflow scheduling problem; they aimed to minimize cost and met the user’s deadline and risk rate constraints. The experimental results show that in terms of cost and time, GA-based algorithms outperform PSO-based algorithms.
-
Sujana et al. [45] proposed a PSO-based approach to overcome the secure workflow scheduling issue. They used a Smart PSO algorithm to minimize cost and time and met security requirements, and they are based on a Variable Neighborhood PSO algorithm to fix the local optima issue.
-
Thanka et al. [47] suggested a more effective Artificial Bee Colony (ABC) algorithm to reduce time and cost while maintaining the risk rate restriction. According to the experimental findings, the algorithm guarantees security and is better than other similar algorithms in terms of cost, time, and task migration throughout the schedule.
-
Bidaki et al. [8] suggested an Symbiotic Organism Search (SOS)-based method to reduce the processing time and cost while maintaining security. The simulations demonstrate that in terms of cost, makespan, and level of security, the SOS-based method performs better than the PSO-based method.
-
Naidu and Bhagat [34] suggested a Modified-PSO with a Scout-Adaption (MPSO-SA) scheduling approach to reduce workflow execution time under security restrictions. In order to preserve the security constraint, they schedule the workflow tasks in three modes (secure mode, risky mode, and gamma-risky mode) according to the task security requirements. The simulation findings demonstrate that MPSO-SA offers a more cost-effective, low-security risk alternative to GA, PSO, and VNPSO.
-
Arunarani et al. [6] presented the FFBAT algorithm that hybridizes the Firefly and BAT algorithms to reduce the cost of workflow execution while satisfying deadline and risk restrictions. The simulation results demonstrate that, in terms of cost, time, and risk level, FFBAT is preferable to Firefly and BAT algorithms.
-
Xu et al. [53] proposed data placement method to save costs and energy consumption in the hybrid cloud environment, where the scheduling goals were to retain sensitive data while reducing energy use in the private cloud and financial costs in the public cloud.
-
Shishido et al. [42] suggested a Workflow Scheduling Task Selection Policy (WS-TSP), where they used a MPGA to reduce the execution cost while maintaining the deadline.
-
Swamy and Mandapati [46] proposed a fuzzy logic algorithm to address the dynamic cloud workflow scheduling problem while minimizing energy consumption and preserving the user’s security requirements. According to the simulation findings, the algorithm outperforms Max-Min and Min-Min algorithms in terms of makespan, resource utilization, and degree of imbalance.
-
Wen et al. [50] proposed a Multi-Objective Privacy-Aware (MOPA) workflow scheduling system, which intended to reduce cost while maintaining the privacy protection requirement. The algorithm uses the Pareto optimality technique to determine the trade-off between the scheduling objectives.
-
Abdali et al. [3] suggested a hybrid meta-heuristic scheduling technique that combines the Chaotic PSO algorithm and the ac GA algorithm to reduce risk rate and user limitations while minimizing cost and load balance deviation.
6.2 Security-Enhanced Scheduling Policy
In the literature, various studies have proposed security-enhanced scheduling strategies, where they proposed optimized scheduling schemes that meet the scheduling objectives and QoS constraints, then they add some security service to preserve the task/data privacy as described in Sect. 5.1. Table 2 summarizes and classifies the existing studies regarding the taxonomy proposed in the previous section.
-
Zhu et al. [55] provided a Security-Aware Workflow Scheduling algorithm (SAWS) to save cost and time, enhance resource usage of virtual machines, and maintain security measures. To achieve these objectives and meet the constraints, the approach makes advantage of task slack time, intermediate data encryption, and selective task duplication to fill empty slots.
-
Chen et al. [14] extended the Zhu et al. [55] work, where they presented a scheduling approach with selective tasks duplication, named SOLID, which is a developed version of the SAWS algorithm. The simulation results show that SOLID is more efficient in terms of makespan, monetary costs, and resource efficiency compared to existing similar algorithms.
-
Hammouti et al. [20] established a new workflow scheduling strategy for hybrid cloud to provide clients high security systems at minimal cost and time. The proposed strategy consists of three modules: the Pre-Scheduler, which assigns each task or dataset to be executed or stored in either the private or public cloud; the Security Enhancement Module, which adds the dataset’s necessary security services while minimizing the generated cost overhead; and the Post-Scheduler, which assigns each task or dataset to be executed or stored in the appropriate VM. The results of the experiment demonstrate that the suggested technique maintains the same cost but increases the execution time.
-
Dubey et al. [16] created a new Management System for supplying a Community cloud with multiple organizations (MSMC), where they proposed a new cloud framework enhanced with some security services in addition to three algorithms, where the first is an allocation method that effectively divides up the available VMs across different companies with a variety of employees, the second is scheduling algorithm, called Ideal Distribution Algorithm (IDA) that takes into account cost and time restrictions and the third is an Enhaced IDA (EIDA) algorithm to improve the workload balance.
-
Abazari et al. [1] developed a scheduling technique to reduce makespan and satisfy the task’s security criteria. Moreover, they enhanced the system security by introducing a novel attack response strategy to lessen some cloud security vulnerabilities.
-
Hammed and Arunkumar [19] proposed a new cloud workflow scheduling approach to minimize cost and time and maintain sensitive data. The proposed approach consists of four phases, categorization of tasks, scheduling of tasks, resource allocation, and security provisioning. Where the first phase categorizes the workflow tasks into high sensitive and less sensitive based on user requirements, the second and third phases are concerned with the workflow scheduling and resource allocation with minimum cost and time, and the fourth phase offers a security provisioning only for sensitive tasks resulted from the first phase.
-
Wang et al. [48] proposed a Task Scheduling method concerning Security (TSS) in hybrid clouds, where the scheduling objectives are the completed task number maximization and minimizing the total cost of renting public resources while meeting with user’s security and deadline requirements. Concerning security, they assume that the private cloud is secure, but for tasks assigned to the public cloud, they provide some authentication, integrity, and confidentiality services with different levels according to the user requirements. In addition, the TSS algorithm can control the overhead generated by the security services and minimize the total cost and meet the deadline constraint.
-
Shishido et al. [40] proposed a scheduling strategy employing a multi-population genetic algorithm to save costs and preserve the user’s defined deadline. In addition, they introduced a user annotation technique for workflow tasks according to sensitiveness, subsequently looked at the effects of using security services for delicate tasks. The simulation findings demonstrate that, when compared to existing techniques in the literature, the proposed method can more effectively preserve sensitive tasks at a lower cost.
-
Lei et al. [26] discussed that a hybrid encryption technique is developed using hash functions to maintain data security while data moves between multiple clouds, and a novel privacy- and security-aware scheduling model is also offered. Then, in order to minimize the cost within the restrictions of deadline and privacy, they introduced a simulated annealing method and a privacy- and security-aware list scheduling algorithm.
-
Bal et al. [7] proposed a combined Resource Allocation security with an efficient Task Scheduling algorithm in cloud computing using a Hybrid Machine learning (RATS-HM) technique; it consists of scheduling tasks with minimum makespan and maximum throughput using an improved cat swarm optimization algorithm. Then, allocating resources under bandwidth and resource load constraints using a group optimization-based deep neural network. Finally, an authentication method is suggested for data encryption to secure data storage.
Table 3 summarizes the gaps and disadvantages we found while reviewing the papers, which may help researchers to develop, improve, and cover this research field and provide more effective solutions.
7 Analysis and Discussion
In the present paper, we reviewed about 32 secure scheduling approaches in cloud computing as shown in Tables 1 and 2. In this section, we provide a comprehensive analysis and discussion of the reviewed approaches regarding different aspects, including cloud environment, scheduling strategy, security levels, proposed algorithms, and scheduling objectives as illustrated in Fig. 4.
Cloud Environment. Figure 4a illustrates that the public cloud gains the interest of about 75% of the approaches reviewed, while 22% focus on the hybrid cloud. However, the community cloud is not yet sufficiently studied.
Scheduling Strategy. Figure 4b indicates that most of the studied researches (84%) use static scheduling strategies, while 13% use dynamic strategies and only 3% use static and dynamic strategies, despite the hybrid strategy is more useful than the others.
Security Level. Figure 4c shows that 58% of the reviewed researches aim to secure tasks, while 35% aim to secure data and only 07% aim to secure both task and data simultaneously.
Proposed Algorithm. Figure 4d demonstrates that 50% of the reviewed researches proposed meta-heuristic algorithms to solve the problem, while 41% of them proposed heuristic algorithms and only 9% proposed hybrid algorithms.
Optimization problem and Scheduling Objectives. Among Fig. 4e we notice that 62% of studied researches investigated single-objective optimization problems, while 38% considered multi-objective optimization problems. Concerning the scheduling objectives, we observe that Cost and Makespan are the most targeted objectives.
Figure 5 indicates that the problem of secure workflow scheduling has not been discussed sufficiently in the past decade and that most of the papers reviewed were published in 2017. However, it didn’t receive much attention during 2010–2014 and 2020–2022.
8 Open Issues and Challenges
Among the previous sections, we conclude that the problem of secure workflow scheduling in cloud computing is not yet sufficiently discussed in the literature. Consequently, we extract the following issues and challenges:
-
Introduce dynamic scheduling strategies, as they are more adaptable to real systems and take more parameters into consideration.
-
Introduce hybrid scheduling strategies (static and dynamic), as they provide high-quality solutions and they are adaptable to the real systems at the same time.
-
Provide scheduling approaches that aim to secure both task and data, in order to improve and ensure the security of all the workflow.
-
Provide more secure scheduling approaches that address the hybrid and community clouds as they are insufficiently studied.
-
Introduce secure scheduling approaches that address more scheduling objectives, e.g., energy, load balancing, etc.
-
Focus on multi-objective optimization approaches, as they aim to provide trade-off solutions between different scheduling objectives.
-
Provide more robust scheduling security-enhanced policies to keep tasks and data secure simultaneously.
9 Conclusion
In this paper, we reviewed the existing secure workflow scheduling strategies, we outlined important aspects surrounding the problem, and then we introduced a taxonomy to categorize existing research papers. Moreover, we provided a comprehensive analysis, and hence we derived different gaps, issues, and challenges that can help researchers to improve and cover this research area and provide more effective solutions. In future studies, we can investigate the aforementioned issues and challenges.
References
Abazari F, Analoui M, Takabi H, Fu S (2019) Mows: multi-objective workflow scheduling in cloud computing based on heuristic algorithm. Simul Model Pract Theory 93:119–132
Adhikari M, Amgoth T, Srirama SN (2019) A survey on scheduling strategies for workflows in cloud environment and emerging trends. ACM Comput Surv (CSUR) 52(4):1–36
Ali Abdali S (2019) A new optimization method for security-constrained workflow scheduling. Indian J Comput Sci Eng (IJCSE) 10(1)
Alkhanak EN, Lee SP, Rezaei R, Parizi RM (2016) Cost optimization approaches for scientific workflow scheduling in cloud and grid computing: a review, classifications, and open issues. J Syst Softw 113:1–26
Anju Baby J (2013) A survey on honey bee inspired load balancing of tasks in cloud computing. Int J Eng Res Technol 2(12):1442–5
Arunarani A, Manjula D, Sugumaran V (2017) FFBAT: a security and cost-aware workflow scheduling approach combining firefly and bat algorithms. Concurr Comput Pract Exp 29(24):e4295
Bal PK, Mohapatra SK, Das TK, Srinivasan K, Hu YC (2022) A joint resource allocation, security with efficient task scheduling in cloud computing using hybrid machine learning techniques. Sensors 22(3):1242
Bidaki M, Tabbakh SRK, Yaghoobi M, Shakeri H (2017) Secure and efficient SOS-based workflow scheduling in cloud computing. Int J Secur Its Appl 11:41–58
Bittencourt LF, Goldman A, Madeira ER, da Fonseca NL, Sakellariou R (2018) Scheduling in distributed systems: a cloud computing perspective. Comput Sci Rev 30:31–54
Blythe J, Jain S, Deelman E, Gil Y, Vahi K, Mandal A, Kennedy K (2005) Task scheduling strategies for workflow-based applications in grids. In: CCGrid 2005. IEEE international symposium on cluster computing and the grid, vol 2, pp 759–767. IEEE
Buyya R, Murshed M (2002) A deadline and budget constrained cost-time optimisation algorithm for scheduling task farming applications on global grids. arXiv preprint cs/0203020
Cao J, Spooner DP, Jarvis SA, Saini S, Nudd GR (2003) Agent-based grid load balancing using performance-driven task scheduling. In: Proceedings international parallel and distributed processing symposium. IEEE, pp 10–pp
Chen C, Liu J, Wen Y, Chen J, Zhou D (2015) A hybrid genetic algorithm for privacy and cost aware scheduling of data intensive workflow in cloud. In: International conference on algorithms and architectures for parallel processing. Springer, pp 578–591
Chen H, Zhu X, Qiu D, Liu L, Du Z (2017) Scheduling for workflows with security-sensitive intermediate data by selective tasks duplication in clouds. IEEE Trans Parallel Distrib Syst 28(9):2674–2688
Desale S, Rasool A, Andhale S, Rane P (2015) Heuristic and meta-heuristic algorithms and their relevance to the real world: a survey. Int J Comput Eng Res Trends 351(5):2349–7084
Dubey K, Shams MY, Sharma SC, Alarifi A, Amoon M, Nasr AA (2019) A management system for servicing multi-organizations on community cloud model in secure cloud environment. IEEE Access 7:159535–159546
Fakhfakh F, Kacem HH, Kacem AH (2014) Workflow scheduling in cloud computing: a survey. In: 2014 IEEE 18th international enterprise distributed object computing conference workshops and demonstrations. IEEE, pp 372–378
Francis AO, Emmanuel B, Zhang D, Zheng W, Qin Y, Zhang D (2018) Exploration of secured workflow scheduling models in cloud environment: a survey. In: 2018 sixth international conference on advanced cloud and big data (CBD). IEEE, pp 71–76
Hammed SS, Arunkumar B (2019) Efficient workflow scheduling in cloud computing for security maintenance of sensitive data. Int J Commun Syst 35(2)
Hammouti S, Yagoubi B, Makhlouf SA (2020) Workflow security scheduling strategy in cloud computing. In: International symposium on modelling and implementation of complex systems, Springer, pp 48–61
Houssein EH, Gad AG, Wazery YM, Suganthan PN (2021) Task scheduling in cloud computing based on meta-heuristics: review, taxonomy, open challenges, and future trends. Swarm Evol Comput 62:100841
Ibrahim IM et al (2021) Task scheduling algorithms in cloud computing: a review. Turk J Comput Math Educ (TURCOMAT) 12(4):1041–1053
Jain S, Meena J (2019) Workflow scheduling algorithms in cloud computing: an analysis, analogy, and provocations. In: Innovations in computer science and engineering. Springer, pp 499–508
Jianfang C, Junjie C, Qingshan Z (2014) An optimized scheduling algorithm on a cloud workflow using a discrete particle swarm. Cybern Inf Technol 14(1):25–39
Kaur S, Bagga P, Hans R, Kaur H (2019) Quality of service (QoS) aware workflow scheduling (WFS) in cloud computing: a systematic review. Arab J Sci Eng 44(4):2867–2897. http://springerlink.bibliotecabuap.elogim.com/10.1007/s13369-018-3614-3
Lei J, Wu Q, Xu J (2022) Privacy and security-aware workflow scheduling in a hybrid cloud. Futur Gener Comput Syst 131:269–278
Li Z, Ge J, Yang H, Huang L, Hu H, Hu H, Luo B (2016) A security and cost aware scheduling algorithm for heterogeneous tasks of scientific workflow in clouds. Futur Gener Comput Syst 65:140–152
Liu H, Abraham A, Snášel V, McLoone S (2012) Swarm scheduling approaches for work-flow applications with security constraints in distributed data-intensive computing environments. Inf Sci 192:228–243
Liu W, Peng S, Du W, Wang W, Zeng GS (2014) Security-aware intermediate data placement strategy in scientific cloud workflows. Knowl Inf Syst 41(2):423–447
Marcon DS, Bittencourt LF, Dantas R, Neves MC, Madeira ER, Fernandes S, Kamienski CA, Barcelos MP, Gaspary LP, da Fonseca NL (2013) Workflow specification and scheduling with security constraints in hybrid clouds. In: 2nd IEEE Latin American conference on cloud computing and communications. IEEE, pp 29–34
Masdari M, ValiKardan S, Shahi Z, Azar SI (2016) Towards workflow scheduling in cloud computing: a comprehensive analysis. J Netw Comput Appl 66:64–82. https://linkinghub.elsevier.com/retrieve/pii/S108480451600045X
Mell P, Grance T (2011) The NIST definition of cloud computing, p 7
Mohialdeen IA (2013) Comparative study of scheduling algorithms in cloud computing environment. J Comput Sci 9(2):252–263
Naidu PS, Bhagat B (2017) Secure workflow scheduling in cloud environment using modified particle swarm optimization with scout adaptation. Int J Model Simul Sci Comput 9(01):1750064
Prince PB, Ruphavathani DA, Lovesum SJ (2016) A security aware resource allocation model for cloud based healthcare workflows. Indian J Sci Technol 9(45):2–6
Rodriguez MA, Buyya R (2017) A taxonomy and survey on scheduling algorithms for scientific workflows in IaaS cloud computing environments. Concurr Comput Pract Exp 29(8):e4041
Sharif S, Watson P, Taheri J, Nepal S, Zomaya AY (2016) Privacy-aware scheduling SaaS in high performance computing environments. IEEE Trans Parallel Distrib Syst 28(4):1176–1188
Sharif S, Taheri J, Zomaya AY, Nepal S (2013) Mphc: preserving privacy for workflow execution in hybrid clouds. In: 2013 international conference on parallel and distributed computing, applications and technologies. IEEE, pp 272–280
Sharma Y, Javadi B, Si W, Sun D (2016) Reliability and energy efficiency in cloud computing systems: survey and taxonomy. J Netw Comput Appl 74:66–85
Shishido HY, Estrella JC, Toledo CF, Reiff-Marganiec S (2021) Optimizing security and cost of workflow execution using task annotation and genetic-based algorithm. Computing 103(6):1281–1303
Shishido HY, Estrella JC, Toledo CFM, Arantes MS (2017) Genetic-based algorithms applied to a workflow scheduling algorithm with security and deadline constraints in clouds. Comput Electr Eng 69:378–394
Shishido HY, Estrella JC, Toledo CFM, Reiff-Marganiec S (2018) Tasks selection policies for securing sensitive data on workflow scheduling in clouds. In: 2018 IEEE international conference on services computing (SCC). IEEE, pp 233–236
Singh P, Dutta M, Aggarwal N (2017) A review of task scheduling based on meta-heuristics approach in cloud computing. Knowl Inf Syst 52(1):1–51
Smanchat S, Viriyapant K (2015) Taxonomies of workflow scheduling problem and techniques in the cloud. Futur Gener Comput Syst 52:1–12
Sujana J, Revathi T, Priya T, Muneeswaran K (2017) Smart PSO-based secured scheduling approaches for scientific workflows in cloud computing. Soft Comput 23(5):1745–1765
Swamy SR, Mandapati S (2017) A fuzzy energy and security aware scheduling in cloud. Int J Eng Technol 7(2):117–124
Thanka MR, Uma Maheswari P, Edwin EB (2019) An improved efficient: artificial bee colony algorithm for security and QoS aware scheduling in cloud computing environment. Clust Comput 22(5):10905–10913
Wang B, Wang C, Huang W, Song Y, Qin X (2021) Security-aware task scheduling with deadline constraints on heterogeneous hybrid clouds. J Parallel Distrib Comput 153:15–28
Wang Y, Guo Y, Guo Z, Liu W, Yang C (2019) Securing the intermediate data of scientific workflows in clouds with ACISO. IEEE Access 7:126603–126617
Wen Y, Liu J, Dou W, Xu X, Cao B, Chen J (2018) Scheduling workflows with privacy protection constraints for big data applications on cloud. Futur Gener Comput Syst 108:1084–1091
Wu F, Wu Q, Tan Y (2015) Workflow scheduling in cloud: a survey. J Supercomput 71(9):3373–3418
Xiaoyong T, Li K, Zeng Z, Veeravalli B (2010) A novel security-driven scheduling algorithm for precedence-constrained tasks in heterogeneous distributed systems. IEEE Trans Comput 60(7):1017–1029
Xu X, Zhao X, Ruan F, Zhang J, Tian W, Dou W, Liu AX (2017) Data placement for privacy-aware applications over big data in hybrid clouds. Secur Commun Netw 2017
Zeng L, Veeravalli B, Li X (2015) Saba: a security-aware and budget-aware workflow scheduling strategy in clouds. J Parallel Distrib Comput 75:141–151
Zhu X, Zha Y, Jiao P, Chen H (2016) Security-aware workflow scheduling with selective task duplication in clouds. In: Proceedings of the 24th high performance computing symposium, pp 1–8
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Hammouti, S., Yagoubi, B., Makhlouf, S.A. (2023). Secured Workflow Scheduling Techniques in Cloud: A Survey. In: Rao, U.P., Alazab, M., Gohil, B.N., Chelliah, P.R. (eds) Security, Privacy and Data Analytics. ISPDA 2022. Lecture Notes in Electrical Engineering, vol 1049. Springer, Singapore. https://doi.org/10.1007/978-981-99-3569-7_7
Download citation
DOI: https://doi.org/10.1007/978-981-99-3569-7_7
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-3568-0
Online ISBN: 978-981-99-3569-7
eBook Packages: Computer ScienceComputer Science (R0)