Abstract
Cryptographic key establishment is an essential component between any pairwise resource-constrained sensor nodes inside an Internet of Things (IoT) infrastructure. Keeping in mind that IoT devices are computationally limited and resource constrained, it is important that the primitives employed in the construction of any key generation mechanism are lightweight. During communication among IoT sensor nodes/ smart devices, data privacy preservation is a major challenge to handle. In this paper, we propose an oracle for securing communication in IoT environment using lightweight key generation-assisted homomorphic authenticated encryption. In order to judge it’s efficiency and adaptability, we carried out the computational complexity, security, correctness analysis and experimental evaluation of the developed framework. Later, the comparative analysis is also performed with some significant state-of-the-art approaches.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others

Keywords
1 Introduction
With the Internet of Things (IoT) predicted to connect approx 29 billion devices by the end of 2022, securing these particular connected appliances is surely a big security concern [1]. Security is a term that is used to encompass the notions such as integrity, confidentiality and privacy that typically are achieved utilizing cryptographic encryption procedures [2, 3]. Establishing and supervising a group key in a particular IoT environments, where the involved devices are resource constrained, battery-powered, as well as the groups [4] are dynamic by computational nature, which is certainly a non-trivial problem. During the communication among IoT sensor nodes/ smart devices, data privacy preservation is a major challenge to handle. During communication among IoT sensor nodes/ smart devices, data privacy preservation is a major challenge to handle. Homomorphic encryption [5] is one of the most feasible and compatible method to exploit in this scenario. In the field of abstract algebra, homomorphism can be defined as—mapping that preserves all the algebraic structures between domain and the range of an algebraic set.
1.1 Organization of the Paper
Rest of this paper is organized as: Sect. 2 presents the summary of prior works done in this domain over the past years. Our proposed framework/ oracle is presented in Sect. 3. Section 4 presents empirical analysis of the proposed oracle. Experimental evaluation and obtained results along with the comparisons with different schemes are presented in Sect. 5. Finally, Sect. 6 presents the conclusive summary of this paper.
2 Related Work
A matrix-based key establishment scheme without the secret sharing consideration is presented in [2]. Mesmoudi et al. [3] proposed an smart and dynamic key management prototype for the hierarchical wireless sensor networks. Chen et al. in [6] developed a secure light weight network coding pseudonym scheme. This developed scheme can defend against insider as well as outsider adversarial attackers. Authors in [7] have proposed efficient linearly homomorphic authenticated encryption method. Nafi et al. [8] Given a lightweight key establishment protocol for IoT sensor nodes exploiting matrix-based primitives. Singh et al. [9] have given a scheme for pairwise key agreement with updation of key pre-distribution private shares while new nodes are being added to the MANET. Zhang et al. [10] given an authenticated key agreement scheme using one-way hash functions. Gebremichael et al., in their work [4], implemented a computationally secure and lightweight group key establishment protocol appropriate for resource-constrained IoT nodes.
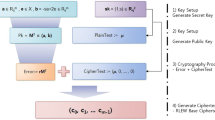
3 Proposed Framework
The adopted framework along with the detailed algorithmic procedure steps is given in this section. Summary of notations used is provided in Table 1.
3.1 Authentication
Consider \(S_i\) is the i-th registered sensor node in the communication ecosystem. The steps in this authentication phase are as follows:
-
1.
Each \(S' \in set~of~S_{i}^{s}\) inputs their \(\lbrace I, P \rbrace \), then mobile computes SID = \(SID^m \oplus h(I||P)\), \(a_i\) = \(a_i^m\) \(\oplus \) h(I||P). Next, it randomly selects the 140-bit number \(\theta \) \(\in \) \(Z_n^*\) & current time-stamp T. Finally, it sends auth_req message \((msg_1, msg_2, msg_3, msg_4)\) to CS via public channel. \(msg_1\) = h(\(SID_s || T\)) \(\oplus \) \(SID_i\) \(msg_2\) = h(\(SID_i || SID_s || a_i\)) \(\oplus \) \(\theta \) \(msg_3\) = h(\(SID_i || SID_s || a_i || \theta \)) \(\oplus \) \(SID_j\) \(msg_4\) = h(\(SID_i || SID_j || SID_s|| a_i || \theta \))
-
2.
After receiving \((msg_1, msg_2, msg_3 and msg_4)\) from each \(S'\), CS checks validation of time as \(\mathbb {T} - T\) \(\le \) \(\delta \), where \(\delta \) is max time threshold for acceptance of messages and \(\mathbb {T}\) is depicting the current time obtained message. If it’s true \(\Rightarrow \) (goes towards the next phase), else \(\Rightarrow \) (CS rejects authentication request).
3.2 Key and Other Parameters Generation
-
1.
KMC Generates ’a’.
-
2.
KMC chooses \(\mathcal {K}\)[ ][ ] as random orthogonal matrix of dimension ’n’ using sub-procedure given below 2(a): Use recursive definition for \(\mathcal {K}^{(n)}\), starting with \(\mathcal {K}^{(1)}\) = [1] as
$$ \mathcal {K}^{(2n)}= \left[ {\begin{array}{cc} \mathcal {K}^{(n)}c_n &{} -\mathcal {K}^{(n)}s_n \\ \widehat{\mathcal {K}}^{(n)}s_n &{} \widehat{\mathcal {K}}^{(n)}c_n \\ \end{array} } \right] $$where, \(\widehat{\mathcal {K}}^{(n)}\) has some form as \(\mathcal {K}^{(n)}\) except that the \(c_i\) and \(s_i\) indices are all increased by n. 2(b): Use the following formula to determine the (i, j) entry, \((\mathcal {K}^{(n)})_{i,j}\), in \(\mathcal {K}^{(n)}\): \((\mathcal {K}^{(n)})_{i,j}\) = \(\prod _{r = 1}^{k} {{t_i}_r}\) \((\theta _{{2}^r} \lfloor \frac{(i-1)}{2^{r}} \rfloor + 2^{(r-1)} + j_r \frac{\pi }{2})\) where, i-1 = \(i_1\) + 2\(i_2\) + \(\cdots \) + \(2^{(k-1)} i_k\) j-1 = \(j_1\) + 2\(j_2\) + \(\cdots \) + \(2^{(k-1)} j_k\) the \({i_r}'s\) and \({j_r}'s\) are 0 (or) 1, \({t_0}(\theta ) = cos(\theta )\) & \({t_1}(\theta ) = sin(\theta )\)
-
3.
KMC sends generated parameters ’a’ and \(\mathcal {K}\)[ ][ ] to IoT sensor node over the secure channel.
3.3 IoT Sensor Node Side Computation
-
1.
Generates two equal size sets \(S_1\) and \(S_2\) having elements as random primes, where each set consists of ’a’ number of elements
$$S_1 = X_1, X_2, X_3, \cdots , X_a$$$$S_2 = Y_1, Y_2, Y_3, \cdots , Y_a$$ -
2.
Compute \(n_1 \leftarrow X_1 \times Y_1, n_2 \leftarrow X_2 \times Y_2, \ldots , n_a\) \(\leftarrow X_a \times Y_a\)
$$S = \prod \limits _{i=1}^{a} n_i$$ -
3.
Calculate transpose of orthogonal matrix \(\mathcal {K}\) as \(\mathcal {K}^T\)
$$\mathcal {K}^T \leftarrow \, \text {Transpose}\,(\mathcal {K})\, \text {mod} \mathbb {Z}_{S}$$ -
4.
Node provides input as \(\mathcal {M}\) ranges from 1 to S.
-
5.
Node generates \(\mathbb {R}\) ranges from 1 to S such that \(\mathbb {R}\) \(\ne \) \(\mathcal {M}\).
-
6.
Create matrix Y of dimension [\(a \times (n-1)\)], such that each row comprises only single event of \(\mathcal {M}\) and remaining (\(n-2\)) occurrences of \(\mathbb {R}\).
-
7.
Apply Chinese Remainder Theorem (CRT) to obtain the solutions (\(\alpha _1\), \(\alpha _2\), \(\alpha _3\),..., \(\alpha _{(n-1)}\)) of corresponding simultaneous equations as follows:
$$\begin{array}{cc} Y_{11}\, \text {mod}\, n_1 = \alpha _1, Y_{12}\, \text {mod}\, n_1 = \alpha _2, \cdots , Y_{1(n-1)}\, \text {mod}\, n_1 = \alpha _{(n-1)}\\ Y_{21}\, \text {mod}\, n_2 = \alpha _1, Y_{22}\, \text {mod}\, n_2 = \alpha _2, \cdots , Y_{2(n-1)}\, \text {mod}\, n_2 = \alpha _{(n-1)}\\ \cdot \\ \cdot \\ Y_{a 1}\, \text {mod}\, n_a = \alpha _1, Y_{a 2}\, \text {mod}\, n_a = \alpha _2, \cdots , Y_{a (n-1)}\, \text {mod}\, n_a = \alpha _{(n-1)}\end{array}$$ -
8.
Node encrypts input data \(\mathcal {M}_i\) as:- \(\mathcal {C}_{i_{\_}MAT}\) \(\leftarrow \) \(\mathcal {K}^T\) \(\times \) D[\(\mathcal {M}_i\), \(\alpha _1\), \(\alpha _2\), \(\alpha _3\),..., \(\alpha _{n-1}\)] \(\times \) \(\mathcal {K}\), where D represents diagonal matrix of dimension n\(\times \)n with diagonal elements as \(\mathcal {M}_i\), \(\alpha _1\), \(\alpha _2\), \(\alpha _3\),..., \(\alpha _{n-1}\) and remaining elements are zeros.
-
9.
Node outsources the encrypted data \(\mathcal {C}_{i_{\_}MAT}\) to the cloud server for computation.
3.4 Computation on Encrypted Data
-
1.
Perform homomorphic computation on received encrypted data from sensor node.
-
2.
Circuit computation for encrypted data \(\mathcal {C}_{i_{\_}MAT}\) upto optimal depth.
-
3.
Sends back the computed results to sensor node.
3.5 Decryption Circuit Evaluation
Sensor node decrypts the computed result as
\(P_{i_{\_}MAT}\) \(\leftarrow \) \(\mathcal {K}\) \(\times \) \(\mathcal {C}_{i_{\_}MAT}\) \(\times \) \(\mathcal {K}^T\)
Do, \(\psi _i\) \(\leftarrow \) \(P_{i_{\_}MAT[1][1]}\)
if (\(\psi _i\) == \(\mathcal {M}_i\))
Results Verified.
4 Empirical Analysis of Proposed Oracle
4.1 Computational Complexity Analysis
Subprocedure 3.2 takes \(O(log(n)n^2)\) time complexity, where n is dimension of the random orthogonal matrix.
Subprocedure 3.3 (step 4) takes \(O(n^2)\) time in computation.
Subprocedure 3.3 (step 7) involves to take a system of t congruences of form \(x \equiv a_i~(mod~{n_i})\) and carrying out certain computations to obtain all the solutions which are in form
Thus, (I) involves amortized cost of \(O(len(\mathbb {N})^2)\).
Subprocedure 3.3 (step 8) and 3.5 consist of mainly matrix multiplication which requires essentially cubic number of operations, i.e. runs in \(O(n^3)\) time. Though, there is a possibility to follow procedure [11] with an improved amortized complexity bound as \(O(n^{2.373})\); however, for some higher tensor powers [12], the complexity bound obtained was \(\approx \) \(O(n^{2.5621})\).
4.2 Security and Correctness Analysis
The plaintext \(\mathcal {M}\) is getting encrypted with the generated key \(\mathcal {K}\). Any query comes from IoT sensor node side privately at cloud server such that the cloud responds on requests (i.e. carry out scientific computations on outsourced query parameters) without any intention to know them. The proposed method has ability to perform operations on encrypted data without decrypting them which solves the problem of confidentiality and privacy while communication in IoT infrastructure. We observe that,
Dec_Proc (\(\mathcal {K}\), \(\mathcal {K}^T\), \(\mathcal {C}_{i}\), S)
\(\mapsto \) \(\mathcal {K}\) \(\times \) \(\mathcal {C}_{i_{\_}MAT}\) \(\times \) \(\mathcal {K}^T\)
\(\mapsto \) \(\mathcal {K}\) \(\times \) \(\mathcal {K}^T\) \(\times \) D[\(\mathcal {M}_i\), \(\alpha _1\), \(\alpha _2\), \(\alpha _3\),\(\cdots \), \(\alpha _{n-1}\)] \(\times \) \(\mathcal {K}\) \(\times \) \(\mathcal {K}^T\)
since, \(\mathcal {K}^{-1} = \mathcal {K}^{T}\) i.e. \(\mathcal {K} . \mathcal {K}^{T}\) = \(\mathcal {K}^{T} . \mathcal {K}\) = I
\(\mapsto \) I \(\times \) D[\(\mathcal {M}_i\), \(\alpha _1\), \(\alpha _2\), \(\alpha _3\),\(\cdots \), \(\alpha _{n-1}\)] \(\times \) I
\(\mapsto \) D[\(\mathcal {M}_i\), \(\alpha _1\), \(\alpha _2\), \(\alpha _3\),\(\cdots \), \(\alpha _{n-1}\)]
\(\mapsto \) \(P_{i_{\_}MAT}\)
do, \(\psi _i\) \(\looparrowleft \) \(P_{i_{\_}MAT[1][1]}\)
\(\psi _i\) == \(\mathcal {M}_i\)
It validates the correctness of the proposed oracle.
5 Experimental Evaluation and Results Discussion
Our experimental set-up contains system environment as Ubuntu 16.04 LTS with 64 bit OS, 8 GB RAM, processor as Intel Core i7-860 @ 2.80 GHz clock speed.
Python (v’3.5.2) installed and used for implementation. Results analysis is compiled in form of Tables 2 and 3. In Table 2, different parameter values for a and Dim(\(\mathcal {K}\)) are taken into consideration in each case. After executing proposed procedure, the correctness of the prototype functionality and Error% in decryption circuit is judged. In Table 3, Additive (+) and Multiplicative (\(\times \)) homomorphic properties are validated on different test cases.
5.1 Comparative Analysis
This section presents the benchmarking/ comparisons with some significant existing schemes for secure communication in IoT infrastructure.
In Table 4, N: is the size of problem input with respect to growth rate, MAC: represents message authentication code and \(\lambda \): is the security parameter. Both, the resource requirements of the cryptographic algorithm (or protocol) as well as the adversary’s probability of breaking security are expressed in terms of the security parameter.
6 Conclusion
With the eruptive surge of data produced by different sensor nodes in an IoT ecosystem, the conventional cloud computing strategies by outsourcing entire data to the cloud for computation and processing has moderately failed in order to meet the certain requirements such as: maintaining data privacy, resource-constrained nature, low storage cost and authentication during communication. During communication among IoT sensor nodes/ smart devices, data privacy preservation is a major challenge to handle. This paper proposes an oracle and validates in terms of experimental evaluation, performance and comparative analysis for securing communication in IoT environment using lightweight key generation-assisted homomorphic authenticated encryption.
References
Zhang Y, Xiang Y, Huang X, Chen X, Alelaiwi A (2018) A matrix-based cross-layer key establishment protocol for smart homes. Inf Sci 429:390–405
Mesmoudi S, Benadda B, Mesmoudi A (2019) SKWN: smart and dynamic key management scheme for wireless sensor networks. Int J Commun Syst. 32(7):e3930
Gebremichael T, Jennehag U, Gidlund M (2018) Lightweight IoT group key establishment scheme using one-way accumulator. Computers and Communications (ISNCC), Rome, International Symposium on Networks, pp 1–7
Peralta Goiuri, Cid-Fuentes Raul G, Bilbao Josu, Crespo Pedro M (2019) Homomorphic encryption and network coding in IoT architectures: advantages and future challenges. Electronics 8:827. https://doi.org/10.3390/electronics8080827
Chen YJ, Wang LC (2019) Privacy protection for Internet of Drones: a network coding approach. IEEE Internet Things J 6(2):1719–1730. https://doi.org/10.1109/JIOT.2018.2875065
Cheon JH, Han K, Hong SM, Kim HJ, Kim J, Kim S, Seo H, Shim H, Song Y (2018) Toward a secure drone system: flying with real-time homomorphic authenticated encryption. IEEE Access 6:24325–24339
Nafi M, Bouzefrane S, Omar M (2020) Matrix-based key management scheme for IoT networks. Ad Hoc Netw 97. https://doi.org/10.1016/j.adhoc.2019.102003
Singh A, Tentu AN, Venkaiah VC (2021) A dynamic key management paradigm for secure wireless ad hoc network communications. Int J Inf Comput Secur 14(3/4):380–402. https://doi.org/10.1504/IJICS.2021.10029986
Zhang Y, He D, Li L, Chen B (2020) A lightweight authentication and key agreement scheme for internet of drones. Comput Commun. https://doi.org/10.1016/j.comcom.2020.02.067
Vassilevska Williams V (2012) Multiplying matrices faster than Coppersmith-Winograd. Proc ACM Symp Theor Comput (STOC) 44:887–898
Lim LH (2013) Tensors and hypermatrices. In: Hogben L (ed) Handbook of linear algebra, 2nd edn. CRC Press, Boca Raton, FL
Blom R (1984) An optimal class of symmetric key generation systems. In: Workshop on the theory and application of cryptographic techniques. Springer, Heidelberg, pp 335–338
Zhang Y, Xiang Y, Huang X, Chen X, Alelaiwi A (2018) A matrix-based cross-layer key establishment protocol for smart homes. Inf Sci 429:390–405
Malina L, Srivastava G, Dzurenda P, Hajny J, Ricci S (2019) A privacy-enhancing framework for Internet of Things services. eprint.iacr.org. https://doi.org/10.1007/978-3-030-36938-5_5
Gheisari M, Wang G, ZadaKhan W, Christian F (2019) A context-aware privacy-preserving method for IoT-based smart city using software defined networking. Comput Secur 87:101470
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Singh, A., Tiwari, V., Tentu, A.N., Saxena, A. (2023). Securing Communication in IoT Environment Using Lightweight Key Generation-Assisted Homomorphic Authenticated Encryption. In: Satapathy, S.C., Lin, J.CW., Wee, L.K., Bhateja, V., Rajesh, T.M. (eds) Computer Communication, Networking and IoT. Lecture Notes in Networks and Systems, vol 459. Springer, Singapore. https://doi.org/10.1007/978-981-19-1976-3_26
Download citation
DOI: https://doi.org/10.1007/978-981-19-1976-3_26
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-1975-6
Online ISBN: 978-981-19-1976-3
eBook Packages: EngineeringEngineering (R0)