Abstract
Cognitive radio (CR) technology is a promising solution to the inevitable problem of spectrum scarcity and underutilization. Cognitive radios can perform spectrum sensing, dynamically identify unused spectrum, and opportunistically utilize those spectrum holes for their own transmission. Cognitive radio technology is also a key concept suggested to be part of the fifth generation of cellular wireless standards (5G). Efficient spectrum sensing is crucial to the effective deployment of CR networks. Cooperative spectrum sensing (CSS) schemes can significantly improve the sensing accuracy of CR networks by exploiting multiuser spatial diversity. However, the cooperative gain can be impacted by factors such as the detection performance of each secondary user (SU) and the fusion techniques used to combine the secondary users’ decisions. Moreover, CSS incurs cooperation overhead that may deteriorate its overall performance. In this chapter, we provide a comprehensive survey on the different factors that contribute to the efficient design of CSS schemes for cognitive radio networks. We specifically focus on the elements of cooperative sensing that can leverage the achievable cooperative gain, limit the cooperation overhead, or provide trade-off between the gain and overhead such as the number of channels sensed in each sensing period, the selection of secondary users, the selection of the fusion scheme, and the correlation between the cooperating secondary users. We also highlight key open research challenges in cooperative spectrum sensing.
Access provided by Autonomous University of Puebla. Download reference work entry PDF
Similar content being viewed by others
Introduction
Driven by the proliferation of new wireless services and applications, as well as the steadily increasing number of wireless users, the demand for radio spectrum has increased dramatically. The government regulatory agencies employ inflexible spectrum management approaches by granting each operator an exclusive license to operate in a certain frequency band. With most of the prime radio frequency spectrum already exclusively assigned, it is becoming exceedingly hard to find vacant bands to either deploy new services or enhance existing ones. However, this spectrum scarcity is mainly due to inefficient fixed frequency allocations rather than a physical shortage in the spectrum. This inefficiency in the spectrum usage necessitates a new communication paradigm to exploit the existing wireless spectrum opportunistically. Dynamic spectrum access (DSA) has been proposed as an alternative policy to allow the radio spectrum to be more efficiently utilized [1]. Using DSA, a portion of the spectrum can be licensed to one or more users, which are called primary users (PUs) ; however, the use of that spectrum is not exclusively granted to these licensed users, although they have higher priority in using it. The unlicensed users, which are referred to as secondary users, are allowed to opportunistically utilize the unused licensed bands, commonly referred to as “white spaces” or “spectrum holes,” as long as the primary users’ transmissions can be adequately protected. By doing so, the radio spectrum can be reused in an opportunistic manner or shared all the time which can significantly improve the spectrum utilization efficiency [2]. The key enabling technology of DSA is the cognitive radio (CR) technology.
A cognitive radio system is a radio system which is aware of its operational and geographical environment, established policies, and its internal state. Moreover, it is able to dynamically and autonomously adapt its operational parameters and protocols and to learn from its previous experience [3]. Cognitive radios are enabled by the rapid and significant advancements in radio technologies (e.g., software-defined radios, frequency agility, power control, etc.) and can be characterized by the utilization of disruptive techniques such as wideband spectrum sensing, real-time spectrum allocation and acquisition, and real-time measurement dissemination [4]. To reliably identify the vacant licensed bands, some methods that the secondary users can employ are geolocation combined with access to database, beacons, spectrum sensing, or a combination of any of those methods [5, 6]. In the geolocation method, primary users register the relevant data such as their location and transmit power as well as expected duration of usage at a centralized database. Secondary users then have to access this database to determine the availability of vacant licensed bands at their location. Geolocation database is based on field strength estimates for the primary users obtained using terrain-based radio propagation models. However, the limited geographical information restricts the achievable accuracy of the field strength estimates. Therefore, radio environment mapping (REM) has been introduced as an alternative or complementary procedure to radio propagation models [7,8,9].
In the beacon method, secondary users only transmit if they receive a control signal (beacon) identifying vacant channels within their service areas. Without reception of this control signal, no transmissions are permitted by the secondary users. In [10], beacon-assisted channel access was assumed in which a codeword from the codebook of the primary users is reserved as a beacon, and each time a primary user releases a channel, it broadcasts this beacon message. The authors assumed that the codebook of the primary users as well as the beacon codeword was a priori known to the secondary users. The proposed protocol showed performance gain in terms of more reliable detection of spectrum holes as well as achieving higher secondary channel capacity. In [11], novel detection schemes employed at the fusion center, namely, the robust estimator-correlator detector and the robust generalized likelihood detector, were proposed for multiple beacon signaling-based cooperative spectrum sensing in multiple-input multiple-output wireless cognitive radio networks with channel state information (CSI) uncertainty. Simulation results demonstrated that the proposed detection techniques yield a significant improvement in the detection performance compared to the conventional CSI uncertainty matched filter detector.
With the aforementioned methods, secondary devices will need additional connectivity in a different band in order to be able to access the database [5] or a dedicated standardized channel will be needed to broadcast the beacons [6]. In the spectrum sensing method, secondary users autonomously detect the presence of the primary signals and only use the channels that are not used by the primary users. All the abovementioned methods have their advantages and disadvantages. It is up to the regulator to decide on the best approach with the considerations from all the stakeholders. However, it is expected that in the future, both database and spectrum sensing techniques will be used together in order to have flexibility and achieve maximum efficiency for secondary users [12]. In this chapter, we focus on spectrum sensing performed by cognitive radios because of its relatively lower infrastructure cost and its compatibility with licensed primary systems which allows for broader application areas.
Spectrum sensing enables the capability of a cognitive radio to measure, learn, and be aware of the radio’s operating environment, such as the spectrum availability and interference status. Availability of radio spectrum varies depending on time, frequency, and location resulting in spectrum access opportunities. Secondary users can use the available idle spectrum in an opportunistic manner by identifying the available spectrum reliably and rapidly. It also helps in quickly determining if the primary users have become active in the bands used by secondary users so that those bands can be vacated immediately. This is important for ensuring that the interference caused to the primary users’ transmissions remains below a permitted level. Moreover, detection of other secondary users may be necessary as well for coexistence with other secondary networks. However, due to the effects of multipath fading and shadowing, the signal-to-noise ratio (SNR) of the received primary signal can be extremely low, and a secondary user may not be able to distinguish between a deeply faded band and an idle one. Since receiver sensitivity indicates the capability of detecting weak signals, the sensitivity requirement of the secondary user’s receiver may end up being too stringent. In order to mitigate these effects, secondary users often cooperate for spectrum sensing.
The main idea of cooperative spectrum sensing (CSS) is to enhance the sensing performance by exploiting the spatial diversity in the observations of spatially located secondary users [13,14,15,16,17]. Having multiple cooperating secondary users increases diversity by providing multiple measurements of the signal and, therefore, guarantees a better detection performance. Consequently, the diversity gain achieved through cooperative spectrum sensing improves the overall detection sensitivity without imposing higher sensitivity requirements on individual secondary users [18]. A less stringent sensitivity requirement is particularly appealing from the implementation point of view due to the reduced hardware cost and complexity. The performance improvement due to spatial diversity is called cooperative gain. However, cooperative gain is not limited to the improved detection performance and relaxed sensitivity requirement. For instance, since it is difficult, using a single radio, to transmit on a licensed band and sense it simultaneously, sensing has to be interleaved with data transmission [13, 19]. Therefore, if the sensing time can be reduced due to cooperation, secondary users will have more time for data transmission so as to improve their opportunistic throughput which is also considered a part of the cooperative gain. From the above discussion, it is apparent that well-designed techniques for cooperative spectrum sensing can significantly contribute to improving the achievable cooperative gain. However, CSS can incur cooperation overhead and the achievable cooperative gain can be impacted by many factors. The goal of this chapter is to point out several aspects of cooperative spectrum sensing. These aspects are discussed in the rest of this chapter.
In section “Fundamental Concepts of Spectrum Sensing,” we present the fundamental concepts of spectrum sensing. In section “Sensing Techniques,” we review the most common spectrum sensing techniques for cognitive radio networks and detail their advantages and disadvantages. In section “Cooperative Spectrum Sensing (CSS),” we present the different elements of cooperative spectrum sensing. In section “Performance of Cooperative Spectrum Sensing,” we discuss the different factors impacting the performance of cooperative spectrum sensing. We present some research challenges which offer directions for future work in section “Research Challenges.” Section “Conclusions” concludes this chapter.
Fundamental Concepts of Spectrum Sensing
The spectrum sensing problem is traditionally formulated as a binary hypothesis testing problem as described below. To identify the idle spectrum and protect the primary users’ transmissions, different local spectrum sensing techniques have been proposed for individual secondary users based on hypothesis testing. Some of the most common spectrum sensing techniques for the detection of primary users’ transmissions for cognitive radio networks are discussed in section Sensing Techniques.
Hypothesis Testing
A key task in spectrum sensing is to decide whether the spectrum is idle or busy. The spectrum sensing problem is traditionally formulated as a binary hypothesis test [20]. The null hypothesis denoted by H0 corresponds to the absence of the primary user’s transmission, i.e., the received signal being only noise. On the other hand, the alternative hypothesis denoted by H1 indicates that the primary user’s transmission is present, i.e., the received signal contains the primary signal along with noise. In case the hypotheses have no unknown parameters, the hypotheses are called simple. If there are unknown or unspecified parameters, then the hypotheses are called composite. As an example, a binary hypothesis test for detecting the primary user’s transmission in an additive white Gaussian noise (AWGN) channel is given by
where x(n) denotes the sampled received signal with sampling rate fs (Hz) and an observation time T. The channel gain and primary user’s transmitted signal are denoted by h(n) and s(n), respectively, and v(n) is the AWGN noise.
In most practical cases, a test statistic Y is computed from the observation vector x = [x(1), x(2), .., x(N)] containing N observation samples, where \(N\triangleq f_{s}T\) is assumed to be an integer. The detection is based on comparing the test statistic Y to the threshold γ. If the test statistic is greater than the threshold, i.e., Y > γ, then H1 is declared true. Otherwise, H0 is declared true. Two main performance metrics that are crucial in the design of spectrum sensing techniques are the probability of miss-detection, Pm, and the probability of false alarm, Pf. The probability of miss-detection is defined as the probability that the detector declares the absence of a primary user (PU) transmission (decide H0), when PU transmission is actually present (H1 is true). The probability of false alarm is defined as the probability that the detector declares the presence of PU transmission (decide H1), when PU transmission is actually absent (H0 is true). Therefore, we represent the probabilities of miss-detection and false alarm, respectively, as [21]
and
It is clear that we need the probability of detection to be high as it indicates the level of protection of the primary users’ transmissions from the interfering secondary users’ transmissions. On the other hand, low probabilities of false alarm are necessary in order to maintain high opportunistic secondary throughput, since a false alarm would prevent the unused bands from being accessed by secondary users leading to inefficient spectrum usage .
Primary Transmitter Detection
The transmitter detection model is based on the detection of weak signals from a primary transmitter through the local observations of secondary users. This model has a wider applicability due to its compatibility with the licensed systems. The main drawback of the primary transmitter sensing model is its reliance on the detection of primary transmitters to infer the availability of white spaces while the interference happens at the primary receivers. As such, a detection margin has to be included in order to protect primary receivers [6].
When the primary system employs bursty transmission, the secondary user can detect the empty time slots and multiplex its signal over them without causing any performance degradation at the primary receivers. On the other hand, when the primary system employs continuous transmission, the secondary user has to estimate the interference it generates at the primary receivers by using signal level measurements. If the transmitter of the secondary user is far from the primary receiver, depending on the signal-to-interference ratio (SIR) limit at the receiver of the primary user supplied by the regulatory bodies, both the primary user and the secondary user could transmit data simultaneously [6, 22]. In this case, the interference range is defined as the minimum distance that a secondary transmitter should be away from the primary receiver such that it does not cause harmful interference at this receiver. Figure 1 shows the primary receiver located at a distance \(D^{\prime }_{1}\) from the primary transmitter and \(D^{\prime }_{2}\) is the interference range. The interference range will depend on the SU-transmitted power and the primary receiver’s interference tolerance and can be obtained from [23]
where \(P^{\prime }_{u}\) and \(P^{\prime }_{s}\) are the transmit power of the primary and secondary users, respectively, h(D′) is the channel gain at distance D′ from the transmitter, and \(P^{\prime }_{b}\) is the background interference power at the primary receiver.
To avoid causing harmful interference to the primary receiver, the secondary user must be able to detect a signal from the primary transmitter within the range of \(D^{\prime }_{1}+D^{\prime }_{2}\) which can translate to a certain sensitivity requirement for the secondary detector. Although the cases where an active primary transmitter is present but it is far away from the secondary user fall under hypothesis H1, the interference to the primary receiver would not be harmful, and as such these cases should be treated as white space by definition. In particular, since the detection of the primary transmitter is dependent on the SNR at the secondary user as seen in (1), it would be unlikely for low-SNR primary signals to trigger the secondary user’s detector resulting in unusable white spaces [24].
Sensing Techniques
In this section, we will discuss some of the most common spectrum sensing techniques for the detection of the primary transmitter in the cognitive radio literature. From the perspective of signal detection, sensing techniques can be classified into two broad categories: coherent and noncoherent detection. In coherent detection, the primary signal can be coherently detected by comparing the received signal or the extracted signal characteristics with prior knowledge of primary signals. In noncoherent detection, no prior knowledge of the primary signal is required for detection. Another way to classify sensing techniques is based on the bandwidth of the spectrum of interest, that is, narrowband and wideband. The classification of sensing techniques is shown in Fig. 2. Next, we introduce matched filter detection, energy detection, and cyclostationary detection and briefly discuss some other spectrum sensing techniques. A more complete review on various spectrum sensing techniques and design challenges can be found in [25, 26].
Matched Filter Detection
Matched filtering is known as the optimum method for the detection of the primary signal when the transmitted signal is known, since it maximizes the received signal-to-noise ratio (SNR). The main advantage of matched filtering is the short time it requires to achieve a certain detection performance, such as low probabilities of miss-detection and false alarm [27], since a matched filter needs less received signal samples. However, matched filtering requires the secondary users to demodulate the received signals. Therefore, it requires perfect knowledge of the primary users’ signaling features such as bandwidth, operating frequency, modulation type and order, and pulse shaping as well as accurate synchronization at the secondary user [25, 28, 29]. However, in cognitive radio networks, such knowledge is not readily available to secondary users, and the implementation cost and complexity of this detector are high. Another significant drawback of matched filter detection is that a secondary user would need a dedicated receiver for every primary user class [30].
Energy Detection
Energy detection [21, 31] is a noncoherent detection method that is most commonly used if the receiver cannot gather sufficient information about the primary user’s signal. This simple scheme accumulates the energy of the received signal during the sensing interval and declares the primary band to be occupied if the energy surpasses a certain threshold which depends on the noise floor [21]. Due to its simplicity and the fact that it does not require prior knowledge of the primary users’ signals, energy detection is the most popular sensing technique among others for spectrum sensing [6, 15, 32,33,34]. However, some of the challenges with energy detection include selection of the threshold for detecting primary users, inability to differentiate interference from primary users’ transmission and noise, and poor performance under low signal-to-noise ratio [29]. Moreover, energy detection does not work efficiently for detecting spread spectrum signals for which more sophisticated signal processing algorithms need to be devised [35].
In addition to narrowband sensing, energy detection has been used for multiband joint detection in wideband sensing by employing an array of energy detectors, each of which detects one frequency band [36]. The multiband joint detection framework enables secondary users to simultaneously detect primary users’ signals across multiple frequency bands for efficient management of the wideband spectrum resource at the cost of detection hardware.
Cyclostationary Feature Detection
Another detection method that can be applied for spectrum sensing is the cyclostationary feature detection . Modulated signals are in general coupled with sinusoidal wave carriers, pulse trains, repeated spreading or hopping sequences, or cyclic prefixes, which result in built-in periodicity. Cyclostationary features are caused by the periodicity in the signal or in its statistics such as mean and autocorrelation [29]. Cyclostationary feature detection is a method for detecting primary user transmissions by exploiting the cyclostationary features of the received signals. Instead of power spectral density (PSD), cyclic correlation function is used for detecting signals present in a given spectrum. The cyclostationary-based detection algorithms can differentiate noise from primary users’ signals. This is a result of the fact that noise is wide-sense stationary with no correlation, while modulated signals are cyclostationary with spectral correlation due to the redundancy of signal periodicity. Therefore, a cyclostationary feature detector can perform better than the energy detector in discriminating against noise due to its robustness to the uncertainty in noise power [28, 37]. However, it is computationally complex and requires significantly long observation time. Moreover, it requires the knowledge of the cyclic frequencies of the primary users, which may not be available to the secondary users.
Other Sensing Techniques
Alternative spectrum sensing methods include waveform-based sensing, multitaper spectral estimation, and wavelet detection. Waveform-based sensing is usually based on correlation with known signal patterns. Known patterns are usually utilized in wireless systems to assist synchronization or for other purposes. Such patterns include preambles, regularly transmitted pilot patterns, and spreading sequences. In [35], it was shown that waveform-based sensing outperforms energy detector-based sensing in reliability and convergence time. Furthermore, it was shown that the performance of the sensing algorithm increases as the length of the known signal pattern increases. Waveform-based sensing, however, is only possible when the target primary user’s signal contains known signal patterns.
In [38], the authors proposed a spectrum sensing method based on the autocorrelation of the received samples. The proposed method was evaluated by means of experiments wherein the probabilities of detection and false alarm at different signal-to-noise ratios (SNRs) were observed. A metric called the Euclidean distance was derived to analyze the autocorrelation of the received samples in order to decide whether only noise was present or signal plus noise. Simulation results showed that the proposed method is more efficient than using autocorrelation function at first lag method in terms of probability of detection and false alarm and more efficient than the energy detection method in terms of probability of false alarm.
Multitaper spectrum estimation was proposed in [39]. The proposed algorithm was shown to be an approximation to the maximum likelihood power spectral density estimator, and for wideband signals, it is nearly optimal. Most importantly, unlike the maximum likelihood spectral estimator, the multitaper spectral estimator is computationally feasible. In [40], wavelets are used for detecting edges in the power spectral density of a wideband channel. Once the edges, which correspond to transitions from an occupied band to an empty band or vice versa, are detected, the power within the bands between two edges is estimated. Using this information and the edges’ positions, the power spectral density can be characterized as occupied or empty in a binary fashion. The assumptions made in [40], however, need to be relaxed for building a practical sensing algorithm. The method proposed in [40] was extended in [41] by using sub-Nyquist sampling (compressed sensing). Assuming that the signal spectrum is sparse, sub-Nyquist sampling is used to obtain a coarse spectrum knowledge in an efficient way. Table 1 presents a brief comparison of the above spectrum sensing techniques.
Cooperative Spectrum Sensing (CSS)
In cooperative spectrum sensing , information from multiple secondary users are incorporated for the detection of the primary signal. In the literature, cooperative sensing is discussed as a solution to problems that arise in spectrum sensing due to noise uncertainty, fading, and shadowing since the uncertainty in a single user’s detection can be minimized [32]. The main idea of cooperative sensing is to enhance the sensing performance by exploiting the spatial diversity in the observations of spatially located secondary users. By cooperation, secondary users can share their sensing information for making a combined decision more accurate than the individual decisions [17]. The performance improvement due to spatial diversity is called cooperative gain. While cooperative gain such as improved detection performance and relaxed sensitivity requirement can be obtained, cooperative sensing can incur cooperation overhead. Cooperation overhead refers to any extra sensing time, delay, energy, and operations devoted to cooperative sensing and any performance degradation caused by cooperative sensing.
Cooperation Architecture
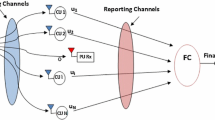
Depending on how the secondary users share their sensing data, several cooperative spectrum sensing architectures for CR networks have been proposed in the literature [15, 42,43,44]. The most commonly proposed architecture is the parallel fusion architecture, in which all the sensing secondary users send their sensing information directly to a centralized controller called a fusion center. This fusion center then makes a final decision regarding the presence or absence of the primary signal and broadcasts this information to other secondary users or directly controls the cognitive radio network traffic [15, 32, 42]. The parallel fusion architecture is illustrated in Fig. 3.
Another possible sensing architecture is the decentralized sensing architecture which does not rely on a fusion center for making the cooperative decision [16, 35, 44]. In this case, secondary users exchange the sensing observations and converge to a unified decision on the presence or absence of primary user’s transmissions by iterations. Based on a distributed algorithm, each secondary user sends its own sensing data to other users, combines its data with the received sensing data, and decides whether or not the primary user’s transmission is present by using a local criterion. If the criterion is not satisfied, secondary users send their combined results to other users again and repeat this process until the algorithm is converged and a decision is reached. The decentralized sensing architecture is illustrated in Fig. 4.
Fusion Schemes
In cooperative sensing, a fusion scheme refers to the process of combining locally sensed data of individual secondary users. Depending on which type of sensing data is transmitted to the fusion center or shared with neighboring users, CSS can employ data or decision fusion schemes. In soft-decision schemes (data fusion), secondary users exchange their test statistics calculated from their local observations. On the other hand, in the hard decision schemes (decision fusion), secondary users only exchange their individual binary decisions.
Soft Combining and Data Fusion
Existing receiver diversity techniques such as equal gain combining (EGC) and maximal ratio combining (MRC) can be utilized for soft combining of local observations or test statistics. If the channel state information (CSI) between the primary users and the secondary users are perfectly known, the optimal combining strategy, which is MRC, can be used for achieving the highest output SNR . In MRC, the local observations of secondary users are weighted proportionately to their channel gain and then summed up [45]. In EGC, the local observations of secondary users are weighted equally [46]. The EGC scheme has a performance close to that of MRC but with simpler implementation.
It was shown in [47] that the soft combining scheme yields better gain than the hard combining scheme. However, there is a significant difference in the cooperation overhead between the hard- and soft-decision-based detectors, which requires a wideband control channel for the soft-decision cooperative approach. The soft information-based signal detection method for the single-carrier case and multi-carrier case was investigated in [48]. In [33], a linear cooperation strategy was developed which is based on the optimal combination of the local statistics from spatially distributed secondary users. In [49], an optimal soft combination scheme based on Neyman-Pearson criterion was proposed to combine the weighted local observations. The proposed scheme reduces to EGC at high SNR and reduces to MRC at low SNR. Since such a soft combining scheme results in large overhead, a softened two-bit combining scheme was also proposed for energy detection. In this method, there are three decision thresholds dividing the whole range of test statistics into four regions. Each secondary user reports the quantized two-bit information of its local test statistics. The performance of this method is comparable to the performance of the EGC scheme with less complexity and overhead.
In [50], the authors proposed a cooperation strategy in which the local decisions are combined with weighting factors that reflect the local sensing reliability of each secondary user based on partial channel side information to make a final decision with the correspondingly optimized threshold level. In [51], the authors proposed a weighted cooperative spectrum sensing scheme for which the optimal weights are derived under the constraint of equal probabilities of false alarm and miss-detection. They also incorporated reference matrix into the weight setting procedure to store the most recent sensing data in either noise matrix or signal energy matrix according to their corresponding sensing decisions in order to acquire the primary user signal energies from the sensing data of the cooperating sensing nodes. In [52], the authors proposed a cooperative spectrum sensing technique which considers the spatial variation of secondary users, and each user’s contribution is weighted by a factor that depends on the received power and path loss. The proposed scheme provides better probability of detection and spectrum utilization when compared to EGC scheme.
In [53], the authors proposed a weighted cooperative sensing scheme that assigns weights to secondary users based on the local detection accuracy of each SU, instead of SNR. In this scheme, the authors used the total error probability, which combines the false-alarm probability and miss-detection probability, to measure the detection accuracy. At the fusion center, each cooperating user is assigned a weight corresponding to its probability of error, i.e., an SU with higher probability of error is assigned lower weight. The optimal detection threshold, as well as the number of SUs required to participate in cooperative sensing, was derived, subject to a given total error probability. Simulation results showed that the proposed scheme provides performance improvement, in terms of the probability of error, when compared to the equal weighted and SNR-based weighted schemes. The authors in [54] proposed a penalty-based weight adjustment mechanism for cooperative spectrum sensing (CSS) to enhance the adaptability of secondary users in time-varying environments. Similar to [53], each secondary user is characterized by its probability of error but the weight factor is adjusted using a penalty mechanism based on the current local decision made by the secondary user. The final result is then computed by fusion of weighted soft decisions made by each cooperating secondary user.
In [55], an adaptive weighting scheme with double threshold energy detection based on the water-filling principle was proposed for cooperative spectrum sensing. For this scheme, each secondary user was allocated a weighting factor based on the relation between the instantaneous SNR of the sensing channel and the water level. The authors showed that the proposed weighting scheme can achieve better detection performance and lower average number of sensing bits when compared to the equal weighted and SNR weighted schemes. A cooperative spectrum sensing scheme based on ROCQ reputation management model for cognitive radio networks was proposed in [56]. The ROCQ scheme is a reputation-based trust management system that computes the trustworthiness of peers on the basis of transaction-based feedback. The ROCQ model combines four parameters: (i) reputation, (ii) a peer’s global trust rating or opinion formed by a peer’s firsthand interactions, (iii) credibility of a reporting peer, and (iv) the quality or the confidence a reporting peer puts on the feedback it provides. In this scheme, each secondary user has a reputation degree used to calculate its coefficient in the linear fusion process, and the reputation degree is initialized and adjusted by the fusion center according to each secondary user’s sensing result, sensing correctness, and report consistency. Simulation results showed that the detection performance of the proposed scheme in [56] is approximately the same as that of the optimal linear fusion scheme while it requires no instantaneous SNR .
Hard Combining and Decision Fusion
In the hard combining scheme, the final decision is reached by taking into consideration the individual local decisions reported by each secondary user. When binary local decisions are reported to the fusion center, it is convenient to apply linear fusion rules to obtain the cooperative decision. The main advantage of the hard combining scheme is the reduction of communication overhead. Hard decision combining for CSS has been considered in several works [47, 49, 57]. The commonly used fusion rules are AND, OR, and majority voting rules which are special cases of the general K-out-of-M rule. Those decision fusion rules can be summarized as below [58]:
-
K-out-of-M rule : In this fusion rule, the fusion center decides on the presence of the primary user’s transmission if, and only if, K or more than K secondary users out of the total M cooperating secondary users report the detection of the primary user’s signal, where K ∈ [1, M]. Therefore, in the K-out-of-M rule, if K users or more decide in favor of H1, then the cooperative decision declares that H1 is true. If the decisions from all the secondary users are independent, the network probabilities of detection and false alarm are, respectively, given by [59]
$$\displaystyle \begin{aligned} P_{D}=\sum_{k=0}^{M-K}\binom{M}{K+k} {(1-P_{d,k})}^{M-K-k} {(P_{d,k})}^{K+k}, \end{aligned} $$(5)and
$$\displaystyle \begin{aligned} P_{F}=\sum_{k=0}^{M-K}\binom{M}{K+k} {(1-P_{f,k})}^{M-K-k} {(P_{f,k})}^{K+k}, \end{aligned} $$(6)where Pd,k and Pf,k are, respectively, the probabilities of detection and false alarm of the kth secondary user and \(\binom {M}{K+k}=\frac {M!}{(K+k)!(M-K-k)!}\).
-
Majority voting (MV) rule : In the MV fusion rule, also known as half-voting rule, if half, or more than half, of the local detectors decide that there is a primary user’s transmission, then the final decision at the fusion center declares that there is a primary user’s transmission [58]. Therefore, for the MV rule, the cooperative decision declares H1 only if half or more than half of the secondary users decide on H1, i.e., \(K= \lceil \frac {M}{2}\rceil \) in (5) and (6), where \(\lceil \frac {M}{2} \rceil \) denotes the smallest integer not less than \(\frac {M}{2}\). If the decisions from all the secondary users are independent, the network probabilities of detection and false alarm are, respectively, given by
$$\displaystyle \begin{aligned} P_{D}=\sum_{k=0}^{M-\lceil\frac{M}{2}\rceil}\binom{M}{\lceil\frac{M}{2}\rceil+k} {(1-P_{d,k})}^{M-\lceil\frac{M}{2}\rceil-k} {(P_{d,k})}^{\lceil\frac{M}{2}\rceil+k}, \end{aligned} $$(7)and
$$\displaystyle \begin{aligned} P_{F}=\sum_{k=0}^{M-\lceil\frac{M}{2}\rceil}\binom{M}{\lceil\frac{M}{2}\rceil+k} {(1-P_{f,k})}^{M-\lceil\frac{M}{2}\rceil-k} {(P_{f,k})}^{\lceil\frac{M}{2}\rceil+k}. \end{aligned} $$(8) -
Logical OR rule : In this fusion rule, the fusion decides on the presence of primary user’s transmission if any of the secondary users reports the detection of the primary user’s transmission. Therefore, for the OR rule, the cooperative decision declares H1 if any of the secondary users decides on H1, i.e., setting K = 1 in (5) and (6). Since an SU occupying a licensed frequency band may cause interference to the primary users, the risk of SUs causing interference to the primary users is minimized using the logical OR rule. If the decisions from all the secondary users are independent, the network probabilities of detection and false alarm are, respectively, given by
$$\displaystyle \begin{aligned} P_{D}=1-\prod_{k=1}^{M}(1-P_{d,k}), \end{aligned} $$(9)and
$$\displaystyle \begin{aligned} P_{F}=1-\prod_{k=1}^{M}(1-P_{f,k}). \end{aligned} $$(10) -
Logical AND rule : In the AND fusion rule, if all local detectors decide that there is a primary user’s transmission, then the final decision at the fusion center declares that there is a primary user’s transmission [58]. Therefore, for the AND rule, the cooperative decision declares H1 only if all of the secondary users decide on H1, i.e., setting K = M in (5) and (6). Using this fusion rule, the probability of false alarm is minimized, but the risk of causing interference to primary users will increase. If the decisions from all the secondary users are independent, the network probabilities of detection and false alarm are, respectively, given by
$$\displaystyle \begin{aligned} P_{D}=\prod_{k=1}^{M}P_{d,k}, \end{aligned} $$(11)and
$$\displaystyle \begin{aligned} P_{F}=\prod_{k=1}^{M}P_{f,k}. \end{aligned} $$(12)
In [60], the authors proposed a decision fusion rule for the sensing-throughput trade-off design that considers the differences in the signal-to-noise ratios of the secondary users. These differences were reflected in the weighing of the decisions based on the likelihood ratio test at the fusion center. A decision fusion scheme was proposed in [61] that combines all secondary users decisions, taking into account the credibility of each decision via Dempster-Shafer (D-S) theory of evidence. This scheme can give a significant improvement in detection probability as well as reduction in false-alarm rate and is best suited for a fast-changing radio frequency environment. In [62], an enhanced scheme was proposed that assigns a reliability value to each detector based on its SNR. This value reflects the relative relationship between detectors and is used to adjust the credibility of each decision to a more accurate value before combining the decisions via D-S theory. In [63], the authors proposed a trust weighted cooperative spectrum sensing scheme to identify malicious secondary users and mitigate their harmful effect on sensing performance. To make an accurate final decision, the trust weight factor of each SU is calculated by their trust values. The fusion center initializes the trust values of SUs by the number of true sensing that agrees with the primary user’s actual behavior and the number of total sensing. The trust value for each secondary user is then increased or decreased according to whether it provides true or false sensing information. Simulation results showed a performance improvement in the probability of detection as compared to the conventional cooperative spectrum sensing scheme without trust weighted factors for OR, AND, and majority fusion rules. In [64], a centralized trust management scheme for secondary user base station was proposed. The authors introduced the notion of self-confidence and trust. Self-confidence is a rate supplied by a sensing secondary user of its own confidence on the accuracy of its sensing results. Trust is a measure of reputation and represents the historical accuracy of secondary user’s sensing reports. The authors incorporated the trustworthiness evaluation from a modified beta reputation model into the K-out-of-M decision fusion rule to give greater weight to the opinions of more trustworthy secondary users .
Performance of Cooperative Spectrum Sensing
In this section, we discuss some of the factors affecting the performance of CSS, in terms of cooperation gain or incurred overhead, such as the number of channels sensed in each sensing period, the selection of secondary users, the selection of the fusion scheme, and the correlation between the cooperating secondary users. We also discuss the performance of cooperative wideband spectrum sensing.
Cooperative User Selection
The selection of secondary users for cooperative sensing plays a key role in determining the performance of CSS because it can be utilized to improve the trade-off between cooperative gain and cooperation overhead. In [57], for the case of independent secondary users’ observations with energy detection-based cooperation, it was shown that cooperating with all users in the network does not necessarily achieve the optimum performance. It was observed that including secondary users experiencing bad channels, in terms of the SNR received at a secondary user, for cooperation may degrade the performance. In order to relax the requirement on prior knowledge of the received SNR at each secondary user, the authors in [65] proposed to select the sensing secondary users that have the best detection probabilities with respect to a given false-alarm probability. Specifically, the false-alarm probability is set to be identical at each secondary user. Therefore, the SU that reports the largest number of 1’s is first chosen to participate in cooperative sensing. In [66], the optimal number of secondary users, K, that minimizes the total error probability for secondary users with independent local decisions for the general K-out-of-M fusion rule was found to be approximately half of the total number of secondary users M. A user selection strategy based on a modified deflection coefficient with low complexity was proposed in [67]. The optimal number of secondary users and the user set were obtained in order to provide sufficient protection to the primary users and improve the total throughput of the cognitive radio network. CSS using counting rule was studied in [68], and the sensing errors were minimized by choosing the optimal probability of false alarm to satisfy a given constraint and the optimal number of cooperating secondary users for both matched filtering and energy detection.
When the cooperating secondary users experience correlated shadowing, it was shown in [18] that selecting independent secondary users for cooperation can improve the robustness of sensing results. In [69], a correlation-aware user selection algorithm was developed to address the dynamic changes in the spatial correlation experienced by mobile secondary users. To accurately derive the spatial correlation coefficient, a correlation model between mobile secondary users was first developed. Based on this correlation model, a distributed user selection algorithm that adaptively selects uncorrelated secondary users through the spatial correlation coefficient was designed. In [70], a joint spatial-temporal sensing scheme for CR networks was proposed, where secondary users collaboratively estimate the location and transmit power of the primary transmitter. Based on those estimates, secondary users determine their maximum allowable transmission power and use the location information to decide which users should participate in cooperative sensing in order to minimize the correlation among the secondary users’ observations. CSS with correlated secondary users’ local decisions was studied in [71]. The probability of sensing error was minimized by choosing the optimal assignments for the number of cooperating secondary users, K, in the K-out-of-M fusion rule and the local threshold for a certain correlation index.
Moreover, removing malicious users from cooperation ensures the security and the reliability of the network. A robust secondary user selection algorithm for CSS considering the presence of malicious users was proposed in [72]. The users were selected based on the consistency check with known trusted users, and simulation results showed that the proposed algorithm is effective in identifying and excluding malicious secondary users. The authors in [73] presented a soft-decision reporting scheme that is robust against malicious users. They proposed a heuristic approach to iteratively identify malicious users, where the fusion center computes the secondary user’s suspicious level, i.e., the posterior probability that this SU is an attacker, based on the honest SU and malicious SU report probabilities. These probabilities are estimated assuming that the fusion center knows the position of the users’ and the attackers’ policy. When the suspicious level of the secondary user goes beyond a threshold, it is discarded from the final decision process and moved into a malicious user set. This process is repeated until no more malicious users can be found, and only the reports from honest users are fused to make the final decision.
Most of the existing cooperative sensing schemes assume all the secondary users are willing to cooperate. In reality, some selfish secondary users may refuse to provide the sensing results to save energy or transmission time, while benefiting from sensing results of other users which may disrupt CSS. To enhance the cooperation, several researchers investigate this incentive problem from the perspective of game theory.
In [74], the authors modeled the cooperative spectrum sensing as an N-player horizontal infinite game and then studied various strategies with it. They examined the classical grim trigger strategy and proved it can sustain cooperation easily but will result in poor performance under uncertainty of wireless channel. They then proposed a strategy based on the carrot-and- stick strategy which can recover cooperation from deviation. The authors proved that the proposed strategy can achieve mutual cooperation as well as recover from failures. Performance evaluation showed that the proposed strategy can achieve good network performance and reduce interference to primary users.
In [75], the author proposed an evolutionary game-theoretic framework to develop the best cooperation strategy for cooperative sensing with selfish users. Using replicator dynamics, users can try different strategies (behavior dynamics) and learn a better strategy through strategic interactions (evolutionarily stable strategy). The authors also proposed a distributed learning algorithm that aids the secondary users approach the evolutionarily stable strategy only with their own payoff history. Simulation results showed that the proposed game has a better performance, in terms of total throughput, than having all secondary users sense at every time slot.
In [76], the authors proposed a game in which every user can choose to collaborate or not in each time slot depending on whether the benefit of the cooperation is worth the cost. From this perspective, the cooperative spectrum sensing game was modeled as the stag hunt game. The authors then proposed cooperative communication incentive scheme (CCIS) to enhance the cooperative sensing. The basic idea is to introduce a periodically available trusted authority to compensate the secondary users (e.g., using the relay to help transmit their data during transmission time) who suffer losses in the cooperative sensing .
Cooperation Overhead
The exploitation of spatial diversity in cooperative sensing results in a significant improvement in detection performance. However, cooperation among secondary users may also introduce a variety of overheads that limit or even compromise this improved detection performance. The overhead associated with all elements of cooperative sensing is called cooperation overhead. Cooperation overhead can refer to any transmission cost, extra sensing time, delay, energy, and operations devoted to cooperative sensing and any performance degradation caused by cooperative sensing.
Since the sensing time is proportional to the number of samples taken by each individual secondary user, the longer the sensing time is, the better the detection performance will be. However, when each secondary user is equipped with a single radio transceiver, it will be difficult for the secondary users to simultaneously perform sensing and transmission. Therefore, the more time is devoted to sensing, the less time is available for transmissions which reduces the secondary users’ throughput, also known as opportunistic throughput. In addition, the cooperation overhead due to the extra sensing time will generally increase with the number of cooperating users due to the increased volume of data that needs to be reported to and be processed by the fusion center. This is known as the sensing efficiency problem [77] or the sensing-throughput trade-off [59] in spectrum sensing.
The cooperation overhead, in terms of the extra sensing time or reduced opportunistic throughput, will also increase as the delay in finding an available channel increases [78]. In [79], a sensing-period optimization mechanism and an optimal channel-sequencing algorithm were developed to maximize the discovery of spectrum access opportunities and minimize the delay in discovering an available channel when all secondary users participate in sensing an identical channel in each sensing period. In [80], two different channel sensing policies, the random sensing policy and the negotiation-based sensing policy, were proposed to discover the available channels. In both policies, different users are allowed to sense different channels that are selected either randomly or through negotiation, which enables SUs to identify and utilize the maximum number of vacant channels. The authors assumed that each secondary user is equipped with two transceivers. One transceiver is tuned to the dedicated control channel, and another transceiver is used to periodically sense and dynamically use the identified unused channels. Parallel cooperative sensing was proposed in [81, 82] where the cooperative secondary users are divided into multiple groups, and each group senses one channel such that more than one channel are sensed in each sensing period. Since multiple channels are detected in one sensing period, the cooperation overhead associated with the delay in finding an available channel is significantly reduced.
Since each sensing phase is usually separated into several subslots used for signal detection and decision reporting, reporting delay will also affect the performance of cooperative spectrum sensing. In [83], the authors proposed cooperative spectrum sensing where the secondary network optimizes the decision thresholds at the sensors and the division between time samples used for sensing the primary users and time slots used for reporting the sensing results. Simulation results showed that joint optimization of thresholds and sensing/reporting time slots achieve good sensing performance in terms of the network probabilities of false alarm and miss-detection.
In [84], the authors proposed two distributed reporting SU selection methods to reduce the overall sensing overhead and to mitigate the interference to PUs in CR networks. The authors also considered the reporting channel errors and the interference impact on PUs induced by decision reporting. Simulation results showed that the proposed strategies achieve better detection performance and lower sensing overhead than the traditional case.
In cooperative sensing, secondary users involve in activities such as local sensing and data reporting that consume additional energy. The energy consumption overhead can be significant if the number of cooperating secondary users or the amount of sensing results to be reported is large. One approach to address this issue is to use censoring to limit the amount of reported sensing data according to certain criteria or constraints. Since the censoring criteria are chosen to refrain cooperating secondary users from transmitting unnecessary or uninformative data, the energy efficiency can be improved in cooperative sensing. In [85], a simple censoring method was proposed to decrease the average number of sensing bits reported to the fusion center. In this method, the energy detector output of each secondary user is compared to two thresholds, and the decision is sent to the fusion center if the energy detector output is between those two thresholds. Otherwise, no decision is made and this sensing output is censored from reporting. The simulation results showed that even though the network probability of false alarm may degrade due to the possibility that the sensing outputs of all secondary users are censored, the amount of reported local decisions can be dramatically reduced. Therefore, the energy efficiency can be traded off with the network probability of false alarm.
Another approach to reduce the cooperation overhead in terms of energy consumption is to minimize the energy consumption with detection performance constraints. In [86], the energy efficiency problem was addressed by energy minimization under detection performance constraints. This method investigates the trade-off between the two aspects of sensing time. On one hand, longer sensing time consumes more energy at each secondary user. On the other hand, longer sensing time can improve detection performance at each secondary user and reduce the number of cooperating users and the associated energy consumption overhead. Therefore, this method finds the optimal sensing time and the optimal number of cooperating users to balance the energy consumption in local sensing and the energy overhead due to cooperation for a required detection performance.
An energy-efficient CSS scheme was proposed in [87] to maximize the energy efficiency. The authors proposed a method in which sensing time, sensing threshold, and the number of cooperating SUs are jointly optimized. In [88], the authors proposed an efficient algorithm to solve the general problem of spectrum efficiency and energy efficiency trade-off in cognitive radio with cooperative sensing. The authors then considered the trade-off between spectrum efficiency and energy efficiency such that the energy efficiency (spectrum efficiency) is maximized via joint optimization of sensing duration and final decision threshold under the constraint that the spectrum efficiency (energy efficiency) requirement is satisfied. Simulation results showed that different spectrum efficiency (energy efficiency) requirements need different optimal values of sensing duration and final decision threshold, and there exists a trade-off between the spectrum efficiency and energy efficiency.
To alleviate the energy deficiency, radio frequency (RF) harvesting techniques have become alternative methods through which green energy can be used to power the next generation wireless networks [89]. Recently, energy harvesting communication has been considered for cognitive radio networks in order to improve both energy and spectral efficiency in wireless and mobile networks. In [90], the transmitters in a CR network either opportunistically harvest RF energy from transmissions by nearby devices in a primary network or transmit data if the devices are not in the interference range of any other primary network. The optimal transmit power and density of the secondary transmitters that maximize the throughput of the CR network were derived under an outage probability constraint. The authors in [91] investigated the optimal detection threshold for opportunistic spectrum access in an energy harvesting CR network to maximize the expected total throughput under both the energy causality constraint and the collision constraint. In [92], the authors extended the work in [91] to investigate the optimal sensing duration and sensing threshold that jointly maximize the average throughput for a given amount of harvested energy .
Multiband Spectrum Sensing
Wideband spectrum sensing , which we also refer to in this chapter as multiband sensing, faces technical challenges, and there is limited work on it in the literature. To sense multiple frequency bands simultaneously, secondary users may need to scan the spectrum or use multiple radio frequency (RF) front ends for sensing multiple bands. However, using these approaches for wideband sensing either causes long sensing delay or incurs high computational complexity and hardware cost. Recent advances in compressed sensing [41, 93] enable the sampling of the wideband signals at sub-Nyquist rate to relax the analog-to-digital converter (ADC) requirements. The techniques of compressed sensing provide promising solutions to promptly recover wideband signals and facilitate wideband sensing at a reasonable computational complexity. Compressed sensing can be achieved by various sensing matrix techniques such as random matrices. However, due to the sub-Nyquist rate sampling and insufficient number of samples, a weak primary user’s signal with a nearby strong signal may not be properly reconstructed for detection in a wideband spectrum [17]. In addition, a new ADC architecture with nonuniform timing and a pseudorandom clock generator is needed [94]. In [95], the authors proposed two algorithms for wideband spectrum sensing at sub-Nyquist sampling rates for the single node and cooperative multiple nodes, respectively. In single node spectrum sensing, a two-phase spectrum sensing algorithm based on compressive sensing is proposed to reduce the computational complexity and improve the robustness at secondary users. In the cooperative multiple node case, the signals received at SUs exhibit a sparsity property that yields a low-rank matrix of compressed measurements at the fusion center. This leads to a two-phase cooperative spectrum sensing algorithm for cooperative multiple SUs based on low-rank matrix completion. The numerical results showed that the proposed algorithms are robust to channel noise with low computational complexity.
In multiband cooperative sensing, secondary users cooperate to sense multiple narrowbands instead of focusing on one band at a time. In [36], a multiband joint detection scheme was proposed for combining the statistics of sensing multiple bands from spatially distributed secondary users. The fusion center calculates the test statistic and makes a cooperative decision in each band. The weight coefficients and detection thresholds of all bands were obtained by jointly maximizing the aggregate opportunistic throughput in each band subject to constraints on the miss-detection and false-alarm probabilities. To enable the multiband sensing at each secondary user, an energy detector is required for each band of interest. As a result, the method may incur high hardware cost when the number of bands for cooperative sensing is large. In [96], the authors proposed a multiband adaptive joint detection framework for wideband spectrum sensing that collectively searches the secondary transmission opportunities over multiple frequency bands. In this framework, both the sensing slot duration and detection thresholds for each narrowband detector were jointly optimized to maximize the achievable opportunistic throughput of the secondary network subject to a limit on the interference introduced to primary users.
In [81], a parallel cooperative sensing scheme was proposed to enable the multichannel sensing by optimally selected cooperating secondary users. Different from the multiband sensing scheme in [36, 96], each cooperating secondary user senses a different channel. In [82], the authors proposed a group-based CSS scheme in which the cooperative secondary users are divided into several groups, and each group senses a different channel during a sensing period, while the secondary users in the same group perform joint detection on the targeted channel. In [97], the authors proposed an adaptive user-group assignment algorithm for group-based CSS that considers cooperating secondary users with heterogeneous sensing ability in terms of the sensing accuracy. By the methods in [81, 82, 97], multiple channels can be cooperatively sensed in each sensing period. The objective is to maximize the secondary opportunistic throughput while minimizing the sensing overhead such as the sensing time and the number of secondary users required for cooperation .
Implementation of Sensing Techniques on Testbeds
Testbeds are essential to advance the development of cognitive radio networks by verification of proposed sensing techniques in a practical system and evaluation of key performance metrics. Some of the existing CR testbed researches are focusing on the algorithms of spectrum sensing and signal processing. In [98], the authors proposed an experimental setup based on the Berkeley Emulation Engine 2 (BEE2) platform, which is a multi-FPGA emulation platform, to experiment with various sensing techniques and develop a set of metrics and test cases to allow them to measure the sensing performance of these techniques. The authors in [99] proposed KNOWS, which has a reconfigurable transceiver based on a modified Wi-Fi hardware. The hardware consists of a development board with a scanner/receiver radio and a reconfigurable transceiver. KNOWS spectrum allocation engine maintains up-to-date information about the spectrum usage by all its neighbors and stores it in a resource allocation matrix (RAM). The authors studied the bandwidth allocation problem and designed a spectrum-aware medium access control (MAC) protocol . The MAC protocol uses the RAM to dynamically decide on the portion of the spectrum to use for a given communication. Simulations results showed that KNOWS significantly increases the capacity when compared to IEEE 802.11-based systems.
In [100], the authors presented a real-time testbed, based on programmable system-on-chip processors, for the evaluation of cognitive radio MAC algorithms. The proposed testbed is much easier to configure and control than the traditional FPGA-based testbed. The authors introduced the testbed implementation details of the spectrum sensing of PHY layer, the channel selection strategy, and the access control strategy of MAC layer.
In [101], the author studied the performance of normal collaborative spectrum sensing (NCSS) based on coalitional games and implemented NCSS in wireless open-access research platform. Wireless open-access research platform is a scalable and extensible programmable wireless platform, developed by Rice University [102], to prototype advanced wireless networks. Based on testbed implementation, the authors showed that under poor reporting channel conditions, the coalition splits and the weaker SUs exhibit inefficient sensing performance. The authors then proposed relay-based collaborative spectrum sensing that uses neighboring SU with low error-prone relay path to share sensing results between affected SUs and channel. Testbed results revealed that relay-based collaborative spectrum sensing performs better than all other collections of coalitions, and it improves sum-utility by 20%, as compared to NCSS at the cost of minimal 2.3% loss in energy efficiency.
Research Challenges
Many operations in cooperative spectrum sensing, such as sharing data, broadcasting spectrum-aware routing information, and coordinating spectrum access, rely on control message exchange on a common control channel. The implementation of a common control channel is one of the most challenging issues in cognitive radio networks, since a fully reliable control channel cannot be created without reserving bandwidth specifically for this purpose. However, if a dedicated channel is used, the bandwidth available for traffic communications reduces. In addition, since the common control channel may be subject to primary user’s activity, secondary users have to negotiate a new control channel when the original one is occupied by primary users. In [103], the authors investigate a promising solution that exploits the ultrawideband (UWB) technology to allow the secondary users to discover each other and exchange control information for establishing a communication link. Other works assume that secondary users use an out-of-band common control channel to report the local sensing results to the fusion center to avoid interfering with the primary user [104, 105]. Setting up and maintaining common control channel is still an open issue for CR networks.
In cooperative spectrum sensing, it is usually assumed that all cooperating CR users are perfectly synchronized, and their sensing results are also assumed to be available instantly at the fusion center. In reality, this is not always valid, and therefore, the CSS scheme should consider the case of asynchronous observations and reporting delay which result in time offsets between local sensing observations and the final decision at the fusion center. In [106], a probability-based combination scheme was proposed to combine asynchronous reports at the fusion center. The proposed combining scheme considers both detection errors and time offsets between local sensing observations and the final decision. Based on the knowledge of the primary user channel usage model and the Bayesian decision rule, the conditional probabilities of the local sensing decisions received at different times, conditioned on each hypothesis, and their combined likelihood ratio were calculated to make the final decision at the fusion center.
Most of the studies on CSS analyze its performance based on the assumption of perfect knowledge of the average received SNR at the secondary user. However, in practice, this is not always the case. The effect of average SNR estimation errors on the performance of CSS was examined in [107]. In the noiseless sample-based case, it was found that the probability of false alarm decreases as the average SNR estimation error decreases for both independent and correlated shadowing. In the noise sample-based case, it was found that there exists a threshold for the noise level. Below this threshold, the probability of false alarm increases as the noise level increases, while above the threshold, the probability of false alarm decreases as the noise level increases.
Spectrum mobility, in which SU has to move from one spectrum hole to another to avoid interference in case of the reappearance of PU, is another challenging problem in CR networks. CR networks need to perform mobility management adaptively depending on the heterogeneous spectrum availability that is dependent on the primary traffic.
Some new research directions focus on the design of architectures for the integration of cognition network and cooperative communications in wireless heterogeneous networks (HetNet) for better utilization of radio resources and guaranteeing quality of service. The authors in [108] have focused their research on the coexistence of wireless fidelity (Wi-Fi)and 4G cellular networks sharing the unlicensed spectrum. They have introduced the network architecture for long-term evolution (LTE)/LTE-advanced small cells to exploit unlicensed spectrum used by Wi-Fi systems. They showed that the proposed architecture along with interference avoidance schemes increases the capacity of 4G cellular networks by maintaining the quality of service (QoS)of Wi-Fi systems. Cognitive radio networks are also highly promising for providing timely smart grid wireless communications by utilizing all available spectrum resources [109].
Conclusions
Cognitive radio technology allows a wireless network to expand its spectrum on demand at a relatively low cost, thereby offering a natural solution to cope with random and diverse mobile data traffic which makes it a promising candidate for 5G communication networks. In this chapter, the most common spectrum sensing techniques for cognitive radio networks were surveyed and classified to provide an overview of the research direction in the area of cognitive radio networks. To address the limitations of the spectrum sensing techniques by a single secondary user, cooperative spectrum sensing and its main elements have been discussed. Different cooperation architectures and fusion schemes for fusion the decisions of cooperating secondary users were presented, and their advantages and disadvantages were highlighted.
We further identified some of the main factors that contribute to the efficient design of cooperative spectrum sensing schemes for cognitive radio networks. Different criteria for selecting the cooperating secondary users were discussed, and the performance improvement achieved by the different selection criteria was highlighted. The performance degradation due to cooperation overhead in terms of transmission cost, extra sensing time, delay, energy, and operations devoted to cooperative sensing was investigated which provided an insight on some of the key challenges facing cooperative spectrum sensing in cognitive radio networks.
References
Mitola I, Maguire J (1999) Cognitive radio: making software radios more personal. IEEE Pers Commun Mag 6:13–18
Liang Y, Chen K, Li GY, Mhnen P (2011) Cognitive radio networking and communications: an overview. IEEE Trans Veh Technol 60:3386–3407
Federal Communications Commission (2002) Spectrum policy task force report. ET Docket no. 02-135
Stevenson CR, Chouinard G, Lei Z, Hu W, Shellhammer SJ, Caldwell W (2009) IEEE 802.22: the first cognitive radio wireless regional area network standard. IEEE Commun Mag 47: 130–138
Nekovee M (2010) Cognitive radio access to TV white spaces: spectrum opportunities, commercial applications and remaining technology challenges. In: IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Singapore, Apr 2010, pp 1–10
Ghasemi A, Sousa ES (2008) Spectrum sensing in cognitive radio networks: requirements, challenges and design trade-offs. IEEE Commun Mag 46:32–39
Gavrilovska L, Atanasovski VM (2013) Dynamic REM towards flexible spectrum management. In: International Conference on Telecommunication in Modern Satellite, Cable and Broadcasting Services, Oct 2013, pp 287–296
Li S, Zhao Y, Sun C, Guo X (2014) Development of an advanced geolocation engine-based cognitive radio testbed. In: IEEE/CIC ICCC 2014 Symposium on Wireless Communications Systems, Oct 2014, pp 528–533
Yilmaz HB, Chae C-B, Tugcub T (2014) Sensor placement algorithm for radio environment map construction in cognitive radio networks. In: IEEE Wireless Communications and Networking Conference, Apr 2014, pp 2096–2101
Tajer A, Wang X (2009) Beacon-assisted spectrum access with cooperative cognitive transmitter and receiver. In: IEEE International Conference on Acoustics, Speech and Signal Processing, Apr 2009, pp 2341–2344
Patel A, Biswas S, Jagannatham AK (2013) Multiple beacon based robust cooperative spectrum sensing in MIMO cognitive radio networks. In: IEEE Vehicular Technology Conference, Sept 2013, pp 1–5
Fitch M, Nekovee M, Kawade S, Briggs K, MacKenzie R (2011) Wireless services provision in TV white space with cognitive radio technology: a telecom operator’s perspective and experience. IEEE Commun Mag 49:64–73
Ghasemi A, Sousa E (2007) Optimization of spectrum sensing for opportunistic spectrum access in cognitive radio networks. In: IEEE Consumer Communications and Networking Conference, Las Vegas, Jan 2007, pp 1022–1026
Unnikrishnan J, Veeravalli V (2007) Cooperative spectrum sensing and detection for cognitive radio. In: IEEE Global Telecommunications Conference, Washington, DC, Nov 2007, pp 2972–2976
Unnikrishnan J, Veeravalli VV (2008) Cooperative sensing for primary detection in cognitive radio. IEEE J Sel Top Signal Proces 2:18–27
Ganesan G, Li Y (2005) Cooperative spectrum sensing in cognitive radio networks. In: IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, Nov 2005, pp 137–143
Akyildiz IF, Lo BF, Balakrishnan R (2011) Cooperative spectrum sensing in cognitive radio networks: a survey. Phys Commun (Elsevier) J 4:40–62
Mishra S, Sahai A, Brodersen R (2006) Cooperative sensing among cognitive radios. In: IEEE International Conference on Communications, Istanbul, June 2006, vol 4, pp 1658–1663
Huang S, Liu X, Ding Z (2009) Optimal sensing-transmission structure for dynamic spectrum access. In: IEEE Conference on Computer Communications, Rio de Janeiro, Apr 2009, pp 2295–2303
Sahai A, Hoven N, Tandra R (2004) Some fundamental limits on cognitive radio. In: Allerton Conference on Communication, Control and Computing, Monticello, Oct 2004
Digham F, Alouini M, Simon M (2003) On the energy detection of unknown signals over fading channels. In: IEEE International Conference on Communications, Anchorage, May 2003, vol 5, pp 3575–3579
Koufos K (2013) Spectrum access in white spaces using spectrum sensing and geolocation databases. PhD thesis, Aalto University
Hossain E, Niyato D, Han Z (2009) Dynamic spectrum access and management in cognitive radio networks. Cambridge University Press, Amsterdam
Varnamkhasti AG (2008) Spectrum sensing in cognitive wireless networks: requirements, challenges annd design trade-offs. PhD thesis, University of Toronto
Zeng Y, Liang Y, Hoang AT, Zhang R (2010) A review on spectrum sensing techniques for cognitive radio: challenges and solutions. EURASIP J Adv Signal Process 2010:1–15
Haykin S, Thomson D, Reed J (2010) Spectrum sensing for cognitive radio. Proc IEEE 97:849–877
Tandra R, Sahai A (2005) Some fundamental limits on detection in low SNR under noise uncertainty. In: IEEE International Conference on Wireless Networks, Communications and Mobile Computing, Wuhan, June 2005, vol 1, pp 464–469
Yucek T, Arslan H (2009) A survey of spectrum sensing algorithms for cognitive radio applications. IEEE Commun Surv Tutorials 11:116–130
Cabric D, Mishra S, Brodersen R (2004) Implementation issues in spectrum sensing for cognitive radio. In: Asilomar Conference on Signals, Systems and Computers, Pacific Grove, Nov 2004, vol 1, pp 772–776
Arslan H (2007) Cognitive radio, software defined radio, and adaptive wireless systems. Springer, Dordrecht
Urkowitz H (1967) Energy detection of unknown deterministic signal. Proc IEEE 55:523–531
Ghasemi A, Sousa E (2005) Collaborative spectrum sensing for opportunistic access in fading environment. In: IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, Nov 2005, pp 131–136
Quan Z, Cui S, Sayed A (2008) Optimal linear cooperation for spectrum sensing in cognitive radio networks. IEEE J Sel Top Signal Proces 2:28–40
Quan Z, Cui S, Sayed A, Poor H (2008) Wideband spectrum sensing in cognitive radio networks. In: IEEE International Conference on Communications, Beijing, May 2008, pp 901–906
Tang H (2005) Some physical layer issues of wide-band cognitive radio systems. In: IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, Nov 2005, pp 151–159
Quan Z, Cui S, Sayed A, Poor H (2009) Optimal multiband joint detection for spectrum sensing in cognitive radio networks. IEEE Trans Signal Process 57:1128–1140
Cabric D, Brodersen R (2005) Physical layer design issues unique to cognitive radio systems. In: IEEE Personal Indoor and Mobile Radio Communications, Berlin, Sept 2005, vol 2, pp 759–763
Reyes H, Subramaniam S, Kaabouch N, Hu W (2016) A spectrum sensing technique based on autocorrelation and euclidean distance and its comparison with energy detection for cognitive radio networks. Elsevier Comput Electr Eng J 52:319–327
Haykin S (2005) Cognitive radio: brain-empowered wireless communications. IEEE J Sel Areas Commun 23:201–220
Tian Z, Giannakis GB (2006) A wavelet approach to wideband spectrum sensing for cognitive radios. In: IEEE International Conference on Cognitive Radio Oriented Wireless Networks and Communications, Mykonos Island, June 2006, pp 151–159
Tian Z, Giannakis G (2007) Compressed sensing for wideband cognitive radios. In: IEEE International Conference on Acoustics, Speech, and Signal Processing, Honolulu, Apr 2007, pp 1357–1360
Ganesan G, Li Y (2007) Cooperative spectrum sensing in cognitive radio: part I: two user networks. IEEE Trans Wirel Commun 6:2204–2213
Shankar NS, Cordeiro C, Challapali K (2005) Spectrum agile radios: utilization and sensing architectures. In: IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, Nov 2005, pp 160–169
Ganesan G, Li Y (2007) Cooperative spectrum sensing in cognitive radio: part II: multiuser networks. IEEE Trans Wirel Commun 6:2214–2222
Ahn KS, Jr Heath RW (2009) Performance analysis of maximum ratio combining with imperfect channel estimation in the presence of cochannel interferences. IEEE Trans Wirel Commun 8:1080–1085
Song Y, Blostein SD, Cheng J (2003) Exact outage probability for equal gain combining with cochannel interference in Rayleigh Fading. IEEE Trans Wirel Commun 2:865–870
Vistotsky E, Kuffner S, Peterson R (2005) On collaborative detection of TV transmissions in support of dynamic spectrum sharing. In: IEEE International Symposium on New Frontiers in Dynamic Spectrum Access Networks, Baltimore, Nov 2005, pp 338–345
Uchiyama H, Umebayashi K, Fujii T, Ono F, Sakaguchi K, Kamiya Y, and Suzuki Y (2008) Study on soft decision based cooperative sensing for cognitive radio networks. IEICE Trans Commun E91-B:95–101
Ma J, Zhao G, Li Y (2008) Soft combination and detection for cooperative spectrum sensing in cognitive radio networks. IEEE Trans Wirel Commun 7:4502–4507
Oh DC, Lee HC, Lee YH (2010) Linear hard decision combining for cooperative spectrum sensing in cognitive radio systems. In: IEEE Vehicular Technology Conference, Ottawa, Sept 2010, pp 1–5
Shen B, Huang L, Zhao C, Kwak K, Zhou Z (2008) Weighted cooperative spectrum sensing in cognitive radio networks. In: International Conference on Convergence and Hybrid Information Technology, Busan, Nov 2008, vol 1, pp 1074–1079
Shahid MB, Kamruzzaman J (2008) Weighted soft decision for cooperative sensing in cognitive radio networks. In: IEEE International Conference on Networks, New Delhi, Dec 2008, pp 1–6
Zhao Y, Song M, Xin C (2011) A weighted cooperative spectrum sensing framework for infrastructure-based cognitive radio networks. Comput Commun 34:1510–1517
Hasan N, Ejaz W, Kim HS (2012) PWAM: penalty-based weighted adjustment mechanism for cooperative spectrum sensing in centralized cognitive radios networks. Int J Innov Comput Inf Cont 8:1510–1517
Chuan L-qing, Zhi-ming W (2011) Adaptive weighted algorithm Of cooperative spectrum sensing in cognitive radio networks. In: IET International Communication Conference on Wireless Mobile and Computing, Shanghi, Nov 2011, pp 121–126
Zhou M, Chen H, Xie L, Wang K (2012) A reliable collaborative spectrum sensing scheme based on the ROCQ reputation model for cognitive radio networks, In: IEEE Vehicular Technology Conference, Quebec, May 2012, pp 1–5
Peh E, Liang Y (2007) Optimization for cooperative sensing in cognitive radio networks. In: IEEE Wireless Communications and Networking Conference, Hong Kong, Mar 2007, pp 27–32
Hossain E, Bhargava V (2007) Cognitive wireless communication networks. Springer, New York
Liang Y, Zeng Y, Peh EC, Hoang AT (2008) Sensing-throughput tradeoff for cognitive radio networks. IEEE Trans Wirel Commun 7:1326–1337
Peh EC, Liang Y, Guan YL, Zeng Y (2010) Cooperative spectrum sensing in cognitive radio networks with weighted decision fusion schemes. IEEE Trans Wirel Commun 9:3838–3847
Qihang P, Kun Z, Jun W, Shaoqian L (2006) A distributed spectrum sensing scheme based on credibility and evidence theory in cognitive radio context. In: IEEE International Symposium on Personal, Indoor and Mobile Radio Communications, Helsinki, Sept 2006, pp 1–5
Nguyen-Thanh N, Koo I (2009) An enhanced cooperative spectrum sensing scheme based on evidence theory and reliability source evaluation in cognitive radio context. IEEE Commun Lett 13:492–494
Feng J, Lu G, Bao Z (2012) Weighted-cooperative spectrum sensing scheme using trust in cognitive radio networks. In: IEEE International Conference on Signal Processing, Beijing, Oct 2012, pp 1693–1696
Qin T, Yu H, Leung C, Shen Z, Miao C (2009) Towards a trust aware cognitive radio architecture. ACM SIGMOBILE Mob Comput Commun Rev 13:86–95
Khan Z, Lehtomaki J, Umebayashi K, Vartiainen J (2010) On the selection of the best detection performance sensors for cognitive radio networks. IEEE Signal Process Lett 17:359–362
Zhang W, Mallik RK, Letaief KB (2008) Cooperative spectrum sensing optimization in cognitive radio networks. In: IEEE International Conference on Communications, Beijing, May 2008, pp 3411–3415
Li X, Li W, Hei Y (2012) Joint spectrum sensing and user selection strategy for cognitive radio networks. In: IEEE International Conference on Wireless Communications and Signal Processing, Huangshan, Oct 2012, pp 1–6
Jiang T, Qu D (2008) On minimum sensing error with spectrum sensing using counting rule in cognitive radio networks. In: International ICST Conference on Wireless Internet, Maui, Nov 2008, pp 1–9
Cacciapuoti AS, Akyildiz IF, Paura L (2012) Correlation-aware user selection for cooperative spectrum sensing in cognitive radio ad hoc networks. IEEE J Sel Areas Commun 30:297–306
Do T, Mark BL (2009) Joint spatial-temporal spectrum sensing for cognitive radio networks. In: Conference on Information Sciences and Systems, Baltimore, Mar 2009, pp 124–129
Khalid L, Anpalagan A (2012) Cooperative sensing with correlated local decisions in cognitive radio networks. IEEE Trans Veh Technol 61:843–849
Zeng K, Wang J, Li S, Cabric D (2011) Robust node selection for cooperative spectrum sensing with malicious users. In: IEEE Military Communications Conference, Baltimore, Nov 2011, pp 79–84
Wang W, Li H, Sun Y, Han Z (2010) Securing collaborative spectrum sensing against untrustworthy secondary users in cognitive radio networks. EURASIP J Adv Signal Process 2010:106–117
Song C, Zhang Q (2009) Achieving cooperative spectrum sensing in wireless cognitive radio networks. ACM SIGMOBILE Mob Comput Commun Spec Issue Cognit Radio Technol Syst 13:14–25
Wang B, Liu K, Clancy T (2010) Evolutionary cooperative spectrum sensing game:how to collaborate? IEEE Trans Commun 58:890–900
Li S, Zhu H, Yang B, Chen C, Guan X, Lin X (2012) Towards a game theoretical modeling of rational collaborative spectrum sensing in cognitive radio networks. In: IEEE Conference on Communications June 2012, pp 88–92
Lee WY, Akyildiz IF (2008) Optimal spectrum sensing framework for cognitive radio networks. IEEE Trans Wirel Commun 7:3845–3857
Yu R, Zhang Y, Yi L, Xie S, Song L, and Guizani M (2012) Secondary users cooperation in cognitive radio networks: balancing sensing accuracy and efficiency. IEEE Wirel Commun 19:30–37
Kim H, Shin KG (2008) Efficient discovery of spectrum opportunities with MAC-layer sensing in cognitive radio networks. IEEE Trans Mob Comput 7:533–545
Su H, Zhang X (2008) Cross-layer based opportunistic MAC protocols for QoS provisionings over cognitive radio wireless networks. IEEE J Sel Areas Commun 26:118–129
Xie S, Liu Y, Zhang Y, Yu R (2010) A parallel cooperative spectrum sensing in cognitive radio networks. IEEE Trans Veh Technol 59:4079–4092
Liu Y, Yu R, Zhang Y, Yuen C (2013) An efficient MAC protocol with selective grouping and cooperative sensing in cognitive radio networks. IEEE Trans Veh Technol 62:3928–3941
Noel A, Schober R (2012) Convex sensing-reporting optimization for cooperative spectrum sensing. IEEE Trans Wire Commun 11:1900–1910
Dai Z, Liu J, Long K (2015) Selective-reporting-based cooperative spectrum sensing strategies for cognitive radio networks. IEEE Trans Veh Technol 64:3043–3055
Sun C, Zhang W, Letaief K (2007) Cooperative spectrum sensing for cognitive radios under bandwidth constraints. In: IEEE Wireless Communications and Networking Conference, Hong Kong, Mar 2007, pp 1–5
Pham H, Zhang Y, Engelstad P, Skeie T, Eliassen F (2010) Energy minimization approach for optimal cooperative spectrum sensing in sensor-aided cognitive radio networks. In: International ICST Conference on Wireless Internet, Singapore, Mar 2010, pp 1–9
Gao Y, Xu W, Yang K, Niu K, Lin J (2013) Energy-efficient transmission with cooperative spectrum sensing in cognitive radio networks. In: IEEE Wireless Communications and Networking Conference, Apr 2013, pp 7–12
Hu H, Zhang H, Liang Y-C (2016) On the spectrum- and energy-efficiency tradeoff in cognitive radio networks. IEEE Trans Commun 64(2):490–501
Huang K (2013) Spatial throughput of mobile ad hoc networks powered by energy harvesting. IEEE Trans Inf Theory 59:7597–7612
Lee S, Zhang R, Huang K (2013) Opportunistic wireless energy harvesting in cognitive radio networks. IEEE Trans Wirel Commun 12:4788–4799
Park S, Kim H, Hong D (2013) Cognitive radio networks with energy harvesting. IEEE Trans Wirel Commun 12:1386–1397
Chung W, Park S, Lim S, Hong D (2014) Spectrum sensing optimization for energy-harvesting cognitive radio systems. IEEE Trans Wirel Commun 13:2601–2613
Donoho D (2006) Compressed sensing. IEEE Trans Inf Theory 52:1289–1306
Ragheb T, Kirolos S, Laska J, Gilbert A, Strauss M, Baraniuk R, Massoud Y (2007) Implementation models for analog-to-information conversion via random sampling. In: Midwest Symposium on Circuits and Systems, Montreal, Aug 2007, pp 325–328
Qin Z, Gao Y, Plumbley MD, Parini CG (2015) Wideband spectrum sensing on real time signals at sub-nyquist sampling rates in single and cooperative multiple nodes. IEEE Trans Signal Process 64(12):3106–3117
Paysarvi-Hoseini P, Beaulieu NC (2011) Optimal wideband spectrum sensing framework for cognitive radio systems. IEEE Trans Signal Process 59:1170–1182
Khalid L, Anpalagan A (2014) Adaptive grouping scheme for cooperative spectrum sensing in cognitive radio networks. In: IEEE Vehicular Technology Conference, May 2014, pp 1–5
Mishra S, Cabric D, Chang C, Willkomm D, van Schewick B, Wolisz A, Brodersen R (2005) A real time cognitive radio testbed for physical and link layer experiments. In: IEEE Symposium on New Frontiers in Dynamic Spectrum Access Networks, Nov 2005, pp 8–11
Yuan Y, Bahl P, Chandra R, Chou P, Ferrell J, Moscibroda T, Narlanka S, Wu Y (2007) KNOWS: kognitiv networking over white spaces. In: IEEE Symposium on New Frontiers in Dynamic Spectrum Access Networks, Apr 2007, pp 416–427
Gu S, Xu P, Wang X, Gan X, Yu H (2010) A real time testbed for the evaluation of cognitive radio MAC. In: IEEE Global Telecommunications Conference, Dec 2010, pp 1–5
Manna T, Misra IS (2013) Implementation of relay based collaborative spectrum sensing using coalitional games in wireless cognitive radio networks. Elsevier Comput Electr Eng J 45:77–99
Rice University, “warp.rice.edu.” WARP homepage, 2013
Masri A, Chiasserini C-F, Casetti C, Perotti A (2012) Common control channel allocation in cognitive radio networks through UWB communication. J Commun Netw 14:710–718
Chowdhury K, Akyildiz I (2011) OFDM based common control channel design for cognitive radio ad hoc networks. IEEE Trans Mob Comput 10:228–238
Jia J, Zhang Q, Shen X (2008) HC-MAC: a hardware constrained cognitive MAC for efficient spectrum management. IEEE J Sel Areas Commun 26:106–117
Zhou X, Ma J, Li GY, Kwon YH, Soong AC (2010) Probability-based combination for cooperative spectrum sensing. IEEE Trans Commun 58:463–466
Chen Y, Beaulieu N (2009) Performance of collaborative spectrum sensing for cognitive radio in the presence of gaussian channel estimation errors. IEEE Trans Commun 57:1944–1947
Zhang R, Wang M, Caiy LX, Zheng Z, Shen X, Xie L-L (2015) LTE-unlicensed: the future of spectrum aggregation for cellular networks. IEEE Wirel Commun 22:150–159
Khan AA, Rehmani MH, Reisslein M (2015) Cognitive radio for smart grids: survey of architectures, spectrum sensing mechanisms, and networking protocols. IEEE Commun Surv Tutorials 18:860–898
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2019 Springer Nature Singapore Pte Ltd.
About this entry
Cite this entry
Khalid, L., Anpalagan, A. (2019). Principles and Challenges of Cooperative Spectrum Sensing in Cognitive Radio Networks. In: Zhang, W. (eds) Handbook of Cognitive Radio . Springer, Singapore. https://doi.org/10.1007/978-981-10-1394-2_12
Download citation
DOI: https://doi.org/10.1007/978-981-10-1394-2_12
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-10-1393-5
Online ISBN: 978-981-10-1394-2
eBook Packages: EngineeringReference Module Computer Science and Engineering