Abstract
Nations have designed biosecurity systems to protect their animal, plant, and environmental resources from invasion by pests. Surveillance serves as a key component of that regulatory continuum. This chapter discusses “surveillance” and touches on many topics associated with it: Sampling, detection thresholds, Geographic Information Systems (GIS), and cyberinfrastructure.
Surveillance is an official process which collects and records data on pests (presence or absence) by survey, monitoring or other procedures. Here we outline types of survey operations, survey planning, survey design, GIS, and information management. Surveillance programmes are used to promote early pest detection, support trade by demonstrating pest freedom, delimit pest incursions, and monitor eradication and management programmes. Special emphasis is provided for pest-free areas including scenario tree modelling, statistical power and system approaches. An overview of survey planning is provided for targeted surveillance including the use of habitat, climate and pathway models to identify locations and time periods when exotic pests are most likely to be detected. The survey design section describes the basic principles for developing a sampling plan for detection surveys (including confidence and detection thresholds) and surveys for information (including sampling units, sample size and implementation). GIS and cyberinfrastructure are tools for data integration, project management and for communication to stakeholders. The chapter concludes with a surveillance case study, the USDA Cooperative Agriculture Pest Survey (CAPS), a joint Federal and State pest detection programme for exotic plant pests in the USA. CAPS conducts targeted “high hazard” surveillance including pest and commodity surveys. CAPS committees select national and state survey targets from annually prioritized pest lists.
Access provided by Autonomous University of Puebla. Download chapter PDF
Similar content being viewed by others
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
11.1 Introduction
Countries design biosecurity systems to protect their animal, plant, and environmental resources from invasive alien species. Countries maintain biosecurity systems to safely manage trade and prevent the introduction of invasive pests (insects, diseases and weeds) through numerous pathways of entry.
Plant biosecurity programmes seek to exclude exotic organisms from becoming established on agricultural crops, ornamental plants and “natural” areas. Without barriers for entry, invasive organisms can expand their range, colonize new territory and cause considerable economic and environmental damage (Magarey et al. 2009). Spatially, one country’s biosecurity efforts may be categorised as “pre-border”, “border” and “post-border” when describing that country’s attempts at minimising the movement of unwanted organisms. Countries collaborate internationally on a range of interrelated biosecurity activities to confront these exotic invasive species. Surveillance is a key component of that continuum.
The International Plant Protection Convention (IPPC) defines surveillance as an official process which collects and records data on pest occurrence or absence by survey, monitoring or other procedures. The diverse purposes of surveillance include:
-
Promote early detection of pests to facilitate eradication or management;
-
Support trade by demonstrating areas of pest freedom or low pest prevalence;
-
Describe the distribution and prevalence of risk organisms already present;
-
Delimit the full extent of pest population following a detected incursion;
-
Measure the success of biosecurity systems;
-
Enable management and cost benefit decisions;
-
Develop a list of pests or hosts present in an area;
-
Monitor progress in a pest eradication campaign;
-
Enable reporting to other organisations.
National Plant Protection Organisations (NPPO) and other regulatory agencies conduct different types of survey programmes to fulfil these needs. In addition, these Plant Protection agencies often rely on outreach to passively surveil partners who report pest detections. For example, in New Zealand most new pest detections are reported by industry, researchers, and the public via a toll-free telephone number (Froud et al. 2008).
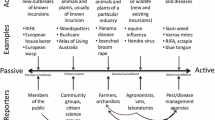
The success of plant protection programmes depends on the ability to detect pests. To conduct a survey, a large number of associated tools and technologies are required (Fig. 11.1). Some of the tools/technology involve statistics, GIS, data management and risk mapping, and will be discussed in this chapter. However, effective surveillance tools and technology are often lacking. When no effective insect trap or lure exists, officials must rely on visual surveys. Detecting plant diseases often presents an even greater challenge. The combination of high costs and inadequate technology leads to survey programmes that are less than optimal. As a result, pests frequently are introduced and become established before timely detection. With delay in discovery of invasive pests, the likelihood of eradication decreases while the cost of control/management/eradication increases dramatically.
Figure 11.2 shows the hierarchy of surveillance activities and the flow of information. The flow of information starts at the point of collection in the field. From that point, the information is integrated and tailored to meet the needs of various end-users. For a fruit fly trapping example, regulatory officials collect, clean and compile survey data for managers to use to control fruit fly outbreaks (Chap. 15). For another application, industry collects survey data as part of the day-to-day commercial operations. This data is then used as a basis to run predictive models that can help industry understand the movement of emerging pests or pests of phytosanitary concern (Chap. 9). The same data might also be used by growers or regulatory officials to take action in support of surveillance or eradication.
Information architecture for surveillance (Magarey et al. 2009). Arrows represent the directed flow of information
This chapter outlines types of survey operations and provides a review of survey design, information management, data integration, modelling, and GIS. Surveys may be structured around high-consequence target pests. Other surveys may focus on commodities and the survey of exotic pests that may be found associated with that commodity. Still other surveys may target high-risk areas. The USDA, APHIS PPQ Cooperative Agricultural Pest Survey (CAPS) serves as an example of a large surveillance programme that demonstrates various surveillance concepts in practise.
11.2 Survey Operations
11.2.1 Detection Surveys
The goal of detection surveys to is discover an invasive species while its populations are numerically small and geographically confined. Early Detection Surveys locate species that are in the process of establishing in an area An Early Detection Survey could, for example, determine whether non-native snails are present in an intermodal container yard.
A Targeted Detection Survey focuses on areas more likely to experience new pest introductions. Targeted surveys are based upon phytosanitary data such as emergency action notifications or pest-interception data. In the USA, the High Hazard (or “Hotzone”) Programme is designed to enhance the ability of the CAPS Programme to identify and target high-risk areas and sentinel sites within the USA. The methodology for a High Hazard Survey decides upon which species or high-risk pathways to search, and which areas should be the focus of a survey. In the programme, three types of high-risk sites are identified: Primary; secondary and tertiary (Watkins and Messineo, personal communication).
Primary risk sites include business, organisation, operation, or areas that have functioned as a destination or waypoint for commerce that has a confirmed record or recent association with invasive organisms or pests. These sites have a high potential for pest introduction and/or establishment and therefore should be of highest priority for survey efforts. Primary risk sites require intensive monitoring. For example, in large metropolitan areas (especially where high volumes of international trade and/or travel exist) a primary hot zone may include such areas as an international airport, seaport and their environs, a foreign trade zone, a container yard, or trucking terminal.
Secondary risk sites have physical descriptions or characteristics similar to a primary risk site but with no known history of invasive organisms or pest interception and/or introduction. The key characteristic of this zone is that it is documented as having recently received potentially infested commodities directly or indirectly from a primary hot zone. Secondary hot zones contain moderate risk and require routine monitoring to evaluate whether there is a change in status.
Tertiary risk sites share similarity in commerce or commerce-related activities with known hot zones and that have no known record of invasive organism, pest interception and/or introduction. The key characteristic of this hot zone is that it is not documented as having recently received potentially infested commodities from either a primary or secondary hot zone. Tertiary hot zones are of undefined yet suspected risk and therefore require periodic monitoring to evaluate for a change in status. This is similar to a scheme developed in Australia that involves a four-level classification system for risk sites (Self and Kay 2005).
11.2.2 Monitoring Surveys
The International Standards for Phytosanitary Measure (ISPM) 5 defines monitoring survey as an ongoing survey to verify the characteristics of a pest population. By this definition, monitoring surveys apply where a pest is known to be present and the survey is planned to examine aspects of the pest population such as prevalence of the pest and changes in pest prevalence over time (Evans and McMaugh 2005). Two reasons for using a Monitoring Survey are: Survey to assist with pest management and to develop and maintain an area of Area of Low Pest Prevalence (ALPP) status. One example of the former is the APHIS PPQ area-wide pest management programme for Glassy Winged Sharpshooter (GWSS, (Homalodisca vitripennis (Germar)) in California. The GWSS is a vector for Pierces Disease (caused by Xylella fastidiosa Wells et al.), which is very damaging to grapevines. Citrus is a reservoir for GWSS, so monitoring is used to determine when citrus groves should be sprayed to prevent the build-up of damaging GWSS populations that could impact grapevines (Hix et al. 2003). Another example involves monitoring for Asian Soybean Rust (caused by Phakopsora pachyrhizi Syd. & P. Syd.) in the USA (Isard et al. 2007). Sentinel plots were deployed initially across the entire soybean belt and later mostly in southern states. Sentinel plots were funded by government and industry and maintained by university extension specialists. The sentinel plots in southern states provided a warning system that allowed northern-state producers (where most soybeans are grown) to avoid application of fungicide sprays.
11.2.3 Delimiting Surveys
Delimiting Surveys are another type of survey (see ISPM 6 IPPC 1997) used to establish the boundaries of an area considered to be infested by or free from a pest. Delimiting Surveys are conducted to determine the extent and distribution of a pest incursion, and to determine whether the pest is eradicable. A good example of a Delimiting Survey is the survey used to determine the extent of Citrus Greening (HLB) (caused by ‘Candidatus Liberibacter’ spp.) outbreaks in Florida. The discovery of HLB in Florida City, Florida immediately prompted a survey to delimit the infection (Gottwald et al. 2007). East–west transects were surveyed every five miles northward from Florida City in an attempt to determine the northern extent of HLB distribution. A positive detection within a transect immediately prompted a survey in the adjacent transect 5 miles to the north. HLB distribution was quickly confirmed to extend northward to the Fort Pierce residential area, 120 miles (193 km) from the initial detection.
11.2.4 Pest-Free Areas
The definition of a Pest-free Area (PFA) for the purposes of this chapter is: An area prescribed by the IPPC Secretariat and relevant ISPMs that covers this broad area. All PFA and Systems Approaches must be science based. PFAs and Systems Approaches are generally highly regulated processes that are “officially maintained” and can be cost and management intensive. PFAs can deliver low-risk pathways that allow high-value plant-based commodities to be traded with confidence from areas outside or within an endemic area for a particular pest (see ISPM 10, IPPC 1999). Ideally these approaches should allow the delivery of a quality commodity without the need for drastic endpoint measures like fumigation that may cause residue issues, physiological changes in the produce and reduce the shelf life of a commodity.
A PFA approach may be used to indicate that a pest does not occur within a designated area/property (or above a stipulated level of prevalence) and these need to be confirmed for trade purposes. Conversely, the PFA does not mean that a pest is not present within a prescribed area. Rather, it means that a pest cannot be or never has been detected at the agreed level of surveillance/sampling to allow trade.
SPS Agreements define the Appropriate Level of (sanitary or phytosanitary) Protection, (ALOP) as the level of protection deemed appropriate by the member establishing a sanitary or phytosanitary measure to protect human, animal or plant life or health within its territory. This concept is also referred to as the “acceptable level of risk”.
PFAs are created through a science-based agreement between two trading (country/regional) partners generally for a specific pest. PFAs are not multi-lateral agreements that can be applied automatically to other pests and situations. PFAs rely on goodwill from both partners with respect to transparent compliance and auditing procedures. Nevertheless, an existing agreement could be used as the basis of a new agreement.
11.2.5 Scenario Tree Modelling for Evaluation of Surveillance Supporting Pest-Free Status
We cannot prove that an area is free of any pest. Proof would require testing of all susceptible individuals with a perfect test (a test free of error), and then would only provide freedom for that point in time. The best that can be done is to estimate the probability that the area is “free” of the pest, based on the available evidence. In this context, “freedom” from the pest must be interpreted as “there is less of it present than some agreed low but detectable threshold level” (Cameron and Baldock 1998; Martin et al. 2007).
Evidence for estimation of probability of area freedom comes in two forms: (1) Historical records of pest occurrence and eradication, and (2) negative results of more current surveillance activities aimed at detecting the pest. Often, such surveillance activities are non-random and designed to look for the pest in places where it would be most likely to occur if present. Such biased surveillance information is not amenable to standard techniques for analysing representative surveys. Biased surveillance often is ignored in quantitative evaluations of claims of pest-free status. Similarly, that the pest “has not been seen” or is “not known to occur” (i.e., has not been detected in the general, passive surveillance process) is also ignored.
Scenario Tree Modelling is designed for evaluation of animal health surveillance, and may be used for evaluation of evidence supporting pest-free status. In this approach a surveillance system for pest detection comprises multiple components, each of which has a probability of detecting the pest, when present at or above the threshold level. The process by which each component detects the organism (when present in the area) is described using a stochastic Scenario Tree Model (Martin et al. 2007). This model defines the activities of the component and includes all factors that affect probabilities of pest presence and pest detection in a surveillance unit (often an area of land, a tree, or a sample of grain) selected at random from among those “processed” in the surveillance activity. The probability is calculated that this representative unit gives a positive outcome. Then, the probability can be calculated that the surveillance component will give one or more positive outcomes when the pest is present at the threshold level. In calculating this sensitivity of the surveillance component, any clustering of the pest can be identified along with other causes of lack of independence among surveillance units and detection processes, and differential risk of infestation among surveillance units. Sensitivity calculations are based on the assumption that in surveillance for a pest that is not present, false positive results are not acceptable, and will always be resolved into true positives or negatives (Martin et al. 2007).
The sensitivities of surveillance components are then combined to give a surveillance-system sensitivity. This process may be repeated for sequential surveillance time periods (often months or years). The probability that the area is “free” from the pest may then be estimated from the surveillance sensitivity and a prior estimate of the probability of freedom. For sequential time periods, these prior estimates are best based on previous surveillance evidence for pest freedom. The posterior estimate of probability of freedom for one time period is used as the basis of prior estimate for the following time period, adjusted for possibility of pest introduction during the period between rounds of surveillance (Martin et al. 2007). Thus, past surveillance evidence is accumulated over time to give a current probability of pest freedom.
11.2.6 Statistical Power Approach to Pest-Free Areas
Certification of a country (or a region within a country) as pest-free enables it to avoid trade restrictions that another country may impose on importation of commodities associated with the pest in question. This certification is a matter between the two trading countries, which occurs under rules that should be compliant with international phytosanitary standards (IPPC 2009b).
These standards and reports enable the establishment and evaluation of pest freedom claims, but the claims have a complex mix of quantitative and qualitative components, which must somehow be integrated for a single decision. Inescapably, this decision is partly subjective and it would be desirable to have a more empirical and less subjective measure of a claim’s merits. With diverse sources of quantitative and qualitative information, we cannot place an overall measure on the quality of knowledge about pest freedom.
A quantitative component is provided by the surveillance programme, which should be compliant with ISPM 6 (IPPC 1997). This identifies two major types of surveillance systems: General Surveillance and Specific Surveys. General Surveillance refers to sources of information of many types that may lend weight by inference to the pest freedom claim. Specific surveys collect direct data on pest status. The information obtained from General Surveillance rarely provides empirical evidence of pest freedom, but is more of the nature of “the pest in question has never been observed”, without quantification of the surveillance effort made. Empirical evidence in the form of “the pest is known not to occur” normally is derived only from specific surveys. Specific surveys tend to be simple designs (e.g. specified number of trees and fruit that must be sampled in a district of given size) to give a certain level of confidence (e.g. 99 %) of pest freedom at a certain design prevalence (e.g. 1 %). Other sources of evidence (observations of farm consultants, negative diagnostic samples in a district lab, etc.) tend to be ignored or at most, provided as general surveillance information.
11.2.7 Systems Approaches as an Adjunct for Pest Free Area Status
In Australia, regulatory officials are withdrawing dimethoate and fenthion for post-harvest treatments of horticultural products, especially for commodities with edible skins. Consequently, alternative methods must be developed to control plant pests. “Systems Approach” is among the options considered. The ISPM defines System Approach as…‘The integration of different risk management measures, at least two of which act independently, and which cumulatively achieve the appropriate level of protection against regulated pests’ (FAO 2009).
For the Systems Approach to pest management to gain widespread acceptance in international trade, new analytical methods are required to demonstrate that the efficacy of the multiple risk-reduction measures in a system are equivalent to a single post-harvest treatment with dimethoate and fenthion.
A major issue facing advancement of a Systems Approach is the need to determine how efficacy of measures in a Systems Approach will be determined. Historically, ‘Probit 9 statistical standard’ (Baker 1939), has been used as the basis for evaluating efficacy of measures. When a single post-harvest measure (e.g. post-harvest dip, forced hot-air) has been used to manage phytosanitary risk, their acceptability has been evaluated against a standard. For example, the ‘Probit 9 statistical standard’ has long been required by the USDA for demonstrating the efficacy of phytosanitary treatments applied to certain pests, especially tephritid fruit flies (See Sect. 15.3; Baker 1939).
In contrast, ‘Probit 8.7’ is widely accepted throughout the Asia-Pacific region as the basis for approving quarantine treatments for tephritid fruit flies. None of these statistical standards makes operational sense when evaluating systems approaches because they focus on survivorship of insects rather than determining the level of infestation and its acceptability. Quantitative risk assessment could be used to demonstrate equivalence for the purpose of international and domestic trade, evaluate the potential of risk reduction strategies and prioritize research/information needs (See Sect. 5.5).
A quantitative risk assessment can be defined as a mathematical model in which inputs and outputs are expressed numerically (Evans and Olson 1998). In some quantitative models, referred to as Stochastic or Probabilistic Models, some or all of the inputs are probability distributions (See Sect. 5.5; Evans and Olson 1998). Complexity and resource requirements are greatest for a Stochastic Model. However, the benefit of using a Stochastic Model is that we can explore variability and uncertainty.
In conclusion, Probit 9 measures do not make operational sense when evaluating systems approaches because they focus on survivorship of insects rather than determining the level of infestation and its acceptability. The most appropriate model depends on the purpose of the model. Consequently, regulators must agree on other approaches for the evaluation of the efficacy of measures, when more than one measure is combined in a systems approach.
11.3 Survey Planning
11.3.1 Targeted Surveillance Overview
National Plant Protection Organisations do not have resources to conduct surveillance programmes for all crops, forests and natural environments that are vulnerable to exotic plant pests. Thus, surveillance programmes require spatial and temporal targeting to identify regions, areas and locations, and seasons or periods where and when exotic pests are most likely to be detected. Spatial Targeting enables resources to be allocated in the most efficient manner. Temporal Targeting enables traps or personnel to be deployed during periods of time when the pest is most active.
Suitable survey sites are selected by:
-
Geographical distribution of production areas and/or their size;
-
Pest management programmes (commercial and non-commercial sites), cultivars present;
-
Points of consolidation of harvested commodity (e.g., a nursery, pallet or container storage-area, or a dense area of host material);
-
Sampling technique appropriate to type of harvested commodity;
-
Previously reported presence and distribution of pest;
-
Biology of pest;
-
Climatic suitability of sites for pest.
Timing of survey procedures may be determined by:
-
Life cycle of pest;
-
Phenology of pest and its hosts;
-
Timing of pest management programmes;
-
Whether pest is best detected on crops in active growth or in harvested crop.
Additional Points:
Surveyors need identification aids for suspects or target species for which they will be searching (Chap. 12). Images on websites such as CABI, EXFOR, or Invasives.org may be useful. Chose a survey interval in which your target species is active and visible.
Decontaminate surveyors and survey equipment! (For plant diseases, utilise a suitable decontaminant.) This action helps prevent invasive pests, from spreading to new sites (See Sects. 18.3 and 18.4). Report findings to your local Plant Protection Organisation or NPPO.
More sophisticated targeting information can be provided by a combination of techniques and data derived from pest data sheets, pest risk maps and pest models. Targeting information can be created by habitat, climate pathway, economic and prioritization models. The Habitat (host) Model represents where an invasive organism is likely to find suitable hosts or which hosts are available at a given location. The Climate Model provides information about where or when an invasive organism is likely to survive and reproduce. The Pathway Model provides the most likely entry points for an invasive organism. The Economic Model integrates habitat, climate and pathway models to determine costs and benefits of a particular surveillance programme. Individual maps or models can be summarized using techniques such as the Multi Criteria Decision System (BRS 2007), which allows users to weigh individual risk layers. Pareto Ranking is being evaluated for this purpose in the USA and Canada (Magarey et al. 2010).
Prioritization is the process of determining invasive organisms that are most important to target in a particular area. Here, we describe only habitat, climate and pathway models because they are the most essential components for a surveillance programme.
11.3.2 Habitat Models
These models are used to determine areas most likely to be points of introduction and establishment for an invasive organism. Habitat Models can be challenging to construct because many sources of information are needed including crop and forest inventory data, land-use data and species distribution data. Complexities may arise in constructing maps for a pest species that attacks crop, forest and environmental hosts of importance because the data may be in different formats. For example, crop distribution data may be in acres, forest inventory in species per acre, and species distribution in presence/absence for a geographical location or jurisdiction. We discuss data sources in turn and indicate some of their limitations or advantages.
A land-use database is the fundamental data source for constructing a host risk-map. This data source can be used in the absence of other information or used to downscale other data sources to a finer resolution. A typical land-use database will describe classes including cropland, deciduous, evergreen and mixed forests, rangeland and urban areas. Land-use databases are usually derived from satellite imagery. Consequently they are widely available. For example, a global land-use database, derived from satellite imagery, is now available at a 300 m resolution (European Space Agency http://due.esrin.esa.int/prjs/prjs68.php).
In the USA, crop inventory data is supplied by the USDA’s National Agricultural Statistics Service (NASS) and collected under the Agricultural Census Programme. Data is available at the resolution of a County and is available for 127 crop types. Several different units of host availability are recorded including acreage, production and economic value. Usefulness of this approach is limited because the data is available in 4-year installments (2007 is latest), with a lag-time of 1 year or more before release. For some commodities, we must consult industry or commercial sales databases to determine the best surveillance locations. Commercial sales databases may require georeferencing before the information can be mapped. In countries where spatially explicit information about crop production is not available, one option is to take broad-scale information such as production figures for a state or country, and distribute the production to cropland areas from a land-use database.
In the USA, forestry data is available on the USFS Forest Inventory data site (FIDO) site (http://fia.fs.fed.us/). These data sources include the acreage of individual forest species by county. The FIDO database does not record the distribution of understory species that may be important hosts for some invasive organisms, and this is a limitation.
In forest and natural environments, the distribution of many host-plant species can be estimated from species distribution databases such as the Global Biodiversity Information Facility (GBIF, http:www.gbif.org). GBIF is a data portal that contains worldwide georeferenced species distribution records from museums and herbaria. GBIF is a powerful resource with two major limitations. First, the data confirm presence only and the abundance of the host species is typically not known. Second, only a proportion of the known species distribution data are present in GBIF. Country data sources may contain more records.
In the CAPS programme, a summary host risk-map is made for each exotic pest that is on its priority list. The host risk-map is created by estimating host-density within a county, which is a function of total acreage of susceptible hosts and total acres in that county. Primary hosts (as determined by a pest database such as the CABI Crop Compendium) and secondary hosts are included in the model. A one-to-ten scale describes the proportion of total host acreage per county.
11.3.3 Climate Models
Climate models are used to determine a pest’s potential range and to help estimate the best time for survey activities. Climate is a major influence on a pest’s phenology, reproduction, dispersion, and overwintering survival, and a critical component of pest targeting. Climate-based modeling may be useful for pathogens that are weather-driven or moisture-dependent, but may not be helpful for pathogens that have broad requirements or are pests of indoor environments (e.g. greenhouses). In addition, crops growing in unique microclimates or grown under irrigation present additional challenges to modelers. The three most important components of climate models are climate databases, model selection and interpretation.
Climate databases (including those with global extents) are now widely available. In recent years, we have seen a shift to grid databases and away from those based on station datasets. Databases can be discussed in terms of variables, resolution and period. Date in a modern agricultural weather database includes native variables and data derived from models of native variables. The most important variables for pest risk modeling are degree days and extremes in temperature. Leaf wetness (which can be derived from commonly collected native variables), relative humidity and precipitation are of primary importance for predicting infection periods of certain fungal pathogens and bacteria or periods when mollusks are active. Other variables such as wind speed and direction are important in predicting the dispersal of diseases such as rusts, but this is beyond the scope of the section.
Time period is the second important component for a database. Many risk maps are created using 10 or 30-year climate data. This allows a user to predict the most likely pest behaviour in an average year. Maps with low spatial resolution may miss climate variability driven by topographical features such as mountains. Decision-makers wish to see the highest possible spatial resolution, but it comes at increasing costs.
Several climate-based risk mapping systems (CLIMATE, CLIMEX, NAPPFAST, and MAXENT) have been used for plant pest risk analysis (Venette 2010). Climate risk-mapping tools will use either deductive or inductive mapping approaches (Baker 2002). Deductive approaches (e.g., CLIMEX compare locations, NAPPFAST) use experimental data to create biological models that predict a pathogen’s distribution from weather or climate data. Deductive techniques work best when there is adequate information available about the biological requirements (e.g., day-degree thresholds, cardinal temperatures for growth, cold or heat-killing thresholds, leaf wetness or relative humidity requirements for infection etc.) of the pathogen. Many of these requirements are available from databases such as the CABI Crop Compendium or may be estimated from a closely related species. Inductive techniques (e.g. MaxEnt, CLIMEX match climates) are based on a statistical match of a pathogen’s observed distribution and climate variables.
11.3.4 Pathway Models
Pathway risk mapping and modeling is perhaps the most important component of targeting. Pathway risk maps define location at most risk to the introduction of exotic pests. The main sources of data for the creation of these maps include phytosanitary data (e.g., interceptions, emergency actions, fumigations, commodity or nursery import data), trade and freight data and commercial sales data sets. The simplest method to create pathway risk maps is to map locations or ports by frequency of pest interceptions or emergency actions. An excellent example is the USDA APHIS PPQ CAPS Florida Tile Warehouse Survey that resulted in the discovery of several new (previously undetected) species/genera (Beckwith 2004). Sometimes, species new to science are discovered in regulatory surveys. Surveillance may also be conducted at other high-risk or hazard zones such as airports, rail yards or national parks (Self and Kay 2005).
More recently in the USA, techniques have been developed to create pathway maps using the Freight Analysis Framework (FAF) database (Colunga-Garcia et al. 2010a, b). Pathways in FAF were classified according to seven international regions of origin and 43 broad import commodity classes. Imports entering the USA were distributed to 131 regions including major metropolitan areas, remainder of state and border areas. For each pest, the introduction pathways were assessed from its international distribution and from its trade (HS) import commodity association. The final risk classes represent the tonnage of potentially infested commodities (hosts) coming from countries where the pest has been reported (Colunga-Garcia et al. 2010a, b).
11.3.5 Statistical Methods and Sampling
Introduction. The success of plant protection programmes depends on our ability to detect pests. However, often we cannot survey all potential locations or every host plant in a given area where a pest may occur. Survey designs and sampling methods are used to provide a level of confidence that the pest is not present or make inferences about the pest population. Here we describe the basic principles of surveying for detection (presence/absence of a pest) versus survey for information (level of infestation) and give examples of developing a sampling plan that will support the surveillance programme.
Several key points must be considered:
-
Confidence Level: Our level of accuracy (confidence) in our results (conclusions). When we say we are 95 % sure a shipment is “pest free” we mean that (on average) given our methods and assumptions, we are correct at least 95 % of the time. For agricultural regulatory work, confidence levels are seldom less than 95 % but often may be higher, e.g., 99.9 %.
-
Detection Level or Threshold: The smallest infestation rate at which we can detect a pest, given our sampling effort and confidence level.
-
Sample Unit: The basic unit we are inspecting to find the pest. Depending on circumstances this could be a tree, a single leaf, a box of fruit, or a bouquet of flowers.
-
Sample Size: The number of sample units inspected, e.g., the number of traps placed in a field.
-
Sampling Efficiency: A rate or percentage that reflects the accuracy of our inspections. If a pest is in a sample unit (e.g., a fruit or bouquet), then how likely is it to be found? Historically many people have assumed this to be near 100 %, but for many inspections this is not realistic. A low sampling efficiency must result in a larger sample size for any stated conclusions to be correct.
-
Important Observation: We can never say that we are 100 % certain that an area (or population) is pest free unless we inspect 100 % with 100 % efficiency. This standard is rarely realistic. The best we can do is to say that we are sure (at some Confidence Level) that a pest is present in a population at less than a level of detection.
How do all of the above points fit together? Confidence Level, detection threshold, and sample size are all interrelated. Any two features determine the third. Most often we start with a Confidence Level and Detection Threshold and from that determine the appropriate sample size. For example: Say we are visually inspecting an orchard with 1,000 trees for an insect pest. If our inspections are all negative, we can make the following statements:
-
If we inspected 18 trees, then we could say with 95 % confidence that the infestation rate is less than 0.16 (16 %).
-
If we inspected 72 trees, then we could say with 95 % confidence that the infestation rate is less than 0.04 (4 %).
-
If we inspected 205 trees, then we could say with 95 % confidence that the infestation rate is less than 0.01 (1 %).
-
If we inspected 86 trees, then we could say with 99 % confidence that the infestation rate is less than 0.05 (5 %) (Table 11.1).
Table 11.1 Summary of two basic types of sampling conducted by biosecurity agencies
Sampling for information vs. sampling for detection. To conduct a statistically sound survey, the sampling method must be clearly detailed, so trading partners can decide whether the method is valid. An invalid method can cause sampling error, which would call the results of the study into question.
Typical Methods:
-
Simple random: Each sample has an equal probability of selection: The population is not subdivided or partitioned (example: Survey 10 trees in a grove of 100 trees, using a random number table to select the 4, 12, 13, 27th etc. tree);
-
Systematic: The target population is arranged according to some ordering scheme and then samples are selected at regular intervals through that ordered list (example: Survey every 10th tree in the grove);
-
Stratified: When the population can be divided into distinct categories and then the samples are randomly selected from that ‘strata’ (example: The grove is divided into lime, orange and grapefruit trees and 10 trees are randomly selected from each type);
-
Cluster: The sample is selected from certain areas only, or at certain time-periods only (example: Citrus groves in Orange Co.);
-
Convenience sampling (Accidental or Opportunity Sampling): When the sample is drawn from part of the population that is nearby (example: Survey a citrus tree along a road). With this type of sample we cannot scientifically make generalizations about the total population from the sample because it would not be sufficiently representative. This method of sampling is most useful for pilot testing.
Survey Design: Sampling for Detection. Surveys can be designed for the detection of pest (presence/absence) or created to give information about the pest (e.g. its abundance). Surveying for detection only requires sampling up to the discovery of the pest. The surveyor using this design can only make inferences about the sample taken. This type of survey can be used for early detection of pests to facilitate eradication or management, to support trade by demonstrating areas of pest freedom or low pest prevalence or to delimit the full extent of a pest following an incursion. After a pest is found, other types of monitoring programmes may be established to quantify the prevalence of a pest in an area in order to make conclusions about the pest population. This type of monitoring programme can be used to describe the distribution and prevalence of pest already present.
Although surveys based on convenience sampling are commonly used in detection and eradication programmes, they can never be used to confirm that a species is absent from a location. Was the species there but not detected, or was the species genuinely absent? At times, a species can be present in an area but go undetected due to random chance. Therefore, detection threshold or confidence limits are used to provide a tolerance limit or acceptable risk that a pest may be present in an area.
Detection thresholds. Detection thresholds refer to the minimum level of pest that can be detected given the sample size, detection methods, and conditions of the survey. It is used when the prevalence is thought to be near-zero. Even if a pest is never found, there is a chance that some or a few of the pests are still present. Because they are in very small numbers and do not appear to be causing damage, their presence could be tolerated. Threshold is usually based on scientific analysis, policy decisions, and risk assessment by all parties involved. If the survey involves trading partners, then the detection threshold will be set equal to the negotiated tolerance level.
Declaring an invasive species eradicated is usually based on a prescribed time for a series of negative results (“no finds”). For instance, three consecutive years of negative survey results may be used. However, such an approach has limitations, especially when the species becomes more rare as eradication efforts become successful. It also does not consider the cost of the surveys relative to the cost of premature declaration of eradication.
Confidence of Detection. If a pest is not found, then a degree of uncertainty still exists concerning the plants or areas that have not been examined or tested. A statistical confidence statement expresses the probability that the actual pest prevalence will be no more than the detection threshold. For example, after sampling a 95 % confidence interval for a detection level of .01 states that there is a 95 % probability that the actual prevalence is .01 or less. The relationship between confidence and sample size is simple – the more sites surveyed the more certain one can be about the detection results.
As a general rule a confidence level of at least 95% is considered acceptable, but in some cases, a confidence of up to 99.9 % may be necessary. For example, trading partners may require a particular level of confidence that the pest would be detected in a survey, independent of any logistical or financial constraints.
Sampling for Information. A selection of the population is used to make generalised conclusions about the entire population. Many planning decisions must be made before the first samples are acquired. When you go out looking for plant pests you have already decided where to survey, how many samples to take, and what type of data is necessary.
The sampling process comprises several stages:
-
Defining the specific survey objective (detect, delimit or determine prevalence);
-
Defining the population of concern (country, pest-free area, commodity);
-
Specifying a sampling unit or events to measure (individual insect, box of fruit, individual plant);
-
Specifying a method for selecting sample unit (random, systematic, stratified/targeted);
-
Determining the sample size (number of plants, number of farms);
-
Implementing the sampling plan;
Sampling and data collecting:
Sampling Units. The population must be divided into sampling units before a sample can be collected. The units must cover the entire population and must not overlap; that is, the sampling units must be mutually exclusive. In this sense every element in the population must belong to one and only one sampling unit. Sometimes the selection of the sampling unit is obvious: A population of insects in which the unit is a single insect. Sometimes there is a choice of unit: Sampling commodities entering the country in which the sampling unit may be the individual commodity unit. For instance, a potato, an apple etc. or a box or crate of the commodity with a complete sample of all the individual items it contains. Alternatively, it could be a selected shipping container with a subsample of the units contained therein. In sampling an agricultural crop, the unit might be a field, a farm, or an area of land whose shape and dimensions are at our disposal.
-
Sample size. Sample size is the number of sites or sampling units required to survey in order to detect a specified proportion of pest infestation with a specific level of confidence. Sample size is based on detection threshold, the accuracy of the methods and the confidence required. The specified proportion of infestation (detection threshold) required may be set by you or your trading partners. Generally, the larger the sample size, the better the results. However, time and resources usually limit the number of units sampled.
-
Implementing the survey plan. A survey plan should be well documented and the results should represent the actual pest status. Most important, the plans should be physically and financially acceptable. There is no one-way to design and implement a survey and determine the correct number of samples. Consequently, the reasons for choosing design steps must be transparent. The most successful surveys are designed and implemented through a close collaboration of biologists, statisticians and other relevant parties. The biologist has expert knowledge of species and system of interest with an appreciation of field techniques that could be employed; the statistician has knowledge of appropriate analytic techniques and awareness of data requirements.
11.4 Spatial Analysis (GIS)
11.4.1 Introduction
The term and technology of GIS has existed for more than 25 years, and GIS has taken on several meanings. The acronym originally meant “Geographic Information Systems” and referred to the integrated software that enabled the collection, manipulation, analysis, and presentation of spatial data. Subsequently, as the numbers of users and applications grew, GIS was defined by some practitioners as “Geographic Information Science” stressing the analysis and rigor behind many of the applications used today. They point to areas of GIS such as remote sensing, modeling, and spatial statistics to show where GIS, under either definition, has matured from creating simple, static maps to a system that can produce dynamic, interactive applications. In this section we use GIS in the classic definition (Geographic Information Systems) but hope to present examples of GIS applications that include more involved analysis.
11.4.2 GIS as a Project Management Tool
All biosecurity data has a spatial component, hence it can be represented on a map. As such, a GIS is critical to any control/management/survey programme conducted by a biosecurity agency. A good illustration of a GIS as a management tool is the Citrus Canker Eradication Programme that occurred in Miami, Florida, during 2003–2006 (see Sect. 18.3). Critical information that the programme needed to track for each individual property included:
-
Is citrus on the premises?
-
When was a particular property last surveyed?
-
Were suspect trees found?
-
Have the canker finds been confirmed by a pathologist?
-
Have homeowners given permission for tree removal?
-
Were trees removed and destroyed?
-
Are there other properties within 200 m with citrus trees?
This programme encompassed more than 100,000 properties and a million people. The ability of a manager to visualize the data on a map is invaluable. A GIS linked to the programme’s database can assist with answering these kinds of questions:
-
Where have we surveyed and where will we need to survey next?
-
How has a new positive detection changed our surveys?
-
In which areas will we need more personnel?
-
Which areas are ahead of or behind schedule?
-
How is the pest spreading?
-
Where are our management procedures not working?
-
What areas are of greater risk?
GIS can be an effective tool for data management and project oversight. GIS can help collect field data with tools like ArcPad, it can be used for QA/QC, and it can assist in managing personnel and equipment.
Figure 11.3 shows an example from a 2010 fruit fly monitoring programme in Central Florida. It uses a GIS to coordinate, manage, and report its survey activities. This map shows the history of fruit fly finds over a 10-year period.
The Florida Fruit Fly Detection (FFD) programme is a cooperative effort between the Florida Department of Agriculture & Consumer Services’ (FDACS), Division of Plant Industry (DPI) and the USDA APHIS PPQ (see Sect. 15.6.3). The programme was designed to detect new introductions of exotic target flies before they become established, reproduce, and spread. State and federal survey technicians monitor nearly 56,000 traps dispersed across 9,300 square miles of the state.
Traps are serviced at 2–3 week intervals depending on the risk assessment of the county in which they are located. In an average month, federal survey technicians visit over 56,000 trapsite locations. Global Positioning System (GPS) coordinates have been captured for all trapsites. This information gives programme officers and supervisors the ability to see and measure the spatial distribution of traps and ensure that targeted high-risk areas have a sufficient number of traps. Fruit Fly Detection data, including geographic coordinates, are collected in the field via PDAs and stored in a central database (ETRAP) that is accessible to officers, supervisors, programme coordinators and supporting staff.
Each FFD office has at least one installation of ArcGIS so local staff can create maps using a customized toolbar developed for those who have little or no GIS software experience. The maps contain a dynamic link to the ETRAP database so current trapsite locations can be viewed at any time.
11.4.3 GIS as an Analysis Tool
GIS provides tools that allow a more inclusive and complex analysis to support managers and programmes. Data may come from many sources and may include: Point data (survey data); line data (rivers and roads); polygon data (quarantine areas); or remotely sensed data (aerial photographs and satellite images). GIS allows an analyst to incorporate various kinds of data into a model to help predict introduction of a pest, the spread of a pest, the best quarantine boundaries, etc.
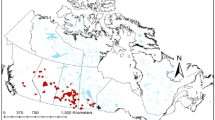
One example of this kind of work is an analysis of Asian Gypsy Moth (AGM) trap locations in Washington and Oregon states. The goal of this analysis was to support trap placement by the two states’ Departments of Agriculture. The analyst created a map showing areas of likely introduction. This “model” was based on many layers and combines data on population, trade, roads, ports, waterways, hosts, and intermodal facilities to estimate the risk on introduction of Asian Gypsy Moth into Washington and Oregon. The red areas are of higher risk (Fig. 11.4).
The map from the model was compared to the current (previous year’s) trap locations. For the project managers in Washington and Oregon, this was a valuable comparison to see where their map agreed with their trapping and where the two differed. It helped them evaluate their trap locations and trap densities. Note that the GIS model does not dictate to the manager where to place their traps. It is a tool to assist managers in the allocation of their resources.
11.4.4 GIS as a Communication Tool
The third area of focus for this brief overview of GIS involves using maps as a communication tool. Most people can read and interpret maps, which make maps ideal reporting, and summarizing tools. The legal description of a quarantine area is ponderous and difficult to visualize. In contrast, a map can clearly show the area. Maps can also show a manager or supervisor areas that have been surveyed, the locations of positives, and the locations that the programme will survey next.
A map can summarize a risk or models into an easily understood package. Most people would rather look at a map than a table of figures. A map can’t replace a detailed tabulation, but it can make the numbers more easily understood. The key is to produce maps that present their message in a clear, concise, and understandable manner.
Below, we give two examples of maps trying to present the same data. The “bad” map is clearly poor, but it is not that different from many maps presented routinely. Many map-making software products are commercially available, but using these tools doesn’t guarantee a good result anymore than using MS Word guarantees a clearly written report. Creating a map should be like constructing a good paragraph.
Consider the two maps in Figs. 11.5 and 11.6. Either map may work for someone who is actively involved in a specific programme, but would anyone not involved in the project understand the map in Fig. 11.5? Does everyone know the area, know the insect of concern, when the map was made and by whom? Most people would say the second map communicates more effectively.
Guidelines for a good map:
-
What is the purpose of the map and what information must be included?
-
What map projection is most suitable?
-
What characteristics are not relevant to the map’s purpose?
-
Can we reduce the map’s complexity?
-
What is the best way to convey the map’s message?
-
Data is the focus of the map. Is the eye is drawn to data before other places?
-
Title is an appropriate size/length and descriptive of map’s data?
-
Scale bar, North Arrow, Legend and Supplemental Information are adequate in size and do not detract from data.
-
Reference location data are included in the map (counties, cities, roads, etc.).
-
Symbology of data is logical: Low values coloured green, high values coloured red.
-
Supplemental Information includes: Author, date of creation, data source and Projection.
Features of bad maps:
-
Data is overwhelmed with other items on map;
-
Background colour detracts from data;
-
Other items detract from data (legend, scale bar, etc.);
-
Vague title or legend values (not logical);
-
No reference data.
Good practise: Have all your maps proofread by another person for clarity and design – just as you would for a written document.
11.5 Data Integration: Cyber Infrastructure
11.5.1 Computer Infrastructure (Cyber Infrastructure)
Computer infrastructure (Cyber infrastructure) is needed to organise the large quantity and diversity of data sources required for targeted surveillance. Cyber infrastructure helps (a) collect, manage and share data, (b) create pest risk models and analyses, (c) interpret data and risk products for national and local needs, and (d) manage the distribution of information products to end users including managers, field staff and stakeholders (Fig. 11.2) (Magarey et al. 2009; Barrett et al. 2010). A cyber infrastructure should be designed to integrate heterogeneous data sources for (a) tabular data such as phytosanitary records and trade data, pest observations, pest biology, meteorological station records, and crop statistics, and (b) cartographic data including all baseline information (bio-physical and administrative boundary maps) remote sensing based maps, and spatial modeling outputs (e.g., weather maps). A cyber infrastructure also supports people (e.g. inspectors, data managers, risk analysts, programme managers and industry or extension specialists) and their responsibilities through a role-based access system. Role-based access is defined by a user’s organisation, geographical responsibility (e.g. state, regional) and a user’s job title. Role-based access determines what data or pest programmes a user will see, and which on-line tools they will have access.
Examples of emerging cyber infrastructure include the USDA-APHIS iPHIS system, the NAPPFAST system (Magarey et al. 2009) and the Australian Biosecurity Information Network (ABIN) (http://www.abin.org.au/). Both iPHIS and NAPPFAST system support the integration of pest observations and risk maps. The main objective is to provide decision support data for government, industry and researchers.
Data sharing is one of the greatest challenges in the development of a cyber infrastructure. This challenge results from a lack or complexity of data-sharing protocols and standards especially between federal and state governments, between countries and with industry. The incorporation of industry into cyber infrastructure is especially important because industry may provide long-term funding.
11.5.2 Data
The most common data fields usually collected or recommended for collection (ISPM 6), in surveillance programmes are: Data source ID, dates of collection, identification and verification, location, pest (scientific name, Family/Order names and pest code if available), host (scientific name and host code if available), means of collection (e.g. attractant trap, soil sample, sweep net), sample and diagnostic information. Location information may include latitude and longitude, country, state, city, zip code/postcode, address and the owner’s contact information. Address and contact details may often not be included because it may violate privacy legislation. Pest information may include pest ID (or scientific name), phenological stage, quantity, and diagnostic determination. Survey and diagnostic information may also include diagnostic method, sample ID, laboratory ID, inspector ID and survey or trap method. Additional information may also be included as comments, e.g., nature of host relationship, infestation status, growth stage of plant affected, or found only in greenhouses; references (if any) and reports of pest occurrence on commodities.
11.6 Cooperative Agriculture Pest Survey (CAPS)
11.6.1 Introduction
In the USA, the post-border detection of exotic plant pests is the responsibility of the USDA, Animal Plant Health Inspection Service, Plan Protection and Quarantine (USDA-APHIS-PPQ) and its cooperators (Magarey et al. 2010). Here, CAPS, a joint Federal and State pest detection programme for exotic plant pests in the USA plays a major role (Wheeler and Hoebeke 2001).
CAPS has a multi-tiered structure with national and state level committees with representation from a diversity of organisations, including federal and state agencies, universities and industry. The first set of detection activities conducted by CAPS is targeted surveillance, also known as “Hotzone,” “Risk Point,” or “High Hazard” surveys (Wheeler and Hoebeke 2001). These surveys examine high-risk pathways based on the analysis of phytosanitary data including pest interceptions and emergency actions.
A second set of detection activities conducted by CAPS are pest and commodity surveys. CAPS committees select national and state survey targets from multiple sources including an annually prioritized list of about 50-60 pests. The prioritized list is selected from a larger PPQ pest list developed from sub-lists compiled from professional societies (e.g., American Phytopathological Society, Entomological Society of America) and from PPQ records. From this larger list, the prioritized list was developed using the Analytical Hierarchy Process (AHP, Saaty 1994). Expert opinion is used to answer questions regarding pest biology, pathways and impact for each pest. Pests are then prioritized by AHP using criteria weights selected by PPQ programme managers or other cooperators.
The CAPS 2011 pest list included 33 arthropods, 12 nematodes, 10 pathogens, 3 mollusks and 1 weed (Magarey et al. 2011). Some of the CAPS targets are selected at the generic rather than species level. Examples of CAPS national targets are the Giant African Snail (Achatina fulica Bowditch), the Summer Fruit Tortrix Moth (Adoxophyes orana (Fischer von Röeslerstamm)), and the False Columbia Root-knot Nematode (Meloidogyne fallax Karssen). Recently, CAPS began to implement commodity-based surveys that allow inspectors to sample for multiple pests during a single visit, potentially enhancing the survey process. The CAPS survey data are collected using the Integrated Plant Health Information System (iPHIS) and also archived in a central database known as the National Agricultural Pest Information System (NAPIS).
The USDA APHIS PPQ Center for Plant Health Science and Technology (CPHST) provides information on pest biology, survey methods, and risk analyses for many of these targets to help the CAPS programme cooperators plan surveys (Magarey et al. 2010). These surveys examine pathways identified as high risk on the basis of the analysis of phytosanitary data such as emergency action notifications or pest-interception data (USDA PESTID, formerly known as the Port Information Network, or PIN). Emergency Action Notifications are documents produced as part of an electronic reporting system used to enforce APHIS treatments and regulations.
When a high-risk pathway is identified, individual sites are ranked on the basis of data such as the type of establishment, phytosanitary history, logistical distance from the importation pathway, and sales data (Self and Kay 2005). For instance, targeted surveillance was carried out on ceramic importers and distributors in Miami, Florida (Beckwith 2004). After an analysis of past records of pest detections in Miami, 76 warehouses receiving tile shipments were selected for an in-depth survey. The survey resulted in the detection of new exotic arthropod species, including two new continental records and several new state and county records. The survey also found more than 20 genera from the Orders Coleoptera and Hemiptera (including Homoptera) that were not in the USDA PESTID database.
USDA APHIS PPQ’s Smuggling Interdiction and Trade Compliance (SITC) is another programme actively involved in targeted surveillance. APHIS created SITC in the mid-1990s in response to the growing volume of smuggled or improperly imported agricultural products entering the USA. The mission of the SITC programme is to identify the unlawful entry and distribution of prohibited products that may harbour exotic plant and animal pests. SITC was responsible for seizing and destroying more than 2.7 thousand tons of prohibited material in 2002 (USDA-APHIS-PPQ 2004).
11.6.2 CAPS: Looking Toward the Future
Two areas with potential for future enhancement of the CAPS programme are aimed at industry and the citizen scientist.
Industry has extensive data-gathering capabilities that have not been widely incorporated into general surveillance systems (Magarey et al. 2010; Whittle et al. 2009). For example, seed companies routinely collect data from activities including: (1) Pest scouting of research and seed production fields, (2) phytosanitary field inspections; and (3) disease diagnostic testing for their customers. Another potential source of industry surveillance data would be voluntary contributions from crop consultants. In the USA, thousands of crop consultants routinely scout agricultural fields. Although many industry observations would require validation, some industry diagnostic labs are now certified by national or international agencies.
Citizen Scientist is a term used for projects or ongoing programme of scientific work in which individual volunteers or networks of volunteers (many of whom may have no specific scientific training) perform or manage research-related tasks such as observation, measurement or computation. The use of citizen scientist networks often allows scientists to accomplish research objectives more feasibly than otherwise would be possible. A citizen scientist programme is potentially one of the most important cooperative survey programmes. Citizen scientists have been responsible for the first detection of many important exotic pests including Light Brown Apple Moth (Epiphyas postvittana Walker) and the Asian Longhorned Beetle (Anoplophora glabripennis Motschulsky) (Chap. 16). In the case of LBAM, retired UC Berkeley Professor of Entomology (a moth taxonomist) first detected LBAM in his Berkeley backyard on July 19, 2006. In the case of Asian Longhorned Beetle, beetles were first found by an unsuspecting landlord of an apartment building in Greenpoint area of Brooklyn, New York in the USA during 1996 (Sect. 16.2).
A citizen scientist programme could be created using existing observer networks, professional societies and school students to collect data on exotic pests. An example of an observer network that might be co-opted for exotic pest detection is the National Phenological Network (http://www.usanpn.org). Examples of professional societies whose members might cooperate include the Entomological Society of America and the American Phytopathological Society. APHIS currently is investigating the use of citizen science programmes for Asian Longhorned Beetle. Citizen scientist programmes might target high-risk pests or high-risk commodities such as specialty crops. Recently, we noted that specialty crops in urban areas (with high concentrations of potential participants) are at high risk of introduction to exotic pests (Colunga-Garcia et al. 2010a, b). A cyber infrastructure, described earlier in the chapter, can provide the information technology to build a system for collecting, integrating and analyzing citizen scientist data.
11.7 Conclusions
This chapter has introduced many methods and ideas concerning Surveillance and biosecurity, but it has only scratched the surface in a rapidly changing field. Even as this chapter was being written, there were advances in “sniffer” technologies, databases that allow real-time tracking of commodities, and cloud-based platforms that can deliver modeling applications into a port or field for better monitoring of resources. These can rapidly change how an organisation works. Many of the changes are technology based, and that will continue to be the case into the future. With a general worldwide trend toward tighter governmental budgets, increasing global trade, and climate change disrupting traditional patterns, technology offers a hope to allow countries to keep up with the increasing pressures on their biosecurity organisations.
References
Baker AC (1939) The basis for treatment of products where fruitflies are involved as a condition for entry into the United States, vol 551, Circular. U.S. Department of Agriculture, Washington, DC
Baker RHA (2002) Predicting the limits to the potential distribution of alien crop pests. In: Hallman GJ, Schwalbe CP (eds) Invasive arthropods in agriculture. Science Publishers, Enfield, pp 208–241
Beckwith J (2004) A survey of tile warehouses in Florida. US Department of Agriculture, Animal and Plant Health Inspection Service, Plant Protection and Quarantine, Cooperative Agriculture Pest Survey, Riverdale
Barrett S, Whittle P, Mengersen K, Stoklosa R (2010) Biosecurity threats: the design of surveillance systems, based on power and risk. J Environ Ecol Stat 17:503–519
Biosecurity Australia (2009) Report of the assessment of northern China’s fruit fly pest free areas: Hebei, Shandong and Xinjiang. Online at http://bit.ly/cCYtCe. Biosecurity Australia, Canberra
BRS (2007) Multi-criteria analysis shell, MCASS-S, Version 1.0, User Guide. Australian Government, Bureau of Rural Sciences. Canberra. Http://www.brs.gov.au
Cameron AR, Baldock FC (1998) A new probability formula for surveys to substantiate freedom from disease. Prev Vet Med 34(1):1–17
Colunga-Garcia M, Magarey RD, Haack RA, Gage SH, Qi J (2010a) Enhancing early detection of exotic pests in agricultural and forest ecosystems using an urban gradient framework. Ecol Appl 20:303–310
Colunga-Garcia M, Haack RA, Magarey RD, Margosian ML (2010b) Spatial establishment patterns of exotic forest insects in urban areas in relation to urban tree cover and propagule pressure. J Econ Entomol 103:108–118
Evans G, McMaugh T (2005) Surveying for plant pests: ISPM Terminology. Association of South East Asian Nations. http://www.aseanet.org/events/bogor_sept2005/sps/Relevant%20Documents/Surveying%20Plant%20Pests-ISPM%20Guidelines%20(G.%20Evans).doc
Evans JR, Olson DL (1998) Introduction to simulation and risk analysis. Prentice-Hall International, Upper Saddle River
Froud KJ, Oliver TM, Bingham PC, Flynn AR, Rowswell NJ (2008) Passive surveillance of new exotic pests and diseases in New Zealand. In: Froud KJ, Popay AI, Zydenbos SM (eds) Surveillance for biosecurity: pre-border to pest management. New Zealand Plant Protection Society, Paihia
Gottwald TR, da Graça JV, Bassanezi RB (2007) Citrus Huanglongbing: the pathogen and its impact. Online. Plant Health Prog doi:10.1094/PHP-2007-0906-01-RV
Hix R, Toscano N, Gispert C (2003) Area-wide management of the glassy-winged sharpshooter in the Temecula and Coachella Valleys. In: Tariq MA, Oswalt S, Blincoe P, Spencer R, Houser L, Ba A, Esser T (eds) Proceedings of CDFA Pierce’s disease research symposium, 8–11 December 2003, Copeland Printing Sacramento, Coronado, pp 292–294
IPPC (1997) ISPM No. 6, Guidelines for surveillance. International Plant Protection Convention. FAO-UN, Rome, p 8
IPPC (1999) ISPM No. 9, Guidelines for pest eradication programmes (1998). International Plant Protection Convention, FAOUN, Rome, 10 pp
IPPC (2009a) International Standards for Phytosanitary Measures (ISPMs) 1-32. International Plant Protection Convention. FAO-UN, Rome
IPPC (2009b) Explanatory document on International Standards for Phytosanitary Measures (ISPMs) 31. International Plant Protection Convention. FAO-UN, Rome
Isard SA, Russo JM, Ariatti A (2007) The Integrated Aerobiology Modeling System applied to the spread of soybean rust into the Ohio River valley during September 2006. Aerobiologia 23:271–282
Magarey RD, Borchert DM, Engle JS, Colunga-Garcia M, Koch FH, Yemshanov D (2011) Risk maps for targeting exotic plant pest detection programs in the United States. EPPO Bull 41:46–56
Magarey RD, Dolezal WM, Moore TJ (2010) Worldwide monitoring systems. The need for public and private collaboration. In: Gisi U et al (eds) Recent developments in management of plant diseases, 349 Plant Pathology in the 21st Century 1. doi:10.1007/978-1-4020-8804-9_24, Springer Science Business Media B.V.
Magarey RD, Colunga-Garcia M, Fieselmann D (2009) Plant biosecurity in the United States: roles, responsibilities and information needs. Bioscience 59:875–883
Martin PAJ, Cameron AR, Greiner M (2007) Demonstrating freedom from disease using multiple complex data sources: 1: a new methodology based on scenario trees. Prev Vet Med 79:71–97
Saaty TL (1994) Fundamentals of decision making and priority theory with the analytic hierarchy process. RWS Publications. Pittsburgh, 527 pp
Self M, Kay C (2005) Development of methodology for targeted post border surveillance for exotic pest incursions. Paper presented at the workshop on post-border surveillance for exotic pests of plants hosted by the Department of Agriculture Food and Forestry; 7–8 June 2005, Canberra
USDA (2002) Alternatives for quarantine security (Agricultural Research Service, United States Department of Agriculture). http://www.ars.usda.gov/is/np/mba/jan97/secure.htm. Accessed 26 Sept 2008
USDA-APHIS-PPQ (2004) Smuggling interdiction and trade compliance program (11 November 2007 www.aphis.usda.gov/lpa/pubs/fsheet_faq_notice/fs_phsouthwestsitc.html)
Venette RC et al. (2010) Pest risk maps for invasive alien species: a roadmap for improvement. Bioscience 60:349–362
Wheeler AG, Hoebeke ER (2001) A history of adventive insects in North America: their pathways of entry and programs of entry and programs for their detection. In: Detecting and monitoring invasive species, plant health conference. USDA-APHIS, Raleigh, pp 3–15
Whittle P, Barrett S, Jarrad F, Murray J, Mengersen K, Hardie D, Nietrzeba A, Stoklosa R, Parkes J, Majer J (2009) Design of detection surveillance program for non-indigenous species of terrestrial invertebrates, plants and vertebrates on Barrow Island. Report to Chevron Australia Pty Ltd. Cooperative Research Centre for National Plant Biosecurity, Bruce
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2014 Springer Science+Business Media Dordrecht (outside of the USA)
About this chapter
Cite this chapter
Kalaris, T. et al. (2014). The Role of Surveillance Methods and Technologies in Plant Biosecurity. In: Gordh, G., McKirdy, S. (eds) The Handbook of Plant Biosecurity. Springer, Dordrecht. https://doi.org/10.1007/978-94-007-7365-3_11
Download citation
DOI: https://doi.org/10.1007/978-94-007-7365-3_11
Published:
Publisher Name: Springer, Dordrecht
Print ISBN: 978-94-007-7364-6
Online ISBN: 978-94-007-7365-3
eBook Packages: Biomedical and Life SciencesBiomedical and Life Sciences (R0)