Abstract
Recently, there are many MNs (Mobile Nodes) are efficient and stable when they move to operate with variety schemes have emerged. Recently, there is a growing interest about PMIPv6 (Proxy Mobile IPv6) and, this paper is the based on the way to mobility support system will stand on the basis from PMIPv6 network to NEMO (NEtwork MObility). PMIPv6 is mobility support system from single domain, it actual network is composed with nested in a multiple domain structural system. The proposed scheme in the domain of two or more, the LMA (Local Mobility Anchor) communication between LMA and MAG (Mobile Access Gateway) of movable domain can increase performance in terms of handover delay and signaling.
Access provided by CONRICYT-eBooks. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The current mobile network wants the internet connection which is not disconnected even when it is moved to a new region. The MIPv6 [1] is the protocol which represents IP layer at the IPv6 network. But it is limited to apply it in practice, because the amount of usage increases in wireless section due to the signaling between mobile terminals and AR (Access Router), and because complicated standardized specification must be realized at the terminals. As these problems emerge, the NETLMM working group of IETF was newly established, and then the standardization of the network-based mobility protocol is in process.
The network-based mobility protocol contains typically the NBS (NEMO Basic Support) protocol [2]. The MR (Mobile Router) of the NBS carries out the AR role. If the MN is in the home network, it will gain the IP address which is called HoA (Home Address) by the HA (Home Agent). This IP maintains the same address even when it moves out of the same domain to a new region. If the MR moves to a new region, the MR receives a new network prefix, on whose base a new address called as CoA (Care-of Address) is generated. Then the BU (Binding Update) message which contains the CoA is sent to the HA, so that the connection with the HA is maintained. The HA sends BA (Binding Acknowledgement) message to the MR as the response which means it receives the BU message. The MNN (Mobile Network Node) in the region of the MR doesn’t pass through any procedure because the MR carries out the signaling. But, the NBS also is the host-based mobility management protocol like the MIPv6. In the case of the host-based management protocol, when the MR moves, the MNN adjacent to it carries out the signaling, and consequently the performance delay is caused. Thus, recently network-based protocol is being paid attention. The typical protocol of it is the PMIPv6 (Proxy Mobile IPv6) [3,4,5].
This paper uses the scheme which applies the NEMO to the PMIPv6 domain [6]. The MN of the existing PMIPv6 first passes through the MAG(Mobile Access Gateway) and communicates with external nodes, and here the MR is placed in the middle. One MAG has a lot of MNs (Mobile Nodes). Here the MR regroups again a lot of MNs, and carries out vicariously the unnecessary signaling between the MN and the MAG. But, the current PMIPv6 doesn’t support the whole area mobility of the host. If the MR moves to other domain, the subsequent handover delay occurs.
This paper, to compare the performances of domains, compared and analyzed the NBS, Light-NEMO (PMIPv6 which supports the NEMO), and proposed scheme. This paper first presents signaling cost in domain, packet tunneling cost, and handover delay, and analyzed the performances in terms of signaling cost between domains, packet tunneling cost, and handover delay. As the result of the analysis, in terms of signaling cost, handover delay, and ‘in domain’ and ‘between domains,’ the proposed scheme generates less cost than the NBS and the Light-NEMO. In terms of packet tunneling cost, the proposed scheme is same as the Light-NEMO, but less than the NBS.
This paper describes the protocol related to the Sect. 2. And Sect. 3 describes the proposed scheme, Sect. 4 analyzes the performance of the proposed scheme. Finally, Sect. 5 draw conclusions.
2 Related Work
NEMO (NEtwork MObility) is a technology that can provide a seamless service on the network connected to the MNNs (Mobile Network Nodes). NEMO is performed as to each of the terminals belonging to the operation associated with the mobility in MNNs, the router that is dedicated to the MNNs as a representative to the MR. Signaling that the existing terminals perform direct MR can use the network because they do instead is more efficient [2,3,4,5,6,7].
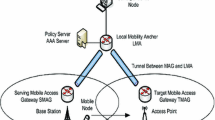
PMIPv6 of the mobile node from the mobility management domain is managed by a PMIPv6. In the terminal domain are subject to the control of the LMA(Local Mobility Anchor) and MAG. LMA performs the role of the home agent to the mobile node. This is placed in position within the domain gateway, the home network prefix allocated to it and also plays a role to send to the mobile node. MAG is responsible for the connectivity and routing for the network of the mobile node. When the mobile node is connected to the access router, rather than by using the information of the mobile node to the LMA and the authentication and connection [8].
NEMO is the support PMIPv6 domain, LMA has a binding list, including the HNP and MNP of the MR. Therefore, LMA is able to delete the record in the other MAG to move the address relocation and an existing area of the MR. When MR move to a new MAG in the existing area MAG zone, the new MAG is sent to the LMA through PBU message. LMA is the binding update list by using the existing registered information such as HNP and MNP. MAG is newly created through a PBA message transmitted to the LMA, and updates the list information on the MR. Because HNP is a permanent address, MR is continued to use the existing information even if the move to the new MAG.
3 Cost-Effective Inter-LMA Domain Handover Scheme in NEMO-PMIPv6 with NEMO Supporting
This paper purposes that the proposed scheme improves the performance regarding handover delay due to movement of the MR in more than two domains. The LMA of the PMIPv6 manages one domain. If the number of domains is two, the domains, which have their own LMA different from each other, cannot communicate with each other because their network bandwidths are different each other.
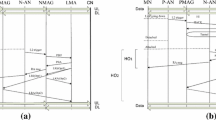
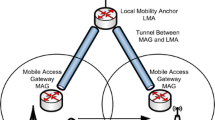
As in Fig. 1, if the MR moves to a new domain, the LMA gains the information of the MR, and carries out the binding list update to it. After that, the MAG of corresponding area can recognize the MR. This paper proposes the improvement of performance for handover delay by reducing the communication process, when the MR moves out of the PMIPv6 domain which is different from each other to a new PMIPv6. It is assumed that when the MR is about to move to the MAG3 of other PMIPv6, the MAG2 recognizes the information of it as the L2 trigger which contains addresses of the MAG3 and the LMA when the MR moves to a new domain. The MAG1 transmits the DeReg-PBU message to the LMA1, and then the LMA1 in this process knows of the PMIPv6 domain which the MR will move to and the IP address of the MAG3. If the MR moves to a new domain, it must exchange the information with the LMA. But by the scheme proposed by this paper, because the LMA1 knows the address of the MAG3, it doesn’t pass through the LMA2, and then immediately exchanges the information of the MR. the LMA1 and the MAG3 take over the communication process between the LMA1 and the LMA2. Figure 2 shows the structure of a data packet tunnel between LMA1 and MAG3.
If the MR in the PMIPv6 domain which supports the NEMO moves to the new MAG2, the MAG2 gains the information of the MR (MR-ID, HNP, MNP) through the LMA which is responsible for the basic data communication. This paper proposes that before the proposed scheme, if the MR moves in one PMIPv6 domain, the communication is to be carried out between the MAGs without passing through the LMA. It is assumed that when the MR moves to the MAG2, the L2 trigger is generated. Now, the MR can gain the address information of the MAG2, and delivers the address of the MAG2 to the MAG1. The MAG1 sends to the LMA the DeReg-PBU message which contains the addresses of the MR-ID and the MAG2, so that it requests to delete the information of the MR in the existing MAG1. The LMA as the response message of the DeReg-PBU message sends the DeReg-PBA message which contains the MR-ID, HNP and MNP, and updates the list of the MAG2-MR. It is assumed that the MAG1 knows of the address of the MAG2 from the MR by the L2 trigger. And then the MAG1 sends to the MAG2 the HI (Handover Initialize) message which contains the information of MR-ID, address of MAG2, and MR-HNP. This is as similar as the stage which corresponds to the PBA message which the existing LMA sends to the MAG2. Then, the MAG2 as the response message of reception transmits the HAck (Handover Ack) message. In the process, the MAG2 knows of the information about the MR. The MAG2 has the buffering process. Till the MR is connected to a new domain through the buffering, the MAG2 stores the information of the HI message, and sends to the LMA2 the Pre-PBU message which beforehand has the information of the MR. The LMA2 as the response to it responds with the Pre-PBA message. Not long after the MR is linked down to the existing MAG1, it is linked up at the MAG2. And the two-way tunnel between the MAG1 and the MAG2 is formed. After the certification procedure through the certification server, the MR transmits the RS message to the MAG2, and the MAG2 transmits to the MR the RA message which contains the HNP and the MNP. The MR forms addresses by using the HNP, and advertises the MNP to the mobile nodes by the broadcasting method.
This paper proposes the scheme that the method by which the communication is operated between the MAGs in one PMIPv6 domain is improved and developed to the method by which the communication is operated in two domains without passing through the LMA, as shown in Fig. 3. It is assumed that when the MR in the MAG2 of the LMA1 moves to the MAG2 of the LMA2, the L2 trigger is generated in the MR. The MAG2 acquires the information of the MR-ID and the LMA2 through this L2 event. The MAG1 transmits to the LMA1 the DeReg-PBU message which contains the LMA2 address which is transmitted from the MR, the MAG2 address and the MR-ID. The LMA1, as the response to receive the DeReg-PBU message, transmits to the MAG1 the DeReg-PBA message, and deletes the information of the MR from the binding list. The LMA1 knows about the address of the MAG2. And the LMA1 sends to the MAG2 the HI which contains the MR-ID and the HNP. The MAG2, as the response to receive the HI, sends the HAck message. The MAG2 transmits to the LMA2 the Pre-PBU message which contains the MR-ID, and registers the information of the LMA2-MR in the binding list. The LMA2, as the response to the PBU message, sends so the MAG2 the Pre-PBA which contains the MR-ID, the HNP and the MNP. Then it is linked up to the MR, and passes through the certification procedure by the certification server in the domain. After the certification, the MR transmits the RS message to the MAG2, and the MAG3 sends to the MR the RA message which contains the HNP and the MNP. The MR forms the address by using the HNP, and advertises the MNP to the mobile nodes by the broadcasting method.
4 Performance Analysis
In this section, the NBS, Light-NEMO and our scheme will be compared and analyzed. Signaling, packet tunneling cost, handover delay in respect will present numerical results.
In relation to authentication and access of the MR in this experiment had will assume the same value. In this paper, we’ll learn why the handover latency values IP layer traffic value. The following notation is used in the proposed performance analysis.
-
A session connection for the MR is estimated utilizing a Poisson distribution. Therefore, the continuous time of the session connection MR is used for the \(\lambda _s\) an exponential distribution.
-
E(S) refers to the length of the session MR and it’s determined by the number of the fixed packet size.
-
1/\(\mu _{_L}\) is used, which means the density distribution of time to be connected to MR. The density function is using the
 means a Laplace transform of the
means a Laplace transform of the  .
. -
\(N_n\) is the number for the link to move the MR. \(P_r[N_L=K]=a(K)\) is the probability for the moves to be MR, the session is maintained for K links. \(S_\sigma \) refers to the SMR containing \(\lambda _s/\mu _L\). The session is \(a(0)=1-(1-f^*_L(\lambda _s))/S_\sigma \), given by \((k\ge 1)=1/S_\sigma (1-f^*_L(\lambda _s))^2(f^*_L(\lambda _s))^{k-1}\). The holding time is assumed as the exponential distribution time to link with MR, \(1/\mu _{_L}\).
-
Laplace transform of the \(f_{L(t)}\) is represented as \(f^*_L(\lambda _s)=e^{-st}\prod \mu _{_L}e^{{-\mu Lt}}dt\).
-
\(D_P\) which means a service packet delay, packet service delay means the sum of the processing delay and a transmission delay of the entity (MR, AR/MAG, \(HA_{MR}/LMA_{MR}\)). Packet services will delay applying the M/M/1 queuing model. The processing procedure will assume that there is a packet loss. \(1/\mu _p\) refers to the average packet transmission time, \(\lambda _P\) means the average arrival rate. \(D_P\) is given by \(1/(1-p)u\). (Especially, \(p=p/\mu _p\))
-
Enlarge delay also should be considered. The enlarge delay of the link \(D_a\) depends on the physical distance by an entity d and a wired link \(\psi \) speed. \(D_a\) is given by \(d/\psi \). Enlarge delay for a wireless \(D_B\) is assumed to be 1us. Wired link is not nearly failed during message transmission, believed to occur during the message transmission on the radio link fails.
Table 1 describes The notations for the performance analysis.
4.1 Cost Analysis
Signaling cost is given by the signaling occurring in the handover for the mobile registration process. On the other hand, the packet is sent from CN to MR, the tunneling cost, is determined by the data packet [9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26].
\(C^{(PRO)}_{LU}\) is the time of signaling cost for our proposed scheme.
-
If within a domain
$$\begin{aligned} \begin{array}{crl} C^{(PRO)}_{LU}&{}=&{}[i\displaystyle \sum ^\infty _{i=0}a(i)\times LU^{(PRO)} \\ &{}=&{}[\displaystyle \sum ^\infty _{i=1}\frac{i}{S\sigma }(1-f^*_L(\lambda _s))^2(f^*_L(\lambda _s))^{i-1}]\times LU^{(PRO)}\\ &{}=&{}T_w \end{array} \end{aligned}$$(1) -
If between domains
$$\begin{aligned} \begin{array}{crl} C^{(PRO)}_{LU}&{}=&{}[i\displaystyle \sum ^\infty _{i=0}a(i)\times LU^{(LM)} + H_{LMA1-MAG2}(Q_{req}+Q_{res})\\ &{}=&{}T_w+H_{LMA1-MAG2}(Q_{req}+Q_{res}) \end{array} \end{aligned}$$(2)
\(LU^{(PRO)}\) is the cost of location updates from the proposed scheme. In the proposed scheme, since \(LU^{(PRO)}\) to update the location of the MR in advance, HI/HAck message transmission process include only \(T_w\).
\(C^{(PRO)}_{PT}\) is the cost per packet tunneling in the proposed scheme. It is calculated as follows:
4.2 Handover Delay Analysis
In Fig. 4, Light-NEMO in the Intra Domain handover procedure, shows the time required in each stage of the diagram. \(L^{(LM)}_{(HO)}\) is one of the Light-NEMO handover delay. This analysis is similar with the formula in NBS. The result shows the following:
-
If within a domain
$$\begin{aligned} L^{(LM)}_{HO}=T_{L2}+T_{AU}+T_{WRS}+T_{RS}+T^{(LM)}_{LU}+T^{(LM)}_{P} \end{aligned}$$(5)\(T_{RS}\) shows the following:
$$\begin{aligned} T_{RS}=\frac{P_fH_{MR-MAG}(D_P+D_E)}{1-P_f} \end{aligned}$$(6)
In the proposed handover procedure, MAG sends the PBU for the handover messages on behalf of the registered MR. \(LMA_{MR}\) sends a MR with the PBA message and the data packets. \(T^{(LM)}_{LU}+T^{(LM)}_{P}\) represents the following:
\(T_{PBA}\) is the arrival delay of the PBA message directed to the MR in \(LMA_{MR}\). \(T_{PBA}\) and \(T^{(LM)}_P\) is calculated as follows:
\(\tau \) affects only tunnel between the proposed technology MAG and \(LMA_{MR}\).
– If within a domain
The handover timing diagram for the proposed scheme is shown in Fig. 5.
Finally, the equation of inter domain handover is equal to that of intra domain.
4.3 Numerical Results
The signaling costs are given in Fig. 6. Value of \(N_L\), \(P_f\) is 0.1 or 0.5 when, we will assume one kinds from eight kinds. The proposed scheme is numerically when viewed as a result of rising costs because of location update signaling is likely twice two times higher than the NBS.
Figure 7 shows the packet tunneling costs for three schemes. Packet tunneling cost is proportional to E(S). NBS only affected by the \(P_f\). The proposed scheme is less than the NBS in terms of the packet tunneling cost.
Figure 8 was compared to handover performance in comparison to the proposed method and the comparative protocol. From the graph, it shows the high packet loss ratio, such as the retransmission of the MR from the NBS.
Table 2 summarizes parameters used for the mathematical evaluations [9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26].
5 Conclusion
This paper proposed the scheme that when the MR moves between two domains which support the NEMO, not the communication between the LMAs but the communication between the LMA and the MAG is to be operated. While the existing studies have intensively dealt with the handover in one domain, it is the key of this paper to enable the performance improvement from the perspective of the delay and signaling in a case of handover between domains. Consequently, it has been demonstrated that in comparison with the PMIPv6 which supports the NBS and the NEMO which are widely known, the proposed scheme shows better performance. In the future, the additional paper is going to be conducted to propose the possibility to reduce the delay time of the handover.
References
Johnson, D., Perkins, C., Arkko, J.: Mobility Support in IPv6. RFC 3775 (2004)
Devarapalli, V., Wakikawa, R., Petrescu, A., Thubert, P.: Network Mobility: NEMO, Basic Support Protocol. RFC 3963 (2005)
Lee, J.H., Han, Y.H., Gundavelli, S., Chung, T.-M.: A comparative performance analysis on hierarchical mobile IPv6 and proxy mobile IPv6. Telecommun. Syst. 41(4), 279–292 (2009)
Lee, J.H., Ernst, T., Chung, T.-M.: Cost analysis of IP mobility management protocols for consumer mobile devices. IEEE Trans. Consum. Electron. 56(2), 1010–1017 (2010)
Gundavelli, S., Leung, K., Devarapalli, V., Chowdhury, K., Patil, B.: Proxy Mobile IPv6. RFC 5213 (2008)
Lim, H.-J., Kim, M., Lee, J.H., Chung, T.-M.: Route optimization in nested NEMO: Classification, evaluation and analysis from NEMO fringe stub perspective. IEEE Trans. Mobile Comput. 8(11), 1544–1572 (2009)
Muhanna, A., Khalil, M., Gundavelli, S., Chowdhury, K., Yegani, P.: Binding Revocation for IPv6 Mobility. RFC 5846 (2010)
Choi, J.Y., Cho, Y., Lee, T., Cho, J.D., Jeong, J., Roh, S.S., Kim, H.T.: Cost analysis of integrated HIP-PMIPv6 handoff scheme in multicasting-based mobile networks. Adv. Sci. Lett. 21(3), 321–327 (2015)
Jang, H., Song, B., Cheong, Y., Jeong, J.: Sensor-based global mobility management scheme with multicasting support for building IoT applications. Adv. Intell. Syst. Comput. 570(5), 289–299 (2017)
Cho, C., Choi, J.Y., Jeong, J., Chung, T.M.: Performance analysis of inter-domain handoff scheme based on virtual layer in PMIPv6 networks for IP-based internet of things. PLoS ONE 12(1), e0170566 (2017)
Im, I., Jeong, J.: Cost-effective and fast handoff scheme in proxy mobile IPv6 networks with multicasting support. Mobile Inf. Syst. 10(3), 287–305 (2014)
Jeong, J., Cho, C., Kang, J.J.: Hashing based lookup service in mobile ad-hoc networks with multi-hop stretchable clustering. Int. J. Sens. Netw. 15(3), 183–197 (2014)
Cho, C., Kang, J.J., Jeong, J.: Design and performance analysis of a dynamic-paging AAA mobility management scheme for PMIPv6based wireless networks. Int. J. Sensor Netw. 15(4), 214–222 (2014)
Cho, C., Choi, J.Y., Cho, J.D., Jeong, J.: Design and performance analysis of a cost-effective proxy-LMA mobility management scheme in IP-based mobile networks with global mobility support. Int. J. Ad Hoc Ubiquitous Comput. 21(4), 273–289 (2016)
Song, B., Shin, J., Kwon, Y., Jeong, J., Kim, Y.: On bandwidth-efficient handoff scheme for PMIPv6 networks. Procedia Comput. Sci. 94, 152–159 (2016)
Song, B., Kwon, Y., Jang, H., Jeong, J., Cho, J.-D.: On efficient SC-based soft handoff scheme in proxy mobile IPv6 networks. In: Gervasi, O., Murgante, B., Misra, S., Rocha, A.M.A.C., Torre, C., Taniar, D., Apduhan, B.O., Stankova, E., Wang, S. (eds.) ICCSA 2016. LNCS, vol. 9787, pp. 251–262. Springer, Cham (2016). doi:10.1007/978-3-319-42108-7_19
Jeong, J., Cho, J.-D., Choi, Y., Kwon, Y., Song, B.: On multicasting-based fast inter-domain handover scheme in proxy mobile IPv6 networks. In: Huang, D.-S., Han, K., Hussain, A. (eds.) ICIC 2016. LNCS, vol. 9773, pp. 494–505. Springer, Cham (2016). doi:10.1007/978-3-319-42297-8_46
Song, B., Shin, J., Jang, H., Lee, Y., Jeong, J., Cho, J.-D.: On cross-layer based handoff scheme in heterogeneous mobile networks. In: Huang, D.-S., Han, K., Hussain, A. (eds.) ICIC 2016. LNCS, vol. 9773, pp. 482–493. Springer, Cham (2016). doi:10.1007/978-3-319-42297-8_45
Choi, J.Y., Jeong, J.: Design and performance analysis of cost-optimized handoff scheme based on fuzzy logic for building smart car IoT applications. Information (Japan) 18(10), 4339–4345 (2015)
Jang, S., Jeong, J.: Cost-effective approach inter-LMA domain management and distributed mobility control scheme in proxy mobile IPv6 networks. Inf. Syst. 48, 248–261 (2015)
Song, M., Cho, J.D., Jeong, J.: Optimization of authentication cost based on key caching for inter-MME handover support. Information (Japan) 18(3), 1095–1100 (2015)
Song, B., Shin, J., Kim, S., Jeong, J.: On PMIPv6-based mobility support for hierarchical P2P-SIP architecture in intelligent transportation system. In: Proceedings of the Annual Hawaii International Conference on System Sciences, pp. 5446–5452 (2015)
Song, M., Cho, J.D., Jeong, J.: Multicasting service for Inter-Domain mobility management scheme in sensor-based PMIPv6. Information (Japan) 18(3), 1073–1078 (2015)
Choi, J.Y., Yang, S., Jeong, J.: On QoS provisioning based on user mobility patterns for Proxy mobile IPv6 networks. In: Park, J., Stojmenovic, I., Jeong, H., Yi, G. (eds.) Computer Science and its Applications. Lecture Notes in Electrical Engineering, vol. 330, pp. 983–989. Springer, Heidelberg (2015)
Cho, C., Kang, J.J., Jeong, J.: Performance analysis of DNS-assisted global mobility management scheme in cost-optimized proxy mobile IPv6 Networks. Inf. Syst. 48, 226–235 (2015)
Song, M., Cho, J.D., Jeong, J.: Global mobility management scheme for seamless mobile multicasting service support in PMIPv6 networks. KSII Trans. Internet Inf. Syst. (TIIS) 9(2), 637–658 (2015)
Acknowledgments
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (NRF-2016R1D1A1B03933828). Corresponding author: Jongpil Jeong.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Park, S., Um, C., Jeong, J. (2017). On Cost-Effective Inter-LMA Domain Handover Scheme in NEMO-PMIPv6 Networks. In: Younas, M., Awan, I., Holubova, I. (eds) Mobile Web and Intelligent Information Systems. MobiWIS 2017. Lecture Notes in Computer Science(), vol 10486. Springer, Cham. https://doi.org/10.1007/978-3-319-65515-4_22
Download citation
DOI: https://doi.org/10.1007/978-3-319-65515-4_22
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-65514-7
Online ISBN: 978-3-319-65515-4
eBook Packages: Computer ScienceComputer Science (R0)





 means a Laplace transform of the
means a Laplace transform of the  .
.



