Abstract
The deployment of different types of wireless technologies led to additional challenges to the issue of mobility management in next generation wireless networks. In addition to the regular movement of the mobile users in a heterogeneous environment, users’ demand for more real time services results in more handover complexity. Even though the network-based proxy mobile IPv6 (PMIPv6) is considered a favorable protocol for mobility management and the IEEE 802.21 media independent handover (MIH) framework designed to support seamless handover in heterogeneous networks, these protocols, each one separately, fails to provide seamless handover procedure for time sensitive applications in heterogeneous wireless networks. Therefore, several works have been done to integrate the network-based PMIPv6 with the capabilities of MIH to obtain an enhanced solution. In this paper, we reviewed the PMIPv6 and MIH integration schemes in the literature and we categorized them into six schemes based on the signals or network entities modifications. Also, we provide a comparative analytical evaluation for handover procedures of these schemes in terms of signaling cost, total handover latency, and packet loss. Based on the features and analysis, the integration with network is the best solution that to be considered.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The requirements of reliable mobile communication systems led to rapid developments in wireless communication technologies and gave the motivation to innovate many wireless networks. Nowadays, most of the mobile gadgets are supported with multiple wireless interfaces to operate with various wireless technologies like wireless fidelity (WiFi), worldwide inter-operability for microwave access (WiMAX), universal mobile telecommunications systems (UTMS) and long term evaluation (LTE) [1].
To provide anytime anywhere wireless connection to mobile users, the next generation wireless networks (NGWN) are moving to become all IP-based networks to support ubiquitous wireless environment by interconnecting different wireless access technologies in a heterogeneous infrastructure [1].
As the heterogeneous networks becomes larger and users demand for higher data traffic with quality of services, the mobility management solutions has increasingly become an important area of interest to provide seamless handover mechanisms not only for simple mobile data, but also for real-time and multimedia applications such as voice over IP (VoIP), video conferencing, IPTV, and internet gaming [2].
One of the most representative efforts of the mobility management is the host-based MIPv6 protocol standardized by internet engineering task force (IETF). However, this protocol suffered from several problems such as high signaling cost, long handover delay, critical packet loss, MN power consumption, advanced MN processing ability and the requirement to change protocol stack. Therefore, IETF introduced the network-based Proxy MIPv6 to overcome the host-based problems by supporting mobility management without host involving in any mobility signaling [3–5].
Since the handover mechanism has become more complex, the PMIPv6 failed to insure the required performance due to the network heterogeneity; therefore, the mobility management requires comprehensive standards to provide seamless handover across NGWN. The IEEE 802.21 addresses this issue by providing a media independent handover (MIH) framework which identifies the services and structure to enable seamless handover mechanism in heterogeneous wireless networks [6]. The ultimate purpose of IEEE 802.21 MIH is to provide mobility mechanisms independent of media by offering useful information about link layer and candidate networks [7, 8].
There are several approaches have been proposed to integrate the network-based PMIPv6 with MIH framework to optimize the handover performance. Some of these proposals give the theoretical part only, while other works supported by analytical and simulation work.
In this paper, we present a survey on PMIPv6 and IEEE 802.21 MIH integration schemes and explained their operations in detail with summary of most important features. A comparative performance analysis of these schemes in terms of signaling cost, handover latency, and packet loss are presented. Based on the overall results and features, the scheme with network only functionalities can be considered as the best solution because it excludes the MN from participation in any mobility related signaling, reduces wireless handover delay, provides the required quality of service in heterogeneous environment and matched with trend of network based mobility management protocols.
The remainder of this paper is organized as follows: Sect. 2 presents related works. Section 3 provides a brief overview of the PMIPv6 protocol and MIH framework. In Sect. 4, we explain in detailed the integration of PMIPv6 and MIH approaches in the literature and we classify them into six categories based on the signals or network entity modification. We present a comparative performance analysis and evaluation of these approaches in Sect. 5. Section 6 concludes this paper.
2 Related Works
In this section, we present and critically analyze related work in mobility management.
Authors in [9] have studied the performance of various mobility management protocols in terms of average hop delay, wired and wireless delay, and binding update delay using simple numerical analysis. However, authors have not considered other metrics such as signaling cost and packet loss. Authors in [10] have surveyed the host-based MIPv6 and the network-based Proxy MIPv6 protocols with their extensions of Fast MIPv6 and Hieratical MIPv6 and Fast PMIPv6 with detailed signaling of each protocol. Although the analysis in terms of handover latency and signaling cost has been presented, but this survey did not considered other metrics such as wireless delay and packet loss analysis
In [11], authors have explained the main desirable features and the key strengths of PMIPv6 through qualitative and quantitative analyses of the host-based and the network-based mobility management protocols. However, this study limited to wireless delay and handover latency and did not considered the signaling cost and packet loss. Authors in [12] have surveyed the mobility management services with their techniques, strategies, and protocol categories. Even though the authors have identified and discussed several issues and challenges facing the mobility management protocols by providing comparative summary, they did not provide any performance analysis for these protocols. In [13], authors have surveyed the PMIPv6 handover procedures and proposed approaches including the predictive and reactive Fast PMIPv6 and PMIPv6 with IEEE 802.21 framework accompanied with discussion about points of weaknesses, but the authors presents only one scheme of integration of fast PMIPv6 with MIH.
Authors in [14] have presented an overview of the IEEE 802.21 MIH framework specifications to enable seamless inter-technology handover. Authors in [15] have provided a survey of vertical handovers with MIH framework and classify them into two categories which are MIPv4 and MIPv6 with the comparison of their performances and characteristics. However, the authors focus on MIPv4 and MIPv6 and they did not present a comparative performance between host-based and network-based protocols. In [16], authors have analyzed the proposed mobility management mechanism that used MIH framework and categorized the efforts according to the layer of the mobility management. Also, the authors have presented the extensions and amendments proposed on MIH framework. Even though authors have presented an integration of MIPv6 and PMIPv6 with MIH framework, but they have presented only one integration scheme which based on standard MIH primitives.
The main contribution of this paper is to focus on various mobility management schemes that integrate network-based PMIPv6 with IEEE 802.21 MIH framework for vertical handover. We then analyze the performance of the integrated schemes in terms of the chosen metrics.
3 Mobility Protocols
3.1 Proxy Mobile IPv6 (PMIPv6) Protocol
The PMIPv6 is an effective network-based localized mobility management scheme for NGWN standardized by IETF NetLMM working group. This protocol enables IP mobility for a MN without requiring its participation in any mobility related signaling. The network is responsible in managing IP mobility on behalf of the MN. This protocol does not need any change or improvement in the IPv6 protocol stacks [4].
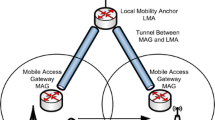
The core components of a PMIPv6 domain are mobile access gateway (MAG) and local mobility anchor (LMA) which are two network functional entities. The MAG performs mobility related signaling, tracks the movement of the MN and authenticates the MN by exchanging binding update/acknowledge messages with LMA. The MAG is typically implemented in the default access router which provided with care of address (CoA) in which many MAGs in the PMIPv6 domain attached to the LMA. The LMA is a topological anchor point for the MN’s that stores all the routing information and MN’s home network prefix (HNP) to ensure MN’s reachability state in the corresponding local domain. The LMA is equivalent to home agent (HA) in the MIPv6 protocol. Fig. 1 shows the network architecture of PMIPv6 protocol.
When the MN first enters the PMIPv6 domain and performs L2 attachment to the access network, the MAG at the serving network sends a proxy binding update (PBA) to the LMA that may have the followings: mobile node ID, Network Access ID, HNP, and a link local address. The LMA responds with a Proxy Binding Acknowledge (PBA) message after updating the binding cache entry (BCE). Subsequently a bidirectional communication tunnel between the MAG and LMA is established.
The MN drives its address using network prefix information in the router advertisement (RA) where the serving network assigns a unique HNP to the MN. The MN uses the same HNP during its movement inside the PMIPv6 domain and it is not required to assign a CoA at the MN.
Network architecture of PMIPv6 [11]
3.2 Media Independent Handover (MIH) Framework
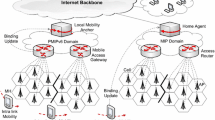
The IEEE 802.21 MIH framework is standardized by IEEE MIH working group to maintain seamless mobility handover across heterogeneous wireless technologies. Generally, the MIH protocol assigns information exchange that support topological and location information of service networks, neighbor networks, dynamic wireless medium, and some events and commands that altering the condition of the wireless link.
The MIH defines media independent handover functions (MIHF) to enhance the handover performance to the users during mobility across heterogeneous wireless networks. The MIHF uses the collective information from both MN and network infrastructure in handover execution by logically located between link layer (layer 2) and network layer (layer 3) in the protocol stack. The MIHF offers services to the upper layer and the MIH users such as PMIPv6 through service access point (SAP). This SAP is a unified interface that hides the heterogeneity of the access technology, while communicating with lower layers through media dependent specific SAPs based on the access technology [6].
The MIHF has three functional services designed to transfers network status information and events that happen in the lower layers to the higher layers and carry the higher layers commands to the lower layers to ensure optimize mobility performance. These services are as follows (see Fig. 2):
-
1.
Media independent event service (MIES): this service provides services to upper layers by reporting dynamically both local and remote changing events. These events such as link_going_down, link_down, and link_up are reported to upper layer protocol like PMIPv6 which acts based on these events.
Fig. 2 MIH general architecture [14]
-
2.
Media independent command service (MICS): this service provides a command from upper layers which is MIH user (such as PMIPv6 protocol) to manage and control the behavior of the lower layers (wireless link) related to connectivity and mobility issues. These command services such as poll, scan, configure, and handover commit can be issued by both local and remote MIH users.
-
3.
Media independent information service (MIIS): this service provides static and dynamic information about the serving and neighboring networks to both higher and lower layers. This information such as link information, network type, security information, and cost can be available through query/response mechanism.
4 PMIPv6 Enabled MIH Protocols Integrated Schemes
There are several schemes benefits from the cross layer design of layer 2 (L2) MIH framework and layer 3 (L3) PMIPv6 protocol to optimize handover latency, packet loss or the overall handover performance [17]. Hence, in this section we classify the PMIPv6 and MIH integration into six schemes and explain briefly the detailed operation using signaling flow diagram.
4.1 PMIPv6 Assisted MIH Using Standard Approach
Figure 3 shows the handover flow diagram of PMIPv6 protocol assisted by MIH using the standard mechanism. This scenario proposed by [18–32] follows the handover procedure exactly as stated in the protocols drafts.
When the serving wireless link signal becomes weak, the MIHF receives an event message about the signal strength of the serving link. The MN tries to search for other available neighbor networks by sending MIH_Get_Information request to MIIS server which replies with MIH_Get_Information response. The MN initialized the handover by sending MIH_MN_HO_Candidate_Query request to the serving network. The serving network checks for the resources availability at the candidate networks by sending MIH_N2N_HO_Query_Resources request message to the candidate networks which replies with MIH_N2N_HO_Query_Resources response. Then the serving network sends the resources availability check to the MN by MIH_MN_HO_Candidate_Query response message.
Based on the queried information, the MN determines the target candidate network and sends MIH_MN_HO_Commit request message to notify the serving network about the target network. The resources preparation occurs by sending MIH_N2N_HO_Commit request to the candidate target network which then responds with MIH_N2N_HO_Commit to the serving network which informs MN with MIH_MN_HO_Commit response.
During handover to the target network, the MN may detect the L2 detachment from the serving network. The serving network informs the LMA with deregistration PBU with life time set to zero and requests the LMA to buffer packets coming to the MN. The LMA then responds with PBA. Depending on the MN movements speed and the coverage area of the serving network, the detachment process with deregistration PBU/PBA with LMA may occur after MN attaches to the target network. The target network registers the MN location once it established L2 connection by sending PBA to the LMA which update their BCE and responds the PBA message and forward buffered packets to the MN. The target network can be solicited periodically or by router solicitation (RS) message from the MN and replies with RA message. After PMIPv6 handover is complete, the target network sends MIH_N2N_HO_Complete request message to the previous serving network which responds with MIH_N2N_HO_Complete response message.
4.2 PMIPv6 Assisted MIH Using Wireless Modified MIHF Signals
There are six wireless messages between the MN and the network side in the exiting MIH procedure from the target network selection to the reserving resources. A suggested procedure proposed by [33] deals with the wireless signals overhead and reduce handover latency. The proposed work suggests two MIH new messages to the overall MIH wireless signals messages. These messages are MIH_MN_HO request and MIH_MN_HO response.
As shown in Fig. 4, the MN initializes the handover operation by sending MIH_MN_HO request message to the serving network. The serving network sends the MIH_Get_Information request to MIIS server to query information in which MIIS server replies with MIH_Get_Information response. The serving network checks the resources availability of the candidate networks through normal MIH functions. Then, the serving network determines the target network based on the resources information instead of the MN in normal MIH procedure. Subsequently, the serving network notifies the target network by MIH_N2N_HO_Commit request in which the target network responds with MIH_N2N_HO_Commit response message. Then the serving network informs the MN about the target network through MIH_MN_HO response message including the information of the target network. The following handover steps follow conventional PMIPv6 procedure assisted by MIH and ends with MIH message of resources releasing of the previous service network.
4.3 PMIPv6 Assisted MIH Using MIHF at Network Side Only
The main idea of the suggested mechanism proposed by [34–36] is to provide fast mobility handover for the MN regardless of the presence or absence of IP mobility functionality as well as MIH functionality at the MN. Therefore, the proposed mechanism support the main objective of PMIPv6 network-based mobility management protocol by excluding the MN from participating in any MIH handover related signaling.
The proposed approach can effectively reduce the burden and power consumption of the MN which has limited resource and battery power by using a base station (BS) with MIH functionality to perform handover on the behalf of the MN.
As illustrated by the signaling diagram in Fig. 5, when the MN sense weak signal strength, the MN’s L2 generates a handover trigger and informs the MIH-BS of the serving network. Then, the MIH-BS sends MIH_Link_Going_Down Indication to the serving network (PoS), which queries the MIIS server to retrieve information about neighbor networks through normal MIH_Get_Information request/response messages.
The MIH-BS initiates the network-based handover by sending MIH_Net_HO_Candidate_Query request message to the serving network. Then, the serving network checks the availability of recourses of the candidate networks through MIH_N2N_HO_Quer_Resources request and response messages as normal mechanism.
The serving network can determine the target network based on the resources availability information of the candidate networks and notifies the MIH-BS by MIH_Net_HO_Candidate_Query response message.
The serving network informs the target network about the coming movement MN through MIH_N2N_HO_Commit request message which responds with MIH_N2N_HO_Commit response. Then, the serving network notifies the MIH-BS about the handover commitment by sending MIH_Net_HO_Commit response.
The target network queries the incoming MN’s profile information from the AAA server and starts to register the MN in the LMA, which updates its BCE of the MN location.
The next steps are similar to the handover procedure of the standard mechanism and end with resources release of the previous service network.
In this scheme, the six wireless signaling messages between the MN and MIH-BS in the MAG has been eliminated or removed. As a result, the proposed scheme can considerably minimize the signaling cost overheads over wireless link.
4.4 PMIPv6 Assisted MIH with Neighbor Discovery
Neighbor discovery (ND) is a mechanism that supports the network discovery and selection process by transferring network information to the neighbor networks. The network information may contain information about router discovery and MN profile that may contain MN-Identifier (MN-ID), MN HNP, LMA address, MIH messages etc, of nearby networks links. Thus, when the MN performs handover from one access network to another in a PMIPv6 domain, the target network does not need to acquire the MN profile from the policy/AAA server. Figure 6 presents the signaling flow diagram of the proposed system that suggested by [37–40] for PMIPv6 using MIH functions with ND.
Since the authentication process, attachment notification, MN profile detection and router reconfiguration are the major reasons of handover latency when the MN access to new network, then using of MIH functions with ND messages of IPv6 will effectively enhance the handover performance by reducing handover latency and packet loss.
When the serving network receives MIH_Link_Going_Down trigger, it transmits the MN profile to the neighbor candidate network using ND messages of IPv6. The MN-ID, MN HNP, LMA address and MIH messages are included in the ND messages and it does not need to acquire any information from AAA server. The packets designated to the MN are buffered at the serving network to avoid packet loss.
During the MN’s attaching to the target network, a MIH_Link_Up event message will be received by the target network. Then, the target network sends PBU to the LMA to update its BCE which replies with PBA message. The buffered packets are forwarded to the target network and the handover procedure proceeds as conventional mechanism in standard approach.
The main drawback of this approach is that it does not provide the required quality of service in heterogeneous environment since there is no query information with MIIS to check for resources availability.
4.5 PMIPv6 Assisted MIH with Handover Coordinator
The handover coordinator (HC) is a logical functional entity that has cooperative operation with the LMA in the PMIPv6 domain and it is normally placed at the main domain router. It controls the coordination of the handover procedure when the MN enters the overlapping region in the heterogeneous wireless networks. The HC used to support overall coordination of the mobility process by managing pre-authentication and pre-registration of the new target network, bicasting packets to both previous serving and new target networks, forwarding packets to new target network after detaching from previous network, etc.
A proposed approach of PMIPv6 protocol assisted by MIH services and HC is suggested by [41, 42] to improve the handover performance by reducing signaling cost overhead, handover latency and packet loss.
The signaling flow diagram of the proposed system is explained in Fig. 7. When the MN enters into the overlapping region of two access networks, the MN realizes that the received signal strength becomes very weak and the link will be lost. Therefore, MIH_Link_Going_Down message is sent to the serving network and the MN wakes up other interface to search for another candidate network to handover.
The serving network notifies the HC that the handover is needed soon with message includes the ID of the target network (MAG-ID) such that the target network can perform pre-authentication and pre-registration process. Then, the HC informs the LMA to bicasting the packets to both the serving network and the target network since both are connected to the LMA. When Link_Down event occurs, the MN understands that it is detaching from the serving network. It then sends MIH_Link_Down message and the HC notifies the LMA to stop bicasting and forward packets to the target network only and then the handover procedure continues normally.
4.6 PMIPv6 Assisted MIH Using Fast Handover Scheme
The PMIPv6 assisted by MIH using fast handover are proposed by [43–45] and the best development approach is presented in [45]. In the proposed approach, to minimize the MN participation in the handover process, the network side manages the handover procedure by performing handover initiation (HI), target network selection, and MN switching time to the target network.
As explained by the signaling flow diagram of Fig. 8, when one of the MN interfaces senses low signal strength, the MN sends MIH_Link_Going_Down to the serving network to start searching for the available neighbor networks. Then, the serving network sends the MIH_Get_Information request to MIIS server to query information and MIIS server replies with MIH_Get_Information response.
The resources negotiation begins with MIH_Net_HO_Candidate_Query request message that sends by the serving network to the MN in which it replies with MIH_Net_HO_Candidate_Query response. Then, the serving network performs resources availability check by sending MIH_N2N_HO_Candidate_Query request to the candidate neighbor networks which respond with MIH_N2N_HO_Candidate_Query response. The serving network decides the target network based on the resources information received. Since the authentication process with the target network is the major part of the MN attachment delay, fast PMIPv6 ensures to perform the new network attachment quickly to minimize the packets buffering delay at the MN and the target network. Also, using MIH services helps to execute the pre-authentication process during handover preparation phase. After the target network determined, the serving network sends MIH_N2N_HO-Commit request to inform the target network about the coming MN and the target network replies with MIH_N2N_HO-Commit response to the serving network.
Now, the serving network sends HI message to the target network containing MN ID, MN interface ID, and LMA address. The target network performs binding pre-registration with the LMA setting the flag for transient BCE entry creation and respond to the serving network with Handover Acknowledgement (HAck) message to indicate successful operation. Then, the serving network sends MIH_Net_HO_Commit request message to the MN specifying the target network information and indicating the completion of pre-authentication, and the MN replies with MIH_Net_HO_Commit response. The last two messages are very important in reducing the service disruption time by providing MN detachment and pre-registration synchronization. Also, the transient BCE will allow simultaneous reception from both networks during handover.
When the MN’s attachment is completed, the MN sends MIH_Link_Up message to the target network and the buffered packets are forwarded to MN. The up link packets sent to the LMA which already has transient BCE, while in the normal fast PMIPv6 without pre-registration, the traffic should move through a tunnel between the previous MAG and the new MAG which causes extra delay. Then the target network sends PBU to the LMA completing binding registration which responded with PBA. In normal fast PMIPv6, when the LMA receives PBU from the target network, the data path is switched to the target network resulting in out-of-order packet delivery.
5 Comparative Analytical Evaluation
In order to provide a clear and systematic comparison of all the efforts in the collected literature, Table 1 shows summary of previous works focusing on the evaluation method used (analytical or simulation), applicable area, traffic type, and the main handover performance metrics (signal cost, handover latency, packet loss, throughput).
In the following section we investigate the performance of the six schemes through quantitative evaluation, and present a comparative performance analysis in terms of signaling cost, handover latency, and packet loss. The analytical model is described first with default parameters values used in the evaluation.
5.1 Analytical Model
5.1.1 Network Model
We assume a circular domain which consisting of many identical circular cells, each cell contains MAG and the radius of each cell is \(R\), then the area of each cell is given by \(A = \pi \, R^{2}\). Also, we refer to the hop distance (average number of hops) between two network entities \(x\) and \(y\) by \(H_{x-y}\) and it is assumes to be symmetrical, i.e. \(H_{x-y}= H_{y-x}\).
5.1.2 Mobility and Traffic Model
We assume the handovers occurs when the MN move from one cell to another, thus the handover rate is equal to the cell crossing rate. We assume the session arrival to an MN follows a Poisson process with mean rate \(\lambda _{s}\). Also, we assume that the MN’s residence time in the cell is an exponentially distributed random variable and the MN movement follows a Fluid Flow model and the direction of the movement is uniformly distributed over the range \([0,2\pi ]\) with average speed \(\upsilon \). Then, the cell crossing rate and the average number of movement during inter session arrival can be expressed as follows:
Table 2 presents the defaults parameters values used in the evaluation analysis according to [33, 46–50]. Moreover, we assume the PoA and PoS are on the same network location, so we neglect any signaling and delay between them.
5.2 Signaling Cost (SC) Analysis
The signaling cost of the PMIPv6 and MIH integration schemes may include all the necessary signaling of initialization, execution, and ending of the handover procedure. Generally, the signal cost can be calculated by the product of the control signal size and the average hop distance where the processing cost is considered to be negligible in our calculations. Therefore, signaling cost of the six schemes can be expressed as follows:
5.3 Handover Latency (HL) Analysis
The handover latency of MIH and PMIPv6 integration schemes can be considered as the summation of L2 MIH preparation time and L3 PMIPv6 execution time until MN connected to the target network. Even though the handover trigger event generated before some time of the handover, the preparation to handover may take longer time depending on MN speed, signals overhead, wireless channel reliability, resources availability, and so on. Also we ignore MN L2 attachment and AAA policy authentication since they are the same for all schemes.
As the handover latency occurs due to the delays of messages exchanged between network entities to prepare and execute handover, hence, the handover latency of the standard approach which given in Eq. (9) can be explained as follows:
-
1.
There are six messages between MN and serving MAG \((6.\hbox {D}_{\mathrm{MN-sMAG}})\) which include the following, see Fig. 3:
-
MIH_Get_Information request to trigger the serving MAG to perform Information query with MIIS server
-
MIH_Get_Information response to inform the MN about information query of MIIS server
-
MIH_MN_HO_Candidate_Query request
-
MIH_MN_HO_Candidate_Query response
-
MIH_MN_HO_Commit request
-
MIH_MN_HO_Commit response
-
-
2.
There are two messages between serving MAG and MIIS server \((2.\hbox {D}_{\mathrm{sMAG-MIIS}})\):
-
MIH_Get_Information request
-
MIH_Get_Information response
-
-
3.
There are four messages between the serving and target MAGs \((4.\hbox {D}_{\mathrm{sMAG-tMAG}})\):
-
MIH_N2N_HO_Query_Resources request
-
MIH_N2N_HO_Query_Resources response
-
MIH_N2N_HO_Commit request
-
MIH_N2N_HO_Commit response
-
-
4.
There are two messages between serving MAG and LMA \((2.\hbox {D}_{\mathrm{sMAG-LMA}})\):
-
De-registration PBU
-
De-registration proxy binding acknowledgement (PBA)
-
-
5.
There are two messages between target MAG and LMA \((2.\hbox {D}_{\mathrm{tMAG-LMA}})\):
-
PBU
-
PBA
-
-
6.
There are two messages between MN and target MAG \((2.\hbox {D}_{\mathrm{MN-tMAG}})\):
-
RS
-
RA
-
Important to note that it is not necessary to include MIH completion messages which are MIH_N2N_HO_Complete request and MIH_N2N_HO_Complete response in the handover latency equation since the handover was finished before this point. Similarly, the handover latency of all other approaches can be expressed in the same way:
5.4 Packet Loss (PL) Analysis
The packet loss happens due to handover latency since there is no packet buffering is considered during MN movement. Hence, the packet loss is proportional to the handover latency and the packet arrival rate to the MN and it can be expressed by:
5.5 Numerical Results
The numerical results are obtained from the analytical functions and the default parameters values as presented in Table 2. The impact of MN speed on the SC is shown in Fig. 9. Since the handover rate is directly proportional to MN speed, then the SC increases linearly with MN speed increasing. It can be seen that the ND approach consumes lower SC while fast approach consumes higher SC compared with other approaches. However, the ND approach eliminates the MIIS server query information and the resources check messages which necessary to select the best MAG to handover. This leads to the loss of the quality of service insurance supported by MIH framework for multimedia and time sensitive applications, especially in heterogeneous wireless networks.
Figure 10 presents the impacts of the cell’s radius on the SC. It is observed that the SC decreases as radius increases. This is because when radius increases, the residence time in the cell increases, hence handover rate decreases. Also, it can be seen that the ND approach gives lower SC, while fast approach gives higher SC due to signals overhead compared with other approaches. Even though the neighbor discover approach gives lower SC, but it lacks quality of service insurance. On the other hand, the fast approach adds fast PMIPv6 messages of handover indicator (HI) and HAck to perform new network attachment quickly; this leads to reducing the packet buffering delay on the MN and target network.
The wireless delay is considered one of the most important parameters that affect the total handover latency. Wireless delay depends on several factors such as the type of the wireless access technology, frequency band, channel reliability, interference, and so on. The impact of the wireless delay on the total HL is shown in Fig. 11. It can be seen that the best HL is given by network only MIHF approach since it eliminates any use of wireless signaling between MN and access networks. However, the most advantages of the network only MIHF approach is not only reducing the total handover latency, but also reducing the power consumption and the processing requirement of the MN. Also, it can be noted that ND approach may give lower HL when the wireless link delay is small, but the total HL increases as the wireless link delay increases especially when the wireless link delay reaches 30 ms and more, then the total HL becomes higher than the network only MIHF approach.
Figure 12 shows the impact of varying delay between MAG and LMA on the total HL. This delay depends on several factors such the distance between MAG and LMA and the link type (wire, wireless, optical). It can be noted that the standard, modified wireless, and network only MIHF are more affected by the increasing delay between MAG and LMA since there are four messages delays between serving/target MAGs and the LMA, while the ND, HC, and fast approaches give lower HL due to only two messages delays between the target MAG and LMA.
Figure 13 shows the impact of varying delay between service MAG and target MAG on the total HL. It can be noted that the HC approach is not affected by varying the delay since there is no signaling between the neighbor MAGs, where the HC starts bicasting packets to both the serving and the target MAGs when the serving MAG receives MIH_Link_Going_Down of the old link and then MIH_Link_Up of the new link, Then the HC stops bicasting packets to serving MAG when it receives MIH_Link_Down. However, the ND approach gives lower HL and the fast approach gives higher HL compared to other approaches.
The impact of the session arrival mean rate on the PL is shown in Fig. 14. Although we presents the evaluation of all approaches in this figure and shows that the ND as the approach with lower PL, the HC and fast approaches specially designed to obtain zero packet loss. In HC approach, the HC which located in LMA bicasting the data packets to both the serving and the target MAGs during handover preparation phase benefits from MIH messages of MIH_Link_Going_Down and MIH_Link_Up. This is because the MN attached to the target MAG and performing handover assisted by MIH framework before detach from the serving MAG. The HC stop bicasting when the MN detached from the serving MAG which receives MIH_Link_Down message. In fast approach, the serving MAG performs pre-registration and authentication with target MAG sing HI and HAck messages and then start buffering the data packets. The buffered packets forwarded to MN directly after receiving MIH_Link_Up message to notify connection with target MAG.
The overall summary of the evaluated results and features of the six integration schemes are presented in Table 3. Even though it can be note that the ND approach gives enhanced handover performance in terms of SC, HL, and PL, but it lacks the required quality of service required for time sensitive applications and also it suffers from wireless messages between MN and access networks. Therefore, the integration scheme with network only mechanism can be considered as the best solution since it matched with the trend of network-based approach and provides the necessary quality of services in heterogeneous environment.
6 Conclusions
Literature and simulation works show that network-based PMIPv6 cannot cope with the requirements of real-time applications in heterogeneous wireless networks; therefore, several approaches have been proposed to integrate PMIPv6 with MIH framework to improve the handover performance. In this paper, we have presented in detail a survey on PMIPv6 and MIH integration schemes in the literature and we have classified them into six main categories by modifying the protocols message signals, adding new messages, and deploying of new network entities. Furthermore, we have summarized the main features of the literature survey based on evaluation method, applicable area, traffic type, and performance metrics.
We have also developed analytical model to evaluate and compare the handover performance of the six schemes in terms of signaling cost, total handover latency, and packet loss. The numerical results shows that ND approach gives the best performance compared to other approaches, but the HC and fast approaches designed to overcome the packet loss problem. However, based on the overall features and analysis, we can conclude that the network only MIHF can be considered the best solution due to several reasons: i) no new signals or messages, ii) no new network entity, iii) eliminates six wireless signals between MN and access network, iv) provides the required quality of service since it quires MIIS server for resources, v) matches well with the trend of network-based PMIPv6 by excluding MN participation in any mobility management operations. This approach may be further developed to improve its performance in mobility management.
References
Bhebhe, L. (2012). Mobility management issues in heterogeneous mobile wireless networks. In The 4th IEEE International Workshop on Management of Emerging Networks and Services, (pp. 787–791).
Udugama, A., Iqbal, M., Toseef, U., Fan, C., & Schlaeger, M. (2009). Evaluation of a network based mobility management protocol: PMIPv6. In IEEE 69th Vehicular Technology Conference, (pp. 1–5).
Bernardos, C., Gramaglia, M., Contreras, L., Calderon, M., & Soto, I. (2010). Network-based localized IP mobility management: Proxy mobile IPv6 and current trends in standardization. Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications, 1(2/3), 16–35.
Gundavelli, S., Leung, K., Devarapalli, V., Chowdhury, K., Patil, B. (2008). IETF RFC 5213: Proxy mobile IPv6. http://tools.ietf.org/pdf/rfc5213.pdf. Access 14 April 2014.
Yokota, H., Chowdhury, K., Koodli, R., Patil, B., Xia, F. (2010). IETF RFC 5949: Fast handovers for PMIPv6. http://tools.ietf.org/pdf/rfc5949.pdf. Access 14 April 2014.
Lan, MAN Standards Committee of the IEEE Computer Society. (2009). Part 21: Media independent handover services, IEEE standard 802.21-208. http://www.ieee802.org/21/doctree/Temp/P802-21-D11.pdf. Access 14 April 2014.
Sharma, V., t Agarwal, A., Abdul Qadeer, M. (2011). Media independent handover (IEEE 802.21): Framework for next generation vertical handover protocols. In International Conference on Computational Intelligence and Communication Systems, (pp. 507–511).
Taniuchi, K., Ohba, Y., Fajardo, V., Das, S., Tauil, M., Cheng, Y., et al. (2009). IEEE 802.21: Media independent handover: Features, applicability, and realization. IEEE Communication Magazine, 47(1), 112–120.
Vasu, K., Mahapatra, S., & Kumar, S. (2012). MIPv6 protocols: A survey and comparative analysis. Computer Science & Information Technology, 7, 73–93.
Ashraf, K., Amarsinh, V., & Satish, D. (2013). Survey and analysis of mobility management protocols for handover in wireless network. In IEEE 3rd International Advanced Computing Conference (IACC), (pp. 413–420).
Kong, K., Han, Y., Shin, M., & You, H. (2008). Mobility management for All-IP mobile networks: Mobile IPv6 vs. proxy mobile IPv6. IEEE Wireless Communication, 15(2), 36–45.
Al-Surmi, I., Othman, M., & Ali, B. (2012). Mobility management for IP-based next generation mobile networks: Review, challenge and perspective. Journal of Network and Computer Applications, 35, 295–315.
Modares, H., Moravejosharieh, A., Lloret, J., & Salleh, R. (2014). A survey on proxy mobile IPv6 handover. IEEE Systems Journal, 9, 1–10.
De La Oliva, A., Banchs, A., Soto, I., Melia, T., & Vidal, A. (2008). An overview of IEEE 802.21: Media independent handover services. IEEE Wireless Communications, 15(4), 96–103.
Khattab, O., & Alani, O. (2013). Survey on media independent handover (MIH) approaches in heterogeneous wireless networks. In The 19th European Wireless Conference, (pp. 1–5).
Ghahfarokhi, B., & Movahhedinia, N. (2013). A survey on applications of IEEE 802.21 media independent handover framework in next generation wireless networks. Computer Communications, 36, 1101–1119.
Bernardos, CJ., de la Oliva, A., Zuniga, JC., Melia, T., & Das, S., (2010). PMIPv6 operation with IEEE 802.21. Draft-bernardos-netext-pmipv6-mih-01. http://tools.ietf.org/pdf/draft-bernardos-netext-pmipv6-mih-01.pdf. Access 14 April 2014.
Pandey, D., Bashir, F., Kee, G., & Pyun, J. (2013). Performance evaluation of vertical handover for IEEE 802.21 enabled proxy mobile IPv6. In 2013 International Conference on Computing, Management and Telecommunications, (pp. 27–31).
Song, H., Kim, J., Lee, J., & Lee, H. (2011). Analysis of vertical handover latency for IEEE 802.21-enabled proxy mobile IPv6. In International Conference on Advanced Communication Technology. (pp. 1059–1063).
Kim, H., Park, S., & Yi, M. (2009). Fast-handover mechanism between 802.11 WLAN and 802.16 WiMax with MIH in PMIPv6. In The 4th International Conference on Ubiquitous Information Technologies and Applications, p. 6, Japan.
Magagula, L., Falowo, O., & Chan, H. (2009). PMIPv6 and MIH enhanced PMIPv6 for mobility management in heterogeneous wireless networks. In IEEE AFRICON, Nairobi, Kenya, (pp. 1–5).
Magagula, L., & Chan, H. (2008). IEEE802.21- assisted cross-layer design and PMIPv6 mobility management framework for next generation wireless networks. In The 4th IEEE International Conference on Wireless and Mobile Computing, Networking and Communication, (pp. 159–164).
Magagula, L., & Chan, H. (2008). IEEE802.21 optimized handover delay For proxy mobile IPv6. In IEEE Military Communications Conference, (pp. 1–7).
Melia, T., Giust, F., Manfrin, R., de la Oliva, A., Bernardos, C., & Wetterwald, M. (2011). IEEE 802.21 and proxy mobile IPv6: A network controlled mobility solution. In IEEE Conference on Future Network and Mobile Summit, (pp. 1–8).
Magagula, L., Falowo O., & Chan, H. (2009). Handover optimization in heterogeneous wireless networks: PMIPv6 vs. PMIPv6 with MIH. SATNAC, South Africa. http://www.satnac.org.za/proceedings/2009/papers/management/Paper%2020.pdf. Access 14 April 2014.
Kim, M., & Lee, S. (2009). Load balancing based on layer 3 and IEEE 802.21 frameworks in PMIPv6 networks. In IEEE 20th International Symposium on Personal, Indoor and Mobile Radio Communications, (pp. 788–792).
Kim, M., & Lee, S. (2010). Load balancing and its performance evaluation for layer 3 and IEEE 802.21 frameworks in PMIPv6-based wireless networks. Wireless Communications and Mobile Computing, 10(11), 1431–1443.
Jung, Y., & Kim, Y. (2008). QoS-aware customer network management (Q-CNM) system for efficient handovers with PMIPv6 and MIH. Lecture notes in computer science (Vol. 5297). Berlin: Springer.
Hussain, H., & Abu Bakar, K. (2011). A novel intra-domain continues handover solution for inter-domain Pmipv6 based vehicular network. International Journal of Advanced Computer Science and Applications, 2(12), 12–18.
Hussain, H., & Abu Bakar, K. (2012). Using media independent handover to support PMIPv6 inter-domain mobility based vehicular networks. International Journal of Communication Networks and Information Security, 4(3), 182–195.
Sanchez, M., & Uruena, M. (2013). On providing mobility management in WOBANs: integration with PMIPv6 and MIH. IEEE Communications Magazine, 51(10), 172–181.
Corujo, D., Guimarães, C., Santos, B., & Aguiar, R. (2011). Using an open-source IEEE 802.21 implementation for network-based localized mobility management. IEEE Communications Magazine, 49(9), 114–123.
Choi, G., Kim, B., & Min, S. (2010). A novel MIH handover procedure for efficient PMIPv6 networks. In IEEE International Conference on Information and Communication Technology Convergence (ICTC), (pp. 492–496).
Kim, P. (2013). An alternative IEEE 802.21-assisted PMIPv6 to reduce handover latency and signaling cost. Engineering Letters, 21(2), 68–71.
Kim, P., Jang, S., & Lee, E. (2013). An IEEE 802.21 MIH functionality assisted proxy mobile IPv6 for reducing handover latency and signaling cost. In IEEE 10th International Conference on Information Technology: New Generations, (pp. 692–695).
Kim, P., & Choi, J. (2010). A fast handover scheme for proxy mobile IPv6 using IEEE 802.21 media independent handover. World Academy of Science, Engineering and Technology, 43, 654–657.
Hassan, M., & Poo, K. (2011). Handover latency reduction using integrated solution scheme for proxy mobile IPv6. Recent Trends in Wireless and Mobile Networks Communications in Computer and Information Science, 162, 45–56.
Hassan, M., & Poo, K. (2011). Integrated solution scheme for handover latency diminution in proxy mobile IPv6. International Journal of Wireless & Mobile Networks (IJWMN), 3(4), 250–269.
Hassan, M., & Poo, K. (2011). Performance simulation and analysis of video transmission over proxy mobile IPv6 in a micro mobility domain. In International Conference on Telecommunication Technology and Applications, 5, (pp. 229–235).
Hassan, M., & Poo, K. (2011). One-time key and diameter message authentication protocol for proxy mobile IPv6. International Journal on New Computer Architectures and Their Applications (IJNCAA), 3, 624–639.
Jose, M., & Prithiviraj, A. (2012). PMIPV6-HC-MIH: An approach for improving handover performances in NGWN. In IEEE International Conference on Computing, Electronics and Electrical Technologies (ICCEET), (pp. 910–914).
Magagula, L., Falowo O., & Chan, H. (2010). Enhancing PMIPv6 for better handover performance among heterogeneous wireless networks in a micro-mobility domain. EURASIP Journal on Wireless Communications and Networking. http://jwcn.eurasipjournals.com/content/2010/1/274935. Access 14 April 2014.
Kim, I., & Kim, Y. (2011). Performance evaluation and improvement of TCP throughput over PFMIPv6 with MIH. In The 6th IFIP/IEEE International Workshop on Broadband Convergence Networks, (pp. 997–1004).
Kim, I., Jung, Y., & Kim, Y. (2009). MIH-assisted PFMIPv6 predictive handover with selective channel scanning, fast re-association and efficient tunneling management. Lecture Notes in Computer Science, 5787, 321–330.
Kim, I., Jung, Y., & Kim, Y. (2008). Low latency proactive handover scheme for proxy MIPv6 with MIH. Lecture notes in computer science (pp. 344–353). Berlin: Springer.
Makaya, C., & Pierre, S. (2008). An analytical framework for performance evaluation of IPv6-based mobility management protocols. IEEE Transactions on Wireless Communications, 7(3), 972–983.
Lee, J., Ernst, T., & Chung, T. (2010). Cost analysis of IP mobility management protocols for consumer mobile devices. IEEE Transactions on Consumer Electronics, 56(2), 1010–1017.
Lee, J., Han, Y., Gundavelli, S., & Chung, T. (2009). A comparative performance analysis on hierarchical mobile IPv6 and proxy mobile IPv6. Telecommunication Systems, 41(4), 279–292.
Lee, J., Bonnin, J., You, I., & Chung, T. (2013). Comparative handover performance analysis of IPv6 mobility management protocols. IEEE Transactions on Industrial Electronics, 60(30), 1077–1088.
Lee, J., Gundavelli, S., & Chung, T. (2009). A performance analysis on route optimization for proxy mobile IPv6. In 2009 IEEE International Conference on Communications. ICC’09, pp. (1–6).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Murtadha, M.K., Noordin, N.K. & Ali, B.M. Survey and Analysis of Integrating PMIPv6 and MIH Mobility Management Approaches for Heterogeneous Wireless Networks. Wireless Pers Commun 82, 1351–1376 (2015). https://doi.org/10.1007/s11277-015-2287-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-015-2287-4