Abstract
A heterogeneous wireless network consists of various devices that generate different types of traffic with heterogeneous requirements for bandwidth, maximal delay and energy consumption. An example of such networks is a Wi-Fi HaLow network that serves a big number of Machine Type Communication battery-powered devices and several offloading client stations. The first type of devices requires an energy-efficient data transmission protocol, while the second one demands high throughput. In this paper, we consider a mechanism that allocates a special time interval (Protected Interval) inside of which only battery powered-powered devices can transmit. We show that appropriate selection of the Protected Interval duration allows battery-powered devices to consume almost the minimal possible amount of energy on the one hand, and to provide almost the maximal throughput for offloading stations on the other hand. To find such duration, we develop a mathematical model of data transmission in a heterogeneous Wi-Fi network.
The reported study was partially supported by RFBR, research project No. 15-07-09350 a.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
- Internet of Things
- Machine Type Communications
- Restricted Access Window
- Traffic Indication Map
- Power save
1 Introduction
The number of devices connected to the Internet grows every day. According to Cisco prognosis [1], the number of connected devices, both Human and Machine Type Communications, will exceed 50 billion by 2020, most of them being wireless. Along with the number of devices, grows the variety of device and traffic types, increasing the heterogeneity. Wi-Fi networks are perfectly fit for such a challenge, which can be illustrated by the new amendment of the Wi-Fi standard, IEEE 802.11ah. On one hand, it is designed for the Internet of Things (IoT) scenarios with a swarm of energy-limited sensors that rarely transmit data. On the other hand, one of its use cases is cellular data offloading, which includes user devices that transmit saturated data flows.
Let us consider data transmission in an infrastructure heterogeneous Wi-Fi network with two types of devices. The first type, active stations (STAs), transmit or receive heavy data streams and are not sensitive to energy consumption. The second type, power-saving (PS) STAs, rarely transmit or receive single data frames from the Access Point (AP). To minimize energy consumption, the Wi-Fi standard has a palette of methods which are based on the following idea.
In the PS mode, a STA switches between the awake and the doze states. In the awake state, the STA can receive and transmit frames, while in the doze state the STA consumes minimal energy and neither receives, nor transmits any information. A PS STA is mainly in the doze state and awakes only to transmit a message or to receive one from the AP. The latter works as follows. The AP buffers data targeted for the PS STAs. To inform the STAs about buffered data, the AP periodically includes a Traffic Indication Map (TIM) in broadcast beacon frames. From time to time, the PS STA awakes to check the TIM in the next beacon for the pending data. When a STA receives a beacon with a TIM indicating that it has data to receive, the STA sends a PS-poll frame (after contending for the channel), and the AP sends buffered data as a response to the successfully received PS-poll frame.
Since STAs can sleep during some beacons, i.e., the period between two consequent awakenings can be greater than the beacon period, the set of STAs that are awake after a beacon is unknown to the AP. So the AP cannot schedule transmissions for the PS STAs and they use random channel access to transmit PS-polls. However the performance of random channel access degrades with the increase of the number of contending STAs, and it is an important issue for dense IoT networks. To limit the contention and to prioritize the PS STAs, it is reasonable to protect their transmissions from the active STAs, dividing each Beacon Interval (BI) into two parts: the Protected Interval (PI) and the Shared Interval (SI). During the PI, only PS STAs are allowed to retrieve their frames, while in the SI all STAs can transmit their data. The Wi-Fi standard specifies several ways how to organize the PI, one of which is the new Restricted Access Window mechanism introduced in 802.11ah [2, 3]. However, at this point a problem arises: how to choose a proper duration of the PI? On one hand, it shall be long enough to let the PS STAs receive the buffered data. On the other hand, the longer is the PI, the less time the active STAs have to transmit their data, therefore their throughput degrades. In addition, the PS STAs can finish their transmissions during the SI, but the contention with active STAs increases energy consumption.
In this paper, we study this problem and propose a solution based on a mathematical model of such heterogeneous data transmission. Our model takes into account the fact that during the PI, devices operate in non-saturated mode, i.e., they simultaneously start contending for the channel to transmit a frame to the AP, while in SI, we combine the transmission of non-saturated and saturated flows.
The rest of the paper is organized as follows. Section 3 reviews related papers. Section 2 contains the formal problem statement. The developed analytical model is described in Sect. 4. Section 5 shows the numerical results. The conclusion is given in Sect. 6.
2 Problem Statement
Consider a network with an AP, PS STAs and \(M-1\) active STAs (PS STAs and active STAs are different devices) being in the transmission range of each other. Active STAs work in saturated mode, i.e., they always have packets for transmission. The AP queue of packets destined to active STAs is saturated too. For shortness, considering saturated data transmission, we do not distinguish the AP and \(M-1\) active STAs, assuming that we have M active STAs.
As for the PS STAs, they rarely receive single packets from the AP. Specifically, the AP periodically broadcasts beacons containing TIM information element, which indicates the STAs for which the AP has buffered data. We consider a situation, when the AP has data for several, say, K, PS STAs. As PS STAs do not need to awake before every beacon, not all K PS STAs receive the TIM. For clarification, we introduce probability p that a PS STA awakes to receive a particular beacon and receives the TIM.
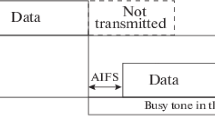
When a PS STA receives a TIM which indicates that no data is buffered for the STA, it switches to the doze state. Otherwise, the PS STA transmits PS-poll frame to retrieve the buffered packet from the AP. To protect PS-poll frames from collisions with active STAs’ packets, the AP establishes the PI of duration \(\tau _{PI}\) which should, obviously, depend on K and p. If some PS STAs do not successfully retrieve the data from the AP during \(\tau _{PI}\), they can try again in the SI, contending for the channel with M active STAs. After a successful data reception from the AP, each PS STA turns to the doze state.
To contend for the channel, both PS STAs and active STAs use the default Wi-Fi channel access — called the Distributed Coordination Function (DCF) — which works in the following way. When a STA has a frame for transmission, it waits random backoff time. Specifically, it initializes backoff counter with a random integer value uniformly drawn from interval \([0,CW - 1]\), where CW is the contention window. It equals \(CW_{min} = 16\) for the first packet transmission attempt and doubles after every unsuccessful transmission, until it reaches \(CW_{max} = 1024\) (we use the default \(CW_{min}\) and \(CW_{max}\) values for 802.11ah STAs, provided in [2]). Being in the awake state, STAs continuously sense the channel. While the channel is idle, STAs decrement the backoff counter every \(T_e\) seconds. A STA suspends its backoff counters when the channel is busy, and resumes when the channel becomes idle and DCF InterFrame Space (DIFS) passes. Finally, when the backoff counter reaches zero, the STA transmits a packet.
If a transmission is successful, a Short InterFrame Space (SIFS) after that the receiver sends an acknowledgement (ACK). If the STA does not receive the ACK frame within \(T_{ACK}\), it retries, unless the packet retry counter reaches retry limit RL. In this case, the packet is dropped.
Depending on the channel state — idle, STA’s transmission or reception — the STA consumes power \(N_{TX}\), \(N_{RX}\) and \(N_{IDLE}\), respectively.
To achieve the best performance, the AP has to estimate the number of active STAs each BI and to re-select the duration \(\tau _{PI}^*\) of the PI in such manner that (i) energy consumption by PS STAs is minimal while (ii) the active STAs’ throughput is maximal. Note that generally speaking, such a value may not exist. However in this paper, we show that there is a range of values which provide suboptimal results for both performance indices.
To find such values, we need to develop a mathematical model of the described transmission process. Specifically, given \(\tau _{PI}\), the model shall allow obtaining
-
the probability P that a chosen awaken PS STA retrieves its buffered data from the AP till the next beacon (i.e. within BI);
-
the average energy \(\overline{E}\) that this PS STA consumes when retrieving its packet from the AP;
-
aggregated throughput S of M active STAs.
3 Related Work
A process of energy efficient transmission of single packets by a large number of stations has been studied in many papers.
Specifically, in [4], the authors consider a system, where multiple RFID tags transmit data to a single reader. The reader periodically allocates to the tags a frame that consists of several slots. The tags use slotted Aloha to choose the slots when they transmit data. The authors solve the problem of choosing such a frame duration, that the ratio of the expected number of successful slots duration to the total frame duration is maximal. This is done by estimating the number of tags, initially unknown to the reader, using the Maximum Likelihood approach. Unfortunately, the results of this paper cannot be applied to select the PI duration in our case, for two reasons. First, the medium access used in Wi-Fi is significantly different from the one used for RFID. Second, the number of contending PS STAs may significantly vary from a BI to a BI, as well as inside a BI.
In [5], similarly to our paper, the authors consider a 802.11ah network consisting of an AP and several associated STAs. The AP periodically allocates a Restricted Access Window to the STAs to protect their transmission, thus implementing the PI. The authors devise a way for the AP to estimate the number of STAs and describe a model of data transmission during the PI that can be used to find the probability of the successful transmission. However, the authors consider a case when the STAs transmit in saturated mode, i.e., in their case the number of contending STAs does not decrease during the PI, therefore their model is inapplicable in our case.
Non-saturated transmission is considered in [6], the authors of which model a network of PS STAs connected to an AP. The STAs awake every BI to receive their data from the AP. The authors develop a model that can be used to find the average packet delay and the average energy consumption per packet. However, this model is inapplicable to solve our problem, because it does not consider the existence of active STAs that transmit their data along with the PS STAs.
To address the issues of modeling the transmission of non-saturated data flows along with background saturated traffic, in our paper we develop a new mathematical model, which is described in Sect. 4.
4 Analytical Model
4.1 General Description
To estimate throughput of active STAs, we assume that the probability that a PS STA succeeds to retrieve its data from the AP during the PI is close to 1. With this assumption we, firstly, can consider each BI separately, i.e., there are no PS STAs that had started to retrieve their data in the previous BI and did not succeed until the considered BI. Secondly, the number of PS STAs that retrieve their data during the SI is low and these PS STAs do not affect the probability that an active STA transmits in a slot during the SI. Note that this assumption likely holds in the range of suboptimal \(\tau _{PI}\) values, as we show in Sect. 5. We also assume that the duration of SI is much longer than the duration of a packet. Under such assumptions the active STAs throughput in the SI can be estimated with well-known Bianchi’s model [7]. Since active STAs cannot transmit outside the SI, the average throughput can be found as follows:
where \(S_{Bianchi}\) is the throughput found with Bianchi’s model.
Let us find P and \(\overline{E}\). For that, we consider a BI. As a PS STA wakes up with probability p, the total number k of awaken PS STAs among the K STAs for which the AP has buffered data in the beginning of a BI is a binomially distributed random number. In Sects. 4.2 and 4.3, we obtain probability \(P'\) that a chosen PS STA succeeds to retrieve the data till the end of the BI and the average energy \(\overline{E'}\) consumed by the PS STA to retrieve a data packet provided that the number k of awaken PS STAs is given. Obviously, sought-for values of P and \(\overline{E}\) can be expressed as follows
4.2 Process of Retrieving Packets
Since all STAs and the AP are located within transmission range of each other, they count their backoffs synchronously. Similar to [7], we denote a time interval between two consequent backoff countdowns as a slot. We distinguish the following types of slots.
-
In an empty (e) slot, no STAs transmit.
-
In a successful (s) slot, only one PS STA transmits its PS-poll and the AP replies with a data frame. Then the PS STA acknowledges reception of the frame.
-
In a collision (c) slot, more than one PS STAs transmit a PS-poll, while active STAs do not transmit.
-
In an active (a) slot, at least one active STA transmits. The transmission may be successful or not, however we do not distinguish these cases. Note that active slots can be present only in SI.
The durations of empty, successful, collision and active slots are \(T_e, T_s, T_c\) and \(T_a\), respectively.
Let t be a slot number starting from the beginning of the BI. We choose an arbitrary PS STA and describe the evolution of the network from the beginning of the BI with a Markov process \(I_t\) with state \(I = (c, s, a, r)\), where c, s and a are the numbers of collision, successful and active slots, respectively, and r is the number of retries for the chosen PS STA. Note that unlike Bianchi’s model, we consider not a steady-state distribution of the process \(I_t\), but its evolution during the BI.
In each state we can easily find the number of empty slots as \(t - c - s - a\). So the real time T can be obtained from the model time t and the process state parameters as
For the defined process we introduce successful \(A^S\) and unsuccessful \(A^U\) absorbing states. A transition to \(A^S\) occurs when the chosen STA successfully transmits its data. The process transits to \(A^U\) when the chosen STA reaches its retry limit RL or the end of the BI is reached.
Let \(Q_a\) be the probability that at least one active STA transmits in a given slot. Obviously, during the PI, i.e. when \(T < \tau _{PI}\), \(Q_a(T)=0\). In the SI \(Q_a>~0\) and under aforementioned assumption can be estimated with the Bianchi’s model [7]:
where \(\pi \) is the probability that a given active STA transmits in a slot, obtained using Bianchi’s model.
Figure 1 shows possible transitions from state (c, s, r, a). We denote a transition probability as \(P_X^Y\), where X represents the type of slot t, i.e. X is e, s, c or a, and Y is either \(+\) or − depending on whether the chosen PS STA transmits or not. Since by definition, in an empty slot no STAs transmit, we simply write \(P_e\), omitting the upper index.
To find these probabilities, we introduce \(P_{TX | t, r}\) which is the conditional probability that the chosen PS STA transmits in slot t, provided that by that time it has made r unsuccessful transmission attempts. We also introduce \(P_{e|-}, P_{s|-}, P_{c|-}\) which are the conditional probabilities that the slot is empty, successful or collision, respectively, provided that the chosen STA does not transmit, and express transition probabilities as
Given \(P_{TX | t, I}\), the probability of a PS STA to transmit if the process is in state I at time instant t, these probabilities can be found as follows:
Using the approach from [8], we estimate \(P_{TX | t, r}\) as follows:
where \(a_{t, r}\) and \(b_{t, r}\) approximate the unconditional probability of the chosen STA transmitting in slot t with retry counter r, and the probability of the STA having retry counter r in time slot t, respectively:
and
Having the approximation of \(P_{TX | t, r}\), we approximate the probability that another STA transmits provided that the process is in state I as follows:
Now we consider the evolution of the process. The process starts in time 0 in state (0, 0, 0, 0). With the described transitions of the process, we can iteratively find its state probability distribution \(\Pr (t, I)\) at each time slot t. Moreover using (4), we can find the probability that the chosen STA successfully retrieves its data during the BI with given k:
4.3 Calculating Average Energy \(\overline{E}'\)
Let E (I, t) be the average energy that the chosen STA has consumed by time instant t when its state is I. It equals 0 for \(t = 0\), otherwise it is calculated according to the following equation:
where we sum over all possible states \(I'\) at time \(t - 1\) and corresponding transitions to state I at time t. Similar to transition probabilities, we denote the energy consumed by such transitions as \(E_X^Y\). This energy depends on \(N_{tx}, N_{rx}\) and \(N_{idle} \), which are the power consumed in transmission, reception or idle state, as follows:
where \(T_{PS}, T_{ACK}, T_{D}, T_{AD}\) are the durations of PS-poll, ACK, data frames transmitted for PS STAs and data frames transmitted by active STAs, respectively.
The average energy that the chosen STA consumes to successfully retrieve a packet equals
5 Numerical Results
To validate our model, we consider an 802.11ah network with K PS STAs for which the AP has buffered data at every BI and M active STAs, all STAs being located 10 meters from the AP. Such a short distance guarantees that transmission errors are caused only by collisions. Active STAs transmit and receive data frames 1500 bytes long and PS STAs retrieve data frames 100 bytes long. A PS STA awakes with probability \(p = 0.5\). We assume that active STAs and PS STAs operate in a 2 MHz channel. Active STAs use MCS5 while PS STAs use the most reliable modulation coding scheme (MCS0)[2]. Table 1 shows the scenario parameters. Transmit, receive and idle power are derived from voltage and current values given in the IEEE simulation scenario recommendations [9].
Although an 802.11ah AP can support up to 8191 connected STAs, we consider only small numbers of simultaneously operating STAs, assuming that the AP uses some standard mechanisms to decrease the contention between the STAs. One of such mechanisms — TIM segmentation — is described in 802.11ah amendment [2]. It allows the AP to divide the TIM into several parts and broadcast only a single part of the TIM in a beacon. The AP thus divides the STAs into groups, e.g. with a clusterization method from [10], and services each group in a separate BI. Even if the total number of STAs is big, only a reasonable number of them will retrieve their data during the BI, while the rest of the STAs will wait for a beacon containing their part of the TIM.
At first, we find the average energy \(\overline{E}\) that the chosen PS STA consumes to retrieve a packet from the AP. Figure 2 shows that the results obtained with the developed analytical model almost coincide with those obtained with simulation, except for short PIs. If the PI is short, the PS STAs mostly finish their transmissions during the SI, contending for the channel with active STAs, so only in this area our assumption that PS STAs do not affect the performance of active STAs does not hold. Small PI duration yields high energy consumption, and by increasing the PI duration we can manifold reduce it down to some value at \(\tau ^*\) (indicated with big markers), where it reaches a plateau that corresponds to the case when the PI is long enough for PS STAs to receive their data during it. More accurately, we can state that \(\tau ^*\) is the minimal \(\tau _{PI}\) for which power consumption differs from the optimal one not more than by 10 %.
Increasing the PI duration beyond \(\tau ^*\) does not significantly affect power consumption, but reduces the time available for active STAs, decreasing their throughput. In more detail, such an effect is shown in Fig. 3. An important result is that initially, i.e. when PI is small, the throughput of active STAs grows with the PI. It means that in addition to PS STAs, active STAs benefit from the introduction of the PI, too, since they do not suffer from contention for the channel with a high number of PS STAs. However, at some point the throughput reaches the maximal value, after which it goes down, since the amount of the time available for active STAs decreases.
An important fact is that although choosing \(\tau _{PI} = \tau ^*\) does not maximize throughput, it provides suboptimal performance. Indeed, in the worst considered case, with 40 active STAs and 20 PS STAs, the throughput at \(\tau ^*\) differs from the maximal one by less than 30 %, see Fig. 3, but for smaller number of STAs the difference decreases. Note that the maximal throughput can only be achieved with manifold increase of energy consumption.
Another important fact is that the throughput obtained analytically at this point is close to the value obtained with simulation.
6 Conclusion
In this paper, we have studied efficiency of the Wi-Fi power saving mechanism in an heterogeneous Wi-Fi network with energy-limited devices. To improve performance of the network, the AP protects transmission of PS-polls from collisions with transmission of active STAs. To model operation of the network, we have developed a mathematical model, which provides us such performance indices as throughput and power consumption. With this model, we show that the duration of the protection interval can be chosen in such a way that provides suboptimal results for both the throughput and power consumption, which is important for implementation.
The future research is connected with considering scenarios with hidden STAs and TIM segmentation, a novel mechanism introduced in IEEE 802.11ah.
References
Evans, D.: The internet of things: how the next evolution of the internet is changing everything. CISCO white paper, San Jose, vol. 1, pp. 1–11 (2011)
IEEE P802.11ahTM, D5.0 Draft Standard for Information technology – Telecommunications, information exchange between systems Local, metropolitan area networks Specific requirements - Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications - Amendment 6: Sub 1 GHz License Exempt Operation, March 2015
Khorov, E., Lyakhov, A., Krotov, A., Guschin, A.: A survey on IEEE 802.11 ah: an enabling networking technology for smart cities. Comput. Commun. 58, 53–69 (2015)
Khandelwal, G., Lee, K., Yener, A., Serbetli, S.: ASAP: a MAC protocol for dense and time-constrained RFID systems. EURASIP J. Wirel. Commun. Netw. 2007(2), 3 (2007)
Park, C.W., Hwang, D., Lee, T.-J.: Enhancement of IEEE 802.11 ah MAC for M2M communications. IEEE Commun. Lett. 18(7), 1151–1154 (2014)
Liu, R.P., Sutton, G.J., Collings, I.B.: Power save with offset listen interval for IEEE 802.11 ah smart grid communications. In: 2013 IEEE International Conference on Communications (ICC), pp. 4488-4492. IEEE (2013)
Bianchi, G.: Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 18(3), 535–547 (2000)
Khorov, E., Krotov, A., Lyakhov, A.: Modelling machine type communication in IEEE 802.11 ah networks. In: 2015 IEEE International Conference on Communication Workshop (ICCW), pp. 1149–1154. IEEE (2015)
TGax Simulation Scenarios. https://mentor.ieee.org/802.11/dcn/14/11-14-0980-10-00ax-simulation-scenarios.docx
Levin, M.S.: Combinatorial clustering: literature review, methods, examples. J. Commun. Technol. Electron. 60(12), 1403–1428 (2015). http://dx.doi.org/10.1134/S1064226915120177
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2016 Springer International Publishing AG
About this paper
Cite this paper
Bankov, D., Khorov, E., Kureev, A., Lyakhov, A. (2016). Improving Efficiency of Heterogeneous Wi-Fi Networks with Energy-Limited Devices. In: Galinina, O., Balandin, S., Koucheryavy, Y. (eds) Internet of Things, Smart Spaces, and Next Generation Networks and Systems. ruSMART NEW2AN 2016 2016. Lecture Notes in Computer Science(), vol 9870. Springer, Cham. https://doi.org/10.1007/978-3-319-46301-8_15
Download citation
DOI: https://doi.org/10.1007/978-3-319-46301-8_15
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-46300-1
Online ISBN: 978-3-319-46301-8
eBook Packages: Computer ScienceComputer Science (R0)