Abstract
Physical Unclonable Function (PUF) has emerged as a hardware security block designed with low-cost and key generation for IC identification and authentication. The process variations being uncontrollable, they can be exploited as PUF that could generate unique identifiers representing robust keys. Arbiter-based PUFs work on the principle of the conventional delay-based approach realized between two symmetrical engaged paths. On the other hand, oscillator-based PUFs work on frequency differences among a group of identical oscillators arranged in a specific pattern. In this paper, a novel PUF is proposed based on Relaxation Oscillator PUF (ReOPUF) topology for device identification and authentication that can produce unique, unpredictable, and reliable keys to improve the robustness against the supply voltage and temperature variations. The ReOPUF is designed to generate a 4.4 MHz frequency that is suitable for powering IoT sub-systems including sensors while protecting them from malicious attacks. Based on Monte Carlo simulations, the reliability of PUF responses has been improved from 95.33% for the regular Ring Oscillator (RO) PUF to 99.19% for the proposed ReOPUF over a temperature range of \(-40\,^\circ \)C to +120 \(^\circ \)C with ±10% fluctuations in supply voltage. Moreover, it achieves a good uniqueness result of 49.22%, diffuseness of 49.52%, and worst-case reliability of 97.41% over a range of 10 \(^{\circ }\)C to 85 \(^{\circ }\)C, and 10% fluctuations in supply voltage. Thus, we report significant improvement over previous works.
Access provided by Autonomous University of Puebla. Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
The design of secure electronic systems is very important so that they can store sensitive information as well as communicate securely with the authorized devices. The rapid down scaling in feature sizes of Integrated Circuits (ICs) has exponentially improved computing power of processors which require robust security mechanisms [1]. Currently, the secure device authentication and data integration is provided by incorporating cryptographic functions implemented as hardware blocks [4]. The secret key is stored in non-volatile memory such as erasable programmable read-only memories which is vulnerable to invasive or non-invasive attacks. Physical Unclonable Function (PUFs) [2, 3, 5] emerged as robust security primitives to generate volatile security keys based on the inherent random manufacturing Process Variations (PVs) [6]. It offers a strong volatile key generation and storage to make the system tamper-resistant. When a PUF is fed with a challenge, it generates unique responses based on the physical characteristics of the silicon and is an alternative to the conventional digital signature mechanism.
A group of identical PUF cells with the same manufacturing process leverage the physical properties of each cell and generate a device-specific fingerprint or key [7]. PUF can be used in several applications such as device authentication or identification, key generation for encryption, and pseudo-noise random number generation [8, 9]. The uniqueness and randomness are the unpredictable features of a PUF that makes it resistant to security attacks. PUFs are only uncertain in power-up conditions when side-channel or power analysis attacks are performed. To make a strong PUF the key generation must stable and reliable which means the key should not change over time. Several PUF topologies have been proposed to improve reliability in the past decade, such as Arbiter PUF, Ring Oscillator (RO) PUF, SRAM PUF, etc. Among them, Arbiter PUFs [10] are very complex and generate strong challenge and response pairs [11, 12], whereas, RO PUFs are less complex and easy to design.
As mobile electronic gadgets become more widespread, day-to-day business (financial transactions, document exchange, health data, etc.) is done through integrated circuits. Thus, it is essential to incorporate strong security to ensure data privacy and trust [1]. PUFs serve as key generators for cryptographic devices to provide secure communication in an untrusted environment [7]. Security in data is generally raised through data sharing or distribution of the keys generated through key generators. The main characteristics of the key generated by a PUF are its randomness and uniqueness due to PVs. The key should be unaffected due to temperature and supply voltage variations and must be resistant to side-channel attacks.
RO PUFs [12, 13] are most popular due to their security, simplicity, ease of implementation, and evaluation. However, the main disadvantage of RO PUFs is poor response generation with temperature and supply voltage variations [14, 15]. Therefore, the reliability is enhanced by selecting a strong RO pair from 1-out of n-RO pairs, which has the maximum frequency distance from n-pairs. Multi-level supply voltage powered RO PUF are proposed to select the highest reliable voltage configuration [16]. The feedback-based supply voltage control can improve the reliability better than the conventional RO PUFs [17]. A temperature-aware RO PUF with different RO pairs can generate reliable bits against temperature variations [18, 19]. The temperature sensitivity is the major drawback in RO PUFs and can be reduced by applying a negative temperature coefficient of resistance to the inverters with two source feedback resistors. However, to achieve high reliability, a lightweight hybrid RO PUF was proposed with high thermal stability against supply voltage variation [15]. The security can be further strengthened when the system is designed with machine learning [21] based schemes for IoT edge node security.
To this end, we make the following contributions:
-
We propose a new Relaxation Oscillator PUF design which we refer to as ReOPUF. The ReOs in ReOPUF is designed to explicitly produce the low frequency i.e., 4.4 MHz suitable for IoT sensor node security.
-
The respective PUF quality metrics are evaluated and analyzed for the proposed PUF to demonstrate the high reliability in key generation.
-
We perform extensive simulations (in 65 nm CMOS technology) to compare the proposed PUF with conventional RO PUFs in terms of PUF quality metrics with respect to supply voltage and temperature variations. We evaluate two more quality metrics, namely, Diffuseness (D) and Uniformity (u). We compare the strong CRP generation of the proposed ReOPUF with that of arbiter PUF. Further, we perform the entropy and correlation analysis.
The rest of the paper is organized as follows. Section 2 motivates the IoT authentication with PUFs. Section 3 surveys related research regarding existing PUFs and their reliability measurement with PUF quality metrics in response key generation. Section 4 proposes the methodology to achieve high uniqueness and reliability to enhance the security of IoT devices. Section 5 reports the simulation results, evaluates PUF quality metrics and, compares the proposed design with other PUFs. Section 6 presents a detailed security evaluation. Finally, Sect. 7 concludes the paper.
2 IoT Node Authentication with PUFs - Motivation
With the increasing demands on strong security, key generation and device authentication became the most challenging design concerns, particularly for IoT-enabled devices. Traditional security mechanisms that store keys in erasable programmable memories and use them with standard cryptographic algorithms suffer from power limitations. To implement information encryption and authentication, the tamper-resistant devices are equipped with countermeasures to defeat different types of physical attacks. Severe limitations on resources such as memory, CPU and battery power make classical cryptographic solutions unaffordable. Therefore, PUF has become a relatively simple and fast alternative for security.
PUFs are promising hardware security primitives to produce device-dependent challenge-response pairs based on unclonable properties and thus are suitable for reliable key generation [1]. The keys generated by PUFs are more resilient to malicious attacks from physical tampering. Figure 1 shows the security concept of IoT-enabled devices. An IoT device equipped with ReOPUF generates PUF key as a unique ID and is shared through a gateway with the Cloud server. PUF keys are acquired by the Advanced Encryption Standard (AES) engine in the Cloud that can be employed to identify and authorize an IoT device. For example, consider an IoT-enabled sensor node in the field that senses the temperature or moisture data continuously upload the data to the Cloud at regular intervals. This data can be protected in the Cloud by encrypting it with PUF keys generated by ReOPUF. Therefore, due to the uniqueness and reliability of the ReOPUF, the sensor node can be authenticated.
3 Related Research
In this section, we briefly summarize the existing PUF topologies and their quality metrics to generate CRPs for device identification or authentication.
3.1 Ring Oscillator PUF
Figure 2 shows a conventional Ring Oscillator (RO) PUF for key generation [11]. It consists of N identically designed ROs (RO1, RO2, \(\ldots \), RON), two multiplexers, two counters, and one comparator. Each RO oscillates at different frequency due to manufacturing process variations, even though ROs are designed with an equal number of inverter stages [12]. An N-bit multiplexer can select a pair of frequencies generated from the RO stage based on the challenge input (through selection lines). The counters are used to get the count of the pulses obtained from the MUX stage. The difference in the pulses between the two counters is verified by the comparator and a response is generated. For example, if Counter 1 output is greater than that of Counter 2 then a ‘1’ is generated, otherwise, a ‘0’. In this manner, an N-bit key can be obtained from an N copies of RO PUF.
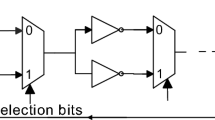
3.2 Arbiter PUF
Figure 3 shows a basic arbiter PUF. It consists of switch components (SCs) and arbiter block to route the input signal and to perform the arbitration process for earlier response detection respectively [9]. Input and a random challenge are simultaneously fed to the switching components (multiplexers). Based on the delay of the paths the arbiter will detect early rising edge as the response. The mechanism of delay-based PUF is to introduce a race condition between two equally designed delay paths and the faster path will determine the output.
The circuit accepts of n-bit input challenge ‘C’ and computes 1-bit response ‘R’ based on the contention between two symmetrical paths based on relative delay difference (\(\mathrm {\varDelta }\)d = d1 − d2). The delay of the input is determined by the two-path processing of multiplexers (MUXs). Formally, the SCs are designed with 2 \(\times \) 1 MUXs and properly tuned to get the precise delay (d) as a response. The delays are generally considered as PVs in APUFs, such as produced by the placement of a different combination of transistor arrangements in MUXs to produce certain delays at SCs. The MUXs will active the straight path if the selection (challenge) C\(_{i}\) is ‘0’ and crossed when C\(_{i}\) is ‘1’. Likewise, MUX stages acting as SCs can create a pair of delay paths that can be selected with challenge input. The output is evaluated for a particular input while a rising signal is fed to both paths at the same time. The two signals race through the delay paths and the arbiter circuit (generally use D Flip-flop) catches the signal which comes earlier. The arbiter determines which rising edge arrives first and sets its output to ‘0’ or ‘1’ depending on the winner. For example, if a 16-bit input is given with a pre-defined challenge, an output ‘1’ is produced if path1 is arrived early otherwise ‘0’ is produced for path2.
3.3 PUF Quality Metrics
The quality of a PUF is measured using three major metrics, namely, Uniqueness, Randomness, and Reliability [20]. Uniqueness measures how different PUF instances can generate different responses when the same challenge is applied. The average inter-chip Hamming Distance (HD) calculated between the obtained responses should ideally be 50%. Randomness is the measure of unpredictability of responses from a PUF. For a good PUF design, the generation of response bits ‘1’s and ‘0’s should be distributed equally i.e., 50%. Reliability of a PUF determines how efficiently a PUF can generate the same response at different operating conditions for a given challenge. It is considered as intra-HD and should ideally be 0%.
4 Proposed Relaxation Oscillator PUF (ReOPUF)
An oscillator is a circuit that generates a repetitive waveform of fixed amplitude and frequency without any external input signal. Oscillators are used in radio, television, computer, and communications. Relaxation Oscillator (ReO) shown in Fig. 4 is specifically preferred for low-frequency applications such as waveform generators, triggering circuits, etc. ReO is considered as a non-linear oscillator that can generate a periodic non-sinusoidal waveform (either voltage or current) at its output such as a square wave, triangular wave, etc. It is also called a non-sinusoidal waveform generator. ReOs do not require external components and are easily implemented in CMOS technology. In addition, ReOs are capable of producing sustained square wave oscillations determined by the time constant RC even though the frequency accuracy is restricted by the tolerances of on-chip capacitors and resistors. ReOs consume less current and power to generate jitter less clock generation.
A major drawback of ReO is its susceptibility to process and temperature variations. By the use of polysilicon resistors and the utilization of electron mobility in a MOS transistor offers an accurate frequency reference subjected to achieve fewer process variations and frequency stability over temperature. Most of the reported oscillators suffer from external components, reliability, and excessive power consumption and are not suitable for low-frequency applications requiring long battery lifetime.
The circuit can be designed with an energy storing device such as a capacitor or inductor which charges and discharges continuously to produce a cycle regarding a pre-determined threshold voltage. The frequency (f) or period (t) of oscillation with ReO is determined by the time constant (\({\tau = 2.2RC}\)) of the capacitive or inductive circuit. Likewise, the frequency is calculated for the basic ReO is \(f=1/{\tau }\) i.e., 4.4 MHz. ReOs are widely used to produce internal clock signals in several low frequency digital circuits. ReOs are also found in applications of thyristor triggering circuits, oscilloscopes, etc.
ReOPUF is a hardware PUF that exploits PVs occurring in the silicon manufacturing process to produce reliable keys. The random number extracted via ReOPUF is unique and unclonable that can be used as a silicon “fingerprint” for a wide range of security purposes, including encryption, identification, authentication, and security key generation.
Figure 5 shows a Relaxation Oscillator (ReO) PUF consists of ‘N’ identical ReOs (ReO1, ReO2, .....ReON), two n-bit multiplexers (MUXs), two counters, and a comparator. Each ReO generates a unique frequency when fed with different challenges or inputs. The frequency of 4.4 MHz is specially designed and generated for IoT sensor node applications. The MUXs can produce non-identical frequencies due to the process variations of the device, even though they are designed with the same device characteristics. The challenge or input applied to both MUXs selects one pair of ReO the frequency difference of which will determine the output. The obtained frequency difference in terms of 1-bit response (either 0 s or 1 s) is considered for key generation. The counter can help to count the number of oscillations of selected ReO pairs processed from MUXs in a fixed time interval. The pulse counts from the counters are compared with the comparator, which gives the response ‘0’ or ‘1’.
5 Experimental Results
The proposed ReOPUF circuit is implemented in UMC 65 nm technology and simulated with Cadence Spectre. To perform characterization of 50 different PUFs, 100 runs of Monte-Carlo simulations are performed. During simulation, intra-die and inter-die PVs are generated to evaluate the responses. Each 32-stage ReOPUF becomes active with the 5-bit challenge or input (C\(_{0}\) to C\(_{4}\)) and is evaluated under the nominal operating conditions of 27 \(^{\circ }\)C and 1.2 V supply voltage.
5.1 Evaluation of PUF Quality Metrics
The performance of the ReOPUF is measured and evaluated with the following metrics [20] as defined by National Institute of Standards and Technology (NIST).
5.1.1 Uniformity (u)
Uniformity is the measure of distribution of ‘1 s’ and ‘0 s’ in the response vector R\(_{i,j}\) and is defined as
where, R\(_{i,j}\) is the \(j^{th}\) binary bit of an n-bit response for an \(i^{th}\) input. An ideal PUF should have equal probabilities for ‘1’ and ‘0’ in response, i.e., 50%. We evaluate the 32-bit responses from 50 ReOPUF instances at nominal operating condition i.e., 27 \(^{\circ }\)C, 1.2 V is shown in Fig. 6. The distribution of 1’s and 0’s generated by the ReOPUF is shown in Fig. 7 as a pixel distribution with a white pixel interpreted as a ‘1’ and a black pixel as a ‘0’. The probability of generating 1 s is 45.31%, which indicates that ReOPUF output is not predictable and it is hard to attack.
5.1.2 Diffuseness (D)
Diffuseness (shown in Fig. 8) is the degree of variation observed in same ReOPUF with different challenges applied nominally. It can be measured by calculating the mean of Hamming Distance (HD) from the response vectors obtained as 49.53%. It is defined as
where ‘l’ represents randomly selected response vector from CRP space. \(R_{i}\) and \(R_{j}\) are two different n-bit response vectors obtained from two different challenges.
5.1.3 Uniqueness (U)
The randomness in different PUF responses reflects the performance in terms of uniqueness. Ideally, the probability of each response (i.e., ‘0’ or ‘1’) generated by identical PUFs with the same challenge should be 50%. Uniqueness (shown in Fig. 9) measures inter-chip variation among different ReOPUF instances implemented with same challenge. It can be calculated with inter-chip hamming distance (inter-HD) 49.22% as shown below
where \(R_{i}\) and \(R_{j}\) are two different n-bit response vectors obtained from same challenge and ‘m’ represents different ReOPUF instances with same challenge.
5.1.4 Reliability (R)
A PUF should generate the same response in any state for the same challenge applied. Unfortunately, the variations in the supply voltage or temperature can change the behavior of the IC in the form of circuit delay and lead to unpredicted responses. Therefore, the same response bits should be produced at different operating conditions.
Reliability is measured by intra-HD, which is performed between two n-bit response vectors generated from the same PUF instances with the same challenges. Ideally, it should be close to 0% for an environment-friendly PUF and can be calculated as follows.
where ‘m’ represents some measured trials applied on ReOPUF instances with the same challenge. \(R_{i,ref}\) is the reference response measured at normal operating conditions (27 \(^{\circ }\)C and 1.2 V), R\(_{i,t}\) is the \(t^{th}\) measured response at a different operating conditions. We measure the reliability of the 32-bit responses from 50 ReOPUF instances in different operating conditions.
The average reliability calculated from 50 ReOPUF responses over commercial range (0 \(^{\circ }\)C to 85 \(^{\circ }\)C) is 99.31% at 27 \(^{\circ }\)C as shown in Fig. 11, and the worst-case reliability is 97.19% at 0 \(^{\circ }\)C. A supply voltage variation up to ±10% VDD is applied to the ReOPUF as shown in Fig. 10. The corresponding reliability is 99.19% at 1.2 V, and the worst-case reliability is 97.97%. In addition, over the industrial range (−40 \(^{\circ }\)C to 100 \(^{\circ }\)C) the reliability is 97.41%. Table 1 presents the comparison of different PUF designs with ReOPUF. Table 2 shows the ReOPUF analysis with different temperatures.
6 Security Evaluation of the Proposed PUF
PUFs are specifically proposed for security applications that can withstand attacks under various threat models [21]. A PUF uses a CRP mechanism derived from inbuilt process variations performed by the ICs. Invasive attacks (such as reverse engineering attacks) may alter the physical properties of the device resulted in breaching of CRPs. However, PUF-based systems may be susceptible to two threat models such as PUF for authentication and PUF for secret key generation. If a PUF is used for authentication, the attacker can perform different trials to extract valid CRPs which can be used to crack the PUF function. If it is a secret key generation the attacker can concentrate on the PUF response pairs by exploiting the PUF weakness. In this section, we evaluate the security of PUF by performing the entropy analysis on the responses.
6.1 Entropy Analysis
Entropy can be used as a measure of unpredictability of a response key from PUFs, though the uncertainty from process variations is unmeasurable [22]. For example, a 32-bit key that is uniformly and randomly generated has 32 bits of entropy. It also takes (ignoring actual computing) 2\(^{32}-1\) guesses to break by brute force. Entropy fails to capture the number of guesses required if the possible keys are not chosen uniformly. Entropy is measured for ReOPUF generated 32-bit response when varying with different temperature and supply voltage variations as shown in Figs. 12 and 13. From the analysis, we assure that the ReOPUF responses offer high uncertainty and high average information carried out for communication. It is observed that at different temperatures the entropy varies from 2.39 to 2.48, while at different supply voltages it varies from 2.41 to 2.44.
6.2 Correlation Coefficient Analysis
The correlation coefficient is calculated for every PUF instance to determine if there is any correlation among the PUF cells [23]. If zero correlation is attained, then there is no such dependency exists among PUF cells. In the occurrence of −1 or +1 attainment there exists a linear dependency among the PUF cells i.e., weakly dependent (−1) or strongly dependent (+1) based on the CRPs generated by PUFs. For this test, 32 PUF cells are used. Pairwise, the covariance of two cells is divided by the product of their standard deviations as shown:
where \(\rho \) is defined as the correlation coefficient of two independent variables X and Y, \(\mu \) and \(\sigma \) represent mean and standard deviation of the independent responses obtained from the PUFs respectively. A positive (negative) value of \(\rho \) indicates a positive (negative) correlation between the two variables. The higher (lower) the value of \(\rho \) stronger the positive (negative) correlation. The closer this value lies to zero the weaker the relationship between the two PUF cells. The obtained \(\rho \) for ReOPUF falls between 1.57 to 2.59 states that the responses are strongly correlated to the respective challenges and the uncertainty becomes the matter of reliability in security evaluation.
6.3 Power Analysis of ReOPUF
We measure the power consumption of the single-stage implementation of ReOPUF and RO-PUF as shown in Table 3. For 32-bit key implementations, the estimated average powers of ReOPUF and RO-PUF are 3.79 mW and 15 mW respectively.
7 Conclusion
In this paper, we have introduced a relaxation oscillator-based PUF mechanism with the advantage that challenges fed through simple oscillation can achieve more reliability than any other oscillator PUFs. The experimental evaluation of ReOPUF shows the uniqueness and reliability of 49.22% and 97.97% respectively, which is better than that of the previous works. ReOPUF significantly improves upon the previous ROPUF designs, and has the potential to be the basis for CRPs based identification and authentication applications designed for IoT.
References
Babaei, A., Schiele, G.: Physical unclonable functions in the internet of things: state of the art and open challenges. Sensors 19(14), 3208 (2019)
Challa, R.P., Islam, S.A., Katkoori, S.: An SR flip-flop based physical unclonable functions for hardware security. In: Proceedings of 2019 IEEE 62nd International Midwest Symposium on Circuits and Systems (MWSCAS), Dallas, TX, USA, pp. 574–577 (2019)
Govindaraj, R., Ghosh, S., Katkoori, S.: Design, analysis and application of embedded resistive RAM based strong arbiter PUF. IEEE Trans. Dependable Secure Comput. 17(6), 1232–1242 (2020)
Potkonjak, M., Goudar, V.: Public physical unclonable functions. Proc. IEEE 102(8), 1142–1156 (2014)
Liang, W., Liao, B., Long, J., Jiang, Y., Peng, L.: Study on PUF based secure protection for IC design. Microprocess. Microsyst. 45, 56–66 (2016)
Abu-Rahma, M.H., Anis, M.: Variability in VLSI circuits: sources and design considerations. In: 2007 IEEE International Symposium on Circuits and Systems, pp. 3215–3218. IEEE, May 2007
Lee, J.W., Lim, D., Gassend, B., Suh, G.E., Van Dijk, M., Devadas, S.: A technique to build a secret key in integrated circuits for identification and authentication applications. In: 2004 Symposium on VLSI Circuits. Digest of Technical Papers (IEEE Cat. No. 04CH37525), pp. 176–179. IEEE, June 2004
Lim, D., Lee, J.W., Gassend, B., Suh, G.E., Van Dijk, M., Devadas, S.: Extracting secret keys from integrated circuits. IEEE Trans. Very Large Scale Integr. (VLSI) Syst. 13(10), 1200–1205 (2005)
O’donnell, C.W., Suh, G.E., Devadas, S.: PUF-based random number generation. In: MIT CSAIL CSG Technical Memo, vol. 481 (2004)
Suh, G.E., Devadas, S.: Physical unclonable functions for device authentication and secret key generation. In: 2007 44th ACM/IEEE Design Automation Conference, pp. 9–14. IEEE, June 2007
Bernard, F., Fischer, V., Costea, C., Fouquet, R.: Implementation of ring-oscillators-based physical unclonable functions with independent bits in the response. Int. J. Reconfig. Comput. 2012 (2012)
Gao, M., Lai, K., Qu, G.: A highly flexible ring oscillator PUF. In: Proceedings of the 51st Annual Design Automation Conference, pp. 1–6, June 2014
Avaroğlu, E.: The implementation of ring oscillator based PUF designs in Field Programmable Gate Arrays using of different challenge. Phys. A 546, 124291 (2020)
Tao, S., Dubrova, E.: MVL-PUFs: multiple-valued logic physical unclonable functions. Int. J. Circuit Theory Appl. 45(2), 292–304 (2017)
Cao, Y., Zhang, L., Chang, C.H., Chen, S.: A low-power hybrid RO PUF with improved thermal stability for lightweight applications. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 34(7), 1143–1147 (2015)
Mansouri, S.S., Dubrova, E.: Ring oscillator physical unclonable function with multi level supply voltages. In: 2012 IEEE 30th International Conference on Computer Design (ICCD), pp. 520–521. IEEE, September 2012
Rahman, M.T., Forte, D., Fahrny, J., Tehranipoor, M.: ARO-PUF: an aging-resistant ring oscillator PUF design. In: 2014 Design, Automation & Test in Europe Conference & Exhibition (DATE), pp. 1–6. IEEE, March 2014
Liu, C.Q., Cao, Y., Chang, C.H.: ACRO-PUF: a low-power, reliable and aging-resilient current starved inverter-based ring oscillator physical unclonable function. IEEE Trans. Circuits Syst. I Regul. Pap. 64(12), 3138–3149 (2017)
Sahoo, S.R., Kumar, S., Mahapatra, K., Swain, A.: A novel aging tolerant RO-PUF for low power application. In: 2016 IEEE International Symposium on Nanoelectronic and Information Systems (iNIS), pp. 187–192. IEEE, December 2016
Maiti, A., Gunreddy, V., Schaumont, P.: A systematic method to evaluate and compare the performance of physical unclonable functions. In: Athanas, P., Pnevmatikatos, D., Sklavos, N. (eds.) Embedded Systems Design with FPGAs, pp. 245–267. Springer, New York (2013). https://doi.org/10.1007/978-1-4614-1362-2_11
Laguduva, V., Islam, S.A., Aakur, S., Katkoori, S., Karam, R.: Machine learning based IoT edge node security attack and countermeasures. In: 2019 IEEE Computer Society Annual Symposium on VLSI (ISVLSI), pp. 670–675. IEEE, July 2019
Van Den Berg, R.: Entropy analysis of physical unclonable functions. MSc. thesis, Dept. Math. Comput. Sci., Eindhoven Univ. Technol., Eindhoven (2012)
Lin, L., Holcomb, D., Krishnappa, D.K., Shabadi, P., Burleson, W.: Low-power sub-threshold design of secure physical unclonable functions. In: Proceedings of the 16th ACM/IEEE International Symposium on Low Power Electronics and Design, pp. 43–48, August 2010
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2022 IFIP International Federation for Information Processing
About this paper
Cite this paper
Podeti, R., Patri, S.R., Katkoori, S., Pullakandam, M. (2022). ReOPUF: Relaxation Oscillator Physical Unclonable Function for Reliable Key Generation in IoT Security. In: Camarinha-Matos, L.M., Heijenk, G., Katkoori, S., Strous, L. (eds) Internet of Things. Technology and Applications. IFIPIoT 2021. IFIP Advances in Information and Communication Technology, vol 641. Springer, Cham. https://doi.org/10.1007/978-3-030-96466-5_11
Download citation
DOI: https://doi.org/10.1007/978-3-030-96466-5_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-96465-8
Online ISBN: 978-3-030-96466-5
eBook Packages: Computer ScienceComputer Science (R0)