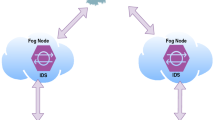
Abstract
Smart healthcare applications such as smart fitness, smart watches, and elderly remote monitoring devices have reduced the load on traditional healthcare organizations and led to healthier lifestyles. Nevertheless, these devices are under high risk of zero-day attacks because of their fragile nature and network characteristics. Furthermore, few companies developing these devices take care of security requirements. Attack detection using machine learning techniques such as ensemble learning has been adopted to IoT as a second line of defense. However, most of the proposed approaches are either heavy to implement at Internet of Medical Things (IoMT) devices or are cloud based which lead to delay in the detection of attacks. Also, these detections are centralized which are less compatible with IoT. In this study, an ensemble attack detection method is proposed for the detection of stream data attack at fog layer. The base classifiers are stream and incremental based algorithms, which are compatible with IoMT nature and fog devices. A weighted majority algorithm is followed to obtain best accuracy with reduced latency. The results demonstrated that the proposed model is effective for attack detection at fog layer, while it gives better accuracy, higher detection rate and lower false positive rate with average detection time.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Farahani, B., Firouzi, F., Chang, V., Badaroglu, M., Constant, N., Mankodiya, K.: Towards fog-driven IoT eHealth: promises and challenges of IoT in medicine and healthcare. Future Gener. Comput. Syst. 78, 659–676 (2018)
Gatouillat, A., Badr, Y., Massot, B., Sejdic, E.: Internet of medical things: a review of recent contributions dealing with cyber-physical systems in medicine. IEEE Internet Things J. 5(5), 3810–3822 (2018). https://doi.org/10.1109/jiot.2018.2849014
Pandey, P., Litoriya, R.: Elderly care through unusual behavior detection: a disaster management approach using IoT and intelligence. IBM J. Res. Dev. 64(1/2), 15:1–15:11 (2020). https://doi.org/10.1147/JRD.2019.2947018
Firouzi, F., Rahmani, A.M., Mankodiya, K., Badaroglu, M., Merrett, G.V., Wong, P., Farahani, B.: Internet-of-Things and big data for smarter healthcare: From device to architecture, applications and analytics. Future Gener. Comput. Syst. 78, 583–586 (2018)
Uddin, M.A., Stranieri, A., Gondal, I., Balasubramanian, V.: Continuous patient monitoring with a patient centric agent: a block architecture. IEEE Access 6, 32700–32726 (2018). https://doi.org/10.1109/ACCESS.2018.2846779
Ma, Y., Wang, Y., Yang, J., Miao, Y., Li, W.: Big health application system based on health Internet of Things and big data. IEEE Access 5, 7885–7897 (2017). https://doi.org/10.1109/ACCESS.2016.2638449
Dang, L.M., Piran, M., Han, D., Min, K., Moon, H.: A survey on internet of things and cloud computing for healthcare. Electronics 8(7), 768 (2019)
Rahmani, A.M., Gia, T.N., Negash, B., Anzanpour, A., Azimi, I., Jiang, M., Liljeberg, P.: Exploiting smart e-Health gateways at the edge of healthcare Internet-of-Things: a fog computing approach. Future Gener. Comput. Syst. 78, 641–658 (2018)
Fornasier, M.D.: The applicability of the Internet of Things (IoT) between fundamental rights to health and to privacy. Rev. Investig. Const. 6(2), 297–321 (2019). https://doi.org/10.5380/rinc.v6i2.67592
Yaacoub, J.-P.A., Noura, M., Noura, H.N., Salman, O., Yaacoub, E., Couturier, R., Chehab, A.: Securing internet of medical things systems: limitations, issues and recommendations. Future Gener. Comput. Syst. 105, 581–606 (2020). https://doi.org/10.1016/j.future.2019.12.028
Hatzivasilis, G., Soultatos, O., Ioannidis, S., Verikoukis, C., Demetriou, G., Tsatsoulis, C.I.: Review of security and privacy for the Internet of Medical Things (IoMT) resolving the protection concerns for the novel circular economy bioinformatics. In: 2019 15th IEEE International Conference on Distributed Computing in Sensor Systems, pp. 457–464. IEEE, New York (2019)
Jaigirdar, F.T., Rudolph, C., Bain, C.: Can I trust the data I see? A physician’s concern on medical data in IoT health architectures. In: Proceedings of the Australasian Computer Science Week Multiconference, p. 10 (2019)
Rathore, H., Mohamed, A., Guizani, M.: Deep learning-based security schemes for implantable medical devices. Energy Eff. Med. Devices Healthcare Appl. 1st edn. Elsevier, Cambridge (2020)
Newaz, A., Sikder, A.K., Rahman, M.A., Uluagac, A.S.: A survey on security and privacy issues in modern healthcare systems: attacks and defenses. arXiv preprint arXiv:2005.07359 (2020)
Sun, Y., Lo, F.P.-W., Lo, B.: Security and privacy for the Internet of Medical Things enabled healthcare systems: a survey. IEEE Access 7, 183339–183355 (2019)
Cui, L., Yang, S., Chen, F., Ming, Z., Lu, N., Qin, J.: A survey on application of machine learning for Internet of Things. Int. J. Mach. Learn. Cybern. 9(8), 1399–1417 (2018)
Zhang, H., Li, J., Wen, B., Xun, Y., Liu, J.: Connecting Intelligent Things in smart hospitals using NB-IoT. IEEE Internet Things J. 5(3), 1550–1560 (2018). https://doi.org/10.1109/JIOT.2018.2792423
Durga, S., Nag, R., Daniel, E.: Survey on machine learning and deep learning algorithms used in Internet of Things (IoT) healthcare. In: 2019 3rd International Conference on Computing Methodologies and Communication (ICCMC), pp. 1018–1022. IEEE (2019)
Escamilla-Ambrosio, P., Rodríguez-Mota, A., Aguirre-Anaya, E., Acosta-Bermejo, R., Salinas-Rosales, M.: Distributing computing in the Internet of Things: cloud, fog and edge computing overview. In: NEO 2016, pp. 87–115. Springer (2018)
Sun, H., Wang, X., Buyya, R., Su, J.: CloudEyes: cloud-based malware detection with reversible sketch for resource-constrained Internet of Things (IoT) devices. Softw. Pract. Exp. 47(3), 421–441 (2017)
Pace, P., Aloi, G., Gravina, R., Caliciuri, G., Fortino, G., Liotta, A.: An edge-based architecture to support efficient applications for healthcare industry 4.0. IEEE Trans. Ind. Inform. 15(1), 481–489 (2019). https://doi.org/10.1109/TII.2018.2843169
Alrashdi, I., Alqazzaz, A., Alharthi, R., Aloufi, E., Zohdy, M.A., Ming, H.: FBAD: fog-based attack detection for IoT healthcare in smart cities. In: 2019 IEEE 10th Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), pp. 0515–0522. IEEE (2019)
Kumar, A., Kaur, P., Sharma, P.: A survey on Hoeffding tree stream data classification algorithms. CPUH-Res. J. 1(2), 28–32 (2015)
Bifet, A., Holmes, G., Pfahringer, B., Kranen, P., Kremer, H., Jansen, T., Seidl, T.: MOA: massive online analysis, a framework for stream classification and clustering. In: Proceedings of the First Workshop on Applications of Pattern Analysis, pp. 44–50 (2010)
Bifet, A.: Mining Internet of Things (IoT) big data streams. In: SIMBig, pp. 15–16 (2016)
Akbar, A., Khan, A., Carrez, F., Moessner, K.: Predictive analytics for complex IoT data streams. IEEE Internet Things J. 4(5), 1571–1582 (2017)
Bifet, A., Gavaldà, R., Holmes, G., Pfahringer, B.: Machine Learning for Data Streams: With Practical Examples in MOA. MIT Press, Cambridge (2018)
Gupta, A., Pandey, O.J., Shukla, M., Dadhich, A., Mathur, S., Ingle, A.: Computational intelligence based intrusion detection systems for wireless communication and pervasive computing networks. In: 2013 IEEE International Conference on Computational Intelligence and Computing Research, pp. 1–7. IEEE (2013)
Jan, S.U., Ahmed, S., Shakhov, V., Koo, I.: Toward a lightweight intrusion detection system for the Internet of Things. IEEE Access 7, 42450–42471 (2019)
Balakrishnan, N., Rajendran, A., Pelusi, D., Ponnusamy, V.: Deep belief network enhanced intrusion detection system to prevent security breach in the Internet of Things. Internet Things 100112 (2019, in press)
Hou, X., Wang, J., Jiang, C., Guan, S., Ren, Y.: A sink node assisted lightweight intrusion detection mechanism for WBAN. In: 2018 IEEE International Conference on Communications (ICC), pp. 1–6. IEEE (2018)
Maleh, Y., Ezzati, A., Qasmaoui, Y., Mbida, M.: A global hybrid intrusion detection system for wireless sensor networks. Procedia Comput. Sci. 52, 1047–1052 (2015)
Jia, B., Huang, X., Liu, R., Ma, Y.: A DDoS attack detection method based on hybrid heterogeneous multiclassifier ensemble learning. J. Electr. Comput. Eng. 2017, 1–9 (2017)
Gao, X., Shan, C., Hu, C., Niu, Z., Liu, Z.: An adaptive ensemble machine learning model for intrusion detection. IEEE Access 7, 82512–82521 (2019)
Canadian Institute for Cybersecurity. https://www.unb.ca/cic/datasets/nsl.html. Access Date
Begli, M., Derakhshan, F., Karimipour, H.: A layered intrusion detection system for critical infrastructure using machine learning. In: 2019 IEEE 7th International Conference on Smart Energy Grid Engineering (SEGE), pp. 120–124. IEEE (2019)
Lopez-Martin, M., Carro, B., Sanchez-Esguevillas, A., Lloret, J.: Conditional variational autoencoder for prediction and feature recovery applied to intrusion detection in IoT. Sensors 17(9), 1967 (2017)
Pajouh, H.H., Javidan, R., Khayami, R., Ali, D., Choo, K.-K.R.: A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Trans. Emerg. Topics Comput. 7, 314–323 (2016)
Hameed, S.S., Hassan, R., Muhammad, F.F.: Selection and classification of gene expression in autism disorder: use of a combination of statistical filters and a GBPSO-SVM algorithm. PloS One 12(11), e0187371 (2017)
Kumar, R., Zhang, X., Wang, W., Khan, R.U., Kumar, J., Sharif, A.: A multimodal malware detection technique for Android IoT devices using various features. IEEE Access 7, 64411–64430 (2019)
Roopak, M., Tian, G.Y., Chambers, J.: Multi-objective-based feature selection for DDoS attack detection in IoT networks. IET Netw. 9(3), 120–127 (2020)
Hameed, S.S., Petinrin, O.O., Osman, A., Hashi, F.S.: Filter-wrapper combination and embedded feature selection for gene expression data. Int. J. Adv. Soft Comput. Appl. 10(1), 90–105 (2018)
Hameed, S.S., Muhammad, F.F., Hassan, R., Saeed, F.: Gene selection and classification in microarray datasets using a hybrid approach of PCC-BPSO/GA with multi classifiers. J. Comput. Sci. 14(6), 868–880 (2018)
RM, S.P., Maddikunta, P.K.R., Parimala, M., Koppu, S., Reddy, T., Chowdhary, C.L., Alazab, M.: An effective feature engineering for DNN using hybrid PCA-GWO for intrusion detection in IoMT architecture. Comput. Commun. 160, 139–149 (2020)
Cao, L., Chua, K.S., Chong, W., Lee, H., Gu, Q.: A comparison of PCA, KPCA and ICA for dimensionality reduction in support vector machine. Neurocomputing 55(1–2), 321–336 (2003)
Alhaj, T.A., Siraj, M.M., Zainal, A., Elshoush, H.T., Elhaj, F.: Feature selection using information gain for improved structural-based alert correlation. PloS One 11(11), e0166017 (2016)
Singh, N.A., Singh, K.J., De, T.: Distributed denial of service attack detection using naive Bayes classifier through info gain feature selection. In: Proceedings of the International Conference on Informatics and Analytics, pp. 1–9 (2016)
Sagi, O., Rokach, L.: Ensemble learning: a survey. Wiley Interdiscip. Rev. Data Min. Knowl. Discov. 8(4), e1249 (2018)
Mukherjee, A., De, D., Ghosh, S.K.: FogIoHT: a weighted majority game theory based energy-efficient delay-sensitive fog network for internet of health things. Internet Things 11, 100181 (2020)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Hameed, S.S., Hassan, W.H., Latiff, L.A. (2021). An Efficient Fog-Based Attack Detection Using Ensemble of MOA-WMA for Internet of Medical Things. In: Saeed, F., Mohammed, F., Al-Nahari, A. (eds) Innovative Systems for Intelligent Health Informatics. IRICT 2020. Lecture Notes on Data Engineering and Communications Technologies, vol 72. Springer, Cham. https://doi.org/10.1007/978-3-030-70713-2_70
Download citation
DOI: https://doi.org/10.1007/978-3-030-70713-2_70
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-70712-5
Online ISBN: 978-3-030-70713-2
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)