Abstract
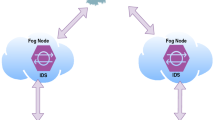
Malicious attacks are common among the Internet of Things (IoT) devices that are installed in several locations like offices, homes, healthcare facilities, and transportation. Due to massive amounts of data created by IoT devices, machine learning is frequently used to detect cyber-attacks on these devices. The fact that fog devices may not have the computing or memory capability to identify threats in a timely manner is a source of concern. According to this article, machine learning model selection and real-time prediction can both be offloaded from the cloud, and both jobs can be performed by fog nodes, which are distributed computing devices. A cloud-based ensemble machine learning model is constructed using the provided method, and subsequently, attacks on fog nodes are identified in real time using the model. The NSL-KDD dataset is used to evaluate the performance of this approach. The results indicate that the proposed technique is effective in terms of a variety of performance criteria, including execution time, precision, recall, accuracy, and the F1 measure.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Akhtar MS, Feng T (2022) Comparison of classification model for the detection of cyber-attack using ensemble learning models. EAI Endorsed Trans Scalable Inf Syst e39–e39. https://doi.org/10.4108/eai.1-2-2022.173293
Shahraki A, Abbasi M, Taherkordi A, Jurcut AD (2022) A comparative study on online machine learning techniques for network traffic streams analysis. Comput Netw 207:108836. https://www.sciencedirect.com/science/article/pii/S1389128622000512
Omolara AE, Alabdulatif A, Abiodun OI, Alawida M, Alabdulatif A, Arshad H (2022) The internet of things security: a survey encompassing unexplored areas and new insights. Comput Secur 112:102494. https://www.sciencedirect.com/science/article/pii/S0167404821003187
Ahmad W, Rasool A, Javed AR, Baker T, Jalil Z (2021) Cyber security in iot-based cloud computing: a comprehensive survey. Electronics 11(1). https://www.mdpi.com/2079-9292/11/1/16
Sivakamasundari S, Dharmarajan K (2021) Fast and frugal random forest decision tree classifier based cloud user authentication for secure cloud IoT services. J Mech Eng 6(3). ISSN: 0974-5823. Anna University Annexure-https://Kalaharijournals.Com/Ijme-V6-3-2021.Php
Sharma P, Jain S, Gupta S, Chamola V (2021) Role of machine learning and deep learning in securing 5G-driven industrial IoT applications. Ad Hoc Netw 123:102685. https://doi.org/10.1016/j.adhoc.2021.102685
Ahakonye LAC, Amaizu GC, Nwakanma CI, Lee JM, Kim DS (2021) Enhanced vulnerability detection in SCADA systems using hyper-parameter-tuned ensemble learning. In: 2021 International conference on information and communication technology convergence (ICTC), pp 458–461. IEEE
Singh S, Sulthana R, Shewale T, Chamola V, Benslimane A, Sikdar B (2021) Machine-learning-assisted security and privacy provisioning for edge computing: a survey. IEEE Internet Things J 9(1):236–260. https://ieeexplore.ieee.org/document/9490350
Sivakamasundari S, Dharmarajan K (2021) Fast syndrome-cryptographic hash storage based tanimoto index margin relaxing support vector regressive data auditing with IoT. Webology 18(5). https://Www.Webology.Org/Abstract.Php?Id=1451
Al-Garadi MA, Mohamed A, Al-Ali AK, Du X, Ali I, Guizani M (2020) A survey of machine and deep learning methods for internet of things (IoT) security. IEEE Commun Surv Tutorials 22(3):1646–1685. https://ieeexplore.ieee.org/document/9072101
Divya V, Leena Sri R (2020) Intelligent real-time multimodal fall detection in fog infrastructure using ensemble learning. In: Challenges and trends in multimodal fall detection for healthcare, pp 53–79
Pashaei Barbin J, Yousefi S, Masoumi B (2020) Efficient service recommendation using ensemble learning in the internet of things (IoT). J Ambient Intell Humanized Comput 11(3):1339–1350. https://www.researchgate.net/publication/335924004_Efficient_service_recommendation_using_ensemble_learning_in_the_internet_of_things_IoT
Sivakamasundari S, Dharmarajan K (2020) Adaptive discriminant quadratic boosting classification based radix hash data storage for context aware cloud IoT services. Eur J Mol Clin Med 7(11): 7808–7825. https://Ejmcm.Com/Article_10364.Html
Verma A, Ranga V (2020) Machine learning based intrusion detection systems for IoT applications. Wireless Pers Commun 111(4):2287–2310
Tuli S, Basumatary N, Gill SS, Kahani M, Arya RC, Wander GS, Buyya R (2020) HealthFog: an ensemble deep learning-based smart healthcare system for automatic diagnosis of heart diseases in integrated IoT and fog computing environments. Future Gener Comput Syst 104:187–200. https://www.sciencedirect.com/science/article/abs/pii/S0167739X19313391
Ullah I, Mahmoud QH (2020) A two-level flow-based anomalous activity detection system for IoT networks. Electronics 9(3):530
Jurcut A, Niculcea T, Ranaweera P, Le-Khac NA (2020) Security considerations for internet of things: a survey. SN Computer Science 1(4):1–19
Susilo B, Sari RF (2020) Intrusion detection in IoT networks using deep learning algorithm. Information 11(5):279
Ahmim A, Maglaras L, Ferrag MA, Derdour M, Janicke H (2019) A novel hierarchical intrusion detection system based on decision tree and rules-based models. In: 2019 15th International conference on distributed computing in sensor systems (DCOSS), pp 228–233. IEEE
Cihan ATAÇ, Akleylek S (2019) A survey on security threats and solutions in the age of IoT. Avrupa Bilim ve Teknoloji Dergisi 15:36–42
Bakhsh ST, Alghamdi S, Alsemmeari RA, Hassan SR (2019) An adaptive intrusion detection and prevention system for Internet of Things. Int J Distrib Sens Netw 15(11):1550147719888109
Soe YN, Feng Y, Santosa PI, Hartanto R, Sakurai K (2019) Implementing lightweight IoT-IDS on raspberry pi using correlation-based feature selection and its performance evaluation. In: International conference on advanced information networking and applications, pp 458–469. Springer, Cham
Thamilarasu G, Chawla S (2019) Towards deep-learning-driven intrusion detection for the internet of things. Sensors 19(9):1977
Sivakamasundari S, Dharmarajan K (2019) Survival study on secured cloud service provisioning techniques with IoT. J Crit Rev 7(01). ISSN: 2394-5125. http://Www.Jcreview.Com/Index.Php?Iid=2019-7-1.000&&Jid=197&Lng
Anthi E, Williams L, Burnap P (2018) Pulse: an adaptive intrusion detection for the internet of things. In: IET, Cybersecurity of the IoT—2018. London
Doshi R, Apthorpe N, Feamster N (2018) Machine learning DDoS detection for consumer internet of things devices. In: 2018 IEEE security and privacy workshops (SPW), pp 29–35. IEEE
Sharafaldin I, Habibi Lashkari A, Ghorbani AA (2018) A detailed analysis of the CICIDS2017 data set. In: International conference on information systems security and privacy, pp 172–188. Springer, Cham. https://www.semanticscholar.org/paper/A-Detailed-Analysis-of-the-CICIDS2017-Data-Set-Sharafaldin-Lashkari/cafa09df1905ec46f5a0ab25c2daa77252ed458d
Keegan N, Ji SY, Chaudhary A, Concolato C, Yu B, Jeong DH (2016) A survey of cloud-based network intrusion detection analysis. HCIS 6(1):1–16
Yassin W, Udzir NI, Muda Z, Abdullah A, Abdullah MT (2012) A cloud-based intrusion detection service framework. In: Proceedings of the 2012 international conference on cyber security, cyber warfare and digital forensic (CyberSec), pp 213–218. IEEE
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Sivakamasundari, S., Dharmarajan, K. (2023). Certain Investigations on Ensemble Learning and Machine Learning Techniques with IoT in Secured Cloud Service Provisioning. In: Khanna, A., Polkowski, Z., Castillo, O. (eds) Proceedings of Data Analytics and Management . Lecture Notes in Networks and Systems, vol 572. Springer, Singapore. https://doi.org/10.1007/978-981-19-7615-5_53
Download citation
DOI: https://doi.org/10.1007/978-981-19-7615-5_53
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-19-7614-8
Online ISBN: 978-981-19-7615-5
eBook Packages: Intelligent Technologies and RoboticsIntelligent Technologies and Robotics (R0)